附件
Created By AccessData® FTK® Imager 4.7.1.2
Case Information:
Acquired using: ADI4.7.1.2
Case Number:
Evidence Number:
Unique Description:
Examiner:
Notes:
--------------------------------------------------------------
Information for C:\Users\skills\Desktop\disk.ad1:
[Custom Content Sources]
F:\:NONAME [NTFS]|[root]|Windows|*(Wildcard,Consider Case,Include Subdirectories)
F:\:NONAME [NTFS]|[root]|ProgramData|*(Wildcard,Consider Case,Include Subdirectories)
F:\:NONAME [NTFS]|[root]|Program Files (x86)|*(Wildcard,Consider Case,Include Subdirectories)
F:\:NONAME [NTFS]|[root]|Program Files|*(Wildcard,Consider Case,Include Subdirectories)
F:\:NONAME [NTFS]|[root]|Documents and Settings|*(Wildcard,Consider Case,Include Subdirectories)
F:\:NONAME [NTFS]|[root]|PerfLogs|*(Wildcard,Consider Case,Include Subdirectories)
F:\:NONAME [NTFS]|[root]|System Volume Information|*(Wildcard,Consider Case,Include Subdirectories)
[Computed Hashes]
MD5 checksum: a576646c40769abb7dd36904417b6a4f
SHA1 checksum: 9cee1fe36957674626661e1197b19b5f0b047026
Image information:
Acquisition started: Tue Nov 5 11:04:42 2024
Acquisition finished: Tue Nov 5 11:49:00 2024
Segment list:
C:\Users\skills\Desktop\disk.ad1
Image Verification Results:
Verification started: Tue Nov 5 11:52:50 2024
Verification finished: Tue Nov 5 12:07:07 2024
MD5 checksum: a576646c40769abb7dd36904417b6a4f : verified
SHA1 checksum: 9cee1fe36957674626661e1197b19b5f0b047026 : verified告诉我们disk.ad1是由 FTK Imager 4.7.1.2创建的映像,可以用FTK挂载,另一个附件是磁盘镜像,vol即可分析
威胁分析1
请问,firefox 进程自有记录以来一共发送了多少字节的数据?
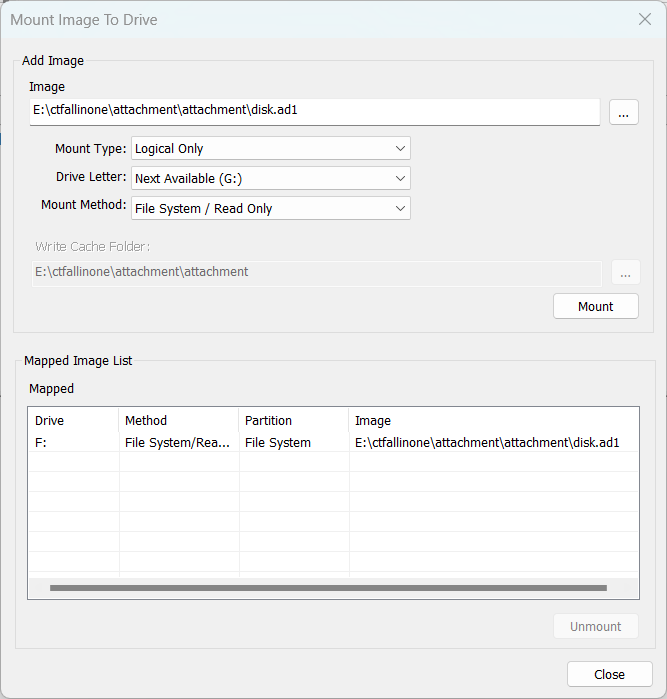
先挂载一下
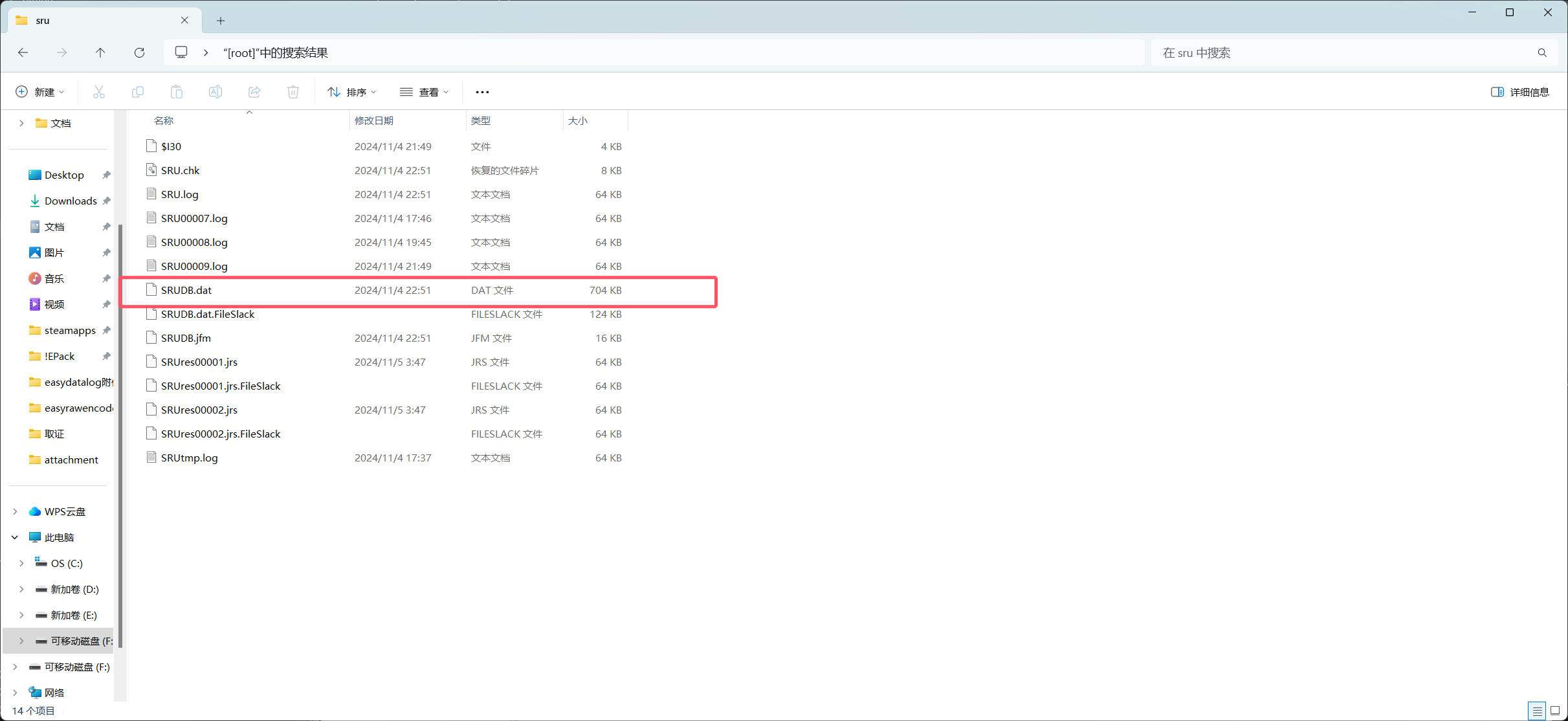
windows服务报告可以使用SRUDB.dat查看
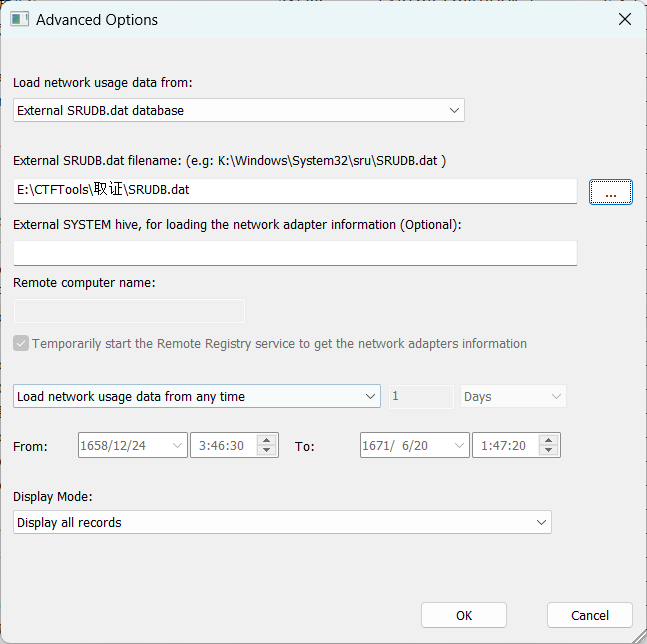
使用NetworkUsageView解析
选择外部SRUDB.dat
过滤出firefox进程的使用情况
一共发送3981907+384784=4366691字节
威胁分析2
请问,Windows Defender 检测到的第一个恶意软件的威胁 ID 是什么?
Windows Defender检测恶意威胁的日志ID为1116,所以需要找第一个日志ID为1116的事件
直接用windows事件查看器查看Defender的事件
传入磁盘\Windows\System32\winevt\Logs\Microsoft-Windows-Windows Defender%4Operational.evtx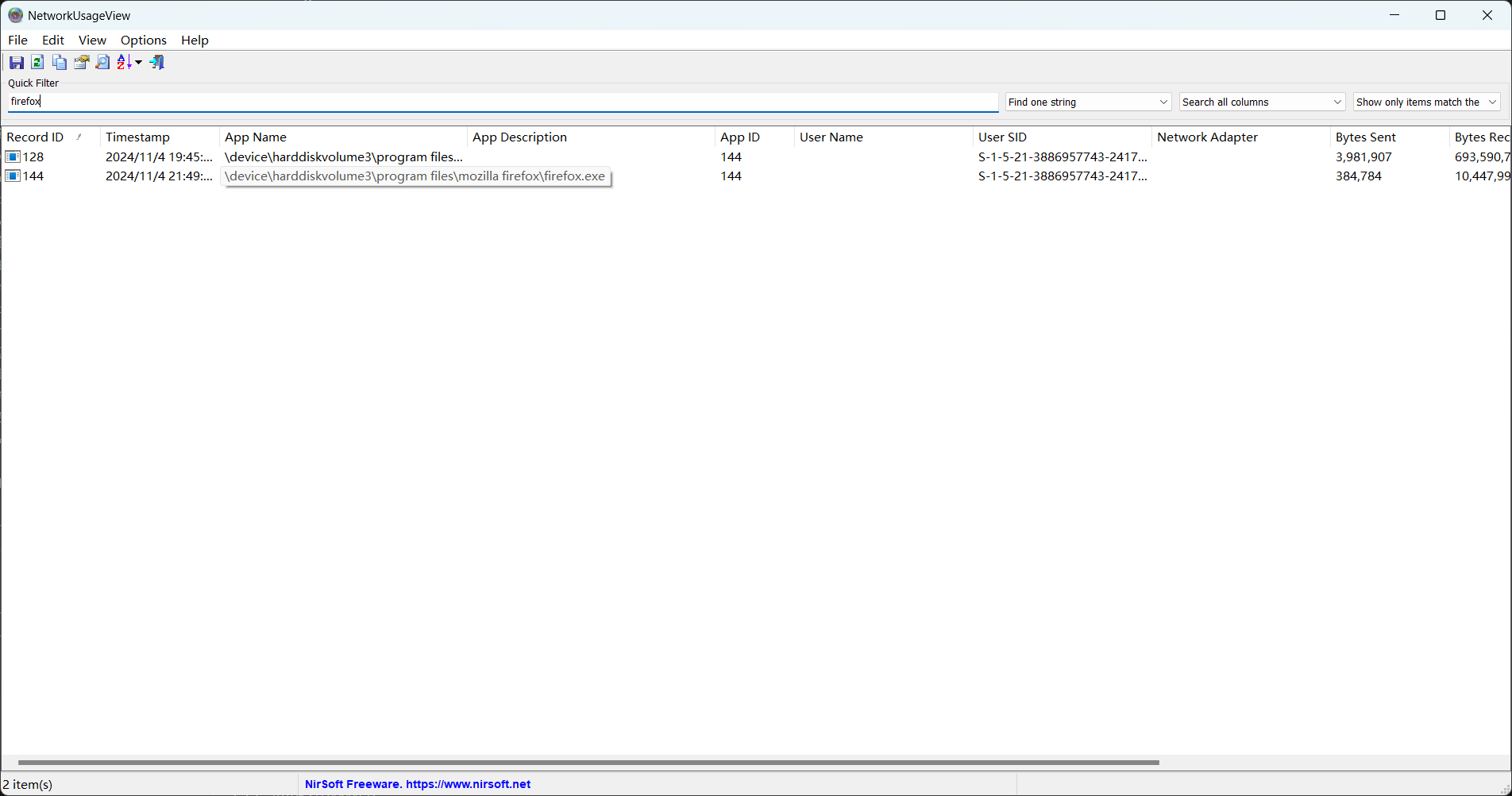
ID:2147729928
威胁分析3
请问,系统中正在运行的恶意软件的内部名称是什么?
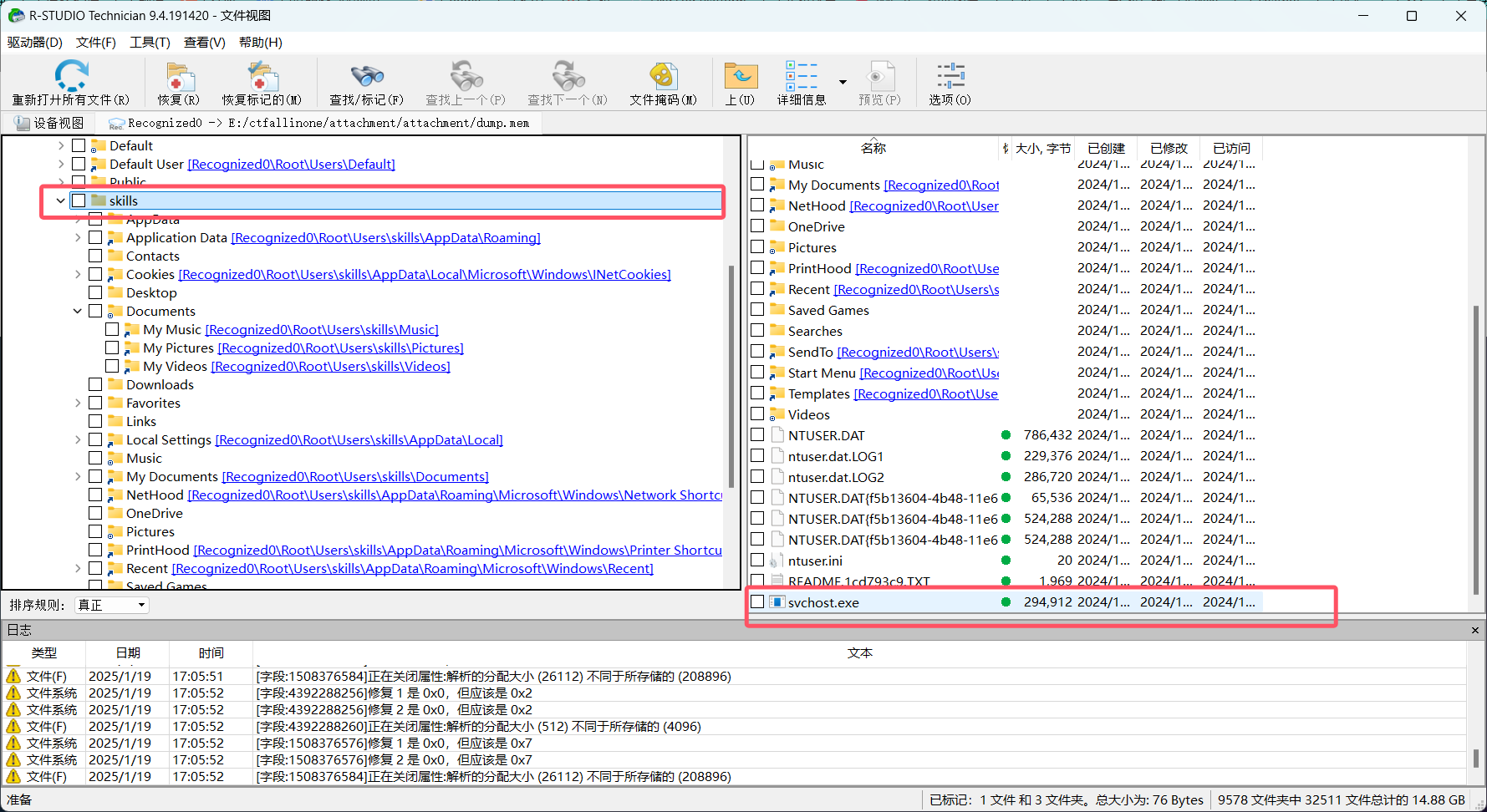
R-S查看文件,发现用户目录下有个奇怪的文件svchost.exe,它应该在C:\Windows\System32\svchost.exe
用volality dump下来
PS E:\CTF\取证> .\volatility.exe -f .\dump.mem --profile=Win10x64_14393 dumpfiles --regex "skills\\svchost\.exe" -D .
Volatility Foundation Volatility Framework 2.6
ImageSectionObject 0xffff9a88056a9ef0 5784 \Device\HarddiskVolume3\Users\skills\svchost.exe
DataSectionObject 0xffff9a88056a9ef0 5784 \Device\HarddiskVolume3\Users\skills\svchost.exe用pestudio查看文件名称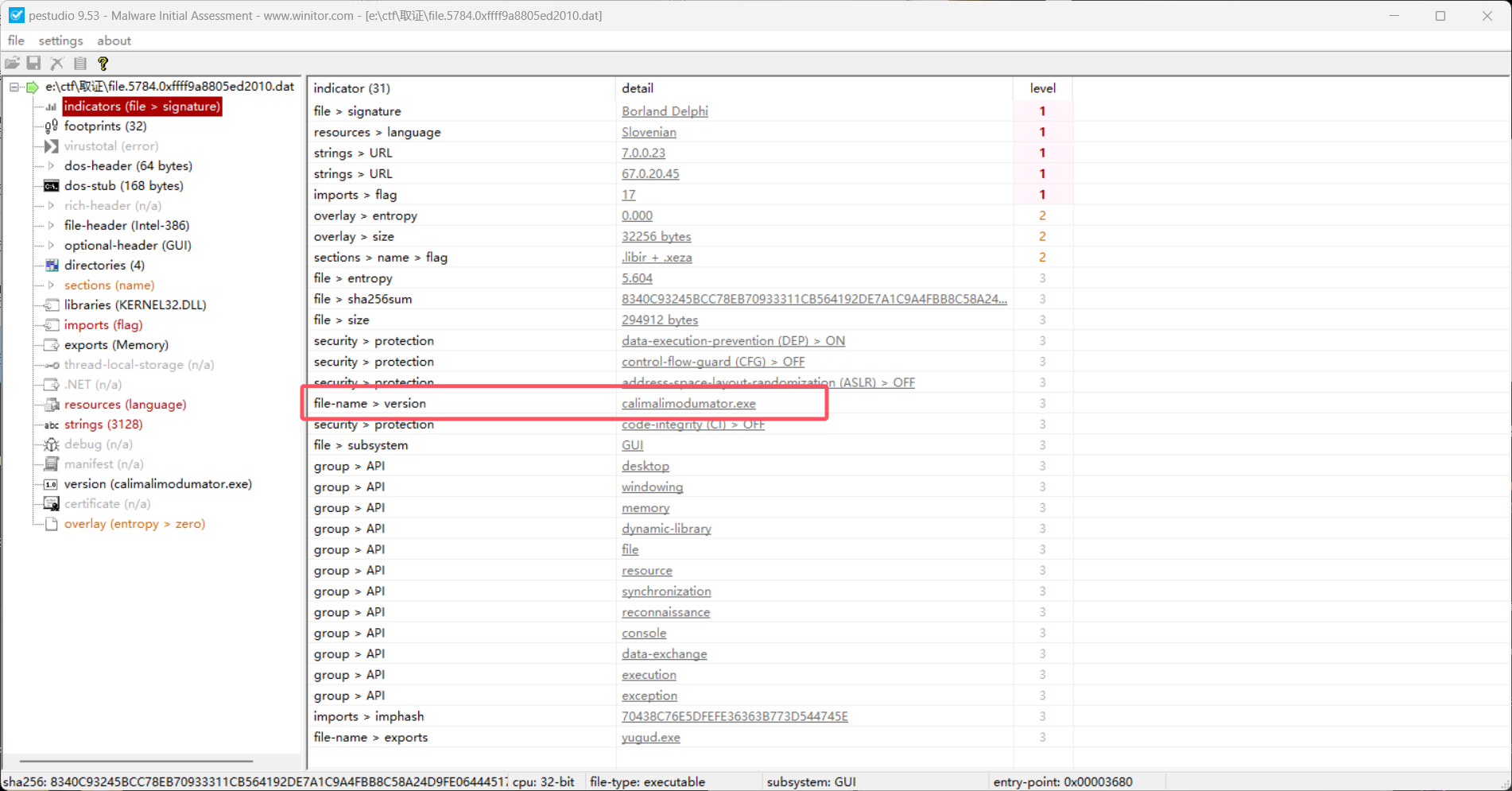
calimalimodumator.exe
威胁分析4
请问,恶意软件在进程内存中存储密钥的内存地址是什么?
对磁盘按关键词搜索找到勒索信息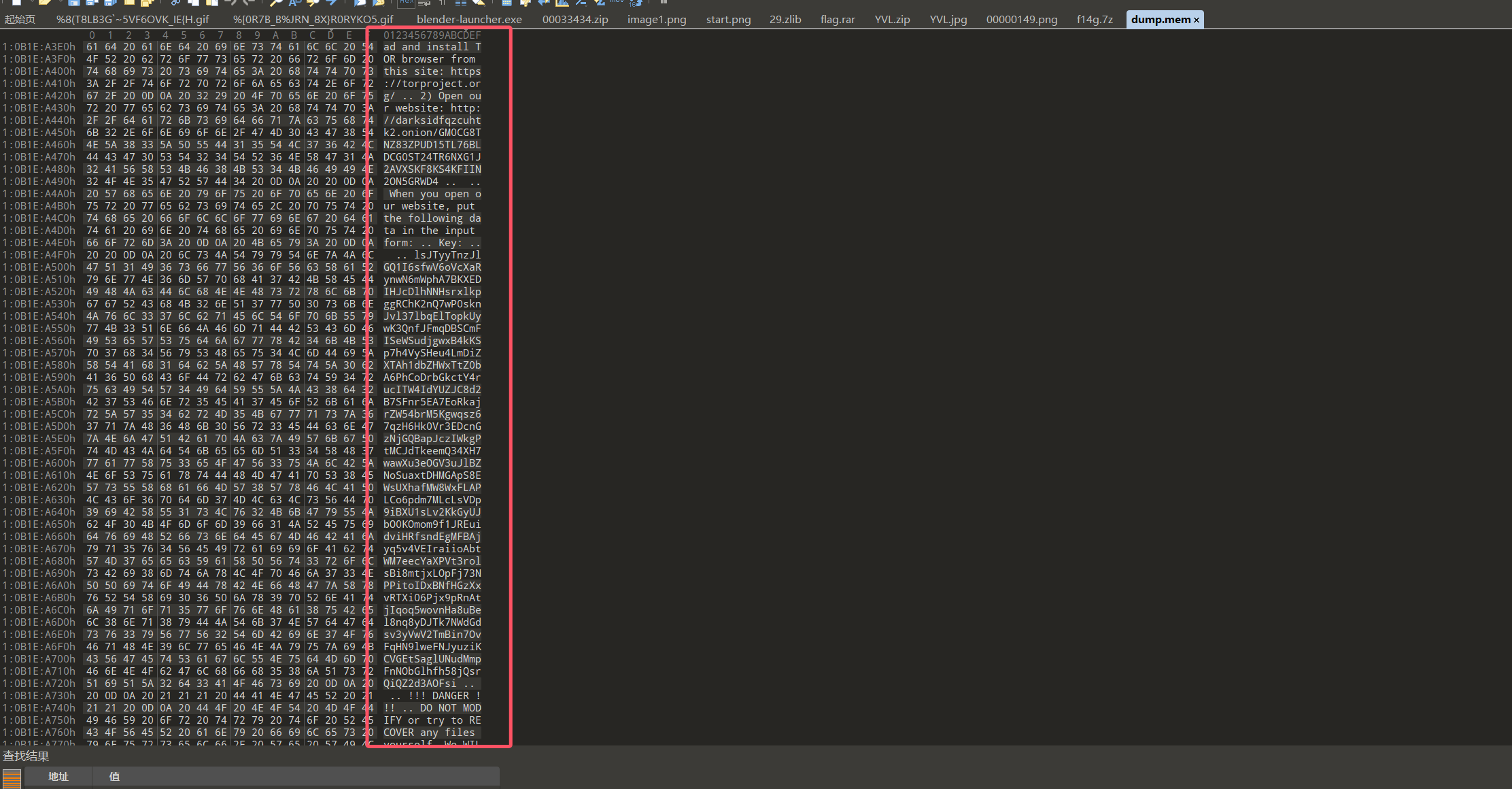
下面写了key
lsJTyyTnzJlGQ1I6sfwV6oVcXaRynwN6mWphA7BKXEDIHJcDlhNNHsrxlkpggRChK2nQ7wP0sknJvl37lbqElTopkUywK3QnfJFmqDBSCmFISeWSudjgwxB4kKSp7h4VySHeu4LmDiZXTAh1dbZHWxTtZ0bA6PhCoDrbGkctY4rucITW4IdYUZJC8d2B7SFnr5EA7EoRkajrZW54brM5Kgwqsz67qzH6Hk0Vr3EDcnGzNjGQBapJczIWkgPtMCJdTkeemQ34XH7wawXu3eOGV3uJlBZNoSuaxtDHMGApS8EWsUXhafMW8WxFLAPLCo6pdm7MLcLsVDp9iBXU1sLv2KkGyUJbO0KOmom9f1JREuidviHRfsndEgMFBAjyq5v4VEIraiioAbtWM7eecYaXPVt3rolsBi8mtjxLOpFj73NPPitoIDxBNfHGzXxvRTXi06Pjx9pRnAtjIqoq5wovnHa8uBel8nq8yDJTk7NWdGdsv3yVwV2TmBin7OvFqHN9lweFNJyuziKCVGEtSaglUNudMmpFnNObGlhfh58jQsrQiQZ2d3AOFsi然后用vol进行yarascan
PS E:\CTF\取证> .\volatility.exe -f .\dump.mem --profile=Win10x64_14393 yarascan -Y "lsJTyyTnzJlGQ1I"
Volatility Foundation Volatility Framework 2.6
Owner: Process svchost.exe Pid 5784
0x00d1a585 6c 73 4a 54 79 79 54 6e 7a 4a 6c 47 51 31 49 36 lsJTyyTnzJlGQ1I6
0x00d1a595 73 66 77 56 36 6f 56 63 58 61 52 79 6e 77 4e 36 sfwV6oVcXaRynwN6
0x00d1a5a5 6d 57 70 68 41 37 42 4b 58 45 44 49 48 4a 63 44 mWphA7BKXEDIHJcD
0x00d1a5b5 6c 68 4e 4e 48 73 72 78 6c 6b 70 67 67 52 43 68 lhNNHsrxlkpggRCh
0x00d1a5c5 4b 32 6e 51 37 77 50 30 73 6b 6e 4a 76 6c 33 37 K2nQ7wP0sknJvl37
0x00d1a5d5 6c 62 71 45 6c 54 6f 70 6b 55 79 77 4b 33 51 6e lbqElTopkUywK3Qn
0x00d1a5e5 66 4a 46 6d 71 44 42 53 43 6d 46 49 53 65 57 53 fJFmqDBSCmFISeWS
0x00d1a5f5 75 64 6a 67 77 78 42 34 6b 4b 53 70 37 68 34 56 udjgwxB4kKSp7h4V
0x00d1a605 79 53 48 65 75 34 4c 6d 44 69 5a 58 54 41 68 31 ySHeu4LmDiZXTAh1
0x00d1a615 64 62 5a 48 57 78 54 74 5a 30 62 41 36 50 68 43 dbZHWxTtZ0bA6PhC
0x00d1a625 6f 44 72 62 47 6b 63 74 59 34 72 75 63 49 54 57 oDrbGkctY4rucITW
0x00d1a635 34 49 64 59 55 5a 4a 43 38 64 32 42 37 53 46 6e 4IdYUZJC8d2B7SFn
0x00d1a645 72 35 45 41 37 45 6f 52 6b 61 6a 72 5a 57 35 34 r5EA7EoRkajrZW54
0x00d1a655 62 72 4d 35 4b 67 77 71 73 7a 36 37 71 7a 48 36 brM5Kgwqsz67qzH6
0x00d1a665 48 6b 30 56 72 33 45 44 63 6e 47 7a 4e 6a 47 51 Hk0Vr3EDcnGzNjGQ
0x00d1a675 42 61 70 4a 63 7a 49 57 6b 67 50 74 4d 43 4a 64 BapJczIWkgPtMCJd地址就是0x00d1a585
威胁分析5
请问,恶意软件在其进程中启用了多少个权限?
查看pid 5784的进程权限
PS E:\CTF\取证> .\volatility.exe -f .\dump.mem --profile=Win10x64_14393 privs -p 5784
Volatility Foundation Volatility Framework 2.6
Pid Process Value Privilege Attributes Description
-------- ---------------- ------ ------------------------------------ ------------------------ -----------
5784 svchost.exe 2 SeCreateTokenPrivilege Create a token object
5784 svchost.exe 3 SeAssignPrimaryTokenPrivilege Replace a process-level token
5784 svchost.exe 4 SeLockMemoryPrivilege Lock pages in memory
5784 svchost.exe 5 SeIncreaseQuotaPrivilege Present,Enabled Increase quotas
5784 svchost.exe 6 SeMachineAccountPrivilege Add workstations to the domain
5784 svchost.exe 7 SeTcbPrivilege Act as part of the operating system
5784 svchost.exe 8 SeSecurityPrivilege Present,Enabled Manage auditing and security log
5784 svchost.exe 9 SeTakeOwnershipPrivilege Present,Enabled Take ownership of files/objects
5784 svchost.exe 10 SeLoadDriverPrivilege Present,Enabled Load and unload device drivers
5784 svchost.exe 11 SeSystemProfilePrivilege Present,Enabled Profile system performance
5784 svchost.exe 12 SeSystemtimePrivilege Present,Enabled Change the system time
5784 svchost.exe 13 SeProfileSingleProcessPrivilege Present,Enabled Profile a single process
5784 svchost.exe 14 SeIncreaseBasePriorityPrivilege Present,Enabled Increase scheduling priority
5784 svchost.exe 15 SeCreatePagefilePrivilege Present,Enabled Create a pagefile
5784 svchost.exe 16 SeCreatePermanentPrivilege Create permanent shared objects
5784 svchost.exe 17 SeBackupPrivilege Present,Enabled Backup files and directories
5784 svchost.exe 18 SeRestorePrivilege Present,Enabled Restore files and directories
5784 svchost.exe 19 SeShutdownPrivilege Present,Enabled Shut down the system
5784 svchost.exe 20 SeDebugPrivilege Present,Enabled Debug programs
5784 svchost.exe 21 SeAuditPrivilege Generate security audits
5784 svchost.exe 22 SeSystemEnvironmentPrivilege Present,Enabled Edit firmware environment values
5784 svchost.exe 23 SeChangeNotifyPrivilege Present,Enabled,Default Receive notifications of changes to files or directories
5784 svchost.exe 24 SeRemoteShutdownPrivilege Present,Enabled Force shutdown from a remote system
5784 svchost.exe 25 SeUndockPrivilege Present,Enabled Remove computer from docking station
5784 svchost.exe 26 SeSyncAgentPrivilege Synch directory service data
5784 svchost.exe 27 SeEnableDelegationPrivilege Enable user accounts to be trusted for delegation
5784 svchost.exe 28 SeManageVolumePrivilege Present,Enabled Manage the files on a volume
5784 svchost.exe 29 SeImpersonatePrivilege Present,Enabled,Default Impersonate a client after authentication
5784 svchost.exe 30 SeCreateGlobalPrivilege Present,Enabled,Default Create global objects
5784 svchost.exe 31 SeTrustedCredManAccessPrivilege Access Credential Manager as a trusted caller
5784 svchost.exe 32 SeRelabelPrivilege Modify the mandatory integrity level of an object
5784 svchost.exe 33 SeIncreaseWorkingSetPrivilege Present,Enabled Allocate more memory for user applications
5784 svchost.exe 34 SeTimeZonePrivilege Present,Enabled Adjust the time zone of the computer's internal clock
5784 svchost.exe 35 SeCreateSymbolicLinkPrivilege Present,Enabled Required to create a symbolic link数一下enabled,23个
答案就是23
威胁分析6
请问,打开勒索软件文件的设备的虚拟地址是什么(16 进制)?
用volshell解析内存地址结构
PS E:\CTF\取证> .\volatility.exe -f .\dump.mem --profile=Win10x64_14393 volshell -p 5784
Volatility Foundation Volatility Framework 2.6
Current context: svchost.exe @ 0xffff9a8805cfb4c0, pid=5784, ppid=7136 DTB=0x30400000
Welcome to volshell! Current memory image is:
file:///E:/CTF/%C8%A1%D6%A4/dump.mem
To get help, type 'hh()'
>>> dt('_FILE_OBJECT',0xffff9a88056a9ef0)
[_FILE_OBJECT _FILE_OBJECT] @ 0xFFFF9A88056A9EF0
0x0 : Type 5
0x2 : Size 216
0x8 : DeviceObject 18446632507711949952
0x10 : Vpb 18446632507711953536
0x18 : FsContext 18446651757703889232
0x20 : FsContext2 18446651757801468480
0x28 : SectionObjectPointer 18446632507741760728
0x30 : PrivateCacheMap 0
0x38 : FinalStatus 0
0x40 : RelatedFileObject 0
0x48 : LockOperation 0
0x49 : DeletePending 0
0x4a : ReadAccess 1
0x4b : WriteAccess 0
0x4c : DeleteAccess 0
0x4d : SharedRead 1
0x4e : SharedWrite 0
0x4f : SharedDelete 1
0x50 : Flags 278594
0x58 : FileName \Users\skills\svchost.exe
0x68 : CurrentByteOffset 18446632507729944408
0x70 : Waiters 0
0x74 : Busy 0
0x78 : LastLock 0
0x80 : Lock 18446632507729944432
0x98 : Event 18446632507729944456
0xb0 : CompletionContext 0
0xb8 : IrpListLock 0
0xc0 : IrpList 18446632507729944496
0xd0 : FileObjectExtension 0DeviceObject就是设备的虚拟地址
转16进制得到0xffff9a8804580c80